what virus modifies the directory table entries so they point to the virus code instead of the actual program?
Answers
There is a type of virus known as a “cluster” virus that infects your files not by changing the file or planting extra files but by changing the DOS directory information so that directory entries point to the virus code instead of the actual program.
What is a directory table virus?Type of virus which will modify directory table entries so that it points users or system processes to the virus code instead of the actual program. There is only one copy of the virus on the disk infecting all the programs in the computer system.
When does a virus affect a computer?Some viruses affect computers as soon as their code is executed; other viruses lie dormant until a pre-determined logical circumstance is met. Identify the virus that modifies the directory table entries so that directory entries point to the virus code instead of the actual program.
To know more about cluster visit :-
https://brainly.com/question/15016224
#SPJ4
Related Questions
What system do businesses use to ensure products work correctly?
A. Access control
B. File management
C. Quality control
D. Quality procedures
Answers
Answer:
i believe it should be quality control
Explanation:
it kind of says it in the name quality control makes sure that the products are working and functioning correctly
tle electrical instulation maintance
1.what is inventory 2. what is job order 3. what is barrow form 4. what is purchase request
Answers
Inventory refers to the process of keeping track of all materials and equipment used in electrical insulation maintenance. A job order is a document that contains all the information necessary to complete a specific maintenance task.
Definition of the aforementioned questions1) Inventory refers to the process of keeping track of all materials and equipment used in electrical insulation maintenance. This includes maintaining a list of all the items in stock, monitoring their usage, and ensuring that there are enough supplies to meet the demands of the job.
2) A job order is a document that contains all the information necessary to complete a specific maintenance task. This includes details about the task, such as the materials and tools required, the location of the work, and any safety considerations.
3) A barrow form is a document used to request materials or equipment from the inventory. It contains details about the requested item, including the quantity, the purpose of the request, and the name of the person or team making the request. The form is usually signed by an authorized person and submitted to the inventory manager or other appropriate personnel.
4) A purchase request is a document used to initiate the process of purchasing new materials or equipment for the electrical insulation maintenance program. It contains details about the item to be purchased, including the quantity, the cost, and the vendor or supplier. The purchase request is typically reviewed and approved by a supervisor or manager before the purchase is made.
learn more about electrical insulation maintenance at https://brainly.com/question/28631676
#SPJ1
Which of the following BEST describes a front-end developer?
Answers
Answer:
plz give me BRAINLIEST answer
Explanation:
Definition: Front end development manages everything that users visually see first in their browser or application. Front end developers are responsible for the look and feel of a site. ... As a front end developer you are responsible for the look, feel and ultimately design of the site.
A front-end developer is a type of software developer who specializes in creating the user interface (UI) and user experience (UX) of a website or application. They are responsible for translating design mock-ups and wireframes into functional code using programming languages such as HTML, CSS, and JavaScript.
Front-end developers work on the client-side of web development, focusing on the visual aspects and interactions that users see and experience directly. They ensure that the website or application is visually appealing, responsive, and user-friendly across different devices and browsers.
In addition to coding, front-end developers collaborate closely with designers and back-end developers to integrate the UI with the back-end systems and databases. They may also be involved in optimizing the performance and accessibility of the front-end code, as well as testing and debugging to ensure smooth functionality.
Learn more about databases on:
https://brainly.com/question/30163202
#SPJ6
You work for a public relations (PR) firm and communicate regularly with the internal team and the clients on a PR campaign. You need to quickly send and receive professional messages that may contain text files and short media. These messages need to be accessible at any time of the day and in different time zones, and they should be able to reach all members (internal and external) relatively inexpensively. Which communication channel would best suit this purpose?
Answers
Answer:
You Need To Quickly Send And Receive Professional Messages That May Contain Text Files And Short Media. These Messages Need To Be Accessible At Any Time Of The Day And In Different ... You work for a public relations (PR) firm and communicate regularly with the internal team and the clients on a PR campaign.
Explanation:
Where will your project appear on the system if you save your project in the "shared" location?
Answers
However, in general, if you save your project in a shared location, it will be accessible to other users who have permission to access that shared location. The specific location or method of accessing the shared location may depend on the system or platform you are using. For example, on a networked computer system, the shared location may be a network drive or folder that other users can access over the network. On a cloud storage service, the shared location may be a shared folder or workspace that other users can access through their accounts. It is important to note that the specific details of how shared locations work may vary depending on the system or platform you are using, so it is always a good idea to consult the documentation or support resources for that particular system or platform if you have questions about how to use shared locations effectively.
Review the scenario below. Identify the conceptual model and the physical model from the scenario.
1. Zoe was about to go into a store to purchase drinks for the birthday party scheduled fort hat evening. Zoe knows that she needs drinks for 48 people and is expecting the store to accept a check for payment and to provide her with some assistance carrying the product to her car. Zoe wants to have carbonated drinks, non-carbonated drinks, and sugar free drinks. She is expecting to purchase eight six-packs. Zoe enters the store and discovers the entire drink distribution system is automated. She also discovers that the drinks come in varying package sizes and that she must choose the correct vending option for the products to be disbursed. Drinks are packaged in four-packs, six packs,and ten-packs.
2. Five reasons for creating a conceptual data model.
Answers
In the given scenario, the conceptual model refers to Zoe's understanding of the different types of drinks she needs, the quantity required, and her expectations from the store. The physical model pertains to the automated drink distribution system and the varying package sizes for the drinks.
The conceptual model in this scenario encompasses Zoe's understanding and expectations related to the drinks she needs for the birthday party. It includes her knowledge of the three types of drinks required (carbonated, non-carbonated, and sugar-free), the quantity needed for 48 people, and her expectation of purchasing eight six-packs. The conceptual model represents Zoe's mental representation of the situation and the required information.
On the other hand, the physical model in the scenario refers to the actual implementation of the drink distribution system in the store. Zoe discovers that the entire system is automated, indicating a physical representation of how drinks are dispensed. Additionally, the physical model includes the varying package sizes (four-packs, six-packs, and ten-packs) that Zoe must select to obtain the desired drinks from the vending system.
In summary, the conceptual model represents Zoe's understanding and expectations, while the physical model refers to the automated drink distribution system and the varying package sizes available in the store.
learn more about conceptual model here:
https://brainly.com/question/11274859
#SPJ11
PLS HURRY!!!
which of the following is NOT a benefit of using modules in programming?
A. modules can help break the problem down into smaller pieces
B. modules are reusable
C. modules do not contain syntaxes errors
D. modules save the programmer time instead of rewriting code.
Answers
C. modules do not contain syntax errors
Look at the color key below the map that shows the overall performance range. What is the range for 1 Year Performance? How does it compare to the 1 Day Performance range?
Answers
A performance range simply means the threshold and maximum percentage of shares that may become earned.
What is a performance range?Your information is incomplete. Therefore, an overview will be given. A performance range is the maximum percentage if shares that may become earned shares due to the attainment of the requirements of the performance.
It should be noted that in this case, the opportunity to incentivize performance will be associated with the relative performance.
Learn more about performance on:
https://brainly.com/question/26256535
TB MC Qu. 01-119 (Static) The following information relates... The following information relates to the manufacturing operations of the JNR Compary for the year: The raw materials used in manufacturing during the year totaled \$118.000. Raw materials purchased during the year amount to Multiple Choice 5107,000 5115.000 5118.000 $121000 $126000
Answers
The raw materials used in manufacturing by JNR Company during the year amounted to $118,000. The raw materials purchased during the year totaled $121,000.
In the manufacturing operations of JNR Company for the year, the total cost of raw materials used was $118,000. This cost represents the value of raw materials consumed in the production process. It includes materials that were transformed and incorporated into the final products. These raw materials could include components, parts, or ingredients required for the manufacturing process.
Additionally, the company purchased raw materials worth $121,000 during the year. This amount reflects the total expenditure made by the company on acquiring new raw materials to support its manufacturing operations. Purchased raw materials are typically added to the company's inventory and are available for use in future production cycles.
The difference between the cost of raw materials used ($118,000) and the raw materials purchased ($121,000) suggests that the company may have utilized some of its existing inventory from previous periods. This could be due to factors such as efficient inventory management, optimization of production processes, or the use of recycled materials.
Overall, the JNR Company used $118,000 worth of raw materials in its manufacturing operations for the year, while purchasing raw materials worth $121,000 to replenish its inventory and support future production needs.
To learn more about JNR company visit:
brainly.com/question/15261370
#SPJ11
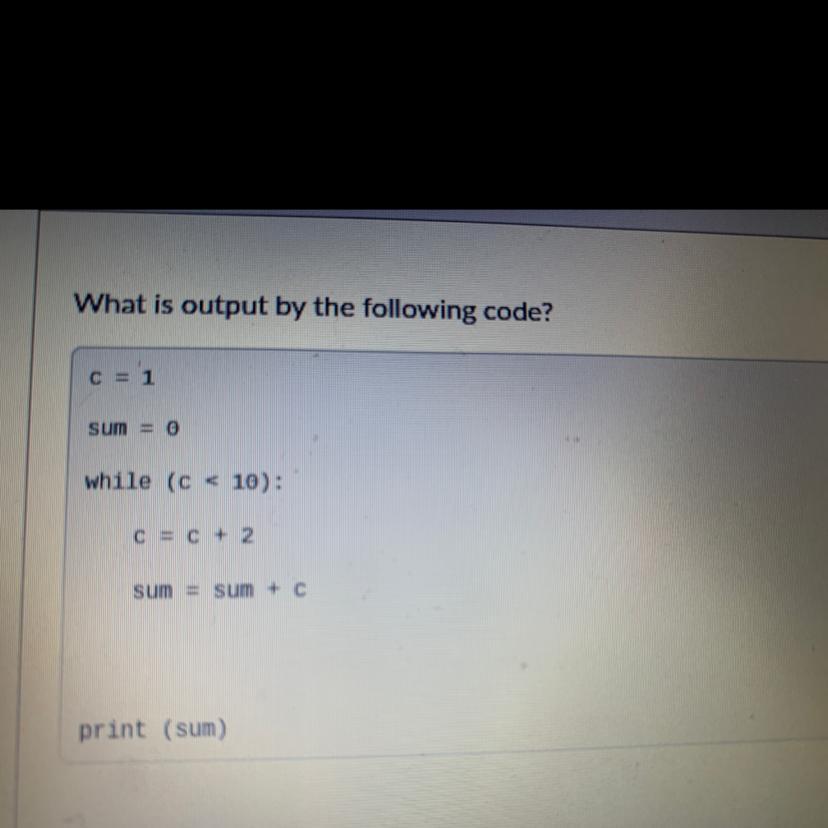
What is output by the following code?
C = 1
sum = 0
while (c 4 10):
C=C+2
sum = sum + c
print (sum)
Answers
Answer :
Sum = 3,8,15,24,35
Steps :
Initially, c = 1, so
while (c=1 < 10)
c= 1+2 =3
Sum = 0 + 3 = 3
while (c=3 < 10)
c= 3+2 =5
Sum = 3 + 5 = 8
while (c=5 < 10)
c= 5+2 =7
Sum = 8 + 7 = 15
while (c=7 < 10)
c= 7+2 =9
Sum = 15 + 9 = 24
while (c=9 < 10)
c= 9+2 =11
Sum = 24 + 11 = 35
Therefore, Sum = 3,8,15,24,35
You can learn more about while loop from the given link:
https://brainly.in/question/16569909
#SPJ13
A security system is desired that can be used to detect whenever any one of two doors in a house and any one of two windows are open. Derive a boolean expression from this description and draw the corresponding logic network that can be used to solve the problem.
Answers
Answer:
Z = A + B
Explanation:
The logic network can be seen attached below. This basically shows that if either of the two inputs are True then the output would apply. In this scenario, the output would be the alarm going off. Since either one of the windows being opened in this scenario would set off the alarm then the logic operator that needs to be used would be OR. In this scenario, the two windows are represented by the variables A and B while the output can be represented by the variable Z. Using these variables, we can apply the following boolean expression.
Z = A + B

How do I make audio sound better in Adobe Audition?
Answers
1. Clean up background noise: Use the noise reduction tool to reduce any background noise in the audio.
What is noise?Noise is a term used to describe unwanted sound. It is an unwanted and undesired sound that has no informational content or meaning and can be heard in everyday life.
2. Normalize levels: Use the normalize effect to make sure the audio is at a consistent level.
3. Adjust EQ: Use the equalizer effect to adjust the frequencies and tone of the audio.
4. Adjust Dynamics: Use the dynamics effect to adjust compressor, expander, and limiter settings to adjust the overall level of the audio.
5. Add Reverb: Use the reverb effect to add space and depth to the audio.
6. Apply Effects: Use effects such as chorus, delay, and flanger to enhance the sound of the audio.
7. Bounce: Bounce the audio to a new file to save the changes.
To learn more about noise
https://brainly.com/question/30369845
#SPJ4
Click on the arrow in A. What will enable you to do?
Answers
Answer:
We need a picture
Explanation:
What does a computer program use as a means to evaluate a condition as True or False?
Answers
Answer:
true
Explanation:
Answer:
A Boolean expression.
Explanation:
A Boolean expression is a logical statement that is either TRUE or FALSE . Boolean expressions can compare data of any type as long as both parts of the expression have the same basic data type.
N an AWS design template, the "depends on" property of a resource is represented by an _________ color dot. Red Orchid Blue Black
Answers
Answer:
Black
Explanation:
Explicit dependencies in Amazon Web Services are used to determine the order in which resources are added or deleted on AWS Cloud Formation. If a user wishes to create explicit dependency, a line from the "dependson" dot located at the route is moved to the gateway-VPC attachment.
The "dependson" dot helps to specify which resource is created before another. It is signified by a black dot (*). It can be used to override parallelisms and also to determine when a wait condition becomes activated.
(100 points) Which sentences in the passage are true concerning a function?
Which sentences in the passage are true concerning a function?
A spreadsheet function takes values in the form of arguments, performs a calculation, and returns a result. All spreadsheet functions start with the hash sign (#). The arguments go inside angle brackets, < and >, and are always separated by colons (:). Instead of specifying constants as arguments, it generally makes more sense to use cell references. You can even specify a range of cells by using a comma (,) in place of a colon (:).
I wont see this answer so no brainliest, just putting this question here to hopefully help someone in the future who needs a answer. This question is from epic.
Answers
Answer:All spreadsheet functions start with the hash sign (#). .
Explanation:This is the answer it has function
Let's say you are the Robot (Give yourself a name) you are talking to the customer.
The customer wants to purchase a bicycle.
The customer wants to know the purchase of the 3 bicycles. What's included in the total cost? Taxes 8%
How will the customer be paying? Will this customer needs deliver or they will pickup?
Use your mathematical operators....
Answers
Let the robot's name be Alpha.
Alpha will follow a predetermined algorithm to interact with the customer.
Algorithm -
Alpha: Hello. Please select the model of the bicycle from the list.
Alpha: The selected model's MRP is $x.
Alpha: The MRP will be subject to an additional 8% tax.
Alpha: Total cost of 1 bicycle is MRP+(8% of MRP).
Alpha: Total cost of 3 bicycle is 3*(MRP+(8% of MRP)).
Alpha: Choose a payment option from the list.
Alpha: Choose the delivery option. Pickup or home delivery
What is an Algorithm?
A set of finite rules or instructions to be followed in calculations or other problem-solving operations or A procedure for solving a mathematical problem in a finite number of steps that frequently involves recursive operations.
For example,
An algorithm to add two numbers:
• Take two number inputs
• Add numbers using the + operator
• Display the result
To know more about how Algorithm works, kindly visit: https://brainly.com/question/15802846
#SPJ13
Daniel has a list of numbers that are not in any order. He wants to find the order of the numbers with the help of a spreadsheet. Which statistical function will help him do so?
Answers
Answer:
The rank function
Explanation:
Required
Function to find the order of a list
In a spreadsheet application (say Microsoft Office Excel), the rank function are used to execute what Daniel wants to achieve with the list of numbers (i.e. determine their order)
The syntax to do use this function is:
=RANK (number, ref, [order])
Where
number = the number to rank
ref = The range to rank
order = Whether to rank in ascending or descending order
in the destroy phase of the data lifecycle, a data analyst might shred paper files. 1 point true false
Answers
The given statement, "in the destroy phase of the data lifecycle, a data analyst might shred paper files," is true (T) because shredding paper files ensures that the information contained within them cannot be recovered or accessed by unauthorized individuals.
When data has reached the end of its useful life or is no longer required, it must be securely disposed of to prevent it from falling into the wrong hands. In the case of paper files, shredding is a common method of destruction. This involves using a machine to cut the paper into small pieces, making it impossible for someone to piece together the information it contained.
Shredding ensures that confidential or sensitive information is not accidentally or deliberately leaked, and is a standard practice in industries such as healthcare, finance, and legal services.
Learn more about the destroy phase https://brainly.com/question/30327656
#SPJ11
Thinking carefully about a speaker's reasoning and purpose can help you _____ that speaker's message. In other words, you consider the message and decide whether it is believable.
Answers
Thinking carefully about a speaker's reasoning and purpose can help you comprehend (understand) that speaker's message. In other words, you consider the message and decide whether it is believable.
What do you think is the purpose of the speakers in their speech?Making sense of the world around us is referred to as reasoning. A communication must be evaluated during critical listening in order to be accepted or rejected. Critical listening can be practiced while listening to a sales pitch.
Speakers must provide proof to back up their claims in order to be convincing. Listeners who pay close attention are wary of assertions and generalizations. When the speaker is not regarded as an authority on the subject of the speech, strong evidence is especially crucial.
Therefore, When communicating, speakers aim to achieve both broad and detailed goals. There are two main goals for speaking in college and beyond: to inform or to persuade. There is no clear distinction between the two; many talks will combine elements of both.
Learn more about reasoning from
https://brainly.com/question/25175983
#SPJ1
Irene wants to connect her smartphone wirelessly to her laptop in order to transfer images. Which two technologies could she reasonably employ to connect these devices?
Wi-Fi
infrared
satellite
mobile network
Bluetooth
Answers
Answer:
The correct answers are
Wifi
Bluetooth
Explanation:
I got it right on the Edmentum test.
Irene wants to connect her smartphone wirelessly to her laptop in order to transfer images two technologies could she reasonably employ to connect these devices are Wi-Fi and Bluetooth.
What is the wireless network?As an example, it's far usually hired in headsets for cell phones, allowing hands-unfastened cell smartphone use. Wi-Fi, on the alternative hand, lets in gadgets hook up to the Internet. Bluetooth limits the range of gadgets that can join at someone's time, while Wi-Fi is open to greater gadgets and greater users.
Wi-Fi is possibly the largest and maximum tricky example, as are different Bluetooth receivers and gadgets, that can intrude on one another. The backside line is this: WiFi is the wi-fi community you operate to your house, however it is able to be made out of any form of network connection.
Read more about the mobile network:
https://brainly.com/question/917245
#SPJ2
In Microsoft Windows 10,

Answers
Answer: Cancel all Print Jobs
Explanation: Whoever gave you this clearly doesn't know how to themselves cause the exact wording to cancel all print jobs is as follows
"Cancel All Documents". if this was a teacher tell them to read up on their technology skills before they give the next test. I'm currently working on my Master's in computer Programming and have been working with Computers for over 15 years. I could put a better multiple choice quiz together in less than 10 mins. I wonder how long it took this idiot to put that quiz together.
"Caller ID" is the feature that displays the telephone number of the caller on the telephone of the person he or she calls. With Caller ID now routine and widely used, it might be surprising that when the service was first available, it was very controversial because of privacy implications. (a) What aspect of privacy (in the sense of Section 2.1.1) does Caller ID protect for the recipient of the call? What aspect of privacy does Caller ID violate for the caller? (b) What are some good reasons why a nonbusiness, noncriminal caller might not want his or her number displayed?
Answers
Answer: Provided in the explanation section
Explanation:
please follow this explanation for proper guiding.
(a)
i. What aspect of privacy does Caller ID protect for the recipient of the call?
* The beneficiary of the call utilizing the Caller ID highlight becomes more acquainted with who precisely the guest is, independent of the guest being a decent/terrible individual or authentic/ill-conceived call.
* Depending on how the call went or wound up, i.e., the discussion, business, messages passed on, the beneficiary would have the option to act in like manner and suitably dependent on the guest and his message's respectability, habits, morals, demonstrable skill, or telephone decorums, and so forth.
* Also, the beneficiary gets the alternative to choose how to manage the call even before him/her picking the call, when he/she comes to know who the guest is through Caller ID include, the beneficiary gets security by either separating the call, sending or diverting the call, recording the call, not noting the call, or in any event, blocking or announcing the number in any case. Along these lines, the beneficiary's security is ensured from various perspectives.
ii. What aspect of privacy does Caller ID violate for the caller?
* Even however as it were, in fact it distinguishes, confirms, and validates the guest demonstrating he/she is who he/she professes to be. In any case, the guest ID highlight or innovation unveils numerous information and data about the guest, for example, his accurate phone number or PDA number, nation code, the specific phone or versatile transporter organize he/she is utilizing, and so on., as this data may make dangers the guest's security, (for example, character burglaries or just assailants caricaturing others utilizing this current guest's data), classification, it might cause accessibility issue for the guest as when the guest is besieged with ill-conceived calls, spam, and undesirable calls, there are chances their telephone numbers could and would be imparted to many advertising and selling organizations or industry without the guest's assent, there are chances somebody focusing on the guest may tap or wire his/her significant, basic business, social, expert, individual, or private calls for touchy data to assault them and abuse the bantered data. The guest certainly loses his/her secrecy, opportunity, directly for discourse, security, and wellbeing when passing on messages over the call when they know there could be somebody tapping or recording the call, or even the beneficiary may abuse the guest's character and his/her passed on data.
* Hence, the guest doesn't get the opportunity from reconnaissance i.e., from being followed, followed, watched, and spying upon by trouble makers.
* The guest would lose the control of their data on how it would be put away or utilized.
* The guest probably won't get opportunity from interruptions.
(b). What are some good reasons why a non-business, non-criminal caller might not want his or her number displayed?
* A non-business and a noncriminal guest would need to enjoy typical, common, and regular exercises; mingle and do his/her own day by day close to home, private, and public activities' assignments, occupations, occasions, social occasions, correspondences, individuals organizing, and so on., without making any whine about things, exposure stunts, without causing anyone to notice tail, screen, follow, question, or explore the guest superfluously except if the guest has enjoyed, asked, stated, discussed, or passed on any message that is unlawful, exploitative, wrongdoing, and culpable.
* Such a guest would need total or most extreme namelessness, as to them, guest ID innovation just uncovers their own and private life exercises, correspondences, and so forth., to others to pass judgment on them, question them, and later cross examine and research them on their interchanges.
* Such guests for the most part search for security in general.
* Specifically, such guests need classification of their calls, discussions, messages, call logs, and so forth.
* The beneficiary on occasion may get the guest's private unlisted number without the guest's assent or authorization.
* The beneficiary may utilize the guest's telephone number and name to get a lot other data about him/her, which the beneficiary should, that would incorporate the guest's location (area) through an opposite catalog or just turning upward in any phone registry.
* The beneficiary might not have any desire to talk, mingle, or work with the guest in view of the area (address), ethnicity (from the name), race, or district the guest is from.
A mixed reality application detects the spatial layout of a room and is able to overlap or hide a virtual object based on its position in the image. what effect makes this possible?
modeling
occlusion
tethering
virtualization
Answers
The effect that makes it possible for a mixed reality application to detect the spatial layout of a room and overlap or hide a virtual object based on its position in the image is called occlusion.
In computer vision, occlusion is the act of hiding or obstructing an item or object from view. Occlusion is used in augmented and mixed reality systems to conceal virtual objects that are obstructed by real objects in the environment. It gives the appearance that virtual objects are interacting with the real world by obscuring objects behind or in front of them.
A mixed reality application is an application that allows users to experience a combination of the real and virtual worlds. It detects and maps the physical world to construct a mixed reality environment. Mixed reality applications can overlay digital images, videos, and animations onto real-world objects, as well as provide interactive experiences for users.
Learn more about Computer Vision: https://brainly.com/question/14471845
#SPJ11
(a)What is digital literacy
(b)state two benefits of digital divide
(c)list and explain the (2) types of digital literacy.
(Computer Studies.)
Answers
Digital literacy refers to the ability to use, understand, and critically evaluate digital technologies and media. It includes skills such as using a computer and the internet, creating and editing digital content, and understanding how to protect oneself online.
There are several benefits to closing the digital divide, which refers to the gap between individuals and communities that have access to digital technologies and those that do not. Some of these benefits include:
Improved access to information and education: Digital literacy enables individuals to access a vast amount of information and educational resources online, which can help to increase knowledge and skills.Increased economic opportunities: Digital literacy can help individuals to find jobs and participate in the global economy. It can also help businesses to expand their reach and increase productivity.Enhanced social connections: Digital literacy can help individuals to connect with others and participate in online communities, which can help to improve social connections and support networks.There are two main types of digital literacy:
Basic digital literacy: This refers to the basic skills and knowledge needed to use digital technologies and media, such as navigating websites, using email, and protecting oneself online.Advanced digital literacy: This refers to more advanced skills and knowledge related to creating and manipulating digital content, such as coding, graphic design, and video editing.
Both types of digital literacy are important for different reasons. Basic digital literacy is essential for participating in modern society and accessing information and services online. Advanced digital literacy can open up additional career opportunities and enable individuals to create and share their own digital content.
Working on this program in Python 3.7:A year in the modern Gregorian Calendar consists of 365 days. In reality, the earth takes longer to rotate around the sun. To account for the difference in time, every 4 years, a leap year takes place. A leap year is when a year has 366 days: An extra day, February 29th. The requirements for a given year to be a leap year are:1) The year must be divisible by 42) If the year is a century year (1700, 1800, etc.), the year must be evenly divisible by 400Some example leap years are 1600, 1712, and 2016.Write a program that takes in a year and determines whether that year is a leap year.Ex: If the input is 1712, the output is:1712 is a leap year. Ex: If the input is 1913, the output is:1913 is not a leap year. Your program must define and call the function IsLeapYear(userYear). The function should return true if the input year is a leap year and false otherwise.
Answers
Answer:
def is_leap_year(year):
if(year % 400 == 0):
return True
elif year % 100 == 0:
return False
elif year%4 == 0:
return True
else:
return False
if __name__ == '__main__':
n = int(input())
if(is_leap_year(n)):
print(n,"is a leap year.")
else:
print(n, "- not a leap year")
Explanation:
PLZ HURRY TIMED 20 POINTS + BRAINLEIST
Describe a situation where video conferencing software would make things easier for a business.
Answers
Answer:
Corona Virus
Explanation:
Perdón necesito los puntos, te quiero
Determine the consequence frequency for a regulator failure if the system is designed with three IPLs, (Assuming PFD = 10-2 For the toolbar, press ALT+F10 (PC) or ALT+FN+F10 (Mac).
Answers
Main answer: The consequence frequency for a regulator failure, with a system designed with three IPLs and a PFD of 10-2, is expected to be low.
Explanation:
When evaluating the consequence frequency of a regulator failure, several factors come into play, including the number of independent protection layers (IPLs) and the probability of failure on demand (PFD). In this case, the system is designed with three IPLs, which implies that there are multiple layers of protection in place to prevent or mitigate a regulator failure. Additionally, the PFD value of 10-2 suggests a relatively low probability of failure on demand, indicating a reliable and well-designed system.
Having three IPLs enhances the system's overall reliability as each layer provides an additional safeguard against a regulator failure. If one layer fails, the remaining IPLs act as backups, reducing the likelihood of a catastrophic event. This redundancy in protection contributes to a lower consequence frequency, meaning that the frequency of severe consequences resulting from a regulator failure is expected to be rare.
The PFD value of 10-2 further reinforces the reliability of the system. PFD represents the probability that a safety instrumented function (SIF) will fail to perform its intended task upon demand. A PFD of 10-2 implies that there is only a 1 in 10,000 chance of failure on demand for the regulator. This level of reliability indicates that the system has undergone thorough design, engineering, and testing processes to ensure the appropriate functioning of the regulator.
In summary, a system designed with three IPLs and a PFD of 10-2 for a regulator failure is expected to have a low consequence frequency. The multiple layers of protection and the low probability of failure on demand contribute to a robust and reliable system, reducing the likelihood of severe consequences resulting from a regulator failure.
Learn more about:
The concept of independent protection layers (IPLs) in process safety is vital for designing reliable systems. Each IPL acts as a barrier against potential hazards, and having multiple IPLs increases the overall safety and reduces the chances of a catastrophic event. Additionally, understanding the calculation of probability of failure on demand (PFD) provides insights into the reliability of safety instrumented functions (SIFs) and their ability to perform their intended tasks when required. By implementing multiple IPLs and ensuring a low PFD, industries can enhance safety measures and mitigate risks effectively. #SPJ11
Larry has created a web page using HTML 4.01. He hasn’t included the declaration in the file. When he opens the page in a browser, Larry sees a page load error. Why does Larry need to use the declaration in an HTML file?
A.
to define the HTML version in which the page is written
B.
to define the web language in which the page is written
C.
to tell the browser what the content is
D.
to check whether the code is error-free
Answers
Answer:
To define the html version in which the page is written.

Helppppppppppp please

Answers
Answer:
1.75
Explanation:
It is marked at 3/4 (.75) of the line so it would be 1.75