What profession do you prefer to have in the future? In what way could you make an impact on society using the Internet?
Answers
Answer:
lawyer
Explanation:
by helping my society in terms of solving land cases that have been not settled in our history
Related Questions
a table of contents does not _____ automatically [customize table of contents]
Answers
Answer:
update
Explanation:
a table of contents does not update itself automatically.
You're the network administrator for a consulting firm. Your network consists of the following:
• 30 laptops in the sales department
10 computers for HR
• 5 laptops for management
• 20 computers in marketing
• 15 computers in IT
You're using Microsoft Intune to manage the company's devices. You've configured an update ring named Management and
enrolled the ring in the Semi-Annual Servicing Channel. You've also set updates to be delayed for 30 days, which gives you ample
time to test them before they're rolled out to the user machines. However, you want to make sure you can rollback a feature
update if a problem comes up after the update has been installed on the user machines.
What is the maximum number of days you can configure a feature update uninstallation period for?
Answers
Answer:
anytime
Explanation:
as far as i know you can manage in real time meaning add or remove any hardware or software anytime but im not sure once its rewritten each is considered version 1.0 but uninstallation happens each time you reinstall so uninstallation is actualy anytime
last i checked all tho trial activation is usualy one week or one month so 7 or 30 days till installation but uninstall is anytime unless it service or updates
Describe the examples of expressions commonly used in business letters and other written communications with some clearer alternatives:
Answers
When writing business letters and other written communications, it is important to use expressions that convey your message clearly and professionally.
Here are some examples of commonly used expressions in business letters along with clearer alternatives:
1. "Enclosed please find" → "I have enclosed"
This phrase is often used to refer to attached documents. Instead, simply state that you have enclosed the documents.
2. "As per our conversation" → "As we discussed"
Rather than using a formal phrase, opt for a more conversational tone to refer to previous discussions.
3. "Please be advised that" → "I want to inform you that" or "This is to let you know that"
Instead of using a lengthy phrase, use more straightforward language to convey your message.
4. "In regard to" → "Regarding" or "Regarding the matter of"
Use a more concise phrase to refer to a specific topic or issue.
5. "We regret to inform you" → "Unfortunately" or "I'm sorry to say"
Instead of using a lengthy expression, choose simpler words to deliver disappointing news.
Remember, it is important to maintain a professional tone while also ensuring that your message is clear and easy to understand. Using simpler alternatives can help improve the readability of your business letters and written communications while still maintaining a polite and professional tone.
For more such questions on letters,click on
https://brainly.com/question/18319498
#SPJ8
Many companies use telephone numbers like 555-GET-FOOD so the number is easier for their customers to remember. On a standard telephone, the alphabetic letters are mapped to numbers in the following fashion: A, B, and C = 2 D, E, and F = 3 G, H, and I = 4 J, K, and L = 5 M, N, and O = 6 P, Q, R, and S = 7 T, U, and V = 8 W, X, Y, and Z = 9 Write a program that asks the user to enter a 12-character telephone number in the format: XXX-XXX-XXXX. Acceptable characters (X's) are A-Z and a-z. Your program should check for: The length of the phone number is correct. The dashes are included and are in the correct positions. There are no characters in the illegal characters in the string. The application should display the telephone number with any alphabetic characters that appeared in the original translated to their numeric equivalent. If the input string is not entirely correct then you should print an error message. For example, if the user enters 555-GET-FOOD the program should display 555-438-3663. If the user enters 123-456-7890, the program should display 123-456-7890. Rules: You must have one function (in addition to main()) that converts an alphabetic character to a digit. Or you can have one function that coverts all characters to digits. You can make your own function or use a built-in function if one exists.
Answers
Answer:
The program in Python is as follows:
def convertt(phone):
splitnum = phone.split ('-')
valid = True
count = 0
err = ""
numphone = ""
if len(phone) != 12:
err = "Invalid Length"
valid = False
elif phone[3] != '-' or phone[7] != '-':
err = "Invalid dash [-] location"
valid = False
while valid== True and count < 3:
for ch in splitnum[count]:
if ch.isdigit():
numphone += ch
elif ch.upper()in 'ABC':
numphone += '2'
elif ch.upper()in 'DEF':
numphone += '3'
elif ch.upper()in 'GHI':
numphone += '4'
elif ch.upper() in 'JKL':
numphone += '5'
elif ch.upper()in 'MNO':
numphone += '6'
elif ch.upper()in 'PQRS':
numphone += '7'
elif ch.upper()in 'TUV':
numphone += '8'
elif ch.upper()in 'WXYZ':
numphone += '9'
else:
valid = False
err = "Illegal character in phone number"
if count!=2:
numphone += '-'
count += 1
if valid == False:
print (err)
else:
print ("Phone Number", numphone)
phone = input("Phone number: ")
convertt(phone)
Explanation:
See attachment for complete source code where comments are used for explanation
Describe what should go into the blank space:
public class
A. a keyword
B. java syntax
C. a command
D. the name of the program
Answers
Answer:
d
Explanation:
Write and execute a query that will determine the average number of days that automobiles are rented. Show your result broken out by makes. Do not include an automobile if it has not yet been returned.
Answers
Using the knowledge in computational language in SQL it is possible to write a code that query that will determine the average number of days that automobiles are rented
Writting in SQL:select Customer.CID,CName,Age,Resid_City,BirthPlace,
Rentcost.Make,Cost,Rentals.Rtn,Date_Out,Pickup,Date_returned,Return_city
from Customer,Rentcost,Rentals where
Customer.CID=Rentals.CID and Rentcost.Make=Rentals.Make
order by Customer.CID, Rentcost.Make asc;
select Customer.CID,CName from Customer,Rentals where Customer.CID=Rentals.CID
and Pickup='Cary';
select distinct(CName),age from Customer,Rentals where Customer.CID=Rentals.CID
and Return_city='Erie' order by CName asc;
select Customer.CID,CName from Customer,Rentals where Customer.CID=Rentals.CID
and Return_city is null;
select CName from Customer,Rentals where Customer.CID=Rentals.CID
and Resid_City=Pickup;
See more about SQL at brainly.com/question/13068613
#SPJ1

Abstract: Design, implement, explain, test, and debug a simple, but complete command- line interpreter named cli.
Detail: Design, implement, document, test and run a simple shell, known here as a command-line interpreter (cli). This tool is invoked via the cli command plus possible arguments. Commands are OS commands to be executed. Multiple commands are separated from one another by commas, and each may in turn require further arguments. Cli 'knows' a list of commands a-priori; they are predefined. When invoked, cli checks, whether the first argument is an included command. If so, cli confirms this via a brief message. If not, a contrary message is emitted, stating this is not one the predefined commands. After the message, cli executes all commands in the order listed. After executing the last command, cli prints the current working directory, i.e. it acts as if the pwd command had been issued. Sample runs are shown further below.
Multiple commands of cli must be separated from one another by commas. Possible parameters of any one command are separated from the command itself (and from possible further parameters) by white space. White space consists of blanks, tabs, or a combination, but at least 1 blank space. Here some sample runs with single and multiple commands; outputs are not shown here: .
/cli pwd looks like Unix command pwd; is your sw .
/cli rm -f temp, mv temp ../temp1 ditto: input to your running homework 5
./cli ls -la another "single unix command"
./cli rm a.out, gcc sys.c, cp a.out cli
Cli starts out identifying itself, also naming you the author, and the release date. Then cli prints the list of all predefine commands. Finally, cli executes all commands input after the cli invocation. For your own debug effort, test your solution with numerous correct and also wrong inputs, including commas omitted, multiple commas, leading commas, illegals commands, other symbols instead of commas etc. No need to show or hand-in your test and debug work.
The output of the cli command "cli pwd" or "./cli pwd" should be as shown below, assuming your current working directory is ./classes Sac State/csc139. Here is the output of a sample run with a single command line argument:
herbertmayer$ ./cli pwd
hgm cli 4/12/2020
Legal commands: cd exec exit gcc Is man more mv rm pwd sh touch which $path
2 strings passed to argv[]
next string is 'pwd'
new string is 'pwd
1st cind 'pwd' is one of predefined
/Users/herbertmayer/herb/academia/classes Sac State/csc139
Here the output of another sample run, also with a single cli command:
herbertmayer$ ./cli ls
hgm cli 4/12/2020
Legal commands: cd exec exit gcc ls man more mv rm pwd sh touch which Spath
2 strings passed to argv[]
next string is 'ls'
new string is 'ls!
1st cmd 'is' is one of predefined. admin cli.c sac state yyy
backup 1 24 2020 docs sac state hw
backup 3 9 2020 grades sac state xxx
cli 1 notes
/Users/herbertmayer/herb/academia/classes Sac State/csc139
Interpretation of commands that cli handles can proceed through system(), executed from inside your C/C++ program cli.
List of all commands supported by your cli:
char * cmds [ ] = {
"cd",
"exec",
"exit",
"gcc",
"ls",
"man",
"more",
"mv",
"Im
"pwd"
"sh",
"touch",
"which",
"Spath"
What you turn in:
1. The source program of your homework solution; well commented, preferably one single source file.
2. Four progressively more complex executions of your correctly working cli program, showing all user inputs and corresponding output responses.
Answers
Answer:
that is very long question ask a profesional
Explanation:
identify any mechanism (gear, lever etc.) that is common to haul trucks, forklifts, graders, and excavators. (2)
describe the operation of this mechanism you have identified. (4)
Answers
One common mechanism found in haul trucks, forklifts, graders, and excavators is the hydraulic system.
How do they work?The hydraulic system operates using fluid pressure to generate force and control various functions.
It consists of a hydraulic pump that pressurizes the fluid, hydraulic cylinders that convertthe fluid pressure into mechanical force, and control valves that regulate the flow of fluid.
This system enables the machines to perform tasks such as lifting heavy loads, steering,and controlling attachments with precision.
Learn more about hydraulic system at:
https://brainly.com/question/2166835
#SPJ1
Explain how navigation aids work.
Answers
Answer:
VOR facilities allow the pilot to follow a designated flight path by using the aircraft's cockpit gauges to indicate their positions. ILS transmits guidance beams to allow the pilot to land safely and efficiently.
Explanation:
GThe transmiter must beresolved in order to guide the transmission to arcraft
Words that when clicked on can link to another website are called:
Answers
Answer:
hyperlink
Explanation:
youwelcome:)
I need help
I am thinking about coming out to my mom because we are going to the store today and I will be in the car, I dont know if I should or not
Answers
Answer:
do it! you will have to one day so why not now? hopefully she will understand and say nice things as well and be like mom ive
been thinking a lot and i really want to tell you something. Explanation:
Answer:most likely she is your parent that you live with so she might already know but has not said anything it also depends her personality but if your ready and know or think she would not hate you forever go for it
Explanation:
Write a program that reads a list of integers, and outputs whether the list contains all even numbers, odd numbers, or neither. The input begins with an integer indicating the number of integers that follow.If the input is:5246810Then the output is:all evenIf the input is:513579
Answers
Answer:
uuuuu
Explanation:
Answer:
57677748957394209690369-34064666
Explanation:
Create a TeeShirt class for Toby’s Tee Shirt Company. Fields include:
orderNumber - of type int size - of type String color - of type String price - of type double Create set methods for the order number, size, and color and get methods for all four fields. The price is determined by the size: $22.99 for XXL or XXXL, and $19.99 for all other sizes. Create a subclass named CustomTee that descends from TeeShirt and includes a field named slogan (of type String) to hold the slogan requested for the shirt, and include get and set methods for this field.
Answers
Answer:
Here is the TeeShirt class:
public class TeeShirt{ //class name
private int orderNumber; // private member variable of type int of class TeeShirt to store the order number
private String size; // to store the size of tshirt
private String color; // to store the color of shirt
private double price; // to store the price of shirt
public void setOrderNumber(int num){ //mutator method to set the order number
orderNumber = num; }
public void setColor(String color){ //mutator method to set the color
this.color = color; }
public void setSize(String sz){ //mutator method to set the shirt size
size = sz;
if(size.equals("XXXL") || size.equals("XXL")){ //if shirt size is XXL or XXXL
price = 22.99; // set the price to 22.99 if shirt size is XXL or XXXL
}else{ //for all other sizes of shirt
price = 19.99; } } //sets the price to 19.99 for other sizes
public int getOrderNumber(){ //accessor method to get the order number stored in orderNumber field
return orderNumber; } //returns the current orderNumber
public String getSize(){ //accessor method to get the size stored in size field
return size; } //returns the current size
public String getColor(){ //accessor method to get the color stored in color field
return color; } //returns the current color
public double getPrice(){ //accessor method to get the price stored in price field
return price; } } //returns the current price
Explanation:
Here is the sub class CustomTee:
public class CustomTee extends TeeShirt { //class CustomTee that inherits from class TeeShirt
private String slogan; //private member variable of type String of class CustomTee to store slogan
public void setSlogan(String slgn) { //mutator method to set the slogan
slogan = slgn; }
public String getSlogan() { //accessor method to get the slogan stored in slogan field
return slogan;} } //returns the current slogan
Here is DemoTees.java
import java.util.*;
public class DemoTees{ //class name
public static void main(String[] args) { //start of main method
TeeShirt tee1 = new TeeShirt(); //creates object of class TeeShirt named tee1
TeeShirt tee2 = new TeeShirt(); //creates object of class TeeShirt named tee2
CustomTee tee3 = new CustomTee(); //creates object of class CustomTee named tee3
CustomTee tee4 = new CustomTee(); //creates object of class CustomTee named tee4
tee1.setOrderNumber(100); //calls setOrderNumber method of class TeeShirt using object tee1 to set orderNumber to 100
tee1.setSize("XXL"); //calls setSize method of class TeeShirt using object tee1 to set size to XXL
tee1.setColor("blue"); //calls setColor method of class TeeShirt using object tee1 to set color to blue
tee2.setOrderNumber(101); //calls setOrderNumber method of class TeeShirt using object tee2 to set orderNumber to 101
tee2.setSize("S"); //calls setSize method of class TeeShirt using object tee2 to set size to S
tee2.setColor("gray"); //calls setColor method of class TeeShirt using object tee2 to set color to gray
tee3.setOrderNumber(102); //calls setOrderNumber method of class TeeShirt using object tee3 of class CustomTee to set orderNumber to 102
tee3.setSize("L"); //calls setSize method of class TeeShirt using object tee3 to set size to L
tee3.setColor("red"); //calls setColor method of class TeeShirt using object tee3 to set color to red
tee3.setSlogan("Born to have fun"); //calls setSlogan method of class CustomTee using tee3 object to set the slogan to Born to have fun
tee4.setOrderNumber(104); //calls setOrderNumber method of class TeeShirt using object tee4 of class CustomTee to set orderNumber to 104
tee4.setSize("XXXL"); //calls setSize method to set size to XXXL
tee4.setColor("black"); //calls setColor method to set color to black
tee4.setSlogan("Wilson for Mayor"); //calls setSlogan method to set the slogan to Wilson for Mayor
display(tee1); //calls this method passing object tee1
display(tee2); //calls this method passing object tee2
displayCustomData(tee3); //calls this method passing object tee3
displayCustomData(tee4); } //calls this method passing object tee4
public static void display(TeeShirt tee) { //method display that takes object of TeeShirt as parameter
System.out.println("Order #" + tee.getOrderNumber()); //displays the value of orderNumber by calling getOrderNumber method using object tee
System.out.println(" Description: " + tee.getSize() + " " + tee.getColor()); //displays the values of size and color by calling methods getSize and getColor using object tee
System.out.println(" Price: $" + tee.getPrice()); } //displays the value of price by calling getPrice method using object tee
public static void displayCustomData(CustomTee tee) { //method displayCustomData that takes object of CustomTee as parameter
display(tee); //displays the orderNumber size color and price by calling display method and passing object tee to it
System.out.println(" Slogan: " + tee.getSlogan()); } } //displays the value of slogan by calling getSlogan method using object tee
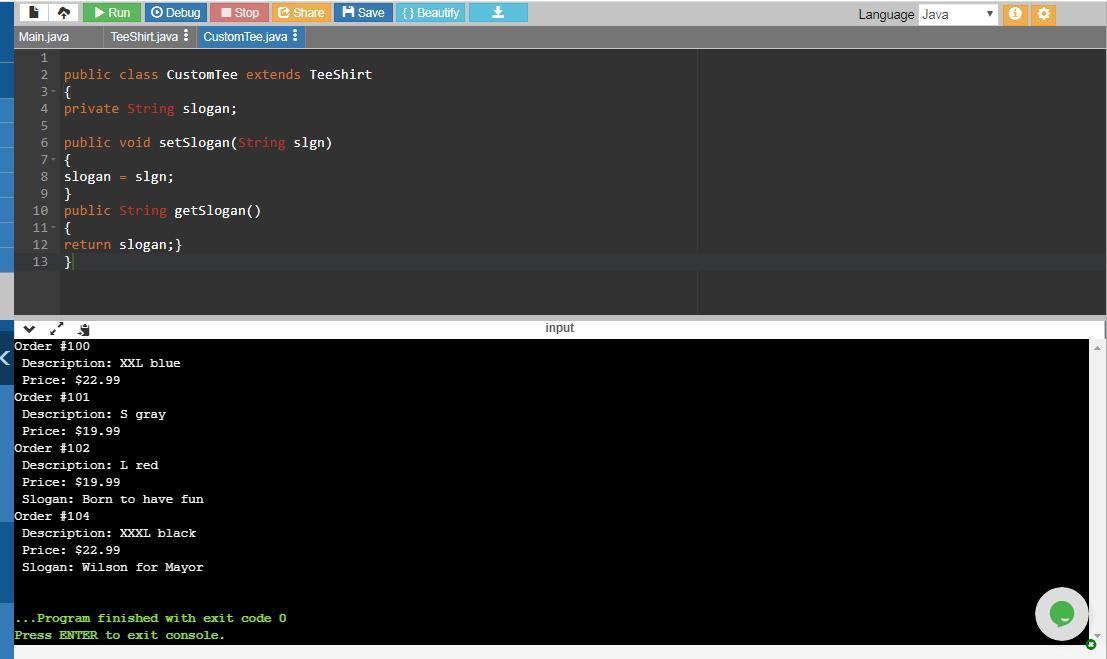
In this exercise we have to use the knowledge in computational language in JAVA to write the following code:
We have the code can be found in the attached image.
So in an easier way we have that the code is
public class TeeShirt{
private int orderNumber;
private String size;
private String color;
private double price;
public void setOrderNumber(int num){
orderNumber = num; }
public void setColor(String color){
this.color = color; }
public void setSize(String sz){
size = sz;
if(size.equals("XXXL") || size.equals("XXL")){
price = 22.99;
}else{
price = 19.99; } }
public int getOrderNumber(){
return orderNumber; }
public String getSize(){
return size; }
public String getColor(){
return color; }
public double getPrice(){
return price; } }
public class CustomTee extends TeeShirt {
private String slogan;
public void setSlogan(String slgn) {
slogan = slgn; }
public String getSlogan() {
return slogan;} }
import java.util.*;
public class DemoTees{
public static void main(String[] args) {
TeeShirt tee1 = new TeeShirt();
TeeShirt tee2 = new TeeShirt();
CustomTee tee3 = new CustomTee();
CustomTee tee4 = new CustomTee();
tee1.setOrderNumber(100);
tee1.setSize("XXL");
tee1.setColor("blue");
tee2.setOrderNumber(101);
tee2.setSize("S");
tee2.setColor("gray");
tee3.setOrderNumber(102);
tee3.setSize("L");
tee3.setColor("red");
tee3.setSlogan("Born to have fun");
tee4.setOrderNumber(104);
tee4.setSize("XXXL");
tee4.setColor("black");
tee4.setSlogan("Wilson for Mayor");
display(tee1);
display(tee2);
displayCustomData(tee3);
displayCustomData(tee4); }
public static void display(TeeShirt tee) {
System.out.println("Order #" + tee.getOrderNumber());
System.out.println(" Description: " + tee.getSize() + " " + tee.getColor());
System.out.println(" Price: $" + tee.getPrice()); }
public static void displayCustomData(CustomTee tee) {
display(tee);
System.out.println(" Slogan: " + tee.getSlogan()); } }
See more about JAVA at brainly.com/question/18502436
4. Interaction between seller and buyer is called___.
A. Demanding
B. Marketing
C. Transactions
D. Oppurtunity
Answers
Answer:
C. Transactions.
Explanation:
A transaction can be defined as a business process which typically involves the interchange of goods, financial assets, services and money between a seller and a buyer.
This ultimately implies that, any interaction between a seller and a buyer is called transactions.
For example, when a buyer (consumer) pays $5000 to purchase a brand new automobile from XYZ automobile and retail stores, this is referred to as a transaction.
Hence, a transaction is considered to have happened when it's measurable in terms of an amount of money (price) set by the seller.
Price can be defined as the amount of money that is required to be paid by a buyer (customer) to a seller (producer) in order to acquire goods and services. Thus, it refers to the amount of money a customer or consumer buying goods and services are willing to pay for the goods and services being offered. Also, the price of goods and services are primarily being set by the seller or service provider.
How does computer hardware and software work together?
Answers
Answer:
Computer software controls computer hardware which in order for a computer to effectively manipulate data and produce useful output I think.
Explanation:
find four
reasons
Why must shutdown the system following the normal sequence
Answers
If you have a problem with a server and you want to bring the system down so that you could then reseat the card before restarting it, you can use this command, it will shut down the system in an orderly manner.
"init 0" command completely shuts down the system in an order manner
init is the first process to start when a computer boots up and keep running until the system ends. It is the root of all other processes.
İnit command is used in different runlevels, which extend from 0 through 6. "init 0" is used to halt the system, basically init 0
shuts down the system before safely turning power off.
stops system services and daemons.
terminates all running processes.
Unmounts all file systems.
Learn more about server on:
https://brainly.com/question/29888289
#SPJ1
Timothy is an architect. He needs to create a prototype of a new apartment that his firm is building. Which multimedia software would he use? A. image editing program B. painting program C. animation program D. digital video program E. 3D modeling program
Answers
____________________ solves the design problem of basic subnetting by allowing different masks on the subnets.
Answers
Answer:
Variable Length Subnet Mask (VLSM)
Explanation:
VLSM is a subnet design strategy that allows all subnet masks to have variable sizes. VLSM solves the design problem of basic subnetting by allowing different masks on the subnets.
I hope this helps!
How SPARQL 1.1 has advantage over SPARQL 1.0??
Answers
Which of the following statements are true about how technology has changed work? Select 3 options. Responses Businesses can be more profitable by using communication technology to reduce the costs of travel. Businesses can be more profitable by using communication technology to reduce the costs of travel. With the spread of technology and the Internet, smaller businesses are not able to compete as effectively as before. With the spread of technology and the Internet, smaller businesses are not able to compete as effectively as before. In a gig economy, workers are only hired when they are needed for as long as they are needed. In a gig economy, workers are only hired when they are needed for as long as they are needed. Through the use of the Internet and collaboration tools more workers are able to perform their jobs remotely. Through the use of the Internet and collaboration tools more workers are able to perform their jobs remotely. Technology has not really changed how businesses operate in the last fifty years. Technology has not really changed how businesses operate in the last fifty years.
Answers
The three genuine statements almost how technology has changed work are:
Businesses can be more productive by utilizing communication technology to decrease the costs of travel. This can be genuine since advances like video conferencing and virtual gatherings permit businesses to conduct gatherings, transactions, and collaborations remotely, lessening the require for costly travel courses of action.With the spread of technology and the Web, littler businesses are not able to compete as successfully as some time recently. This explanation is genuine since innovation has empowered bigger companies to use their assets and reach a worldwide advertise more effortlessly, making it challenging for littler businesses to compete on the same scale.Through the utilize of the Web and collaboration devices, more laborers are able to perform their occupations remotely. This explanation is genuine as innovation has encouraged farther work courses of action, allowing employees to work from anyplace with an online association. Collaboration instruments like extend administration computer program and communication stages have made inaccessible work more doable and effective.Technology explained.
Technology alludes to the application of logical information, aptitudes, and devices to form innovations, fathom issues, and move forward proficiency in different spaces of human movement. It includes the improvement, usage, and utilize of gadgets, frameworks, and processes that are outlined to achieve particular assignments or fulfill specific needs.
Technology can be broadly categorized into distinctive sorts, such as data technology, communication technology, therapeutic innovation, mechanical technology, and transportation technology, among others. These categories include different areas, counting computer science, hardware, broadcast communications, building, and biotechnology.
Learn more about technology below.
https://brainly.com/question/13044551
#SPJ1
Why is it good for companies like Google to test for possible collisions and related cyber attacks?
Answers
Answer:
Technology companies, like Google, constantly need to carry out tests and evaluations of their products that allow them to corroborate the security of their products, to avoid possible collisions or hacker attacks. This is so because when dealing with computer products, which in many cases store enormous amounts of information from their clients or users, they must guarantee their security to generate the trust of their clients, which in the end will end up being what maximizes their sales and earnings.
In other words, they must guarantee the safety of the user when using their products, which is precisely the reason why the customer purchases the company's product.
Good companies like IT companies that need to carry out the tests to verify their integrity and authenticity. This allows them to collaborate and secure their user and provide possible solutions to their problems.
Encryption is one of the easiest and simplest methods of data protection from the collision of cyber attacks. These can be avoided if cyber security is enhanced by the use of tools and techniques so that threats don't collide.Learn more about the companies like to test for possible.
brainly.com/question/13967762.
Describe how data is transmitted using half-duplex serial data transmission.
Answers
Answer:
In half duplex mode, the signal is sent in both directions, but one at a time. In full duplex mode, the signal is sent in both directions at the same time. In simplex mode, only one device can transmit the signal. In half duplex mode, both devices can transmit the signal, but one at a time.
A client sends a 128-byte request to a server located 100 km away over a 1 GB optical fiber. What is the efficiency of the line during the remote procedure call? ANS: Sending 128x8=1024 bits over a 1 Gbps line takes ~
Answers
The efficiency of the line during the remote procedure call is the is 1 microsec.
What is efficiency about?Efficiency deals with the ability for one to be able to avoid wasting time or materials resources to get a result.
Note that :
In sending Sending 128 x 8= 1024 bits over a 1 Gbps
Note therefore that will take the line about ~1 microsec.
Learn more about efficiency from
https://brainly.com/question/25350730
#SPJ1
You would like the user of a program to enter a customer’s last name. Write a statement thaUse the variables k, d, and s so that they can read three different values from standard input--an integer, a float, and a string respectively. On one line, print these variables in reverse order with exactly one space in between each. On a second line, print them in the original order with one space in between them.t asks user "Last Name:" and assigns input to a string variable called last_name.
Answers
Answer:
1st question:
Use the variables k, d, and s so that they can read three different values from standard input an integer, a float, and a string respectively. On one line, print these variables in reverse order with exactly one space in between each. On a second line, print them in the original order with one space in between them.
Solution:
In Python:
k = input() #prompts user to input value of k i.e. integer value
d = input() #prompts user to input value of d i.e. float value
s = input() #prompts user to input value of s i.e. a string
print (s, d, k) #displays these variable values in reverse order
print (k, d, s)#displays these variable values in original order
In C++:
#include <iostream> // to use input output functions
using namespace std; //to identify objects like cin cout
int main() { //start of main function
int k; //declare int type variable to store an integer value
float d; // declare float type variable to store a float value
string s; // declare string type variable to store an integer value
cin >> k >> d >> s; //reads the value of k, d and s
cout << s << " " << d << " " << k << endl; //displays these variables values in reverse order
cout << k << " " << d << " " << s << endl; } // displays these variable values in original order
Explanation:
2nd question:
You would like the user of a program to enter a customer’s last name. Write a statement that asks user "Last Name:" and assigns input to a string variable called last_name.
Solution:
In Python:
last_name = input("Last Name:")
# input function is used to accept input from user and assign the input value to last_name variable
In C++:
string last_name; //declares a string type variable named last_name
cout<<"Last Name: "; // prompts user to enter last name by displaying this message Last Name:
cin>>last_name; // reads and assigns the input value to string variable last_name
The programs alongwith their outputs are attached.


The statement that Use the variables k, d, and s so that they can read three different values from standard input--an integer, a float, and a string respectively and print these variables in reverse order with exactly one space in between each and on a second line, print them in the original order with one space in between them can be represented as follows:
k = int(input("write an integer input: "))
d = float(input("write a float input: "))
s = str(input("write a string input: "))
print(s, d, k)
print(k, d, s)
The code is written in python.
A variable k is declared that prompt the user to input an integer.
A variable d is declared that prompt the user to input a float.
A variable s is declared that prompt the user to input a string.
The variable are printed in reverse order.
The the variables are printed accordingly in the original order.
Note the bolded part of the code are python keywords.
read more: https://brainly.com/question/20709863?referrer=searchResults

write the steps to insert picture water mark
Answers
Answer:
Is there a picture of the question?
Explanation:
HELP im soooo confused

Answers
Choose all items that represent common website
design flaws.
menu at the top of the page
distracting background
short page-load times
too many or confusing fonts
poor navigation
dead hyperlinks
Answers
Answer:
2,4,5,6
Explanation:
just answered it
**GIVING ALL POINTS** 4.02 Coding With Loops
I NEED THIS TO BE DONE FOR ME AS I DONT UNDERSTAND HOW TO DO IT. THANK YOU
Output: Your goal
You will complete a program that asks a user to guess a number.
Part 1: Review the Code
Review the code and locate the comments with missing lines (# Fill in missing code). Copy and paste the code into the Python IDLE. Use the IDLE to fill in the missing lines of code.
On the surface this program seems simple. Allow the player to keep guessing until he/she finds the secret number. But stop and think for a moment. You need a loop to keep running until the player gets the right answer.
Some things to think about as you write your loop:
The loop will only run if the comparison is true.
(e.g., 1 < 0 would not run as it is false but 5 != 10 would run as it is true)
What variables will you need to compare?
What comparison operator will you need to use?
# Heading (name, date, and short description) feel free to use multiple lines
def main():
# Initialize variables
numGuesses = 0
userGuess = -1
secretNum = 5
name = input("Hello! What is your name?")
# Fill in the missing LOOP here.
# This loop will need run until the player has guessed the secret number.
userGuess = int(input("Guess a number between 1 and 20: "))
numGuesses = numGuesses + 1
if (userGuess < secretNum):
print("You guessed " + str(userGuess) + ". Too low.")
if (userGuess > secretNum):
print("You guessed " + str(userGuess) + ". Too high.")
# Fill in missing PRINT statement here.
# Print a single message telling the player:
# That he/she guessed the secret number
# What the secret number was
# How many guesses it took
main()
Part 2: Test Your Code
Use the Python IDLE to test the program.
Using comments, type a heading that includes your name, today’s date, and a short description.
Run your program to ensure it is working properly. Fix any errors you observe.
Example of expected output: The output below is an example of the output from the Guess the Number game. Your specific results will vary based on the input you enter.
Output
Your guessed 10. Too high.
Your guessed 1. Too low.
Your guessed 3. Too low.
Good job, Jax! You guessed my number (5) in 3 tries!
When you've completed filling in your program code, save your work by selecting 'Save' in the Python IDLE.
When you submit your assignment, you will attach this Python file separately.
Part 3: Post Mortem Review (PMR)
Using complete sentences, respond to all the questions in the PMR chart.
Review Question Response
What was the purpose of your program?
How could your program be useful in the real world?
What is a problem you ran into, and how did you fix it?
Describe one thing you would do differently the next time you write a program.
Answers
Answer:
import random
from time import sleep as sleep
def main():
# Initialize random seed
random.seed()
# How many guesses the user has currently used
guesses = 0
# Declare minimum value to generate
minNumber = 1
# Declare maximum value to generate
maxNumber = 20
# Declare wait time variable
EventWaitTime = 10 # (Seconds)
# Incorrect config check
if (minNumber > maxNumber or maxNumber < minNumber):
print("Incorrect config values! minNumber is greater than maxNumber or maxNumber is smaller than minNumber!\nDEBUG INFO:\nminNumber = " + str(minNumber) + "\nmaxNumber = " + str(maxNumber) + "\nExiting in " + str(EventWaitTime) + " seconds...")
sleep(EventWaitTime)
exit(0)
# Generate Random Number
secretNumber = random.randint(minNumber, maxNumber)
# Declare user guess variable
userGuess = None
# Ask for name and get input
name = str(input("Hello! What is your name?\n"))
# Run this repeatedly until we want to stop (break)
while (True):
# Prompt user for input then ensure they put in an integer or something that can be interpreted as an integer
try:
userGuess = int(input("Guess a number between " + str(minNumber) + " and " + str(maxNumber) + ": "))
except ValueError:
print("ERROR: You didn't input a number! Please input a number!")
continue
# Increment guesses by 1
guesses += 1
# Check if number is lower, equal too, or higher
if (userGuess < secretNumber):
print("You guessed: " + str(userGuess) + ". Too low.\n")
continue
elif (userGuess == secretNumber):
break
elif (userGuess > secretNumber):
print("You guessed: " + str(userGuess) + ". Too high.\n")
continue
# This only runs when we use the 'break' statement to get out of the infinite true loop. So, print congrats, wait 5 seconds, exit.
print("Congratulations, " + name + "! You beat the game!\nThe number was: " + str(secretNumber) + ".\nYou beat the game in " + str(guesses) + " guesses!\n\nThink you can do better? Re-open the program!\n(Auto-exiting in 5 seconds)")
sleep(EventWaitTime)
exit(0)
if __name__ == '__main__':
main()
Explanation:
Answer:
numGuesses = 0
userGuess = -1
secretNum = 4
name = input("Hello! What is your name?")
while userGuess != secretNum:
userGuess = int(input("Guess a number between 1 and 20: "))
numGuesses = numGuesses + 1
if (userGuess < secretNum):
print(name + " guessed " + str(userGuess) + ". Too low.")
if (userGuess > secretNum):
print( name + " guessed " + str(userGuess) + ". Too high.")
if(userGuess == secretNum):
print("You guessed " + str(secretNum)+ ". Correct! "+"It took you " + str(numGuesses)+ " guesses. " + str(secretNum) + " was the right answer.")
Explanation:
Review Question Response
What was the purpose of your program? The purpose of my program is to make a guessing game.
How could your program be useful in the real world? This can be useful in the real world for entertainment.
What is a problem you ran into, and how did you fix it? At first, I could not get the input to work. After this happened though, I switched to str, and it worked perfectly.
Describe one thing you would do differently the next time you write a program. I want to take it to the next level, like making froggy, tic tac toe, or connect 4
Which octet of the subnet mask 255.255.255.0 will tell the router the corresponding host ID?
Answers
Answer: The last octet
Explanation: The last octet of the subnet mask will tell the router the corresponding host ID.
The last octet is the octet of the subnet mask 255.255.255.0 will tell the router the corresponding host ID.
What is octet in IP address?An octet is a decimal value between 0 and 255, and it is referred to as x in the IPv4 component of the address. The octets are separated by periods. The IPv4 portion of the address must contain three periods and four octets.
People may have also heard people refer to the four digits that make up an IP address as "octets." An octet is the correct term to describe the four different digits that make up an IP address.
In subnetting, the third octet is used to identify particular subnets of network 150.150.0.0. Each subnet number in the example in the image has a different value in the third byte, indicating that it is a distinct subnet number.
Thus, it is last octet.
For more details about octet in IP address, click here:
https://brainly.com/question/10115477
#SPJ2
A company wants to transmit data over the telephone, but they are concerned that their phones may be tapped. All of their data is transmitted as four-digits. They have asked you to write a program that will encrypt their data so that it may be transmitted more securely. Your program should read a four-digit integer and encrypt it as follows: 1. Replace each digit by (the sum of that digit and 3) modulus 10. Then 2. Swap the first digit with the third, and swap the second digit with the fourth. 3. Print the encrypted integer.
Answers
Answer:
def encrypt_digit(digit):
if type(digit) is int or float:
digit = str(digit)
hold = list()
for x in digit:
d = str((int(x) + 3)%10)
hold.append(d)
first = hold.pop(0)
second = hold.pop(0)
third = hold.pop(0)
fourth = hold.pop()
print(int("".join([third,fourth, first, second])))
encrypt_digit(7836)
Explanation:
The python function accepts a four-digit parameter which represents the data transmitted over the company's telephone network. The function encrypts the data by adding 3 to each digit and getting the modulus of division 10, then the digits are swapped and printed out encrypted and ready for transmission.
Encryption are used to protect data and files when they are is being transmitted
The encryption program written in Python, where comments are used to explain each line is as follows:
#This gets input for the number
num = int(input())
#This converts the number to string
digit = str(num)
#This creates a list
myList = list()
#This encrypts the number, and add the numbers to a list
for i in digit:
d = str((int(i) + 3)%10)
myList.append(d)
#This prints the result of the encryption
print(int("".join([myList[2],myList[3], myList[0], myList[1]])))
Read more about encryption at:
https://brainly.com/question/14298787