What is the top buying criteria for the high tech market segment?.
Answers
The high tech market is a highly dynamic and competitive sector, and so it is crucial for marketers to understand their customers’ buying criteria.
When it comes to this market segment, the top buying criteria are technological superiority, quality, innovation, and performance. Technological superiority means that the product must have the most advanced and up-to-date technology, to ensure it is compatible with other high-tech devices and meets the customer’s expectations. Quality is the key determinant of the product's value in terms of durability, reliability, and safety.
Innovation is a crucial factor in attracting customers, especially early adopters who are always looking for the latest technology to gain a competitive edge. Performance measures the product's ability to function effectively and efficiently. It is necessary to prove the product's performance with data and other performance indicators.
To know more about sector visit:
https://brainly.com/question/32234164
#SPJ11
Related Questions
Usually a WAN covers no more than one building.
Group of answer choices
True
False
Answers
Answer:
False
Explanation:
WAN's are a wide area covered in LAN's. LAN's only cover 1 building, while WAN's are a bunch of LAN's in a WIDE area (WAN = wide area network)
i hope this helps you :D
WAN and LAN, you can find a definition on Gooogle. And then, you can get the correct the answer.
Choose the word that correctly completes the sentence. I noticed I was consistent in my verb tense ______I didn't revise the proposal for clarity.
Answers
The correct word that fills the blank is although.
Explanation:
The sentence expresses that the speaker noticed they were consistent in their verb tense, but they did not revise the proposal for clarity. The word that correctly completes the sentence should indicate that the two ideas are contrasting or opposing.
The word "although" accomplishes this because it contrasts two ideas. In this case, it introduces the second clause which contradicts or contrasts with the idea expressed in the first clause.
Therefore, the correct word to complete the sentence is "although."
To get a similar answer on verb tense:
https://brainly.com/question/26055242
#SPJ11
The task where verified data is coded or converted into machine
Answers
Input-this step is defined as the task of coding and converting the verify data into the machine breedable form so that it can be processed through software or an application.
How does lower latency benefit the users connected to a network?
Answers
Users connected to a network benefit from lower latency "by reducing the delay when sending and receiving data between devices". The correct answer is C.
Lower latency refers to the amount of time it takes for data to be sent and received between devices on a network. When latency is low, the delay between when a user sends a request and when they receive a response is minimized, resulting in a more responsive and smoother experience for the user. This is particularly important in applications such as online gaming, video conferencing, and real-time control systems, where fast response times are critical. A low-latency network allows for faster data transfer, which results in a better user experience.
This question should be provided with answer choices, which are:
(A) by expanding the range over which the network's signals are transmitted.(B) by enabling more devices to connect to the network at the same time.(C) by reducing the delay when sending and receiving data between devices.(E) by limiting network access to users with higher security credentials.The correct answer is C.
Learn more about high latency here: brainly.com/question/30185656
#SPJ4
due to advances in high speed communication networks, the information lag, or the time it takes for information to be disseminated around the world, has been significantly shortened.
Answers
True, due to advances in high speed communication networks, the information lag, or the time it takes for information to be disseminated around the world, has been significantly shortened.
The information lag, or the time it takes for information to be disseminated around the world, has been significantly shortened due to advances in high speed communication networks. This has had a number of important implications for businesses and individuals alike.
For businesses, the shorter information lag means that they can react more quickly to changes in the market. They can also take advantage of opportunities more quickly. For individuals, the shorter information lag means that they can stay up-to-date with what is happening in the world more easily.
The shorter information lag is also having an impact on the way we live and work. We are now more connected to the rest of the world than ever before. This is making it easier for us to find information and to communicate with people from all over the globe.
Learn more on high speed communication networks here:
https://brainly.com/question/13216536
#SPJ4
What are the characteristics journalism shares with the professions? can you elucidate one characteristic and give an example to clarify your answer
Answers
One characteristic that journalism shares with many professions is a commitment to ethical conduct. This includes upholding principles such as objectivity, accuracy, impartiality, and accountability.
For example, journalists are expected to avoid conflicts of interest that may compromise their work and to correct any errors or inaccuracies in their reporting promptly. They are also often required to maintain confidentiality when necessary and to protect sensitive information that may be harmful to individuals or society. By adhering to these ethical standards, journalists help to maintain the credibility of their profession and ensure that the public trust in the media is upheld.
Learn more about journalism: https://brainly.com/question/13105719
#SPJ4
A wireless laptop at an organization is not able to access any internal network resources, but can browse the Internet. An IT support specialist finds the cause of the problem after examining the laptop. Based on the functionality, what does the specialist most likely conclude the cause to be
Answers
The IT support specialist is likely to conclude that the cause of the problem is due to a misconfigured or malfunctioning firewall.
A firewall is a network security device that monitors and filters incoming and outgoing network traffic based on an organization's previously established security policies. It is possible that the firewall settings have been configured to allow the laptop to connect to the Internet but not to the internal network resources.
This could be due to an oversight during the configuration process or a deliberate security measure to prevent unauthorized access to sensitive information. The specialist may need to adjust the firewall settings to allow the laptop to access the internal network resources or investigate further to determine if there are any other issues at play.
Learn more about specialist here:
https://brainly.com/question/28233540
#SPJ11
How is video compression accomplished?
Video compression works by making the pixel size smaller.
Video compression works by removing the sound.
Video compression works by smoothing the pixels.
Video compression works by removing unnecessary parts of frames
Answers
Answer:
A. Video compression works by making the pixel size smaller.
Explanation:
E2020!
A ___ error means the web page you are trying to view isn't available, perhaps because the page has been deleted from the server.
601
404
500
Answers
Answer:
A 404
Explanation:
I've seen it many times.
Answer:
404
Explanation:
Dan needs to print sheet1, sheet6, and sheet9 of a large workbook. What is the most efficient way to accomplish his task?
Answers
By selecting multiple sheets and printing them together, Dan can save time and avoid the need to print each sheet separately.
The most efficient way for Dan to print sheet1, sheet6, and sheet9 of a large workbook would be to follow these steps:
Open the workbook in Microsoft Excel or another spreadsheet program.Hold down the Ctrl key and click on the tab for sheet1, sheet6, and sheet9 to select them all.Right-click on one of the selected tabs and choose "Print" from the context menu.In the Print dialog box, choose the desired printer and select the page range for each sheet (e.g., "1-1" for sheet1, "6-6" for sheet6, and "9-9" for sheet9).Click "Print" to print the selected sheets.This method also ensures that the selected sheets are printed in the correct order and with the correct settings.
To learn more about Microsoft Excel visit;
https://brainly.com/question/24202382
#SPJ4
Which statement describes what happens when a user configures No Automatic Filtering in Junk Mail Options?
No messages will ever be blocked from the user’s mailbox.
Messages can still be blocked at the server level.
Messages cannot be blocked at the network firewall.
Most obvious spam messages will still reach the client computer.
Answers
Answer:
The last one
Explanation I think it is D because all of the other answers are saying what happen if you filter it.
The majority of obvious spam messages will continue to reach the client's computer. The correct answer is D.
What is junk mail?Email spam, also known as junk email, spam mail, or plainly spam, is an unrequested email sent in mass. The name is derived from a Monty Programming languages sketch that includes the name of a canned pork product is mentioned. Spam is pervasive, unavoidable, and monotonous.
Back out of the Folder or any message folders users are viewing to access the Mailboxes view. The Junk folder is located beneath the Drafts and Sent directories in the Mailboxes view.
The Junk Email Filter settings can be changed in the Junk E-mail Dialogue box. Click Junk in the Deactivate group on the Home tab, and then click Garbage E-mail Options.
Most obvious spam messages will still reach the client's computer. Then the correct option is D.
More about the junk mail link is given below.
https://brainly.com/question/28354330
#SPJ6
Write a program that displays the results of: 4 x ( 1.0 - 1.0 / 3.0 1.0 / 5.0 - 1.0 / 7.0 1.0 / 9.0 - 1.0 / 11.0 1.0 / 13.0 ) And 4 x ( 1 - 1 / 3 1 / 5 - 1 / 7 1 / 9 - 1 / 11 1 / 13 ) In your comments, add a discussion on the difference between the two outputs and the cause. Which is best
Answers
The output of the first calculation is 3.1415926535900345, while the output of the second calculation is 2.9760461760461765. The first output is more accurate and is the best one to use if precision is important.
Here's the program in Java that displays the results of 4 x (1.0 - 1.0 / 3.0 + 1.0 / 5.0 - 1.0 / 7.0 + 1.0 / 9.0 - 1.0 / 11.0 + 1.0 / 13.0) and 4 x (1 - 1 / 3 + 1 / 5 - 1 / 7 + 1 / 9 - 1 / 11 + 1 / 13).class Main{public static void main(String[] args){double sum1 = 4.0 * (1.0 - 1.0 / 3.0 + 1.0 / 5.0 - 1.0 / 7.0 + 1.0 / 9.0 - 1.0 / 11.0 + 1.0 / 13.0);double sum2 = 4.0 * (1 - 1 / 3 + 1 / 5 - 1 / 7 + 1 / 9 - 1 / 11 + 1 / 13);
System.out.println("Result 1: " + sum1);System.out.println("Result 2: " + sum2);}}The output of the first calculation is 3.1415926535900345, while the output of the second calculation is 2.9760461760461765.
The difference between the two outputs is due to the fact that the first calculation uses double values for the fractional parts of the division, while the second calculation uses integer values.When dividing integers, Java truncates the decimal part, so the result is always an integer.
In the second calculation, the decimal values are being truncated, leading to a less accurate result. Therefore, the first output is more accurate and is the best one to use if precision is important.
Learn more about integers here,
https://brainly.com/question/929808
#SPJ11
the courts can adjust the penalties in lawsuits to reflect the fact that infringements may be _____.
Answers
The courts are authorized to adjust the penalties in lawsuits in order to reflect the fact that infringements may be willful.
What is a court?A court can be defined as an enclosed space such as a hall or chamber, where legal practitioners (judges, lawyers or attorneys and a jury) converge to hold judicial proceedings, especially by listening to evidences and giving a verdict about legal cases.
In the Judicial system, the courts are authorized to adjust the penalties in lawsuits in order to reflect the fact that infringements may be willful.
Read more on Courts here: https://brainly.com/question/1991159
#SPJ1
The courts can adjust the penalties in lawsuits to reflect the fact that infringements may be wilful.
What are the consequences of infringement?In general, everybody discovered responsible of civil copyright infringement can be ordered to pay both real damages or “statutory” damages affixed at now no longer much less than $750 and now no longer extra than $30,000 in line with paintings infringed. For “willful” infringement, a courtroom docket can also additionally award up to $150,000 in line with paintings infringed.
Infringement or lively inducement of infringement is willful whilst it's miles accomplished intentionally and intentionally, and with know-how of the patent. Copying of an invention, if such copying keeps after the lifestyle of the patent is made known, is proof of willfulness.
Read more about the infringements :
https://brainly.com/question/1078532
#SPJ1
what does you are not allowed to make dialed carrier calls mean
Answers
It's time to upgrade your SIM if you are unable to make called carrier calls. Due to an outdated SIM, your carrier can be preventing you from placing calls.
Why does my phone continually indicating that I can't dial a carrier number?It indicates that voice conversations via LTE or HD Voice are not supported by your phone. Perhaps you use an outdated SIM card, a dated handset, or a non-compatible unlocked handset.
If it states that my call cannot be completed as dialed, am I blocked?If you phone someone and get an automated response saying anything to the effect of "the customer is unavailable," their wireless provider might have blocked you. Although the messaging may differ, the end consequence is the same. Your call won't be answered.
To know more about carrier calls visit:-
https://brainly.com/question/30474210
#SPJ1
When a call is placed, caller ID typically shows a name or number. This information will also be recorded in the call history on your phone.
What is the dialed carrier calls mean?That means that your phone does not allow voice calls over LTE or HD Voice. You might be using an old SIM card, an out-of-date phone, or an unlocked phone that is incompatible.
It's possible that their cellphone provider has barred you if you call someone and get an automated message that says something to the effect of “the customer is unavailable.” The outcome is the same, regardless of the messaging. You call, but no one answers.
Therefore, If you can't make carrier calls, it's time to upgrade your SIM. Your carrier can be stopping you from making calls because your SIM is out of date.
Learn more about call here:
https://brainly.com/question/30474210
#SPJ1
which technology enables the company to aggregate the user's browsing history across multiple sites? choose 1 answer: choose 1 answer:
Answers
The in response to the question "which technology enables the company to aggregate the user's browsing history across multiple sites?" the answer is as follows:One technology that enables companies to aggregate user browsing history across multiple sites is cookies.
Cookies are small text files that are stored on a user's device when they visit a website. They contain information about the user's browsing activity on that website, such as login information, user preferences, and other data that can be used to track the user's behavior.Cookies can also be used to track a user's activity across multiple websites, allowing companies to create a profile of the user's interests and behaviors. This information can be used to deliver personalized ads and content to the user or to sell to third-party advertisers.Cookies can be first-party, meaning they are set by the website the user is visiting, or third-party, meaning they are set by a different website that the user has visited. Third-party cookies are often used by advertising networks to track user behavior across multiple websites and deliver targeted ads to the user. However, many web browsers now block third-party cookies by default in an effort to protect user privacy.In conclusion, cookies are a technology that enables companies to aggregate user browsing history across multiple sites. However, their use is becoming increasingly restricted due to concerns about user privacy.For such more question on technology
https://brainly.com/question/7788080
#SPJ11
what is the main function of the output on a computer or what is it use for?
Answers
Answer:
It is used to transfer data
Explanation:
An output used on a computer is used for transferring your data from your device to another by any user
What’s ur guys rank of all 3D Mario games (all of these are great games btw)? These are my opinions I’d rly enjoy hearing yours. I’d say mine is
8. Super Mario 64
(sorry guys just all the bottomless pits were an issue and sometimes I was frustrated like with tryna shoot the cannon getting all those coins in the first level and the little corner parts in front of the pyramid but overall rly important and still fun)
8.5/10
7. Super Mario Sunshine
(it’s like Mario 64 but less frustrating without the bottomless pits and have to start all the way over but still has the issue of having to climb all the way up from high areas but those are the only issues with these two and how they have to )
8.8/10
6. Super Mario 3D Land
(not as mind blowing as 3D World or as big as it but still fun)
9/10
5. Bowsers Fury (actual power ups and it’s one interconnected world with a giant bowser and most of it is platforming challenge after platforming challenge which I like in my 3D Mario games)
9.3
4. Super Mario Odyssey (it’s great and not a lot of bottomless pits but the moons don’t feel super worth because of how many there are sometimes I stumble onto them)
9.5/10
3. Super Mario 3D World (I’ve had it since kindergarten ok? Its basically 3D Land but even better with tons of platforming challenges and even tho the first 6 or 7 worlds are a cakewalk the later parts get harder and harder and it’s super fun with friends)
9.9/10
1 & 2 tie Mario Galaxy 1 & 2 (I’ve had the first since I’ve existed and I recently got the second and I somehow feel so nostalgic towards it even tho I’ve never played it before this year (a lot of games from around 2009-2011 I feel nostolgic for even tho I’ve never played them) these two games are basically perfect with the only bad level being cleaning up trash for that robot but with the gravity mechanics and super fun platforming challenges while also being super original they are going to stand the test of time I’m sure of it)
10/10
Answers
Answer:
super mario galaxy best of all time
Explanation:
Please! I need help matching this.
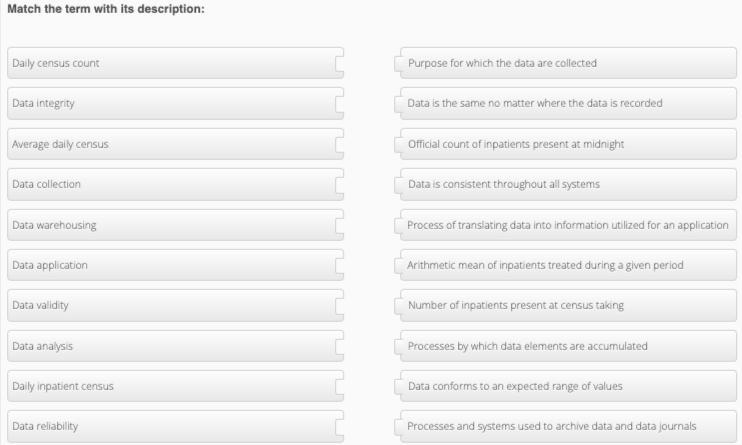
Answers
We can see here that matching the term with its description, we have:
Daily census count: Official count of inpatients present at midnightData integrity: Data conforms to an expected range of valuesAverage daily census: Arithmetic mean of inpatients treated during a given periodData collection: Processes by which data elements are accumulatedData warehousing: Processes and systems used to archive data and data journals.What is data?Data refers to a collection of facts, figures, statistics, measurements, or any other information that can be analyzed or used to gain insights and knowledge about a particular subject or topic. In today's digital age, data can exist in various forms such as text, numbers, images, audio, and video.
Continuation of the matching:
Data application: Process of translating data into information utilized for an applicationData validity: Purpose for which the data are collectedData analysis: Processes by which data elements are accumulatedDaily inpatient census: Number of inpatients present at census takingData reliability: Data is consistent throughout all systems.Learn more about data on https://brainly.com/question/28132995
#SPJ1
Which of the following best describes today’s average gamer?
The average age is eighteen, and many more males play than females.
The average age is thirty, and only slightly more males play than females.
The average age is thirty, and many more males play than females.
The average age is eighteen, and only slightly more males play than females.
Answers
I’ll give Brainly if u answer all please
ASAP

Answers
Answer:
Answers are: 38, 135, 23, 209, 53 & 181 respectively
Explanation:
How to design remote access policy using the appropriate access controls for systems,applications, and data access
Answers
Answer:
All remote access users connect to the network and maintain all security standards on the device including
Valid and virus protection
Malware protection
Maintain the OS
Explanation:
The remote access policy applies to employees and other affiliates who owned devices to remotely access the Network CCC. The remote policy access connection is used to perform the work activities on the behalf of CCC. Remote access system, application and can be accessed with the internal CCC network. Example of application are as follow:
Internal Academic System
Internal websites
Documents files on internal file
Local colleges resources
Servers
Remote access will be managed by System Data Center and use security measures based on requirements.
Remote access is provided as an extension of the normal work environment.
Review the CCC information technology for protecting information via the remote method.
The employee will use remote procedures. Employees disclose the passwords and if the business is conducted from home.
All remote access includes a "time-out" system. In accordance with CCC and will time out the specified period of inactivity.
The access users accept the access and connection to networks and monitored to record dates, time. Identify accounts and have been compromised by external parties.
The remote access user may be listed in the remote access application.
Your supervisor has asked you to configure a new system using existing configurations. He said to use either an ARM template or a blueprint. What would you suggest and why? When do you think it is appropriate to use an ARM template and when is it not?
Answers
If precise control over infrastructure configuration is needed, use an ARM template. If enforcing standards and ensuring consistency is the priority, opt for Azure Blueprints.
When considering whether to use an ARM template or a blueprint for configuring a new system using existing configurations, the choice depends on the specific requirements and circumstances of the project.
Here are some considerations for each option:
ARM Templates:
1. ARM templates are Infrastructure as Code (IaC) templates used to define and deploy Azure infrastructure resources. They provide a declarative approach to provisioning resources.
2. Use ARM templates when you need precise control over the infrastructure configuration, including virtual machines, networking, storage, and other Azure services.
3. ARM templates are beneficial when you require version control, repeatability, and scalability for infrastructure deployments.
4. They allow for automation and rapid provisioning of resources, making it easier to manage and maintain infrastructure deployments.
Blueprints:
1. Azure Blueprints are used to create and manage a collection of Azure resources that can be repeatedly deployed as a package.
2. Use blueprints when you want to enforce compliance, governance, and organizational standards across multiple deployments.
3. Blueprints are suitable for scenarios where you need to ensure consistency and security compliance within a specific environment or for specific types of workloads.
4. They enable centralized management and governance, allowing organizations to maintain control over deployments and ensure compliance with regulations.
The choice between ARM templates and blueprints ultimately depends on the specific needs of the project. If the focus is on infrastructure provisioning and customization, ARM templates provide granular control.
On the other hand, if the emphasis is on governance, compliance, and enforcing standards, blueprints offer a higher level of abstraction and central management.
It is appropriate to use ARM templates when you require flexibility, customization, and fine-grained control over the infrastructure. However, if the primary concern is enforcing standards and ensuring consistency across deployments, blueprints would be a more suitable choice.
In summary, evaluate the project requirements in terms of infrastructure control versus governance needs to determine whether to use an ARM template or a blueprint for configuring the new system using existing configurations.
Learn more about Blueprints:
https://brainly.com/question/4406389
#SPJ11
A copyright is registered, while a trademark is____
Answers
Answer: Approved
Explanation: Copyright is generated automatically upon the creation of original work, whereas a trademark is established through common use of a mark in the course of business.
which argument of the messagebox macro action determines the text in the top portion of the message dialog box?
Answers
The message box macro action's argument determines the text that appears in the message dialog box's top part.
What is dialog box?A dialog box is a frequent sort of window in the GUI of an operating system (sometimes spelled dialogue box and termed a dialog). In addition to providing more details, the dialog box also requests feedback from the user. For instance, you interact with the "File Open" dialog box while you are using a program and want to open a file. A file or group of files can be opened by specifying the drive, directory, and name in the Open dialog box. By initializing an OPEN FILE NAME structure and giving the structure to the Get Open File Name function, an Open dialog box is created and shown.To learn more about dialog box, refer to:
https://brainly.com/question/28655034
#SPJ4
what os the full form of cpu
Answers
Answer:
central processing unit
Central processing unit
Consider the following code segment. Int count = 5; while (count < 100) { count = count * 2; } count = count 1; what will be the value of count as a result of executing the code segment?
Answers
Using the while loop, the value of count as a result of executing the following code segment is 161.
int count = 5;
while (count < 100)
{
count = count * 2; // count value will 10 20 40 80 160 then exit the while loop as count<100
}
count = count + 1; // here, 161 +1
When a condition is not satisfied, a "While" loop is used to repeat a certain piece of code an undetermined number of times. For instance, if we want to ask a user for a number between 1 and 10, but we don't know how often they might enter a greater number, until "while the value is not between 1 and 10."
While the program is running, the statements are continually executed using both the for loop and the while loop. For loops are used when the number of iterations is known, but while loops execute until the program's statement is proven incorrect. This is the main distinction between for loops and while loops.
To learn more about While loop click here:
brainly.com/question/29102592
#SPJ4
Translate these two functions into MIPS Language
int moveRobots(int *arg0, int *arg1, int arg2, int arg3)
{
int i, *ptrX, *ptrY, alive = 1;
ptrX = arg0;
ptrY = arg1;
for (i=0;i<4;i++) {
*ptrX = getNew(*ptrX,arg2); // update x-coordinate of robot i
*ptrY = getNew(*ptrY,arg3); // update y-coordinate of robot i
// check if robot caught user
if ((*ptrX == arg2) && (*ptrY == arg3)) {
alive = 0;
break;
}
ptrX++;
ptrY++;
}
return alive;
}
Answers
The given code is a function in C language that accepts four integer pointers: two integer pointers, two integers, and returns an integer. The function loops through four robot coordinates (x and y) updating them and checks if they have caught the user.
If a robot caught the user, the function returns 0. If no robot caught the user, the function returns 1.The MIPS assembly language code will achieve this same function. Here is the MIPS code:moveRobots:
addi $sp, $sp, -12 # Allocate space for 3 variables on stack
sw $ra, 8($sp) # Save the return address on the stack
sw $s1, 4($sp) # Save the value of s1 register on the stack
sw $s2, 0($sp) # Save the value of s2 register on the stack
add $s1, $a0, $zero # Assign pointer arg0 to $s1 register
add $s2, $a1, $zero # Assign pointer arg1 to $s2 register
addi $t0, $zero, 0 # Initialize alive to 1
lw $t0, ($s0) # Load the value of alive to $t0 register
lw $ra, 8($sp) # Load the return address from the stack to $ra
lw $s1, 4($sp) # Load the value of s1 register from stack to $s1
lw $s2, 0($sp) # Load the value of s2 register from stack to $s2
addi $sp, $sp, 12 # Deallocate the memory on stack
jr $ra # Return from function.
To know more about language visit:
https://brainly.com/question/32089705
#SPJ11
The four main parts of a computer system are the Input, output, processor, and:
O A core.
OB. hardware.
OC. software.
OD. storage.
Answers
Answer:D) Storage
Explanation:
Select the incorrect statement concerning GHB. A. It has a rapid onset. B. It is generally taken orally. C. Instructions for how to make GHB can be found on the Internet. D. It has a very long half-life.
Answers
The incorrect statement concerning GHB (Gamma-Hydroxybutyrate) is D. It has a very long half-life.
GHB is a central nervous system depressant that is commonly abused as a recreational drug. It is known for its sedative and euphoric effects. While the other statements (A, B, and C) are true about GHB, statement D is incorrect. GHB actually has a relatively short half-life, typically ranging from 30 minutes to 1 hour. The half-life refers to the time it takes for half of the substance to be eliminated from the body.
Due to its short half-life, GHB's effects are relatively short-lived, and users may need to take multiple doses to sustain its desired effects. It's important to note that GHB is a dangerous substance with high abuse potential and associated risks, including overdose and addiction. Its use should be strictly monitored and regulated under medical supervision.
Learn more about depressant here: brainly.com/question/28285166
#SPJ11
Assignment 4: Evens and Odds (FIX PLEASE)
Write a program that will ask a user for how many numbers they would like to check. Then, using a for loop, prompt the user for a number, and output if that number is even or odd. Continue doing this as many times as the user indicated. Once the loop ends, output how many even numbers were entered and how many odd numbers were entered.
Hint: For a number to be even, when the number is divided by 2, there should be no remainder - so you will want to use the modulus (%) operator.
Hint: You will need two count variables to keep track of odd and even numbers.
Sample Run 1
How many numbers do you need to check? 5
Enter number: 20
20 is an even number.
Enter number: 33
33 is an odd number.
Enter number: 4
4 is an even number.
Enter number: 77
77 is an odd number.
Enter number: 8
8 is an even number.
You entered 3 even number(s).
You entered 2 odd number(s).
Sample Run 2
How many numbers do you need to check? 3
Enter number: 10
10 is an even number.
Enter number: 3
3 is an odd number.
Enter number: 400
You entered 2 even number(s).
You entered 1 odd number(s).
Benchmarks
Prompt the user to answer the question, “How many numbers do you need to check? “
Create and initialize two count variables - one for odd and one for even.
Based on the previous input, create a for loop that will run that exact number of times.
Prompt the user to “Enter number: “
If that number is even, output “[number] is an even number.”
Update the even count variable.
Or else if the number is odd, output “[number] is an odd number.”
Update the odd count variable.
Output “You entered [number] even number(s).”
Output “You entered [number] odd number(s).”

Answers
n = int(input("How many numbers do you need to check? "))
odd = 0
even = 0
for x in range(n):
num = int(input("Enter number: "))
if num % 2 == 0:
even += 1
print(str(num)+" is an even number")
else:
odd += 1
print(str(num)+" is an odd number")
print("You entered "+str(even)+" even number(s).")
print("You entered "+str(odd)+" odd number(s).")
This uses a for loop. Sorry about the previous answer. Also, you may want to check the text inside the input functions. For instance, int(input("Enter number: ")) might have different capitalization similar to int(input("Enter Number: "))
In this exercise we have to write a python code requested in the statement, like this:
find the code in the attached image
We can write the code in a simple way like this below:
n = int(input("How many numbers do you need to check? "))
odd = 0
even = 0
for x in range(n):
num = int(input("Enter number: "))
if num % 2 == 0:
even += 1
print(str(num)+" is an even number")
else:
odd += 1
print(str(num)+" is an odd number")
print("You entered "+str(even)+" even number(s).")
print("You entered "+str(odd)+" odd number(s).")
See more about python at brainly.com/question/26104476
