What is the primary purpose of a slideshow presentation
Answers
Answer:
to help us to complete all of useless project given by school
Answer:
support the presenter's ideas
Explanation:
Related Questions
Which of the following would allow for the QUICKEST restoration of a server into a warm recovery site in a case in which server data mirroring is not enabled?a. Full backupb. incremental backupc. Differential back upd. Snapshot
Answers
Answer: C. Differential backup
Explanation: There are several ways od ensuring the preservation and storage of data even cases of disaster, one of such ways is data data mirroring which allows data to be replicated or copied in real time and several backup options. In cases where there there is need to restore a server, the warm recovery site provides a data or disaster recovery option used to mitigate the effect of data loss on organization. In the absence of data mirroring, differential backup option, provides the quickest recovery option as it only requires changes in the data stored after the last full backup. These speed experieced should be expected due to the relatively low data been dealt with rather than the entire data.
irving is running cable underground beside his driveway to power a light at his entrance .what type of cable is he most likely using?
A.MC
B.NNC
C.UFD
D.UF
Answers
Based on the given information, Irving is running cable underground beside his driveway to power a light at his entrance. The most likely type of cable he would use in this scenario is "D. UF" cable.
Why is the cable Irving is using a UF cable and its importanceUF stands for "Underground Feeder" cable, which is specifically designed for underground installations.
It is commonly used for outdoor applications, such as running power to lights, pumps, or other outdoor fixtures. UF cable is moisture-resistant and has insulation suitable for direct burial without the need for additional conduit or piping.
Read more about cables here:
https://brainly.com/question/13151594
#SPJ1
How do I write this in binary number ?
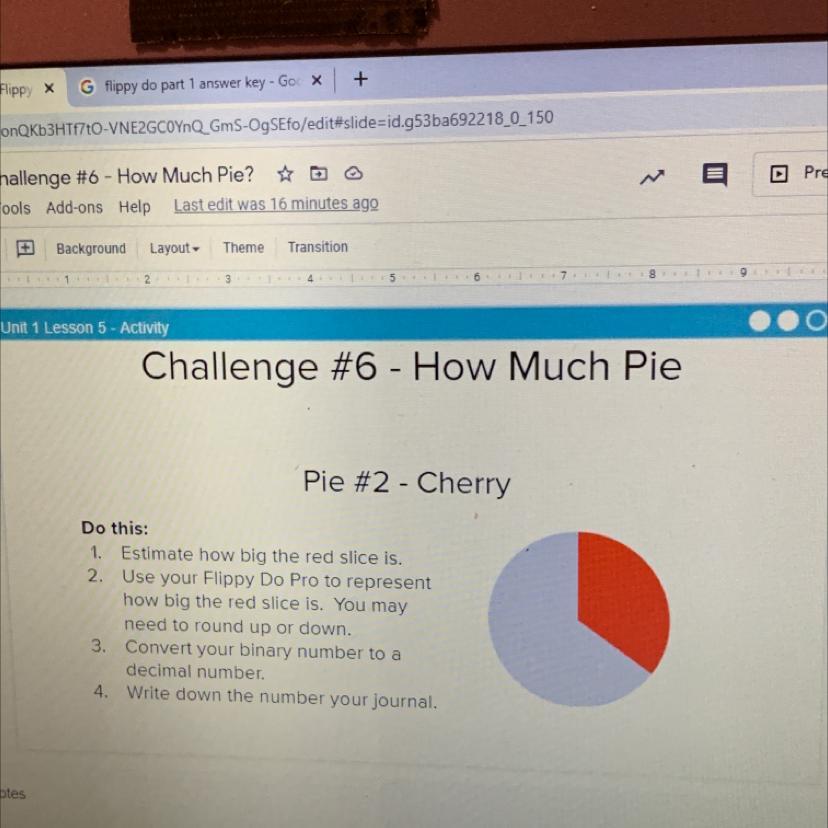
Answers
1/3 ~ 100001.010101...
an exact value cannot be found; therefore, the zeros in ones in this binary representation of 1/3 alternate forever.
During the test, the proctor should: (Check all that apply.)
Stop sharing the proctor’s video.
Unmute the proctor’s audio only if there is a test taker problem to resolve.
Step away from the computer for a brief break.
Closely monitor any behaviors that would violate the testing rules.
Answers
During the test, the proctor should:
Stop sharing the proctor's video.Unmute the proctor's audio only if there is a test taker problem to resolve.Closely monitor any behaviors that would violate the testing rules.What is Exam ProctoringIn Exam Proctoring, one have to disable proctor video sharing during the test. To avoid distracting exam takers, the proctor's video is controlled. Unmute proctor audio for test taker issues only.
This prevents proctor audio from disrupting test takers. Take a short break from the computer- not typically required for the proctor during testing. Proctors must be present and attentive to maintain test integrity. Monitor test takers for rule violations.
Learn more about proctor from
https://brainly.com/question/29607721
#SPJ1
Use the drop-down menus to complete the statements about the recall option in Outlook 2016.
Recalling a message stops its delivery before the recipient
it.
It only works about half the time, and it only works when recipients are in the same
.
Once it is recalled, the
will get a message informing them of the recalled message.
Be sure to check your message before you send it, and assume it will be read within 30
of sending the message.
Answers
Answer:
Recalling a message stops its delivery before the recipient
opens it.
It only works about half the time, and it only works when recipients are in the same organization
.
Once it is recalled, the recipient will get a message informing them of the recalled message.
Be sure to check your message before you send it, and assume it will be read within 30 seconds of sending the message.
Explanation:
explain 3 advantages and 3 disadvantages of computers
Answers
Answer:
advantage
1: finish tedious tasks faster (writing an essay)
2: the internet (you can learn anything)
3: reduces the use of paper
disadvantage
1: social media (being addictive toxic)
2: decreasing jobs
3: less time for people to interact in person
Explanation:
advantages:
1. computers make information more accessible
2. they help pass time
3. they store documents and data
disadvantages:
1. information can get leaked
2. costly
3. uses up electricity
What enables image processing, speech recognition & complex gameplay in ai
Answers
Deep learning, a subset of artificial intelligence, enables image processing, speech recognition, and complex gameplay through its ability to learn and extract meaningful patterns from large amounts of data.
Image processing, speech recognition, and complex gameplay in AI are enabled by various underlying technologies and techniques.
Image Processing: Convolutional Neural Networks (CNNs) are commonly used in AI for image processing tasks. These networks are trained on vast amounts of labeled images, allowing them to learn features and patterns present in images and perform tasks like object detection, image classification, and image generation.Speech Recognition: Recurrent Neural Networks (RNNs) and their variants, such as Long Short-Term Memory (LSTM) networks, are often employed for speech recognition. These networks can process sequential data, making them suitable for converting audio signals into text by modeling the temporal dependencies in speech.Complex Gameplay: Reinforcement Learning (RL) algorithms, combined with deep neural networks, enable AI agents to learn and improve their gameplay in complex environments. Through trial and error, RL agents receive rewards or penalties based on their actions, allowing them to optimize strategies and achieve high levels of performance in games.By leveraging these technologies, AI systems can achieve impressive capabilities in image processing, speech recognition, and gameplay, enabling a wide range of applications across various domains.
For more such question on artificial intelligence
https://brainly.com/question/30073417
#SPJ8
A choropleth map is used to
Group of answer choices
do a scatter plot.
show live satellite images.
present geographical regions in 3D.
present geographical regions coloured, shaded, or graded according to some variable.
Answers
What is a computer graphic? explain it role in designing.
Answers
Answer:
Computer Graphics is used where a set of images needs to be manipulated or the creation of an image in the form of pixels and is drawn on the computer. Computer Graphics can be used in digital photography, film, entertainment, electronic gadgets, and all other core technologies which are required
Explanation:
Computer graphic design combines skills in technology, business and art, using computer-generated images and words to create unique concepts and messages for publishing and advertising.
Select the correct answer.
Alan wants to retouch some of his photographs before he sends them to a client. What will the Liquify filters help him achieve?
A. changes in color tones
B. addition of lighting effects
C. distortions of organic forms
D. copying of elements in an image
E. increased or decreased contrast
λ
Answers
Answer:
Explanation:
D
Distortions of organic form liquify filters is the thing which will help Alan in achieving it. Thus, the correct option is C.
What are liquify filters?The Liquify filter are the options which lets us push, pull, rotate, reflect, pucker, and bloat any area of an image on the adobe photoshop. The distortions which we create through this can be subtle or drastic, this makes the Liquify command a powerful tool for the purpose of retouching images as well as creating artistic effects on it.
Distortion filters are generally used to change the shape of layers, twisting, and pulling them in different directions in a document. There are 27 different distortion filters available which include Black hole. Black hole distorts an image by causing part of it to disappear from it into the specified center point o the image, bowing the top, bottom, and sides towards inward.
Therefore, the correct option is C.
Learn more about Liquify filters here:
https://brainly.com/question/8721538
#SPJ2
Hattie uses the line of code num == 7 to assign the number 7 to the variable named num. What correction should be made?
Answers
Answer:
Its change == to =
the guy up there is right but was not spefic hope it helps
Explanation:
Numbering exception conditions, which often uses hierarchical numbering, in a fully developed use case description is helpful to _______. a. tie the exception condition to a processing step b. show which exception conditions are subordinate to other exceptions c. provide an identifier for each exception condition d. tie exception conditions to other diagrams or descriptions
Answers
Answer:
a) tie the exception condition to a processing step
Explanation:
Numbering exception conditions, in a fully developed use case description is helpful to tie the exception condition to a processing step
The fully developed use case description is useful for the documentation of the context, purpose, description, conditions, and workflow of each use case. Activity diagrams give a graphical image of the use case workflow and serve the purpose of illustrating the alternative paths through a business process.
Select all the activities Samil could so through his banking app.
Answers
Answer:
Make a deposit
Talk to a representative
Transfer money
Check account balances
Explanation:
Answer:
Make a deposit
Talk to a representative
Transfer money
Check account balances
Explanation:
i need help with project i dont know how to code and it is a console application using c#
Answers
The Program based on the information will be:
using System;
class Program {
static void Main(string[] args) {
Console.Write("Enter your name: ");
string name = Console.ReadLine();
Console.WriteLine("Hello, " + name + "!");
}
}
How to explain the programWhen you run this program, it will display the message "Enter your name: " on the console.
The user can then type in their name, and press Enter. The program will read the user's input using the Console.ReadLine() method, store it in the name variable, and then display the message.
Learn more about Program on
https://brainly.com/question/26642771
#SPJ1
Which technology is making quantum computing easier to access and adopt
Answers
The technology that is making quantum computing easier to access and adopt is known to be option c: cloud.
What technologies are used to build quantum computers?A lot of Efforts is known to be used in creating a physical quantum computer that is known to be based on technologies such as transmons, ion traps and others
Cloud computing is seen as a kind of an on-demand presence of computer system resources, and it is one that is made up of data storage and computing power, and it is one where there is no direct active management by the user.
Hence, The technology that is making quantum computing easier to access and adopt is known to be option c: cloud.
Learn more about quantum computing from
https://brainly.com/question/28082752
#SPJ1
See full question below
Which technology is making quantum computing easier to access and adopt?
a. Edge Computing
b. Virtual Reality
c. Cloud
d. Blockchain
(Reverse number) Write a program that prompts the user to enter a four-digit inte- ger and displays the number in reverse order. Here is a sample run:
Answers
Answer:
The program in Python is as follows:
num = int(input("4 digit number: "))
numstr = str(num)
if(len(numstr)!=4):
print("Number must be 4 digits")
else:
numstr = numstr[::-1]
num = int(numstr)
print(num)
Explanation:
This prompts user for input
num = int(input("4 digit number: "))
This converts the input number to string
numstr = str(num)
This checks if number of digits is or not 4
if(len(numstr)!=4):
If not, the following message is printed
print("Number must be 4 digits")
else:
If digits is 4,
This reverses the string
numstr = numstr[::-1]
This converts the reversed string to integer
num = int(numstr)
This prints the reversed number
print(num)
[2]
(c) Describe how the microprocessor can determine when to sound the clock alarm.
Answers
Answer:
The first is to set .As soon as the timer is set,the microprocessor starts counting. When the number it counts to is the same as the number of cycles.
Once the timer is set, the microprocessor begins keeping score. when the amount it counts up to equals the quantity of cycles.
What is a microprocessor?A microprocessor is a type of computer processor where the logic and control for data processing are housed on a single integrated circuit or a few interconnected integrated circuits.
The arithmetic, logic, and control circuitry needed to carry out the tasks of a computer's central processing unit are all included within the microprocessor.
Each microprocessor has an internal clock that controls how quickly it processes instructions and synchronises it with other parts of the system. Clock speed is the rate at which a microprocessor carries out instructions.
When an alarm clock goes off, the inside bell vibrates, producing sound waves that quickly pass through the atmosphere and reach our ears.
Thus, this way, the microprocessor can determine when to sound the clock alarm.
For more details regarding microprocessor, visit:
https://brainly.com/question/1305972
#SPJ2
Why do people make Among Us games on Ro-blox, and thousands of people play them, when Among Us is free on all devises?
A) Maybe they think the Ro-blox version is better???
B) They don't know it's on mobile. Nor do they know it's free.
C) I have no idea.
D) I agree with C).
Answers
I think its A) Maybe they think the Ro-blox version is better
Plus, Among Us isn't free on all devices. (like PC)
And, to be honest I like the normal Among Us better than the Ro-blox version...
Hope This Helps! Have A GREATTT Day!!Plus, Here's an anime image that might make your day happy:
A Process of receiving selecting
organizing interpreting checking and
reacting to sensory stimuli or data
so as to form a meaningful and
coherent picture of the world is
Select one:
a. Attitude
b. Perception
c. Communication
d. Thinking
= Perception
Answers
Answer:
I think it’s B based on the answer choices
Explanation:
A vendor conducting a pilot program with your organization contacts you for
organizational data to use in a prototype. How should you respond?
Answers
Since the vendor is conducting a pilot program with your organization contacts you for organizational data to use in a prototype, The way that you can respond is to Refer the vendor to the right personnel.
What is an example of a reference vendor?A report outlining the payment history between a company customer and its supplier or vendor is known as a supplier reference (or trade reference). It helps a supplier to evaluate your creditworthiness and determine whether you're a trustworthy customer before extending credit to you.
You can determine whether you are prepared to undertake the project fully by running a pilot program. It might highlight unforeseen difficulties that must be resolved, providing you the chance to change and improve in a way that lessens the effects of those difficulties.
Hence, An organization can discover how a large-scale project might function in practice by conducting a small-scale, brief experiment known as a pilot program, also known as a feasibility study or experimental trial.
Learn more about pilot program from
https://brainly.com/question/28920126
#SPJ1
Your goals as the IT architect and IT security specialist are to: Develop solutions to the issues that the specified location of IDI is facing. Develop plans to implement corporate-wide information access methods to ensure confidentiality, integrity, and availability. Assess risks and vulnerabilities with operating IT facilities in the disparate locations where IDI now functions and develop mitigation plans and implementation methods. Analyze the strengths and weaknesses in the current systems of IDI. Address remote user and Web site user’s secure access requirements. Develop a proposed budget for the project—consider hardware, software, upgrades/replacements, and consulting services. Prepare detailed network and configuration diagrams outlining the proposed change to be able to present it to the management. Develop and submit a comprehensive report addressing the learning objectives and your solutions to the issues within the scenario. Prepare a 10- to 15-slide PowerPoint presentation that addresses important access control, infrastructure, and management aspects from each location.
Answers
Te chequen casa para ver en su mouse hombre de doble
Java Fundamental
Step 1:
Ask the user to enter the clock speed (in Megahertz) of their graphics card (GPU). This is an indicator of how fast their graphics card is.
Step 2:
Ask the user to enter the clock speed (in Megahertz*) of their processor (CPU). This is an indicator of how fast their processor is.
Step 3:
Ask the user to enter the number of cores that their processor (CPU) has. The more cores a processor has, the more work it can do.
Step 4:
Output the following text: "Computer Hardware Graphics Quality Recommendation Tool"
Step 5:
Display the following output (See sample Input and Output below):
- The GPU clock speed
- The CPU clock speed
- The number of cores
Sample Input and Output (user input is in bold) - The output of your program should match the formatting and spacing exactly as shown.
Please enter the clock speed (in Megahertz) of your graphics card: 1000
Please enter the clock speed (in Megahertz) of your processor: 3000
Please enter the number of cores of your processor: 2
Computer Hardware Graphics Quality Recommendation Tool
GPU Clock Speed: 1000.0 MHz
CPU Clock Speed: 3000.0 MHz
Number of cores: 2
Answers
The law for this would look commodity like this
(" GPU Clock Speed" gpuClockSpeed" MHz");
(" CPU timer Speed" cpuClockSpeed" MHz");
(" Number of cores" numCores);
The final law would look commodity like this ;
public class ComputerHardwareTool{ public static void main( String() args){
Scanner input = new Scanner(System.in);
(" Please enter the timer speed( in Megahertz) of your plates card");
int gpuClockSpeed = input.nextInt();
(" Please enter the timer speed( in Megahertz) of your processor");
int cpuClockSpeed = input.nextInt();
(" Please enter the number of cores of your processor");
int numCores = input.nextInt();
(" Computer Hardware Graphics Quality Recommendation Tool");
(" GPU Clock Speed" gpuClockSpeed" MHz");
(" CPU timer Speed" cpuClockSpeed" MHz");
(" Number of cores" numCores);}}
Java is an object- acquainted programming language that is generally used in software development. It's designed to be platform-independent, allowing it to run on any system that has a Java Virtual Machine installed.
Step 1 Ask the user to enter the timer speed( in Megahertz) of their plates card( GPU). This is an indicator of how presto their plates card is. To do this, you will need to use the Scanner class to read in the user's input. The law for this would look commodity like this
Scanner input = new Scanner(System.in);
System.out.print(" Please enter the timer speed( in Megahertz) of your plates card");
int gpuClockSpeed = input.nextInt();
Step 2 Ask the user to enter the timer speed( in Megahertz *) of their processor( CPU). This is an indicator of how presto their processor is. The law for this would look commodity like this (" Please enter the timer speed( in Megahertz) of your processor"); int cpuClockSpeed = input.nextInt();
Step 3 Ask the user to enter the number of cores that their processor( CPU) has. The farther cores a processor has, the farther work it can do. The law for this would look commodity like this (" Please enter the number of cores of your processor");
int numCores = input.nextInt();
Step 4 Affair the following text" Computer Hardware Graphics Quality Recommendation Tool". The law for this would look commodity like this (" Computer Hardware Graphics Quality Recommendation Tool");
Step 5 Display the preceding affair( See sample Input and Affair below)-
The GPU timer speed- The CPU timer speed- The number of cores
The law for this would look commodity like this (" GPU Clock Speed" gpuClockSpeed" MHz");
(" CPU timer Speed" cpuClockSpeed" MHz");
(" Number of cores" numCores);
The final law would look commodity like this ;
public class ComputerHardwareTool{ public static void main( String() args){
Scanner input = new Scanner(System.in);
(" Please enter the timer speed( in Megahertz) of your plates card");
int gpuClockSpeed = input.nextInt();
(" Please enter the timer speed( in Megahertz) of your processor");
int cpuClockSpeed = input.nextInt();
(" Please enter the number of cores of your processor");
int numCores = input.nextInt();
(" Computer Hardware Graphics Quality Recommendation Tool");
(" GPU Clock Speed" gpuClockSpeed" MHz");
(" CPU timer Speed" cpuClockSpeed" MHz");
(" Number of cores" numCores);}}
For more such questions on String, click on:
https://brainly.com/question/24994188
#SPJ8
Write a pseudocode that receives a positive number from the user, and then,
starts printing and keep printing the word “CS” until the number of the printings matches the received number from the user.
b-) Write an algorithm for the same problem. c-) Draw a flowchart for the same problem.
Please help me
Answers
Algorithm, pseudocodes and flowcharts are used as prototypes for a complete program.
The pseudocode is as follows:
input n
for i = 1 to n
print("CS")
The algorithm is as follows:
1. Begin
2. Input number
3. For 1 = 1 to number
3.1 Display "CS"
4. End For
5. Stop
The following explanation of the pseudocode can be used for algorithms and flowcharts
This gets an integer input from the user (the integer represents the number of times to print "CS")
input n
This is repeated n times
for i = 1 to n
This prints "CS" in each iteration
print("CS")
See attachment for flowchart
Read more about algorithm, pseudocodes and flowcharts at:
https://brainly.com/question/21172316

What can toxic substances do to your body?
Select all that apply.
Answers
Answer:
burn you, affect your whole body
Explanation:
hope this helps :) !!!
Most slide layouts include at least one ________ by default.
Question 2 options:
placeholder
action button
transition
animation
Answers
Hey
I think that the answer placeholder :)
Sry if im wrong tho
Answer:
The answer is placeholder.
Please don't answer if you don't know Type the correct answer in the box
. Spell all words correctly. How does SQA differ from SQC? SQA involves activities to evaluate software processes, and SQC involves activities that ensure quality software.
Answers
Software Quality Assurance (SQA) and Software Quality Control (SQC) are two distinct aspects of quality management in software development, each with its own focus and activities.
How different are they?SQA encompasses efforts directed toward assessing and enhancing the procedures of software development at every stage. The main emphasis is on guaranteeing that appropriate techniques, norms, and protocols are adhered to in order to create software of superior quality. SQA encompasses various tasks, including scrutinizing requirements, conducting process audits, and administering quality control procedures.
Conversely, SQC pertains to actions that prioritize assuring the quality of the actual software product. This involves employing methods such as testing, inspections, and reviews in order to detect flaws and guarantee that the software satisfies the stated demands and standards. The goal of SQC is to identify and rectify any shortcomings or irregularities within the software product.
To put it succinctly, SQA focuses on assessing and enhancing the manner in which software is developed, while SQC is primarily focused on verifying the excellence of the resulting software product. SQC and SQA both play a vital role in attaining an optimum level of software quality.
Read more about software here:
https://brainly.com/question/28224061
#SPJ1
Data analytics benefits both financial services consumers and providers by helping create a more accurate picture of credit risk.
True
False
Answers
Answer:
True
Explanation:
Luke is setting up a wireless network at home and is adding several devices to the network. During the setup of his printer, which uses 802. 11g standard, he finds that he can't connect to the network. While troubleshooting the problem, he discovers that his printer is not compatible with the current wireless security protocol because it is an older version of hardware.
What wireless network security protocol will allow Luke to use the printer on his wireless network?
a. WPA
b. WEP
c. WPA2
d. WPA-PSK+WPA2-PSK
Answers
The wireless network security protocol that will allow Luke to use the printer on his wireless network is WEP. The correct answer is option b.
WEP (Wired Equivalent Privacy) is a security protocol that is used to secure wireless networks. It was introduced in 1999 and was widely used in the early days of wireless networking. However, it is an older version of hardware and is considered less secure than newer protocols such as WPA (Wi-Fi Protected Access) and WPA2 (Wi-Fi Protected Access 2).
Since Luke's printer is an older version of hardware, it is not compatible with the current wireless security protocol. Therefore, using WEP will allow Luke to use the printer on his wireless network.
Learn more about wireless network security:
brainly.com/question/30087160
#SPJ11
Viruses and worms can affect a system by:
A. Deleting hard drives
B. Slowing down the system
C. Improving system functions
D. Productive fake applications
Answers
Answer:
A
Explanation:
Worms can modify and delete files, and they can even inject additional malicious software onto a computer. Sometimes a computer worm's purpose is only to make copies of itself over and over — depleting system resources, such as hard drive space or bandwidth, by overloading a shared network
write down the character of Morden computer
Answers
The characteristics of a modern computer are :
Speed Accuracy storage Automation Communication Versatility Memory Reliability