What is the Internet of Things (IoT)?
A. The Internet of Things (IoT) is a theory that explains how internet devices communicate with each other using human-to-human language.
B. The Internet of Things (IoT) refers to a software network that use cloud storage and connectivity to share data.
C. The Internet of Things (IoT) is a theory that explains how computers store data collected from users online activities
D.The Internet of Things (IoT) refers to a network of physical de pres that use sensors, software, and connectivity to share data.
Answers
Answer:
D
Explanation:
The “things” in the internet if things means physical devices. It’s all the stuff that is internet-connected even if it may not be what your would normally think of, such as your thermostat, or fancy fridge.
The correct definition for the term 'Internet of Things' or IoT would be:
D). The Internet of Things (IoT) refers to a network of physical devices that use sensors, software, and connectivity to share data.
The Internet of Things often called IoT denotes an arrangement of associated physical devices that are permitted to gather and transmit data across the internet or wi-fi network.A number of infrared detectors, digital technologies, software, etc. are inserted together to serve the purpose of linking the devices and sharing of data.It helps the exchange of data without involving any kind of human intrusion and hence, making communication among devices convenient and effective.Thus, option D is the correct answer.
Learn more about 'computers' here:
brainly.com/question/2175764

Related Questions
30 POINTS! PLEASE ANSWER QUICK!!!
When coding in html, do you put \(<\)html\(>\) or \(<\)!DOCTYPE html\(>\) first?
Does it matter?
Answers
Answer:
your doctype comes first.
Explanation:
The first thing you should make sure to have in any HTML document you create is a "document type definition (DTD)" declaration.
it defines what elements and attributes are allowed to be used in a certain flavor of HTML
briefly define or describe a clustered index in 2-4 sentences.
Answers
A clustered index is a type of database index that determines the physical order of data storage within a table. It reorganizes the entire table to match the indexed column, allowing for faster retrieval of data and improved query performance. There can only be one clustered index per table.
This means that the rows of data are physically arranged in the same order as the clustered index, which can significantly improve query performance when accessing data that matches the indexed column.
Because the clustered index determines the physical order of the data, there can only be one per table. However, this index can be composed of multiple columns, which is known as a composite clustered index.
Creating a clustered index involves rearranging the data in the table, which can be time-consuming and resource-intensive for large tables. As a result, it's important to carefully select the column or columns to use as the clustered index to ensure that it will have a significant impact on query performance.
Overall, a clustered index can be a powerful tool for improving database performance, but it requires careful consideration and planning to implement effectively.
Know more about the clustered index click here:
https://brainly.com/question/28579836
#SPJ11
How do I delete the Chrome apps folder, because I tried to remove from chrome but it won't let me
Answers
Answer:
Explanation:
1. Open your Start menu by selecting the Windows logo in the taskbar and then click the “Settings” cog icon.
2. From the pop-up menu, click “Apps.”
3.Scroll down the “Apps & Features” list to find g00gle chrome
4. Click “G00gle Chrome” and then select the “Uninstall” button.
Hope this help!
Helped by none other than the #Queen herself
How do i launch a web browser on your computer.
Answers
Answer: Regardless of which version of Windows you have, you can also open the browser from the start menu. Select the start button and type in Chrome. If the Chrome browser is on your computer, it will be displayed in the menu, where you can now see the icon and select it to open.
Explanation:
The collaborative team responsible for creating a film is in the process of creating advertisements for it and of figuring out how to generate excitement about the film. Which of the five phases of filmmaking are they most likely in?
1 distribution
2 pre-production
3 production
4 post-production
Answers
Answer:
1. distribution
Explanation:
Filmmaking can be defined as the art or process of directing and producing a movie for viewing in cinemas or television. The process of making a movie comprises of five (5) distinct phases and these are;
1. Development.
2. Pre-production.
3. Production.
4. Post-production.
5. Distribution.
In this scenario, the collaborative team responsible for creating a film is in the process of creating advertisements for it and of figuring out how to generate excitement about the film.
Hence, they are likely in the distribution phase of the five phases of filmmaking.
Distribution refers to the last phase of filmmaking and it is the stage where the collaborative team considers a return on investment by creating advertisements in order to have a wider outreach or audience.
Answer:
a: distribution
Explanation:
edg2021
Distribution si where the movie gets distributed and promoted
What it means to say media is a continuum, not a category?
Can someone help me with that real quick please?
Answers
It means that media exists along a spectrum with various degrees of characteristics, rather than being strictly defined by rigid categories.
What does such ideology of media being a continuum imply?This perspective acknowledges the fluidity and overlapping nature of different media forms and their ever-evolving roles in communication, entertainment, and information dissemination.
As technology advances and media platforms continue to converge, the boundaries between traditional media categories (such as print, radio, television, and digital) become increasingly blurred. New forms of media often incorporate elements of existing forms, creating a continuous spectrum of media experiences.
Find more media related question here;
https://brainly.com/question/14047162
#SPJ1
Kerry is debugging a program. She identifies a line of code to begin execution and a line of code to end execution so that she is only running part of the computer program. Which is she using?
a.variable inspections
b.breakpoints
c.stepping functions
d.line-by-line search
Answers
Answer:
I think it's B on Edge, breakpoints
Explanation:
Answer:
B
Explanation:
If you are assignod "A", complele thrs fr your post-lis asiignment, dve 9/14 Graphing Data Set A Name: Lab Section: Most everyone has heard of "pi" but what is it exactly? Pi (π) is the ratio of the circumference of a circle to its diameter. The value of this ratio is a constant regardless of the size the circle; thus pi is a universal physical constant. The diameter and circumference of several circles were measured by CHEM 1114 students, each using a different ruler. 1. Inspect the data below and calculate the value of pi using two pairs of the data: 2. Prepare a hand-drawn plot of the two variables on the reverse side of this worksheet. Estimate the circumference of a circle with a diameter of 4.50 cm : Estimate the diameter of a circle with a circumference of 3.94 inches: 3. Prepare a plot using a software graphing program. Include the equation of the best-fit line and the R
2
value on the graph. Re-write the equation of the best-fit line substituting "Diameter" for x and "Circumference" for y directly on the graph. Attach the fully labeled graph to this worksheet. 4. What is the value of pi based on the equation for the best-fit line? Include units if applicable. Determine the percent error using the definition of percent error: Use a value of 3.142 for the actual value of pi. % error =
∣
∣
Actual
∣ Actual-Experimental
∣
∣
×100 \% Error = 6. Using your computer-generated graph, a. visually estimate the circumference of a circle when the diameter is 4.50 cm : b. calculate the circumference for d=4.50 cm using the equation of the best fit line: Inspect the graph to ensure that this value is reasonable. c. compare the calculated circumference to the two visually interpolated values (Steps 2 and 6a ). Comment on any discrepancies. 7. Using your computer-generated graph, a. visually estimate the diameter of a circle with a circumference of 3.94 inches: b. calculate the diameter using the equation of the line: Inspect the graph to ensure that this value is reasonable. c. compare the calculated diameter to the two visually interpolated values (Steps 2 and 7 a). Comment on any discrepancies.
Answers
The value of pi (π) is the ratio of the circumference of a circle to its diameter. It is a universal physical constant that remains constant regardless of the size of the circle. In this experiment, the diameter and circumference of several circles were measured using different rulers. The value of pi can be calculated using the data and a best-fit line equation. The percent error can also be determined by comparing the calculated value of pi to the actual value.
Pi (π) is a fundamental mathematical constant that represents the relationship between the circumference and diameter of a circle. It is an irrational number approximately equal to 3.14159. In this experiment, the CHEM 1114 students measured the diameter and circumference of various circles using different rulers. By analyzing the data, it is possible to calculate the value of pi.
To calculate pi, two pairs of data can be used. The diameter and circumference values are plotted on a graph using a software graphing program. The best-fit line equation is determined, and its equation is rewritten with "Diameter" as x and "Circumference" as y. This equation represents the relationship between the diameter and circumference of the circles measured.
Using the equation of the best-fit line, the value of pi can be determined. By substituting the actual value of pi (3.142) into the equation, the calculated value of pi can be obtained. The percent error can then be calculated by comparing the actual value to the experimental value.
To visually estimate the circumference of a circle with a diameter of 4.50 cm, one can refer to the computer-generated graph. The graph provides a visual representation of the relationship between the diameter and circumference. Additionally, the circumference can be calculated using the equation of the best-fit line, ensuring that the calculated value is reasonable.
Similarly, to estimate the diameter of a circle with a circumference of 3.94 inches, the computer-generated graph can be used. The graph helps in visually estimating the diameter. Additionally, the diameter can be calculated using the equation of the line to ensure the calculated value aligns with the visually interpolated values.
Learn more about Circumference
brainly.com/question/28757341
#SPJ11
How many possibilities does the password “Ilike_2_learn_about_cybersecurity!” have if I use both caps and lowercase, numbers, and special characters? Hint = there are 32 characters in the password
Answers
Answer:
Read Explanation
Explanation:
Uhh what do you mean by possibilities? Is there any option?
In the rma database, update a customer’s records. Write an SQL statement to select the current fields of status and step for the record in the rma table with an orderid value of "5175." What are the current status and step? Write an SQL statement to update the status and step for the orderid, 5175 to status = "Complete" and step = "Credit Customer Account." What are the updated status and step values for this record? Provide a screenshot of your work. Delete rma records. Write an SQL statement to delete all records with a reason of "Rejected." How many records were deleted? Provide a screenshot of your work. Create an output file of the required query results. Write an SQL statement to list the contents of the orders table and send the output to a file that has a .csv extension.
Answers
To load the data from each file into the table with the same name, use the import feature of your database application.
What is SQL?The domain-specific programming language known as SQL is used for managing data stored in relational database management systems or for stream processing in relational data stream management systems.
This step needs to be completed three times, one for each table. And can be done as:
LOAD DATA INFILE '/home/codio/workspace/customers.csv' INTO TABLE Customers FIELDS TERMINATED BY ',' ENCLOSED BY '"'LINES TERMINATED BY '\n'LOAD DATA INFILE '/home/codio/workspace/orders.csv' INTO TABLE Orders FIELDS TERMINATED BY ',' ENCLOSED BY '"'LINES TERMINATED BY '\n';LOAD DATA INFILE '/home/codio/workspace/rma.csv' INTO TABLE RMA FIELDS TERMINATED BY ',' ENCLOSED BY '"'LINES TERMINATED BY '\Thus, this can be the query for the given situation.
For more details regarding SQL, visit:
https://brainly.com/question/13068613
#SPJ1
You can only edit slides while in the Outline view.
True or False.
Answers
Answer:
true
Explanation:
You can easily add new text in Outline view, as well as edit existing slide text.
Answer:
the answer is false I got it correct on assignment
Explanation:
Imagine you're planning a wedding, and you need to transport all your wedding guests from the ceremony to the reception. A bus can carry 40 passengers. Please write a program to input the names of the bride(s) and groom(s), and how many guests are coming to the wedding. Then output the names of the couple, followed by how many buses are needed, and the number of extra people you could carry with those buses (empty seats)
Answers
To begin with, let's start by writing a program that can take in the necessary inputs and perform the calculations we need.
bride = input("Enter the name(s) of the bride(s): ")
groom = input("Enter the name(s) of the groom(s): ")
guests = int(input("Enter the number of guests attending the wedding: "))Next, we need to calculate how many buses we will need to transport all the guests. Since each bus can carry 40 passengers, we can divide the total number of guests by 40 and round up to the nearest integer to get the number of buses required. We can do this using the math.ceil() function, like so:
import math
buses_needed = math.ceil(guests/40)Finally, we need to calculate how many extra people we can carry with those buses. To do this, we can subtract the total number of guests from the number of buses times 40. If the result is positive, that means we have some extra seats on the buses that we can fill with additional guests. If the result is negative, that means we don't have enough buses to transport everyone. We can do this using a simple calculation, like so:
extra_seats = (buses_needed * 40) - guestsNow that we have all the necessary information, we can output it to the user using the print() function, like so:
print("Wedding details:")
print("Bride(s): " + bride)
print("Groom(s): " + groom)
print("Number of guests: " + str(guests))
print("Number of buses needed: " + str(buses_needed))
print("Extra seats: " + str(extra_seats))And that's it! With this program, you can easily calculate how many buses you need to transport your wedding guests and how many extra people you can carry with those buses. Good luck with your wedding planning!
For such more questions on Python
https://brainly.com/question/28675211
#SPJ11
what network is carrying the us open golf tournament
Answers
Peacock & Golf Channel will also be broadcasting
terms identify the type of web resource such as .com, .edu, and .org, are called? Please answer this quickly. I need help!!!!
Answers
Answer:
domain names
Explanation:
Answer: Top-level domains.
Explanation: Quizzed
What are some websites to watch free movies on? (anybody answer with like 3 or 4 websites)
Answers
fox that what i get on at school
Answer:Kodi with builds
Explanation:
its a perfectly safe download
the company's board of directors would like you to create private folders, which users should not know exist. while you are creating the new network share for their folders, which new share option should you choose to prevent users from seeing the folders?
Answers
The following is a possible answer.There are several new share options that one can choose when creating a new network share for private folders that should not be visible to users.
However, to prevent users from seeing the folders, one should choose the option to "Hide this share" when creating the new network share for their folders. This new share option will prevent users from viewing or accessing the folders through the network.To create a private folder, one should also assign appropriate permissions and rights to the user or group that will access the folder. One should restrict access to only the user or group that needs to access the folder and ensure that the folder is not shared with unauthorized users. Additionally, one can encrypt the folder or use password protection to add an extra layer of security to the private folder.The use of private folders is essential in protecting sensitive and confidential data in an organization.It is, therefore, important to ensure that the private folders are adequately protected to prevent unauthorized access or exposure to the data.for more such question on encrypt
https://brainly.com/question/20709892
#SPJ11
HELP PLEASE ive literally been here for hours
Binh has a few hours' time to create a presentation. She has most of the text and pictures she intends to use. Which feature can help her to quickly transfer the content into an attractive presentation?
A.
slide layout
B.
slide themes
C.
Slide Master
D.
Slide pane
Answers
Answer:slide layout
Explanation:
The following statements about regression using pooled cross section data are correct, with the exception of:
a. one should compute cluster-robust standard errors for conducting inference.
b. the increase in sample size increases the precision of estimators.
c. an important application is policy analysis using differences-in-differences method.
d. it enables time-varying intercepts and slope coefficients.
Answers
The statement that is incorrect regarding regression using pooled cross section data is: "d. It enables time-varying intercepts and slope coefficients."
Regression using pooled cross section data involves combining multiple cross-sectional observations over time to analyze relationships between variables. The correct statements are as follows:
a. One should compute cluster-robust standard errors for conducting inference: When dealing with pooled cross section data, it is important to account for potential correlation within clusters, such as individuals within households or firms within industries. Computing cluster-robust standard errors helps to address this issue and produce valid inference.
b. The increase in sample size increases the precision of estimators: With larger sample sizes, the estimates of coefficients become more precise and have smaller standard errors, leading to more reliable results and stronger statistical inference.
c. An important application is policy analysis using the differences-in-differences method: Pooled cross section data allows for the implementation of the differences-in-differences (DID) method, which is commonly used in policy analysis. DID compares the treatment effect on a group exposed to a policy intervention with a control group, providing insights into the causal impact of the policy.
d. It enables time-varying intercepts and slope coefficients: This statement is incorrect. Pooled cross section data assumes that the relationship between the dependent variable and independent variables is constant over time, so it does not accommodate time-varying intercepts and slope coefficients. Other methods, such as panel data analysis, are more suitable for examining such dynamics over time.
learn more about regression here
https://brainly.com/question/32505018
#SPJ11
Suppose the following formula is inputted into excel: =mround(1/4,100) the output in the cell will be?
Answers
'Suppose the following formula is inputted into Excel: =MROUND(1/4,100) The output in the cell will be: 0.2500 0.25 8' Download the App! Get 24/7 study help with the Numerade app for iOS and Android.
What is an Excel?The fundamental capabilities of all spreadsheets are present in Microsoft Excel, which organizes data manipulations like arithmetic operations using a grid of cells arranged in numbered rows and letter-named columns. It has a variety of built-in functionalities to address financial, engineering, and statistical requirements. Additionally, it has a very limited three-dimensional graphical display and can present data as line graphs, histograms, and charts. Data can be divided into sections to show how different things affect it from various angles (using pivot tables and the scenario manager). A data analysis tool is a pivot table. This is accomplished by using PivotTable fields to condense big data sets.
To learn more about Excel from the given link:
brainly.com/question/25879801
#SPJ4
A nested "if" statement only executes if the "if" statement in which it is nested evaluates to True. True False
Answers
The given statement "a nested "if" statement only has an impact if the "if" statement it is contained within evaluates to True" is TRUE.
What is a nested "if" statement?The use of nested IF functions, or one IF function inside another, increases the number of outcomes that may be tested and allows for the testing of numerous criteria.
Based on their performance, we wish to assign each student a grade.
Return an A if Bob's score in B2 is greater than or equal to 90.
Only if the "if" statement in which it is nested evaluates to True does a nested "if" statement take effect.
The OR function allows you to test many conditions in each IF function's logical test and returns TRUE if any (at least one) of the OR arguments evaluates to TRUE.
Therefore, the given statement "a nested "if" statement only has an impact if the "if" statement it is contained within evaluates to True" is TRUE.
Know more about the nested "if" statement here:
https://brainly.com/question/14915121
#SPJ4
How your private data and information are used, who has access to them, which techniques and technologies protect them, and the communications and preferences surrounding how they are handled are components of Internet
Answers
The security components of Internet describes how user's private data are used, who has access to them, which techniques and technologies protect them.
What are the security components of Internet?The security components of Internet can be defined as a strategic process that highlights and describes how all end user's private data and information are used, who has access to them, which techniques and technologies protect them.
Furthermore, the communications and preferences surrounding how an user's private data and information are handled describes are the security components of Internet.
Read more on security here: https://brainly.com/question/14286078
#SPJ1
Whats the formatting of a letter to the editor?
Answers
Answer:
Date: Make sure to write the date below the sender's address excluding one space or line. Receiving Editor's address: You should mention the address of the recipient that is the editor's address. The Subject of the letter: It must convey the main purpose of the letter to the readers.
Explanation:
Hope this will help
Arrange the code so that the numbers are swapped.
Second part
savec
First part
C=D
Third part
D= save
Answers
Answer:
Following are the correct code for swapping:
save=C
C=D
D=save
Explanation:
Please find the attached file of the program with output.
In the above, we let that the three integer variable "save, C, and D" is declared that in which the variable "C and D" holds a value and "save" variable is used to hold "C" variable value.
At this the "C" variable is empty. so, it holds a "D" variable value and when it is empty it holds a save value. At this, we perform the swapping.

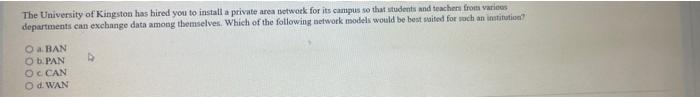
the university of kingston has hired you to install a private area network for its campus so that students and teachers from various departments can exchange data among themselves. which of the following network models would be best suited for such an institution?
Answers
The network models that would be best suited for such an institution is known as CAN.
How does a CAN network work?The CAN is known to be a kind of a peer-to-peer network. This is a term that connote that there is not any master that act to controls when the all the nodes have access to read as well as write data on the CAN bus.
Note that if a CAN node is said to be ready to transmit data, it looks to see if the bus is said to be busy and then it is one that often writes a CAN frame onto the network.
Note that network model is seen as a kind of database model that is set up as a flexible method to showing objects and their relationships
Therefore, The network models that would be best suited for such an institution is known as CAN.
Learn more about network models from
https://brainly.com/question/23369075
#SPJ1
Help pweeze this is due today :(
I will give u brainliest just pweeze, I need this answer :(
Answers
Answer:
just go in a website and see why important to them
Explanation:
and why the share with more people
The series of steps that describe exactly what each portion of a program is supposed to do is known as a(n)?
Answers
The series of steps that describe exactly what each portion of a program is supposed to do is known as an Algorithm.
What is algorithm and how it works?An algorithm is known to be a kind of a coded formula that is said to be written into software and it is one if triggered can make the tech to take some action to handle a problem.
Note that Computer algorithms work through the use of input and output and as such, The series of steps that describe exactly what each portion of a program is supposed to do is known as an Algorithm.
Learn more about Algorithm from
https://brainly.com/question/15802846
#SPJ1
What symbol do you use to choose a feature for your notes on Notion?
Answers
Answer:
The core element of notions is called blocks from where all the content bring forth. It has around fifty blocks.
Explanation:
Notion is the newest and fastest growing productivity tools for the recent memory. Notions has been reached out to the fight club meme status. When it is plain, it is easy to use and start. But even after it many of the users have difficulty in using this tools when it comes to the powerful cases.
There are some steps through that one can start to use this tool for their productivity.
To built the blocks
To organize the notions.
To create the habit tracker
To move the pages in notions
Data base and the views.
Type / - type table - select online- full page
A table that automatically analyzes and summarizes your data is called a/an
Answers
Spreadsheet numbers and a graph cannot be placed on thesame worksheet.
True orFalse
Answers
Answer:
True
Explanation:
In recent years, technology has greatly improved our listening experience through better earphones and headphones. Some of the popular brands offering headphones with the latest technology are Suny and Base. Answer the following questions: a. One of the technologies used in these headphones is Active Noise Cancellation (ANC). Headphones with ANC provides a better listening experience for their users. It is hard for customers to find other substitutions to replicate the same experience using these headphones. With this said. we can say that the demand for headphones with ANC will likely be . Type I for Inelastic, E for Elastic or U for Unit Elastic. b. Suny is experimenting to decide the best price to sell their newest headphone. In a surveyed market, it is estimated that 985 headphones can be sold in a day if it is sold at a price of $496. If prices drop to $422, more headphones can be sold and it is estimated that 1099 headphones will be sold. What is the estimated price elasticity of demand using the mid-point formula? Answer to the nearest two decimal places. c. Assume that Suny is trying to maximise revenue. Considering your findings in part b), should Suny increase the price for this headphone in hopes to increase revenue? Type Y for Yes, N for No or U for Unknown.
Answers
Price Elasticity of Demand = ((Q2 - Q1) / ((Q1 + Q2) / 2)) / ((P2 - P1) / ((P1 + P2) / 2))
a. The demand for headphones with Active Noise Cancellation (ANC) will likely be Type I for Inelastic.
b. To calculate the price elasticity of demand using the mid-point formula, we can use the following formula:
Price Elasticity of Demand = ((Q2 - Q1) / ((Q1 + Q2) / 2)) / ((P2 - P1) / ((P1 + P2) / 2))
Given:
Q1 = 985 headphones
Q2 = 1099 headphones
P1 = $496
P2 = $422
Price Elasticity of Demand = ((1099 - 985) / ((985 + 1099) / 2)) / (($422 - $496) / (($496 + $422) / 2))
Calculating the value, we find that the estimated price elasticity of demand is approximately -0.76.
c. Since the price elasticity of demand is negative (-0.76), it indicates that the demand for headphones is elastic. In order to maximize revenue, Suny should decrease the price for this headphone, rather than increase it. Therefore, the answer is N for No.
Learn more about Elasticity here
https://brainly.com/question/30999432
#SPJ11