What is the area of rectangle URST?
24 mm
48 mm
135 mm2
144 mm2
Answers
Answer:
135 mm²
Explanation:
Rectangles A B C D and U R S T are congruent. The length of sides A B is 9 millimeters and the length of sides R S is 15 millimeters.
What is the area of rectangle URST?
Answer: Two rectangles are said to be congruent if the size of their sides are equal. If Rectangles A B C D and U R S T are congruent, this means that AB = UR, BC = RS, CD = ST and AD = UR
Given that:
AB = 9 millimeters and the length of sides RS = 15 millimeters.
Area of rectangle URST = length × breadth = UR × RS
but since ABCD and URST are congruent, UR = AB. Therefore:
Area of rectangle URST = length × breadth = AB × RS = 9 mm × 15 mm = 135 mm²
Answer:
C 135 MM2
Explanation:
Got it right on edge2020
Related Questions
1.What are some examples of cyber crime?
2. What is a computer virus?
3. What are some ways a computer can get a virus?
4. What are some things you can do to be safe on the internet?
Answers
Answer: 1.Illegal Gambling. The Internet Skill Game Licensing and Control Act was introduced in Congress in 2008.
2. A computer virus is a type of computer program that, when executed, replicates itself by modifying other computer programs and inserting its own code.
3.Malicious online ads, also known as Malvertising, is just another way your computer can get a virus without any realization or traceable evidence.
4.Secure Your Network. Many of our computers connect to our files, printers, or the Internet via a Wi-Fi connection.
Explanation:
What is the use of an NDP?
A). identifying pointers at the other end of a network
B). sending an error message if a packet gets lost due to a bad connection
C). finding other computers on the network
D). taking an IP address from a network layer and identifying the associated MAC address
Answers
Answer:
Taking an IP address from a network layer and identifying the associated MAC address
Explanation:
Option D
When the prompt function is used in JavaScript, _____ appears.
A.
an error message
B.
a pop-up box
C.
a data warning
D.
a password request
Answers
Answer:
B
Explanation:
instructs the browser to display a dialog with an optional message prompting the user to input some text, and to wait until the user either submits the text or cancels the dialog
What is the best response to cyberbullying?
A. Confront the bully in person to resolve the situation.
B. Send similar responses to show the bully how it feels.
C. Confide in an adult you trust, such as a teacher or parent.
D. Write the bully an e-mail asking him or her to stop.
Answers
Question: How do you file a complaint using a food restaurant? 100 POINTS WILL BE GIVEN INCLUDING BRAINLIEST
Answers
send it through the mail
Answer: Be prepared to provide the following information:
1.Your Name, Address and Phone Number (your information will remain anonymous to the restaurant)
2.Name of restaurant
3.Location/address of the restaurant
4.Date of incident
5.Nature of complaint
If you suspect you became ill from this incident. You will need to give specific information about the suspected foods that made you sick, as well as when your symptoms began, and what they were. In addition, you will need to give a 3-day food eating history.
Explanation
Why is it Called Eleven and Not Onety-One? This is an actual question I'm curious.
Same goes for Twelve. Onety-Two? 13? Onety-Three?
Answers
Answer: Ten is not called onety because you have ten fingers and not nine. That part is actually extremely logical and straightforward. Besides, what do you think "ty" actually means? You suggest that we say "one ten" every time we want to say "ten". Now that is illogical.
Explanation:
An example of how a merge code would appear in a letter would be _____.
Answers
Answer:
Space blank
Explanation:
It means the question needs you to answer the question
Answer:
An example of how a merge code would appear in a letter would be C i.e. /University_Name/. Explanation: Merge codes help speed up the method of making letters by inserting data into your letters.
Explanation:
I hope this helps
Hi! Does anyone know how long it takes for a S o u n d C l o u d import to finish importing to a video-making website (Flixier to be exact) It'll be much appreciated if you answer this! I'll mark brainliest!
Answers
Answer:
It takes me around 20 to even an hour but its always different depending on the length
Explanation:
Answer:
It can take 5-7 business days
Explanation:
Hope this helps
When should students practice netiquette in an online course? Check all that apply.
when sending texts to friends
when sending e-mails to classmates
when collaborating in library study groups
when participating in online discussion boards
when collaborating as part of a digital team
Answers
A college campus uses robots to give students tours. The prospective students can ask the robot questions about life on campus. The robot allows the visiting student to choose which parts of campus to visit. What best describes the type of AI possessed by the robot?
weak AI
neural network AI
symbolic AI
Strong AI
Answers
The type of AI possessed by the robot in this scenario is Weak AI, also known as Narrow AI or Applied AI.
Weak AI is designed to perform a specific task, and it operates within a limited domain. The robot in this scenario is programmed to give tours of the campus and answer questions about life on campus. It does not have general intelligence, consciousness, or the ability to think and reason like a human being, and it cannot perform tasks outside of its programmed capabilities.
In contrast, Strong AI, also known as Artificial General Intelligence (AGI), is a theoretical form of AI that would possess human-like intelligence and the ability to reason and perform any intellectual task that a human can do. However, Strong AI does not currently exist.
Neural network AI and Symbolic AI are categories of techniques and approaches used in the development of AI, and they can be applied to both Weak AI and Strong AI systems. Neural network AI involves developing algorithms that are modeled after the structure and function of the human brain, while Symbolic AI involves creating AI systems based on a set of rules or symbols. However, the type of AI possessed by the robot in this scenario is more specifically described as Weak AI.
Teaching Machine Learning system means feeding _________ to computer.
Answers
Explanation:
information and data to the computer
Answer:
Information. I'm pretty sure that's what it is.
what is the answer i need them now pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls

Answers
Answer: Insert ribbon > table drop down menu
Explanation:
Answer:Insert ribbon > table drop down menu
Explanation:
3 different ways color sensors are used in everyday life.
Answers
Answer: The most famous way is to grade colored products, but it's also useful for; Distinguishing coded markings and to detect data codes on a package.
This is the complex version:
Color sensors are widely used in various applications to detect and analyze colors. Here are three different ways color sensors are used in everyday life:
Color Sorting in Manufacturing: Color sensors play a crucial role in industrial manufacturing processes, particularly in product sorting and quality control. For example, in the food industry, color sensors are used to sort fruits, vegetables, candies, or other items based on their color and appearance. By accurately detecting and categorizing different colors, the sensors ensure that only products meeting specific color criteria are selected, improving efficiency and maintaining product consistency.Color Calibration in Displays: Color sensors are employed in devices with displays, such as smartphones, monitors, and televisions, to ensure accurate color reproduction. These sensors measure the ambient light and adjust the display's color settings accordingly. By analyzing the surrounding light conditions, color sensors help optimize the color temperature, brightness, and contrast of the display to provide a visually pleasing and consistent viewing experience.Color Recognition in Home Automation: Color sensors are utilized in smart home automation systems to detect and recognize specific colors. For instance, in lighting automation, color sensors can identify the color of objects or surfaces in a room and adjust the lighting accordingly. This enables dynamic lighting scenes where the color and intensity of the lights can change based on the detected colors, creating an immersive and personalized environment.Additionally, color sensors are used in various applications such as printing, textile manufacturing, medical diagnostics, and color analysis in scientific research. They provide precise and reliable measurements of color information, allowing for enhanced accuracy, efficiency, and improved user experiences in many everyday scenarios.
public class Main {
public static void main(String[] args) {
String firstName = "John ";
String lastName = "Doe";
String fullName = firstName + lastName;
System.out.println(fullName);
}
}
From this example copy and paste code that when run would say your name. in javascript with my first name being Ryan and my last name being Smith
Answers
Answer:
const firstName = "Ryan ";
const lastName = "Smith";
const fullName = firstName + lastName;
console.log(fullName);
Explanation:
public static void main(String[] args) {
String firstName = "Ryan";
String lastName = "Smith";
String fullName = firstName + lastName;
System.out.println(fullName);
}
Explain the difference between SLR cameras’ and point-and-shoot cameras’ viewfinders. Which viewfinder do you think would be easier to use? Why?
Answers
Answer: A point-and-shoot digital camera estimates the light that will reach the sensor on an LCD screen. A SLR camera is a single lens reflex camera. As an SLR camera has a reflex mirror, it allows you to see through the viewfinder the real image that the film will see.
Explanation:
Optical viewfinders show you a true image. Which means that there's no lag; you're simply looking at a scene through a lens. Cameras using electronic viewfinders, on the other hand, have to convert the light into a digital image and then display it via the EVF. And that can take time, which manifests as viewfinder lag.
Which statement uses the example type of context clue for the underlined word?
a) The constant interruptions discomfited, or frustrated, her.
b) The arduous task involves shoving, lifting, and hurling bricks.
c) The opportunity didn’t last long; it quickly dwindled, or went away.
d) Most of the house was destroyed, but the kitchen remained intact.
Answers
How does a resident virus differ from a non-resident virus? !!!25 POINTS!!!!!
A) Resident viruses simply disrupt operations while non-resident viruses will control hosts.
B)Resident viruses will control hosts while non-resident viruses simply disrupt operations.
C)Resident viruses find networks to infect while non-resident viruses load themselves into memory.
D)esident viruses load themselves into memory while non-resident viruses find networks to infect.
Answers
Answer:
The correct answer is **D)** Resident viruses load themselves into memory while non-resident viruses find networks to infect. A resident virus is a type of computer virus that’s deployed and resides within a computer’s random access memory (RAM). A non-resident computer virus, on the other hand, is a type of computer virus that doesn’t reside within a computer’s RAM. Non-resident computer viruses can still be deployed within RAM, but they don’t stay there.
how do i end my current plan that i never signed up for, the basic one it charged me $24
Answers
Answer:
...
Explanation:
I think you need to call the brainly HQ other then that i don't know.
Da heck is happening in my history class

Answers
Answer:
wow what in the word why tho lol
Explanation:
Tonya is creating a program that will allow the user to input their work address. Which kind of variable should Tonya use for this?
A.
a syntax variable
B.
a float variable
C.
a string variable
D.
an alphabetic variable
Answers
Answer:
B.
a float variable is the answer
Explanation:
becouse it is float variable
Which of the following is not a language commonly used for web programming? PHP Assembly Java Python
Answers
Answer:
If you’re a software developer, then you probably—every now and then—feel overwhelmed by the super-fast pace at which our industry evolves, and that’s fine. I certainly feel that way sometimes, especially when trying to keep up with the latest trends.
But it’s possible to be well-informed about what’s going on out there, and use that information to your advantage, by being economical about your learning.
Sure, there are lots of programming languages. Sure, new ones keep being created every week—and don’t even get me started on JavaScript frameworks.
Do you need to learn all of them? Of course not.
First, learn about a number of the most popular programming languages. Then, narrow that list down, by picking the ones that make the most sense for your current knowledge level, employment status and other criteria that might make sense for your scenario.
For instance, if you intend to learn the functional paradigm, then pick a functional language from the list. Rinse and repeat.
That’s what this post is about. We’ve done the legwork for you, compiling a list of five of the most popular programming languages for 2019. Now you only have to read it and put it to good use.
(Hope this helped if not i am so so sorry hope you have a blessed day goodbye)
Answer:
Hypertext Preprocessor, better known under the old acronym PHP, is a scripting language based on C and Perl. It is mainly used for programming dynamic websitesweb applications. PHP is considered to be beginner-friendly and can be integrated integrated into HTML
Java is the most popular web programming language. It is used to develop website content, games, apps, and software.
Be sure to answer the following in complete and detailed sentences.
1. What might be a benefit of wirelessly connecting smart devices in a physical computing project?
2. How might you connect more than two micro:bits to activate multiple outputs triggered by one micro:bit?
3. How do batteries and other types of power sources make physical computing systems more mobile? Why is that helpful?
Answers
Answer: 1, 3
Explanation:
1: It can not just cause less of a wire mess. It can also cause easy travel if you want to do something from somewhere else!
3: It can make it easier to power up a device quickly when you CAN replace the batteries. It can also make charging more efficient overall.
Answer:1: It can not just cause less of a wire mess. It can also cause easy travel if you want to do something from somewhere else!
3: It can make it easier to power up a device quickly when you CAN replace the batteries. It can also make charging more efficient overall.
Explanation:
what are some basic commands to remember in terminal? windows 10
please help if you know
Answers
Answer:
If you just need a few, maybe this can help.
Explanation:
Cat - The cat command means 'Concatenate'. It prints the contents of a file or files to stdout. It's frequently used in Linux commands.
Touch - Using the 'Touch' command, you can create a file, or possibly just modify or generate a timestamp.
Move - The 'mv' command stands for 'Move'. As the name says, we can use this command to move files and directories from one place to another.
Chsh - The chsh command changes a user's login shell attribute. If you want to change the shell of another user, execute the command with root permissions.
Sudo - 'Sudo', or 'super user do', is a command that allows you to elevate your user privileges while executing the command to administrator privileges.
Most files in Windows are associated with a specific program that is assigned to open the file by default. At times, remembering these associations can become confusing. You can remind yourself by entering the command assoc to display a full list of filename extensions and program associations. You can also extend the command to change file associations. For example, assoc .txt= will change the file association for text files to whatever program you enter after the equal sign. The assoc command itself will reveal both the extension names and program names, which will help you properly use this command.
In Windows 10, you can view a more user-friendly interface that also lets you change file type associations on the spot. Head to Settings (Windows + I) > Apps > Default apps > Choose default app by file type
2.Cipher
Deleting files on a mechanical hard drive doesn't really delete them at all. Instead, it marks the files as no longer accessible and the space they took up as free. The files remain recoverable until the system overwrites them with new data, which can take some time. The cipher command, however, lets you wipe a directory on an NTFS-formatted volume by writing random data to it. To wipe your C drive, for example, you'd use the cipher /w:d command, which will wipe free space on the drive. The command does not overwrite undeleted data, so you will not wipe out the files you need by running this command.
When you run the cipher command by itself, it returns the encryption state of the current directory and the files it contains. Use cipher /e: to encrypt a file, cipher /c: to retrieve information about encrypted files, and cipher /d: to decrypt the selected file. Most of these commands are redundant with the Windows encryption tool BitLocker.
3.file Compare
You can use this command to identify differences in text between two files. It's particularly useful for writers and programmers trying to find small changes between two versions of a file. Simply type fc and then the directory path and file name of the two files you want to compare.
You can also extend the command in several ways. Typing /b compares only binary output, /c disregards the case of text in the comparison, and /l only compares ASCII text.
So, for example, you could use the following:
fc /l "C:\Program Files (x86)
The above command compares ASCII text in two Word documents.
4.Ipconfig
This command relays the IP address that your computer is currently using. However, if you're behind a router (like most computers today), you'll instead receive the local network address of the router.
Still, ipconfig is useful because of its extensions. ipconfig /release followed by ipconfig /renew can force your Windows PC into asking for a new IP address, which is useful if your computer claims one isn't available. You can also use ipconfig /flushdns to refresh your DNS address. These commands are great if the Windows network troubleshooter chokes, which does happen on occasion.
5.Netstat
Entering the command netstat -an will provide you with a list of currently open ports and related IP addresses. This command will also tell you what state the port is in; listening, established, or closed.
This is a great command for when you're trying to troubleshoot devices connected to your PC or when you fear a Trojan infected your system and you're trying to locate a malicious connection.
6.Ping
Sometimes, you need to know whether or not packets are making it to a specific networked device. That's where ping comes in handy.
Typing ping followed by an IP address or web domain will send a series of test packets to the specified address. If they arrive and are returned, you know the device is capable of communicating with your PC; if it fails, you know that there's something blocking communication between the device and your computer. This can help you decide if the root of the issue is an improper configuration or a failure of network hardware.
7.PathPing
This is a more advanced version of ping that's useful if there are multiple routers between your PC and the device you're testing. Like ping, you use this command by typing pathping followed by the IP address, but unlike ping, pathping also relays some information about the route the test packets take.
i need a essay 3-5 sentences on volleyball
Answers
Answer:Volleyball is a team sport that involves two teams of six players, one of which plays offense and the other defense. Each player has a specific role to play on the court:
Setter – The setter positions herself in front of her teammates, and sets up the ball for them to hit. She also controls the pace at which points are played, as well as how long each point lasts. The setter’s job is to make sure that every point goes smoothly without any errors or mistakes by her teammates.
– The setter positions herself in front of her teammates and sets up the ball
Explanation:
pick and choose the sentences from there
Many websites (mostly online shopping sites), monitor a person’s Internet browsing behavior, such as the websites we often visit, our buying preferences, and so on. Do you think that this is ethical? If not, can you suggest ways to stop this activity? If yes, explain the context in which it is important to us.
Answers
Answer:
Yes, this pratice is ethical
Explanation:
You are freely choosing to go on to these websites and most websites inform you that they are doing this. Edward Snowden, told the world that goverments are spying on them. Most people did not have a problem with this. Since, most people have a way to inform themsevles about the practices on the websites(by reading the terms of serve) and people don't care about spying than this is in no way unethical practice.
Vocabulary and Bridge Information
Directions: Do NOT use bullet points or copy and paste definitions. Put them in YOUR words.
Once you have completed the vocabulary, answer the following discussion questions. In complete sentences.
VOCABULARY
Bridge 16. Beam
Ingenuity 17. Girder
Architecture 18. Abutment
Engineer 19. Truss
Level 20. Anchorage
Protractor 21. Deck
Arch 22. Mortar
Structure 23. Pile Driver
Engineering 24. Suspension Cable
Innovation 25. Rivet
Force
Physics
Prototype
Tension
Compression
DISCUSSION: Research the following bridge disasters and tell me the following: Who built/designed the bridge, what happened and when it happened. Answer in complete sentences.
Iron Bridge
London Bridge
Dee Bridge
Tacoma Narrows Bridge
Point Pleasant Bridge
Answers
This is to bunch of questions..
1. What do you think is the most important event in the history of the internet? What event has had the biggest impact on your daily life?
Answers
Answer:
The biggest event in internet history was YuTubers punching each other in the face. Months of hype came to a peak Saturday for the self-declared “biggest event in internet history” a boxing match between two YuTube celebrities in Manchester, England.
Explanation:
There is no particular event but the whole journey till now which shaped my personality. Every person even if they are the worst has something good in them.
The impact it has had:
Developed into the globally used Internet which is now integrated into modern society and is seen as an essential for good quality of life.
What does the PC troubleshooting process include? Select two answers.
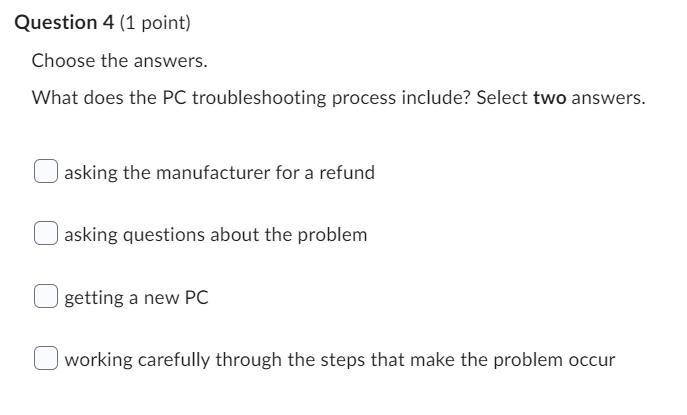
Answers
Troubleshooting is a systematic process used to locate the cause of a fault in a computer system and correct the relevant hardware and software issues. Approaching problem solving using a logical and methodical approach is essential to successful resolution.
Learn more at about PC troubleshooting: https://brainly.com/question/27109345
#SPJ1
Dr. Kim divides a programming class into groups. Each group will create a large program as their
final exam. To make this big project more manageable, which of these should the group use?
an algorithm creator
a binary translator
a text editor
top-down programming
Answers
Why is it recommended to develop a study plan? A. It tells you when your teacher is planning on giving the test. B. It helps you organize what you will study and when you will study to ensure you have enough time. C. It provides all of the information that your teacher will put on the test. D. It tells your Learning Coach when to help you study for your test.
Answers
Answer:
B. It helps you organize what you will study and when you will study to ensure you have enough time.