What feature do you need on a computer if you want to take it with you on vacation to another continent
Answers
Main Answer:
What feature do you need on a computer if you want to take it with on vacation to another continent? Dual-Voltage Selector.
Sub heading:
what is mean by dual voltage selector?
Explanation:
1. A switch used to select primary windings of a transformer.
2.A transformer with one or more windings with two voltage avaliable in order to be able to operate
Reference link:
https//brainly.com
Hashtag:
#SPJ4
Related Questions
Which statement is correct? O a. There could be more than one critical path in a network of activities O b. Delay in performing the activities that are not on the critical path would never lead to a d
Answers
The correct statement is "There could be more than one critical path in a network of activities".
Critical Path Analysis is a technique utilized to define the critical path for a project plan or schedule, which includes determining the shortest time necessary to complete tasks.The critical path in a network diagram is the sequence of linked activities that takes the longest time to finish and is the most crucial path to follow to complete the project in the shortest possible time.If there is no delay in performing the critical path activities, the project is completed on time. In contrast, any delay in performing the activities on the critical path will result in the entire project being delayed.There might be more than one critical path in a network of activities.
When there are more than one critical paths, a delay in one of the activities that lie on one of the critical paths can cause a delay in the project's overall completion date.Therefore, in multiple critical paths, each path's duration is critical to completing the project on time. To ensure that project delivery times are kept to a minimum, the project manager should focus on the critical path tasks' timely completion while keeping an eye on the non-critical path tasks.CPA can provide visibility to all activities in the network of activities, allowing the project manager to optimize project delivery times, manage resources, and identify areas where the project can benefit from improving processes, skills, or technology to complete the project on time and within budget.
Learn more about network :
https://brainly.com/question/31228211
#SPJ11
in classification problems, the primary source for accuracy estimation of the model is ________.
Answers
Answer:
In classification problems, the primary source for accuracy estimation is the confusion matrix (or classification matrix or contingency table)
you are querying a database of ice cream flavors to determine which stores are selling the most mint chip. for your project, you only need the first 80 records. what clause should you add to the following sql query? select flavors from ice cream table where flavor
Answers
To limit the number of records returned by the SQL query to the first 80 records, you can add the "LIMIT" clause to the query. The "LIMIT" clause specifies the maximum number of rows that the query should return.
The modified SQL query would be:SELECT flavors FROM ice_cream_table WHERE flavor = 'mint chip' LIMIT 80;This query will retrieve only the flavors of ice cream that match the criteria of "mint chip" and limit the results to the first 80 rows. This will save time and resources as the database will only need to retrieve and return the necessary data for the project.It is important to note that the syntax for the "LIMIT" clause may vary depending on the specific database management system being used. Therefore, it is recommended to consult the documentation or reference guide for the specific database system to ensure proper syntax is used.
To know more about SQL click the link below:
brainly.com/question/31663284
#SPJ11
How to use proptypes in react functional component
Answers
Answer:
React components use a special property named propTypes to set up type checking
Explanation:
This is your answer.
briefly explain the differences and capabilities between various data recording/capture systems. compare and contrast the value between onboard capture systems and down-linking data systems. why are such systems usually not mandated on private general aviation aircraft?
Answers
Data recording/capture systems are used to store and record all kinds of aircraft data and usually include onboard recording systems and down-linking data systems.
Onboard recording systems capture and store data on the aircraft itself and can include Flight Data Recorders (FDRs) and Cockpit Voice Recorders (CVRs). FDRs capture data such as airspeed, altitude, and engine parameters, while CVRs capture audio data such as transmissions, conversations, and other sounds inside the cockpit.
Down-linking data systems involve real-time data transmission from the aircraft to a ground station or other aircraft. This data can include data from the FDR and CVR as well as other systems such as GPS and navigation systems.
The value of onboard capture systems is that they store data on the aircraft itself, which allows investigators to access the data in the event of an accident. On the other hand, down-linking data systems provide real-time data transmission from the aircraft and can be used to provide more detailed information about the aircraft’s activities.
This information can be used to monitor the aircraft, provide better situational awareness and provide more insight into the cause of an accident.
Private general aviation aircraft are usually not mandated to have data recording/capture systems due to the cost and complexity of the systems. Additionally, private general aviation aircraft are not typically used in commercial operations and therefore do not require the same level of data recording and monitoring as larger commercial aircraft.
For more questions like Data recording systems click the link below:
https://brainly.com/question/29806749
#SPJ4
in a relational database, what distinguishes an exclusion constraint from a check constraint
Answers
In a relational database, the exclusion constraint is distinguished from a check constraint as follows: An exclusion constraint is used to restrict data from being inserted or updated into a table based on other data that already exists in the table.
The exclusion constraint ensures that a condition is true for any pair of rows in a table, thereby allowing for the exclusion of the table's duplicate or overlapping data. This helps in maintaining the integrity of data within a table. A check constraint is used to ensure that a value entered into a column satisfies a specific condition.
Check constraints are used to guarantee that the data entered into the table follows a specific set of rules or guidelines. Check constraints can also be used to ensure that a certain range of values is entered into a column, that the column's values are of a specific data type, or that the column's values are not null.
You can learn more about relational databases at: brainly.com/question/13262352
#SPJ11
Some studies show that 17% of American students don’t have access to a computer at home, and 18% of American students don’t have internet access. This is sometimes referred to as the “homework gap.” How do you think the homework gap will impact those students and ultimately the world?
Answers
The homework gap is likely to translate to lower literacy levels among those that are disadvantaged.
What is the homework gap?The homework gap refers to the difficulties pupils have doing schoolwork when they do not have access to the internet at home, as opposed to those who do.
Homework is the time students spend outside of the classroom doing assigned assignments to practice, reinforce, or apply newly learned skills and information, as well as to master the abilities required for independent study.
Learn more about homework at:
https://brainly.com/question/29612162
#SPJ1
__________ is used to create a document for multiple recipients.
Answers
What does each row represent?
What distinguishes one record from another?
What should you choose as the primary key for
this table?
Answers
Answer:
I think this is your answer broski.
Explanation:

Answer:
a..c,,c
Explanation:
drop down on edge
What are the flowchart symbols?
Answers
Answer:Flowchart use to represent different types of action and steps in the process.These are known as flowchart symbol.
Explanation:The flowchart symbols are lines and arrows show the step and relations, these are known as flowchart symbol.
Diamond shape: This types of flow chart symbols represent a decision.
Rectangle shape:This types of flow chart symbols represent a process.
Start/End : it represent that start or end point.
Arrows: it represent that representative shapes.
Input/output: it represent that input or output.
which computer can be used where is no electricity ?
Answers
Answer:
mechanical computers
Explanation:
A mechanical computer is built from mechanical components such as levers and gears rather than electronic components. The most common examples are adding machines and mechanical counters, which use the turning of gears to increment output displays.
Answer:
Non-electric computers.
A mechanical computer is a computer built from mechanical components such as levers and gears rather than electronic components
What is a table in Excel?
a worksheet that has conditional formatting rules applied to it
a group of cells with content created by the AutoFill feature
a group of related data without any spaces between cells
the header and footer of an Excel worksheet
Answers
Answer:
c
Explanation:
i got it wrong twice so it gave me the correct answer.
A ________ examines each part of a message and determines whether to let that part pass.
Answers
Answer:
packet-filtering
Explanation:
A packet-filtering firewall examines each part of a message and determines whether to let that part pass.
oof x oof = ? idk what that is
Answers
Answer:
= 1 off!
Explanation:
1x1
Answer:
Double OOF!!!!!!!!
Explanation:
I dont have one....
What is Current interrupt register
Answers
Answer: An interrupt control register, or ICR, is a hardware register in a computer chip used to configure the chip to generate interrupts—to raise a signal on an interrupt line—in response to some event occurring within the chip or a circuit connected to the chip.
Explanation:
You have two Windows Server 2016 computers with the Hyper-V role installed. Both computers have two hard drives, one for the system volume and the other for data. One server, HyperVTest, is going to be used mainly for testing and what-if scenarios, and its data drive is 250 GB. You estimate that you might have 8 or 10 VMs configured on HyperVTest with two or three running at the same time. Each test VM has disk requirements ranging from about 30 GB to 50 GB. The other server, HyperVApp, runs in the data center with production VMs installed. Its data drive is 500 GB. You expect two VMs to run on HyperVApp, each needing about 150 GB to 200 GB of disk space. Both are expected to run fairly disk-intensive applications. Given this environment, describe how you would configure the virtual disks for the VMs on both servers.
Answers
The virtual disk configuration for the VMs on both servers in this environment is shown below.
In the Hyper V Test,
Since there will be two or three virtual machines running at once, each of which needs between 30 and 50 GB of the total 250 GB of disk space available,
What is virtual disks?Setting up 5 virtual disks, each 50 GB in size.
2 VMs each have a 50 GB virtual drive assigned to them.
The above setup was chosen because running three VMs with various virtual disks assigned to them will not pose an issue when two or three VMs are running concurrently and sharing the same virtual disk. This is because the applications are disk-intensive.
To learn more about virtual disks refer to:
https://brainly.com/question/28851994
#SPJ1
Given this environment, the virtual disk configuration for the VMs on both servers is shown below. Because two or three VMs will be running at the same time, and each VM has disk requirements ranging from 30 to 50 GB of total disk space of 250 GB.
What is Hyper V Test?While there are several methods for testing new virtual machine updates, Hyper-V allows desktop administrators to add multiple virtual machines to a single desktop and run tests. The Hyper-V virtualization technology is included in many versions of Windows 10. Hyper-V allows virtualized computer systems to run on top of a physical host. These virtualized systems can be used and managed in the same way that physical computer systems can, despite the fact that they exist in a virtualized and isolated environment. To monitor the utilization of a processor, memory, interface, physical disk, and other hardware, use Performance Monitor (perfmon) on a Hyper-V host and the appropriate counters. On Windows systems, the perfmon utility is widely used for performance troubleshooting.Therefore,
Configuration:
Creating 5 Virtual disks of 50 GB each.
1 virtual disk of 50 GB is assigned to 2 VM.
The above configuration is because since two or three VM will be running at the same time and using the same virtual disk will cause a problem since the applications are disk intensive, running three VMs with different virtual disks assigned to them, will not cause a problem.
For Hyper V App,
Two VM will run at the same time, and the disk requirement is 150 - 200 GB of 500 GB total disk space.
Configuration:
Creating 2 virtual disks of 200 GB each with dynamic Extension and assigning each one to a single VM will do the trick.
Since only two VMs are run here, the disk space can be separated.
To learn more about Hyper V Test, refer to:
https://brainly.com/question/14005847
#SPJ1
help me pleasez thank you!!

Answers
We can fill up the blank spaces as follows:
The process of retrieving data is fetching.The process of storing data is Data storageThe event that a database administrator prevents from happening is BreachThe separator between a table and a column name is periodThe process of duplicating data is called redundancyAnother term for delete is remove or dropHow to fill up the blanksWith a basic understanding of data and computer science, we can fill up the blanks with the right words. In programming, another term that is commonly used in place of deletion is dropping or removing.
Also, it is the duty of most database administrators to prevent a breach from occurring. Duplication is also called redundancy.
Learn more about data breaches here:
https://brainly.com/question/27887082
#SPJ1
Name two sensors which would be used in a burglar alarm system
Answers
1. Passive Infrared Sensor
This sensors type is passive in a way that it doesn't radiate its own energy. Instead, it detects the infrared light radiating from objects. This way, it can detect whenever there's a human or another living being in its field of view.
2. Photoelectric Beams
This is also another type of motion detector, but it doesn't work similarly to the others. For one, it doesn't have a coverage area. It only forms a fence, which triggers the alarm if broken.
It consists of two separate parts that form a sort of a fence made of IR beams. When someone steps into the beams, between the two parts, they trigger the alarm.
How electrical current manifests itself?
Thermal
Mechanic
Magnetic
Radiation (electromagnetic)
All listed
Answers
Answer:
Mechianic
Explanation:
How would you define a cloud today?
as a non-factor
networking
server
any remote virtualized computing infrastructure
Answers
Answer:
The answer is "any remote virtualized computing infrastructure".
Explanation:
The term cloud is used as the symbol of the internet because cloud computing is some kind of internet computing, that offers various services for computers and phones in organizations via the internet.
The virtual network allows users to share numerous system resources throughout the network system.It allows you to access the optimal productivity by sharing the resources of a single physical computer on many virtual servers.Is it possible to increase the number of threads within processes without affecting the average
response time of this operating system?
Answers
A process may essentially carry out more tasks at once when the number of threads inside the process is increased. This can shorten the amount of time it takes to do a group of activities, which can enhance the
The performance of software systems can be enhanced by increasing the number of threads within processes. We can shorten the amount of time it takes to do a set of activities by enabling a process to carry out more tasks concurrently. This may lead to quicker processing times and increased system throughput as a whole. The effect of adding more threads on system performance must be carefully considered, though. Increasing the number of threads may not yield noticeable performance gains if the tasks being carried out are not CPU-bound. However, if the system's resources are constrained, adding more threads may actually reduce performance owing to resource competition. increased.
Learn more about increased here:
https://brainly.com/question/20344082
#SPJ4
after class your professor tells you his office hours for the week so you can come by with questions. you don't have your phone or paper/pen, so you try to rehearse the days and times until you can write it down. what are you using and how much info do can you hold?
Answers
Answer: your mind
Explanation: The human brain contains billions of neurons, each forming thousands of connections. A single byte comprises 8 bits, and the human brain can store more than one quadrillion bytes of data – a petabyte.
What hashing algorithm does bitcoin use to hash blocks?.
Answers
Bitcoin uses SHA-256 (Secure Hash Algorithm 256 bit) hashing algorithm to hash blocks. This is the same hashing algorithm used in the creation of SSL certificates and for verification of digital signatures.
What is hashing?Hashing is the process of converting data of any size to a smaller size, known as hash. The hash is a fixed size output which is unique for a specific input. Hashing helps to maintain the integrity of data and make it more secure. Once a hash is created, it is practically impossible to revert the data from the hash.How does SHA-256 work?SHA-256 is a cryptographic hashing algorithm which generates a fixed 256-bit hash output from any input message.
It is a one-way function, which means once the hash is created, it is impossible to retrieve the original data. It is a complex mathematical algorithm which involves a series of logical operations. The output hash generated by SHA-256 is unique for a specific input. Any minor change in the input results in a completely different hash output. SHA-256 is used in the creation of digital signatures, SSL certificates, and in the Bitcoin network for verification of blocks.
To know more about algorithm visit:
https://brainly.com/question/28724722
#SPJ11
Critical thinking skills can be applied to reading.
Please select the best answer from the choices provided
T
F
Answers
Critical thinking means that you do not just accept what an author presents. By reading critically, you read skeptically, questioning the author against your own knowledge and your own world view. Sometimes your ideas will align with an author's.
Answer:
Explanation:
hello i know the answe and the anwer is TRUE
The arp protocol is used to determine what address of a node when what address is known?
Answers
The arp protocol is used to determine address of a node when what address is known ARP cache
Address resolution protocol is used to mapping the system address to the internet protocol address. The address resolution protocol is used to translate a system address into an IP address.
In a local area network, the Address Resolution Protocol (ARP) converts a dynamic IP address to a fixed physical machine address (LAN). A media access control (MAC) address is another name for the actual machine address.
The Domain Name System (DNS), an Internet directory service created to both allow local administrators to create and manage the records that resolve server names to IP addresses and to make those records accessible, is the method most frequently used in the TCP/IP protocol to resolve server names to network addresses.
Learn more about ARP:
https://brainly.com/question/12976506
#SPJ4
7.2 code practice edhesive. I need help!!
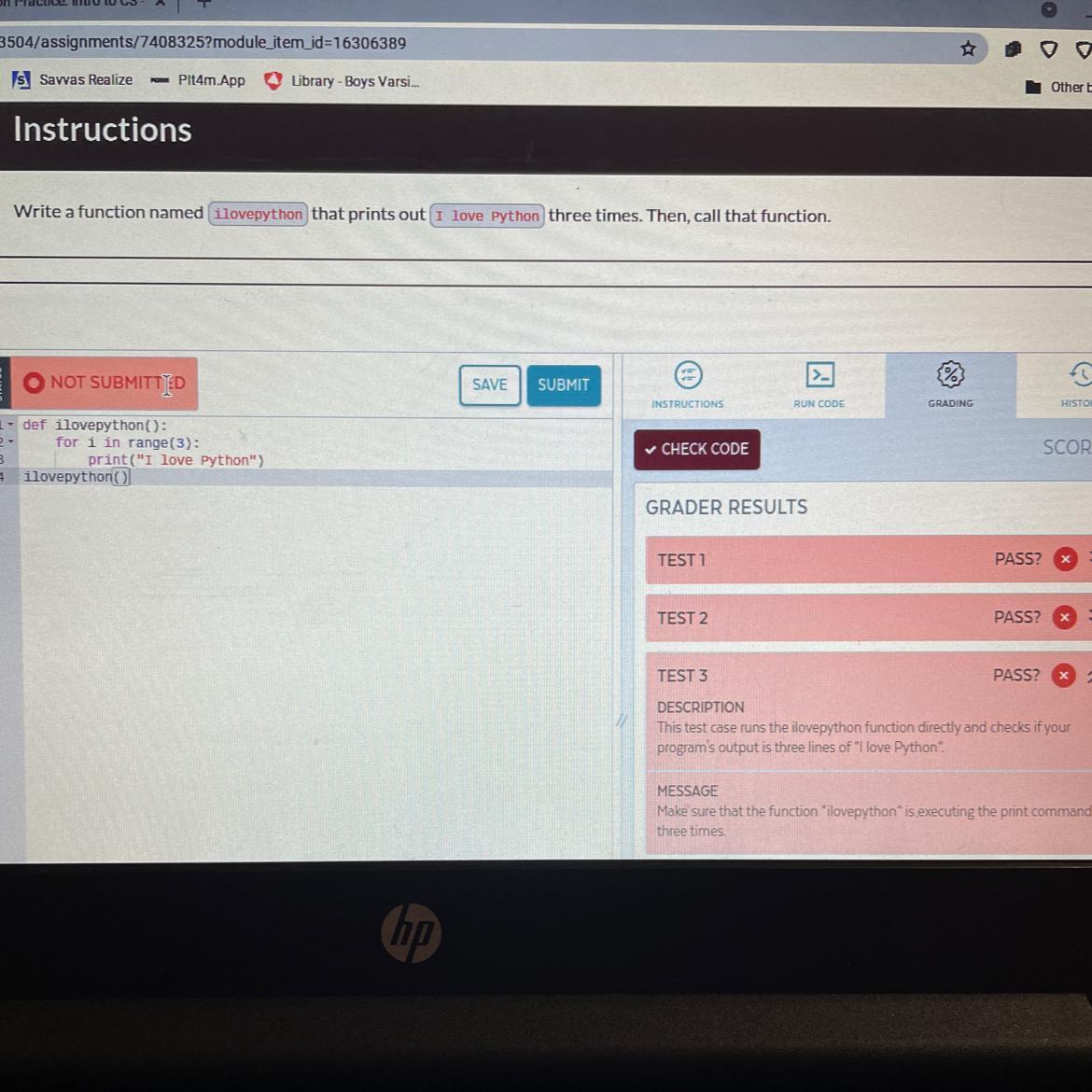
Answers
Answer:
It already looks right so I don't know why it's not working but try it this way?
Explanation:
def ilovepython():
for i in range(1, 4):
print("I love Python")
ilovepython()
if your mission critical services have a maximum tolerable downtime
Answers
If your mission-critical services have a maximum tolerable downtime, it means that there is a limit on how long those services can be down without causing significant harm to the organization.
The maximum tolerable downtime (MTD) is a measure of how much time an organization can afford to have its critical services offline. The MTD is determined by the business impact analysis (BIA), which identifies the critical services that are essential to the organization's operations and calculates the impact of their failure. The MTD is based on a variety of factors, including financial impact, reputational damage, regulatory compliance, and safety risks.
For example, a hospital's MTD for its electronic health records (EHR) system may be 30 minutes because a longer downtime could impact patient care and safety. In contrast, an e-commerce site's MTD for its shopping cart feature may be several hours because it would have a lower impact on customer satisfaction and revenue.
MTD is an essential metric in business continuity planning because it helps organizations prioritize their recovery efforts and allocate resources effectively to minimize downtime and minimize the impact of service failures on their operations and stakeholders.
Know more about maximum tolerable downtime here:
https://brainly.com/question/30812901
#SPJ11
Write a for loop that prints countnum. -1 0. ex: if the input is: -3 the output is: -3 -2 -1 0 c program
Answers
This for loop is given below that starts at the value of countnum and continues until i is less than or equal to 0. In each iteration, it prints the value of i, followed by a space. So if countnum is -3, the loop will print -3 -2 -1 0.
for(int i = countnum; i <= 0; i++) {
printf("%d ", i);
}
Explanation:
The C program that uses a for loop to print the numbers from countnum down to 0:
#include <stdio.h>
int main() {
int countnum;
printf("Enter a number: ");
scanf("%d", &countnum);
for(int i = countnum; i <= 0; i++) {
printf("%d ", i);
}
printf("\n");
return 0;
}
The program first prompts the user to enter a number, which is stored in the countnum variable using scanf. Then, the for loop initializes the variable i to countnum and continues looping as long as i is less than or equal to 0. On each iteration of the loop, the program prints the value of i followed by a space using printf. Finally, the program prints a newline character to move the cursor to the next line.
To know more about the for loop click here:
https://brainly.com/question/30494342
#SPJ11
The process of increasing the length of a metal bar at the expense of its thickness is called
Answers
The process of increasing the length of a metal bar at the expense of its thickness is called drawing out.
The technique of growing the duration of a metallic bar at the rate of its thickness is known as "drawing out" or "elongation." Drawing out entails applying tensile forces to the steel bar, causing it to stretch and end up longer even as simultaneously reducing its move-sectional location.
During this technique, the steel bar is normally clamped at one give up at the same time as a pulling pressure is carried out to the other give up. As the force is exerted, the metal undergoes plastic deformation and elongates. This outcomes in a decrease in the bar's thickness, because the material redistributes alongside its duration.
Drawing out is normally utilized in various manufacturing strategies, which includes wire manufacturing, where a thick steel rod is drawn through a sequence of dies to gradually lessen its diameter whilst increasing its period. This elongation process can enhance the mechanical properties of the metallic, inclusive of its power and ductility, whilst accomplishing the desired dimensions for specific programs.
Read more about elongation at:
https://brainly.com/question/29557461
James wants to buy a pair of pants for $60.
When he went to the store he found that the
price was marked down by 20%. How much do
they cost now?