What does a computer program use as a means to evaluate a condition as True or False?
a Boolean expression
a Boolean string
a Boolean variable
a Boolean operator
Answers
Answer:You use the boolean question type when you want to allow your respondents to switch something on or off
Explanation: cause i serched it on google
Reason: A Boolean is a true or false statement. A Boolean expression is an expression that looks at condition and determines it as true or false.
Think of a Boolean as literally a true or false statement. Ex: Does the value equal 5, answer Yes/No.
I hope this helps you.
Related Questions
I need help with yes lol please and thank you

Answers
Answer:
I think you have the right answer because it is the most self-explanitory
Explanation:
Digital and analog audio recordings have pros and cons. Do you think the pros of digital recordings outweigh the cons and therefore prefer digital audio recordings? Or, do you think the cons outweigh the pros and therefore you prefer analog audio recordings? Explain. ( USE C.E.R *Claim, Evidence, Reasoning* )
Answers
I think the pros of digital recordings outweigh the cons! I prefer digital audio recordings over analog audio recordings because analog recordings require more financing and preservation. Compared to digital recordings, analog recording equipment is more expensive and the tape deteriorates over time. Which to me personally, doesn't seem to be worth the amount of effort since it's such a process to go through. You can possibly go into debt due to that. Digital recording equipment, on the other hand, is more affordable. It's less time-consuming and although it does have its disadvantages, they're minor. Digital recordings can be stored online. Its data get corrupted? You can get it back! It won't cost you anything.
Help me! I'm timed!!!

Answers
1. Why is it important to know how to create a slide?
2. How can you utilize the knowledge in making a slide as a student?
in own sentence pls
Answers
2. As a student, knowing how to create a slide can be beneficial for presenting research findings, summarizing key information, and organizing study materials in a clear and visually appealing way to aid in the learning process.
Answer:
1. Because slides help in improving visual aids. It improves understanding when teaching student.
2. You can make projects, shows, teach others, and play with it just for fun
Explanation:
REAL ANSWERS ONLY!!! BRAINLLIEST AND 50 POINTS FOR BEST ANSWER

Answers
2-Photographs allow people to see visual evidence of events, view nature in artistic ways, and tell stories with little to no words.
3-Successful photojournalists need to understand that the point of photography is to tell a story in an interesting way that will entertain and draw viewers in.
4-Photography connects people all around the world. A large group of people could view the same photo, and evaluate it in a number of different ways. These people can converse and tell each other about what they can take from the photo, and how their perspectives change the meaning of the photo.
The two that I didn't answer were up to your own opinion, so I'll let you try to figure them out yourself with the information that I gave you. :)
In a minimum of 250 words, discuss the technological problems that can occur when consumers emphasize on speed over security.
Answers
1. Vulnerabilities and Breaches: Emphasizing speed often means sacrificing robust security measures. This can lead to vulnerabilities in software, applications, or systems that attackers can exploit. Without adequate security measures, data breaches become more likely, exposing sensitive information such as personal data, financial records, or trade secrets. The aftermath of a breach can be detrimental, including reputational damage, legal consequences, and financial losses.
2. Malware and Phishing Attacks: When speed takes precedence, consumers may overlook potential malware or phishing attacks. By rushing through security checks or bypassing cautionary measures, they inadvertently expose themselves to malicious software or fraudulent schemes. These attacks can compromise personal information, hijack devices, or gain unauthorized access to networks, resulting in financial losses and privacy violations.
3. Inadequate Authentication and Authorization: Speed-centric approaches might lead to weak or simplified authentication and authorization mechanisms. For instance, consumers may choose easy-to-guess passwords or reuse them across multiple platforms, making it easier for attackers to gain unauthorized access. Additionally, authorization processes may be rushed, granting excessive privileges or overlooking necessary access controls, creating opportunities for unauthorized users to exploit system vulnerabilities.
4. Neglected Updates and Patches: Prioritizing speed often means neglecting regular updates and patches for software and systems. By delaying or avoiding updates, consumers miss out on critical security fixes and vulnerability patches. Hackers actively exploit known vulnerabilities, and without timely updates, devices and systems remain exposed to these threats, making them easy targets.
5. Lack of Secure Development Practices: When speed becomes the primary concern, secure development practices might take a backseat. Security testing, code reviews, and quality assurance measures may be rushed or ignored, leading to the inclusion of vulnerabilities in the software or application itself. These vulnerabilities can be exploited by attackers to gain unauthorized access or execute malicious activities.
To mitigate these problems, it is essential to strike a balance between speed and security. Consumers should prioritize security measures such as using strong passwords, enabling multi-factor authentication, regularly updating software, and being cautious of suspicious links or emails. Service providers and developers must also prioritize security in their products and services by implementing secure coding practices, conducting thorough security assessments, and promptly addressing vulnerabilities. Ultimately, a comprehensive approach that values both speed and security is crucial for maintaining a safe and efficient technological ecosystem.
Explanation:
--> used brainly simplify :D
Consumers prioritizing speed over security can lead to several technological problems. This includes vulnerabilities and breaches where attackers can exploit weaknesses in software or systems. Malware and phishing attacks become more likely when security measures are overlooked. Weak or simplified authentication and authorization methods can make it easier for unauthorized users to gain access. Neglecting updates and patches leaves devices and systems vulnerable to known threats. Lastly, rushing through secure development practices may result in the inclusion of vulnerabilities in the software itself. To address these issues, consumers should use strong passwords, update their software regularly, and be cautious of suspicious links or emails. Service providers and developers should prioritize security by conducting thorough security assessments and promptly addressing vulnerabilities. Striking a balance between speed and security is crucial for a safe and efficient technological environment.
Which type of cyber crime offender requires the highest percentage of risk management in terms of computer monitoring?
A) Sex offenders
B) Identity thieves
C) Low-Risk offenders
D) hackers
Answers
Answer: D
Explanation: Hackers are the only type of cyber criminal that monitors your computer
An example of how a merge code would appear in a letter would be _____.
Answers
Answer:
Space blank
Explanation:
It means the question needs you to answer the question
Answer:
An example of how a merge code would appear in a letter would be C i.e. /University_Name/. Explanation: Merge codes help speed up the method of making letters by inserting data into your letters.
Explanation:
I hope this helps
Jackie is planning a birthday party for her little brother and is researching different trampoline parks. She receives a pop-up asking for her name, address, and date of birth so she can receive a special promotion from the trampoline park. What should Jackie do?
a
Ignore the request and not enter any personal information.
b
Provide only her name and date of birth.
c
Provide only her name and address.
d
Provide the requested information to receive the discount.
Answers
Answer:
a
Explanation:
sis is gonna get scammed
Answer:
a
Explanation:
You dont know who is getting your information and it is not someone you know. STRANGER DANGER!
Walt needs to ensure that messages from a colleague in another organization are never incorrectly identified as spam. What should he do?
A.Configure a safe recipient.
B.Configure a blocked sender.
C.Configure a safe sender.
D.Do nothing.
Answers
Answer:
C. Configure a safe sender
Explanation:
It’s dabest thing to do
As per the given scenario, Walt should need to configure a safe sender. The correct option is C.
What is configuration?A system's configuration in communications or computer systems refers to how each of its functional elements is organised in relation to their nature, number, and distinguishing features.
Configuration frequently involves picking the right hardware, software, firmware, and documentation.
A person, group, or organisation that starts the communication is known as the sender. The success of the message stems primarily from this source.
The communication is influenced by the sender's experiences, attitudes, knowledge, competence, perspectives, and culture.
Walt must take care to prevent messages from a colleague in a different organisation from ever being mistakenly classified as spam. He ought to set up a secure sender.
Thus the correct option is C.
For more details regarding configuration, visit:
https://brainly.com/question/13410673
#SPJ2
I will take a screenshot and then put it as an attachment

Answers
Answer:
ok
Explanation:
I dont know
When using correct ergonomic technique be sure to _____.
(A.)Position your wrists so they are angle up while typing.
(B.)Keep your arms comfortable at your side forming a 90° angle with your upper arms.
(C.)Position the keyboard three feet in front of you so that you stretch for the keys.
(D.)Adjust the keyboard height so that your shoulders are stiff and your arms are away from your sides.
Answers
Answer: The answer is C
Answer:
I think The answer is c
Explanation:
Its the most comfertable way to use ergonomic technique
(I made this up teehee) what anime is katski bakugo from
Answers
!!!!PLEASE HELP!!!!! You get to play journalist today. The topic of your story is one of the laws discussed in this lesson. You will select one of them to research. While researching, you will learn more about the law and will locate a case that went to court. Then you will write an unbiased article or broadcast describing the law and summarize the case and the stand of the parties involved. Be sure to review and abide by The Cannons of Journalism. Be sure to include:
a description of the law;
how the law relates to digital media;
one example of a case that went to court;
a discussion of the case and the parties involved; and
a summary of the outcome of the case.
Some helpful hints in finding a case are:
Search for “case law,” “court case examples,” and “case studies.”
Include the full name of the law and the acronym.
Discuss the impact these laws have on one or more media outlets in your community.
You will write your report as an article with at least 500 words that will be posted on an online news site or that a broadcast journalist will report on TV news.
Upload your 500-word story that describes one law, including how it relates to digital media, and summarizes a case that went to the courts and the stand of the parties involved.
Answers
Title: The Digital Privacy Act: Safeguarding Personal Information in the Digital Age
Date: [Insert Date]
Byline: [Your Name]
[City Name] - In an era of rapidly advancing technology and widespread digital connectivity, protecting personal information has become a paramount concern. The Digital Privacy Act, a legislation introduced to address these concerns, aims to safeguard individuals' privacy rights and regulate the handling of personal data in the digital realm.
The Digital Privacy Act, formally known as the Personal Information Protection and Electronic Documents Act (PIPEDA), was enacted in [Insert Year]. This federal law governs how private sector organizations collect, use, and disclose personal information in the course of commercial activities. It establishes rules and principles for obtaining consent, ensuring transparency, and safeguarding personal data from unauthorized access or disclosure.
In the realm of digital media, the Digital Privacy Act plays a crucial role in governing the practices of online platforms, social media networks, and e-commerce websites. It requires organizations to obtain informed consent when collecting personal information, inform individuals of the purpose for its collection, and implement appropriate security measures to protect sensitive data from breaches or unauthorized use.
One prominent case that exemplifies the intersection of the Digital Privacy Act and digital media is the landmark lawsuit of Doe v. SocialMediaCo. In this case, Jane Doe, a user of a popular social media platform, filed a complaint against the company for unauthorized disclosure of her personal information.
According to court documents, the plaintiff alleged that SocialMediaCo, without her consent, shared her private messages with third-party advertisers, resulting in a breach of her privacy. The case brought into focus the importance of user consent and the responsibility of online platforms in protecting personal information.
During the trial, the plaintiff argued that the actions of SocialMediaCo violated the provisions of the Digital Privacy Act. She contended that the company failed to obtain proper consent and did not adequately safeguard her personal data, leading to emotional distress and reputational harm.
On the other hand, SocialMediaCo maintained that their practices were in compliance with the Digital Privacy Act. They argued that users implicitly consented to the sharing of their information with third-party advertisers through the platform's terms of service agreement.
After careful deliberation, the court ruled in favor of Jane Doe, emphasizing the importance of explicit consent and the duty of organizations to protect user privacy. The court found SocialMediaCo liable for the unauthorized disclosure of personal information and awarded damages to the plaintiff.
The outcome of the case set a precedent for other digital media companies, reinforcing the need for stringent privacy practices and ensuring compliance with the Digital Privacy Act. It also served as a reminder to individuals about the importance of understanding privacy policies and exercising caution when sharing personal information online.
As we navigate the digital landscape, the Digital Privacy Act stands as a crucial safeguard, protecting individuals from the potential risks associated with the collection and use of personal data. It places the responsibility on organizations to respect privacy rights, obtain informed consent, and prioritize the security of sensitive information.
In an ever-evolving digital world, the Digital Privacy Act serves as a shield, empowering individuals to assert their rights and reinforcing the notion that personal information deserves protection, both offline and online.
I hope this helps. Cheers! ^^
explain the history of computing of mechanical era
Answers
Answer:The Mechanical Era
Created a machine that could add and subtract numbers. Dials were used to enter the numbers. ... Designed a machine called the Analytical Engine. The design had all the basic components of a modern day computer. In addition, it was designed to be programmable using punched cards.
Explanation:Hope this helped
How do I find/search for someone???
I've been looking forever. Please help!!!
Answers
Answer:
if you have seen their profile before and know their name, search their name in your history, or if you know someone who is friended them and your friends with them, then look at your friends, friends list and they should be there, or if they have commented and or answered somewhere you have been, you can search there.
Explanation:
List at least one thing to check for when you're checking the clarity and professionalism of a document.
Answers
Answer:
Company Style. Verify that the tone and style of the document matches the document type and purpose. ...
Format Review. ...
Grammar and Spelling. ...
Layout Critique. ...
Confirm Accuracy. ...
Answer:
1. Read the cover letter to make sure it's specific, professional, and clear.
2. If you see anything you'd like to change, do that now. Edge 2022
Explanation:
Trust my doppelganger
When the prompt function is used in JavaScript, _____ appears.
A.
an error message
B.
a pop-up box
C.
a data warning
D.
a password request
Answers
Answer:
B
Explanation:
instructs the browser to display a dialog with an optional message prompting the user to input some text, and to wait until the user either submits the text or cancels the dialog
public class Main {
public static void main(String[] args) {
String firstName = "John ";
String lastName = "Doe";
String fullName = firstName + lastName;
System.out.println(fullName);
}
}
From this example copy and paste code that when run would say your name. in javascript with my first name being Ryan and my last name being Smith
Answers
Answer:
const firstName = "Ryan ";
const lastName = "Smith";
const fullName = firstName + lastName;
console.log(fullName);
Explanation:
public static void main(String[] args) {
String firstName = "Ryan";
String lastName = "Smith";
String fullName = firstName + lastName;
System.out.println(fullName);
}
reasons phone doesnt charge
Answers
Here are 5 reasons possibly why:
1.) Faulty lightning or micro USB port
2.) The lightning or USB port could be dirty
3.) Damaged charging port or cable
4.) Water Damage
5.) Software problems
Write the importance of software in computer . In 6 points
Answers
Answer:
Software is a set of instructions, data or programs used to operate computers and execute important tasks but can also help you work more efficiently.
Uses of Software
Uses of Software in Office.Uses of Software in Business.Uses of Software for Play Game.Uses of Software in Shop.Uses of Software for Entertainment.Explanation:
A large company has extensive downtown office space with many conference rooms. To lower their electric bill, the company has installed a new system that automatically turns off the heat and lights in a conference room when no one is in the room. What is the simplest explanation for how the system works?
A camera in each room is connected to the security desk. When the officer on duty sees that a room is empty, they turn off the heat and lights in that room.
A small robotic device on wheels knows the building layout. It roams the offices, peeking into each conference room to see if anyone is using it. If not, the robot turns off the lights and heat.
A sensor detects and reports on movement in the room. If there is no movement for a few minutes, the system assumes the room is empty and turns off the heat and lights.
Every hour, the system emits a loud sound in each room. Pressing a large red button in the middle of the table turns off the sound in that room. If nobody does so within 30 seconds, the system turns off the heat and lights.
Answers
The simplest explanation for how the system works is option C: a sensor detects and reports on movement in the conference room. If there is no movement for a few minutes, the system assumes the room is empty and turns off the heat and lights.
What is the office space about?The system that automatically turns off the heat and lights in a conference room when no one is in the room is commonly referred to as an occupancy sensor. An occupancy sensor uses various technologies, such as infrared or ultrasonic, to detect the presence or absence of people in a room.
Therefore, Once the sensor detects that no one is in the conference room, it sends a signal to the control system, which then turns off the heat and lights. When someone enters the room again, the sensor detects their presence and sends a signal to turn the heat and lights back on. This system is designed to save energy by ensuring that heating and lighting are only used when needed.
Learn more about office space from
https://brainly.com/question/28885269
#SPJ1
1. What do you think is the most important event in the history of the internet? What event has had the biggest impact on your daily life?
Answers
Answer:
The biggest event in internet history was YuTubers punching each other in the face. Months of hype came to a peak Saturday for the self-declared “biggest event in internet history” a boxing match between two YuTube celebrities in Manchester, England.
Explanation:
There is no particular event but the whole journey till now which shaped my personality. Every person even if they are the worst has something good in them.
The impact it has had:
Developed into the globally used Internet which is now integrated into modern society and is seen as an essential for good quality of life.
How do I bypass blocksi on my school Chromebook

Answers
Answer:
Open Chrome Settings.
Click on the “Privacy”
Under “Content restrictions,” click on the “Block sites” button.
Enter the website address in the “URL” box and click on the “Add site” button.
Explanation:
you could power wash/reset your computer then delete the blocking site
_____ describes the layout of the screen. Block-based, Interface, Editor, Player
Answers
GUYS THERE IS A HACKER IN BRAINLY PLEASE DONT PRESS ON THE WEBSITE THEY WILL HACK YOU.
Answers
yeah ive seen them :( they are files and if you download them you will get a virus or your ip taken so please watch out !!
Answer:
Ok noted
Explanation:
Using AI to predict future crimes might be considered
bias
fair
helpful
smart
Answers
Answer:
helpful
Explanation:
Answer:
I think using Al to predict future crimes might be considered HELPFUL
Refer to the article “The Future of Money” in your Money, Money, Money magazine for a complete version of this text. What is the overall structure of the “Digital Money” and the “No More Go-Betweens” sections of “The Future of Money” article? [BRAINLIEST!!!]
Answers
Money covers three functions:
unit of account since it measures in numeric values what goods and services are worth.
store of value which implies accumulating money increases individuals' and organizations' wealth;
and, medium of exchange because it facilitates transactions between buyers and sellers through a common currency accepted by the two of them.
Remi would like to write a paper about the biggest roller coaster. Before he begins to write he should research amusement parks so he is able to make an
advised decision
informed opinion
informed outcome
uninformed opinion
Answers
Answer:
Informed Outcome
Explanation:
The reason being, assuming he is taking measurements and not just guessing based off of what he likes best it would be an informed outcome.
Informed outcome
i need help someone plz i need it fast ..........
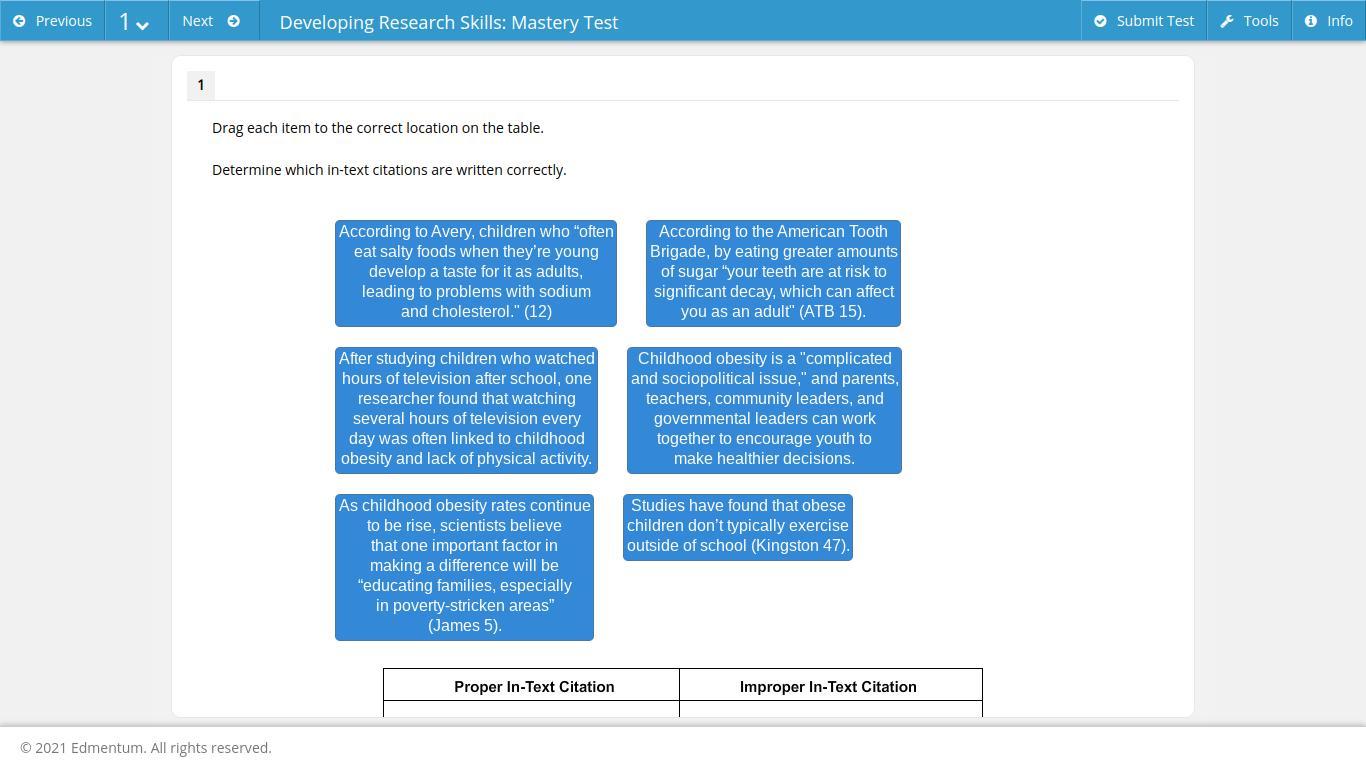
Answers
Answer:
Do you still need help??
Explanation: