what bit rate is possible when an oc-1 is carrying a ds-3 signal?
Answers
The bit rate possible, when an OC-1 is carrying a DS-3 signal, depends on the encoding scheme used. With CBP encoding, the possible bit rate is 44.236 Mbps.
When an OC-1 is carrying a DS-3 signal, the possible bit rate depends on the encoding scheme used. A DS-3 signal has a data rate of 44.736 Mbps, while an OC-1 has a data rate of 51.84 Mbps. However, when a DS-3 signal is carried over an OC-1, some overhead is introduced due to the framing structure used in SONET/SDH networks. This overhead includes the transport overhead, path overhead, and section overhead.
The most commonly used encoding scheme for carrying a DS-3 signal over an OC-1 is the C-Bit Parity (CBP) scheme. With CBP encoding, the DS-3 signal is mapped into a 44.236 Mbps payload, leaving 7.504 Mbps for overhead. This overhead includes the SONET/SDH framing and other necessary overhead. Therefore, the possible bit rate when an OC-1 is carrying a DS-3 signal with CBP encoding is 44.236 Mbps.
You can learn more about bit rate at: brainly.com/question/31434111
#SPJ11
Related Questions
Understanding the logic and processes computers use to solve problems and run programs is known as:_________
Answers
Answer:
Computational Thinking
Explanation:
One of the distinguishing characteristics of computer-based fraud is that access occurs ________________________. A. Through the Dark Web where the value of the stolen funds can be stored on hidden servers B. In violation of computer internal controls whether by management override or other means C. With the intent to execute a fraudulent scheme or financial criminal act D. When a hacker or virus successfully bypasses the firewall protecting financial data
Answers
Answer:
Option A, Through the Dark Web where the value of the stolen funds can be stored on hidden servers
Explanation:
Content that is available on dark web can not be detected by search engines specially through the traditional browsers or standard browsing technology. Along with that it has tens of thousands of sites and at a time only certain limited number of sites are available.
Money related frauds are basically driven by this dark web. Criminal enterprises determine personal details through various means and hence can derive your credentials and financial details. The criminal portions of the dark web makes trade in fraudulent information easy and accessible
Hence, option A is correct
What is meant by Paradigm programming?
Answers
Answer:
a way to classify programming languages based on their features
Explain LCD and give two example
Answers
Answer:
LCD means least common denominator• a "Common Denominator" is when the bottom number is the same for the fractions.
Explanation:
Answer:
least common denominator.
explain what information sources are used for the data and documentation that they use in their work activities
Answers
An information source is a source of knowledge for someone, meaning it can be anything that can educate someone on a topic.
Information can come from a variety of sources, including observations, speeches, records, images, and organizations. Sources of data or proof are frequently divided into primary, secondary, or tertiary categories. These divisions are based on the degree of originality and proximity to the source or origin of the information. Original works are considered primary sources, studies of those original works are considered secondary sources, and collections of secondary source data are considered tertiary sources. Professionals in academia, science, and business employ a combination of all three sorts of sources.
Learn more about information here-
https://brainly.com/question/16759822
#SPJ4
Ceteris paribus, if a student could either earn money tutoring or working as a server in a restaurant, then increases to the wages paid for serving will
Answers
If a student could either earn money tutoring, then increases to the wages paid for serving will Increase the quantity of hours the student would serve.
What is ceteris paribus?This is a term that connotes when all other things being equal. The word Ceteris paribus is known to be a Latin phrase that totally means "all other things being equal."
In economics, it is known to be a shorthand factor that shows the effect one economic variable is said to have on another, given that all other variables remain the same as in the case above.
See options below
A. increase the quantity of hours the student would serve.
B. decrease the quantity of hours the student would serve.
C. increase the quantity of hours the student would tutor.
D.not change the quantity of hours the student would serve.
Learn more about Ceteris paribus from
https://brainly.com/question/868746
Which of the following are NOT possible using the RANDOM(a, b) and DISPLAY(expression) abstractions?
DISPLAY(RANDOM(3,6) + RANDOM(4,5))
Answers
Using the RANDOM(a, b) and DISPLAY(expression) abstractions, the expression DISPLAY(RANDOM(1, 4) + RANDOM(2, 5)) is not possible to evaluate to 9.
Thus, option B is correct.
Let's break it down:
RANDOM(1, 4) can generate random numbers from 1 to 4 (inclusive). RANDOM(2, 5) can generate random numbers from 2 to 5 (inclusive).The maximum value that can be generated by RANDOM(1, 4) is 4, and the maximum value that can be generated by RANDOM(2, 5) is 5.
So, the sum of these two maximum values is 4 + 5 = 9.
Since the maximum value of the expression RANDOM(1, 4) + RANDOM(2, 5) is 9, it is not possible for the result to be greater than 9.
Thus, option B is correct.
Learn more about Abstraction here:
https://brainly.com/question/30626835
#SPJ6
Edhesive Intro to cs quiz 2 q#9
What is output?
Print (3 % 15)
Thanks!!

Answers
Answer:
5
Explanation:
AS we know that % is the sign of division in C language when we divide the 3 into 15 its 5
Answer:
5
Explanation:
Let x = ["Red", 2.55,"Green", 3,"Black","false"], then solve the following:
1. The output of print(x) is
2. The output of print(len(x)) is
3. The output of print(x[10]) is
4. The output of print(x[1]+x[3]) is
Answers
Answer:
Print(x) would be directly calling the x variable so it would print everything but the []Print(x[10]) is calling the number 10 which results in E2 + d= 2dResearch and describe plug-ins and their usage in graphic design.
Answers
Answer:
Plug-ins are software developed to work with another software that is already installed in the computer. They are basically add-on software that enhance a functionality of an existing software. These plug-ins can be used for different purposes based on which software they support. There can be plug-ins for search engines, audio-video players, photo-editing software, graphical design software, and more.
Plug-ins may be developed by the same company which developed the software that the plug-in is supposed to work with. It may also be developed by independent developers who just want to solve or add an element to the existing features of a software.
Plug-ins are mostly free and are released after the target software is tested and released.
Plug-ins offer a lot of assistance in graphical design. It works with the design software for adding or enhancing affects and styles to the original work. Some of the functions that popular plug-in software provide are:
• to improve color, sharpness, and focus (perspective) of the images
• to create (and enhance) natural lighting effects within the image
• to sharpen or define (emphasize) particular parts of the image
• create motion blur
• change point-of-focus of the image
• alter the level of opacity of brushes
• alter the size of brush strokes (different from the ones that already exist)
• Control and enhance the intensity of dark areas in an image
• eliminate distortion due to camera shake
• create metallic edges for elements in the image
• introduce mood and blended contrast effects
Explanation:
This is what it said when I submitted my answer
what is output if the user types 13 click all that apply ABCD

Answers
Answer:
AD?
Explanation:
Answer:
A C D
Explanation:
youre welcome :)
While innovation undoubtedly makes life easier for many, it may also leave some people jobless. In the context of this interview, what are the costs and benefits of technology? Cite evidence from this text, your own experience, and other literature, art, or history in your answer.
Answers
Answer:
I do not see a text to cite evidence from, but you can use this response to incorporate evidence from your text and incorporate YOUR own experience as directed by the prompt.
Here:
Technology has both costs and benefits, as evident in art, literature, and history. One cost is the potential job displacement caused by automation and artificial intelligence. Aldous Huxley's "Brave New World" depicts a future where technology eliminates certain roles, leading to a loss of individuality. However, technology also brings substantial benefits, enhancing communication and efficiency. Jules Verne's "Twenty Thousand Leagues Under the Sea" explores the wonders of submarine technology, showcasing new frontiers and opportunities. Throughout history, technological advancements, like those during the Industrial Revolution, have transformed societies, bringing both improvements and challenges. Artists like William Turner captured the awe and disruption of these developments. Considering the duality of technology's impact is crucial for a balanced and inclusive future with technological progress.
Explanation:
1.printer is an example of......... device.
Answers
Printer is an example of output devise.It gives hard copy output on paper .
1. Printer is an example of output device.
I hope it's help you...
each row in the relational table is known as an ? a. entity set b. entity occurrence c. entity tuple d. entity relation
Answers
A table is a group of data organized in columns and rows. Tables in a relational database should be normalized, which means they should be designed to minimize data redundancy and prevent data inconsistency.
The primary key of a table is a special column that identifies each row in that table uniquely. Each table must have a primary key, and it must be unique for each row in the table.Each column in a table corresponds to an attribute. An attribute is a property of the entity represented by the table. For example, if the table represents customer information, the attributes can be customer name, address, email, phone number, etc. In a table, each row represents an entity tuple. An entity tuple is a unique set of attribute values for a specific entity instance. For example, if the table represents customers, each row in the table represents a unique customer. In addition to tables, relational databases use other structures such as indexes, views, and stored procedures. Views and stored procedures are pre-written SQL statements that allow database administrators and developers to customize the data they retrieve from tables. They can be used to limit the number of columns that are returned or to join tables together to generate complex queries.for more such question on relational
https://brainly.com/question/13262352
#SPJ11
Pls help xD. In pseudocode or python code please. Will mark best answer brainliest. Thx

Answers
Answer:
I'm doing my best to send you my answer,
Explanation:
The coding will be below
A user with "edit" permissions at the Account level will automatically have "edit" permissions at which other levels?
Answers
Answer:
Property and View.
Explanation:
An access control can be defined as a security technique use for determining whether an individual has the minimum requirements or credentials to access or view resources on a computer by ensuring that they are who they claim to be.
Simply stated, access control is the process of verifying the identity of an individual or electronic device. Authentication work based on the principle (framework) of matching an incoming request from a user or electronic device to a set of uniquely defined credentials.
Basically, authentication and authorization is used in access control, to ensure a user is truly who he or she claims to be, as well as confirm that an electronic device is valid through the process of verification. Thus, an access control list primarily is composed of a set of permissions and operations associated with a NTFS file such as full control, read only, write, read and execute and modify.
Hence, a user with "edit" permissions at the Account level will automatically have "edit" permissions at the Property and View levels.
if Z=52 and ACT=48 then BAT= with explanation??
Answers
So, ACT = 2 + 6 + 40 = 48 and
BAT = 4 + 2 + 40 = 46
Anne creates a web page and loads a CSS style script along with the page. However, the entire page appears black and she cannot see any of the
text she has entered. What is the possible could be causing this issue?
Answers
Answer: B. "She might have set backround-color in body to black in the CSS file"
Explanation: I took the test and got 100%
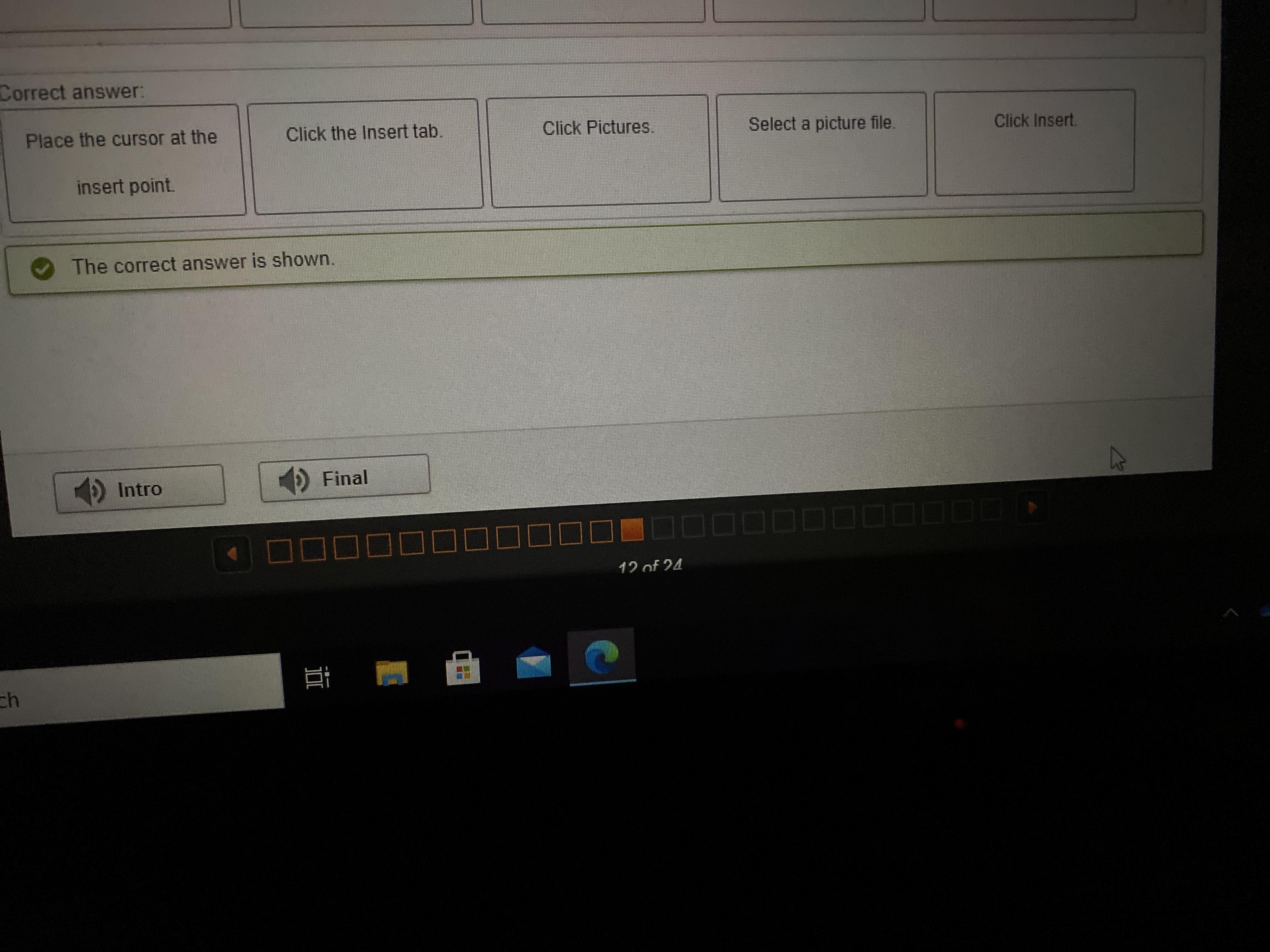
Describing How to Insert a Picture in a Document
What are the correct steps for inserting a picture into a Word 2016 document?
Click Insert.
Click Pictures.
Select a picture file.
Click the Insert tab.
Place the cursor at the
insert point.
Helllpppp
Answers
Answer:
Explanation:
Right answer
which characteristics support an agile mis infrastructure?
Answers
Answer:
The agile MIS infrastructure includes accessibility, availability, flexibility, performance, portability, reliability, scalability and usability. :)
In the cases of int, byte, long, short (In Java) Can you give the heirachy in ascending order?
Answers
Answer:
Byte Short Int Long
Explanation:
Byte's 8 bit, short's 16, int's 32, and long's 65.
when would instant messaging be the least effective means of communication
Answers
Instant messaging would be least effective means of communication when you have a series of complex questions to ask your colleague.
What is the aim of instant messaging?Instant messaging is often used as a means of sending textual messages, It is known to be a short one and also quick in nature. It can occur between business colleagues and friends.
Its disadvantages is that its is an Ineffective tool for mass communication and also has issues when used for system for archiving.
See options below
A. When you want your colleague to let you know if the hyperlink you sent her is working
B. When you want to tell someone "Happy Birthday!"
C. When you have a series of complex questions to ask your colleague
D. When you want to call an impromptu meeting between some of the people in your office
Learn more about instant messaging from
https://brainly.com/question/26271202
Answer:
When you have a series of complex questions to ask your colleague.
Explanation:
Asking these questions on instant messaging is the least professional way you can ask a colleague about series topics that involve your job, it would be more professional to ask this at work rather than on via message.
In what ways can you sort data by using the sort procedure? Check all that apply.
sort ascending
sort descending
sort diagonal
sort by font color
sort by background color
sort by rows
sort by columns
Answers
Answer:
all except c:)
Explanation:
Answer:
1,2,4,5,6,7
Explanation:
all except C
Please help. You dont need to answer the extension.

Answers
Answer:
Hope the below helps!
Explanation:
#Program for simple authentication routine
name = input("Enter name: ")
password = input("Enter password (must have at least 8 characters): ")
while len(password) < 8:
print("Make sure your password has at least 8 characters")
password = input("Enter password (must have at least 8 characters): ")
else:
print("Your password has been accepted - successful sign-up")

why might a patient be required to go to a rehabillition center after a hosptial stay
Answers
Answer:
They'd need to get care from someone who speacialized in their illness, surgery recovery or injury
Explanation:
if theyre recovering from a serious illness, surgery, or injury and require a high level of specialized care that generally cannot be provided in that setting
QUESTION :-
what is Python??
Answers
Answer:
python and Java developer at the end of the
_____ includes the technologies used to support virtual communities and the sharing of content. 1. social media 2.streaming 3. game-based learning
Answers
Answer: it’s A, social media
Explanation:
Social media are interactive digital channels that enable the production and exchange of information. The correct option is 1.
What is Social Media?Social media are interactive digital channels that enable the production and exchange of information, ideas, hobbies, and other kinds of expression via virtual communities and networks.
Social media includes the technologies used to support virtual communities and the sharing of content.
Hence, the correct option is 1.
Learn more about Social Media:
https://brainly.com/question/18958181
#SPJ2
What function does a resource manager in an IDE perform?
A. It's an interface for viewing and organizing files.
B. It's an interface for integrating text and multimedia into a website.
C. It's an environment for tracing and fixing the errors in the source code.
D. It's an environment for running and testing the source code.
E. It's an interface for creating and editing the source code.
Answers
Answer:
I would say D) Its an enviroment for running and testing the source code.
Explanation:
An integrated development environment (IDE) is a software suite that consolidates basic tools required to write and test software.
Developers use numerous tools throughout software code creation, building and testing. Development tools often include text editors, code libraries, compilers and test platforms. Without an IDE, a developer must select, deploy, integrate and manage all of these tools separately. An IDE brings many of those development-related tools together as a single framework, application or service. The integrated toolset is designed to simplify software development and can identify and minimize coding mistakes and typos.
Some IDEs are open source, while others are commercial offerings. An IDE can be a standalone application or it can be part of a larger package.
Answer:
D. It's an environment for running and testing the source code.
Explanation: plato 2023
resource limitations of smartphones, including limited screen size, help explain the popularity of question 3 options: web browsers. magnifying glasses. desktop computers. mobile apps. docs.
Answers
Smartphones have limited screen size, so web browsers, mobile apps, and docs are all popular options for users because they are designed to fit the smaller screen size.
Smartphones have limited screen sizeMagnifying glasses are also popular because they allow users to easily zoom in and out on text or images.Desktop computers are not as popular, because they require more space and resources.The limited screen size of smartphones can make it difficult to view content, so web browsers provide a solution by allowing users to access the internet.Web browsers use a zoom feature to allow users to enlarge the page, making it easier to read text and interact with content.Magnifying glasses are another popular option for those who need to zoom in on small texts or images.Desktop computers, on the other hand, offer a much larger screen and allow for more efficient multitasking.Mobile apps are also gaining popularity as they provide users with the convenience of accessing content on the go.Finally, documents such as PDFs are often used to share content that requires a magnifying glass to read.All of these options provide a solution to the limited screen size of smartphones, making them all popular choices for those with this issue.To learn more about Smartphones have limited screen size refer to:
https://brainly.com/question/5014488
#SPJ4
Which of the following is most likely to occur if a special effects artist holds up production on a feature film because he is not satisfied with the “look” of the work?
A. The artist will be offered future contracts.
B. The artist will not be offered future contracts.
C. The artist will earn the respect of his colleagues.
D. The artist will be fired.