What are three functions of Prisma Access? (Choose three. )
Answers
Three functions of Prisma Access are: Secure access to cloud-based applications, Protection from cyber threats and Secure access for remote users.
Prisma Access is a cloud-based platform that provides a range of security and networking functions.
1. Secure access to cloud-based applications: Prisma Access provides secure access to cloud-based applications, ensuring that data is protected and users are authenticated before gaining access2. Protection from cyber threats: Prisma Access provides protection from a variety of cyber threats, including malware, phishing, and ransomware. This helps to keep data and users safe from potential attacks.3. Secure access for remote users: Prisma Access provides secure access for remote users, allowing them to connect to the network from any location. This is especially important for organizations with remote workers or employees who travel frequently.Overall, Prisma Access is a valuable tool for organizations looking to protect their data and users from potential cyber threats, while also providing secure access to cloud-based applications and remote users.
Learn more about functions of Prisma Access:
brainly.com/question/20848492
#SPJ11
Related Questions
Which web-authoring software enables users to create sophisticated web pages without knowing any html code?.
Answers
Answer: One of the best software
Explanation: Dreamweaver!
Select the correct answer from each drop-down menu.
What should companies and industries practice to avoid the dangers from AI and robots?
Companies and industries should train (BLANK ONE)
and implement effective (BLANK TWO).
Blank one options:
A- HR resources
B- AI resources
C- Customers
Blank two options:
A- Testing programs
B- incentive programs
C- Marketing programs
I accidentally started the test before doing the lesson, I need some help. I will give brainliest for a correct answer.
Answers
To avoid the potential dangers associated with AI and robots, companies and industries should practice AI resources and AI- Testing programs
Blank one: B- AI resources
Companies and industries should invest in training their AI resources.
This involves providing comprehensive education and training programs for employees who work directly with AI and robotics technologies.
This training should encompass not only technical skills but also ethical considerations and best practices in AI development and deployment.
By ensuring that their AI resources are well-trained, companies can minimize the risks associated with AI and make informed decisions about its implementation.
Blank two: A- Testing programs
Implementing effective testing programs is crucial in mitigating the dangers of AI and robots.
These programs involve rigorous testing and validation of AI algorithms and robotic systems before they are deployed in real-world settings.
Thorough testing helps identify potential biases, errors, or unintended consequences that could pose risks to individuals or society at large.
Companies should establish robust testing protocols that include simulations, controlled environments, and real-world scenarios to evaluate the performance, safety, and reliability of AI and robotic systems.
For more questions on AI
https://brainly.com/question/20339012
#SPJ8
which camera effect is used to shoot tall buildings from close by without distortion
Answers
Answer:
the answer is ligma
Explanation:
Answer:
Tilt-shift lenses are a popular type of architecture photography lens
Explanation:
hope it helps
mark me brainliest
What are the letter that go under each note?
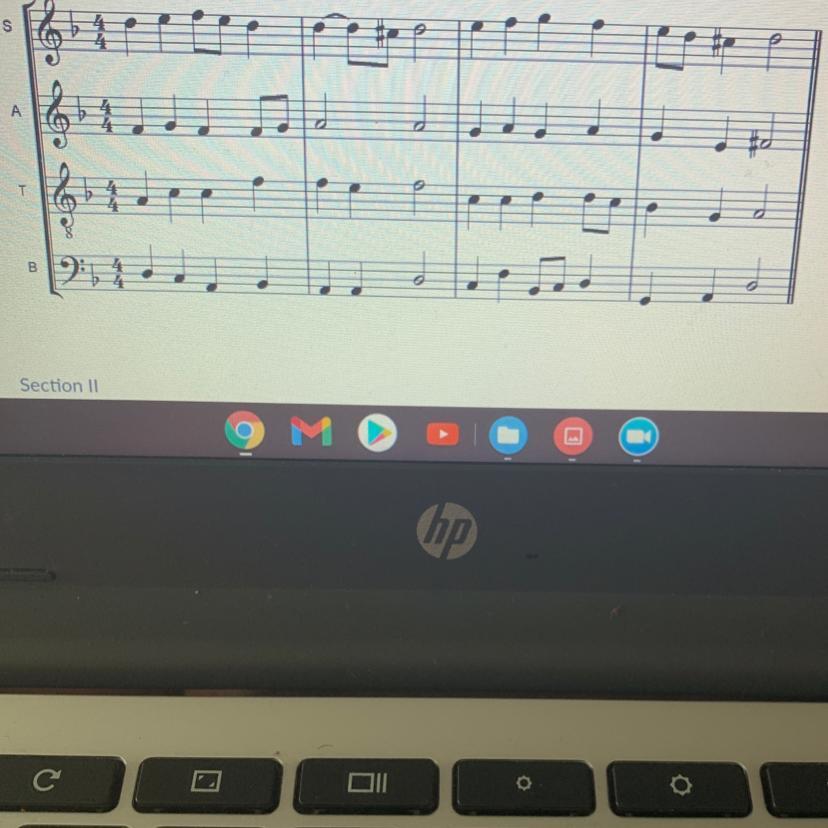
Answers
Answer:
A, B, C, D, E, F, G pls mark me brainliest see explanation below
Explanation:
those are the letters if you search up letters for music you can find them way easier than me explaining and you will also learn faster. please mark me brainliest
Answer:
a b c d e f g
Explanation:
how do you type the symbol • on a laptop?
please someone tell me how!
Answers
Answer:
Shift+8 key
Explanation:
However it depends in the website
Answer:
On a laptop with a numeric keypad, press Ctrl + Alt + 2, or Alt + 64. On an English keyboard for the United States, press Shift + 2. On an English keyboard for the UK, use Shift + `. On a Spanish keyboard for Latin America, press Alt Gr + Q.
Explanation:
C
Describe the scope of the variables in this code.
class cholesterol:
low Density = 0
highDensity = 0
class patient:
definit__(self, firstName.lastName,id Num):
self.firstName = f[rstName
self.lastName = lastName
self.id Num = idNum
def str (self):
return self.firstName +""+self.lastName + " + self.id Num
The scope of high Density is limited to the patient class
The scope of firstName is limited to the cholesterol class

Answers
Answer:
The scope of highDensity is accessible by the entire program .
The scope of firstName is limited to the patient class .
Explanation:
Correct answer edge 2020
The scope of highDensity is limited to the cholesterol class and the scope of the firstName is limited to the patient class.
Variable scopeThe accessibility of a program is described by the scope of a variable.
To put it another way, it's the part of the program where the variable is identified.
The place you declared a variable determines the scope. There are two major scopes of variables in python.
Global variablesLocal variablesTherefore, the scope of highDensity is limited to the cholesterol class and the scope of the firstName is limited to the patient class.
learn more on variable scope here: https://brainly.com/question/21065208
#SPJ2
Difference between Computer safety practices and precautions
Answers
Answer: This is a partial list of basic safety precautions to use when working on a computer: Remove your watch and jewelry and secure loose clothing. Turn off the power and unplug equipment before performing service. Cover sharp edges inside the computer case with tape. Never open a power supply or a CRT monitor.
Make sure the space underneath your desk is free from clutter and your legs have room to move. Use your mouse as close to the keyboard as possible. Adopt good posture while at the computer. Know how to adjust your chair to the most comfortable position.
who developed the first personal computer called the altair
Answers
Write the technical terms for each of the following:
a. The use of the Internet to buy and sell goods and services.
b. Voice communication through the Internet. C. A program that allows the user to log into a remote computer on the Internet as a user on that system.
d. High speed digital communication network evolving from existing telephony.
e. Software that is used for surfing information through the Internet.
Answers
Explanation:
network" (and any subsequent words) was ignored because we limit queries to 32 words.
Which of the following describes an action that serves a goal of equity
Answers
Answer:
Please complete your sentence for me to answer.
redundancy wastes space because you are storing different types of data in the same place. true or false
Answers
False. Redundancy is data stored in different places not in the same place.
What are the problems caused by data redundancy?Anomalies in insertion, deletion, and updating.When multiple layers of data management are used to assess the accuracy of the information, intentional data redundancy may result.When a company has backup storage, data redundancy also takes place.Backups serve as copies of the data to lessen problems with the primary database or the data management system.When data is duplicated but doesn't need to be because of bad coding or complicated processes, there is wasteful data redundancy.Positive redundancy in data: This kind of redundancy protects data and encourages consistency.To learn more about Data redundancy refer,
https://brainly.com/question/28340685
#SPJ4
A _______________ is a particular type of network that uses circuits that run over the Internet but that appears to the user to be a private network.
Answers
Answer:
A virtual privte network is a particular type of network that uses circuits that run over the Internet but that appears to the user to be a private network.
Does technology make us lazy? Explain. (Remember to support your
answer with citations and references)
Answers
The impact of technology on human laziness is a topic that has been widely debated and it is true to some extent.
Does technology make us lazy?Some argue it makes us lazy, while others say it can enhance productivity and efficiency.
Argument - technology makes us lazy. Advocates claim tech's conveniences can promote inactivity and a sedentary lifestyle. Tasks once done by hand can now be completed with machines, leading to possible over-reliance on technology and less physical activity, which causes health issues.
Tech improves productivity and efficiency. Tech revolutionized communication, info access, & task automation, enabling more accomplishment in less time.
Learn more about technology from
https://brainly.com/question/7788080
#SPJ1
Which classic video game, developed and published in 1987, featured four youths called the Light Warriors?
Answers
Im so stuckk on this not the math one sorry

Answers
construction companies use specialized technicians to do which step in the maintenance prosses
Answers
Construction companies use specialized technicians to perform the step of maintenance known as repairs and troubleshooting.
These technicians are skilled professionals who possess expertise in diagnosing and fixing issues in various construction systems, equipment, and structures. They play a crucial role in ensuring that maintenance activities are carried out effectively and efficiently.
These technicians are trained to identify and rectify problems related to electrical systems, plumbing, HVAC (heating, ventilation, and air conditioning), structural integrity, and other construction-related components. They use specialized tools, equipment, and techniques to diagnose and repair faults, perform routine maintenance tasks, and ensure the smooth operation of construction projects.
Their expertise and technical knowledge enable them to troubleshoot issues, identify potential hazards, and implement necessary repairs or replacements. By employing specialized technicians, construction companies can maintain the functionality, safety, and longevity of their projects, minimizing downtime and ensuring optimal performance.
Learn more about troubleshooting here:
https://brainly.com/question/29736842
#SPJ11
A timestamp is three numbers: a number of hours, minutes and seconds. Given two timestamps, calculate how many seconds is between them. The moment of the first
timestamp occurred before the moment of the second timestamp.
Can you put this into python code for me
Answers
hhd fyi ou dfi gd sdi bvb s ujj gr TX cfg y CD vi if dnainfo unlocks Toronto Yazidi
Determine the speed of rotation of a 20- tooth gear when it is driven by a 40-tooth gear and rotating at 10 rpm
Answers
Answer:
20 rpm
Explanation:
if the lager tooth gear is moving a 10 rpm which will move slower than the smaller 20 tooth gear it will push it faster than the 10 rpm
the product of the rpm and the gear ratio: 120 rpm *1/3 = 120/3 = 40.
Write a Python script to input time in minutes , convert and print into hours and minutes.
Answers
Answer:
Following are the Python program to this question: t=float(input("Enter time value in seconds: "))#input time in seconds by user
d = t // (24 * 3600) #calculate day and store in d variable t= t % (24 * 3600)#calculate time and store in t variable h = t // 3600#calculate hour and store in h variable t %= 3600#calculate time and store in t variable m=t // 60#calculate minutes and store in m variable t%= 60#calculate time and store in t variable s = t#calculate second and store in s variable print("day:hour:minute:second= %d:%d:%d:%d" % (d,h,m,s))#print calculated value
Output:
Enter time value in seconds: 1239876
day:hour:minute:second= 14:8:24:36
Explanation:
Description of the above can be defined as follows:
In the above Python program code an input variable "t" is declared, which uses the input method to input value from the user end.In the next step, "d, m, and s" is declared that calculates and stores values in its variable and at the last print, the method is used to print its value.Which type of account functions like a savings account, but limits the number of transactions?
Answers
Savings accounts often have lower minimum balance requirements than money market accounts, although the rates on money market accounts can be higher.
Why Is It Called the Money Market?The market for very liquid, extremely safe short-term debt securities is referred to as the money market. They are frequently seen as cash equivalents that can be quickly exchanged for cash because to their qualities.
What is a savings account?A savings account is a fundamental kind of financial product that enables you to deposit your money but often earn a tiny bit of interest. These accounts provide a secure location for your money while collecting interest and are federally insured up to $250,000 per account owner.
Why would someone open a money market savings account?A money market account is a variety of deposit savings account that builds income dependent on the current markets. A significant purchase or an emergency fund can be saved for using this type of account. Money market accounts are made to have higher interest rates and to be hidden from view in order to make saving more practical.
To know more about savings account visit:
https://brainly.com/question/3811440
#SPJ10
is there a non-graded scratchpad in integrated excel question that you can freely use?
Answers
Answer:
Excel McGraw Hill Excel Question - Saved O Search (Alt + Q) File Home... Scratchpad: Use as a non-graded workspace since p-value is alpha.
Explanation:
In excel, there isn't a built-in, non-graded scratchpad specifically designed for integrated questions.
What is a scratchpad?A scratchpad is a temporary area in computer memory where data can be quickly stored and accessed. It's commonly used for jotting down notes, calculations, or any other temporary information without the need for formal file saving.
Some software applications and operating systems provide scratchpad features for users to quickly take down thoughts or perform calculations.
Furthermore, one can utilize any blank cells or a separate worksheet within the excel file to act as a scratchpad. One needs to be sure that one doesn't submit any content from the scratchpad accidentally.
learn more about scratchpad: https://brainly.com/question/25749469
#SPJ2
The range of an unsigned 6 bit binary number is
0-63
0-64
0-127
1-128
Answers
Answer:
6 bit = 2^6-1=64-1=63
from 0 to 63
true or false? ux designers should consider only current internet users when designing user experiences
Answers
UX designers should consider only current internet users when designing user experiences is a false statement.
What does UX design really entail?The method design teams employ to produce products that offer customers meaningful and pertinent experiences is known as user experience (UX) design. UX design includes components of branding, design, usability, and function in the design of the full process of obtaining and integrating the product.
Note that Making a product or service functional, pleasurable, and accessible is the responsibility of the UX designer. Although many businesses create user experiences, the phrase is most frequently connected to digital design for websites and mobile applications.
Therefore, Note also that UX design is a rewarding career, yes. UX Designers are one of the most sought-after jobs in technology since they are involved at so many phases of a project's life cycle.
Learn more about UX designers from
https://brainly.com/question/898119
#SPJ1
You are creating a program for the school's
upcoming theater production. You would like to
include a picture of the cast on the cover of the
program. Which of the following factors do you
need to consider? Choose all that apply.
•image compression
•image file format
•image resolution
•image scalability
Answers
Answer:
Image file format
Image resolution
Image scalability
Explanation:
Answer:
Image File Format
Image resolution
Image Scalability
The next answer is BMP !
Explanation:
How to get out of guided access when you forgot the password?
Answers
Answer:
Pressure restart your device & Use a third-party tool
Explanation:
There are methods to get out of Guided access whilst you forgot the password:
Pressure restart your device: this may reset Guided get right of entry and you'll be able to get entry to your tool usually. To force restart your tool, press and hold the electricity button and the home button at the identical time till you notice the Apple logo.
Use a third-party tool: here are a few third-party tools that can help you reset your Guided Access password. One popular tool is iMyFone Fixppo. To use iMyFone Fixppo, you will need to connect your device to your computer and then follow the instructions on the screen.
To learn more about Guided access,
https://brainly.com/question/31110082
Pls help me!!!!!!!!!!!!!

Answers
Answer:
think It B
Explanation:
not 100% sure
A local park is interested in building a bridge over a short ravine. They have stressed that keeping costs low is very important to them. What type of bridge would you recommend they build?
Answers
Based on the requirement of low cost, I would recommend the park to build a simple beam bridge or a suspension bridge.
Why to build beam bridge or suspension bridge?
These types of bridges are relatively easy and inexpensive to construct compared to other types of bridges, such as arch bridges or cable-stayed bridges. However, the specific type of bridge would depend on the specific conditions and requirements of the location, such as the width and depth of the ravine, the load capacity required, and local building codes and regulations.
I recommend a beam or suspension bridge for cost-effectiveness. These are simple to build and suitable for short ravines. The specific type depends on site conditions and requirements.
To learn more about suspension bridge, visit: https://brainly.com/question/17582396
#SPJ1
Which of the following is NOT true about data?
A. It is information processed or stored by a computer
B. It is stored and processed in decimal format
C. It can be in the form of figures, texts, images or other types of
information
D. It can be transferred from one computer to another
Answers
Answer: B. It is stored and processed in decimal format
============================================================
Explanation:
Choice B is not true because data is stored and processed in binary format. This is in the often talked about format of 1s and 0s. Binary is preferred because computers are built upon electronic circuits. If an electrical current is passing through a certain node, then you can represent this with 1 for "on", while no electricity would be 0 for "off". Think of a series of switches you can flip up or down. Chaining together 1's and 0's allows us to represent pretty much any kind of thing we want from documents, to pictures, to movies to videogames. The 1's and 0's can represent instructions of a program (aka computer code) or it could represent raw data such as an image file.
In short, data is not stored and processed in decimal format. It's represented in binary instead. Binary is base 2 consisting of the digits 0 and 1. In contrast, decimal format deals with the digits 0 through 9.
What is computer ethics? What are the things that are prohibited by computer ethics?
Answers
Answer:
Computer ethics was set up in 1992. It entails the moral guidelines for computer professionals and users in the usage of the computer. An example is not using the computer to commit any type of fraud etc.
The things prohibited by Computer ethics include
1. Using the computer to commit any type of fraud.
2. Hacking of individual personal and private files.
3. Piracy and usage of pirated softwares etc.
Jorge needs to print out an essay he wrote but he does not have a printer his neighbor has a printer, but her internet connection is flaky. Jorge is getting late for school. What is the most reliable way for him to get printing done
Answers
Answer:
if it's allowed, jorge should print his essay at school. he can also explain the situation to his teacher.
Explanation:
jorge printing his essay using his neighbor's printer would be unreliable because of her flaky internet connection, and jorge doesn't have a printer himself. since he's also getting late for school, he doesn't have many options and seems like he has no other option but to get to school before he's late and print it there instead.
Answer:
D. copy the document onto a thumb drive and take it over to his neighbors
Explanation:
copying the document onto a thumb drive (flash drive) is the safest way to hold hid work if the internet if flaky and unstable. an email might not get sent, same with a file sharing service, physically removing the hard disk is not logical and he might lose other important info on his computer.