What are the three pre-defined tabs in the Next Generation firewall Application Command Center (ACC)
Answers
The three pre-defined tabs in the Next Generation firewall Application Command Center (ACC) are "Applications," "Threats," and "Users."
What are the default tabs in the Next Generation firewall Application Command Center (ACC)?The Next Generation firewall Application Command Center (ACC) provides three pre-defined tabs that offer crucial insights into network activity. The first tab is "Applications," which allows administrators to monitor and manage the applications being used on the network. This tab provides visibility into application usage patterns, bandwidth consumption, and potential risks associated with specific applications.
The second tab is "Threats," which focuses on identifying and mitigating potential security threats. It provides real-time visibility into network threats, including malware, intrusions, and other malicious activities. The Threats tab enables security teams to investigate and respond promptly to any detected threats, ensuring the network remains secure.
The third tab is "Users," which offers a comprehensive overview of user activity within the network. It provides information about user behavior, application usage, and potential security risks associated with specific users. This tab helps in identifying anomalies or suspicious activities that might require further investigation.
Learn more about Application Command Center
brainly.com/question/32082488
#SPJ11
Related Questions
Which of the following is a tool HR managers can use to improve commincations between workers of different generations in the same workplace? A)recruitment pools B)l-9 forms C) mentoring programs D)work/life balance

Answers
Answer:
Mentor Programs
Explanation:
This is because it is talking about different ages which is a mentor type thing
Answer: mentoring programs
Explanation:
A p e x
URGENT! I know it has to be one of these answers, but I cannot tell the difference between them for the life of me. Help.

Answers
I don't see a difference. Otherwise, they both are correct.
If you want to change a number in a cell, you must delete it first before entering a new number
True
False
This is with Google Sheets.

Answers
Answer:
true
Explanation:
hope this helps.................
Please answer these questions! Will mark Brainliest!!

Answers
Answer:
1) bob behnken and doug hurley
2)yes
3) august
the styles button on the tool bar allows you to?
Answers
You can format the cell contents using the buttons and drop-down boxes on this toolbar.
What does a computer tool bar do?A toolbar is a portion of a window, frequently a bar from across top, that has buttons that, when clicked, execute actions. You may configure the toolbars in many programs so that the instructions you use regularly are visible and accessible. Toolbars are also found in many dialog boxes.
How can I get my tool bar back?The following actions can also be used to restore the Taskbar: In addition to pressing the Esc key, hold down the Ctrl key. Let go of both keys. Tapping the Spacebar while keeping the Alt key depressed.
To know more about tool bar visit:
https://brainly.com/question/20915697
#SPJ1
You are installing two new hard drives into your network attached storage device.
Answers
You are installing two new hard drives into your network attached storage device. The correct option is d, RAID 6, because the director requests that they be placed in a RAID setup that prioritizes redundancy above performance.
RAID 6: What Does It Mean?This is a recognized redundant array of separate disks.
Keep in mind that RAID 6 is also referred to as double-parity RAID (redundant array of independent disks).
This is one of many RAID configurations that work by distributing data across several drives and allowing input/output (I/O) activities to overlap in a balanced manner, enhancing performance.
As a result, I'll select option d because the director requests that they be put into a RAID setup that prioritizes redundancy over performance. RAID 6.
Learn more about redundancy from
brainly.com/question/17880618
#SPJ4
Your question is incomplete. See full question below
You're installing two new hard drives into your network attached storage device. Your director asks that they be put into a RAID solution that offers redundancy over performance. Which would you use?
a. RAID 0
b. RAID 1
c. RAID 5
d. RAID 6
e. RAID 10
what are the advantages of user defined abstract data types?
Answers
The advantages of user-defined abstract data types are given below:Advantages:1. Abstraction of Information: The user-defined abstract data types abstract the information from the user. It means that the user only needs to understand what a data type does, not how it does it.2. Encapsulation of Information: Encapsulation is the process of packaging the data in a single unit.
It means that data is not visible to the outside world and can only be accessed through methods.3. Implementation: The user-defined abstract data types provide the implementation details to the user. The user only needs to know how to use it, not how it works.4. Information Hiding: Information hiding is the process of hiding the implementation details from the user. It means that the user does not need to know how the data type works, just how to use it.5. Flexibility: The user-defined abstract data types are flexible and can be changed as per the requirement of the application.
It means that the user can modify it based on the requirements of the application. These are the advantages of user-defined abstract data types.
Read more about Implementation here;https://brainly.com/question/29439008
#SPJ11
Please tell answer fast

Answers
Answer:
a sonos wireless speakers
Why does the evolving technology help the entrants more than the incumbents? 1) Because the incumbents do not have the means to use the new technology 2) Because the entrants can create technology faster than incumbents 3) Because incumbents do not like new technology and neither do their customers 04) Because the entrants can use the technology to target customers that do not currently have solutions 5) Because the incumbents already have a strong customer base and do not see the point of adding new technology Which one of the following factors contributes to enterprises becoming successful in the long run? 1) By leveraging the technological core and their business model. 2) The ability to understand the consumer better and create products that solve their consumers' job. 3) Plan and forecast based on correlated data. 4) By keeping all of the elements of servicing the customer under their control. Which statement best describes the "Theory of Disruptive Innovation"? 1) Disruptive Innovation is the process by which technology eliminates friction and improves efficiency within various e-commerce, retail, and commercial banking transactions. 2) Disruptive Innovation is the process by which technology enables entrants to launch inexpensive and more accessible products and services that gradually replace those of established competitors. 3) Disruptive Innovation is the process by which technology generates data for. and executes instructions from, Al-enabled systems within retail and manufacturing industries. Disruptive Innovation is the process by which technology enables entrants to launch inexpensive and more accessible products that work collectively with today's comparable market offerings. 5) None of the above. 4)
Answers
Evolution of technology helps the entrants more than the incumbents because entrants can use technology to target customers that do not currently have solutions. Entrants can create technology faster than incumbents, and they are not limited by legacy systems that incumbents are stuck with.
They have the agility to innovate and change direction as necessary to keep pace with technological advances. The incumbents are at a disadvantage because they have already established customer bases and a strong reputation, and they are unlikely to be willing to risk losing that by adopting new technology that may not be as reliable as what they already have. So, the evolving technology helps the entrants to compete with the incumbents.
One of the factors that contributes to enterprises becoming successful in the long run is the ability to understand the consumer better and create products that solve their consumers' job. By leveraging the technological core and their business model, businesses can ensure that their products are meeting the needs of their customers. Plan and forecast based on correlated data is another important factor in the success of enterprises.
Learn more about Evolution of technology: https://brainly.com/question/7788080
#SPJ11
Surrendering to digital distractions will likely result in learning more material. O False True
Answers
Answer:True
Explanation:
joann turned on her windows 10 computer today, and while the computer was booting up, it shut down. she restarted the computer and it booted fine but ran slowly. she opened task manager and noticed that her cpu was running at 98% capacity and her network at 75% capacity. when she checked to see what process was using so much network connectivity, she received a message saying that access to the process was denied.
Answers
Based on these indicators, the clear actions which Joann should do with her computer are:
Run antivirus software.Disconnect from the network.Check the file permissions.What is System Security?This refers to the precautions or measures that are taken in order to safeguard or protect a computer system or network from unauthorized usage through the use of things like firewalls, etc.
Hence, we can see that based on the given question, we are told that Joann turned on her windows 10 computer today, and while the computer was booting up, it shut down and when she re-booted it, she found out that her CPU was running at 98% capacity and her network at 75% capacity.
The best actions that she has to take in order to address these issues and also the issue of network connectivity are listed above which are using an antivirus to scan, disconnect from the network, and check file permissions.
Read more about system security here:
https://brainly.com/question/25720881
#SPJ1
The complete question is:
Joann turned on her Windows 10 computer today, and while the computer was booting up, it shut down. She restarted the computer and it booted fine but ran slowly. She opened Task Manager and noticed that her CPU was running at 98% capacity and her network at 75% capacity. When she checked to see what process was using so much network connectivity, she received a message saying that access to the process was denied.
Based on these indicators, what should Joann do with her computer? (Select all that apply.)
what is robotic technology
Answers
Answer:
according to britannica :
"Robotics, design, construction, and use of machines (robots) to perform tasks done traditionally by human beings. ... Robots are widely used in such industries as automobile manufacture to perform simple repetitive tasks, and in industries where work must be performed in environments hazardous to humans"
Explanation:
The non- Kleene Star operations accepts the following string of finite length over setA= {0, 1} | where string s contains even number of 0 and 1. a.01,0011,010101 b.0011,11001100 c.ε,0011,11001100 d.ε,0011,110011100
Answers
We can see that this set includes only those elements that contain even numbers of 0s and 1s. Option(A) is correct
The correct answer is option (a) 01, 0011, 010101.Non-Kleene Star Operations:Non-Kleene Star Operations include three other regular operations known as concatenation, alternation, and positive closure concatenation. The regular languages are closed under these operations as well. The input for the given problem is s, which contains an even number of 0s and 1s. Here are the given options to choose from:A. 01, 0011, 010101B. 0011, 11001100C. ε, 0011, 11001100D. ε, 0011, 110011100The non-Kleene star operations accept the string of finite length. However, we can easily see that some of these given options contain infinite strings.
Hence, the only option that satisfies the given condition is option (a) 01, 0011, 010101. Hence, it is the right answer. Also, we can see that this set includes only those elements that contain even numbers of 0s and 1s. Therefore, it satisfies the given condition.
To know more about operations visit :
https://brainly.com/question/30581198
#SPJ11
what is genetic programming in AI??
urgent
Answers
Answer:In artificial intelligence, genetic programming (GP) is a technique of evolving programs, starting from a population of unfit (usually random) programs, fit for a particular task by applying operations analogous to natural genetic processes to the population of programs.
Explanation:
Answer: Genetic programming (GP) is an artificial intelligence technique for creating programs suited for a specific job from a population of unfit (typically random) programs by applying operations akin to natural genetic processes on the population of programs.
Explanation:
You will need an Excel Spreadsheet set up for doing Quantity Take- offs and summary estimate
sheets for the remainder of this course. You will require workbooks for the following:
Excavation and Earthwork
Concrete
Metals
Rough Wood Framing
Exterior Finishes
Interior Finishes
Summary of Estimate
You are required to set up your workbooks and a standard QTO, which you will submit
assignments on for the rest of the course. The QTO should have roughly the same heading as
the sample I have provided, but please make your own. You can be creative, impress me with
your knowledge of Excel. I have had some very professional examples of student work in the
past.
NOTE: The data is just for reference, you do not need to fill the data in, just create a QTO.
Build the columns, and you can label them, however you will find that you will need to adjust
these for different materials we will quantify.
Here are some examples of what they should look like:
Answers
We can see here that in order to create Excel Spreadsheet set up for doing Quantity Take- offs and summary estimate, here is a guide:
Set up the spreadsheet structureIdentify the required columnsEnter the item details: In each sheet, start entering the item details for quantity take-offs. What is Excel Spreadsheet?An Excel spreadsheet is a digital file created using Microsoft Excel, which is a widely used spreadsheet application. It consists of a grid of cells organized into rows and columns, where users can input and manipulate data, perform calculations, create charts and graphs, and analyze information.
Continuation:
4. Add additional columns to calculate the total cost for each item.
5. Create a new sheet where you will consolidate the information from all the category sheets to create a summary estimate.
6. Customize the appearance of your spreadsheet by adjusting font styles, cell formatting, and color schemes.
7. Double-check the entered quantities, unit costs, and calculations to ensure accuracy.
Learn more about Spreadsheet on https://brainly.com/question/26919847
#SPJ1
What should you do when conducting an informational interview ?
Answers
When conducting an informational interview, it is important to prepare questions in advance, actively listen, and show gratitude for the person's time and insights. Building rapport and gathering valuable information are key objectives.
During an informational interview, it is crucial to approach the conversation with a clear purpose and set of questions to gather insights and information from the interviewee. Actively listen to their responses and take notes to ensure you can follow up and refer back to the conversation later. Show appreciation and gratitude for the interviewee's time and willingness to share their experiences and knowledge. Thank them at the beginning and end of the interview, and consider sending a thank-you note or email afterward as a gesture of appreciation.
Maintain a professional demeanor throughout the interview, ask open-ended questions, and allow the interviewee to share their insights and experiences. Respect their time and avoid overstaying the allotted interview duration. Remember, an informational interview is an opportunity to learn and network, so approach it with curiosity, respect, and a genuine interest in the other person's expertise.
Learn more about information here: https://brainly.com/question/31713424
#SPJ11
Using _____ is a way to solve health issues related to computer equipment. A)correct lighting
B)wired keyboards
C)a high capacity RAM
D)a high speed Internet
Answers
A) Correct lighting is a way to solve health issues related to computer equipment. Poor lighting can cause eye strain, headaches, and neck pain. The correct lighting can reduce glare and eye strain, making it easier to work for extended periods of time.
This can be achieved by using a desk lamp that provides a direct light source, or by positioning your monitor away from windows or bright lights. Another option is to use an anti-glare screen filter, which can help to reduce the amount of glare and reflections on your screen. While wired keyboards and a high capacity RAM can improve the functionality of your computer, they do not directly solve health issues related to computer equipment. A high-speed internet connection can improve the efficiency of your work, but it does not address health concerns. Overall, it is important to prioritize the health and well-being of individuals who work with computers for extended periods of time. Taking steps to ensure proper lighting and ergonomic positioning can help to prevent common health issues such as eye strain, headaches, and neck pain.
Learn more about RAM here-
https://brainly.com/question/31089400
#SPJ11
Identify the data type of each variable as either int, float, string, list, or boolean.

Answers
Data type of each variable is:
i-int
j-string
k-string
m-boolean
n-list
p-float
q-integer
r- boolean
s-int
t- string
u-string
v- float
w-string
What are data types?Data is categorized into different types by a data type, which informs the compiler or interpreter of the programmer's intended usage of the data. Numerous data types, including integer, real, character or string, and Boolean, are supported by the majority of programming languages. Today, binary data transfer is the most widely used type of data transport for all devices.
A collection of 0s and 1s arranged in a precise order makes up a binary kind of data. Every piece of information is translated to binary form and used as needed. Another set of binary data is connected to this binary form to define the type of data being carried since this binary form does not specify what it is carrying. Variables are specific storage units used in computer programming that hold the data needed to carry out tasks.
To know more about Data, check out:
https://brainly.com/question/19037352
#SPJ1
Customer Service. Is an organization's ability to _______ customers
Answers
Answer:
Serve
Explanation:
Customer Service
Answer:
At its most basic level, customer service is an organization's ability to supply their customers' wants and needs. But this definition leaves out the transactional nature of customer service, and it's this transactional aspect that drives customer loyalty.
Explanation: Hope this helps!
When HTTPS is used, the contents of the document are encrypted but the URL of the requested document is still sent in plaintext.
Answers
The given statement that is "When HTTPS is used, the contents of the document are encrypted but the URL of the requested document is still sent in plaintext" is FALSE.
HTTPS stands for Hypertext Transfer Protocol Secure. It is a secure version of HTTP, the protocol used to send data between your web browser and the website you are accessing.
HTTPS is designed to keep your data safe and prevent third parties from accessing it. It is achieved by encrypting the data sent between your browser and the website with a secure connection called SSL (Secure Sockets Layer) or TLS (Transport Layer Security).
When you visit a website using HTTPS, the entire communication between your browser and the website is encrypted. This means that not only the contents of the document, but also the URL of the requested document is encrypted and sent in ciphertext instead of plaintext. Therefore, the given statement is False.
Learn more about HTTPS at
https://brainly.com/question/12717811
#SPJ11
Describe the Order of Operations in Java programming.
Answers
Answer:
You’ll give the multiplication and division operators a rank of 2 and the addition and subtraction operators a rank of 1.
Explanation:
When you code it up, you’ll compare two operators
-2
Write a program that contains a function that takes in a 2D list and an integer as parameters. The integer represents the limit of the values inside the list. The function should change any value in the list that is greater than that limit to be equal to limit, and any values less than -limit to be equal to -limit. For example, if the limit is 200, it should change 250 to 200, it should change -300 to -200, and leave any values between -200 and 200 unchanged. Finally, the function should print the resulting list. Ask the user for 25 integers, put them in a 5x5 list, ask the user for the limit, then call the function and output the result.
Answers
Answer:
The integer represents the limit of the values inside the list. The function should change any value in the list that is greater than Explanation:
SQL DML Query in MySQL SQL Query from A Single Table IS 4420, Database Fundamentals I. DDL We create the following tables in Lecture 7 1. Customer 2. Product 3. Orders 4. Orderline II. DML: Insert data into tables Use the code in Lecture8.rtf to insert data III. DML: query 1. List all data records for all four tables 2. List IDs of products in descending order 3. List the cities (distinctly) for the customers 4. List all orderlines have quantity more or equals to 5 5. List all columns of product with the name that contains the string 'laptop 6. List customers who lived in city 'Tucson 7. Count the number of customers in each city. Show the name of the city and corresponding count. 8. List all orders after and on 2008-11-01 9. List all orders between 2008-10-24 and 2008-11-01 inclusive (including both dates) 10. What is the average price for product that is more than $50? 11. List all customers who do not live Salt Lake City. 12. List all customers who are from SLC and whose name starts with the letter 13. List all product ids that show more than twice in orderline table IV. Deliverables 1. Submit the lab8.txt file that contains your SQL statements to canvas
Answers
The task requires writing SQL statements to perform various operations on a set of tables (Customer, Product, Orders, Orderline) in a MySQL database.
To complete the task, you need to write SQL statements that fulfill the given requirements. These statements involve inserting data into the tables using the code provided in Lecture8.rtf, querying data records from all four tables, listing product IDs in descending order, listing distinct cities for customers, listing orderlines with a quantity greater than or equal to 5.
listing product columns with names containing the string 'laptop', listing customers from the city 'Tucson', counting the number of customers in each city, listing orders after and on a specific date, listing orders between two specific dates, calculating the average price for products over $50, listing customers not from Salt Lake City, listing customers from SLC with names starting with a specific letter, and listing product IDs that appear more than twice in the orderline table.
The final deliverable is a lab8.txt file containing all the SQL statements required to perform the above operations.
Learn more about SQL statements here: brainly.com/question/29607101
#SPJ11
Using Internet resources, find at least five organizations that offer Software as a Service (SaaS). How do their services benefit their users?
Answers
Answer:
1. Antenna Software
2. Cloud9 Analytics
3. CVM Solutions
4. Exoprise Systems
5. GageIn
Explanation:
1. Antenna Software - It has five gateways to routes and manages all transactions between the mobile applications and backend systems
2. Cloud9 Analytics - manages the warehouse separately from the solutions
3. CVM Solutions - Enables users to "clean" supplier information and to centralize and standardize information
4. Exoprise Systems - It avoid use of complex database and Web servers
5. GageIn - It uses Networking and social tools to connect users and facilitate communications
Answer:
1. Antenna Software
2. Cloud9 Analytics
3. CVM Solutions
4. Exoprise Systems
5. GageIn
Explanation:
Which of the following is true of a NOT truth table?
a. The statement will only be true if both statements are true.
b. In order for to be true, one or both of the original statements has to be true.
c. All of these answer choices are correct.
d. The statement that contradicts the first input value and has the opposite truth value or output.
Answers
A statement which is true of a NOT truth table is: D. The statement that contradicts the first input value and has the opposite truth value or output.
What is a truth table?A truth table can be defined as a mathematical table that comprise rows and columns, which is used in logic to show whether or not a compound ststement is true or false.
In Science, there are different types of truth table and these include the following:
AND truth tableOR truth tableNOT truth tableThis ultimately implies that, a statement that contradicts the first input value and it has the opposite truth value or output denotes a NOT truth table.
Read more on NOT operator here: https://brainly.com/question/8897321
Choose all items that are true about the two example of HTML shown on the right.
Example 1 will display differently than example 2 in a web browser.
They are styled differently, but will look the same in a web browser.
Example 2 is easier to analyze and repair.
The styling in example 2 is required by modern web browsers.
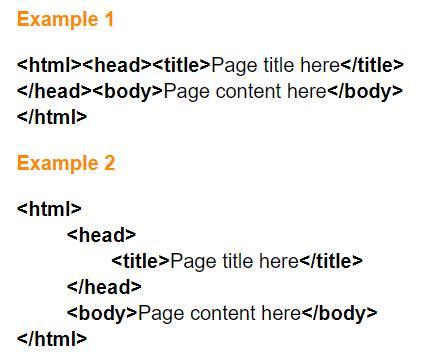
Answers
Answer:
2
Explanation:
Answer:
B and C
Explanation:
2. Media sharing websites let you post photos and videos to share with other people. What are the benefits and drawbacks of using these websites?
Answers
Media sharing websites let you post photos and videos to share with other people. The benefit is that we are up to date and get all the news as well as information worldwide.
What is company's website?The website of the company is all web sites which is operated by any occupied company or via any occupied company conducts the business. Any business website is a website that is designed in such a way that it can represent the identity of a business on the internet.
Company's name and fame id totally depends upon advertisement and its products and websites play an important role in order to make company popular and due to this reason company used the website or designed the website in unique and knowledgeable manner.
Therefore, Media sharing websites let you post photos and videos to share with other people. The benefit is that we are up to date and get all the news as well as information worldwide.
Learn more about website here:
https://brainly.com/question/19459381
#SPJ2
The speed at which data travels from the cpu to various components on the motherboard is called the?
Answers
The speed at which data travels from the CPU (Central Processing Unit) to various components on the motherboard is generally referred to as the "bus speed" or "system bus speed."
The bus speed represents the maximum rate at which data can be transferred between the CPU and other hardware components, such as RAM (Random Access Memory), expansion slots, and peripheral devices.
The bus speed is usually measured in megahertz (MHz) or gigahertz (GHz), representing the number of cycles per second. Higher bus speeds generally indicate faster data transfer rates and can contribute to improved system performance. However, it's worth noting that modern computer architectures employ various types of buses with different speeds, such as the front-side bus (FSB), the memory bus, and the PCIe (Peripheral Component Interconnect Express) bus, each serving specific purposes within the system.
To know more about data click-
https://brainly.com/question/24027204
#SPJ11
If a business/industry does not meet OSHA standards?
Answers
Answer:
Criminal penalties ensue if an employer willfully violates OSHA regulations a
Explanation: will result in individual may be fined up to $10,000 and be jailed for up to six months.
Answer:
Criminal penalties ensue if an employer willfully violates OSHA regulations and an employee is killed as a result. The guilty individual may be fined up to $10,000 and be jailed for up to six months.
Explanation:
Note that common skills are listed toward the top, and less common skills are listed toward the bottom.
According to O*NET, what are common skills needed by Chefs and Head Cooks? Select three options.
technology design
monitoring
management of personnel resources
programming
time management
installation
Answers
Answer:
2,3,5
Explanation:
i took the assignment
According to O*NET, skills needed by Chefs and Head Cooks are monitoring, management of personnel resources, and time management. Hence, options 2, 3, and 5 are correct.
What is O*NET?O*NET (Occupational Information Network) is an online database that provides comprehensive information on job characteristics, worker attributes, and occupational requirements for a wide range of occupations in the United States.
It is maintained by the US Department of Labor and is freely available to the public.
O*NET includes information on job titles, job descriptions, required skills and knowledge, education and training requirements, wages and employment trends, and much more.
The information is collected from a variety of sources, including surveys of workers and employers, industry experts, and other occupational data sources.
Thus, options 2, 3, and 5 are correct.
To learn more about the O*NET, follow the link:
https://brainly.com/question/30823238
#SPJ2