What are the most common types of Asynchronous communication?
Answers
Related Questions
Which of the following is NOT a computer hardware?
Question 2 options:
Monitor
Internet
Keyboard
Mouse
Answers
Answer:
Internet
Explanation:
please make my answer as brainelist
I have a global variable that I want to change and save in a function (in python). I have an if statement contained in a while loop where the code will pass the if and go to the elif part first, and runs the code with certain numbers, and changes some of them. Because of the changed numbers when the while loop runs again it should enter the if part, but it doesn't It uses the old values as if the function has not been run. FYI I am returning the values at the end of the function, it still doesn't work
Answers
From the above scenario, It appears that you could be facing a problem with the scope of your global variable. So It is essential to declare a global variable within a function before modifying it, to avoid creating a new local variable.
Why does the code not work?For instance, by using the global keyword within a function, such as my_function(), Python will know that the aim is to change the my_global_variable variable defined outside the function's boundary.
Therefore, When the my_function() is invoked in the while loop, it alters the global variable that is subsequently assessed in the if statement.
Learn more about code from
https://brainly.com/question/26134656
#SPJ1

clicker game creating in code.org (PLEASE HELP FAST!!!)

Answers
Use code.org's visual programming tools to create a clicker game by adding buttons, score tracking, and event handlers.
To create a clicker game in code.org, you can use the visual programming tools available.
Follow these steps:
1) Start by designing the game interface.
Add buttons, labels, and any other elements you want to display.
2) Create a variable to track the score or points in your game.
Initialize it to 0.
3) Add an event handler to the button's click event.
When the button is clicked, increment the score variable by a specific amount.
4) Update the score display to reflect the updated score value.
5) Consider adding a timer or level system to make the game more challenging.
6) Add sound effects or animations to enhance the user experience.
7) Test and debug your game to ensure it functions as intended.
8) Share and enjoy your clicker game with others.
For more such questions on Visual programming:
https://brainly.com/question/29362725
#SPJ11
A specific type of computer program that manages the other programs on a computer
Answers
Reason: operates systems like desktop CPU’s, laptop computers, smartphones, tablet cpus, and gaming consoles
What types of files we do backup in UNIX and Linux?
Answers
Answer:
Nas ja kaki yawe diy. Kitu mu chuk k a jana a.
Explanation:
Karu explain pudi diya chal puter chuti kar.
sir bilal wants to know your arid number for 2 extra grades.
What can quantum computers do more efficiently than regular computers?
Answers
Quantum computers can also efficiently simulate quantum systems, which is not possible on classical computers. This is useful in fields such as quantum chemistry, where simulating the behavior of molecules can help in the discovery of new materials and drugs.
Quantum computers are capable of solving certain problems exponentially faster than classical or regular computers. This is because quantum computers use quantum bits or qubits, which can exist in multiple states simultaneously, allowing for parallel computations. One of the most well-known examples is Shor's algorithm, which is used to factor large numbers, a problem that is currently infeasible for classical computers to solve efficiently. This has significant implications for cryptography and data security.
Quantum computers can also efficiently simulate quantum systems, which is not possible on classical computers. This is useful in fields such as quantum chemistry, where simulating the behavior of molecules can help in the discovery of new materials and drugs.
Quantum computers also have the potential to greatly improve machine learning and optimization algorithms, allowing for faster and more efficient solutions to complex problems. Overall, quantum computers are expected to have a significant impact on various fields such as cryptography, material science, and artificial intelligence.
For more such questions on Quantum computers, click on:
https://brainly.com/question/29576541
#SPJ11
g Unlike when you create a String, when you create a StringBuilder, you must use the keyword ____________.
Answers
Answer:
Unlike when you create a String, when you create a StringBuilder, you must use the keyword new
Explanation:
Strings are used in programming which also opens the way for StringBuilder to be used too. In javascript, for instance, variables are useful for storing data, We have "Let" and "const" variables. Const variables cannot be changed after they’re created. The data stored are in types an example is a string. Strings allow one to write a value and store the result in a variable.
For example, using the dot operator, when you:
console.log('love'.length); // Prints 4
Note that console.log() allows the computer to evaluate the expression inside the parentheses and print that result to the console.
.length prints 4 as the result. This shows how the string has a property that stores the number of characters in that string.
StringBuilder with the keyword "new" is used when we want to change or modify data property stored in a string.
Question
Which of the following binary numbers (base 2) are multiples of 4? CHOOSE TWO ANSWERS.
11100
1101
10110
10100
Answers
The binary numbers that are multiples of 4 are; 11100 and 10100
Binary to decimal conversionLet us convert each of the given binary numbers to decimal;
A) 11100 = (1 × 2⁴) + (1 × 2³) + (1 × 2²) + (0 × 2¹) + (0 × 2°) = 16 + 8 + 4 + 0 + 0 = 28
B) 1101 = (1 × 2³) + (1 × 2²) + (0 × 2¹) + (1 × 2°) = 8 + 4 + 0 + 1 = 13
C) 10110 = (1 × 2⁴) + (0 × 2³) + (1 × 2²) + (1 × 2¹) + (0 × 2°) = 16 + 0 + 4 + 2 + 0 = 22
D) 10100 = (1 × 2⁴) + (0 × 2³) + (1 × 2²) + (0 × 2¹) + (0 × 2°) = 16 + 0 + 4 + 0 + 0 = 20
Looking at the decimals, only 20 and 28 are multiples of 4.
Read more about binary to decimal conversion at; https://brainly.com/question/17946394
What are vSphere Clusters and how are they utilized in vSphere?
Answers
A group of ESXi hosts set up as a vSphere cluster to share resources like processor, memory, network, and storage In vSphere environments, each cluster can hold up to 32 ESXi hosts, each of which can run up to 1024 virtual machines.
What is vSphere Clusters?The Clusters page in the vSphere Infrastructure view lets you see how many more virtual machines (VMs) can be added to each cluster, how many resources are totaled up in each cluster, and how many resources are currently available in each cluster. It also lets you manage the resources of each host that is part of the cluster.
According to the spare cluster capacity, the page shows information about the number of additional VMs that can be added to each cluster, as well as information about the powered-on and running VMs, their CPU and memory utilization, and other information. By changing the settings for the spare VM basis on this page, you can change how the spare VM basis for an average VM is calculated.
The information on this page helps to address important subsystem-related questions like the following by giving a comprehensive picture of cluster memory usage and contention using Memory metrics:
Is my environment's vSphere memory management functioning properly?In my environment, is the vSphere page sharing mechanism being used effectively? What amount of memory is shared?How much memory can you overcommit?Learn more about vSphere
https://brainly.com/question/28787607
#SPJ1
The protections from the security software must continue when the device is taken off the network, such as when it is off-grid, or in airplane mode and similar. Still, much of the time, software writers can expect the device to be online and connected, not only to a local network but to the World Wide Web, as well. Web traffic, as we have seen, has its own peculiar set of security challenges. What are the challenges for an always connected, but highly personalized device?
Answers
Answer:
third ighjojdudjz
ghddduewjj
wkckdjjj
Explanation:
cchmddkhwmx
ndhdnahdd
jruditndjed
create a powerpoint presentation on various e commerce websites. compare them and write which one is your favourite and why
Answers
The e-commerce websites created for online shopping are shown on this slide, along with how customers may utilize them to compare prices and make purchases and PPT.
Thus, By providing information via various website services, you can raise audience engagement and knowledge. Internet stores Ppt Images and Graphics.
You can deliver information in stages using this template. Using this PPT design, you may also show information on products, exclusive discounts, and strong online websites. This style is entirely changeable, so personalize it right away to satisfy the demands of your audience.
A lousy PowerPoint presentation can detract from the excellent content you're providing with team stakeholders because of poor color choices or unclear slides.
Thus, The e-commerce websites created for online shopping are shown on this slide, along with how customers may utilize them to compare prices and make purchases and PPT.
Learn more about PPT, refer to the link:
https://brainly.com/question/31676039
#SPJ1
Pls help I will get points and brainliest
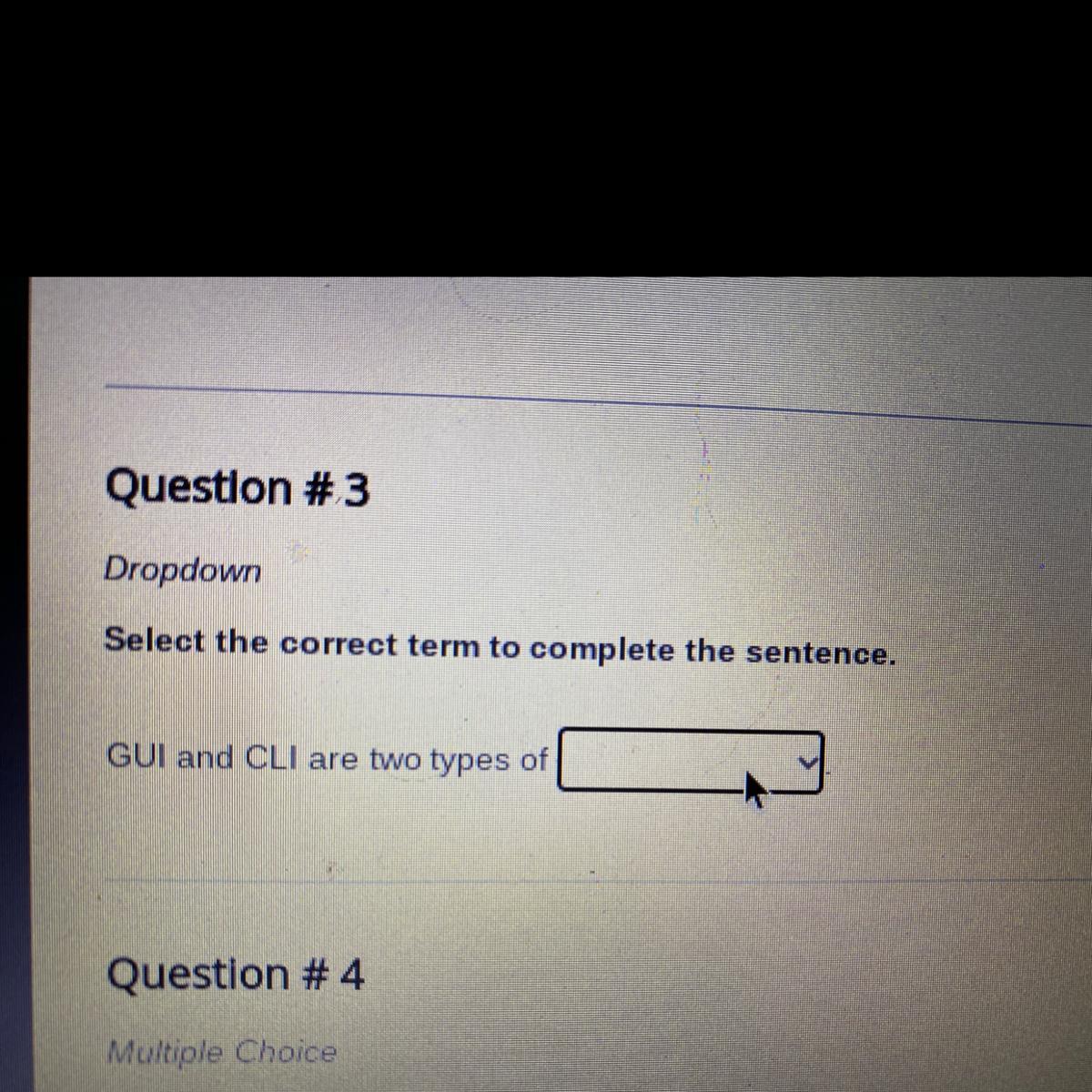
Answers
Answer:
They are both types of interfaces.
Explanation:
Click the answer that includes the word "Interface" or "Interfaces"
Use the drop-down menus to complete each sentence.
If a student wants to participate in an online experiment, she will need to access a digital
If a student wants to watch videos, listen to lectures, and take quizzes for a class, he will access a digital
If a student who is also entering the workforce needs to get some skills training for a new job, she will likely need
access to a digital
Answers
The correct answers are given below:
If a student wants to participate in an online experiment, she will need to access a digital platform or website.
If a student wants to watch videos, listen to lectures, and take quizzes for a class, he will access a digital learning management system (LMS).
If a student who is also entering the workforce needs to get some skills training for a new job, she will likely need access to a digital learning platform or online course.
What is an Online Experiment?An online experiment refers to research that is conducted over the internet, typically using a web-based platform or website. In order to participate in such an experiment, a student will need to access the digital platform or website where the experiment is being conducted.
A digital learning management system (LMS) is a software application for the administration, documentation, tracking, reporting, and delivery of educational courses, training programs, or learning and development programs.
Read more about digital platform here:
https://brainly.com/question/14242512
#SPJ1
Answer:
1.laboratory
2.classroom
3.office
Explanation:edge
Select the correct answer from each drop-down menu.
Which two components help input data in a computer and select options from the screen, respectively?
✓inputs data into computers in the form of text, numbers, and commands. However, a
commands from the screen.
A
Reset
Next
✓selects options and
Answers
Which two components help input data in a computer and select options from the screen, respectively?
✓ Keyboard inputs data into computers in the form of text, numbers, and commands. However, a
✓ Mouse selects options and commands from the screen.
A
Reset
Next
To know more about input data refer here
https://brainly.com/question/30256586#
#SPJ11
How can we tell the computer both what to put on
the web page, and how to organize it?
Answers
There is only 1 answer. Code. You have to code the web page if you want to put stuff on it/organize it.
We instruct the computer and tell how to organize the web-page through Coding.
Coding in essence, means the language that instruct computer and these are used to develop application, websites, software and so on.
In order to learn how to code, you must follow certain procedure:
Learning the Basics of HTML and Understanding Document Structure Learn about the CSS Selectors Knowing how to put together a CSS Stylesheet etc.In conclusion, instruction given to computer to organize a Web-page and communication with the system are made possible through coding.
Learn more here
brainly.com/question/19535447
The are two schools of ____________ are Symmetry and Asymmetry.
Answers
The two schools of design that encompass symmetry and asymmetry are known as symmetrical design and asymmetrical design.
Symmetrical design is characterized by the balanced distribution of visual elements on either side of a central axis. It follows a mirror-like reflection, where the elements on one side are replicated on the other side, creating a sense of equilibrium and harmony.
Symmetrical designs often evoke a sense of formality, stability, and order.
On the other hand, asymmetrical design embraces a more dynamic and informal approach. It involves the intentional placement of visual elements in an unbalanced manner, without strict adherence to a central axis.
Asymmetrical designs strive for a sense of visual interest and tension through the careful juxtaposition of elements with varying sizes, shapes, colors, and textures.
They create a more energetic and vibrant visual experience.
Both symmetrical and asymmetrical design approaches have their merits and are employed in various contexts. Symmetry is often used in formal settings, such as architecture, classical art, and traditional graphic design, to convey a sense of elegance and tradition.
Asymmetry, on the other hand, is commonly found in contemporary design, modern art, and advertising, where it adds a sense of dynamism and creativity.
In conclusion, the schools of symmetry and asymmetry represent distinct design approaches, with symmetrical design emphasizing balance and order, while asymmetrical design embraces a more dynamic and unbalanced aesthetic.
For more such questions on symmetry,click on
https://brainly.com/question/31547649
#SPJ8
irving is running cable underground beside his driveway to power a light at his entrance .what type of cable is he most likely using?
A.MC
B.NNC
C.UFD
D.UF
Answers
Based on the given information, Irving is running cable underground beside his driveway to power a light at his entrance. The most likely type of cable he would use in this scenario is "D. UF" cable.
Why is the cable Irving is using a UF cable and its importanceUF stands for "Underground Feeder" cable, which is specifically designed for underground installations.
It is commonly used for outdoor applications, such as running power to lights, pumps, or other outdoor fixtures. UF cable is moisture-resistant and has insulation suitable for direct burial without the need for additional conduit or piping.
Read more about cables here:
https://brainly.com/question/13151594
#SPJ1
Describe the examples of expressions commonly used in business letters and other written communications with some clearer alternatives:
Answers
When writing business letters and other written communications, it is important to use expressions that convey your message clearly and professionally.
Here are some examples of commonly used expressions in business letters along with clearer alternatives:
1. "Enclosed please find" → "I have enclosed"
This phrase is often used to refer to attached documents. Instead, simply state that you have enclosed the documents.
2. "As per our conversation" → "As we discussed"
Rather than using a formal phrase, opt for a more conversational tone to refer to previous discussions.
3. "Please be advised that" → "I want to inform you that" or "This is to let you know that"
Instead of using a lengthy phrase, use more straightforward language to convey your message.
4. "In regard to" → "Regarding" or "Regarding the matter of"
Use a more concise phrase to refer to a specific topic or issue.
5. "We regret to inform you" → "Unfortunately" or "I'm sorry to say"
Instead of using a lengthy expression, choose simpler words to deliver disappointing news.
Remember, it is important to maintain a professional tone while also ensuring that your message is clear and easy to understand. Using simpler alternatives can help improve the readability of your business letters and written communications while still maintaining a polite and professional tone.
For more such questions on letters,click on
https://brainly.com/question/18319498
#SPJ8
The editor serves as both a creative and technical role. True False
Answers
Answer:
True
Explanation:
You are given a decimal number to convert into binary. Press the buttons to
change their values so that the row represents the decimal number on the left.
When a 1 is used, we consider the value to be ON. When a 0 is used, we consider
the value to be OFF.
128
90
69
93
76
47
12
66
122
70
103
Answers
128: 10000000
90: 01011010
69: 01000101
93: 01011101
76: 01001100
47: 00101111
12: 00001100
66: 01000010
122: 01111010
70: 01000110
103: 01100111
A user is unable to plug a USB 3.0 device into a USB port. Upon inspection, a technician notices the USB 3.0 port appears to be slightly smaller than the other connections. Which of the following is the MOST likely
cause?
1- A foreign object is stuck inside the port.
2- The cable connection utilized the wrong orientation.
3- The USB cable is physically damaged.
4- The USB port belongs to a different form factor.
Answers
Answer:
4- the usb port belongs to a different form factor.
Explanation:
The most likely cause of the USB 3.0 port appears to be slightly smaller than the other connections is the cable connection utilized the wrong orientation. Thus, option B is correct.
Why USB is widely adopted?USB is widely adopted and supports both forward and backward compatibility. The USB 3.0 printer should work with the USB 2.0 computer. However, having a connection like this, the printer will only be able to work at the speeds of the computer’s USB 2.0.
By default, USB is built to allow transfer speeds improvement with upgrades from previous generations while still maintaining compatibility between devices that are supported by them.
A USB hub functions as an extension cord for USB devices. It connects to your computer and allows you to connect more devices than your current USB ports allow. Some USB hubs are powered, while others are not.
Thus, option B is correct.
Learn more about USB on:
https://brainly.com/question/28333162
#SPJ2
Given string userString on one line and character updatedChar on a second line, change the last character of userString to updatedChar.
Ex: If the input is:
cheetah
S
then the output is:
cheetaS
Note: Assume the length of string userString is greater than or equal to 1. C++
Answers
Answer:
#include <iostream>
#include <string>
using namespace std;
int main() {
string userString;
char updatedChar;
// Get the user's string
cout << "Enter a string: ";
cin >> userString;
// Get the updated character
cout << "Enter a character to replace the last character: ";
cin >> updatedChar;
// Replace the last character
int length = userString.length();
userString[length - 1] = updatedChar;
// Print the updated string
cout << "The updated string is: " << userString << endl;
return 0;
}
Explanation:
This program gets the user's input string and the updated character, replaces the last character of the string with the updated character, and finally prints the updated string.
What are two examples of items in Outlook?
a task and a calendar entry
an e-mail message and an e-mail address
an e-mail address and a button
a button and a tool bar
Answers
Answer:
a task and a calendar entry
Explanation:
ITS RIGHT
Answer:
its A) a task and a calendar entry
Explanation:
correct on e2020
Difference between analog and digital computer ??
Answers
Answer:
The analogue computer works on a continuous signal. The digital computer works on a discrete signal. The output is a voltage signal, they are not exact values and are in graphical form.
The disadvantage from using this device results from the fact that any incoming signal on any of its ports is re-created and sent out on any connected ports which has a negative impact on network performance.
Hub
Answers
Hub has a detrimental effect on the functioning of the network Any incoming signal on any of its ports is recreated and sent out on any associated ports, which is a drawback of utilising this device.
In a local area network, a hub is a layer one (physical) device that connects different network components like switches and routers (LAN). It has several ports that are used to link different local area network segments (LAN). Because frames are replicated to every other port on the network when they are received at a hub's port, hubs are typically thought of as being.
Due to the fact that each incoming signal on any of a hub's ports is recreated and sent out on any associated ports, employing a hub has a detrimental effect on network performance.
Learn more about Network here:
https://brainly.com/question/17272513
#SPJ4
Identify the fallacy (if there is one) committed in the following passage: “In America the people appoint the legislative and the executive power and furnish the jurors who punish all infractions of the laws. The intuitions are democratic, not only in their principle, but in all their consequences. The people are therefore the real directing power.”
Ad Hominem
Tu Quoque
Appeal to Popularity
Appeal to Ignorance
No Fallacy In Passage
Answers
Based on the excerpt, we can logically deduce that there is: D. No Fallacy In Passage.
The types of fallacy.In English literature, there are different types of fallacy and these include the following:
Appeal to authoritySlippery slopeHasty generalizationsAd HominemAppeal to Popularity (Ad populum)Based on the excerpt, we can logically deduce that there is no fallacy In the passage because the statement isn't a false belief or based on illogical arguments and reasoning.
Read more on fallacy here: https://brainly.com/question/1395048
#SPJ1
How many times would the following loop iterate?
Set k = 1
While k < 5
Display k
Set k = k + 1
End While
Answers
Answer:
The answer to this question is given below in the explanation section
Explanation:
The code is :
Set k = 1
While k < 5
Display k
Set k = k + 1
End While
this is a while loop, that will iterate 4 times and display the body of loop. and at the fifth iteration, the loop condition does not meet the condition and the loop will get terminated.
Which of the following network-based device logs are the least important when performing an incident investigation? A) Firewalls B) Web servers C) DHCP servers D) Routers and Switches
Answers
Routers and Switches are the least important when performing an incident investigation.
The main function of the switch is to connect terminal devices such as computers, printers, etc. A router's main function is to connect two different networks. Switches operate at the data link layer of the OSI model. Routers, on the other hand, operate at the network layer of the OSI model.
Network switches can connect multiple devices and networks to extend a LAN, while routers allow multiple network devices to share a single IP address. Simply put, Ethernet switches create networks, and routers allow connections between networks.
To know more about router and switches, visit:
https://brainly.com/question/13600794
#SPJ4
what does an attacker need to do to use acquired user and account details from a users smart card
Answers
What an attacker needs to do to acquire user and account details from a user's smart card is to clone it.
What is cloning?Cloning is the technique of producing an identical replica of another application program or object. The phrase can refer to an object, programming, or application that has similar functionality and behavior to another item or application program but does not include the actual source code from the relevant object or program. Cloning is also used to describe the operation of creating an identical replica of a directory file or disk, including any subdirectories or files included inside the disk or directory.
Cloning is the process of creating a genetically identical copy of a cell or an organism, and it is not just used for cyber theft. Cloning occurs frequently in nature. The duplication of any type of biological material for scientific studies, such as a chunk of DNA or a single cell, is known as "cloning" in the field of biomedical research.
learn more about Cloning at:
https://brainly.com/question/16155328
#SPJ1
What is Tesla BEST know for designing this? ANSWER
What car company by Elon Musk honors him? ANSWER
What famous inventor did Tesla work for in New York? ANSWER
What did Tesla help invent that helps us see our bones? ANSWER
What did he first build that kids typically use? ANSWER
What did Tesla tell people he could do? ANSWER
What happened to all of Tesla’s money? ANSWER
What is happening with Teslas wireless technology today?

Answers
Answer:
tesla coilsteslaedisonx rayslinkytime travelhe spent itblue toothExplanation: