What are the dominant InfoSec-related credentials used to document knowledge and/or experience?
Answers
Answer:
One of the most widely cited information security certifications is the Certified Information Systems Security Professional (CISSP), offered by the International Information Systems Security Certification Consortium (ISC)2[1].
Related Questions
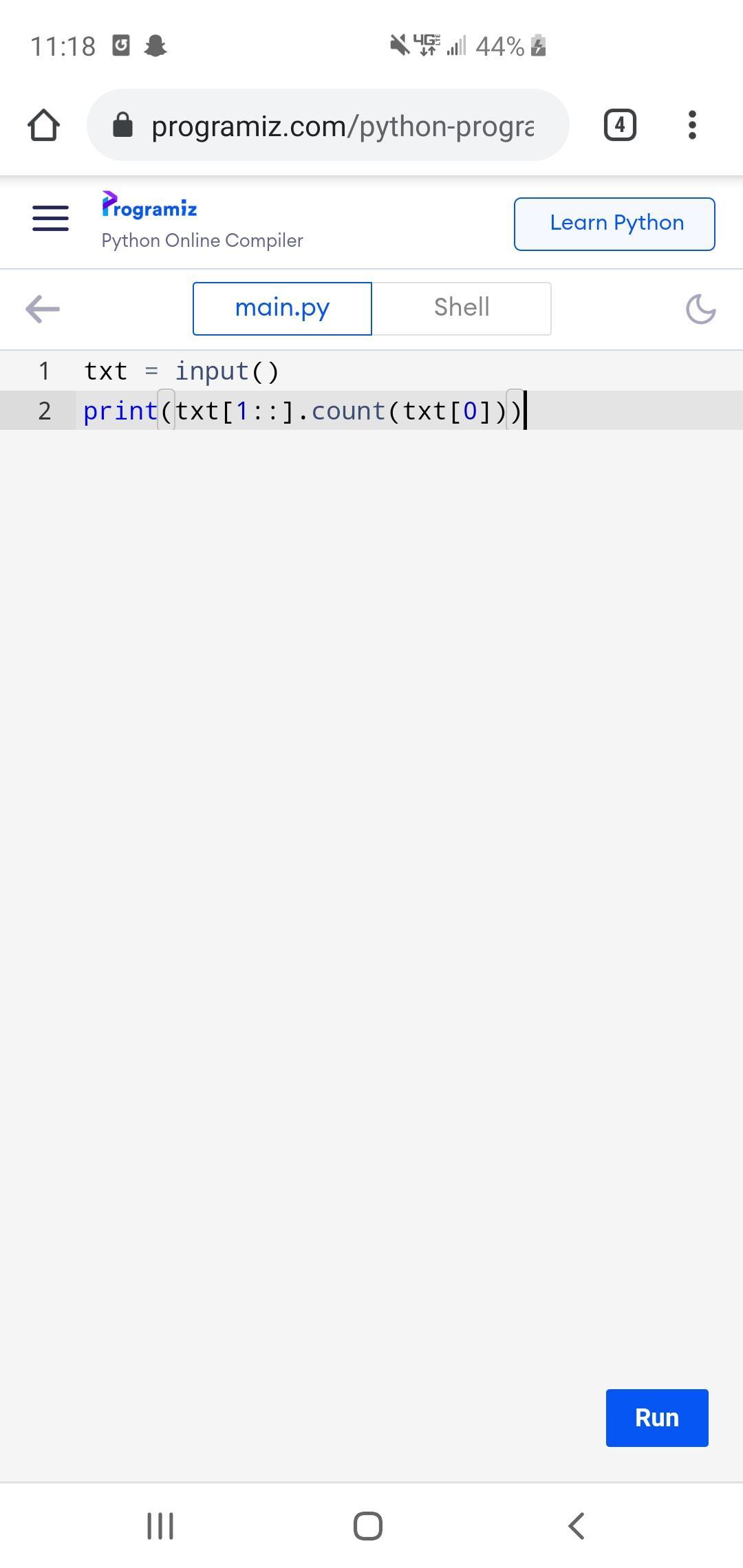
See the picture and answer the coding question

Answers
Answer:
Actually I don't know computer so I can't help you sorry bro
Write a program whose input is a string which contains a character and a phrase, and whose output indicates the number of times the character appears in the phrase.
Ex: If the input is:
n Monday
the output is:
1
Ex: If the input is:
z Today is Monday
the output is:
0
Ex: If the input is:
n It's a sunny day
the output is:
2
Case matters.
Ex: If the input is:
n Nobody
the output is:
0
n is different than N.
Learning Python
Answers
Explanation:
1
Ex: If the input is:
z Today is Monday
the output is:
0
Ex: If the input is:
n It's a sunny day
the output is:
2
Case matters.
Ex: If the input is:
n Nobody
the output is:
0
n is different than N.
Learning Python
I've included my code in the picture below. Best of luck.
Web pages are documents that only contain text, graphics, and animations.
Answers
Answer:
and audios and other media.
2. Write a C program that generates following outputs. Each of the
outputs are nothing but 2-dimensional arrays, where ‘*’ represents
any random number. For all the problems below, you must use for
loops to initialize, insert and print the array elements as and where
needed. Hard-coded initialization/printing of arrays will receive a 0
grade. (5 + 5 + 5 = 15 Points)
i)
* 0 0 0
* * 0 0
* * * 0
* * * *
ii)
* * * *
0 * * *
0 0 * *
0 0 0 *
iii)
* 0 0 0
0 * 0 0
0 0 * 0
0 0 0 *

Answers
Answer:
#include <stdio.h>
int main(void)
{
int arr1[4][4];
int a;
printf("Enter a number:\n");
scanf("%d", &a);
for (int i=0; i<4; i++)
{
for(int j=0; j<4; j++)
{
if(j<=i)
{
arr1[i][j]=a;
}
else
{
arr1[i][j]=0;
}
}
}
for(int i=0; i<4; i++)
{
for(int j=0; j<4; j++)
{
printf("%d", arr1[i][j]);
}
printf("\n");
}
printf("\n");
int arr2[4][4];
int b;
printf("Enter a number:\n");
scanf("%d", &b);
for (int i=0; i<4; i++)
{
for(int j=0; j<4; j++)
{
if(j>=i)
{
arr1[i][j]=b;
}
else
{
arr1[i][j]=0;
}
}
}
for(int i=0; i<4; i++)
{
for(int j=0; j<4; j++)
{
printf("%d", arr1[i][j]);
}
printf("\n");
}
printf("\n");
int arr3[4][4];
int c;
printf("Enter a number:\n");
scanf("%d", &c);
for (int i=0; i<4; i++)
{
for(int j=0; j<4; j++)
{
if(j!=i)
{
arr1[i][j]=c;
}
else
{
arr1[i][j]=0;
}
}
}
for(int i=0; i<4; i++)
{
for(int j=0; j<4; j++)
{
printf("%d", arr1[i][j]);
}
printf("\n");
}
printf("\n");
return 0;
}
Explanation:
arr1[][] is for i
arr2[][] is for ii
arr3[][] is for iii


Research statistics related to your use of the Internet. Compare your usage with the general statistics.
Explain the insight and knowledge gained from digitally processed data by developing graphic (table, diagram, chart) to communicate your information.
Add informational notes to your graphic so that they describe the computations shown in your visualization with accurate and precise language or notations, as well as explain the results of your research within its correct context.
The statistics and research you analyzed are not accomplished in isolation. The Internet allows for information and data to be shared and analyzed by individuals at different locations.
Write an essay to explain the research behind the graphic you develop. In that essay, explain how individuals collaborated when processing information to gain insight and knowledge.
Answers
By providing it with a visual context via maps or graphs, data visualization helps us understand what the information means.
What is a map?The term map is having been described as they have a scale in It's as we call the longitude and latitude as well as we see there are different types of things are being different things are also in it as we see there are different things are being there in it as we see the oceans are there the roads and in it.
In the US, 84% of adults between the ages of 18 and 29, 81% between the ages of 30-49, 73% between the ages of 60 and 64, and 45% between the ages of 65 and above use social media regularly. On average, users use social media for two hours and 25 minutes each day.
Therefore, In a visual context maps or graphs, and data visualization helps us understand what the information means.
Learn more about the map here:
https://brainly.com/question/1565784
#SPJ1
Which of the following is not a form of technology?
A) computer
B) ketchup
C) pencil
D) umbrella
Answers
Answer:
ketchup because all of the others are objects with certain creative functions but ketchup is just K e t c h u p.
A well known answer yes u guessed ryt it’s “Ketchup”.
Horaayy felicitations to u
Now back to the question, according to the definition of “technology”:
“An equipment or machinery made by engineering or applied science/sciences is called technology”.
As u can c that ketchup is this certainly not a technology rather a recipe/food item etc.
some context free languages are undecidable
Answers
are there any other types of technology that can attach to satellites and assist it in data collection?
Answers
Yes, there are other types of technology that can attach to satellites and assist it in data collection.
What is the term used to describe satellite data collection?
The practice of remote sensing involves gathering knowledge about things, places, or phenomena from a distance, usually from planes or satellites. It entails the detection and classification of objects on the Earth's surface, in the atmosphere, and in the oceans using sensor technologies based on satellite or aircraft.
Therefore, Remote sensing methods like optical imaging and synthetic-aperture radar are used to gather satellite imagery data. They collect data and send it to earth.
Learn more about data collection from
https://brainly.com/question/26711803
#SPJ1
Mohammed’s parents learn that his classmates have begun sending him text messages making fun of his heritage. Mohammed says he’s fine because they are just teasing him. Which challenge is making it difficult to stop the cyberbullying of Mohammed? The classmates are using secure computers. The classmates are using technology positively. Mohammed doesn’t have any evidence of the cyberbullying. Mohammed doesn’t believe the cyberbullying exists
Answers
Answer:
Mohammed doesn't believe the cyberbullying exists.
Explanation:
If he knew he wouldn't say they are teasing him. I mean, how would their parents know he is being cyberbullied without evidence? Text messages(such as imessages) are most likely on phones, and not on computers.(Unless its an mac I believe.) And they are bullying him; its not using technology positively.
Answer:
d
Explanation:
🃒🂧🃖🃯🂶🂤ã¨ã’ã½ã‚…ãã£ã–
Oliver wants to send a report to his boss discussing the upcoming project. Which communication facility would he use to send a formal message to his boss?
A. email
B. chat
C. forum
D. blog
Answers
Match the cell reference to its definition,
absolute reference
The cell has combination of two other types
of cell references.
relative reference
The cell remains constant when copied or
moved.
mixed reference
The cell changes based on the position of
rows and columns

Answers
Answer:
Absolute reference- the cell remains constant when copied or moved
Relative reference- the cell changes based on the position of rows and columns
Mixed references- the cell has combination of two other types of cell references
Explanation:
Select the correct answer.
Which symbol should you use for entering a formula in a cell?
A.
+
В.
=
c.
$
D. Divide
E. #
Answers
Answer:
equals operator...............
A washing machine control circuit has 4 inputs: WASH, THERMOSTAT, FULL, EMPTY and 4 outputs: HOT, COLD, MOTOR, and PUMP. When they are high, the outputs turn on the hot and cold taps, the main motor, and the draining pump respectively. THERMOSTAT goes high when the water in the machine is above the required temperature; FULL and EMPTY indicate (when high) that the machine is completely full or completely empty of water respectively; they are both low when it is half full.
Draw a Karnaugh map for each output and hence write down the Boolean equations that describe the operation of the washing machine control circuit.
Answers
Using Karnaugh Map the Boolean expression for each output is attached below
What is a Karnaugh MapA Karnaugh map or K-map can be defined as a visual method used to simplify an algebraic expressions in Boolean functions without using complex theorems or equation manipulations. A K-map is a special version of a truth table that makes it simple or less complex to map out parameter values and achieve a simplified Boolean expression
In this problem, we can express this as
HOT: (WASH) + (THERMOSTAT)
COLD: (WASH)
MOTOR: (WASH) + (FULL) + (EMPTY)
PUMP: (FULL) + (EMPTY)
Karnaugh Map for HOT:
WASH THERMOSTAT
0 0 0
0 1 1
1 0 1
1 1 1
Karnaugh Map for COLD:
WASH
0 0
0 1
1 0
1 1
Karnaugh Map for MOTOR:
WASH FULL EMPTY
0 0 0 0
0 0 1 1
0 1 0 1
0 1 1 1
1 0 0 1
1 0 1 1
1 1 0 1
1 1 1 1
Karnaugh Map for PUMP:
FULL EMPTY
0 0 0
0 1 1
1 0 1
Learn more on Karnaugh Map here;
https://brainly.com/question/15077666
#SPJ1
A Mixed Reality application detects the spatial layout of a room and is able to overlap or hide a virtual object based on its position in the image. What effect makes this possible?
Answers
Tethering A mixed reality program identifies the physical arrangement of a room and can overlay or show a digital include about on its placement in the picture. What impact allows this to happen?
Tethered virtual reality headsets are fueled by a cable modem to a laptop, which further supplies the headgear with the VR experience. Some tethered VR headsets need extra gadgets such as ground stations and lightboxes installed in the showed improvement of a room to track students' movements.
Mixed reality applications have been implemented in a variety of industries, including design, teaching, entertaining, military training, health, commercial document management, and living thing robot control.
To know more about robot click here
brainly.com/question/30258787
#SPJ9
A deferred annuity is an annuity which delays its payouts. This means that the payouts do not start until after a certain duration. Notice that a deferred annuity is just a deposit at the start, followed by an annuity. Your task is to define a Higher-order Function that returns a function that takes in a given interest rate and outputs the amount of money that is left in a deferred annuity.
Define a function new_balance(principal, gap, payout, duration) that returns a single-parameter function which takes in a monthly interest rate and outputs the balance in a deferred annuity. gap is the duration in months before the first payment, payout is monthly and duration is just the total number of payouts. Written in Python code.
Test Case:
new_balance(1000, 2, 100, 2)(0.1)
Output:
1121.0
Answers
Answer:
Explanation:
Here is the requested Python code for the new_balance function:
def new_balance(principal, gap, payout, duration):
def balance(interest_rate):
return principal * (1 + interest_rate)**gap + payout * ((1 + interest_rate)**(gap + duration) - (1 + interest_rate)**gap) / interest_rate
return balance
This function defines a single-parameter function balance which takes in a monthly interest rate and calculates the balance in a deferred annuity based on the given parameters. The balance is calculated using the formula for a deferred annuity, which accounts for the gap between the initial deposit and the start of the payouts, as well as the total number of payouts and the monthly payout amount.
Why is it important to explore an Integrated
Development Environment?
A. To learn more about the syntax of Java
B. To learn more about the features of the environment
C. To learn more about error handling
D. To learn more about abstractions
Answers
Answer:
The answer to this question is given below in the explanation section. The correct answer is B.
Explanation:
The purpose behind to explore an integrated development environment is to learn more about the features of the environment.
So the correct answer is B.
For example, you can use visual studio to build asp.net application using c#, then you need to explore what features visual studio offering to you.
However, other options are incorrect. Because, you can learn more about syntax, error handling, and abstraction in the programming language, not in the IDE.
Suppose you discover that you have a directory called bin2, which includes a bunch of useful programs. You want to move those programs into your bin directory, and then delete bin2. What command(s) will you give
Answers
Answer:
The MV command to move the bin2 directory to the bin directory.
Explanation:
Linux operating system uses a hierarchical arrangement of directories to organise information in its system.
It is an open source operating system with various built-in commands and other commands which can be made by a programmer.
The MV command takes a file or directory from a current directory and a destination directory.
Question One
a) The research department of De-mod Limited has developed a software at a cost of ten million cedi that is a game changer. In other to ensure total ownership and control of the software, you have been consulted to provide an advice on what De-mod Limited can do to maintain absolute ownership and control of the newly developed software.
With the knowledge you have acquired in this course, examine at least three protections for developers of computer software, stating the merits and demerits of each EV(7Marks)
Answers
The three protections for developers of computer software, are:
Patents Copyright and Trade secretsTrademarks.What are the different kinds of protection of computer software?The principal modes of protection of software is known to be copyright and patents. Copyright is said to be used a lot so as to protect computer program, this is due to the fact that writing of a code is one that tends to be similar to any other kinds of literary work.
Patents are known to be exclusive right of a person to make or produce, use their invention and thus The three protections for developers of computer software, are:
Patents Copyright and Trade secretsTrademarks.Note that the use of patent and copyright benefits a person as it tends to give them the power over their products and services.
Learn more about computer software from
https://brainly.com/question/1538272
#SPJ1
"As part of integrating your solution your client indicates that they have certain technologies enabled on their network that allows defined and flagged traffic to reach its source destination based upon the priority of the traffic. What does the client have enabled on their network
Answers
Answer:
quality of service
Explanation:
Hi!
i want to ask how to create this matrix A=[-4 2 1;2 -4 1;1 2 -4] using only eye ones and zeros .Thanks in advance!!
Answers
The matrix A=[-4 2 1;2 -4 1;1 2 -4] can be created by using the following code in Matlab/Octave:
A = -4*eye(3) + 2*(eye(3,3) - eye(3)) + (eye(3,3) - 2*eye(3))
Here, eye(3) creates an identity matrix of size 3x3 with ones on the diagonal and zeros elsewhere.
eye(3,3) - eye(3) creates a matrix of size 3x3 with ones on the off-diagonal and zeros on the diagonal.
eye(3,3) - 2*eye(3) creates a matrix of size 3x3 with -1 on the off-diagonal and zeros on the diagonal.
The code above uses the properties of the identity matrix and the properties of matrix addition and scalar multiplication to create the desired matrix A.
You can also create the matrix A by using following code:
A = [-4 2 1; 2 -4 1; 1 2 -4]
It is not necessary to create the matrix A using only ones and zeroes but this is one of the way to create this matrix.
Which scenario is the best example of intrinsic motivation?
Answers
The difference between reading a book because you have to write a report on it in order to pass a class and reading it because you like it and are interested in the subject or plot is intrinsic motivation.
What does the word "interested" mean?
Interest is defined as "wanting to know more about something." When someone is interested in something, they want to learn more about it, engage in it, or have the desire to do it or have it. These are a few examples of interested in use. One person's interest in another is expressed when they express a wish for them to have a romantic or sexual relationship.
To know more about intrinsic visit:-
https://brainly.com/question/15184439
#SPJ1
What is a digital security risks?
Answers
Answer:
A digital security risk is an action that could result in damage to a computer or similar device's hardware, software, data etc.
6.What does transgenic mean?
Answers
answer:
transgenic means that one or more DNA sequences from another species have been introduced by artificial means.
explanation:
transgenic plants can be made by introducing foreign DNA into a variety of different tissuestransgenic mice are one of the most common animal models usedrelating to or denoting an organism that contains genetic material into which DNA from an unrelated organism has been artificially introduced. being or used to produce an organism or cell of one species into which one or more genes of another species have been incorporated a transgenic mouse transgenic crops and produced by or consisting of transgenic plants or animals.
How do I build a computer where do I get the motherboard and stuff?
Answers
Answer:
Linus Tech Tips is a great place to learn building a PC. All PC parts are available via NewEgg and or other places such as Micro Center though there are more places those two are the best.
Explanation:
^^^
How does Wireshark differ from NetWitness Investigator?
Answers
Answer is given below
Explanation:
Wireshark differ from NetWitness Investigator because Windshark shows a detailed view of individual packets. WireShark captures live traffic and displays the results at the packet level. Netwitness shows a high-level view and can be compared to the new packet capture NetWitiness Investigator provides a comprehensive overview of previously tracked traffic that can be used to view anomalies, compliance and attacks.What makes a source credible?
It is found online.
It contains bias.
It is believable or trustworthy.
It supports multiple perspectives.
Answers
Answer:
C It is believable or trust worthy
Answer:
It's C: It is believable or trustworthy.
Explanation:
I got it right.
Write three tasks students can perform in a digital
classroom.
Answers
Answer:
Collaborating with peers through online forums, and meeting apps.
Ability to get more instructional materials and content from relevant websites and applications.
Students could undertake test, assignments online and monitor their progress in real time.
explain how production values can reveal the quality and accuracy of mass media.
Answers
Production values can reveal the quality and accuracy of mass media as it shows the total or full cost spent in making a quality film.
What are production values in mass media?Production value is known to be employed to know the full cost of making a film, and also the amount of money a film producer spent on props and special effects.
Note that by knowing the above, one can say that a given film reveal the quality and accuracy of mass media.
Learn more about production from
https://brainly.com/question/1501489
#SPJ1
reasons why you should add green computing:
Answers
Answer:
Green Computing aims to reduce the carbon footprint generated by the information systems business while allowing them to save money. Today there is a great need to implement the concept of Green computing to save our environment. About 60-70 percent energy ON and that consumed energy is the main reason of co2 emission
Explanation:
Hope it helps!
If you dont mind can you please mark me as brainlest?
Code HS pet names 2.3.5
Answers
Answer:
<!DOCTYPE html>
<html>
<head>
<title>Pet Names </title>
</head>
<body>
<h1>Favorite Animal<br> Names</h1>
<h2>Cats</h2>
<p>Lillith<br>Jasper<br>Oliver</p>
<hr>
<h2>Dogs</h2>
<p>
Captain Corgi Monster<br>
Buster<br>
Rover
</p>
</body>
</html>
Explanation:
Just pute this in