what are the contents of a .class file in java? a. a c source code program b. bytecodes c. all students in the cscs 212 class d. native machine instructions
Answers
The content of a .class file in Java are bytecodes. So, the option (b) is the correct choice of this question.
Bytecodes are the content of a .class file in java. And, .class file created by the java compiler that is based on .Java file. A .class file contains the bytecodes created by the Java compiler. Bytecodes are the binary program code in a .class file that is executable when run by JVM or Java Virtual Machine. Class files are bundled into .JAR files, which are included in the environment variable path for execution.
The class file can be compiled using the Java's javac command.
While the other options are incorrect because:
.Class file contains the bytecode, while .java file contains the source code program While the student in the cscs 212 class and native machine instructions dont relate to the context of the question. And, these are the irrelevant details.You can learn more about java .class file at
https://brainly.com/question/6845355
#SPJ4
Related Questions
Steeler corporation is planning to sell 100,000 units for 2.00 per unit and will break even at this level of sales fixed expenses will be 75,000 what are the company's variable expenses per unit
Answers
Answer:
1.25 per unit
Explanation:
Number of units to sell = 100,000
Price per unit = 2
Fixed expense = 75000
At break even point :
Revenue = total expenses
Total expenses = fixed cost + variable cost
Let variable cost = x
Revenue = units to sell * price per unit
Revenue = 100,000 * 2 = 200,000
Hence,
Fixed cost + variable cost = Revenue
75000 + x = 200,000
x = 200, 000 - 75000
x = 125,000
Variable cost = 125,000
The variable expense per unit is thus :
Variable expense / number of units
125,000 / 100,000 = 1.25 per unit
another way to express an algorithm is with pseudocode. true or false
Answers
True. Pseudocode is a method of expressing an algorithm using a combination of natural language and programming language-like constructs.
It is not tied to any specific programming language syntax and allows for a more informal and readable representation of an algorithm's logic.
Pseudocode is often used in the early stages of software development as a means of planning and describing the steps and logic of a program before actual coding takes place.
It serves as a communication tool between developers and can be easily understood by both technical and non-technical individuals. Pseudocode typically employs keywords, control structures, and variable names to outline the sequence of operations and decision-making processes within an algorithm.
Its purpose is to provide a clear and concise representation of the algorithm's logic, making it easier to understand and implement in actual code.
learn more about Pseudocode here:
https://brainly.com/question/13208346
#SPJ11
Which type of free software contains embedded marketing material within the program?
shareware
freeware
Spyware
adware
Answers
explain what a relational database to an elderly person is.
Answers
The term relational database been defined to an elderly person is that it is used to established relationships that is to organize data into one or more tables (or "relations") of columns and rows, relational databases make it simple to view and comprehend how various data structures relate to one another.
Why do we use relational databases?The consistency of the data is guaranteed via a relational database model for all users. As a result of everyone seeing the same information, understanding is improved throughout an organization.
For instance, it could be sensible to designate a separate box inside your toy box (database) to hold all of your dolls' heads and another box to hold their arms. Because it keeps track of which dolls' limbs and heads correspond to which dolls, that form of database is known as a relational database.
Learn more about relational database from
https://brainly.com/question/28119648
#SPJ1
in step 5 of this activity, you created the number canceled column to represent the total number of canceled bookings. what value was returned in this column?
Answers
To display the total number of canceled reservations, create a column called "number_canceled." Create a column with the name "average_lead_time" to serve as the average representation.
Column - what is it?
A relational database's columns are sets of data values of a specific type, one for each database row. Text values, numeric values, or even pointers to files in the operating system can all be found in a column. In a graph, table, or spreadsheet, a column is a vertical group of cells.
The Microsoft Excel spreadsheet shown below has the column letters A, B, C, D, E, F, G, and H for the column headers. As you can see in the illustration, the selected cell (D8) is in the D column, and the last column H is highlighted in red. a
To learn more about spreadsheet refer to:
brainly.com/question/4965119
#SPJ4
Answer:
44224
Explanation:
The number returned in this number_canceled column should be 44,224, which represents the total number of canceled hotel bookings. By cleaning and manipulating the data, you were able to answer an important question about it. Going forward, you can use what you know about data cleaning from past courses to help you learn how to clean data in R.
which type of server would support the smtp, pop, and imap protocols?which type of server would support the smtp, pop, and imap protocols?
Answers
The type of server that would support the SMTP (Simple Mail Transfer Protocol), POP (Post Office Protocol), and IMAP (Internet Message Access Protocol) protocols is a mail server or email server.
A mail server is responsible for sending, receiving, storing, and managing email messages. It acts as a central hub for email communication, handling the transmission of messages between email clients (such as Outlook, Thunderbird, or Apple Mail) and other mail servers. Here's a brief explanation of how each protocol is used in the context of a mail server:
1. SMTP (Simple Mail Transfer Protocol): SMTP is used for sending outgoing email messages from a sender's email client to the recipient's email server. It handles the routing and delivery of emails across different mail servers on the internet.
2. POP (Post Office Protocol): POP is a protocol used by email clients to retrieve email messages from a mail server. When an email client connects to a POP server, it downloads the messages from the server to the client device, and typically removes the messages from the server.
3. IMAP (Internet Message Access Protocol): IMAP is another protocol used by email clients to access email messages stored on a mail server. Unlike POP, IMAP allows clients to view and manage messages directly on the server, providing more advanced features such as synchronizing email across multiple devices, organizing folders, and searching for specific messages.
A mail server can support all three protocols simultaneously, allowing users to send outgoing emails using SMTP, retrieve messages from the server using POP, and access and manage email messages stored on the server using IMAP.
It's worth noting that modern mail servers often support additional protocols and technologies such as SMTPS (SMTP over SSL/TLS) for secure email transmission, POP3S (POP3 over SSL/TLS), and IMAPS (IMAP over SSL/TLS) for secure communication between the client and server.
To know more about mail server, please click on:
https://brainly.com/question/27785432
#SPJ11
A Mail Server supports the SMTP, POP, and IMAP protocols. These protocols allow for the sending and receiving of email communications.
Explanation:The type of server that would support the SMTP, POP, and IMAP protocols is a Mail Server. SMTP (Simple Mail Transfer Protocol) sends emails from the email client to the email server or between servers. POP (Post Office Protocol) and IMAP (Internet Message Access Protocol) are used by the email client to retrieve an email from the Mail Server. SMTP is for sending mails while POP and IMAP are for receiving mails.
Learn more about Mail Server here:https://brainly.com/question/32366924
What is the purpose of the 300 Log?
Answers
Answer:
The OSHA Form 300 is a form for employers to record all reportable injuries and illnesses that occur in the workplace, where and when they occur, the nature of the case, the name and job title of the employee injured or made sick, and the number of days away from work or on restricted or light duty, if any.
Explanation: brainliest plzzzz!
which one of the following does the same thing as line 2 of the following code?1. for (int i = 0; i < 400; i) {2. lst.add(i);3. }
Answers
The code that does the same thing as line 2 of the provided code snippet is lst.add(i). However, this line of code alone will not create the desired loop without additional code.
Which one of the following pieces of code does the same thing as line 2 of the provided code snippet? The answer lies in understanding what the code is doing. The code is creating a loop that will run as long as the variable i is less than 400. However, the variable i is not being incremented within the loop, meaning that the loop will run infinitely.
The second line of code, lst.add(i), adds the value of i to a list called "lst". So, the question is asking which piece of code also adds the value of i to a list.
There are a few options for code that accomplish this task, but one possible solution is:
List lst = new ArrayList<>();
for (int i = 0; i < 400; i++) {
lst.add(i);
}
This code creates a new list called "lst", then loops through values of i from 0 to 399, incrementing i by 1 each time. Within the loop, it adds the current value of i to the list using the lst.add(i) method, which is the same as line 2 of the original code.
In summary, the code that does the same thing as line 2 of the provided code snippet is lst.add(i). However, this line of code alone will not create the desired loop without additional code.
Learn more on snippets here:
https://brainly.com/question/31956984
#SPJ11
What is the power of 3 shch that it's power is 1/3 ?
Answers
Answer:
3/1-1
Explanation:
someone please tell me if you watch drag race (rupauls drag race) I need someone to talk to about it
Answers
at the moment, the job column of the sf table is not sorted (no particular order). would the arrays you generated in the jobs column of the previous question be the same if we had sorted alphabetically instead before generating them? explain your answer. to receive full credit, your answer should reference how the .group method works, and how sorting the jobs column would affect this.
Answers
No, the arrays generated in the jobs column of the previous question would not be the same if the job column was sorted alphabetically before generating them.
Sorting the job column would change the order in which the jobs appear, which would in turn change the order in which they are added to the arrays.For example, if the original job column had the following jobs in order: "teacher", "engineer", "doctor", "teacher", "programmer", "doctor", "nurse", "teacher", the corresponding arrays generated in the previous question might be [3, 1, 2, 3, 4, 2, 5, 3] for job_count and ["teacher", "engineer", "doctor", "programmer", "nurse"] for job_names. If the job column were sorted alphabetically before generating these arrays, the resulting arrays might be different, depending on the order in which the jobs appeared after sorting.To know more about arrays visit:
https://brainly.com/question/13950463
#SPJ1
Computer 1 on network b with ip address of 192.168.1.233 wants to send a packet to computer 2 with ip address of 10.1.1.205 on which network is computer 2
Answers
It is evident from the IP addresses that computer 1 is connected to network 192.168.1.0/24 and computer 2 is connected to network 10.1.1.0/24, but it is unclear whether these networks are directly connected.
What network protocol is used to give a computer on a network an IP address automatically?Protocol for Dynamic Host Setup An IP network device that has been automatically configured using the Dynamic Host Configuration Protocol (DHCP), a network management protocol, can access network services including DNS, NTP, and any protocol based on UDP or TCP.
In what command is an IP dispute resolved?Press Enter after entering the command ipconfig/ lushdns. Your device's DNS configurations are updated as a result.
To know more about IP addresses visit:-
https://brainly.com/question/16011753
#SPJ1
6.What connection type is known as "always on"?
Broadband
Ethernet
Plain Old Telephone System (POTS)
Internet
8.What connection type is known as "always on"?
Broadband
Ethernet
Plain Old Telephone System (POTS)
Internet
9.In which wireless configuration type do nodes communicate directly with each other, rather than with an access point?
Ad-hoc
Mesh network
2.4Ghz
802.11b
Answers
The connection type that known as "always on" is Plain Old Telephone System (POTS). The wireless configuration type do nodes communicate directly with each other is Ad-hoc.
POTS or Plain Old Telephone system is a traditional system for analog voice transmission phone system by using the physical copper wires. Because this using connection of physical copper wires, it be called as "always on" connection.
Ad-hoc is the wireless connection that formed spontaneously in LAN. Ad-hoc doesn't need access point such as router to communicate, since the computer in ad-hoc connection will communicate directly to each other.
Learn more about ad-hoc here:
brainly.com/question/29315237
#SPJ4
A pointing device that has a laser guide on its underside and two or more buttons for clicking commands; you control the movement of the pointer by moving the entire thing around on your desk.
Answers
Joe's computer crashed and I was looking for a replacement which of the following criteria is less important.Ram,money, color, usage
Answers
Answer:
color
Explanation: nobody cares what color it is how it works
Colour is the less criteria as Joe's computer crashed, and he was looking for a replacement. Hence, option C is correct.
What is meant by computer crashed?A computer crash occurs when an operating system or program stops functioning properly. When: Hardware has had an irreparable failure.
Computer crashes are the result of hardware or operating system errors. Even though software errors are unquestionably more common, hardware errors can still be quite harmful and are more difficult to spot. A computer cannot function if certain hardware components are malfunctioning.
A crash or system crash occurs when a computer program, such as an operating system or software application, stops functioning properly and exits. A computer cannot operate without a number of hardware parts working properly.
Thus, option C is correct.
For more details about computer crashed, click here:
https://brainly.com/question/4701800
#SPJ2
Which letter is immediately to the right of the letter that comes midway between the letter two to the right of the letter A and the letter immediately to the left of letter H?
ABCDEFGH
• B
• C
• E
• F
• G
Answers
F: The letter two to the right of the letter A is C, and the letter immediately to the left of letter H is G. The letter midway between C and G is E, so the letter immediately to the right of E is F.
What is midway ?Midway is a term used to describe a point halfway between two places, or a point that marks the middle of a journey. It can also refer to a point in a race or a conflict where the two sides are nearly equal in strength or numbers. In a broader sense, the term is used to express a point in a journey or situation when some kind of significant change has occurred. This can be a change in the direction of a conversation, a change in the dynamics of a group, or a change in the strategy of an event. In any situation, a midway point serves to mark the progress of a journey or process, and to signal a shift in the situation.
To learn more about midway
https://brainly.com/question/28498043
#SPJ1
Understand different customer types and analyze how customers make buying decisions.
Answers
There are several types of customers, such as individual consumers, businesses, government agencies, and non-profit organizations.
What are their characteristics?Each customer type has unique characteristics and factors that influence their buying decisions. Individual consumers often make buying decisions based on personal preferences, brand reputation, and price.
Businesses focus on the quality, cost, and reliability of products and services, as well as the potential return on investment.
Government agencies consider factors such as budget constraints, regulations, and the ability to meet specific needs.
Non-profit organizations often prioritize the impact and social responsibility of their purchasing decisions.
Ultimately, customers make buying decisions based on a combination of rational and emotional factors that align with their goals and values.
Read more about customers here:
https://brainly.com/question/26313265
#SPJ1
It is early in the season and the night of the big football rivalry game, and you are so excited to spend time with friends and watch your boyfriend play ball. However, you are assigned to one of the football spreads and must take pictures. What do you do?
Answers
Answer:
take the pictures while watching him play
Explanation:
what does the /a switch used with the copy command indicate
Answers
The "/a" switch used with the copy command in Windows indicates that the copy operation should be performed in ASCII mode. It is used to specify the type of data being copied, indicating that the file being copied contains ASCII characters rather than binary data.
When the "/a" switch is used, the copy command treats the source file as an ASCII text file and performs certain conversions during the copy process. It ensures that the line endings and formatting of the text file are preserved when copying from one location to another. For example, when copying a text file from a source directory to a destination directory, using the "/a" switch ensures that the text file is copied in its original format, without any unintended changes due to differences in line endings or encoding between the source and destination systems. The "/a" switch is particularly useful when copying text files between different platforms or when preserving the formatting and integrity of text files is important. It allows for accurate and reliable copying of ASCII text files while maintaining their intended structure and content.
Learn more about ASCII mode here:
https://brainly.com/question/14006860
#SPJ11
Working with text in presentation programs is very ____
using text in other applications.
a) similar to
b)different from

Answers
Answer:
a) similar to
Explanation:
Answer: it is A
Explanation: Your inquiry states that "Working with text in presentation programs is very ____ using text in other applications." Working in presentation software such as Microsoft PowerPoint and Microsoft Word, is very different. Microsoft PowerPoint allows you to do so much more on the visuals, Microsoft PowerPoint and other presentation software also has capabilities to present information than displaying it in a text-editor.
pls make me branliest
You purchase a new microphone for your computer to use on S.kype calls. You plug it into the microphone jack, but it doesn’t pick up your voice when you speak into it. What might you need to add to your computer to make it work?
A
firmware
B
a device driver
C
open source software
D
a software license
Answers
Answer:
B
Explanation:
Your computer may not have a pre-installed audio input driver or driver corrsponding to said device
guys tell the answer correctly
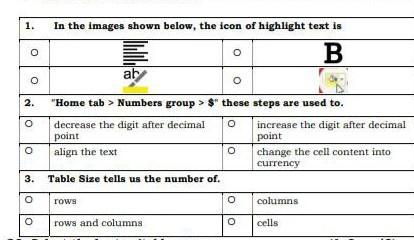
Answers
Answer:
1st ans: where u can see yellow colored line
2nd ans: currency one
3rd ans: cells
Explanation:
A database of students is to be set up with the following fields.
Family name
Others name
Student ID
DOB
Date of entry to school
Current Class
Current School Year/Grade
Email Address
Which field would be the primary key and choose a suitable format for the student ID
Answers
Answer:
primary key is the family name i think
Explanation:
Is a pencil sharpener and open system or a closed system? Defend your answer.
Answers
Answer:
A second class lever has the load located in the middle and the fulcrum and the effort on opposite ends. Examples of second class levers: a wheelbarrow, hand truck, wrench, nutcracker, and the handle to a pencil sharpener. A third class lever has the effort in the middle with the load and fulcrum on opposite ends.
All of the following is the wiring of front panel EXCEPT ONE. A. Power supply b. Reset sw c. Hard drive d. Optical drive
Answers
From the choices, the part that on not wiring of front panel is:
d. Optical drive
The front panel of a computer usually includes buttons and connectors that provide quick access to various components and functions of the system. The wiring of the front panel typically includes the following:
A. Power supply: A button to turn the power supply on or off.
B. Reset switch: A button to reset the system.
C. Hard drive: A light that indicates when the hard drive is active and a button to safely eject the hard drive.
D. Optical drive: This component is not typically wired to the front panel, as the optical drive is usually connected to the motherboard internally.
So, the wiring of front panel does not include the optical drive.
Learn more about Optical drive:
brainly.com/question/23196272
#SPJ4
1. This are tools used to make any presentation interesting and exciting.
a. audio and video
c. hyperlinks
b. animations
d. text and graphics
Answers
Answer:
c. hyperlinks
Explanation:
The correct option is - c.hyperlinks
Reason -
The "hyperlink" function in PowerPoint allows users to advance from one slide to another slide in the presentation when they click on a predetermined word, shape, or image, thereby allowing for a more dynamic and interactive experience than can be obtained with serial presentation of slides alone.
Edmentum Question- Consumer and Credit Loans
When would someone be restricted from filing for bankruptcy?
A. if the debtor fails the asset test
B. if the debtor fails the income-liability test
C. if the debtor fails the credit-overload test
D. if the debtor fails the means test
Answers
Answer:
D, if the debtor fails the means test
Explanation:
i took the test on platos and got it right
______ are small text files that websites place on your computer to record your online activities
A. IP addresses
B. Viruses
C. Cookies
D. Brownies
Answers
Explain how command driven and menu driven user interface is in (a) function
Answers
In terms of function, a command-driven user interface is more efficient for experienced users who are familiar with the system and the available commands, but it can be less accessible for new or inexperienced users.
What is the user interface about?A command-driven user interface and a menu-driven user interface are both used to interact with computer systems, but they differ in their approach to input and interaction.
A command-driven user interface operates using text-based commands entered by the user in a terminal or command prompt. In this type of interface, the user is expected to have a certain level of knowledge about the system and the available commands.
Therefore, one can say that a menu-driven user interface, on the other hand, provides a graphical interface with a series of menus and options to choose from. The user selects options from the menus to interact with the system and initiate actions.
Learn more about user interface at:
https://brainly.com/question/17372400
#SPJ1
Which type of network activities are handled by the presentation layer of the osi model?
Answers
The presentation layer of the OSI model is responsible for managing the formatting and encryption of data exchanged between applications. It handles network activities such as data translation, compression, encryption, and decryption.
Here are some specific network activities handled by the presentation layer:
1. Data formatting: The presentation layer ensures that data is presented in a format that is understandable by the receiving application. For example, it may convert data from ASCII to Unicode or vice versa.
2. Data compression: The presentation layer compresses data to reduce the amount of data that needs to be transmitted over the network. This can help improve network performance and reduce bandwidth usage.
3. Encryption and decryption: The presentation layer can encrypt data before sending it over the network and decrypt it at the receiving end. This ensures data confidentiality and security during transmission.
4. Data syntax validation: The presentation layer checks the syntax and structure of data to ensure it is correct and compatible with the receiving application.
In summary, the presentation layer of the OSI model handles activities such as data formatting, compression, encryption, decryption, and syntax validation to ensure smooth communication between applications.
To know more about network activities visit:
https://brainly.com/question/27629086
#SPJ11