what 4 settings on the ip4 page are needed for a network device to connect to the internet on your soho
Answers
To connect a network device to the internet in a Small Office/Home Office (SOHO) setting, four settings on the IPv4 page are typically required: IP address, subnet mask, default gateway, and DNS server addresses.
The IP address is a unique identifier assigned to the device on the network. It distinguishes the device from others and allows communication with other devices. The subnet mask determines the network portion and the host portion of the IP address. It helps in routing packets within the network.
The default gateway is the IP address of the router or gateway that connects the local network to the internet. It acts as the entry point for all outgoing network traffic destined for external networks. Finally, DNS (Domain Name System) server addresses are used to translate domain names (e.g., www.example.com) into IP addresses. DNS allows devices to locate and communicate with other devices using human-readable domain names.
When configuring a network device, you need to assign a valid IP address within the network's range, set the appropriate subnet mask to define the network boundaries, specify the default gateway as the router's IP address, and configure at least one DNS server address to enable domain name resolution.
In summary, to connect a network device to the internet in a SOHO setting, you need to configure the IP address, subnet mask, default gateway, and DNS server addresses on the IPv4 settings page. These settings ensure proper network communication, routing, and domain name resolution for the device.
To learn more about default gateway, click here:
brainly.com/question/30198951
#SPJ11
Related Questions
what is Human Dignity
Answers
Answer:
what is human dignity
Explanation:
The English word dignity comes from the Latin word, dignitas, which means “worthiness.” Dignity implies that each person is worthy of honor and respect for who they are, not just for what they can do. ... In other words, human dignity cannot be earned and cannot be taken away.
repeating groups must be eliminated by making sure that each column defines a single entity. True or false ?
Answers
True as eliminating repeating groups is an important part of database design. It can help to improve the efficiency, consistency, and usability of your database.
Repeating groups are groups of data that are stored in a single column, but that represent multiple entities. For example, a table of employees might have a column for "children," and each row might have multiple children listed. This is an example of a repeating group, because each row represents a single employee, but the "children" column contains data for multiple children.
Repeating groups can cause a number of problems, including:
Data redundancy: Data redundancy occurs when the same data is stored multiple times in a database. This can waste space and make it difficult to keep the data consistent.
Difficulty updating data: If you need to update data in a repeating group, you need to update it in every row that contains the data. This can be time-consuming and error-prone.
Difficulty querying data: It can be difficult to query data in a repeating group, because you need to know how many rows contain the data you are looking for.
To eliminate repeating groups, you can use a process called normalization. Normalization is a process of organizing data in a database so that it is consistent, efficient, and easy to use. One of the steps in normalization is to break up repeating groups into separate columns. For example, the "children" column in the employee table could be broken up into two columns: "number of children" and "child names."
Eliminating repeating groups is an important part of database design. It can help to improve the efficiency, consistency, and usability of your database.
To learn more about Database, visit here:
https://brainly.com/question/518894
#SPJ11
Pedro needs to write a block of code that will repeat a loop six times. Which type of loop should he use?
O for
O else
O else if
O while
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
Petro needs to write a block of code that repeats six times. The given options in this question that what should he use to implement the six times a block of code are:
for else else if whileThe correct option to this question is: 1 -for-loop.
So, Pedro needs to use for-loop to write a block of code that will repeat a loop six times. Because when you use for-loop, you know how many iterations are in a loop to execute a block of code. So in this case, the number of iteration is known. Therefore, Pedro needs to use for-loop.
While other options are not correct because:
Else and else are used to make decisions, these are not used to repeat a block of code. These are code branching statements in simple words. While while-loop is used to iterate/loop a block of code but when you don't know the exact number of repetitions.
Answer:
for loop
Explanation:
sorry im late
which statements compares the copy and cut commands
Answers
The statement that accurately compares the copy and cut commands is 2)Only the cut command removes the text from the original document.
When using the copy command, the selected text is duplicated or copied to a temporary storage area called the clipboard.
This allows the user to paste the copied text elsewhere, such as in a different location within the same document or in a separate document altogether.
However, the original text remains in its original place.
The copy command does not remove or delete the text from the original document; it merely creates a duplicate that can be pasted elsewhere.
On the other hand, the cut command not only copies the selected text to the clipboard but also removes it from the original document.
This means that when the cut command is executed, the selected text is deleted or "cut" from its original location.
The user can then paste the cut text in a different place, effectively moving it from its original location to a new location.
The cut command is useful when you want to relocate or remove a section of text entirely from one part of a document to another.
For more questions on cut commands
https://brainly.com/question/19971377
#SPJ8
Question: Which statement compares the copy and cut commands?
1. only the copy command requires the highlighting text
2. only to cut command removes the text from the original document
3. only the cut command uses the paste command to complete the task
4. only the copy command is used to add text from a document to a new document
The set of instructions that tells a computer
what to do is called:
Motherboard
Hardware
Keyboard
Softwarling
Answers
Answer:
The answer is the Motherboard
Explanation:
Answer:
Motherboard
Explanation:
When should students in a study session use flash cards to quiz one another ?
Answers
Answer:
while drilling
Explanation:
Where can you find the sizing handles for a graphic, shape, or text box? Check all that apply.
at the top left corner of the document
at the top right corner of the document
in the center of the graphic, shape, or text box
on the edges of the graphic, shape, or text box
on the corners of the graphic, shape, or text box
inside the borders of the graphic, shape, or text box
Answers
Answer:
D and E
Explanation:
Just took it
Answer: the answer are d:on the edges of the graphic, shape, or text box and e:on the corners of the graphic, shape, or text box
Explanation:

Which method deletes a footer from a document?
Double-click the footer region and delete all the content in the Footer.
Click on the Insert tab on the ribbon, click the Footer button, and select Remove Footer from the list.
Double-click the footer region; under the Design tab in the Header & Footer group, click on the Footer button and select Remove Footer from the list.
All the above are methods for deleting a footer from a document
Answers
Compare the features of static and dynamic computing environments and then select the accurate statements.
a. Embedded systems are typically static, while most personal computers are dynamic.
b. A dynamic environment is easier to update than a static environment.
c. A dynamic environment gives less control to a user than a static environment.
d. Dynamic environments are easier to protect in terms of security than static environments
Answers
Compare the features of static and dynamic computing environments are options A and B:
Embedded systems are typically static, while most personal computers are dynamic.A dynamic environment is easier to update than a static environment.What is a static environment computer?A static environment is a group of circumstances, activities, and surroundings that remain constant. Once understood, a static environment doesn't provide any novel or unexpected elements. Any system that users and administrators desire to keep unmodified belongs in a static IT environment.
Note that Leading managed IT service, IT consultancy, and cyber security provider Dynamic Computing serves high-performing businesses. Our customers are small to medium-sized enterprises located locally, regionally, and nationally.
Learn more about computing environments from
https://brainly.com/question/28606168
#SPJ1
a division of a hard drive may be referred to as a
Answers
A division of a hard drive may be referred to as a "partition." A partition is a segment of the hard drive that is separated and treated as an independent storage unit. This allows for better organization and management of data on the hard drive.
In the context of computer storage, partition refers to dividing a physical storage device, such as a hard drive or solid-state drive (SSD), into multiple logical sections or divisions. Each partition acts as a separate unit with its own file system, allowing it to be used independently for data storage and organization.
Here are a few key points about partitions:
1. Purpose: Partitioning a storage device allows for better organization, management, and utilization of storage space. It enables users to separate different types of data, install multiple operating systems on the same device, or create dedicated storage areas for specific purposes.
2. Partition Types: There are different types of partitions, including primary partitions, extended partitions, and logical partitions. Primary partitions are typically used for bootable operating systems, while extended partitions can be subdivided into logical partitions for additional data storage.
3. File Systems: Each partition is typically formatted with a specific file system, such as FAT32, NTFS (Windows), or APFS (macOS). The choice of file system determines how data is stored, accessed, and organized on the partition.
4. Partitioning Tools: Operating systems often provide built-in partitioning tools, such as Disk Management in Windows or Disk Utility in macOS, to create, modify, or delete partitions. There are also third-party partitioning software options available with advanced features and flexibility.
5. Partition Table: A partition table is a data structure that stores information about the partitions on a storage device. Common partition table formats include Master Boot Record (MBR) and GUID Partition Table (GPT), which dictate how the partitions are recognized and accessed by the system.
It's important to note that partitioning a storage device involves modifying its structure, which can result in data loss if not done correctly or without proper backups. It's recommended to exercise caution and follow appropriate guidelines or consult professional assistance when performing partitioning operations.
Learn more about SSD:https://brainly.com/question/28476555
#SPJ11
What is the subnet id associated with the ipv6 address 2001:da48:fc5:a4:3d1b::1/64?
Answers
The subnet ID associated with the IPv6 address 2001:da48:fc5:a4:3d1b::1/64 can be determined by looking at the prefix length of the address.
In this case, the prefix length is /64, which means the first 64 bits of the address are the network prefix. The subnet ID is obtained by removing the host bits from the address, leaving only the network prefix.
In this example, the subnet ID is 2001:da48:fc5:a4::/64.
The subnet ID represents the network portion of the address and is used to identify devices within the same network. It is important to note that the subnet ID is determined by the prefix length and can vary depending on the specific network configuration.
By understanding how the subnet ID is derived from the IPv6 address and prefix length, you can effectively analyze and manage network addressing in IPv6 environments.
To know more about length visit:
https://brainly.com/question/32060888
#SPJ11
Systems that are used by companies to keep a track of attendance primarily in order to pay their wages.
i. Human resoure OR ii. Payroll System OR iii. Attendance
PICK THE CORRECT ANSWER.
Answers
Answer:
option no.3 Attendance
many transportation systems, such as the washington, d.c., metro (subway), charge higher fares during rush hours than during the rest of the day. why might they do this?
Answers
Many transportation system, such as the Washington, D.C., metro (subway), charge higher fares during rush hours than during the rest of the day because, during these hours, the transportation demand is higher than the supply. The cost of transporting people during rush hour is higher than during other times.
The cost of providing transportation is linked to the level of demand for the service. The peak hour fares assist to decrease overcrowding and distribute the burden of transporting people at peak times. The objective of charging higher fares at peak hours is to discourage people from commuting during those hours and to encourage people to commute during the off-peak hours.
This is to make it simpler and more pleasant for commuters to get on and off trains and buses during non-peak hours as well as to incentivize them to travel during off-peak hours to reduce congestion on the system.
To know more about transportation
https://brainly.com/question/27667264
#SPJ11
Need help with my hw.

Answers
Name the first computer brought in Nepal
Answers
Answer:
IBM 1401.Explanation:
The first computer introduced in Nepal was IBM 1401.
PLEASE MARK ME BRAINLIEST.Which snippet of code is in XML?

Answers
Answer:
The top left
Explanation: It uses XML Syntax
Answer: Bottom left '<cd>'
Explanation:
PLAYTO i got it right
How did inventors like lee deforest and edwin howard armstrong fund their initial research and development ventures into radio technologies?.
Answers
Government financing was provided for Marconi (England = public mandate; taxes)
- The United States raised funds from investors in capital.
What is meant by radio technologies?Radio technology, the transmission and reception of communication signals made of of electromagnetic waves that bounce off the ionosphere or a communications satellite or pass through the air in a straight line.
Radio broadcasts that are available 24 hours a day and provide real-time information allow listeners to acquire the most latest news. Radio has the ability to cross international borders and can be a valuable source of news in places where reputable news is difficult to come by.
Radio equipment requires electromagnetic waves to transmit and receive in order to function. The radio signal is an electrical current that moves very quickly. An antenna is used by a transmitter to broadcast this field; a receiver takes it up and transforms it into the audio heard on a radio.
The complete question is : How did inventors like Lee Deforest and Edwin Howard Armstrong fund their initial research and development ventures into radio technologies? How was this different from the funding used by inventors like Guglielmo Marconi in Europe?
To learn more about radio technology refer to:
https://brainly.com/question/4348815
#SPJ1
A column of data in a table is known as a: A Tuple B Field с Key Кеу D. Row
Answers
Answer:
B. Field
Explanation:
Pretty sure i remember this from a computers class.
Answer:
B. Field
Explanation:
Your answer should be B. Field
I hope it helps!
Muffin<3
each entity in a database has a unique attribute called a(n) . group of answer choices identifier index field foreign key public key
Answers
Answer: index field
Explanation:
MARK BRAINLIEST PLS
Describe the shorthand representation of the structure of a relational database. Why is it important to be able to represent the structure of a database in a shorthand fashion
Answers
The shorthand representation is used to depict the database table in an easier way or manner.
What is the shorthand representation?A symbol is known to be a kind of shorthand representation for the object of a specific structure.
Note that the shorthand representation is used to depict the database table in an easier way or manner. as one can be able to do things easily because there is a short cut.
It is known to tell or address the Database table in a simple and reasonable way with ease of utilization.
Learn more about Database from
https://brainly.com/question/26096799
#SPJ1
You use the ____ option with the dcfldd command to designate a hashing algorithm of md5, sha1, sha256, sha384, or sha512.
Answers
When utilizing the dcfldd command, one uses the `hash=` option to define a hashing algorithm of md5, sha1, sha256, sha384, or sha512. This command can be used to create a bit-by-bit image of a disk or to clone disks utilizing the input-output device file (`/dev/sda`) and the output file (`/mnt/backup/image.dd`).
When cloning disks, dcfldd writes the input file to the output file as it reads it, enabling the creation of perfect clones of the input file. Because it is useful for forensic and data recovery applications, the command also includes a variety of checksum, hash, and message digest algorithms that may be used to guarantee data integrity and authenticity. The `hash=` option allows users to specify which hashing algorithm to use.
It can be specified as `hash=md5`, `hash=sha1`, `hash=sha256`, `hash=sha384`, or `hash=sha512`.In conclusion, when utilizing the dcfldd command, one uses the `hash=` option to define a hashing algorithm of md5, sha1, sha256, sha384, or sha512.
To know more about input visit:-
https://brainly.com/question/29310416
#SPJ11
which tool is used to terminate cables into a 66-block
Answers
Answer: Circuit pairs are connected to the block with a punch-down tool by terminating the tip wire on the leftmost slot of one row and ring wire on the leftmost slot of the row beneath the mating tip wire.
Make a list of symptoms of computer virus and preventive measures from computer virus.
Answers
Answer:
Intrusive pop-ups. Slow performance. Frequent crashes. Unknown login items. Storage space shortage. Missing files.
Explanation:
those are symptoms
Does anyone know the answer for 4.2 Code Practice: Question 1 on edhesive
Answers
Answer:
Question 1
sum=0
count=0
while(sum<=100):
x=int(input("Enter a nmber"))
sum=sum+x
count=count+1
print("Sum: "+str(sum))
print("Numbers Entered: "+str(count))
Question 2
count = 0
pet = (input("What pet do you have? "))
while(pet != "rock"):
count = count +1
print("You have a " + pet +" with a total of " + str(count) + " pet(s)")
pet = (input("What pet do you have? "))
Explanation:
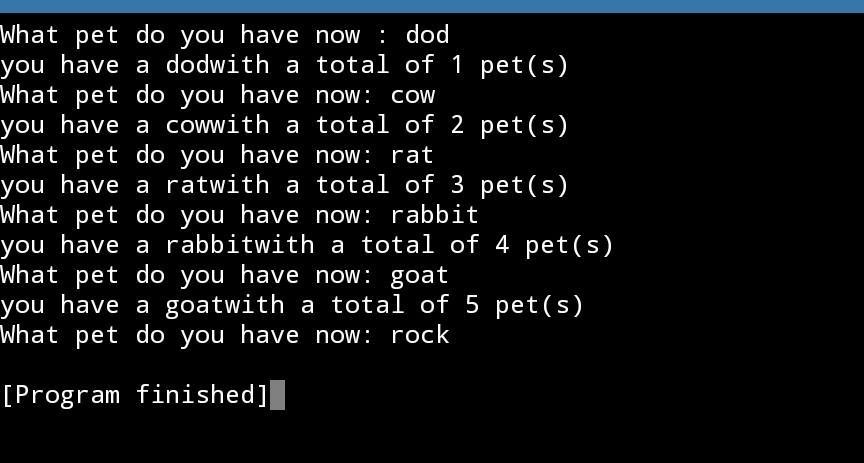
The required program written in python 3 which continues to request user to input a pet name until a rock is entered is as follows :
pet = input('What pet do you have now : ')
#request an input from the user and store in the variable pet
total = 0
#initialize the total number of pets owned to 0
while (pet != 'rock'):
#while loop ensures that program runs until a rock is inputted by the user
total +=1
#adds one to the total after each loop
print('you have a ' + str(pet) + 'with a total of ' + str(total) + ' pet(s)')
#displays the formatted string using the total and pet variables which continues to update
pet = input('What pet do you have now: ')
#requests user to input pet name again as long as rock has not been supplied.
Therefore, an output of the program written is attached below.
Learn more on python programs :https://brainly.com/question/18685986
What are some technical challenges and questions that arise from the need to represent digital information in computers and transfer it between people and computational devices?
Answers
Answer:
security
Explanation:
One technical issue that arises from this is security. Many times the information that is being transferred is private or even valuable, therefore grabbing the attention of hackers/thief's that want this information. This makes security highly important, but making sure that the information is completely secure is impossible. The best that can be done is adding certain safety measures to secure the information as much as possible, which in term is a technical challenge.
HELP I NEED THIS ASAP!!!!!!!
If you want to apply the same custom tab stops for a group of paragraphs that already exist, what should you do?
Select one paragraph, create its tab stops, then select the next paragraph and create its tab stops, and so on.
Delete the paragraphs, create the tab stops, and then retype the paragraphs.
Preselect all of the paragraphs and then apply tab stops.
Change the default tab stops for the entire document.
Answers
Answer:
Preselect all of the paragraphs and then apply tab stops.
Explanation:
In a deed in lieu of foreclosure situation, A) the lender takes the real estate subject to all junior liens. B) the lender is obligated to accept the deed. C) all encumbrances on the property are extinguished. D) a civil action is required.
Answers
In a deed in lieu of foreclosure situation, the lender is obligated to accept the deed and takes the real estate subject to all junior liens.
However, all encumbrances on the property are not necessarily extinguished, as there may be senior liens or other claims that still exist. No civil action is required, but it is important to consult with legal counsel to understand all the potential implications of a deed in lieu of foreclosure.
In a deed in lieu of foreclosure situation, option A) is correct. The lender takes the real estate subject to all junior liens. This means that any subordinate liens on the property remain intact and become the responsibility of the lender. Option B) is incorrect, as the lender is not obligated to accept the deed and can choose other remedies. Option C) is also incorrect, as all encumbrances are not extinguished; only the primary mortgage is settled. Finally, option D) is incorrect, as a civil action is not required for a deed in lieu of foreclosure, as it is a voluntary agreement between the borrower and lender to avoid foreclosure proceedings.
To know more about liens visit:
https://brainly.com/question/14392036
#SPJ11
what is displayed as a result of executing the following code segment?
x < - - 2
y < - - X * 4
z < - - X * Y
x < - - X + Y
z < - - z + ( x - y) * 3
DISPLAY ( x + y + z)
select one answer
A - 72
B - 40
C - 8
D - 54
Answers
Which type of address is the ip address 232. 111. 255. 250?.
Answers
Edhesive 4.2 question 2 answers
Answers
Answer:
total=0
pet=input("what pet do you have? ")
while pet!= "rock":
total=total+1
print("you have a "+pet+" with a total of "+ str(total)+ " pet(s)")
pet=input("What pet do you have? ")
Explanation: Just copy and paste above again just copy and paste this will get you a 100 percent i made another account just to give yall edhesive answers if yall need help with any edhesive just comment below