We'll say that a triple in a string is a character that appears three times in a row. Triples may overlap. For example, the string 'AAAxBBBBxyz' contains three triples. Write code that counts the number of triples in a string named text and stores the result in a variable named triple_count. Assume that the variable text already has a value.
Answers
The code counts the number of triples in a given string, stored in the variable "text," and stores the count in the variable "triple_count."
To count the number of triples in the string "text," we can iterate over the characters in the string using a loop. For each character at index "i" in the range from 0 to the length of the string minus 2, we check if the character at index "i" is the same as the character at index "i+1" and also the same as the character at index "i+2." If all three characters are the same, we increment the "triple_count" variable by 1.
After iterating through the entire string, the "triple_count" variable will contain the total count of triples in the string. The code snippet below demonstrates this logic:
text = "AAAxBBBBxyz"
triple_count = 0
for i in range(len(text) - 2):
if text[i] == text[i+1] == text[i+2]:
triple_count += 1
print(triple_count)
In this example, the output will be 3, as the string "AAAxBBBBxyz" contains three triples: "AAA," "BBB," and "xxx."
LEARN MORE ABOUT string here: brainly.com/question/30099412
#SPJ11
Related Questions
You will watch the short film Figueroa (2019) written, produced, and directed by Victor Hugo Duran. Then answer the following questions:
1. What kind of choices does Duran make in how he covers the scenes? Do you notice a pattern in the kinds of shots he uses?
2. Why do you think he uses the 2.4:1 aspect ratio? What does it do for his story?
3. Why do you think he holds the final shot for so long? How do you think the ending would be different if the shot was only half as long (before the credits come on).
Answers
The kind of choices that Duran makes in how he covers the scenes is
What is a Movie Synopsis?This refers to the brief summary of a screenplay's core content that shows its plot points, conflict, resolution and protagonist's development, etc.
The reason why I think he uses the 2.4:1 aspect ratio is that he wants to cover the action from a wider angle to capture all the actions and activities of the characters.
The reason why I think he holds the final shot for so long is to show the empty room after the two boys had run off.
The ending would have been different if it was half as long because some other story element could have been displayed.
Read more about movie synopsis here:
https://brainly.com/question/1661803
#SPJ1
what are the three data types that we are able to input from the keyboard?
Answers
The three data types that we can input from the keyboard are:
1. Integer
2. Floating-Point
3. String:
The three data types that we can input from the keyboard are:
1. Integer: This data type represents whole numbers without decimal points. Examples of integer input would be 10, -5, or 0.
2. Floating-Point: This data type represents numbers with decimal points. Examples of floating-point input would be 3.14, -2.5, or 0.0.
3. String: This data type represents a sequence of characters. String input can include letters, numbers, and special characters.
Examples of string input would be "Hello", "123", or "#$%".
Learn more about Data type here:
https://brainly.com/question/30781353
#SPJ4
Consider the following instance variables and method from a class: private String descriptor; public String makeSentence(int quant, boolean sign) { String s = "Object is "; if (!sign) { s += "not "; } for (int i = 0; i < quant; i++) { s += "very "; } return s + descriptor; } Suppose an object of this class is initialized so the value of descriptor is "regular". What would be returned by the call makeSentence(3, false) made on this object?
Answers
The call makeSentence(3, false) will return
"Object is not very very very regular"
The program fragment is:
///////////////////////////////////////////////////////////////////////////////////////////////////////////////
private String descriptor;
public String makeSentence(int quant, boolean sign) {
String s = "Object is ";
if (! sign) {
s += "not ";
}
for (int i = 0; i < quant; i++) {
s += "very ";
}
return s + descriptor;
}
///////////////////////////////////////////////////////////////////////////////////////////////////////////////
descriptor is an instance field of the class. When makeSentence(3, false) is called, it does the following;
Initializes a local variable s with "Object is "
s now contains "Object is "
Since sign== false, the if block executes
s now contains "Object is not "
The for loop will execute 3 times to append "very " to s
s now contains "Object is not very very very "
Finally the return statement returns a concatenation of the contents of descriptor (descriptor=="regular") and s
s now contains "Object is not very very very regular"
Learn more about programs here: https://brainly.com/question/19625875
What is the output of the following? *
public class output1
{
public static void main(String str[])
{
int a=1,b=2, c=3;
boolean f1, f2;
f1=a<=b++;
f2=C+9>b++;
System.out.println(f1 + " " + f2);
}
}
a false true
b true false
c 8
d 6
Answers
Answer:
A
Explanation:
well there are numbers and time
In the game Badland, how do you get to the next level?
A.
If you get close enough to the exit pipe, it sucks you up and spits you out in the next level.
B.
If you shoot enough enemies, you automatically advance to the next level.
C.
If you reach the end of the maze, you hear the sound of a bell and are taken to the next level.
D.
If you answer enough puzzles correctly, you advance to the next level.
Answers
In the game Badland, the way a person get to the next level is option C: If you reach the end of the maze, you hear the sound of a bell and are taken to the next level.
What is the story of BADLAND game?
The story occurs throughout the span of two distinct days, at various times during each day's dawn, noon, dusk, and night. Giant egg-shaped robots start to emerge from the water and background and take over the forest as your character is soaring through this already quite scary environment.
Over 30 million people have played the side-scrolling action-adventure game BADLAND, which has won numerous awards. The physics-based gameplay in BADLAND has been hailed for being novel, as have the game's cunningly inventive stages and breathtakingly moody sounds and visuals.
Therefore, in playing this game, the player's controller in Badland is a mobile device's touchscreen. The player's Clone will be raised aloft and briefly become airborne by tapping anywhere on the screen.ult for In the game Badland, the way a person get to the next level.
Learn more about game from
https://brainly.com/question/908343
#SPJ1
Which options are qualities of all good requirements documents?
Consistent
llustrated
verifiable
printed
scholarly
feasible
Answers
feasible
scholarly
verifiable
HRE 401 Chapter 1 Assignment - The Pursuit of Happyness Task: Apply the concepts learned in Chapter One - "Changes Ahead" to the movie The Pursuit of the PURSUIT of Happyness, specifically to Will Smith's character, Chris HAPPYNESS Gardner. This movie is based on the real-life story of stockbroker Chris Gardner in San Francisco in the 1980s. Evaluation: / 30 total K/U - / 10 T- 12 COMM - / 10 APP - 18 1. "Our sense of identity..is a marvelous combination of personality traits, abilities, strengths, weaknesses, interests and values that are uniquely ours" (Koch 14). Using examples from the film, provide two (2) examples that describe each of the following about Chris Gardner. (K/U - 8 marks) Personality -
Answers
Personality:
Perseverance: One example of Chris Gardner's personality trait of perseverance is seen throughout the movie when he faces numerous challenges and setbacks in his pursuit of a better life for himself and his son. Despite facing homelessness, financial struggles, and constant rejections, Chris never gives up and remains determined to achieve his goals. He continues to actively seek job opportunities, even when faced with discouragement.Optimism: Chris Gardner demonstrates his optimistic outlook in the face of adversity. Despite his difficult circumstances, he maintains a positive mindset and believes that he can overcome challenges. He remains hopeful and encourages his son to have a positive attitude as well. For example, when facing homelessness, he tells his son that they are not "homeless," but rather "internally displaced." This reflects his ability to find a silver lining and maintain optimism in challenging situations.Chris Gardner's personality traits of perseverance and optimism play crucial roles in his journey depicted in the film. They contribute to his ability to overcome obstacles and keep striving for a better future.
Learn more about perseverance here
https://brainly.com/question/10618814
#SPJ11
what is the checksum of 148
Answers
Answer:
The summary on the given topic is summarized in the explanation portion below.
Explanation:
A means to ensure that somehow a machine data communication or transfer has no bits missing are termed as Checksum. These would be determined in many extremely difficult directions but there's no response.Whereas if checksum appears unacceptable or inaccurate, the machine is compared mostly with documentation it gets or collects and lends it a position.which type of attack is wep extremely vulnerable to?
Answers
WEP is extremely vulnerable to a variety of attack types, including cracking, brute-force, IV (Initialization Vector) attack, and replay attack.
What is Initialization Vector?An Initialization Vector (IV) is a random number used in cryptography that helps to ensure the uniqueness and randomness of data used in an encryption process. The IV is typically used as part of an encryption algorithm, where it is combined with a secret key to encrypt a message. The IV is unique for each encryption session, and must be unpredictable and non-repeating. A good IV should not be reused across multiple encryption sessions, and it should be kept secret from anyone who does not have access to the decryption key. Without a good IV, a cryptographic system can be vulnerable to attacks such as replay attacks, where an attacker can gain access to the system by repeating an encrypted message.
To learn more about Initialization Vector
https://brainly.com/question/27737295
#SPJ4
highlight the possible risks and problems that should be address during the implementation of information system process
Answers
Answer:
The answer is below
Explanation:
The possible risks and problems that should be addressed during the implementation of the information system process are:
1. power loss or data corruption
2. System design faults
3. Cultural barriers
4. Integration of Software Development device
5. Using the same processes in the company
6. Security breaches
7. Hardware and Software failure
8. Work environment
Technician a says that analog scopes use an lcd display. Technician b says that digital scopes may use a crt display. Which technician is correct?.
Answers
Answer:
CRT aka cathode ray tube so technician b is right
8.3.5: Max In List
Write the function max_int_in_list that takes a list of ints and returns the biggest int in the list. You can assume that the list has at least one int in it. A call to this function would look like:
my_list = [5, 2, -5, 10, 23, -21]
biggest_int = max_int_in_list(my_list)
# biggest_int is now 23
Do not use the built-in function max in your program!
Hint: The highest number in the list might be negative! Make sure your function correctly handles that case.
Answers
Answer:
here!!
Explanation:
# Write code here...
def max_int_in_list(my_list):
highest = my_list[4]
for num in my_list:
if num > highest:
highest = num
return highest
my_list = [5, 2, -5, 10, 23, -21]
biggest_int = max_int_in_list(my_list)
print biggest_int
A version of the required program written in python 3 is given below.
my_list = [5, 2, -5, 10, 23, -21]
def max_int_in_list(my_list):
#iniate the function named max_int_in_list which takes in a list argument
maximum = my_list[0]
#set the first value in the list as maximum
for num in my_list:
#iterate through every value in the list
if num > maximum:
#Check if any of the iterated values in the list is greater than the set maximum value
maximum = num
#if so set the Number as the new maximum value
return maximum
#return the maximum value
print(max_int_in_list(my_list))
A SCREENSHOT of the program output is attached.
Learn more on python programs :https://brainly.com/question/24782250

Argue whether we can infer anything about a candidate's ability to work in a professional environment based on his or her resume's formatting. Compare how you would address a resume with wacky fonts to how you would respond to grammatical errors in a resume.
Answers
Answer:
Candidates resume shows his way of presenting and organizing.
Explanation:
Resume formatting is an important part of a candidate's ability to work. In any professional environment, it's necessary to have a properly formatted resume. The resume formatting should be up to date with the latest information and data. The formatting involves the borders, headings, grammar, and spelling or typo errors, etc. But these mistakes can be easily avoided such as proofreading and removing unnecessary details and sloppy fronts.Which of the following is a lossless compression algorithm?A. PNGB. Run-length encodingC. Compression artifactD. MP4
Answers
Answer:
B. (Run-length encoding)
Explanation:
Run-length encoding compresses data by reducing repeating data. For example, in a text file, if there are 20 instances of the word "is", the program will store the value 20, as well as all the positions where it appears. The file can be fully reconstructed using this stored data when required, so no data is lost.
Both PNG and MP4 are lossy compression formats that reduce file sizes by irretrievably removing some part of the file, and Compression artifacts are noticeable distortions in a file caused by lossy compressions. So A, C, and D are not correct options.
Hope this helps!
3. When a small business buys office supplies online, it is an example of business-to- business e-commerce.
a. True
b. False
Answers
Answer:
TRUE
Explanation:
Answer:
TRUE i think
Explanation: For example, an automobile manufacturer makes several B2B transactions such as buying tires, glass for windscreens, and rubber hoses for its vehicles. The final transaction, a finished vehicle sold to the consumer, is a single B2C transaction.
27. Which attribute is used to set the
border color of a table ?
Answers
Which of the following tools enables a production mixer to sync audio and video?
A Waveform monitor
B Viewfinder
C Clapboard
D Repeater
Answers
Answer:
repeater or waveform monitor
On the Audio Tools contextual tab, which tab will control how the audio file appears, if it appears, on the slide itself?
A.) Bookmarks
B.) Playback
C.) Format
D.) Design
Answers
Answer:
B. PlaybackExplanation:
Playback is the act of reproducing recorded sound; “he was allowed to hear the playback of his testimony”. The part of a tape recorder that reproduces the recorded material.
On the audio tools contextual tab, “playback” will control how the audio file appears, if it appears, on the slide itself.
Therefore, the correct answer is b. playback.
Answer:
C) Format
Explanation:
The audio format tab gives you all of these options to adjust the appearance of the image representing the audio:
What does the ‘SIM’ in the SIM card stand for?
Answers
Answer:
It stands for Subscriber Identity Module
Explanation:
SIM cards are computer chips that store data and enable you to access your network. That implies you may call, text, and connect to mobile internet services such as 4G. SIM cards are portable, and you can store messages, contacts, and emails to them. SIM cards connect a specific account to a specific phone; they inform the phone network firm which account is linked to which phone. Customers are typically referred to as subscribers by network operator providers. A SIM card is a type of user card that allows your phone to connect to a network. Also, if you had a phone accidents and you can s imply insert the SIM card in another phone and you may make a call or utilize your data. Just make sure they each utilize the same size SIM card.
Can someone help me figure out why my else statment is not working?
----------------------------------------------------------------------------------------------------------------------------
print("\tBank of The Funny Money Bunny Farm\n")
print("Client\t\tDeposits\tWithdrawals\tBalance\t\tNotes:")
print("__________________________________________________________________________________________________________________________")
names = ['Judith', 'Jimmie', 'Johnny', 'Joseph', 'Jeffry', 'Buddie', 'Charlie', 'Maxine', 'Jannis', 'Bodine']
deposists = [255.23, 525.55, 323.21, 651.48, 507.11, 101.11, 253.36, 323.22, 611.45, 252.91]
withdrawals = [255.76, 128.65, 156.22, 175.33, 390.12, 255.41, 128.22, 156.23, 728.98, 251.43]
balance = []
notes = []
for i in range(len(names)):
balance.appened(deposits[i] - withdrawals[i])
if(balance < 0):
print((names[i] + ", you are overdrawn. Your account balance is " + "$%.2f"%(balance[i]))
else:
print("" + names[i] + "\t\t" + "%.2f"%(deposits[i]) + "\t\t" + "%.2f"%(withdrawals[i]) + "\t\t" + "%.2f"%(balance[i]) + "\t\t" + notes[i])
print("__________________________________________________________________________________________________________________________")
print("\© Copyright 2021 Funny Bunny Money Productions")
#Main
print("\tBank of The Funny Money Bunny Farm\n")
account = int(input("How many new accounts are needed: "))
for i in range(account):
input("Enter the name of the client: ")
input("Enter the deposist of the client: ")
input("Enter the withdraral of the client: ")
Answers
Answer:
below is a version of your code that runs.
I'm not sure if it does what you expect it to do.

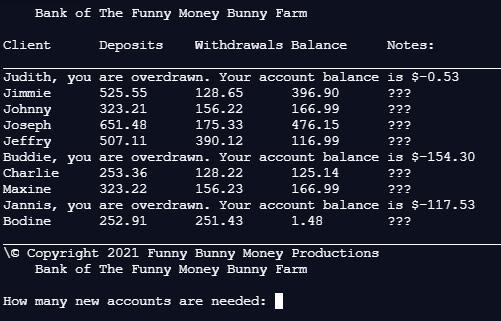
what is the name of the program that enables the device and operating system to communicate with each other?
Answers
Answer:
Explain Operating System working: OS works as an intermediate between the user and computer. It helps the user to communicate with the computer without knowing how to speak the computer's language. The kernel is the central component of a computer operating systems.
Explanation:
A company uses cell phones that do not have SIM cards and can only be managed by a specific
network provider. The company wants to buy 3G cell phones that have SIM cards so they can switch to
any chosen provider. What network type best suits the company's needs?
A. GSM
B. CDMA
C. PRL
D. LTE
Answers
Based on the company's requirement to switch to any chosen network provider, the network type that best suits their needs is GSM (Global System for Mobile Communications).
GSM is a widely adopted standard for mobile communication and is used by the majority of the world's cellular networks. One of the key advantages of GSM is its use of SIM cards (Subscriber Identity Module). SIM cards allow users to easily switch between different network providers by simply swapping out the SIM card in their device. This flexibility provides the company with the freedom to choose the network provider that offers the best coverage, pricing, and services for their specific needs.
On the other hand, CDMA (Code Division Multiple Access) is another network technology used in cellular communication. Unlike GSM, CDMA does not utilize SIM cards. CDMA phones are typically tied to specific network providers and do not offer the same level of flexibility when it comes to switching between providers. Therefore, CDMA is not the best network type for the company's requirement to have the ability to switch to any chosen provider.
PRL (Preferred Roaming List) is not a network type but rather a list that CDMA phones use to prioritize which networks to connect to when roaming. It is not directly relevant to the company's requirement.
LTE (Long-Term Evolution) is a 4G wireless communication standard that provides high-speed data transmission. While LTE is an advanced network technology, it does not specifically address the company's need for flexibility in switching network providers.
In summary, the network type that best suits the company's needs for switching to any chosen provider is GSM.
For more questions on network
https://brainly.com/question/28342757
#SPJ11
Dumas, who has excellent mechanical aptitude, owns a computer with two hard drives. One
drive is used for the operating system and the other drive is used for his personal files. He
decides to install a third disk in a RAID 1 configuration to protect the disk with his files
against data loss. He is not too concerned about data loss on the disk with the operating
system because he could easily reinstall the OS, so that disk is not included in the RAID
configuration. When he is done, he powers up his computer, no error messages are displayed,
yet he is distraught because all his data is lost. Why would this happen?
O The new drive was smaller than the original drive so the data from the original did not
fit.
O He didn't back up his data. When RAID is configured all data on participating drives is
lost.
O The RAID expansion card is not seated properly so the RAID drives are not being
detected.
Since the new drive had no data, and RAID 1 mirrors data, it erased the data on the
original.
Answers
Answer:
He didn't back up his data. When RAID is configured all data on participating drives is lost.
Explanation:
because i'm asian
He didn't back up his data. When RAID is configured all data on participating drives is lost would this happen. Hence, option B is correct.
What is operating system?
The operating system is the most important piece of software that operates on a computer. It manages the computer's memory, processes, software, and hardware. Using this technique, you can communicate with the computer even if you don't comprehend its language.
Examples of operating systems include Apple macOS, Microsoft Windows, g's Android OS, Linux, and Apple iOS.
All of the hardware and software are under the direction of the computer's operating system. It performs core tasks such handling input and output, controlling files, memory, and processes, and controlling peripheral devices like disk drives and printers.
Thus, option B is correct.
For more information about operating system, click here:
https://brainly.com/question/6689423
#SPJ2
For what two reasons is it important to add comments to a program?
Answers
Which of these would you least expect to find at an fbla-pbl meeting?
planning a community service project
role-playing to develop leadership skills
students working on iste certification
working with local business leaders
Answers
role-playing to develop leadership skills
Implement a C# WinForms application that tracks student names, university id, major, phone numbers, and e-mail addresses. The application should support the following features: 1. Allows the user to add new student (i.e., first name, last name, id, major, phone, e-mail address). 2. Allows the user to remove existing student. 3. The application should maintain all student entries in a flat file on the hard-disk. 4. The application should retrieve all student entries from a flat file after application restarts. 5. The application should retrieve and display all student details based on the "lastname, first name". You may use Serialization to read/write the flat file to/from the hard-disk.
Answers
This is a simple C# Windows Form Application that uses a flat file to store the student information.
It can add, delete, and retrieve student information from the flat file and can retrieve and display all the student information based on the "last name, first name. "When the program starts, it loads the student list from the flat file. When the application is closed, it saves the student list to the flat file.
To retrieve and save data from the flat file, we'll use serialization, which is a technique for converting objects into a stream of bytes, which can then be stored on the disk. The stream of bytes can then be deserialized back into an object to retrieve the original data.
To know more about Windows visit:-
https://brainly.com/question/33349385
#SPJ11
The _______ button automatically merges the selected cells and then centers the data from the first cell across the entire merged area. Quick Analysis Merge
Answers
Answer:
Merge and Center
When starting up his computer, Connor notices pop-ups appearing randomly from his browser. Over time, these get worse and prevent him from using the computer. What is MOST likely the cause of this?
Answers
Answer: Sounds like he has a malware problem he should uninstall all of the potentially unwanted programs (PUPs), or run an antivirus software.
Explanation:
It's what I would do if I was in that unlikely of situations because I'm constantly aware of what I download and install. Sounds like Connor should too.
9.6 Code Practice
Instructions
1
Declare a 4x 5 array called N
Please helppp
Answers
Answer:
See Explanation
Explanation:
The question lacks so many details, as the array type and the programming language is not stated.
Assume that, it is Java:
The rule to follow is:
Data-Type[][]Array-Name = new Data-type[rows][columns]
If the given information is for an array of type integer, the code will be;
int[][] N = new int[4][5]
Where
N = Array-Name
int = Data-type
4 and 5 are the dimensions of the array
Consider network below, determine the maximum number of cans (io thousands) an hour from east so tioeth Carolina.
Answers
The maximum number of cans (in thousands) an hour from east to south Carolina is 48.
To determine the maximum number of cans per hour from east to south Carolina, we will need to first find the maximum flow capacity for the network below:Network Diagram To get the maximum flow capacity, we will apply Ford-Fulkerson algorithm as shown below:Step 1: Start with the source node S and perform a depth-first search to find an augmented path to the sink node T. If no path exists, terminate the algorithm and output the maximum flow capacity. If a path exists, proceed to step 2.Step 2: Calculate the residual capacity for the augmented path found in step 1. This is done by finding the minimum capacity among the edges in the path. Subtract this capacity from the forward edges and add it to the reverse edges. Proceed to step 3.Step 3: Update the flow capacity by adding the residual capacity of the augmented path to the previous flow capacity. Proceed to step 1.To find the maximum flow capacity, we will use the following network flow table:Network Flow TableThe algorithm will run as shown below:Augmented Path (in bold): S-A-B-C-D-T Residual Capacity = 10Maximum Flow Capacity = 10Augmented Path (in bold): S-A-B-C-E-T Residual Capacity = 5Maximum Flow Capacity = 15Augmented Path (in bold): S-F-B-C-E-T Residual Capacity = 7Maximum Flow Capacity = 22Augmented Path (in bold): S-F-B-D-T Residual Capacity = 2Maximum Flow Capacity = 24Augmented Path (in bold): S-F-G-D-T Residual Capacity = 8Maximum Flow Capacity = 32Augmented Path (in bold): S-F-G-C-D-T Residual Capacity = 5Maximum Flow Capacity = 37Augmented Path (in bold): S-F-G-C-E-T Residual Capacity = 5Maximum Flow Capacity = 42Augmented Path (in bold): S-F-A-B-C-E-T Residual Capacity = 3Maximum Flow Capacity = 45Augmented Path (in bold): S-F-A-B-C-D-T Residual Capacity = 1Maximum Flow Capacity = 46Augmented Path (in bold): S-F-A-B-D-T Residual Capacity = 2Maximum Flow Capacity = 48Augmented Path (in bold): S-F-G-C-D-T Residual Capacity = 0Maximum Flow Capacity = 48Therefore, the maximum number of cans (in thousands) an hour from east to south Carolina is 48. Answer: 48.
Learn more about algorithm :
https://brainly.com/question/21172316
#SPJ11