use JAVA
Create a HighestGrade application that prompts the user for five grades between 0 and 100 points and stores
the grades in an ArrayList. HighestGrade then traverses the grades to determine the highest grade and then
displays the grade along with an appropriate message.
Output:
Enter a grade (between 0 and 100): 87
Enter a grade (between 0 and 100): 65
Enter a grade (between 0 and 100): 98
Enter a grade (between 0 and 100): 89
Enter a grade (between 0 and 100): 55
The highest grade is: 98
Answers
Answer:
import java.util.*;
public class HighestGrade
{
public static void main(String args[])
{
Scanner sc = new Scanner(System.in);
int n = 5;
ArrayList<Integer> grades = new ArrayList<Integer>(n);
for (int i = 1; i <= n; i++)
{
System.out.print("Enter a grade (between 0 and 100): ");
int num = sc.nextInt();
grades.add(num);
}
int max = grades.get(0);
for (int i = 1; i < n; i++) {
if (grades.get(i) > max) {
max = grades.get(i);
}
}
System.out.print("The highest grade is: "+max);
}
}
Explanation:
The class HighestGrade application rompts the user for five grades between 0 and 100 points and stores the grades in an ArrayList. HighestGrade then traverses the grades to determine the highest grade and then displays the grade along with an appropriate message.
Related Questions
Some scientists hypothesize that Earth's ozone layer is being damaged by ____.
a.
ultraviolet radiation
c.
plant life on Earth
b.
chlorofluorocarbons
d.
global warming
Please select the best answer from the choices provided
A
B
C
D
Answers
Some scientists hypothesize that Earth's ozone layer is being damaged by the emission of certain chemical compounds known as ozone-depleting substances (ODS), such as chlorofluorocarbons (CFCs).
b. chlorofluorocarbonsWhat are ozone-depleting substances (ODS)?These substances have been widely used in various industrial processes, aerosol propellants, refrigerants, and fire suppression systems. When released into the atmosphere,
CFCs can reach the stratosphere and interact with ozone molecules, leading to their depletion and thinning of the ozone layer. Ultraviolet radiation is a consequence of ozone layer depletion, and global warming, while impacting the Earth's climate, is not directly linked to ozone layer damage.
Plant life on Earth plays a vital role in oxygen production and carbon dioxide absorption but is not a direct cause of ozone layer depletion.
Learn more about ozone layer at
https://brainly.com/question/520639
#SPJ1
Data analytics benefits both financial services consumers and providers by helping create a more accurate picture of credit risk.
True
False
Answers
Answer:
True
Explanation:
A(n) is an internal corporate network built using Internet and World Wide Web standards and products.
Answers
An intranet is an internal corporate network built using Internet and World Wide Web standards and products.
What is the definition of intranet?This is known to be small or restricted computer network used by a group to communicate with one another is described as an intranet. An intranet is a private computer network that only employees of a specific workplace can access. noun.
The kind of internet utilized privately is an intranet. Since it is a private network, only authorized users can access the intranet. The intranet has a small user base and only offers a little amount of information to its users. various network types
An intranet is a computer network used exclusively by employees of a company for information exchange, improved communication, teamwork tools, operational systems, and other computing services.
Therefore, An intranet is an internal corporate network built using Internet and World Wide Web standards and products.
Learn more about intranet from
https://brainly.com/question/13139335
#SPJ1
A database designer wants to create three tables: Supplier, Product, and Country. The Supplier table has a Countryld column with values that must appear in the Country table's Countryld column. The Product table has an auto-increment column.
Which table's CREATE TABLE statement(s) must specify a FOREIGN KEY?
a. Supplier
b. Product
c. Country
d. Supplier and Country
Answers
Answer:
(a) Supplier
Explanation:
In database design, two tables are linked together using a FOREIGN KEY. A foreign key is formed from one or more columns of one table that reference or match another key (often called a primary key) in another table. In other words, when a column or a combination of columns on one table points to a primary key of another table, the column(s) will specify the foreign key.
PS: A primary key is used to make each entry of a table unique.
In the given tables - Supplier, Product, Country - since the Supplier table has a column called CountryId referencing the CountryId column of the Country table, then CountryId is a primary key in Country table but a foreign key in Supplier table.
Therefore, the CREATE TABLE statement(s) of the Supplier table must specify a foreign key.
A database management system often reads and writes data in a database, and makes sure there is consistency and availability. The supplier table's CREATE TABLE statement(s) must specify a FOREIGN KEY.
The database system often guards data when a lot of transactions is taking place. it often hinders multiple transactions with the same data at the same time.The Select SQL statement does not alter any database data. A supplier database is made up of different list of service, product or materials providers who can meet orders quickly.
Learn more from
https://brainly.com/question/15281828
What types of traffic can still fool stateful firewalls?
Answers
The types of traffic can still fool stateful firewalls incude the following:
Packets containing hazardous contents.Normal protocols that are running on non-standard ports.What is a firewall?A firewall can be defined as a network security protocol that monitors and controls inbound and outbound traffic based on set aside security rules.
In Computer technology, a firewall is typically used to control access to a computer or network, as it creates a barrier between a computer or a network and the internet in order to protect against unauthorized access.
Additionally, the other functionality which would influence a decision to deploy a stateless, rather than stateful firewall are:
Block TCP portsAllow network protocols.In this context, we can reasonably infer and logically deduce that the types of traffic can still fool stateful firewalls incude the following:
Packets containing hazardous contents.Normal protocols that are running on non-standard ports.Read more on stateful firewall here: brainly.com/question/16157439
#SPJ1
Which of the following describe ways you can align a paragraph in a text box or placeholder? Select all the
options that apply.
a. left-aligned
b. right-aligned
c. centered
d. justified
Answers
Aligned to the left, right, center, or justify The slide's alignment determines how your paragraph will appear. There are four options for paragraph alignment in PowerPoint: Right, Center, Left, and Justify
What does PowerPoint's align-to-slide function do?Align to Slide is the Alignment Tool's second selection. When this option is chosen, all of the selected items on your slide will be aligned to the top, bottom, left, and right sides of your presentation as anchor points. Left, center, right, and justified text orientations are the four different styles available.
What are the four major alignments for paragraphs?Left-aligned text, right-aligned text, centered text, or justified text—which is aligned evenly along the left and right margins—all affect how the paragraph's boundaries look and are oriented.
to know more about PowerPoint here:
brainly.com/question/14498361
#SPJ1
Select the correct answer.
Jasmine is a software developer. Her upcoming project requires building system software for a manufacturing plant. The software should be
powerful and fast and provide high performance. Which programming language should she use while programming the manufacturing plant's
system software?
OA PHP
OB. Python
C C++
OD. Java
Answers
Answer: C++
Explanation: it is correct on PLATO
Why would we need to consider implementing our business blockchain application not on Bitcoin but Ethereum?
Answers
1. Phishing is the act of sending multiple emails to multiple users in hope of having
2. Spoofing is the act of obtaining unauthorized access to data from a computer
network.
3. Extortion is the act of using the internet to threaten or damage someone's
reputation to extort money or anything else of value.
4. In late 2014, LimeWire was raided for the second time due to years of pirating
movies, music, games, books and other software.
5. Electronic harassment is also referred to as cyberbullying.
6. Non-delivery of service is the act of devising a scheme wherein a culprit posts an
item or service for sale over the internet, and once the transactions have been done, does not
give the item or service.
7. Encryption is the process of converting raw to data code.
8. In piracy, trackers are used to identify IP addresses currently sharing a pirated
file.
9. Wager Gambling is the act of betting on any sports event over the internet.
10. Most email services today have spam or bulk folder that automatically puts
these suspicious emails to that folder.
How does ring video doorbell 3 work?
Answers
What does the coding phase involve?
A.
testing and debugging code to remove all possible errors
B.
writing sequences of statements in a suitable programming language to produce the desired program
C.
designing a proper pseudocode using human-readable language
D.
compiling and interpreting programs into machine language
E.
breaking down the entire code into workable modules
Answers
Answer:
I do believe it is D im not sure
Answer:
Ay homie the answer is B
Explanation:
Edmentum
Name the wireless technology that may work with one device and not with another.
a. 802.11n
b. none of the above
c. Wi-Fi
d. Cellular
Answers
Answer: Im guessing b
Explanation:
bc the other ones work devices.
The wireless technology that may work with one device and not with another is not among the options. So the answer is none of the above.
Wireless technology often gives the ability for people to communicate between two or more entities over distances without the use of wires or cables of any sort.
Cellular network such as Mobile networks uses various radio frequencies in its communication with other devices.
Conclusively, This WiFi connection can connect to more than 250 devices. They can connect to computers, cameras, tablets, mobile smartphones, appliances etc.
Learn more from
https://brainly.com/question/19976907
When you save something to the Desktop on a school computer, what drive letter will it save to
Answers
When you save something to the Desktop on a school computer, the drive letter it will save to the C drive.
What is a C drive?C drive is that part of the computer that contains the operating system and files of the system. The files on which we worked are saved on the C drive of the system.
This is a type of hard drive. The work we have done on the system is automatically saved on the drive. We can easily find the C drive on the computer's file explorer. It automatically saved the data, but you can save manually the data of the D drive.
Thus, the drive letter it will save to the C drive.
To learn more about C drive, refer to the link:
https://brainly.com/question/2619161
#SPJ1
what is subnetting. what does subnetting mean
Answers
Answer:
Subnetting is the practice of dividing a network into two or more smaller networks. It increases routing efficiency, enhances the security of the network and reduces the size of the broadcast domain.
Explanation:
Write a program in c++ to read two integers, calculate and print the smallest
Answers
Answer:
#include<iostream>
using namespace std;
int main (){
int n1, n2;
cout<<"Enter 1st number";
cin>>n1;
cout<<"Enter 2nd number";
cin>>n2;
if(n1<n2){
cout<<"The 1st number is the smallest"<<endl<<" is= "<<n1;
}
else{
cout<<"The 2nd number is the smallest"<<endl<<" is= "<<n2;
}
}
return 0;
Actividades que puedes Aser con un martillo y su explicación
Answers
Answer:
hi how are you thx yets1wud
f $500 million. You're on the phone with the manager of software development who has made a request to hire a notorious white hat hacker to probe your company's software products in an attempt to identify any vulnerabilities. The reasoning is that if anyone can find a vulnerability in your software, she can. This will give your firm a head start on developing patches to fix the problems before anyone can exploit them. You feel uneasy about hiring people with criminal records and connections to unsavory members of the hacker/cracker community and are unsure if you should approve the hire. What is the difference between a black hat hacker and a white hat hacker
Answers
Answer:
Whereas a black hat hacker gains access into a software or system product in order to exploit its weaknesses for selfish purposes, a white hat hacker is a professional who finds and fixes system security issues for the welfare of the entity.
Explanation:
Black-hat hackers, who exploit system weaknesses for selfish purposes, rely on the use of viruses, malware, and spyware to gain access into an entity's database. Their intentions are always malicious and criminal in nature. They are not like white hat hackers who try to identify weaknesses in a system before black hat hackers could do the same.
Pick an Industry, other than the automobile industry, in which machines are likely to replace humans. Who will be displaced by those machines and how far will those riplle effects spread? Explain.
Answers
Answer:
One industry in which machines are likely to replace humans is the retail industry, specifically in areas such as cashier and inventory management. The people who are most likely to be displaced by these machines are cashiers and other retail workers who perform tasks that can be automated, such as scanning items and processing payments.
In c please
Counting the character occurrences in a file
For this task you are asked to write a program that will open a file called “story.txt
and count the number of occurrences of each letter from the alphabet in this file.
At the end your program will output the following report:
Number of occurrences for the alphabets:
a was used-times.
b was used - times.
c was used - times .... ...and so, on
Assume the file contains only lower-case letters and for simplicity just a single
paragraph. Your program should keep a counter associated with each letter of the
alphabet (26 counters) [Hint: Use array|
| Your program should also print a histogram of characters count by adding
a new function print Histogram (int counters []). This function receives the
counters from the previous task and instead of printing the number of times each
character was used, prints a histogram of the counters. An example histogram for
three letters is shown below) [Hint: Use the extended asci character 254]:
Answers
Answer:
#include <stdio.h>
#include <ctype.h>
void printHistogram(int counters[]) {
int largest = 0;
int row,i;
for (i = 0; i < 26; i++) {
if (counters[i] > largest) {
largest = counters[i];
}
}
for (row = largest; row > 0; row--) {
for (i = 0; i < 26; i++) {
if (counters[i] >= row) {
putchar(254);
}
else {
putchar(32);
}
putchar(32);
}
putchar('\n');
}
for (i = 0; i < 26; i++) {
putchar('a' + i);
putchar(32);
}
}
int main() {
int counters[26] = { 0 };
int i;
char c;
FILE* f;
fopen_s(&f, "story.txt", "r");
while (!feof(f)) {
c = tolower(fgetc(f));
if (c >= 'a' && c <= 'z') {
counters[c-'a']++;
}
}
for (i = 0; i < 26; i++) {
printf("%c was used %d times.\n", 'a'+i, counters[i]);
}
printf("\nHere is a histogram:\n");
printHistogram(counters);
}




Which of the following activities do not involve Information Technology? *
A. Identification card theft
B.Dissemination of Information through social media
C. Listening to an mp3 device
D. Using a software to generate images
Answers
hope it helps
How can organizations leverage information systems to gain a competitive advantage in today's business landscape? Provide examples to support your answer.
Answers
Organizations can leverage information systems to gain a competitive advantage in several ways in today's business landscape. Here are some examples:
Improved Decision-Making: Information systems can provide timely and accurate data, enabling organizations to make informed decisions quickly. For example, a retail company can use point-of-sale systems and inventory management systems to track sales data and inventory levels in real-time.Enhanced Customer Relationship Management: Information systems can help organizations manage and analyze customer data to personalize interactions, provide better customer service, and build strong customer relationships.Streamlined Operations and Efficiency: Information systems can automate and streamline business processes, improving operational efficiency. For example, manufacturing organizations can implement enterprise resource planning (ERP) systems.Data-Driven Insights and Analytics: Information systems enable organizations to collect, store, and analyze vast amounts of data to gain valuable insights. By using business intelligence tools and data analytics, organizations can uncover patterns, trends, and correlations in data, which can inform strategic decision-making. Agile and Collaborative Work Environment: Information systems facilitate collaboration and communication within organizations. For example, cloud-based project management tools enable teams to collaborate in real-time, track progress.These are just a few examples of how organizations can leverage information systems to gain a competitive advantage. By harnessing technology effectively, organizations can improve decision-making, customer relationships.
for similar questions on organizations.
https://brainly.com/question/30402779
#SPJ8
You are building a predictive solution based on web server log data. The data is collected in a comma-separated values (CSV) format that always includes the following fields: date: string time: string client_ip: string server_ip: string url_stem: string url_query: string client_bytes: integer server_bytes: integer You want to load the data into a DataFrame for analysis. You must load the data in the correct format while minimizing the processing overhead on the Spark cluster. What should you do? Load the data as lines of text into an RDD, then split the text based on a comma-delimiter and load the RDD into a DataFrame. Define a schema for the data, then read the data from the CSV file into a DataFrame using the schema. Read the data from the CSV file into a DataFrame, infering the schema. Convert the data to tab-delimited format, then read the data from the text file into a DataFrame, infering the schema.
Answers
Answer:
see explaination
Explanation:
The data is collected in a comma-separated values (CSV) format that always includes the following fields:
? date: string
? time: string
? client_ip: string
? server_ip: string
? url_stem: string
? url_query: string
? client_bytes: integer
? server_bytes: integer
What should you do?
a. Load the data as lines of text into an RDD, then split the text based on a comma-delimiter and load the RDD into DataFrame.
# import the module csv
import csv
import pandas as pd
# open the csv file
with open(r"C:\Users\uname\Downloads\abc.csv") as csv_file:
# read the csv file
csv_reader = csv.reader(csv_file, delimiter=',')
# now we can use this csv files into the pandas
df = pd.DataFrame([csv_reader], index=None)
df.head()
b. Define a schema for the data, then read the data from the CSV file into a DataFrame using the schema.
from pyspark.sql.types import *
from pyspark.sql import SparkSession
newschema = StructType([
StructField("date", DateType(),true),
StructField("time", DateType(),true),
StructField("client_ip", StringType(),true),
StructField("server_ip", StringType(),true),
StructField("url_stem", StringType(),true),
StructField("url_query", StringType(),true),
StructField("client_bytes", IntegerType(),true),
StructField("server_bytes", IntegerType(),true])
c. Read the data from the CSV file into a DataFrame, infering the schema.
abc_DF = spark.read.load('C:\Users\uname\Downloads\new_abc.csv', format="csv", header="true", sep=' ', schema=newSchema)
d. Convert the data to tab-delimited format, then read the data from the text file into a DataFrame, infering the schema.
Import pandas as pd
Df2 = pd.read_csv(‘new_abc.csv’,delimiter="\t")
print('Contents of Dataframe : ')
print(Df2)
survey and describe the system
Answers
Survey systems help create, distribute, and analyze surveys by providing a framework for designing questionnaires, managing respondents, and analyzing data.
What is survey?A survey system lets users create surveys with different question types and response options. The system offers multiple ways to distribute surveys, including sharing a web link, email invites, website embedding, and social media.
Data is collected from respondents and stored accurately and securely, with error checking and validation in place. After survey completion, analyze data with summary stats, visualizations, filters, and cross-tabulations for identifying patterns. Survey systems have reporting features to generate detailed reports based on its data, including statistics, graphs, etc.
Learn more about survey from
https://brainly.com/question/14610641
#SPJ1
How does a computer work? Explain with an example.
Answers
Answer:
A computer system works by combining input, storage space, processing, and output. ... For example, when we type something using a keyboard, it is known as an Input provided to the Computer. Storage Space: It is the place where our input gets stored. It is known as Computer Memory that keeps the data into it.
Miss Jones is a small business entrepreneur who currently does everything manually. She is the
head chef at her small cook shop which has many loyal repeat customers. Her assistant helps with
cooking as well as the paperwork. Miss Jones also employs someone to makes deliveries to
customers. Customers order via telephone and everything is handwritten.
There are various issues such as missing orders, receipts and customer contact information. Two
stand-alone computers and a printer are in the office. One computer is not working due to a virus
and the other is not connected to the printer so no printing can be done at this time. The assistant
accidentally deleted all files on this second computer which therefore is not being used.
A. Advise Miss Jones of TWO (2) advantages of setting up a computer network. 4 marks)
B. Describe TWO (2) network hardware that Miss Jones will need. (4 marks)
C. Which wired transmission medium would you recommend? Why? (3 marks)
D. What TWO (2) risk management strategies would you recommend? Give reasons for
your answer. (4 marks)
E. Miss Jones has decided to keep customer data in an electronic database to help the
situation. If you were to create a table to hold customer data, what FOUR (4) fields
would you include? (2 marks)
F. Other than customers calling in, which office automation technology could be used to
capture orders? Give reasons for your answer. (3 marks)
Answers
You are given an array of integers, each with an unknown number of digits. You are also told the total number of digits of all the integers in the array is n. Provide an algorithm that will sort the array in O(n) time no matter how the digits are distributed among the elements in the array. (e.g. there might be one element with n digits, or n/2 elements with 2 digits, or the elements might be of all different lengths, etc. Be sure to justify in detail the run time of your algorithm.
Answers
Answer:
Explanation:
Since all of the items in the array would be integers sorting them would not be a problem regardless of the difference in integers. O(n) time would be impossible unless the array is already sorted, otherwise, the best runtime we can hope for would be such a method like the one below with a runtime of O(n^2)
static void sortingMethod(int arr[], int n)
{
int x, y, temp;
boolean swapped;
for (x = 0; x < n - 1; x++)
{
swapped = false;
for (y = 0; y < n - x - 1; y++)
{
if (arr[y] > arr[y + 1])
{
temp = arr[y];
arr[y] = arr[y + 1];
arr[y + 1] = temp;
swapped = true;
}
}
if (swapped == false)
break;
}
}
Which type of evidence should victims collect to help officials catch cyber bullies ?
-home addresses
-birthdays
-social media
-usernames user
-passwords
Answers
Answer:
Social media
Explanation:
1. A network administrator was to implement a solution that will allow authorized traffic, deny unauthorized traffic and ensure that appropriate ports are being used for a number of TCP and UDP protocols.
Which of the following network controls would meet these requirements?
a) Stateful Firewall
b) Web Security Gateway
c) URL Filter
d) Proxy Server
e) Web Application Firewall
Answer:
Why:
2. The security administrator has noticed cars parking just outside of the building fence line.
Which of the following security measures can the administrator use to help protect the company's WiFi network against war driving? (Select TWO)
a) Create a honeynet
b) Reduce beacon rate
c) Add false SSIDs
d) Change antenna placement
e) Adjust power level controls
f) Implement a warning banner
Answer:
Why:
3. A wireless network consists of an _____ or router that receives, forwards and transmits data, and one or more devices, called_____, such as computers or printers, that communicate with the access point.
a) Stations, Access Point
b) Access Point, Stations
c) Stations, SSID
d) Access Point, SSID
Answer:
Why:
4. A technician suspects that a system has been compromised. The technician reviews the following log entry:
WARNING- hash mismatch: C:\Window\SysWOW64\user32.dll
WARNING- hash mismatch: C:\Window\SysWOW64\kernel32.dll
Based solely ono the above information, which of the following types of malware is MOST likely installed on the system?
a) Rootkit
b) Ransomware
c) Trojan
d) Backdoor
Answer:
Why:
5. An instructor is teaching a hands-on wireless security class and needs to configure a test access point to show students an attack on a weak protocol.
Which of the following configurations should the instructor implement?
a) WPA2
b) WPA
c) EAP
d) WEP
Answer:
Why:
Answers
Network controls that would meet the requirements is option a) Stateful Firewall
Security measures to protect against war driving: b) Reduce beacon rate and e) Adjust power level controlsComponents of a wireless network option b) Access Point, StationsType of malware most likely installed based on log entry option a) RootkitConfiguration to demonstrate an attack on a weak protocol optio d) WEPWhat is the statement about?A stateful firewall authorizes established connections and blocks suspicious traffic, while enforcing appropriate TCP and UDP ports.
A log entry with hash mismatch for system files suggest a rootkit is installed. To show a weak protocol attack, use WEP on the access point as it is an outdated and weak wireless network security protocol.
Learn more about network administrator from
https://brainly.com/question/28729189
#SPJ1
I don't know how to fix this, but it needs me to do something to install a game.

Answers
If you encounter an error message stating that the feature you're trying to use is unavailable while installing the game,it may be related to the missing or corrupted Microsoft Visual C++ redistributable package.
How is this so ?To resolve this issue, you can try installing the Microsoft Visual C++ 2015-2022 Redistributable (x64)- 14.36.32532 manually.
Visit the official Microsoft website,download the package, and follow the installation instructions provided to fix the issue and successfully install the game.
Learn more about Microsoft Visual C++ at:
https://brainly.com/question/30743358
#SPJ1
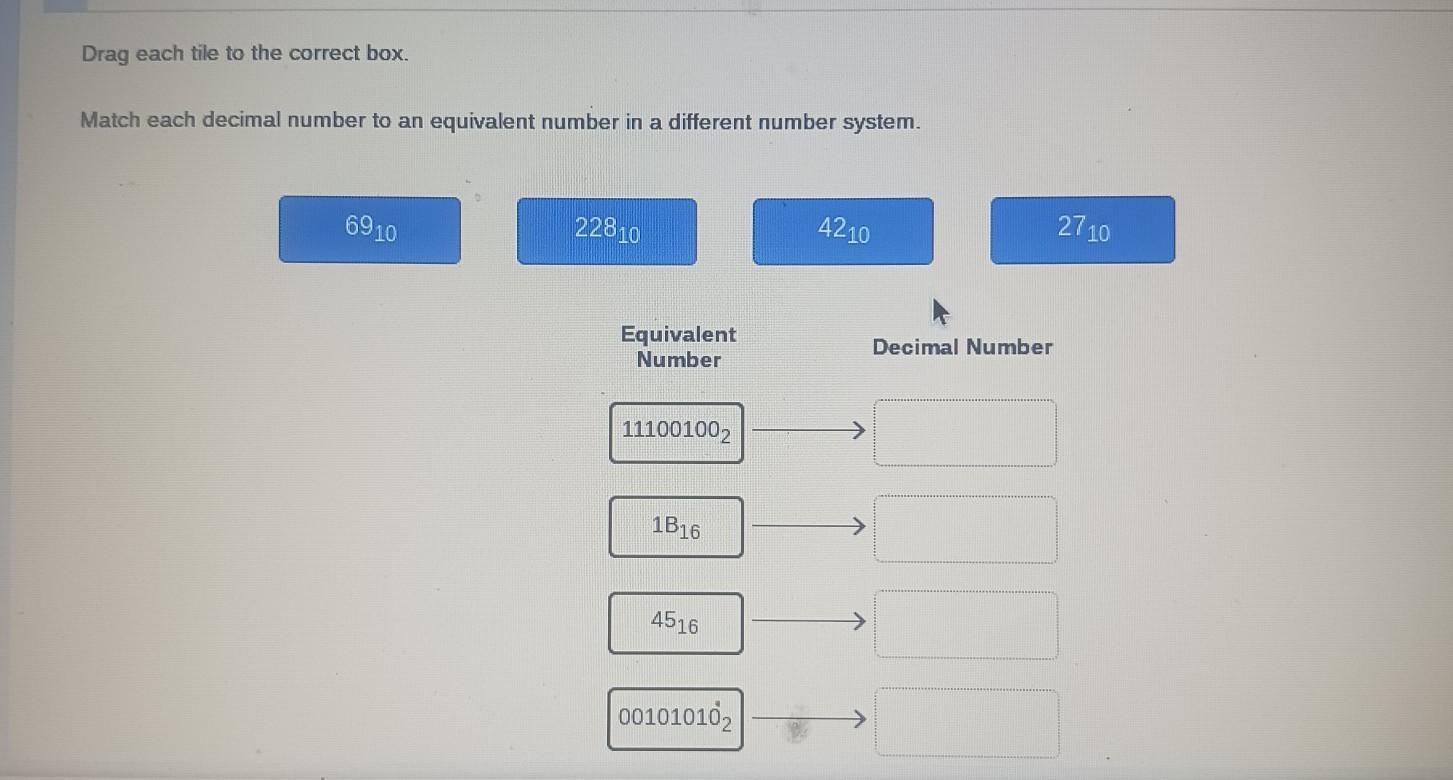
Drag each tile to the correct box. Match each decimal number to an equivalent number in a different number system. 6910 22810 4210 2710
Answers
Explanation:
you can do that with calculator only

If distances are recorded as 4-bit numbers in a 500-router network, and distance vectors are exchanged 3 times/second, how much total bandwidth (in bps) is used by the distributed routing algorithm
Answers
Answer:
A total of 6,000 bps of bandwidth is used by the distributed routing algorithm
Explanation:
This is a bandwidth requirement question.
We proceed as follows;
To calculate the total number of bits for a routing table, we use the following formula;
Routing table=Number of routers * length of cost
we are given the following parameters from the question;
Number of routers = 500
length of cost = 4 bits
Routing table = 500*4
=2000
Hence, a routing table is 2000 bits in length.
Now we proceed to calculate the bandwidth required on each line using the formula below;
Bandwidth = no.of seconds * no.of bits in routing table
Bandwidth required on each line = 3*2000
=6000