To help ensure that an HTML document renders well in many different web browsers, it is important to include which of the following at the top of the file. an tag a doctype declaration a tag a tag
Answers
Answer:
A Doctype
Explanation:
When we first make a HTML document, we ALWAYS add a doctype on the 1st line. It is standard for coders to do so.
Answer:
I think it is:
B. a doctype declarationExplanation:
Related Questions
mobile web apps are actually websites that provide a user experience similar to native apps.
T/F
Answers
True. Mobile web apps are websites designed to be accessed and used on mobile devices.
They utilize responsive design techniques to ensure compatibility and adaptability across various screen sizes. These web apps are accessed through a web browser, similar to traditional websites, but they provide a user experience that closely resembles native mobile apps. Mobile web apps can incorporate features such as push notifications, offline functionality, and access to device hardware (camera, location, etc.) through browser APIs. They are developed using web technologies such as HTML, CSS, and JavaScript, allowing for cross-platform compatibility and easier maintenance compared to developing separate native apps for different operating systems.
Learn more about Mobile web here:
https://brainly.com/question/13110825
#SPJ11
Give 2 example of application software and three advantages and disadvantages
Answers
The concurrent model in the software engineering has been defines the series of the events that will trigger the transition from the state to state for each of the software engineering activities.
What is the use of concurrent model?The concurrent model has been used for the development of the client server applications. The advantages of this model are the following has that it has easy to the implement, the server TCP/IP logic has the simple and one listener has shared by many TPs.
The drawbacks of the model is that it increased the network overhead and delays due to the requirement of the TRM exchange and more CPU and resource intensive than is the Iterative model.
Therefore,The concurrent model in the software engineering has been defines the series of the events that will trigger the transition from the state to state for each of the software engineering activities.
Learn more about concurrent model on:
https://brainly.com/question/4237375
#SPJ1
The AND operator outputs true except where both inputs are false.
True
or
False
Answers
Answer:
true both have to be true for it to have output
Choose the correct term to complete the sentence.
Professional communication must be objective,
, and unemotional
informal
technical
rational
Answers
Answer:
the answer to your question is obviously "rational"
The correct option is rational.
What is Professional communication?Professional communication is a metier subfield of communication that pays close concentration to the theories and methods of communication within professional contexts.After reading this direction, you will better comprehend the four main types of contact: Verbal, non-verbal, written, and visual. You will be able to use this knowledge to improve your transmission and make sure that you are encouraging effective communication skills within your organization. Proficient communication refers to the oral, written, visual, and digital forms of providing information in the context of a workplace. Practical professional communication is essential in today's world. Most situations in an institution arise as a result of poor communication.
To learn more about Professional communication, refer to:
https://brainly.com/question/26152499
#SPJ2
joseph, a black hat hacker, is approached by sigma technology to check the enterprise's security. he is told that the system is being checked to verify whether the higher-security mode of operations is moved automatically to another version during a cyberattack on the network, making it easier to attack. which mode should joseph use to test this vulnerability, and why?
Answers
The mode that Joseph use to test this vulnerability is option A:
. Downgrade attack because, in a downgrade attack, an attacker forces the system to abandon the current mode of operation and instead move it to implement a less secure mode.What is a security downgrade attack?An attempt to coerce a server or client to adopt a less-secure version of a cryptographic protocol (like TLS or SSL), cipher suite (such an export-grade cipher, rather than a standard one), or connection type is known as a "downgrade attack" (HTTP, instead of HTTPS).
Therefore, in regards to the case with Joseph, the use of a downgrade attack, is one that is seen as a threat actor compels the system to "fall back" to using an earlier, less secure mode of operation rather than continuing to operate in its present, higher security mode. The threat actor is therefore free to assault the weaker mode as a result.
Learn more about Downgrade attack from
https://brainly.com/question/28043482
#SPJ1
See full question below
Joseph, a black hat hacker, is approached by Sigma Technology to check the enterprise's security. He is told that the system is being checked to verify whether the higher-security mode of operations is moved automatically to another version during a cyberattack on the network, making it easier to attack. Which mode should Joseph use to test this vulnerability, and why?
a. Downgrade attack because, in a downgrade attack, an attacker forces the system to abandon the current mode of operation and instead move it to implement a less secure mode.
b. Ciphertext attack because, in a ciphertext attack, an attacker forces the system to abandon the current mode of operation instead of moving it to implement a less secure mode.
c. Attacks on misconfigurations because, in a misconfiguration attack, attackers utilize weak configurations to exploit vulnerabilities.
d. Collision attack because, in a collision attack, attackers utilize weak cryptographic algorithms to exploit vulnerabilities.
5 evaluation criteria
Answers
Answer:
relevance, efficiency, effectiveness, impact and sustainability.
Develop an algorithm to print the names of the candidates who should receive a refund. A refund is due if the candidate’s votes received equals or exceeds 20 per cent of the votes cast in the constituency. The algorithm should also determine and print the number of candidates who received a refund. Test the algorithm with data from ten candidates. The algorithm must accept as input the names of the candidates, votes received and the votes cast in the constituency. The algorithm should print the name of the candidate and the words “Refund Due” or “No Refund” and the number of candidates who received a refund.
Answers
Answer:
PROCEDURE calculate_refund(candidates, votes_received, votes_cast)
refund_due = 0
FOR i = 0 TO LENGTH(candidates) - 1
IF votes_received[i] >= 0.2 * votes_cast
PRINT candidates[i] + " Refund Due"
refund_due = refund_due + 1
ELSE
PRINT candidates[i] + " No Refund"
END IF
END FOR
PRINT "Number of candidates who received a refund: " + refund_due
END PROCEDURE
Explanation:
This algorithm takes as input the names of the candidates, the votes received, and the votes cast in the constituency. It loops through each candidate, and if the number of votes received for that candidate is equal to or greater than 20% of the votes cast in the constituency, it prints the candidate name and "Refund Due". If the number of votes received is less than 20% of the votes cast, it prints the candidate name and "No Refund". Finally, the algorithm prints the number of candidates who received a refund.
REOLVER EL SIGUIENTE PROBLEMA: R1=1.7K, R2=33K R3=4.7K R4=5.9K R5=17K IT=20mA CALCULAR: VT, I1, I2, I3, I4, I5 Y RT
Answers
Ok
Step-by-Step Explanation:
Can someone please answer this for me ? What is data centre virtualization?
Answers
Your parents tell you to wear earplugs when you
go see your favorite band in concert. The earplugs
are rated to reduce sound by 40 dB. What will the
earplugs do if you wear them?
cause the band to sound distorted due to
aliasing
o decrease the loudness of the band
decrease the frequency of the band
cause the band to sound clearer due to
oversampling
Answers
Answer:
The answer is B
Explanation:
B. Decrease the loudness of the band
2.2 Code Practice: Question 2
Answers
The codes are written below in python.
What are codes?Coding is a type of computer language that facilitates communication with computers. Human languages are not understood by computers. Coding enables interaction between people and computers.
Code tells the computer what actions to take and which tasks to complete. We read input using the input() method and then convert it to a float using the float() function.
num1 = float(input("Enter a number: "))
num2 = float(input("Enter a number: "))
print("Sum: " + str(num1 + num2))
Therefore, the codes in python are written above.
To learn more about codes, refer to the link:
https://brainly.com/question/18508134
#SPJ9
The complete question is:
Question 2: write a python program to add two numbers.
Lexicographic Comparison • Using the same name from the previous problem, tell the user whether their name comes before or after your name in the dictionary. Indexes • Test whether or not the name contains the letter ‘e’ in the first 3 letters
I have the project in a downloadable pdf.
I can't seem to be able to do "Lexicographic Comparison", with no clue how.
And "Starts With…", I am only able to print if their input is that 1 letter, not the first letter in a word.
Answers
You can also find this code on the repl.it platform. Due to Brainly's policy I can't copy it, I've attached it as a photo and file and you can check it in the comments. Good luck!

________ are a method for tracking what computer users do at various websites and which sites they visit.
Answers
Website cookies are a method for tracking computer users' activities on different websites and monitoring the sites they visit.
Website cookies are small text files that are stored on a user's computer when they visit a website. These cookies serve various purposes, one of which is tracking user activity. When a user visits a website, the site's server sends a cookie to the user's browser, which is then stored on their computer. The cookie contains information such as the user's preferences, login credentials, and browsing behavior.
By tracking the cookies stored on a user's computer, websites can monitor and record their activities across different sites. This tracking allows website owners and advertisers to gather data about user behavior, such as the pages visited, the duration of visits, and the actions taken on the site. This information can be used to personalize the user's experience, deliver targeted advertisements, and analyze user trends.
While cookies can be useful for enhancing user experiences and providing personalized content, they also raise concerns about privacy and data security. Users have the option to manage and control their cookie settings in their browser preferences, including accepting or rejecting certain types of cookies. Additionally, privacy regulations, such as the General Data Protection Regulation (GDPR) in Europe, require websites to obtain user consent before storing and using cookies for tracking purposes.
In conclusion, website cookies serve as a method for tracking computer users' activities on different websites. They provide valuable data for website owners and advertisers but also raise privacy considerations, leading to increased user control and regulatory requirements surrounding their usage.
Learn more about Website cookies here:
https://brainly.com/question/32162532
#SPJ11
What is malicious code and its types?
Answers
Unwanted files or programmes that can harm a computer or compromise data saved on a computer are known as malicious code. Malicious code can be divided into a number of categories, including viruses, worms, and Trojan horses.
A specific kind of destructive computer code or web script intended to introduce system weaknesses that could lead to back doors, security failures, information and data theft, and other potential harm to files and computing systems is referred to as "malicious code" in this context. Antivirus software might not be able to stop the risk on its own. Computer viruses, worms, Trojan horses, logic bombs, spyware, adware, and backdoor programmes are a few examples of malicious programming that prey on common system weaknesses. By accessing infected websites or clicking on a suspicious email link or file, malicious software might infiltrate a machine.
Learn more about malicious from
brainly.com/question/29549959
#SPJ4
What is the output of this program?
numA = 2
numB = 3
if numA == 2 or numB == 2:
print("yes")
elif numA == 2 and numB == 3:
print("no")
Output:
Answers
Answer:
out is no
Explanation:
just took the quiz
The Body Mass Index - BMI is a parameter used to measure the health status of an individual. Various BMI values depicts how healthy or otherwise a person is. Mathematically WEIGHT BMI = WEIGHT/(HEIGHT X HEIGHT) raw the flow chart and write a C++ software for a solution that can a) Collect the following values of an individual: 1. Name 2. Weight 3. Height b) Compute the BMI of that individual c) Make the following decisions if: 1. BMI < 18.5 is under weight 2. BMI >=18.5 but <25 considerably healthy 3. BMI >=25 but <30 overweight 4. BMI >= 30 but <40 Obesity 3 5. BMI >= 40 Morbid Obesity d) Display and explain the results of the individual b) Write brief notes outlining the syntaxes and sample code for the following control structures i. If... Else ii. Nested if iii. Switch iv. For loop v. While loop
Answers
1. Collect the necessary values of an individual: name, weight, and height. 2. Compute the BMI using the formula BMI = weight / (height * height). 3. Use if-else statements to make decisions based on the calculated BMI. For example, if the BMI is less than 18.5, the person is underweight. 4. Display the results of the individual, indicating their BMI category and explaining its meaning.
For the control structures in C++:
1. If... Else: This structure allows you to execute different code blocks based on a condition. If the condition is true, the code within the if block is executed; otherwise, the code within the else block is executed.
2. Nested if: This structure involves having an if statement inside another if statement. It allows for more complex conditions and multiple decision points.
3. Switch: The switch statement provides a way to select one of many code blocks to be executed based on the value of a variable or an expression.
4. For loop: This loop is used to execute a block of code repeatedly for a fixed number of times. It consists of an initialization, a condition, an increment or decrement statement, and the code block to be executed.
5. While loop: This loop is used to execute a block of code repeatedly as long as a specified condition is true. The condition is checked before each iteration, and if it evaluates to true, the code block is executed.
By implementing these control structures in your program, you can control the flow and make decisions based on the BMI value. It allows for categorizing the individual's health status and displaying the results accordingly.
To learn more about if-else statements click here: brainly.com/question/32241479
#SPJ11
Which of the following concerns need to be considered when choosing a modeling too
(1 point)
O the capabilities and the price
O the price and the software security
O the syntax and the software security
O the syntax and the price
Answers
The answer choice that shows the concerns need to be considered when choosing a modeling tool the capabilities and the price
What is a Modelling Tool?This refers to the software application that is used to create and analyze mathematical models of real-world systems or phenomena. Modeling tools can be used in a variety of fields, including engineering, finance, biology, and computer science.
Hence, it can be seen that some concerns about picking a modeling tool include:
Capabilities: It's important to choose a tool that has the features and functionality you need for your modeling project. This might include things like the ability to handle large data sets, support for various types of models, and the ability to visualize and interpret results.
Price: The cost of the modeling tool is also an important consideration. You'll want to choose a tool that fits within your budget, but keep in mind that more expensive options may have more advanced features or better support.
Read more about modelling tools here:
https://brainly.com/question/14208035
#SPJ1
print out the last even number from an array of integers, if there is no even number, then print out a sentence indicating so.
Answers
Answer:
See the sample algorithm below.
Explanation:
array = [1, 2, 3, 4, 5, 6, 7, 8, 9, 22];
function last_even(arr) {
for( i = arr.length-1; i >= 0; i--) {
if (arr[i] % 2 == 0) {
console.log(arr[i]);
break;
}
else {
console.log("There is no even number!");
}
}
}
last_even(array);

name two components required for wireless networking
(answer fastly)
Answers
Explanation:
User Devices. Users of wireless LANs operate a multitude of devices, such as PCs, laptops, and PDAs. ...
Radio NICs. A major part of a wireless LAN includes a radio NIC that operates within the computer device and provides wireless connectivity.
or routers, repeaters, and access points
The binary number represented by the voltage graph below is
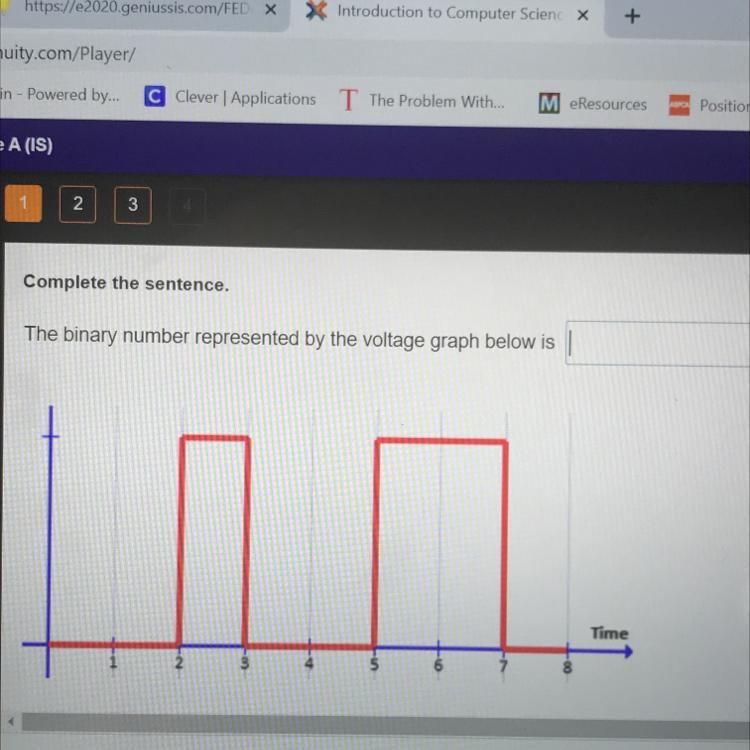
Answers
Answer:
4
Explanation:
Answer: 11010100
here ya go :)
Describe, with examples, the way in which a defect in software can cause harm to a person, to the environment, or to a company
Answers
Answer:
Losing jobs. Fire. Destruction of property.
Explanation:
Having a company shut down due to lack of protection and having people testify products unsafe. If software blows up it could cause desturction of property therefore causing the effect of many people losing their jobs.
hi guy i need advice i am learningto becomea programmer and mybrother islearning to become a materia engineer but when he saw what i am doing with programming he became interest in programming what should i do
Answers
Answer:
he should do programming as it is a very good thing according to me
For Microsoft (MSFT-US), how many changes were made to the 10K between June 2020 and June 2019?
a. 205
b. 117
c. 98
d. None
Answers
Software is Microsoft's annual cost of sales for 2020 increased by 7.38% from 2019 to $46.078B.
Correct option is, D.
What is a fair price for Microsoft's stock?predicated on 29 analysts on Wall Street who have provided Microsoft with 12-month price estimates in the previous three months. With a high projection of $411.00 or a low prediction of $250.00, the average price goal is $291.70. From the most recent price of $252.67, the average selling price target reflects a change of 15.45%.
What is Microsoft famous for?The company was founded in 1975 by Bill Gates and Paul Allen. It is known best for its software products, including the Microsoft Office suite, the Windows operating system, and the web browser Internet Explorer.
To know more about Software visit:
https://brainly.com/question/1022352
#SPJ4
if you set up a network in your home to share your internet connection with several laptops, what type of network have you created?
Answers
You might want to set up a peer-to-peer network, if you have many computers at your house and want to utilize them all to access the Internet.
A distributed application architecture known as peer-to-peer (P2P) computing or networking divides jobs or workloads across peers. Peers are equally qualified and capable members of the network. They are referred to as the nodes in a peer-to-peer network.
Without the need for central coordination by servers or reliable hosts, peers make a portion of their resources, such as processing power, disk storage, or network bandwidth, directly available to other network users.
In contrast to the conventional client-server model, where resource consumption and supply are segregated, peers are both resource suppliers and consumers.
Although peer-to-peer network systems had previously been used in numerous application domains, the architecture was made well-known by the 1999-original file-sharing program Napster.
To know more about peer-to-peer network click here:
https://brainly.com/question/10571780
#SPJ4
During which phase of the writing process is it best to have other
people review your document
O Pre-writing
O Drafting
Revising
O Publishing
Answers
Answer:
the answer should be Revising
Describe the difference between API and ABI services / functions. Which provides access to primitive OS services?
Use the ‘C’ language functions println() and write() as examples of the differences between API and ABI. Hint: how does one use the other? (This was described in class but you should be able to find more online.)
Answers
API (Application Programming Interface) and ABI (Application Binary Interface) are related but distinct concepts in software development. API provides a higher-level interface to access and interact with software components, while ABI defines the low-level interface between compiled code and the operating system. API allows developers to access and use pre-defined functions and services, while ABI ensures compatibility between compiled code and the underlying system.
API (Application Programming Interface) refers to a set of protocols, tools, and definitions that enable developers to build software applications. It provides a higher-level interface that abstracts the underlying implementation details and allows developers to access and use pre-defined functions, libraries, or services. APIs are often documented and provide a standardized way for different software components to interact with each other. Examples of API functions include println() in the C language, which is used to print text to the console, and various functions provided by libraries like Java's java.util or Python's requests.
ABI (Application Binary Interface), on the other hand, defines the low-level interface between compiled code and the operating system or hardware. It specifies the conventions for function calling, parameter passing, memory layout, and other binary-level details. ABI ensures compatibility between different components of the system by defining the binary structure of data and the rules for accessing system services. It provides a standardized interface that allows compiled code to interact with the operating system and utilize primitive OS services. ABI is specific to a particular system architecture and can vary between different platforms.
In the case of println() and write(), println() is an API function provided by a programming language or library, which developers can use to display text. It encapsulates the necessary operations and interacts with the lower-level ABI functions, such as write(), which is a lower-level system call that directly writes data to a file descriptor or device. println() utilizes the underlying write() function to perform the actual output, demonstrating the usage of API functions to utilize ABI services for accessing primitive OS services.
Learn more about Application Programming Interface here :
https://brainly.com/question/32556370
#SPJ11
help wat does ctrl+u means
Answers
Answer:
crtl+u is a shortcut.
Explanation:
Microsoft Windows/KDE/GNOME:
underline
Unix (command line and programs using readline):
Cut text between beginning of line and cursor
Which of these sentences correctly shows how youngsters use the Internet?
A.
Youngsters listen to FM radio programs on the Internet.
B.
Youngsters exchange emails with business organizations.
C.
Youngsters plan their study time and read textbooks online.
D.
Youngsters interact with each other with the help of the Internet.
Answers
Answer:
D
Explanation:
This is the only possible answer lol please give brainliest and good luck :)
Digital Print Project
For this project, explore techniques, new equipment, and software features surrounding one type of digital-printing technology that interests you. Here are some suggestions:
photo retouching
3D printing
multi-function machines
CAD printing machines
T-shirt printing machines
desktop engravers
If you have access to the machine and software connected with your printing technology choice, do some hands-on work to learn more about its features and to improve your skills. If you do not have access to the digital-design software or are interested in professional technologies like 3D printing, you may concentrate on the equipment and process through an online user’s manual.
You should have two kinds of data backing up your report:
DATA COLLECTED HANDS-ON from a physical machine in one or more of these locations:
a school
a public library workshop
a knowledgeable friend or teacher
print professionals
INFORMATION COLLECTED THROUGH ONLINE RESEARCH from at least two of the following:
company websites
free tutorials
designers’ websites
publishing websites
Remember, your report must include both hands-on data and online research information.
Present your project as a three-five page report, plus either:
an eight- to ten-slide presentation, or
• an actual final print that you have made and a digital file of your result.
Your written presentation should clearly explain:
why you chose your selection,
how you actually worked with your selection,
what equipment, software versions, and print interfaces you used,
what you researched that proved helpful,
what type of training or degree program is required working in a field using your chosen digital printing technology,
what you learned about available schools, tutorials, or courses that will sufficiently prepare someone interested in a job using that technology,
whether you like your choice and what you have concluded as a result of your research.
Answers
TOPIC: BIOLOGICAL MACROMOLECULES
answer !
1. Define proteins, nucleic acids, carbohydrates and lipids
2. Summarize the general characteristics of each biomolecule and
3. Appreciate the importance of eating a balance diet
What is bookbinding printing? Letterpress or book printing refers to a certain specialized printing process that produces letterpress stationery. Letterpress, also a type of relief printing, is the process of cutting out the surface and printing from the raised residue. You may have seen letterpress paper before. Most modern letterpress papers can be recognized by their distinctive look on thick paper. Today, letterpress printing products are known for their high quality and unparalleled sophistication. Most people are unaware of the long history behind typographic techniques and tools. Modern letterpress products would not have been possible without a combination of centuries of refinement of old letterpress methods and modern polymer plate technology. Get a behind-the-scenes look at how Minted pays tribute to this centuries-old art form, and learn why book printing is a unique fusion of past and present. Browse Minted's hundreds of gorgeous typographic Christmas cards and typographic wedding invitations to find one that fits your style.
history of printing
"Letterpress" or "letterpress" refers to a printing technique developed by German innovator Johannes Gutenberg in the 15th century. Gutenberg was dissatisfied with modern printing methods and saw an opportunity to develop more effective printing techniques. Gutenberg was also driven by his desire to make books more accessible to the general public and improve literacy. Before the invention of the printing press, printing was time consuming, labor intensive and tedious. The pages of the book he carved into individual wooden panels, one at a time. The letters were left intact while the remaining space was clipped, resulting in raised letters. To further complicate this, printing resulted in a mirror version of the stamp or plate used, so all letters and words were upside down. The lettering in relief is then inked and the paper is lightly touched against the wooden panel where the craftsman has inked it. Because of this, the original typography never quite got the embossed look and feel that is so popular today. This made one page of the book. Gutenberg's attempt to change this method began with a small plate containing a single upside-down letter. These panels, called movable types, can be placed on a sturdy wooden frame to form any word or sentence. However, certain images and designs had to be freely engraved on wood or metal plates. Gutenberg used his knowledge from his background in blacksmithing to invent this wooden-framed printing press. There, the letters were coated with a permanent ink that he had prepared. This is another of his famous inventions. The rotating handle of the press allowed the paper to be scrolled. This paper is flattened and pressed against the inked letters on the crate to create the final product. Hence, this process has rightly earned the name "book printing".
letter printing today
Today, typography is making a comeback in high-quality wedding invitations, wedding dates, Christmas and holiday cards, birth announcements, and more. This revival, especially in the last 30 years, is due not only to unique aspects of modern book printing that cannot be replicated by other printing methods, but also to the support of people like Martha Stewart. Stewart praised 1990s typographic products, especially wedding invitations. Consumers saw a tangible quality of the design pressed into the cardboard, called embossing, in the image of the typographic product Stewart was promoting. This has increased the demand for book printing products. However, this was not the intention of the original book publishers. It's actually a result of the recent use of polymer plates. As such, this handmade tactile typographic stationery is notorious for not being representative of historical typographic products. A modern addition to centuries-old typographic technology, this feature embodies a bridge between classical craftsmanship and modern technology. Today, you might also see letterpress variations such as foil stamping and embossing. One of the only drawbacks of modern letterpress technology is that it loses the uniqueness of the original letterpress product. You can print many identical sheets of polymer from one design on your computer, producing indistinguishable products. This consistency may be desirable in some cases. B. Wedding invitations. However, modern letterpress stationery will never have the rare quality of printing made from unique carved panels of wood or metal. I need to print on very thick paper. Cotton paper is ideal for letterpress printing because of its soft feel, texture, and thickness. Also, cotton paper is more environmentally friendly than paper made from trees. Another modern variation of historical typography is blind printing. In blind letterpress printing, the polymer plate is not inked prior to printing.
discuss the ways in which inheritance promotes software reuse, saves time during program development and helps prevent errors.
Answers
The ways in which inheritance promotes software reuse, saves time during program development and helps prevent errors are:
Reusability: The idea of "reusability" is supported by inheritance; for example, if we want to construct a new class but an existing class already contains some of the code we need, we can derive our new class from the old class. We are utilizing the fields and methods of the pre-existing class by doing this.
A superclass. - Building a class inheritance tree can help developers avoid duplicating functionality across multiple classes, which can save a lot of effort.
What is software development using inheritance?One of the key components of object-oriented programming is polymorphism. In C++, polymorphism enables code reuse by allowing the creation of a single function with various purposes.
One of the fundamental ideas in object-oriented programming (OOP) languages is inheritance. It is a mechanism that allows you to create a hierarchy of classes that share a set of properties and methods by deriving a class from another class.
Therefore, Polymorphism allows for distinct actions depending on context and object, whereas inheritance allows a class to define its own set of behaviors and methods. As a result, inheritance increases the modularity of the code. This strategy makes it possible to reuse code and is advantageous for minimizing program duplication.
Learn more about Reusability from
https://brainly.com/question/25753189
#SPJ1