To allow a document to be opened easily on most computers, save the document as a _____.
a hyperlink
require a password
a template
read only
Answers
Answer:
Explanation:
Answer:read only
Explanation:
Related Questions
Question 4 of 20
most applications will ask you to provide all of the following information
except
a. the date you can start work
b. the dates and hours you are available to work.
c. your desired salary or wage.
d. which of your previous jobs you didn't like.
Answers
Most applications will ask you to provide all of the following information except (d) which of your previous jobs you didn't like. The correct option is D.
Job applications typically require information such as your availability to start work, your preferred work schedule, and your desired salary or wage, as these are relevant to the employer's needs and decision-making process. However, they do not generally ask for personal opinions or preferences about previous jobs, as this is not relevant to the current application.
When filling out job applications, focus on providing the necessary information, such as your availability and desired compensation, and avoid discussing any negative experiences with previous jobs. The correct option is D.
To know more about decision-making process visit:
https://brainly.com/question/29772020
#SPJ11
Sam is a Windows system administrator responsible for setting up client workstations for different departments. After installing the operating system, Sam manually disables certain programs that aren't needed by that department. Recently, Sam learned a few workstations had been compromised. The security analyst suggests that the disabled applications may have been the target. Going forward, what should Sam change in his process
Answers
Answer:
not disable any programs after installing a new operating system
Explanation:
Sam should simply not disable any programs after installing a new operating system. If the system is working as intended then he should leave it be, as the saying says "Don't fix what isn't broken". When a new operating system is installed, the entire system is usually wiped, meaning that the only programs installed have been installed as defaults by the operating system. Usually, this is for a reason and acts as security measures for the user, the system, and all of the data. Most of these programs interact with each other and work off of each other's data. Removing them from the system can prevent other very important functions of the operating system from performing their duties, which in term can compromise the entire security of the system. Therefore, the best thing to do would be to not remove these default programs.
"we cannot provide any information about your refund tax topic 152". What does that mean?
Answers
The status update message "Tax Subject 152" is a confirmation that the IRS has received and is processing the taxpayer's return; it does not imply that there is a problem with the return.
The IRS "Where's My Refund?" website displays a notification that reads "Tax Topic 152." mechanism to let people know that their tax return is being handled and that they will be given a refund date as soon as one is available. It indicates that the IRS has received the taxpayer's return and is currently processing it. This message does not indicate a problem with the return, but rather that the IRS is working on it. If the taxpayer sees this message, they should continue to check the tool for updates and wait for their refund to be processed.
Tax Topic 152 is not a warning or an error notice. It is simply a status update message that lets taxpayers know that their return has been received by the IRS and is being processed. The message may appear after the taxpayer has filed their tax return and is checking the status of their refund using the "Where's My Refund?" tool on the IRS website. It is important to note that the IRS may take several weeks to process a tax return, so it is important to be patient and continue to check for updates. If there are any issues with the return, the IRS will contact the taxpayer directly.
Learn more about IRS here:
https://brainly.com/question/30401300
#SPJ4
how can robots help us with online learning? 3 reasons please thank u :)
Answers
Answer:
The use of robots increases the practicality of online education, such that the difference between in person attendance and online learning is minimized
In elementary school, robots can help deliver teaching materials in a class like setting, to students who are unable to attend classes due to their current situation
In high school, simulators can give driving (and flying) lessons to would be drivers, without the exposure of the students to risk
Robots in higher education, such as medicine, can be used to carry out operational procedures with students where, there are no subjects to perform the surgical procedure on
The use of simulators makes possible training in disaster and crisis management
Explanation:
in question 6, suppose one computer is upgraded from windows 10 professional to windows server 2019. which networking model can the network now support that it could not support without the upgrade?
Answers
In question 6, if a computer is upgraded from Windows 10 Professional to Windows Server 2019, it can now support the Domain-based networking model that it could not support without the upgrade.
What do you mean by domain-based networking model?The Domain-based networking model is a centralized model in which a central server called a domain controller is used to authenticate and authorize network access. This model is typically used in larger organizations and it requires the use of a server operating system like Windows Server.
Windows 10 Professional does not have the capabilities to act as a domain controller, but Windows Server 2019 does.
With the upgrade to Windows Server 2019, the computer can now function as a domain controller and support the Domain-based networking model, allowing for centralized management and control of network access. It also supports other advanced features like active directory, group policy management, and domain name system (DNS) integration, which are not present in Windows 10 Professional.
To know more about server visit:
https://brainly.com/question/7142205
#SPJ4
8. go to the items by category worksheet. anthony created a pivottable that lists each item by category, and then counts the number of those items acquired each year. the data is sorted in alphabetic order by category, but anthony wants to sort the data by total number of items. he also wants to focus on coins and comic books only. change the display of the pivottable as follows: a. sort the data in descending order by grand total. b. apply a label filter that displays category values that begin with co.
Answers
A PivotTable is a powerful tool to calculate, summarize, and analyze data that lets you see comparisons, patterns, and trends in your data.
What is pivot table?PivotTables work a little bit differently depending on what platform you are using to run Excel. One of Excel's most useful features are pivot tables. You can draw the significance from a sizable, comprehensive data collection using a pivot table.
There are 6 fields and 213 records in our data set. Product, Category, Amount, Date, and Country for the Order.
One of the fundamental tools for data analysis is the pivot table. Many significant business concerns can be swiftly resolved with pivot tables.
Therefore, A PivotTable is a powerful tool to calculate, summarize, and analyze data that lets you see comparisons, patterns, and trends in your data.
To learn more about pivot table, refer to the link:
https://brainly.com/question/1316703
#SPJ1
Plot the graph of absorbance versus dilutions of *Saccharomyces
cerevisiae on Microsoft Excel
a) Only plot trend line for linear range of data; show the R^2
value for each dataset
b) You may chose to
Dilutions Blank 1:16 1:8 1:4 1:2 550 0.000 0.098 0.206 0.418 0.810 1.418 Wavelength (nm) 620 0.000 0.075 10.169 0.368 0.714 1.162 690 0.000 0.053 0.134 10.308 0.604 1.044 1:1 Plot the graph of absorba
Answers
I can guide you on how to create the graph you described. Here are the steps: By following these steps, you should be able to create a graph of absorbance versus dilutions in Microsoft Excel, including the trendline and R-squared value for each dataset.
1. Open Microsoft Excel and enter the dilutions in one column and the corresponding absorbance values in another column.
2. Select the data range and click on the "Insert" tab in the Excel menu.
3. Choose the chart type that represents the relationship between dilutions and absorbance. In this case, a scatter plot with markers connected by a smooth line (XY scatter with smooth lines) would be suitable.
4. Right-click on any data point on the graph and select "Add Trendline" from the context menu.
5. In the "Format Trendline" options, select the "Linear" trendline type.
6. Enable the option to display the equation and R-squared value on the chart.
7. Adjust the axis labels, title, and other formatting options to enhance the clarity of the graph.
To know more about Microsoft Excel visit-
https://brainly.com/question/32584761
#SPJ11
which statement most accurately describes the mechanisms by which blockchain ensures information integrity and availability?
Answers
The statement that most accurately describes the mechanisms by which blockchain ensures information integrity and availability is: "Blockchain utilizes a decentralized, distributed ledger with cryptographic hashing.
And consensus algorithms to maintain data integrity and ensure its availability across multiple nodes."
Blockchain ensures information integrity and availability and most accurately describes the mechanisms by which blockchain ensures information integrity and availability. The decentralized nature of blockchain technology allows for multiple copies of the same data to be stored across the network, making it extremely difficult for any one party to tamper with the information without being detected. Additionally, the use of cryptographic hashing and digital signatures further ensures the authenticity and integrity of the data stored on the blockchain. Finally, the availability of the data is ensured through the continuous validation and synchronization of the network nodes, making it accessible to anyone with an internet connection.
To learn more about Blockchain Here:
https://brainly.com/question/31080398
#SPJ11
The complete question is:
Which statement most accurately describes the mechanisms by which blockchain ensures information integrity and availability?
A. Blockchain ensures availability by cryptographically linking blocks of information, and integrity through decentralization.
B. Blockchain ensures availability through decentralization, and integrity through cryptographic hashing and timestamping.
C. Blockchain ensures availability through cryptographic hashing and timestamping, and integrity through decentralization.
D. Blockchain ensures both availability and integrity through decentralization and peer-to-peer (P2P) networking.
Design and implement a program that reads in a string and then outputs the string, but only one character per line. Use a scanner object and the nextLine method to read in the string of characters. Use a for loop to process the string. You will also need to make use of the length and charAt methods defined in the string class. When the input is as shown in Figure 1, your program should produce output as shown in Figure 2.
Answers
The program reads in a string and outputs the string with only one character per line.
Here's the answer to the given question.
1. Using the Scanner object and nextLine method, read in a string of characters.
2. Using a for loop, process the string. Use the length and charAt methods from the string class.
3. Output the string with only one character per line.
Explanation: The solution to the question is as follows:
import java.util.Scanner;class
Main { public static void main(String[] args) { Scanner input = new Scanner(System.in);
System.out.print("Enter a string: ");
String str = input.nextLine();
System.out.println("Output:");
for (int i = 0; i < str.length(); i++) { System.out.println(str.charAt(i)); } }}
Explanation: The above code takes the input string from the user using a Scanner object and the nextLine method.
The for loop is used to iterate over each character of the input string. The length method is used to find the length of the input string. The charAt method is used to find the character at a specific index in the string.
The output is printed using the System.out.print
ln statement with the charAt method. The output is printed with only one character per line using the println method.
The output is displayed with a heading "Output:" using the println statement.
In conclusion, the program reads in a string and outputs the string with only one character per line.
To know more about program visit
https://brainly.com/question/3224396
#SPJ11
who are your favorite You tubers mine are the Dobre Brothers
Answers
Answer:
mine are H2O delerious and Lazar beam
Explanation:
I enjoy watching watching whatever comes up on my recommended page :)
Complete the sentence about RSA encryption.
The two numbers, P and Q, used to find the keys _________
options:
- are divisible by two prime numbers
- usually consist of thousands of bits
- can be small numbers as long as they prime
answer: usually consist of thousands of bits
somebody please add an answer so this doesnt get deleted
Answers
The two numbers, P and Q, used to find the keys as they usually consist of thousands of bits.
What is the numbers P and Q in RSA encryption?The RSA algorithm is known to be the Rivest-Shamir-Adleman. It is said to be a kind of algorithm that is often used by technologies in message encryption and its decryption.
It known to be made up of asymmetric or also of public-key cryptography. In the steps for RSA algorithm, one has to Choose two large prime numbers P & Q.
Learn more about RSA encryption from
https://brainly.com/question/17486027
Answer: usually consist of thousands of bits
Explanation:
Got it right
2.3 pseudocode exercise on edhesive
Answers
Answer:
a=int(input("Enter a numerator: "))
b=int(input("Enter a divisor: "))
quotient=a/b
remainder=a%b
print("Quotient is: " + str(int(quotient)))
print("Remainder is: " + str(int(remainder)))
That's 2.3 question 1
a_ft = int(input("Enter the Feet: "))
a_inc = int(input("Enter the Inches: "))
b_ft = int(input("Enter the Feet: "))
b_inc = int(input("Enter the Inches: "))
sum_inc = a_inc + b_inc
# select the whole and the fractional part
inc_to_ft = sum_inc // 12
rem_from_div = sum_inc % 12
sum_ft = a_ft + b_ft + inc_to_ft
print("Feet: {} Inches: {}".format(sum_ft, rem_from_div))
That's 2.3 question 2
Explanation:
I wasn't sure which one you needed so I added both.
Can covering up your laptop's camera with a sticky note damage it? I see some articles saying not to cover it and some to cover your camera.
Answers
Answer and Explanation:
I have a sticky note in front of my camera, just don't put the sticky part on the camera,
Bend it so that part of the sticky note is covering that top portion of your laptop, while also not covering your actually screen.
This makes sure that no one sees you if they were to hack into your camera with you knowing/not knowing
#teamtrees #PAW (Plant And Water)
When Tomohiro Nishikado invented Space Invaders® in 1978, the microcomputers available in Japan could not handle its initial complexity which led Nishikado to import a CPU from the United States that was integrated into a microprocessor. This is a classic example of what?
A. innovating to overcome a technical challenge
B. the need to import items for any technology to really work
C. how the U.S. is better with technology than Japan
D. quitting when technical challenges arise
Answers
Answer:
The answer is A. Innovating to overcome a technical challenge!
hope this helps! <3
which can be used in passive reconnaissance attacks?
Answers
Passive reconnaissance attacks can utilize various techniques such as network sniffing, monitoring network traffic, and analyzing publicly available information.
How can passive reconnaissance attacks be conducted?Passive reconnaissance attacks refer to techniques used to gather information without actively engaging with the target system or network. These attacks aim to collect data covertly, often by observing network traffic, analyzing publicly available information, or performing network sniffing.
Network sniffing involves capturing and analyzing network packets to extract sensitive information like usernames, passwords, or confidential data. Monitoring network traffic allows attackers to gain insights into the communication patterns and potential vulnerabilities of a target system.
Additionally, analyzing publicly available information, such as through search engines or social media, can provide valuable insights for planning and executing targeted attacks. It's important to note that passive reconnaissance attacks can be a precursor to more aggressive and targeted attacks. Understanding these techniques helps in implementing appropriate security measures to safeguard against such threats.
Learn more about Passive reconnaissance
brainly.com/question/32703039
#SPJ11
write the sum 5 6 7 8 95 6 7 8 9 using sigma notation. the form of your answer will depend on your choice of the lower limit of summation. note that kk is the index of the summation.
Answers
The sum 5 + 6 + 7 + 8 + 95 + 6 + 7 + 8 + 9 can be represented using sigma notation as ∑(k=1 to 9) xₖ, where xₖ represents each number in the sequence. The lower limit of summation is 1. Sum = 151.
To represent the sum of the numbers 5, 6, 7, 8, 95, 6, 7, 8, and 9 using sigma notation, we can choose the lower limit of summation to be 1.
The sigma notation for this sum would be:
∑(k=1 to 9) xᵏ
Where xₖ represents each individual number in the sequence. In this case, xₖ would correspond to the numbers 5, 6, 7, 8, 95, 6, 7, 8, 9 respectively for k = 1, 2, 3, 4, 5, 6, 7, 8, 9.
Thus, the sum in sigma notation would be:
∑(k=1 to 9) xₖ = 5 + 6 + 7 + 8 + 95 + 6 + 7 + 8 + 9
Alternatively, if you want to express the sum explicitly:
∑(k=1 to 9) xₖ = x₁ + x₂ + x₃ + x₄ + x₅ + x₆ + x₇ + x₈ + x₉
Substituting the values:
∑(k=1 to 9) xₖ = 5 + 6 + 7 + 8 + 95 + 6 + 7 + 8 + 9
= 151
Learn more about Sigma notation: https://brainly.com/question/30518693
#SPJ11
What kind of sharpener can be described as having sharpening wheels that are powered to spin against the blade,meaning that it takes very little effort to use?
A.a limestone sharpener
B.a metal rod
C.a manual sharpener
D.an electric sharpener
Answers
The kind of sharpener that can be described as having sharpening wheels that are powered to spin against the blade, meaning that it takes very little effort to use, is an electric sharpener.
This type of sharpener uses a motor to power the sharpening wheels, allowing them to spin rapidly against the blade. This makes the sharpening process much faster and more efficient than with a manual sharpener or a metal rod. Additionally, the electric sharpener's ease of use and convenience make it a popular choice for those who want to sharpen their knives and tools quickly and easily.
learn more about sharpening wheels here:
https://brainly.com/question/21985897
#SPJ11
How do you flatten a 2D array to become a 1D array in Java?
Answers
Answer:
With Guava, you can use either
int[] all = Ints.concat(originalArray);
or
int[] all = Ints.concat(a, b, c);
Explanation:
Use GUAVA
Find the entropy of a source that emits one of 10 symbols A,B,C,D,E,F,G,H and I in a statistically independent sequence with probabilities 1/2,1/4,1/8,1/2,1/8,1/1,1/4,1/2 and 1/4 respectively
Answers
The entropy of the source is 2.079 bits. Entropy can be defined as a measure of the amount of uncertainty in a probability distribution.
In Information theory, it is used to quantify the amount of information that is conveyed by a message.
Given the probabilities p1, p2, ..., pn of n symbols, the entropy of the source is given by the formula:
H(X) = -p1 log p1 - p2 log p2 - ... - pn log pnIn this case, there are 10 symbols A, B, C, D, E, F, G, H, and I. Let p1, p2, ..., p10 denote their respective probabilities. We are told that these symbols are emitted in a statistically independent sequence.
This means that the probability of observing a particular sequence of symbols is simply the product of their individual probabilities.For example, the probability of observing the sequence ABFGI is given by:
P(ABFGI) = p1 * p2 * p6 * p8 * p10 Now, we are given the probabilities of the individual symbols:
p1 = 1/2p2 = 1/4p3 = 1/8p4 = 1/2p5 = 1/8p6 = 1/1p7 = 1/4p8 = 1/2p9 = 1/4
Using these probabilities, we can calculate the entropy of the source: H(X) = -p1 log p1 - p2 log p2 - ... - p10 log p10H(X) = -(1/2) log(1/2) - (1/4) log(1/4) - (1/8) log(1/8) - (1/2) log(1/2) - (1/8) log(1/8) - (1/1) log(1/1) - (1/4) log(1/4) - (1/2) log(1/2) - (1/4) log(1/4)H(X) = 2.079 bits
Therefore, the entropy of the source is 2.079 bits.
To know more about entropy visit:
brainly.com/question/9171028
#SPJ11
What’s Discord Packing?
Answers
Make jokes while yelling and shouting. Joke 4 When you and another person are at odds, you make a joke, and when you're done, the other person does the same. You conduct a poll to determine who was funnier. Loudmicing is what it sounds like, and that's all you do. When you pack but don't make any settings, you are lowsiding.
What best define about Discord Packing?When two or more people engage in “discord packing,” they may roast one another or crack offensive jokes about one another. Discord packing comes in a variety of forms, including stamina packing, blazing, joke-for-joke, loudmicing, and lowsiding. Most people pack in a flaming manner.
Therefore, When people use loud microphones to yell and scream at each other in a voice call for fun or beef. To avoid waking up the participants' parents, they typically take place late at night.
Learn more about packing here:
https://brainly.com/question/15114354
#SPJ2
Exercise #3: Write a program that finds all students who score the highest and lowest average marks of the first two homework in CS (I). Your program should read the data from a file called " "
Answers
To find students with the highest and lowest average marks in the first two CS (I) homework, read data from a file, calculate averages, and print the corresponding student names using the provided Python code.
To write a program that finds all students who score the highest and lowest average marks of the first two homework in CS (I),
Read data from the file.First of all, the program should read data from a file. The file name is " ". Calculate the average of the first two homework for each student. Then the program should calculate the average of the first two homework for each student, and store it in a dictionary with the student's name as the key.Find the highest and lowest averages.After that, the program should find the highest and lowest averages and the corresponding student names.Print the names of the students who have the highest and lowest average marks.Finally, the program should print the names of the students who have the highest and lowest average marks.Below is the Python code that can be used to find the students who score the highest and lowest average marks of the first two homework in CS (I):
```python#open the filefile = open('filename', 'r')#initialize a dictionary to store the average of first two homework marks for each studentdata = {}#iterate through each line of the filefor line in file:#split the line into a list of valuesvalues = line.strip().split()#get the student's name and the first two homework marksname = values[0]marks = [int(x) for x in values[1:3]]#calculate the average of the first two homework marksaverage = sum(marks)/len(marks)#store the average in the dictionarydata[name] = average#find the highest and lowest averageshighest = max(data.values())lowest = min(data.values())#find the students with the highest and lowest averageshighest_students = [name for name, average in data.items() if average == highest]lowest_students = [name for name, average in data.items() if average == lowest]#print the names of the studentsprint('Students with highest average:', ', '.join(highest_students))print('Students with lowest average:', ', '.join(lowest_students))```
Note: Replace the 'filename' with the actual name of the file that contains the data.
Learn more about Python code: brainly.com/question/26497128
#SPJ11
Which of the following robots was considered by the industry as the first useful robot?
a. PLANETBOT
b. ASIMO
c. Colossus
d. AESOP
Answers
Answer:
I think its ASIMO. Though I am not fixed.
Explanation:
Determine whether mr.Mullins is eligible. Why or why not
Answers
Mr. Mullins is not eligible as he made some critical decisions without actually getting to the root of them.
How to determine Mr. Mullin's eligibilityThe text about Mr. Mullins and Mr. Conatser was because the former gave the latter permission to drive a truck because he had seen him driving a similar vehicle.
The only condition in which Mr. Mullins would be eligible would be if he had followed the right steps in determining the legal right of Mr. Conatser to drive a truck.
Learn more about eligibility here:
https://brainly.com/question/1138155
#SPJ1
the screen displayed once a computer completes booting up?
Answers
The screen displayed once a computer completes booting up is called the desktop screen.
After a computer completes the booting process, it displays the desktop screen. The desktop screen is the main graphical user interface (GUI) that allows users to interact with the computer.
The desktop screen typically consists of:
Icons: These represent files, folders, and applications, providing a visual representation of the computer's contents. By clicking on an icon, users can open files or launch applications.Taskbar: Usually located at the bottom of the screen, the taskbar contains the Start button, system tray, and open application windows. The Start button provides access to the computer's programs and settings, while the system tray displays the time, volume control, and other system notifications.Wallpaper: The wallpaper is the background image that appears behind the icons and windows. Users can customize the wallpaper to their preference.The desktop screen serves as a launching point for accessing files, running applications, and performing various tasks on the computer. It provides a visual representation of the computer's contents and allows users to navigate and interact with the system.
Learn more:About computer booting up here:
https://brainly.com/question/28201596
#SPJ11
The screen displayed once a computer completes booting up is called the desktop. It typically consists of icons, a taskbar, and a background wallpaper, providing a graphical user interface (GUI) for users to interact with the operating system and launch applications.
After a computer completes the boot process, the desktop is the user's primary interface with the operating system. It is the visual representation of the user's workspace and provides access to various system resources and applications. The desktop screen typically includes icons that represent files, folders, and applications, allowing users to easily navigate and launch programs or open documents.
The desktop also includes a taskbar or a dock, which is a bar usually located at the bottom or the side of the screen. The taskbar displays the Start menu (in Windows) or the application launcher (in macOS), system tray, and open windows or applications. It provides quick access to frequently used programs and allows users to switch between open applications or documents.
Furthermore, the desktop background, also known as wallpaper, is the image or color scheme displayed as the backdrop of the desktop. Users can customize the desktop background to their preference, choosing from a variety of images or setting their own pictures.
To know more about graphical user interface (GUI) click here,
https://brainly.com/question/10247948
#SPJ11
In a certain code ADVENTURES is written as TRDESAUVEN. How is PRODUCED written in that code
Answers
Answer:
The first and sixth, third and eighth, fifth and tenth letters of the word interchange places in the code. :)
what is the meaning of HML
Answers
Answer:
Explanation:
Hit my line
Which of the variables have the value 50 after executing the code segment?
see the image below for reference
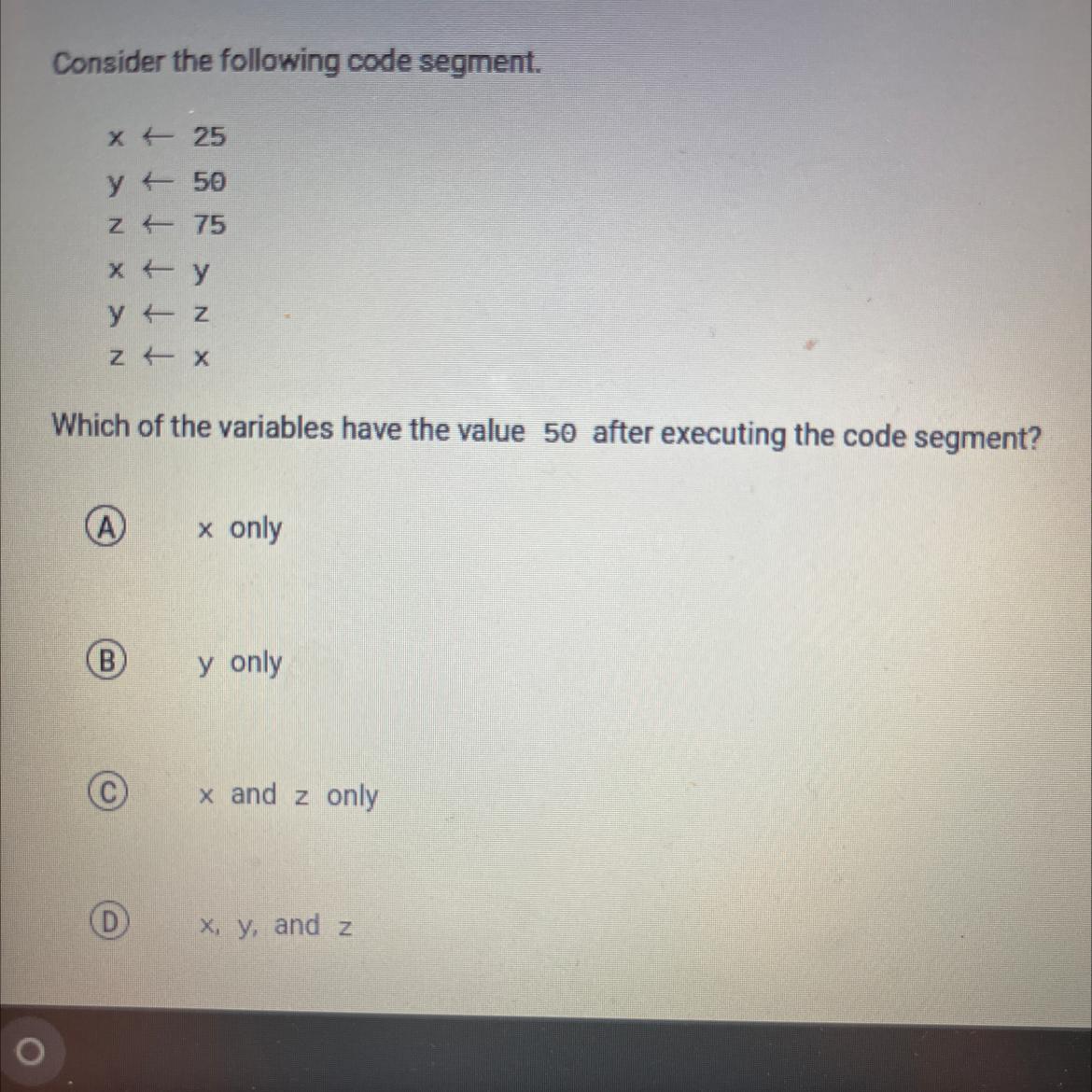
Answers
The segment of code that will have the value of 50 after executing the code segment is this:
C. X and Z only
What is the segment?A segment is a section of code that instructs the computer to take certain actions. In the above code, we can see that the y value is set to return the value of 50.
Also, in the fourth instruction, the x value is instructed to return the value of y. So, the segment of code that is meant to execute and return the number, 50 is option c which contains x and z.
Learn more about coding here:
https://brainly.com/question/22654163
#SPJ1
Accessing cash from some customers' accounts at the ATM during
weekends:
Answers
Answer:
what kinda question is this? i dont see a question i would try to help if i understand.
Explanation:
you're installing two new hard drives into your network attached storage device your director ask sthat they be put ionto a raid solution
Answers
When installing new hard drives, the appropriate choice would be RAID 1 or RAID 5 for redundancy over performance in a RAID solution.
How is this so?RAID 1 (mirroring) duplicates the data across both hard drives, providing a complete copy of the data on each drive for fault tolerance.
RAID 5 distributes data across multiple drives with parity information, allowing for recovery in case of a single drive failure.
RAID 0, RAID 6, and RAID 10 prioritize performance over redundancy.
Learn more about hard drives at:
https://brainly.com/question/28098091
#SPJ1
Full Question:
You're installing two new hard drives into your network attached storage device. Your director asks that they be put into a RAID solution that offers redundancy over performance. Which would you use? RAID 0 RAID 1 RAID 5 RAID 6 RAID 10
Which of the following is concerned with the analyst's time and the costs for system development, hardware, and business employee time?
A. economic feasibility * B. operational feasibility C. tactical feasibility D. technical feasibility
Answers
The option that is concerned with the analyst's time and the costs for system development, hardware, and business employee time is A. economic feasibility.
Economic feasibility is the aspect of a feasibility study that focuses on assessing the financial viability and cost-effectiveness of a proposed system or project. It involves evaluating the costs associated with system development, including the analyst's time, hardware expenses, and the time and resources required from business employees. Economic feasibility analyzes the potential return on investment (ROI) and determines whether the benefits of implementing the system outweigh the costs. This feasibility factor considers factors such as development costs, operational costs, maintenance costs, and the potential impact on the organization's profitability. By assessing the economic feasibility, organizations can make informed decisions about the financial viability of implementing a new system or project and allocate resources effectively to ensure the project's success.
To learn more about hardware visit:
brainly.com/question/3186534
#SPJ11