The ____ tool is an easy-to-use method of modifying the GNOME desktop.
Answers
Answer:
The GIMP tool is an easy-to-use method of modifying the GNOME desktop.
Related Questions
Consider the following MIPS code.
I0: lw $s1, 0($s2)
I1: lw $s3, 12($s4)
I2: add $s5,$s1,$s3 # $s5 := $s1 + $s3
I3: beq $s5,$s7, L1 # if ($s5 = $s7) goto L1
I4: sw $s5,0($s3)
I5: L1: sw $s5,12($s4)
A) Suppose a MIPS processor uses the simple 5-stage pipeline, where the stages are instruction fetch (IF), instruction decode and operand fetch (ID), execute and calculate address (EX), memory access (M), and write back (WB). In addition, suppose that:
The instruction and data cache are unified and can only support one read or write or instruction fetch operation each cycle.
The pipeline does not have “forwarding” hardware. Thus, if an instruction (i + 1) relies on a value written into a register by an instruction (i), then the execute stage for (i + 1) cannot proceed until the register write stage for (i) has completed.
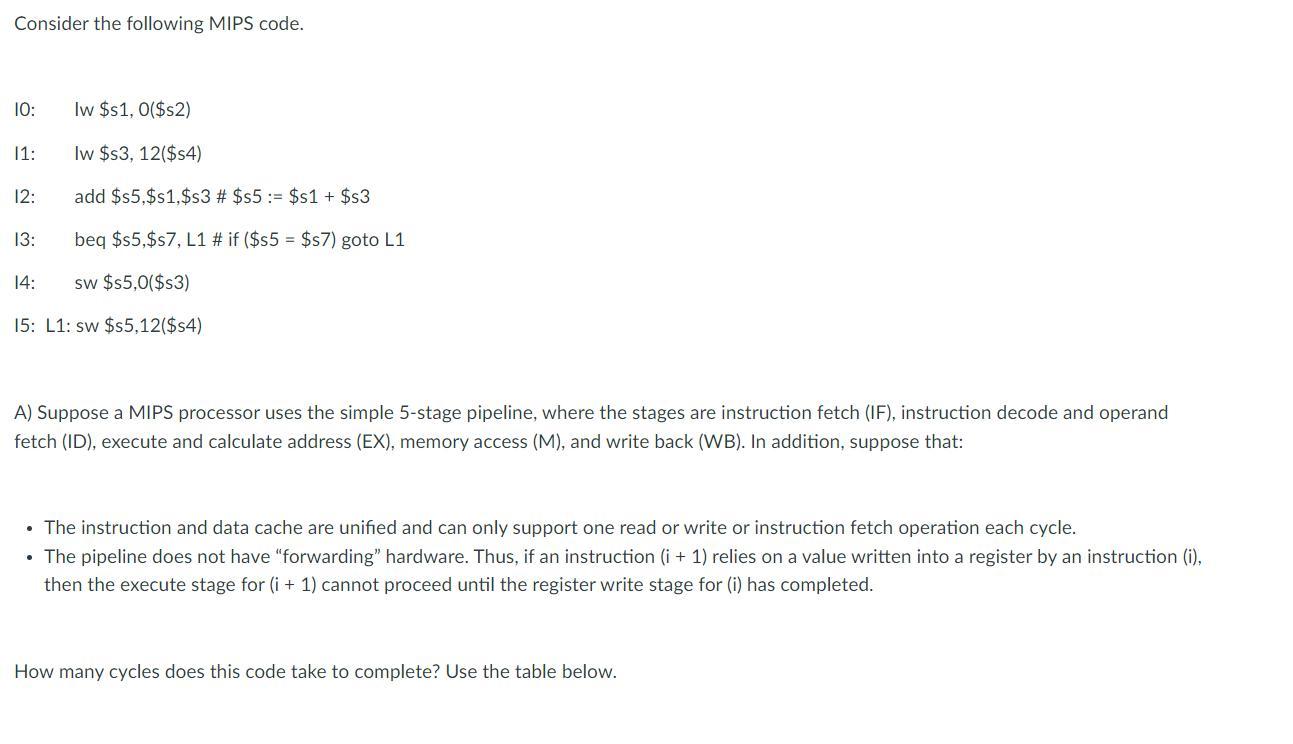
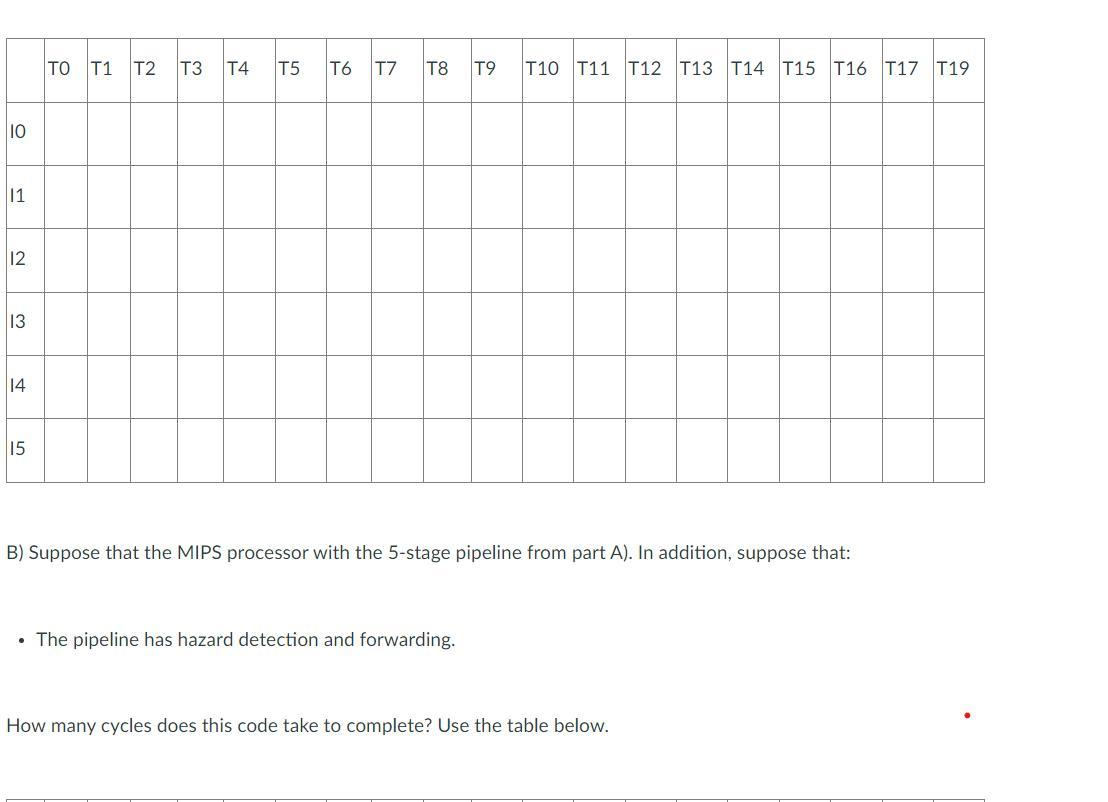
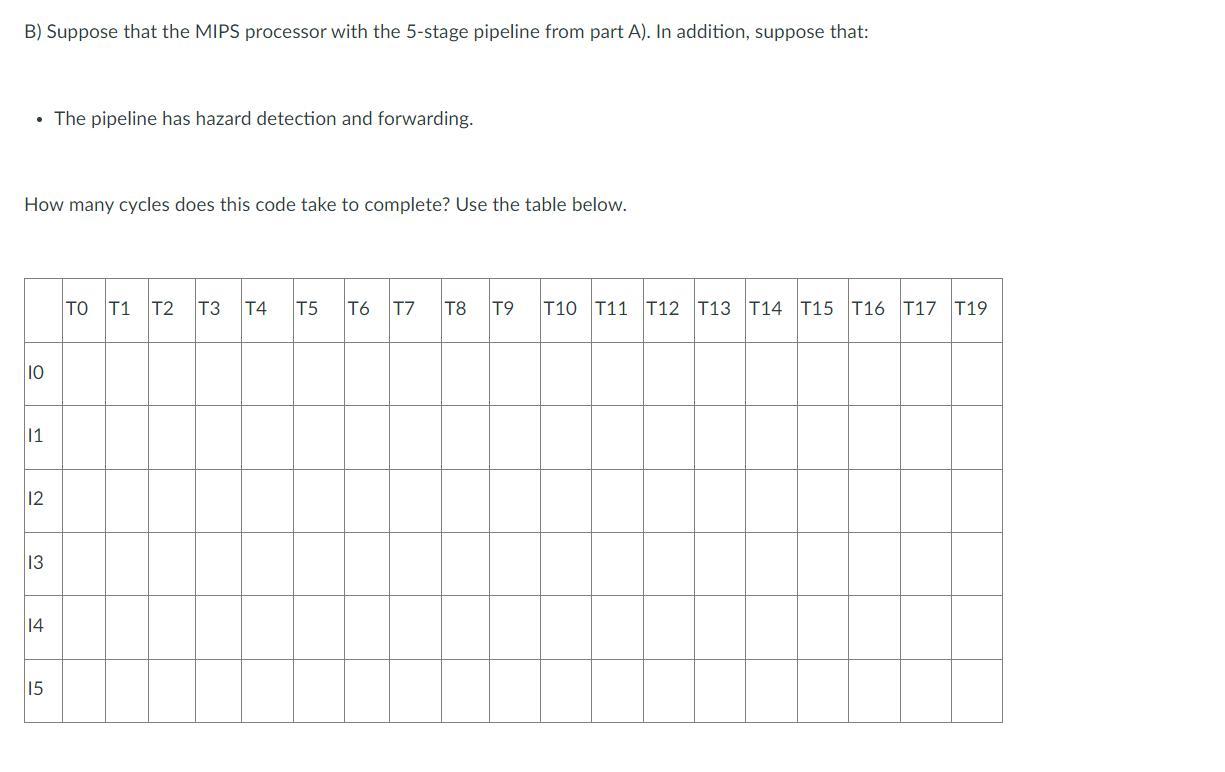
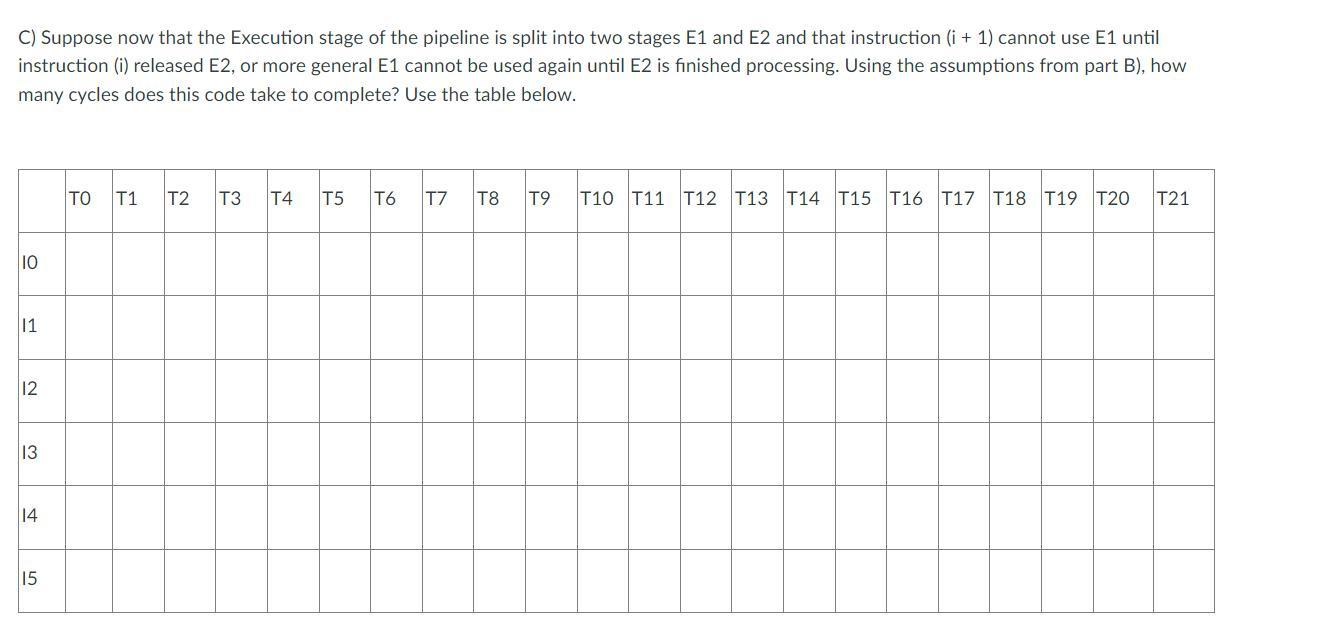
How many cycles does this code take to complete? Use the table below.
Answers
Answer:
10 cycles
Explanation:
To determine the number of cycles it takes for this MIPS code to complete using the simple 5-stage pipeline without forwarding, we can use the following table:
Instruction IF ID EX M WB
lw $s1, 0($s2) 1 1 1 1 1
lw $s3, 12($s4) 1 1 1 1 1
add $s5, $s1, $s3 1 1 1 1 1
beq $s5, $s7, L1 1 1 1 1 0
sw $s5, 0($s3) 1 1 1 1 1
L1: sw $s5, 12($s4) 1 1 1 1 1
Each instruction takes 5 stages to complete, except for the branch instruction (beq) in I3, which takes 4 stages because it does not write anything back to a register. However, since there is no forwarding hardware, the execute stage for I3 cannot proceed until the write back stage for I2 has completed.
Therefore, the total number of cycles it takes for this code to complete is:
1 + 1 + 1 + 5 + 1 + 1 = 10 cycles
Therefore, this code takes 10 cycles to complete using the simple 5-stage pipeline without forwarding.
There is a total of 20 cycles required
What is MIPS Code?MIPS CODE: The term MIPS is an acronym for Microprocessor without Interlocked Pipeline Stages. It is a reduced-instruction set architecture developed by an organization called MIPS Technologies.
The MIPS assembly language is a very useful language to learn because many embedded systems run on the MIPS processor.
Each instruction takes 5 stages to complete, except for the branch instruction (beq) in I3, which takes 4 stages because it does not write anything back to a register.
However, since there is no forwarding hardware, the execute stage for I3 cannot proceed until the write-back stage for I2 has completed.
Read more about codes here:
https://brainly.com/question/26134656
#SPJ1



Consider the following class. public class ClassicClass { private static int count = 0; private int num; public ClassicClass() { count++; num = count; } public String toString() { return count + " " + num; } } What is printed when the following code in the main method of another class is run? ClassicClass a = new ClassicClass(); ClassicClass b = new ClassicClass(); ClassicClass c = new ClassicClass(); System.out.println(a + ", " + b + ", " + c);
Answers
The the code in the main method is run, it will print
"3 1, 3 2, 3 3"
The static/class field count stores the number of instances of the class created. count is always incremented when the instance constructor is called.
The instance field num acts like an identifier/serial number for the instance created. When the constructor is called, the current count is stored in the num field of the instance.
Each instance's toString( ) method will output the total count (from count) and the serial of the instance (from num).
When the code runs in the main method, it creates three instances (making count==3), so that we have
a = {count: 3, num: 1}b = {count: 3, num: 2}c = {count: 3, num: 3}and implicitly calls toString( ) in the println method for each of the three instances to produce the following output
"3 1, 3 2, 3 3"
Learn more about programs here: https://brainly.com/question/22909010
Create a program that uses an array of Shape references to objects of each concrete class in the hierarchy (see program-2). The program should print a text description of the object to which each array element refers. Also, in the loop that processes all the shapes in the array, determine the size of each shape If it‟s a TwoDimensionalShape, display its area. If it‟s a ThreeDimensionalShape, display its area and volum
Answers

The program uses an array for shape reference to objects of each concrete class given. The program is in text description in java language.
What is a program array?Array programming in computer science refers to methods that allow operations to be applied to a whole set of values at once. This kind of solution is frequently used in scientific and engineering settings.
Shape.java
public abstract class Shape { private int sides;
public Shape() {
this.sides=0;
}
public Shape(int sides) { super(); this.sides = sides;
}
public int getSides() { return sides;
}
public void setSides (int sides) { this.sides = sides;
}
public abstract double calcArea();
Override
public String toString() {
return "This Shape has [sides=" + sides + "]";
Therefore, the program array is given above.
To learn more about program array, refer to the link:
https://brainly.com/question/13104121
#SPJ2
Does anyone know how to fix this? Everytime i make a new page it only types in the middle of the page. I want to type at the top

Answers
Answer:maybe start a new page or try hitting delete
Explanation:
Which octet of the subnet mask 255.255.255.0 will tell the router the corresponding host ID?
Answers
Answer: The last octet
Explanation: The last octet of the subnet mask will tell the router the corresponding host ID.
The last octet is the octet of the subnet mask 255.255.255.0 will tell the router the corresponding host ID.
What is octet in IP address?An octet is a decimal value between 0 and 255, and it is referred to as x in the IPv4 component of the address. The octets are separated by periods. The IPv4 portion of the address must contain three periods and four octets.
People may have also heard people refer to the four digits that make up an IP address as "octets." An octet is the correct term to describe the four different digits that make up an IP address.
In subnetting, the third octet is used to identify particular subnets of network 150.150.0.0. Each subnet number in the example in the image has a different value in the third byte, indicating that it is a distinct subnet number.
Thus, it is last octet.
For more details about octet in IP address, click here:
https://brainly.com/question/10115477
#SPJ2
2.) Using Constants and Variables to create a Program (10 points)
You are going to write out a program below that will help calculate the total amount of money made per
week, based on a 5 day work week and making $8 per hour.
You will need to create (2) Constant variables
You will need to create (3) variables
Answers
Using Constants and Variables to create a Program is given below.
How to create the program# Establish constant values
DAYS_PER_WEEK = 5
HOURLY_WAGE = 8
# Introduce changeable parameters
hours_worked = 0
daily_earnings = 0
total_earnings = 0
# Ask user regarding hours labored each day
for day in range(1, DAYS_PER_WEEK + 1):
hours_worked = int(input(f"How many hours did you work on day {day}? "))
daily_earnings = hours_worked * HOURLY_WAGE
total_earnings += daily_earnings
# Display aggregate income for the week
print(f"You made a total of ${total_earnings} this week.")
Learn more about program on
https://brainly.com/question/26642771
#SPJ1
Toney gets his phone bill in the mail the bill was supposed to be for 80 but the mail person spilled water on bill smearing the ink the bill now ask for 8 what part of the cia triad has been broken
Answers
Explanation:
\( \huge \star \mathbb \pink {Hiiiii} \)
Clicking and double-clicking are two of the five
Answers
Answer:
The correct answer is events
Which type of evidence should victims collect to help officials catch cyber bullies ?
-home addresses
-birthdays
-social media
-usernames user
-passwords
Answers
Answer:
Social media
Explanation:
Which of the following tasks can you perform using a word processor?
insert a bulleted list in a document
check a document for spelling errors
edit a video for inclusion in a document
create an outline of sections to be included in a document
set a password to restrict access to a document
Answers
The following task can you perform using a word processor is creating an outline of sections to be included in a document. The correct option is c.
What is a word processor?A word processor is a computer program or device that provides for input, editing, formatting, and output of text, often with additional features.
Simply put, the probability is the likelihood that something will occur. When we don't know how an event will turn out, we can discuss the likelihood or likelihood of several outcomes.
Statistics is the study of events that follow a probability distribution. In uniform probability distributions, the chances of each potential result occurring or not occurring are equal.
Therefore, the correct option is c. create an outline of sections to be included in a document.
To learn more about word processors, refer to the link:
https://brainly.com/question/14103516
#SPJ5
How can knowledge management systems help an organization increase profits and reduce costs?
Answers
Answer:
A powerful knowledge management system will allow you to organise product information. Not only this, but it should also help customers and employees access these details easily. ... Having good knowledge management and sharing practices can boost productivity and cut expenses in different areas.Jun 14, 2019
A company plans to deploy a non-interactive daemon app to their Azure tenant.
The application must write data to the company’s directory by using the Directory.ReadWrite.All permission. The application must not prompt users for consent.
You need to grant the access required by the application.
Which permission should you use?
Select only one answer.
admin-restricted
delegated
application
effective
Answers
Since the application must write data to the company’s directory by using the Directory.ReadWrite.All permission. The permission that you should use is option C: application
What is the permission about?In order for the non-interactive daemon app to write data to the company's directory without prompting users for consent, it must be granted "application" permissions.
This type of permission allows an application to access the directory on behalf of the signed-in user, without the user's interaction. "Directory.ReadWrite.All" is an example of an application permission that would allow the app to write data to the company's directory.
Therefore, It's important to note that application permissions must be consented to by an administrator and are not available for delegation.
Learn more about App permission from
https://brainly.com/question/30055076
#SPJ1
In a balanced budget, the amount is the amount
Answers
In a balanced budget, the Income amount is same as the expense amount.
What is a balanced budget?A balanced budget is one in which the revenues match the expenditures. As a result, neither a fiscal deficit nor a fiscal surplus exist. In general, it is a budget that does not have a budget deficit but may have a budget surplus.
Planning a balanced budget assists governments in avoiding excessive spending and focuses cash on regions and services that are most in need.
Hence the above statement is correct.
Learn more about Budget:
https://brainly.com/question/15683430
#SPJ1
What would be the result of the following calculation in a spreadsheet?
=5+10/5-3*3-1
a. -1
b. -3
c. 1
d. 3
e. 0
answer: B. -3
Answers
Answer:
answer a -1
b-3 hi hello who are you
The process of using the new
information system and doing away
with the old system is known as
system ___.
Answers
Answer:
The process of using the new
information system and doing away
with the old system is known as
system development
Differences between the function and structure of computer architecture
Answers
Answer:
The primary difference between a computer structure and a computer function is that the computer structure defines the overall look of the system while the function is used to define how the computer system works in a practical environment.
The computer structure primarily deals with the hardware components, while the computer function deal with computer software.
A computer structure is a mechanical component such as a hard disk. A computer function is an action such as processing data.
Explanation:
if it helped u please mark me a brainliest :))
what is the name of the program or service that lets you view e -mail messeges?
Answers
The program or service that allows you to view email messages is called an email client.
What is the name of the program?An email client is a software program or service that enables users to access, manage and view their email messages. It provides user-friendly interface for reading, composing and organizing emails.
Popular examples of email clients include Micro/soft Outlook, Gm/ail, Mo/zilla Thunderbird and Ap/ple Mail. These clients allow users to connect to their email accounts, retrieve messages from email servers and display them in an organized manner for easy viewing and interaction.
Read more about email client
brainly.com/question/24688558
#SPJ1
survey and describe the system
Answers
Survey systems help create, distribute, and analyze surveys by providing a framework for designing questionnaires, managing respondents, and analyzing data.
What is survey?A survey system lets users create surveys with different question types and response options. The system offers multiple ways to distribute surveys, including sharing a web link, email invites, website embedding, and social media.
Data is collected from respondents and stored accurately and securely, with error checking and validation in place. After survey completion, analyze data with summary stats, visualizations, filters, and cross-tabulations for identifying patterns. Survey systems have reporting features to generate detailed reports based on its data, including statistics, graphs, etc.
Learn more about survey from
https://brainly.com/question/14610641
#SPJ1
improved pet app user
Answers
By using Internet new sources of input. Determine the information that the app gets from each source of input.
One of the most critical components found currently in IT existence is the user interface. Approximately 90 % of people are mobile and electronic equipment dependent.
Thus, software production was the idea that's happening. Thus, a better customer interface is required to boost output in application development. They have to think of it and create an app with consumers or the performance.
Learn more about internet on:
https://brainly.com/question/13308791
#SPJ1
The complete question will be
Help meeeee - Improved Pet App
Try out the improved version of the pet app that gives the user information about pet stores close by, which uses new sources of input. Determine the information that the app gets from each source of input.
User
Phone Sensors
Internet
Describe at least two ways social media has impacted cybersecurity.
Answers
Answer:
Its Providing Too Much Personal Information since you will be using social media to promote your own small business, you need to take extra precautions. For starters, don’t leave a trail of breadcrumbs for social media hackers. Whether you are representing yourself or your company, avoid sharing stuff like your date of birth, places where you have attended school, as well as names and pictures of your family members.
Disgruntled Employees
While it’s fairly normal for your employees to vent about working for your company, in doing so, they may inadvertently reveal more than they should. It’s a lot more common than you think, since 98% of all employees are using at least one social media platform, and as much as 50% of those are talking about their respective companies. Whether they are sharing sensitive info or posting pictures from their workplace, they may end up sharing something that might hurt your business.
Explanation:
Answer:Its Providing Too Much Personal Information since you will be using social media to promote your own small business, you need to take extra precautions. For starters, don’t leave a trail of breadcrumbs for social media hackers. Whether you are representing yourself or your company, avoid sharing stuff like your date of birth, places where you have attended school, as well as names and pictures of your family members.
Disgruntled Employees
While it’s fairly normal for your employees to vent about working for your company, in doing so, they may inadvertently reveal more than they should. It’s a lot more common than you think, since 98% of all employees are using at least one social media platform, and as much as 50% of those are talking about their respective companies. Whether they are sharing sensitive info or posting pictures from their workplace, they may end up sharing something that might hurt your business
Explanation:
Lira has typed up a document and now she wants to adjust the irregular right edge of the text so that it is even. How can she accomplish this?
by changing the margins
by adjusting the indent markers
by changing the spacing between words
by using the Justify and Automatic Hyphenation options
ANSWER IS D. by using the Justify and Automatic Hyphenation options
Answers
Answer:
d. by using the Justify and Automatic Hyphenation options
Explanation:
In which sections of your organizer should the outline be located?
Answers
The outline of a research proposal should be located in the Introduction section of your organizer.
Why should it be located here ?The outline of a research proposal should be located in the Introduction section of your organizer. The outline should provide a brief overview of the research problem, the research questions, the approach, the timeline, the budget, and the expected outcomes. The outline should be clear and concise, and it should be easy for the reader to follow.
The outline should be updated as the research proposal evolves. As you conduct more research, you may need to add or remove sections from the outline. You may also need to revise the outline to reflect changes in the project's scope, timeline, or budget.
Find out more on outline at https://brainly.com/question/4194581
#SPJ1
I want to write a C++ program to read the diameter of a circle. The program should find and display the area and circumference of the circle. Define a constant of type double PI = 3.14159
I need code for this program
Answers
Answer:
#include <iostream>
const double PI = 3.14159;
int main() {
double diameter;
std::cout << "Please enter the diameter of the circle:" << std::endl;
std::cin >> diameter;
double radius = diameter / 2;
double area = radius * radius * PI;
double circumference = 2 * radius * PI; // or diameter * PI;
std::cout << "Area: " << area << std::endl;
std::cout << "Circumference: " << circumference << std::endl;
}
Explanation:
The first line imports the read/write library. The rest should be self-explanatory.
std::cin is the input stream - we use it to get the diameter
std::cout is the output stream - we write the answers (and commentary) there.
std::endl is the special "character" informing the output stream that we want it to put a newline character (and actually print to the output - it might have been holding off on it).
the // in the circumference computation signifies a comment - the program simply ignores this. I've added it to tell the reader that the circumference could have been computed using the diameter,
how can you stretch or skew an object in paint
Answers
Answer:
Press Ctrl + Shift + Z (Rotate/Zoom). Rotate the roller-ball control about a bit. The outer ring rotates the layer.
Explanation:
The UDP protocol provides reliable, connectionless service.
a) true
b) false
Answers
write a program to accept a name and roll number of 5 student using structure in C
Answers
Answer:
This C program is to store and display the information of a student using structure i.e. to store and display the roll number,name,age and fees of a student using structure.
Basically one should know how to write the syntax of a structure and the rest is just implementation of the programs done so far.
If you yet need a dry run of the program or any other query, then kindly leave a comment in the comment box or mail me, I would be more than happy to help you.
#include <stdio.h>
#include <string.h>
struct student {
char name[50];
int roll;
};
int main() {
struct student student1;
strcpy(student1.name, "Chris Hansen");
student1.roll = 38;
printf("Name: %s\nRoll number: %d\n", student1.name, student1.roll);
struct student student2;
strcpy(student2.name, "Edip Yuksel");
student2.roll = 19;
printf("Name: %s\nRoll number: %d\n", student2.name, student2.roll);
struct student student3;
strcpy(student3.name, "Skeeter Jean");
student3.roll = 57;
printf("Name: %s\nRoll number: %d\n", student3.name, student3.roll);
struct student student4;
strcpy(student4.name, "Sinbad Badr");
student4.roll = 114;
printf("Name: %s\nRoll number: %d\n", student4.name, student4.roll);
struct student student5;
strcpy(student5.name, "Titus Alexius");
student5.roll = 76;
printf("Name: %s\nRoll number: %d\n", student5.name, student5.roll);
return 0;
}
DISPLAYName: Chris Hansen
Roll number: 38
Name: Edip Yuksel
Roll number: 19
Name: Skeeter Jean
Roll number: 57
Name: Sinbad Badr
Roll number: 114
Name: Titus Alexius
Roll number: 76
EXPLANATIONUse string.h to access string functions for names.
Create a struct outside of the main on student name and roll number.
strcpy works for strings.
Create for 1 student and copy and paste for the others.
Display the name and roll number for each student.
New forensics certifications are offered constantly. Research certifications online and find one not discussed in this chapter. Write a short paper stating what organization offers the certification, who endorses the certification, how long the organization has been in business, and the usefulness of the certification or its content. Can you find this certification being requested in job boards?
Answers
Answer:
Computer forensics is gathering information or evidence from a computer system in order to use it in the court of law. The evidence gotten should be legal and authentic.
These organization gives certifications for computer forensics
1. Perry4law: they provide training to students, law enforcement officers. There services includes forensics training, research and consultancy.
2. Dallas forensics also offers similar services
3. The New York forensics and electronic discovery also teach how to recover files when deleted, how to get information from drives and how to discover hidden information.
Question 10 of 10
What information system would be most useful in determining what direction
to go in the next two years?
A. Decision support system
B. Transaction processing system
C. Executive information system
D. Management information system
SUBMIT
Answers
Answer: C. Executive information system
Explanation: The information system that would be most useful in determining what direction to go in the next two years is an Executive Information System (EIS). An EIS is designed to provide senior management with the information they need to make strategic decisions.
An Executive Information System (EIS) would be the most useful information system in determining what direction to go in the next two years. So, Option C is true.
Given that,
Most useful information about determining what direction to go in the next two years.
Since Executive Information System is specifically designed to provide senior executives with the necessary information and insights to support strategic decision-making.
It consolidates data from various sources, both internal and external, and presents it in a user-friendly format, such as dashboards or reports.
This enables executives to analyze trends, identify opportunities, and make informed decisions about the future direction of the organization.
EIS typically focuses on high-level, strategic information and is tailored to meet the specific needs of top-level executives.
So, the correct option is,
C. Executive information system
To learn more about Executive information systems visit:
https://brainly.com/question/16665679
#SPJ6
Which sentence has correct parallel structure?
О А. The software allows users to create new documents, copying files from other sources, and saving new changes.
Users need a laptop, internet connection, and need an appropriate document editor.
SO B.
O C.
To install the application, connect the flash drive, run the setup, and restart the system.
OD.
The application bundle contains a DVD, the flash drive, and instruction manual.
Answers
The sentence that has parallel structure is "To install the application, connect the flash drive, run the setup, and restart the system." (opiton C)
What is parallel structure?The repeating of a certain grammatical form inside a phrase is known as parallel structure (also known as parallelism). A parallel construction is created by making each comparable object or notion in your phrase follow the same grammatical pattern.
Consider this example: "I forgave you when you lost my cat, when you left me at the airport, and when you threw out my favorite stuffed animal." The parallel structure is the recurrent usage of I forgave you when you.
Hence, option C is correct.
Learn more about parallel structure:
https://brainly.com/question/8055410
#SPJ1
Jason works as a financial investment advisor. He collects financial data from clients, processes the data online to calculate the risks associated with future investment decisions, and offers his clients real-time information immediately. Which type of data processing is Jason following in the transaction processing system?
A.
online decision support system
B.
online transaction processing
C.
online office support processing
D.
online batch processing
E.
online executive processing
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
The correct answer to this question is an online decision support system. Because the decision support systems process the data, evaluate and predict the decision, and helps the decision-makers, and offer real-time information immediately in making the decision in an organization. So the correct answer to this question is the decision supports system.
Why other options are not correct
Because the transaction processing system can only process the transaction and have not the capability to make the decision for the future. Office support processing system support office work, while the batch processing system process the task into the batch without user involvement. however, online executive processing does not make decisions and offer timely information to decision-makers in an organization.
Answer: the answer is A.
Explanation: He has to listen to what the people tell him and think about the information he has and make a choice on what to reply with.