The term ________ means that the cloud computing resources can be increased or decreased dynamically in a short span of time and that organizations pay for just the resources that they use.
Answers
The term 'elasticity' means that the cloud computing resources can be increased or decreased dynamically in a short span of time, and that organizations pay for just the resources they use.
Elasticity is the ability of an infrastructure or software application to scale up or down automatically in response to changing demand and traffic.
This ensures that users have the resources they need to carry out their work efficiently without paying for resources they do not require. This ability is considered a hallmark of cloud computing, as it allows organizations to take advantage of computing resources without having to make significant capital investments upfront.
Learn more about the computing resources at:
https://brainly.com/question/15094731
#SPJ11
Related Questions
Please give answers between 500 words.
What have been the major issues and benefits in
Electronic Data Interchanges (EDI) and Web-Based/Internet
Tools?
Answers
The major issues and benefits of electronic data interchange (EDI) and web-based/Internet tools, such as compatibility and standardization, privacy, cost, dependence on internet connectivity, etc.,
One of the challenges of EDI is that it is ensuring compatibility between different systems and also establishing standardized formats for data exchange. It requires agreement and coordination among trading partners in order to ensure the seamless communication, while there are many benefits that include EDI and web-based tools that enable faster and more efficient exchange of information, eliminating manual processes, paperwork, and potential errors. Real-time data exchange improves operational efficiency and enables faster decision-making. Apart from this, there are many other benefits to these.
Learn more about EDI here
https://brainly.com/question/29755779
#SPJ4
Darian is preparing for a presentation about the poor condition of the locker rooms at school. Match each of the key components of a presentation to a detail of Darian's presentation. audience to persuade the school board to improve locker-room condition purpose Darian's school board locker-room condition topic a electronic slideshow method can anyone
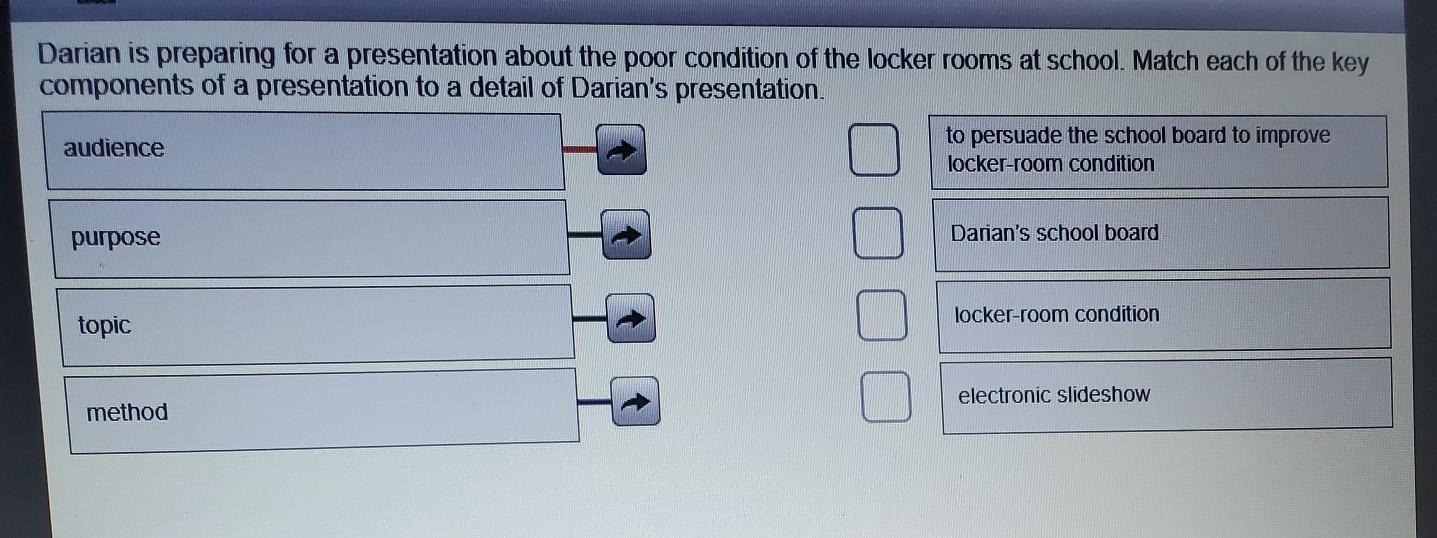
Answers
Answer:
Purpose - To paurswade the board to change the conditions of the locker room
Topic - Locker room condition
Method - Electronic Slideshow
Audience - School Board
para saan po yung points dito?
Answers
Answer:
Hindi kudin Alam eh hahahha
Answer:
Hey, there this is the answer
Users need to use points to post a question. The more points they use, the more quickly their question will be answered. Users gain a basic number of points each time they log into the platform.
unauthorized use of computer system with a view to seeing or changing data is refered to as
Answers
Answer:
I believe hacking I don't know for sure you may want to see what someone else says
Explanation:
Jason is writing a report about a potential security vulnerability in a software product and wishes to use standardized product names to ensure that other security analysts understand the report. Which SCAP component can Jason turn to for assistance?
A. CVSS
B. CVE
C. CPE
D. OVAL
Answers
C. CPE (Common Platform Enumeration) is the SCAP (Security Content Automation Protocol) component that Jason can turn to for assistance in using standardized product names in his report.
CPE provides a structured naming scheme for hardware, software, and other IT products to ensure consistency across different tools and systems. CPE includes a dictionary of product names, versions, and other attributes, allowing security analysts to quickly identify the software products in question and the specific vulnerabilities they may have. CPE is the SCAP (Security Content Automation Protocol) component By using CPE, Jason can provide a clear and consistent identification of the software products involved in the security vulnerability, facilitating communication and collaboration among security analysts and IT professionals.
learn more about SCAP here:
https://brainly.com/question/15776326
#SPJ11
T/F: query by example uses a graphical user interface that assists users with retrieving data.
Answers
Answer: True
Explanation:
Query by Example (QBE) is a technique that uses a graphical user interface (GUI) to assist users in retrieving data from a database. Instead of writing complex queries in a programming language like SQL, users can interact with the GUI and specify their search criteria by providing examples or patterns of the desired data.
With QBE, users typically utilize forms or grids where they can input values, select options, or define conditions using logical operators. The GUI then translates these user inputs into underlying query operations, simplifying the process of constructing queries.
By providing a visual and intuitive interface, QBE allows users with varying levels of technical expertise to interact with databases and retrieve data without the need for extensive knowledge of query languages or complex syntax.
Learn more about graphical user here:
https://brainly.com/question/16956142
#SPJ11
rite the definition of a classtelephone. the class has no constructors and one static method printnumber. the method accepts a string argument and prints it on the screen. the method returns nothing.
Answers
1. Define the class "Telephone".
2. Inside the class, declare the static method "printNumber" with a string parameter.
3. Implement the method to print the string .
4. Any constructor is not needed to be defined.
Here's the C++ code:
```
#include <iostream>
using namespace std;
class Telephone {
public:
static void printNumber(const ::string& number);
};
void Telephone::printNumber(const string& number) {
cout << number << endl;
}
int main( ){
Telephone person1;
string s="0000011110";
person1.printNumber(s);
return 0;
}
```
In 'main( )' function person1 object is created and printNumber method is called with string s pass arguments. Output shown on sreen is '000011110'.
Read more about Static methods : https://brainly.com/question/29607459
#SPJ11
a fraudulent financial deal has just taken place in the company where you are working as a network administrator. the data of the company will be collected in such a way that it can be presented in a court of law for the purpose of prosecution. some of the forensic data available for analysis may be damaged or destroyed if improperly handled. you have been assigned the duty to safeguard sensitive information, logged data, and other legal evidence until the first responder or incident response team can take over the collection of evidence. to prevent contamination of evidence, you have made sure that each device involved is isolated-that is, the device is disconnected from the network and secured to ensure that no one else has contact with it until the response team arrives. what is the next step that you will take in the event of such an illegal activity? group of answer choices
Answers
Document The Scene.
Creating a defensible audit trail is one of the highest priorities in the forensics process. An audit trail is a system of documentation that makes it possible for a third party to inspect evidence later and understand the flow of events.
What is fraudulent financial?Financial fraud happens when someone deprives you of your money, capital, or otherwise harms your financial health through deceptive, misleading, or other illegal practices. This can be done through a variety of methods such as identity theft or investment fraud. What Is Financial Statement Fraud? Financial statement fraud is the deliberate misrepresentation of a company's financial statements, whether through omission or exaggeration, to create a more positive impression of the company's financial position, performance and cash flow. Criminals are constantly creating new types of fraud. But some common standards include embezzlement, insurance fraud, ransomware, identity theft, financial statement fraud, bribery, mortgage fraud, tax evasion, and ponzi schemes.
To know more about fraudulent financial visit:
https://brainly.com/question/26963566
#SPJ4
look at the list of common operating system tasks in section 6.4.1. which of these tasks have you performed in the past several weeks, and how did you perform them? in the course of a typical week, what kinds of computer networks do you use? how many different kinds can you now recognize? how aware have you been of differences in these networks, or do they all create a similar virtual environment? imagine the next new innovation in network technology—what would it look like and what could it do?
Answers
These networks can create distinct virtual environments and have various technologies. The next innovation in network technology could be the widespread adoption of 5G networks, enabling faster speeds and revolutionizing various industries.
In the past several weeks, I have performed several common operating system tasks. These tasks include:
File Management: I have created, edited, and organized files on my computer. For example, I created a document for my school project, edited it multiple times, and saved it in a specific folder.
Software Installation: I have installed new software on my computer. For instance, I downloaded and installed a video editing software to edit a video project.
System Updates: I have regularly updated my operating system to ensure it has the latest security patches and features. I usually do this by going to the system settings and checking for updates.
Troubleshooting: I have encountered issues with my computer and troubleshooted them. For example, I had a problem with my internet connection, so I restarted my router and checked my network settings.
During a typical week, I use various computer networks. Some examples include:
Home Network: I connect to my home network to access the internet and share files with other devices in my house.
School/University Network: I connect to my school or university network to access online resources, submit assignments, and communicate with my classmates and professors.
Public Wi-Fi Networks: When I am outside, I often connect to public Wi-Fi networks in cafes, libraries, or other public places to access the internet.
I can recognize different types of networks, such as LAN (Local Area Network) and WLAN (Wireless Local Area Network). These networks have different characteristics and technologies.
While some networks may have similarities, they can also create different virtual environments. For example, a home network may have restrictions and security settings set by the owner, while a public network may have limited access to certain websites or services.
The next innovation in network technology could be the widespread adoption of 5G networks. This technology would provide faster internet speeds, lower latency, and enable new applications such as remote surgeries, self-driving cars, and smart cities. Additionally, it could revolutionize the Internet of Things (IoT) by connecting a massive number of devices seamlessly.
In conclusion, in the past several weeks, I have performed common operating system tasks like file management, software installation, system updates, and troubleshooting. I use different computer networks, including home, school/university, and public Wi-Fi networks.
These networks can create distinct virtual environments and have various technologies. The next innovation in network technology could be the widespread adoption of 5G networks, enabling faster speeds and revolutionizing various industries.
To know more about Wi-Fi visit:
https://brainly.com/question/32802512
#SPJ11
(a) Willow has created a hangman program that uses a file to store the words the program can select from. A sample of this data is shown in Fig. 3.
Fig. 3
crime, bait, fright, victory, nymph, loose.
Show the stages of a bubble sort when applied to data shown in Fig. 3.
(b) A second sample of data is shown in Fig. 4.
Fig. 4.
amber, house, kick, moose, orange, range, tent, wind, zebra.
Show the stages of a binary search to find the word "zebra" when applied to the data shown in Fig. 4.
Answers
(a) A bubble sort applied to the data in Fig. 3 produces these stages:
Loose, crime, bait, fright, victory, nymph
Crime, loose, bait, fright, victory, nymph
Bait, crime, loose, fright, victory, nymph
Fright, bait, crime, loose, victory, nymph
Victory, fright, bait, crime, loose, nymph
Nymph, victory, fright, bait, crime, loose.
(b) When a binary search is conducted in order to find the word "zebra" in the data in Fig. 4, the following yield occurs:
The search begins by looking at the list's middle item, which is "orange".
Hope to explain the bubble sortSince "zebra" comes after "orange" alphabetically, the search continues amongst the second half of the list.
The centermost item on this narrowed down list proves to be "tent", from there, it is deduced that "zebra" must go after "tent" alphanumerically.
Likewise, the process is repeated for the reminder of the sequence.
Moving forward, the search encounters "wind" in its midst, again concluding that zebra has to appear subsequently.
Finally, when observing the midpoint of the remainder, "zebra" is pinpointed as the desired result.
Learn more about bubble sort on
https://brainly.com/question/30395481
#SPJ1
A computer program that copies itself into other software and can spread to other computer systems is called?
Answers
Answer:
Computer Virus
Definition:
A computer program that copies itself into other software and can spread to other computer systems.
ALSO PLZZZ HELP :P Suppose you are purchasing a game at a local retail store that comes on DVD. In order to install it on your laptop, what must the laptop have?
A. a keyboard with a separate keypad for the arrow keys
B. an optical drive
C. an internet connection
D. an external monitor
Answers
Hope this helps have a great night
3. A file of unknown length needs to be read. The following algorithm is given: students File.open("students.txt") while (studentsFile.readLine() endwhilE Complete the condition in the WHILE loop. print JUTT [1] please help explanation + answer greatly appreciated
Answers
To read a file named "students.txt" of unknown length, use the following code snippet in Ruby:
The Programstudents_file = File.open("students.txt")
students_file.each_line do |line|
puts "JUTT [1]"
# Your code here to process each line
end
students_file.close
This code opens the file, iterates over each line, prints "JUTT [1]" for each line, and allows you to process the line within the loop. Finally, the file is closed.
Read more about programs here:
https://brainly.com/question/23275071
#SPJ1
Consider the various web frameworks that you learned about in this unit. Which one do you think you would most like to work with? Why?
Answers
Looking at the various web frameworks that I have learnt, the one that i think I would most like to work with is React (Frontend).
What frameworks should you learn in web development?Particularly Spring Boot, Node. js, React. js, and Angular are in high demand. Learning these frameworks will increase your opportunity for success and increase your likelihood of landing a job.
Note that the most popular JavaScript library for front-end app development is React. This well-equipped framework enables developers to make entirely responsive web apps while also running in the browser for website front-end functionality. Additionally, React offers customized HTML code that may be used in other projects.
Therefore, React, which was created by Face book, is seen as an open-source JavaScript library that is used for frontend development. You may create web apps with high-quality user interfaces using its component-based library.
Learn more about web framework from
https://brainly.com/question/13263206
#SPJ1
he attribute hierarchy provides a top-down data organization that is used for two main purposes: and drill-down/roll-up data analysis. question 38 options: a) decomposition b) normalization c) aggregation d) de-normalization
Answers
The attribute hierarchy provides a top-down data organization that is used for two main purposes: decomposition and drill-down/roll-up data analysis.
The attribute hierarchy is a hierarchical arrangement of data attributes or dimensions in a database or data model. It enables data to be organized in a top-down manner, starting from higher-level categories or aggregated levels down to more specific or detailed levels. This hierarchy is utilized for two main purposes: 1) Decomposition: Attribute hierarchy allows breaking down complex data into manageable and meaningful subsets.
Learn more about attribute hierarchy here:
https://brainly.com/question/32288838
#SPJ11
the gulf stream question 39 options: moves equatorward, warming the california coast. moves southward and moderates temperatures in eastern south america. moves northward in the western atlantic, moderating temperatures in iceland. creates a warming effect on japan and the aleutians.
Answers
By dispersing heat energy, the direction, speed, and temperature of the water masses swept along by ocean currents are significant factors in climatology.
What are the Gulf Stream's location and flow characteristics?
The Gulf Stream is a warm ocean stream that travels from the Gulf of Mexico to the British Isles via the northeastern coast of the United States. The British Isles' climate pattern is significantly impacted by the Gulf Stream.
What is the path of the Gulf Stream?
In the western North Atlantic Ocean, there is a strong, warm ocean stream called the Gulf Stream. It flows northeast over the Atlantic as it travels north along Florida's coast before turning east off of North Carolina.
To know more about gulf stream visit:
https://brainly.com/question/12662817
#SPJ4
what is Information communication technology?
Answers
Information communication is the use of devices to communicate with others such as family and friends.
In Python, if var1 = “Happy” and var2= “Birthday” and var3 = (var1+var2) *2, then var3 stores the string
A)“Happy BirthdayHappyBirthday”
B)“HappyHappyBirthday”
C)“HappyBirthdayHappyBirthdayHappyBirthday”
D)“HappyBirthdayBirthday”
Answers
Answer:
A
Explanation:
var3 is happy + birthday, ×2
l.e happy birthday happy birthday
Answer:
Your answer is A
How was the creation of the world wide web browser a stepping stone for future scientific breakthroughs?
Answers
Answer:
Following are the point that described the web browser for the stepping stone as a future scientific breakthroughs.
Explanation:
Tim Berners Lee was the founder of world wide web .The Tim Berners Lee is software engineer at CERN they had seen the troubling of exchanging the data .In that time there are various data in various computer .The Tim Berners Lee felt he had found the way for resolving this problem and develop a thing so that we can exchange the data in any where .In that time already lots of computer are already linked each other with the high speed of the internet so tim develop a new technology called hypertext .In the March 1989, in a paper titled known as "Information Management" Tim is developed but this proposal is rejected .In the 1990 Tim is developed the three technology HTML ,URI and HTTP with the help of this the world wide web is developed and we can share the information anywhere in the world .The sharing of information in a easy way gives the future bright the person in anywhere in the world will access the data or the information also We cam communicate anywhere in the world by using email .What feature does RIPng support that is not supported by RIP?a. IPv6b. gigabit Ethernetc. 32-bit addressesd. supernetting
Answers
RIPng supports IPv6, which is not supported by RIP.
What feature does RIPng support?The feature supported by RIPng (Routing Information Protocol next-generation) that is not supported by RIP (Routing Information Protocol) is IPv6. RIP is an older routing protocol primarily designed for IPv4 networks, whereas RIPng is an extension of RIP specifically developed to support IPv6 networks.
RIPng enables the routing and exchange of IPv6 routing information among routers, facilitating the deployment of IPv6 networks. It allows routers to advertise their IPv6 network prefixes and exchange routing updates. By supporting IPv6, RIPng addresses the increasing need for routing protocols compatible with the next-generation IP addressing scheme, providing connectivity and routing capabilities for IPv6 networks.
Learn more about RIPng
brainly.com/question/32104481
#SPJ11
Python program which squares all the number in list number = [2,3,4,5,6,7,8,9] and store it in another list name square. Please write a program :|
Answers
Answer:
l = [2,3,4,5,6,7,8,9]
def solve(l):
for i in l:
print(i**2)
solve(l)
Explanation:
loops through each element of the list and squares it.
How can I make my image fit the page
Profile picture at max can be 3000 x 3000 pixels and at minimum 65 x 65 pixels
Answers
which of the following bim software is used for building performance analysis in bim? select one: a. projectwise b. areo c. sefaira d. trimble connect
Answers
The BIM software that is specifically used for building performance analysis is Sefaira.
Sefaira is a cloud-based software that offers real-time analysis of building performance during the design process. It provides architects and engineers with tools to analyze different aspects of building performance such as energy usage, daylighting, and thermal comfort. With Sefaira, designers can make informed decisions and optimize building performance before construction, resulting in energy-efficient and sustainable buildings. On the other hand, ProjectWise is a collaboration software that helps manage project information and workflows, Aero is a 3D design and visualization software, while Trimble Connect is a project collaboration software. Although these software solutions can be used in BIM, they are not specifically designed for building performance analysis like Sefaira. In summary, Sefaira is the ideal BIM software for building performance analysis, providing designers with real-time feedback on building performance during the design process, helping to optimize building efficiency and sustainability.
Learn more about software :
https://brainly.com/question/985406
#SPJ11
question 7 how does cloud computing help iot devices? select two. 1 point draw insights from data collected from the iot devices and users provide the resources to store and process the data produced by iot devices and users provide a fixed physical location for the data collected from iot devices minimize latency in reporting and responding to data collected through iot sensors from around the world
Answers
Cloud Computing helps IOT in two ways:
(Option B) Provide the resources to store and process the data produced by iot devices and users.
(Option D) minimize latency in reporting and responding to data collected through iot sensors from around the world.
What is Cloud Computing?The availability of computer system services, in particular data storage or we can say cloud storage and processing power, without direct active supervision by the user, is known as cloud computing. Functions in large clouds are frequently dispersed over several sites, each of them is simply a data center. Cloud computing often uses a "pay as you go" model, that can help reduce capital expenses but may also result in unanticipated running expenses for users. Cloud computing depends on resource sharing to accomplish coherence.IaaS--Infrastructure as a Service, PaaS--Platform as a Service, Serverless, and Software, among others, represent the majority of cloud computing services.
to know more about Cloud Computing, visit
https://brainly.com/question/19057393
#SPJ4
Two ways does cloud computing help IOT: Provide the resources necessary to store and process the data generated by iot devices and users
Reduce reporting and response time to global data collected by iot sensors as much as possible.
How does cloud computing work?Cloud computing refers to the provision of computer system services—specifically cloud storage and processing power—without the user's direct active supervision. In big clouds, functions are often spread out over multiple locations, each of which is just a data center. The "pay as you go" model of cloud computing can help cut down on capital expenditures, but it can also cause users to incur unexpected operating costs. Coherence in cloud computing is achieved through the sharing of resources. The majority of cloud computing services are IaaS (Infrastructure as a Service), PaaS (Platform as a Service), serverless, and software, among others.
Learn more about the Cloud Computing :
brainly.com/question/25522987
#SPJ4
You are working as a project manager. One of the web developers regularly creates dynamic pages with a half dozen parameters. Another developer regularly complains that this will harm the project’s search rankings. How would you handle this dispute?
Answers
From the planning stage up to the deployment of such initiatives live online, web project managers oversee their creation.They oversee teams that build websites, work with stakeholders to determine the scope of web-based projects, and produce project status report.
What techniques are used to raise search rankings?
If you follow these suggestions, your website will become more search engine optimized and will rank better in search engine results (SEO).Publish Knowledgeable, Useful Content.Update Your Content Frequently.facts about facts.possess a link-worthy website.Use alt tags.Workplace Conflict Resolution Techniques.Talk about it with the other person.Pay more attention to events and behavior than to individuals.Take note of everything.Determine the points of agreement and disagreement.Prioritize the problem areas first.Make a plan to resolve each issue.Put your plan into action and profit from your victory.Project managers are in charge of overseeing the planning, execution, monitoring, control, and closure of projects.They are accountable for the project's overall scope, team and resources, budget, and success or failure at the end of the process.Due to the agility of the Agile methodology, projects are broken into cycles or sprints.This enables development leads to design challenging launches by dividing various project life cycle stages while taking on a significant quantity of additional labor.We can use CSS to change the page's background color each time a user clicks a button.Using JavaScript, we can ask the user for their name, and the website will then dynamically display it.A dynamic list page: This page functions as a menu from which users can access the product pages and presents a list of all your products.It appears as "Collection Name" in your website's Pages section.To learn more about search rankings. refer
https://brainly.com/question/14024902
#SPJ1
Sending the same messages to a large number of users is called
Answers
Answer:
Can you give me the options
The Principal of a school requires to store the information about the students of his school.
Which application software should he use to create a database? (Do it as homework)
Answers
Answer:
Microsoft office access would be a good application to create a database......it has various advantages such as storage and retrival of data, etc.
Explanation:
By Ms Excel the school principle write everything and to create students profile principle sir or headmaster use Microsoft so that students id cards will be created.
Which one of the following Python statements can be used to create the dataframe x ? Dataframe x :
A
a
NaN
b
NaN
c
NaN
alpha vantage pd. DataFrame(index =[ ' A '] , columns =[ ' a ', ' b ', ' c ' ] ) pd.DataFrame(index =[
′
a
′
,
′
', ' 'c' ], columns='A') pd.DataFrame(index =[ ' a ', ' b ', ' c ' ], columns =[
′
A
′
])
Answers
The correct statement to create the dataframe x is:
```python
x = pd.DataFrame(index=['A'], columns=['a', 'b', 'c'])
The above code uses the pandas library in Python to create a dataframe named x. The `pd.DataFrame()` function is used to create the dataframe, with the specified index and columns. The `index` parameter specifies the row labels of the dataframe, while the `columns` parameter specifies the column labels. In this case, the index is set to ['A'] and the columns are set to ['a', 'b', 'c']. The values of the dataframe are set to NaN (Not a Number) for all the cells.To create the dataframe x with the specified structure, you can use the following Python statement: `x = pd.DataFrame(index=['A'], columns=['a', 'b', 'c'])`. This statement uses the pandas library, which provides high-performance data manipulation and analysis tools. The `pd.DataFrame()` function is a constructor for creating dataframes in pandas. In this case, the `index` parameter is set to `['A']`, which specifies the row label for the dataframe. The `columns` parameter is set to `['a', 'b', 'c']`, which specifies the column labels for the dataframe. The resulting dataframe, x, will have one row labeled 'A' and three columns labeled 'a', 'b', and 'c'. All the cells in the dataframe will have NaN (Not a Number) as their values. NaN is a special floating-point value that represents missing or undefined data. It is commonly used in data analysis to indicate the absence of a value. By creating the dataframe x using the specified index and columns, you can easily access and manipulate the data stored in the dataframe for further analysis and processing. To create the dataframe x with the specified structure, you can use the statement `x = pd.DataFrame(index=['A'], columns=['a', 'b', 'c'])`. This code utilizes the pandas library to construct the dataframe, specifying the row and column labels. The resulting dataframe will have one row labeled 'A' and three columns labeled 'a', 'b', and 'c', with NaN as the value for each cell. NaN is a special value used to represent missing or undefined data. Creating the dataframe in this way allows for easy data manipulation and analysis using the pandas library.
To know more about Dataframe , Visit:
https://brainly.com/question/32136657
#SPJ11
do you think I-beams are a good thing to use for head frame supports? why?
Answers
HELP asap please...

Answers
Answer:
I have absolutely no idea bruddah.
Explanation:
Soz!