The profession of ____ is emerging from a chaotic set of conflicting ethics from both the hobbyist and student communities and those on the information technology career track.
Answers
The profession of network security is emerging from a chaotic set of conflicting ethics from both the hobbyist and student communities and those on the information technology career track.
The profession of network security needs to be handled through strict policy measures and breaching of even the simplest of policies can lead to huge trouble.
Often a time, the ethics being discussed over a certain network issue are conflicting as before taking any step, the professionals have to understand what is ethically right and wrong. The privacy of the users needs to be prioritized along with providing a stable network.
In the field of Information Technology, network security is one of the most conflicting professions as there are many ethical concerns that need to be looked upon when choosing it as a career path.
To learn more about ethics, click here:
https://brainly.com/question/25720881
#SPJ4
Related Questions
what are some of the advantages and disadvantages of a parallel development process? what obstacles might a firm face in attempting to adopt a parallel process?
Answers
Advantages of a parallel development process include faster development and higher quality. Disadvantages include increased complexity and cost.
A parallel development process allows multiple teams to work simultaneously on different parts of a project, which can lead to faster development times and better productivity. It can also lead to more efficient use of resources, as teams can work on different parts of the project without waiting for others to finish their work. However, coordinating and integrating the work of multiple teams can be a challenge, as it requires effective communication and collaboration. In addition, parallel development can lead to increased complexity, as changes made by one team can affect the work of other teams. Adopting a parallel process may require significant organizational changes and investment in tools and resources to support collaboration and communication.
Learn more about parallel development here:
https://brainly.com/question/28555878
#SPJ11
what mode do you use to extract split or reshape your red Builder brush
Answers
Answer:
what the hell is a red builder brush???
What are the requirements of a data dictionary ?
Answers
Answer:
nullability, optionality, size, indexes, data type
Explanation:
Big data are used to _____. Select 3 options.
create artificial intelligence
understand people’s hobbies
analyze people’s interests
process privacy policies
make decisions about marketing
Answers
Answer:
Big data are used to _____. Select 3 options.
understand people’s hobbies
analyze people’s interests
make decisions about marketing
Explanation:
100%
In computer technology and business, Big data are used to:
Understand people’s hobbies.Analyze people’s interests.Make decisions about marketing.What is Big data?Big data refers to a huge collections of data that are typically difficult for end users or business organizations to process, analyze, and manage through the use of conventional data tools.
Generally, Big data are used in collaboration with database management systems (DBMS) to achieve the following:
Understand people’s hobbies.Analyze people’s interests.Make decisions about marketing.Read more on Big data here: https://brainly.com/question/14273643
Match the components to their human counterparts.
1 controller
2 sensor
3 actuator
4 end effector
A fingers
B skin
C muscles
D brain
Will mark brainliest
Answers
When matched, you have:
1 controller - D brain
2 sensor - B skin
3 actuator - C muscles
4 end effector - A fingers
What do the above do?Controller: Manages and coordinates the operation of robotic systems or devices.
Sensor: Detects and measures physical quantities or environmental conditions.
Actuator: Converts control signals into mechanical or physical actions.
End effector: Performs specific tasks or manipulations at the end of a robotic arm or system.
Note that these are parts of robots and are very useful in building any automated system that interact with the human environment.
Learn more about sensors:
https://brainly.com/question/29569820
#SPJ1
anyone can help me answer this puzzle i really need it right now. thanks!
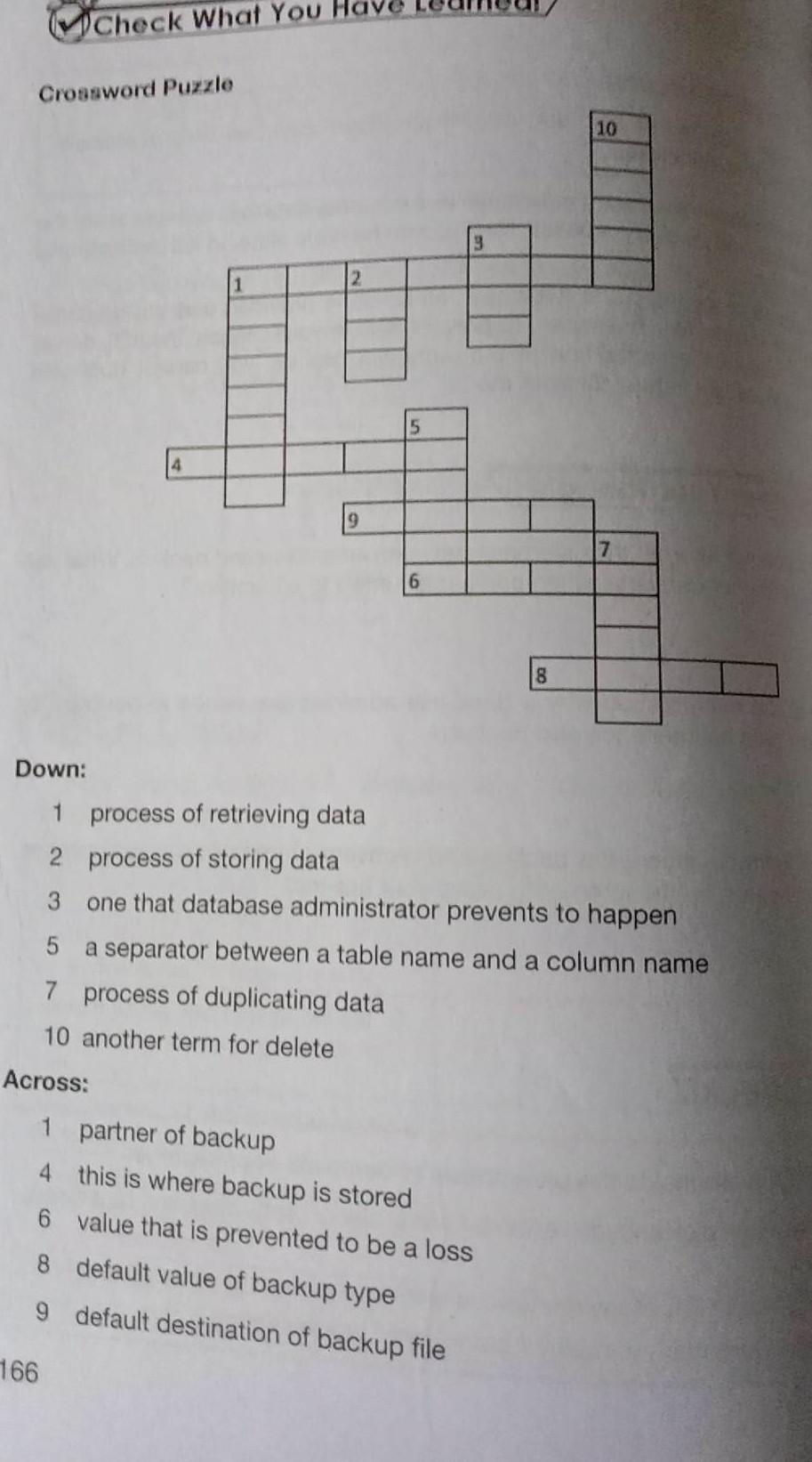
Answers
The right words that can be used to fill up the blank spaces in the puzzle are as follows:
data is fetching. data storagebreachperiodredundancydelete is remove or dropHow to fill up the blanksTo insert the correct words in the puzzles, we need to understand certain terms that are used in computer science.
For example, a data breach occurs when there is a compromise in the systems and it is the duty of the database administrator to avoid any such breaches. Also, data fetching is another jargon that means retrieving data.
Learn more about data fetching here:
https://brainly.com/question/14939418
#SPJ1
Which formula would add the January and February profits?

Answers
thin layer found directly under the crust that floats and moves around is called
Answers
The thin layer found directly under the crust that floats and moves around is called the lithosphere.
The lithosphere is the thin layer found directly under the Earth's crust that is responsible for the movement and floating of tectonic plates. It encompasses the rigid outermost layer of the Earth's surface, including the crust and the uppermost part of the mantle.
The lithosphere plays a crucial role in the process of plate tectonics, which drives the movement of continents, the formation of mountains, and the occurrence of earthquakes and volcanic activity. Understanding the composition and behavior of the lithosphere is essential for gaining insights into the dynamics of the Earth's geology and geophysics, and for studying the evolution of our planet's surface and its geological processes over time.
Learn more about lithosphere: https://brainly.com/question/10162846
#SPJ11
Why should even small-sized companies be vigilant about security?
Answers
Answer:businesses systems and data are constantly in danger from hackers,malware,rogue employees, system failure and much more
Explanation:
Could someone please tell me what is the error in my code?
I'm trying to write a code for finding the cube of a number using C programming.

Answers
I think you have to remove the semicolon at the end of line 15. From what I see, this is not a logic error, rather than a syntax error.
Looking at the error on the bottom, it's expecting a '(' before the '{'.
Do you believe that a paperless environment is something worth striving for in the home? In the bank?
Answers
Yes, I agree that achieving a paperless environment in the home, office, and bank is worthwhile.
Do you believe that we should strive for a paperless society?Eliminating paper from your life can lessen the environmental damage that the paper industry is causing. If everyone in the world stopped using paper, deforestation would be reduced by almost half since the pulp and paper industry uses 42% of all trees that are harvested.
To produce that much paper, ten to twenty trees are needed. Because each tree can produce up to three people's worth of oxygen, the production of oxygen is reduced by 30 to 60 people during the making of one sheet of paper.
To know more about paperless environment visit:
https://brainly.com/question/1579717
#SPJ9
If someone want to type race with me :
https://play.typeracer.com?rt=21mvsi61s8
Let's improve our typing speed.
Reccomendation:(Use computer)
Answers
you have used firewalls to create a screened subnet. you have a web server that needs to be accessible to internet users. the web server must communicate with a database server to retrieve product, customer, and order information. how should you place devices on the network to best protect the servers? (select two.)
Answers
Answer:
Explanation:
1. Put the web server inside the screened subnet.
2. Put the database server on the private network.
Publicly accessible resources (servers) are placed inside the screened subnet. Examples of publicly accessible resources include web, FTP, and email servers. Devices that should not be accessible to public users are placed on the private network. If you have a public server that communicates with another server (such as a database server) and that server should not have direct contact with public hosts, place the server on the private network and allow only traffic from the public server to cross the inner firewall.
In a typical information security program, what is the primary responsibility of information (data) owner
Answers
The typical responsibility of the information that an owner is to determine the level of sensitivity or classification level.
What is an information security program?The information security program is a set of activities, projects, and initiatives that help an organization IT framework and help the organization meet all the business goals leading to corresponding to the benchmarks. The main duty of the data owner is to determine the level of sensitivity of the data.
Find out more information about information security.
brainly.com/question/25226643
what style is used for double spacing
Answers
Which of the following is a type of multimedia?(1 point)
a magazine article about ways to stay active
the handwritten notes from a lecture
a podcast included as part of an online news column
the textbook edition of a Shakespearean play
Answers
Answer: C
a podcast included as part of an online news column
the answers might be in a different order on ur side, but the answer will stil be the same. A podcast included as part of an online news column
I hope this helps : )
if the decoder has active low outputs (74155) instead of active high outputs as the case for our 3-to-8 decoder, why can a nand gate be used to logically or its outputs?
Answers
Due to the fact that there are a total of four possible logic combinations that may be created using just two variables, the initial stage of the 2-to-4 decoder requires four 2-input NAND gates.
A NAND gate (NOT-AND) is a logic gate used in digital electronics that creates an output that is false only if all of its inputs are true; as a result, it is the complement to an AND gate. Only when all of the gate's inputs are HIGH (1) does the output become LOW (0); otherwise, the output becomes HIGH (1) if any input is LOW (0). Transistors and junction diodes are used to create NAND gates. According to De Morgan's rules, the logic of a two-input NAND gate may be written as A • B=A+B, making it the same as inverters followed by an OR gate.
Because any boolean function may be implemented using a combination of NAND gates, the NAND gate is important. The term functional completeness refers to this quality.
To know more about NAND gate click here:
https://brainly.com/question/12969448
#SPJ4
Who invented the television and what year did color come out? Explain
Answers
The television was not invented by a single person, but its development involved contributions from several inventors and engineers.
How is this so?Philo Farnsworth is often credited as one of the key inventors of television, as he successfully demonstrated the first working electronic television system in 1927.
As for color television, it was first introduced commercially in the United States in 1953 by RCA.
The introduction of color television marked a significant milestone in broadcasting, enhancing the viewing experience for audiences worldwide.
Learn more about television at:
https://brainly.com/question/12079773
#SPJ1
Use the drop-down menus to complete the steps for using the Go To feature.
1. Press the shortcut key of F5 ✓
2. Type the
✓in the
3. Hit OK or select Special for more options.
✓box.
4
Answers
Answer:
Explanation:
. Select "Go To Special" from the "Go To" dialog box.
5. Choose the type of cell you want to go to, such as a blank cell or a cell with an error, or select "OK" to go to the default type of cell, which is a blank cell.
6.Click "OK" to go to the selected cell or range of cells.
the electronic data gathering and retrieval (edgar) system provides all publicly available data filed with the u.s. sec.
true or false
Answers
The electronic data gathering and retrieval (edgar) system provides all publicly available data filed with the u.s. sec. The statement is True.
The Electronic Data Gathering, Analysis, and Retrieval (EDGAR) system is a database maintained by the United States Securities and Exchange Commission (SEC) that contains all publicly available information filed by companies and individuals with the SEC. The system was created in 1984 to provide investors and the public with free access to financial reports, company filings, and other important information that can help them make informed decisions. The EDGAR system is updated daily and provides access to over 21 million filings from more than 60,000 entities. Therefore, it is true that the EDGAR system provides all publicly available data filed with the U.S. SEC.
The statement is true. The EDGAR system is a reliable source of information for investors and the public as it provides access to all publicly available data filed with the U.S. SEC.
To know more about database visit:
https://brainly.com/question/6447559
#SPJ11
Myra uses source code belonging to older malware to develop new malware. She also removes some of the functions of the older malware. Why
would Myra do that?
OA
OB
OC
OD. to keep the new malware undetected through heuristic checks
to recreate the older malware
to launch a blended attack
to reduce the size of the malware
Answers
Myra uses source code belonging to older malware to develop new malware. She also removes some of the functions of the older malware to reduce the size of the malware. The correct option is D.
Myra may remove some functions of the older malware to reduce the size of the new malware. By removing unnecessary or unused code, the overall size of the malware can be minimized. This can have several advantages:
Lower detection rate.Faster propagation.Easier distribution.Enhanced stealthiness.Thus, the correct option is D.
For more details regarding malware, visit:
https://brainly.com/question/29786858
#SPJ1
PLEASE HELP!!!!!! ASAP
What are two ways to create forms in Base to search data?
Use a wizard, or use Design View.
Use a wizard, or use a report.
Use a report, or use Design View.
Use a report, or use a table.
Answers
Answer:
use a wizard or use a design view
Explanation:
i took the test
Answer: A
Explanation:
A. Who will use the database?
Drag each tile to the correct box. Wesley is formatting a report for a science project in a word processor. Match each formatting tool to its purpose.
Bullets
Line and Paragraph Spacing
Purpose
Format Painter
emphasize key words in each section
Bold
insert a list of apparatus required
increase the distance between the steps for performing an experiment
copy the formatting of a heading and apply it to other headings
Tool
Answers
Answer:
Bullets: insert a list of apparatus required
Line and Paragraph Spacing: increase the distance between the steps for performing an experiment
Bold: emphasize key words in each section
Format Painter: copy the formatting of a heading and apply it to other headings
Answer:
a-2,b-4,c-1,d-3
Explanation:
!!!!!HELP!!!!! (30PTS)
Suppose you are using a Mac to read your e-mail messages, and your receive an e-mail message with a PowerPoint file attached. PowerPoint is not installed on the Mac you are working with. Which of these could you use to view the file? Choose all answers that are correct.
A. a text editor
B. Keynote
C. PowerPoint Online
D. a photo editor
Answers
Answer:
B. KN
C. PP Online
Explanation:
KN is A's own software for creating slideshow presentations. However, since most people using KN are coming from using MS PP, there is the option to open PPs in KN (albeit with some fonts missing).
You can also view the file from PP Online. Just create a MS account (if you don't already have one), download the email attachment and upload it to your cloud, and you should be able to view it there.
please help
if I clear data on play services framework, will it delete all files on phone
Answers
Answer:
Hey there!
Explanation:
Hope this helps :)

when a cpu executes instructions as it converts input into output, it does so with _____.
Answers
Answer:
1. control unit
2. arithmetic logic unit
Explanation:
CPU is known to executes instructions as it changes input into output via:
The control unit.The arithmetic logic unit.How does a CPU convert input to output?The Central Processing Unit (CPU) is to be the one that uses binary data in terms of input and it is also known to processes data based on the instructions and gives result in form of output.
Therefore, CPU is known to executes instructions as it changes input into output via:
The control unit.The arithmetic logic unit.Learn more about control unit from
https://brainly.com/question/15607873
#SPJ6
The mode that allows the kernel to take care of low-level tasks requiring unlimited access to the hardware is called what
Answers
Answer:
Supervisor mode is used by the kernel for low level tasks that need unrestricted access to hardware, such as controlling how memory is accessed, and communicating with devices such as disk drives and video display devices. User mode, in contrast, is used for almost everything else.
Explanation:
Java uses a left/right brace to mark the beginning/end of if-statement, compare this choice with the language which uses the "beginIF/endIF" keywords.
What language uses "beginIF/endIF" and how does it compate to Java left/right braces?
Answers
Answer:
The answer is "Scribe markup language ".
Explanation:
Using the Code is the same processing in 2 stages which can be defined as follows;
1. by using a scripting language to type a script.
2. Proceed with both the file and produce the necessary documentation through your scribe compiler. If / endif starts with the reserved keyword.
by using BeginIf / EndIf, it is a type of multiple rules to make comments.
In the beginning, if / endif, as well as java left-right braces, are no different.
It uses two blocks or sentences for opening and closing.
Both use the module to distinguish and both use feature isolation, process, and condition in a separate block when the compiler can understand what statement the method or section is using brackets.
PL / SQL is also used for endif.
If the statement to close.
endif is used in c # as well
If the rule is often used for closing.
You are using a device that reads the physical addresses contained in incoming data that travels along network cables. Based on the physical address that it reads, the device then forwards the data out one of its ports to reach the destination device. What type of device are you using
Answers
You are using a device that reads the physical addresses contained in incoming data that travels along network cables. Based on the physical address that it reads, the device then forwards the data out one of its ports to reach the destination device. The type of device you are using is router.
What is Router?A router is an hardware device that is used in transferring information or data from a system to another.
The data can also be transfered from one computer networks to another.
Router makes it easier for more than one device to be connected easily without difficult Internet access.
Therefore, The type of device you are using that reads incoming data that travels along network cables is router.
Learn more on router below
https://brainly.com/question/24812743
#SPJ1
can you cure the effects of fatigue without sleep
True or false
FOR THE LOVE OF GOD I NEED HELP PLEASE HELP