The part of the CPU that is responsible for deciding which job to run at any given time is called the
Answers
The part of the CPU that is responsible for deciding which job to run at any given time is called the scheduler.
The Central Processing Unit (CPU) is a microprocessor that controls the central processing unit of a computer system. It receives input from input devices, performs arithmetic and logical operations on it, and then sends output to output devices.The CPU has two primary components: the arithmetic logic unit (ALU) and the control unit (CU).
The arithmetic logic unit is responsible for performing arithmetic and logical operations, whereas the control unit is responsible for managing and coordinating CPU operations.
A scheduler is a component of the operating system that manages computer processes and ensures that each process gets the resources it requires to operate successfully. The scheduler is responsible for determining which process runs at any given moment, how much time each process gets to run on the CPU, and when to switch from one process to the next.
To know more about Central Processing Unit (CPU) , visit https://brainly.com/question/474553
#SPJ11
Related Questions
Exercise 2. 4. 8: Greetings and Salutations5 points
Write a class called Salutations that prints various greetings and salutations.
The class should have one instance variable, a String called name to represent the person to whom the salutations are directed.
The class should have the following methods
A constructor that takes a String to initialize name with
public void addressLetter()
public void signLetter()
public void addressMemo()
public void signMemo()
addressLetter should print "Dear name", where name is replaced by the value of the instance variable name
signLetter() should print
"Sincerely,
name"
where name is replaced by the value of the instance variable name
addressMemo should print "To whom it may concern"
signMemo should print
"Best,
name
where name is replaced by the value of the instance variable name
Answers
Below is the implementation of the "Salutations" class in Java that meets the provided requirements:
public class Salutations {
private String name;
public Salutations(String name) {
this.name = name;
}
public void addressLetter() {
System.out.println("Dear " + name + ",");
}
public void signLetter() {
System.out.println("Sincerely,\n" + name);
}
public void addressMemo() {
System.out.println("To whom it may concern");
}
public void signMemo() {
System.out.println("Best,\n" + name);
}
public static void main(String[] args) {
Salutations salutations = new Salutations("John Doe");
salutations.addressLetter();
salutations.signLetter();
salutations.addressMemo();
salutations.signMemo();
}
}
Below is the implementation of the "Salutations" class in Java that meets the provided requirements:
java
Copy code
public class Salutations {
private String name;
public Salutations(String name) {
this.name = name;
}
public void addressLetter() {
System.out.println("Dear " + name + ",");
}
public void signLetter() {
System.out.println("Sincerely,\n" + name);
}
public void addressMemo() {
System.out.println("To whom it may concern");
}
public void signMemo() {
System.out.println("Best,\n" + name);
}
public static void main(String[] args) {
Salutations salutations = new Salutations("John Doe");
salutations.addressLetter();
salutations.signLetter();
salutations.addressMemo();
salutations.signMemo();
}
}
In the above class, we have an instance variable called "name" of type String, which represents the person to whom the salutations are directed. The class has a constructor that takes a String argument to initialize the "name" variable.
The class also includes the following methods as specified:
The "addressLetter" method prints "Dear name", where "name" is the value of the instance variable.
The "signLetter" method prints "Sincerely," on one line and then prints the "name" on the next line.
The "addressMemo" method prints "To whom it may concern".
The "signMemo" method prints "Best," on one line and then prints the "name" on the next line.
To test the functionality of the "Salutations" class, a "main" method is included that creates an instance of the class with a sample name "John Doe". It then calls the different methods to demonstrate the expected output.
Executing the main method will result in the following output:
Dear John Doe,
Sincerely,
John Doe
To whom it may concern
Best,
John Doe
Each method performs its respective task as described, utilizing the instance variable "name" in the output statements.
For more questions on Java
https://brainly.com/question/31569985
#SPJ11
Fill in the blank: Sticker sheets are useful in a design system because _____.
designers can work faster and avoid rework
Answers
Answer:
Sticker sheets are useful in a design system because they enable designers to quickly and easily copy and paste components into new designs, reducing the amount of time needed to create designs and avoiding the need for rework.
Explanation:
They enable designers to produce reusable visual components that are consistent with the brand, enhancing user experience all around.
Technical definition sheet: What is it?A technical data file (TDS) is just a document that comes with a product and contains a variety of details about the item. Technical data sheets frequently feature information about the product's composition, usage guidelines, technical specifications, typical applications, cautions, and product images.
What does the word "sheets" mean?Paper each is typically rectangular in appearance. especially: equipment specifically engineered for printing. (2) : a mounted plant specimen on a relatively thin, rectangular sheet of paper. a 100,000 sheet important to the advancement.
To know more about Sheets visit :
https://brainly.com/question/30277396
#SPJ4
Describe each of the principal factors risk factors in
information systems projects (20 marks)
Answers
The principal risk factors in information systems projects encompass various aspects such as project complexity, technology challenges, organizational factors, and external influences.
These factors contribute to the potential risks and uncertainties associated with the successful implementation of information systems projects.
Project Complexity: Information systems projects can be inherently complex due to factors such as scope, scale, and the integration of multiple components. The complexity may arise from intricate business processes, diverse stakeholder requirements, or the need for extensive data management. Complex projects pose risks in terms of project management, resource allocation, and potential delays or cost overruns.
Technology Challenges: Information systems projects often involve implementing new technologies, software systems, or infrastructure. Technological risks include compatibility issues, scalability limitations, security vulnerabilities, and the need for specialized expertise. These challenges may impact the project timeline, functionality, and long-term viability of the system.
Organizational Factors: The success of an information systems project depends on organizational factors such as leadership, communication, and stakeholder engagement. Risks in this domain include lack of management support, insufficient user involvement, resistance to change, inadequate training, and poor project governance. Failure to address these factors can lead to user dissatisfaction, low adoption rates, and project failure.
External Influences: External factors, such as changes in regulatory requirements, market dynamics, or economic conditions, can introduce risks to information systems projects. These factors may necessitate modifications to project scope, increased compliance efforts, or adjustments to business strategies. Failure to anticipate and adapt to external influences can disrupt project timelines and impact the project's overall success.
Understanding and managing these principal risk factors is crucial for effective project planning, risk mitigation, and successful implementation of information systems projects. Proper risk assessment, contingency planning, stakeholder involvement, and ongoing monitoring are essential to minimize the impact of these risks and ensure project success.
Learn more about information systems here:
https://brainly.com/question/13081794
#SPJ11
In our situation now a days in online class we are experiencing different problems such as internet
problems like internet connection low quality gadgets technical problems using laptops and computers set up as an ict student how can you solve these common learning problems based on the knowledge you gained in computer hardware servicing
Answers
How should an artist use the principles of design when creating artistic work?
follow them to the letter
let them come naturally
don’t think about them
experiment with them
Answers
Answer:
Let them come naturally
Explanation:
I think
Explain the expression below
volume = 3.14 * (radius ** 2) * height
Answers
Answer:
Explanation:
Cylinder base area:
A = π·R²
Cylinder volume:
V = π·R²·h
π = 3.14
R - Cylinder base radius
h - Cylinder height
HOW TO USE THIS IN A STORY CAN ANYONE HELP PICK % WORD FROM THE PAGE AN MAKE A STORY WHY DO I LIKE SUMMER ?????////
get 60 piont if you if you help meeeeeeeeeeee
ASAPPPPPPPPPPPPPPPPPPPPPP
The sunshine
Light mornings
Long light nights
BBQs in the garden
The smell of sun cream
Pretty wildflowers
Cloudless blue skies
Going to the beach
Feeling the warm sun on your face
Summer clothes
Sunglasses
Picnics in the park
Long walks
Sitting out on a warm evening
Eating fresh tasty salads
Drinking sangria
Orange glowy sunsets
Fresh air
Exploring new places
Ice cream (or Dairy Free alternative)
Summer playlists
Road trips
Eating fresh strawberries
Ice cold drinks on a hot day
The smell of freshly cut grass
Not having to wear a jacket when out
Autumn is just around the corner
Holidays at home or abroad
Salty sea breezes
Summer always seems to make people happier
Answers
Answer:
Picnic in the Park
Explanation:
Parks are my favorite spots to chill or go for a stroll. Parks make walking in a neighborhood more fun and offer space for common sports, promoting physical activity. They have hiking trails and other amenities to get people moving. Every place, in my opinion, needs some green space where people can get away from the crowds. I live near a park, so if the weather is good, I usually go there once or twice a week. Therefor, my favorite summer activity is going to the park.
excel functions are prebuilt formulas within excel.
Answers
Formulas are mathematical equations that integrate cell references, excel values, and operators to compute results. It is not necessary to write the underlying formula when using functions because they are prebuilt formulas that can be rapidly fed values.
What do Excel's functions and formulas mean?Functions are pre-written formulas that perform calculations using specific variables, also known as inputs, in a predetermined order or structure. Functions can be used to do calculations of any complexity. The Formulas tab on the Ribbon contains the syntax for all of Excel's functions.
What is the name of the pre-written formulas in Excel?An already written formula is a function. A function performs an operation on a value (or values), then returns a new value (or values.)
To know more about excel visit:-
https://brainly.com/question/3441128
#SPJ4
How can you tell an open innovation project from one that is not?
Answers
An open innovation project is one in which a company seeks external ideas, knowledge, and expertise from outside the organization to advance its goals, rather than relying solely on internal resources. Conversely, a project that is not open innovation relies primarily on internal resources and expertise.
Here are some characteristics of an open innovation project:
Collaboration: Open innovation projects involve collaboration between internal teams and external partners such as customers, suppliers, academic institutions, startups, and other companies.
Sharing of knowledge: An open innovation project requires sharing of knowledge, information, and expertise between the internal and external parties.
Involvement of external parties: In an open innovation project, external parties are actively involved in the innovation process, from ideation to commercialization.
Innovation ecosystem: An open innovation project is part of a larger innovation ecosystem that fosters the exchange of ideas, knowledge, and expertise.
Access to resources: An open innovation project provides access to external resources such as funding, facilities, equipment, and talent.
In contrast, a project that is not open innovation is typically driven by internal resources and expertise. Internal teams are responsible for all aspects of the innovation process, and external parties are not involved in any significant way.
In summary, an open innovation project involves collaboration, sharing of knowledge, involvement of external parties, an innovation ecosystem, and access to external resources.
disadvantages of using lossless compression rather than lossy compression
Answers
Answer:
Larger files
Explanation
Lossless advantages and disadvantages Advantages: No loss of quality, slight decreases in image file sizes. Disadvantages: Larger files than if you were to use lossy compression.
Compression, Explained. We use compression to make files smaller, so that they take up less storage space and can be downloaded more quickly.
Lossless vs. Lossy Formats.
Lossy Compression. Lossy compression is useful because of its ability to shrink a file to a more convenient size
Select the Pixel Format to be either Mono8 or BayerRG8.
Ensure ISP Enable is not selected (disabled).
From the Image Compression Mode drop-down, select Lossless.
Select the Adaptive Compression Enable checkbox to allow dynamic updates to compression tables to achieve a better compression ratio.
sometimes groups of data packets are sent together in a package called a:
Answers
Explanation:
On client/server networks, more users can be added without affecting the performance of other nodes. This is known as network
The groups of data packets are sent together in a package called a frame.
What is Data?Data are discrete values that transmit information, such as amount, quality, fact, statistics, or other basic units of meaning, or just sequences of symbols that may be interpreted further. A datum is a single value inside a set of data.
A frame is defined as "the transmission unit of a link layer protocol, consisting of a link layer provided in order by a packet." An interframe gap separates each frame from the next. A frame is a collection of bits that includes frame synchronization bits, the package content, and a frame check sequence.
A frame carries more data about the message being conveyed than a packet. There are two sorts of frames in networking: fixed-length frames and variable-length frames.
Learn more about data here:
https://brainly.com/question/10980404
#SPJ2
What is the result when one tries to compile and run the following code? public final static void main(String[] args) { double d = 10.0 / -; if(d == Double.POSITIVE INFINITY) System.out.println("Positive infinity"); else System.out.println("Negative infinity"); Pick ONE option a. Positive infinity b. Negative infinity c. Will fail to compile d. Runtime exception
Answers
The result, when trying to compile and run, the following code, will fail to compile. The correct option is c.
What is compiling?Compiling is compiling data from several sources and organizing it in a book, report, or list: We are gathering information for a documentary on the topic.
Pre-processing, compilation, assembly, and linking are the four processes that make up the compilation process. The preprocessor removes all the comments from the source code after receiving it as input. The preprocessor interprets the preprocessor directive.
Therefore, the correct option is c. Will fail to compile.
To learn more about compiling, refer to the link:
https://brainly.com/question/28314203
#SPJ1
Adjust the code you wrote for the last problem to allow for sponsored Olympic events. Add an amount of prize money for Olympians who won an event as a sponsored athlete.
The
Get_Winnings(m, s)
function should take two parameters — a string for the number of gold medals and an integer for the sponsored dollar amount. It will return either an integer for the money won or a string Invalid, if the amount is invalid. Olympians can win more than one medal per day.
Here's my answer for question 1 please adjust it thanks!
def Get_Winnings(m):
if m == "1": return 75000
elif m == "2":
return 150000
elif m == "3":
return 225000
elif m == "4":
return 300000
elif m == "5":
return 375000
else:
return "Invalid"
MAIN
medals = input("Enter Gold Medals Won: ")
num = Get_Winnings(medals)
print("Your prize money is: " + str(num))
Answers
Answer:def Get_Winnings(m):
if m == "1": return 75000
elif m == "2":
return 150000
elif m == "3":
return 225000
elif m == "4":
return 300000
elif m == "5":
return 375000
else:
return "Invalid"
MAIN
medals = input("Enter Gold Medals Won: ")
num = Get_Winnings(medals)
print("Your prize money is: " + str(num))
exp: looking through this this anwser seemes without flaws and i dont follow
if you can provide what you are not understanding ican an help
in the waterfall methodology, we complete a document for management review at the end of each phase. the final document in design phase is called the:
Answers
In waterfall model the final documentation in the design phase is called system specification.
What is waterfall methodology?The Waterfall technique, often referred to as the Waterfall model, is a sequential development process that moves like a waterfall through all project phases (such as analysis, design, programming, and testing), with each phase finishing up completely before the next one starts.However, in general, the waterfall approach's tasks can be divided into five stages: planning, design, implementation, verification, and maintenance.The primary difference between Agile and waterfall is Agile encourages the team to work concurrently on several project phases, Waterfall is a linear style of working that demands the team to complete each project phase before moving on to the next one.To learn more about waterfall model refer to :
https://brainly.com/question/25757629
#SPJ1
___ is the process of discovering useful knowledge from a collection of data.
BIG
DATA
THE 3 V’S
KDD
Answers
What are some innovative research ideas for Onshore/Offshore hybrid wind turbines?
I was thinking whether it could be integrated with AI technologies, Pv Cells, thermoelectric plates, piezoelectric etc etc
please give me some inspirations
Answers
Some innovative research ideas for onshore/offshore hybrid wind turbines include integrating AI technologies for advanced control and optimization, incorporating PV cells for hybrid energy generation, utilizing thermoelectric plates for waste heat recovery, and exploring the potential of piezoelectric materials for vibration energy harvesting.
One innovative research idea is to integrate AI technologies into onshore/offshore hybrid wind turbines. AI algorithms can be used to optimize turbine performance by analyzing real-time data and making adjustments to maximize energy production and efficiency. AI can also enable predictive maintenance, allowing for proactive identification of potential issues and minimizing downtime.
Another idea is to incorporate photovoltaic (PV) cells into the hybrid wind turbines. By combining wind and solar energy generation, these turbines can generate power from both sources, maximizing energy output and improving the overall reliability and stability of the system.
Additionally, exploring the use of thermoelectric plates in hybrid wind turbines can enable the recovery of waste heat generated by the turbine. This waste heat can be converted into electricity, enhancing the overall energy efficiency of the system.
Furthermore, researchers can investigate the application of piezoelectric materials in hybrid wind turbines for vibration energy harvesting. These materials can convert mechanical vibrations caused by wind turbulence into electrical energy, supplementing the power output of the turbine.
These innovative research ideas highlight the potential for integrating AI technologies, PV cells, thermoelectric plates, and piezoelectric materials into onshore/offshore hybrid wind turbines to enhance their performance, energy generation capabilities, and efficiency.
Learn more about AI technologies here:
https://brainly.com/question/30089143
#SPJ11
given integer variables seedval, minnum, and maxnum, output two random integers in the range minnum to maxnum inclusive. end each output with a newline. ex: if minnum is 5 and maxnum is 87, then a possible output is:
Answers
To generate two random integers within the range of minnum and maxnum, we can use the following code in Python:
import random
# Set the seed value
seedval = 12345
random.seed(seedval)
# Define the minimum and maximum numbers
minnum = 5
maxnum = 87
# Generate two random integers within the range
rand1 = random.randint(minnum, maxnum)
rand2 = random.randint(minnum, maxnum)
# Output the random integers
print(rand1)
print(rand2)
This code imports the 'random' module, sets the seed value, defines the minimum and maximum numbers, and generates two random integers within the given range using the 'randint()' function. The output is then printed to the console with a newline after each value.By setting the seed value, we can ensure that the same sequence of random numbers is generated each time the program is run, which can be useful for testing and debugging purposes.To know more about coding visit:
https://brainly.com/question/17293834
#SPJ1
the property in css used to change the background colour of an element is
Answers
Answer:
background-color property
The background-color property in CSS is used to specify the background color of an element. The background covers the total size of the element with padding and border but excluding margi
Explanation:
Answer:
CSS | background-color Property. The background-color property in CSS is used to specify the background color of an element. The background covers the total size of the element with padding and border but excluding margin. It makes the text so easy to read for the user.
Explanation:
embedded software usually runs only during the boot process of a device. t or f
Answers
"Embedded software typically only operates during a device's boot phase." This claim is untrue.
The process of booting up, which a embedded system goes through between turning on the power and loading apps, is straightforward in theory but frequently more difficult in practice. Although the primary function of a bootloader is to load the operating system, software and hardware engineers have distinct perspectives on this process.
The concept of the system-boot process may be straightforward, but when you take into account different implementation alternatives, it gets complicated. An example of a well-known case study of a traditional boot sequence is Windows XP. The processor can receive post-reset configuration data via a variety of hardware and software methods. Different starting and kernel-code sizes, read- and write-performance requirements, and other factors are taken into account by primary and secondary boot options. A potent open-source technology called U-Boot (Universal Boot Loader) should be taken into account in Linux-based architectures.
Know more about Embedded software:
https://brainly.com/question/26422781
#SPJ4
Draw a flow chart for the examples in selection 1:2:1
Someone help me please.
Answers
Answer:
See picture
Explanation:
Here is an example of a flowchart I found on the web. You use a rhombus shape for a decision, that usually branches into a yes and a no branch.
Without more details, that's about as much that can be said.

what are the answers for theses question?




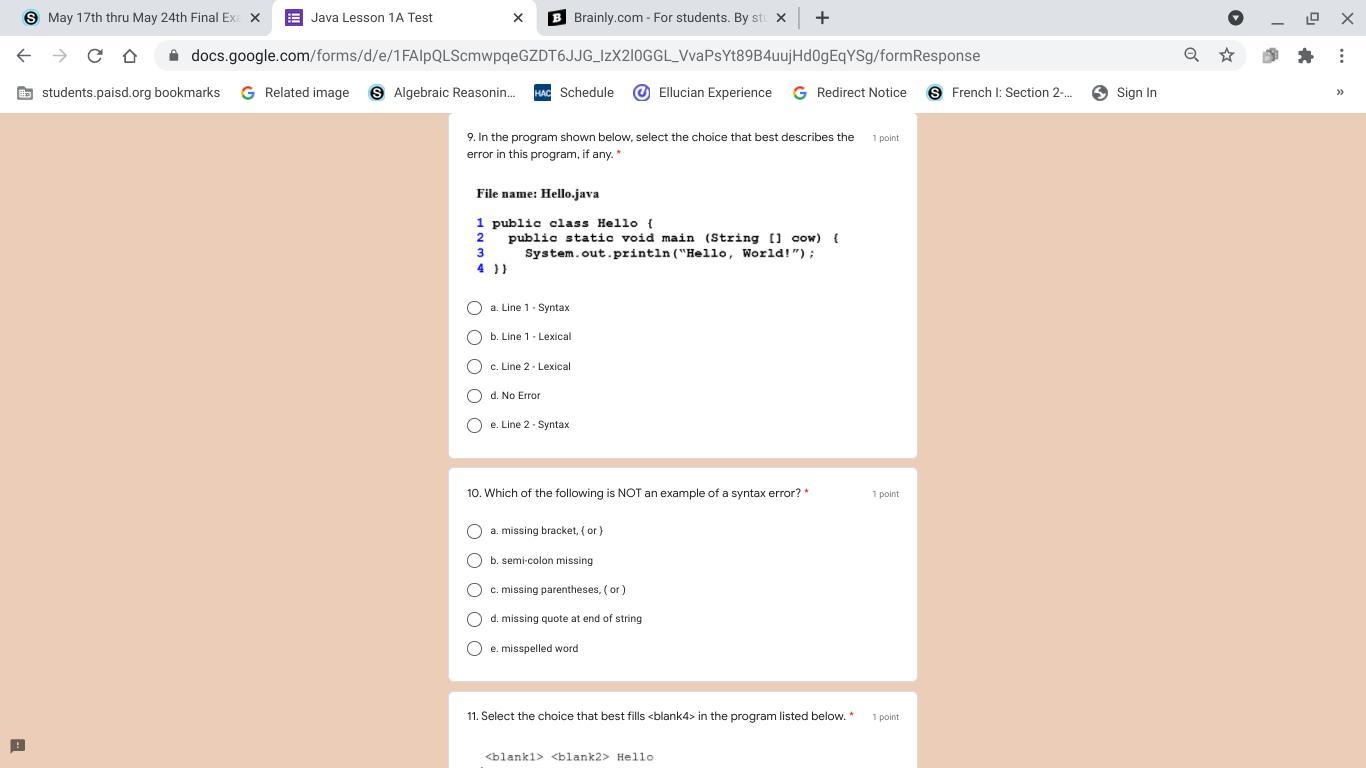
Answers
Answer: me no comprende coding
Explanation:
sorry
Gabby is creating a game in which users must create shapes before the clock runs out. Which Python module should Gabby use to create shapes on the screen? a Design Graphics b Math Module c Turtle Graphics d Video Module
ANSWER QUICKLY
Answers
Answer:
The answer is "Turtle Graphics"
Explanation:
I took the test and got it right.
What types of customizations have you or would you make to your operating system, and why?
Answers
Answer:
Explanation:
I have made a couple of customizations to my OS, which is Windows 10. The first being that I activated dark mode, this feature turns the entire OS into a dark-themed color, including apps and menus. This makes using the computer for extended hours much easier on the eyes. The other very important customization I added was a hover taskbar. This allows me to add many important shortcuts to the taskbar which all appear when I hover over the taskbar. It makes my desktop much cleaner and I have quick and easy access to my most important applications.
outline the steps involved in changing the colour of a theme
Answers
Answer:
Right click on the desktop and click on personalize option and then click on window color. After that window color and appearance window appears. select a color scheme you want. Go to Appearance and personalization, click on theme and select any theme from the list and click on ok.
What does the following line of code do? Assume the user enters 2.3.
answerA = input("Enter a number. ")
It stores an int in the variable.
It stores a string in the variable.
It stores a float in the variable.
This line of code causes an error.
Answers
Answer:
It stores an int in the variable.
Explanation:
Answer:
It will store an int (Integer) into the variable.
Explanation:
Edg 2021
what is the power of the laser beam as it emerges from the filter
Answers
The power of the laser beam as it emerges from the filter depends on the specific characteristics and specifications of the filter used.
Filters are commonly used in laser systems to control and manipulate the properties of laser beams. They can be designed to modify various parameters such as wavelength, intensity, polarization, and beam profile. The power of the laser beam after passing through a filter will depend on the filter's transmission efficiency and any attenuation or loss introduced by the filter.
Filters can be designed to transmit a certain percentage of the incident laser power while blocking or attenuating other wavelengths or intensities. The power of the laser beam emerging from the filter will typically be reduced due to the losses introduced by the filter. The amount of power reduction will vary depending on the specific characteristics of the filter, such as its material, design, and specifications.
To determine the power of the laser beam after passing through a filter, it is necessary to consider the filter's transmission characteristics and any associated losses. Manufacturers typically provide specifications or performance curves that describe the filter's transmission efficiency and power attenuation. By referring to these specifications and considering the incident laser power, one can calculate or estimate the power of the laser beam as it emerges from the filter.
Learn more about laser beam here:
https://brainly.com/question/28807052
#SPJ11
You then explain that the most critical aspect of password security is _______ people use their passwords
Answers
The most critical aspect of password security is how people use their passwords.
To maintain a high level of password security, it's essential to follow these guidelines:
1. Create strong passwords: Use a combination of upper and lowercase letters, numbers, and special characters to make it difficult for attackers to guess or crack the password through brute-force methods.
2. Use unique passwords for each account: Avoid using the same password across multiple platforms, as a breach in one account can lead to compromised access to other accounts.
3. Update passwords regularly: Change your passwords periodically to minimize the risk of unauthorized access due to stolen or guessed passwords.
4. Do not share passwords: Sharing your password with others, even with close friends or family, increases the chances of unauthorized access and compromises security.
5. Enable multi-factor authentication (MFA): MFA adds an extra layer of protection by requiring additional verification, such as a fingerprint, security token, or one-time code, along with the password for accessing an account.
6. Avoid storing passwords insecurely: Writing passwords down or saving them in unprotected files can expose them to potential attackers.
7. Be cautious with password recovery options: Use secure email addresses and alternative recovery methods to ensure that only you can regain access to your account if you forget your password.
By adhering to these best practices, you can significantly improve the security of your passwords and protect your personal information from potential cyber threats.
For more questions on password
https://brainly.com/question/28114889
#SPJ11
The batteries on electric vehicles are recharged using electricity from either a wall socket or dedicated charging unit.
Answers
Answer:
true
Explanation:
A database is an organized collection of ________ related data. group of answer choices logically badly loosely physically
Answers
A database is an organized collection of logically related data. It serves as a structured repository that allows for efficient storage, retrieval, and manipulation of information.
How is a database logically arranged?The logical organization of a database involves designing tables, establishing relationships between them, and defining constraints to ensure data integrity.
The relationships between the tables enable users to access and query the data based on various criteria. By structuring the data logically, databases facilitate effective data management, scalability, and data consistency.
Read more about databases here:
https://brainly.com/question/518894
#SPJ4
Write the removeevens() method, which receives an array of integers as a parameter and returns a new array of integers containing only the odd numbers from the original array. the main program outputs values of the returned array.
hint: if the original array has even numbers, then the new array will be smaller in length than the original array and should have no blank element.
ex: if the array passed to the removeevens() method is [1, 2, 3, 4, 5, 6, 7, 8, 9], then the method returns and the program output is:
[1, 3, 5, 7, 9]
ex: if the array passed to the removeevens() method is [1, 9, 3], then the method returns and the program output is:
[1, 9, 3]
lab: remove all even numbers from an array
labprogram.java l.
1 import java.util.arrays;
2
3 public class labprogram {
4
5 public static int[] removeevens(int [] nums) {
6
7
8 }
9
10 public static void main(string[] args) {
11
12 int [] input {1,2,3,4,5,6,7,8,9};
13 int [] result = removeevens(input);
14
15 // helper method arrays.tostring() converts int[] to a string
16 system.out.println(arrays.tostring(result)); // should print [1, 3, 5, 7, 9]
17 }
18 }
Answers
Answer:
import java.util.*;
import java.util.Arrays;
public class LabProgram
{
// called function
public static int[] removeEvens(int [] nums)
{
// calculates the length of array
int len = nums.length;
int j=0;
// loop to keep count how many odd are there in array
for(int i=0;i<len;i++)
{
// condition for odd
if(nums[i]%2!=0)
{
// keeps count of odd
j++;
}
}
// declaration of array for odd nums
int newarray[] = new int[j];
j = 0;
// loop
for(int i=0;i<len;i++)
{
// condition for odd
if(nums[i]%2!=0)
{
// assigning odd number to new array
newarray[j] = nums[i];
// increment of j
j++;
}
}
// returning new array
return newarray;
}
// main program
public static void main(String[] args)
{
// array declaration
int [] input = {1,2,3,4,5,6,7,8,9};
// calling a function, passing the paramtere
int [] result = removeEvens(input);
//
System.out.println(Arrays.toString(result));
}
}
Explanation: