_____specialized rules, abbreviations, formatting, and symbols that alert users to important information.
Answers
Conventions in the Official Guidelines for Coding and Reporting (OCGR) are specialized rules, abbreviations, formatting, and symbols that alert users to important information.
What regulations apply to official coding?The four collaborating parties produced a set of standards called the Official Guidelines for Coding and Reporting (OGCR) to go along with and supplement the official conventions and guidelines found in the ICD-10-CM and ICD-10-PCS.
What kind of coding convention is this, for instance?The definition of a constant is one of the coding convention examples. Java uses underscore ('_') characters to denote word separations, hence constants should be expressed in capital letters. A static final field in a class is what Java programmers refer to as a constant.
To know more about coding convections visit
brainly.com/question/10585841
#SPJ4
Related Questions
will is the network manager for a large company. he has been tasked with creating a deployment plan to automate installations for 100 computers that need to have windows server 2016 installed. will wants to use wds for the installations. to fully automate the installations, he needs to create an answer file. will does not want to create the answer files with a text editor. what other program can he use to create unattended answer files via a gui interface?
Answers
Will can use Windows System Image Manager (WSIM) to create unattended answer files via a GUI interface instead of a text editor for fully automating installations using WDS.
Windows Deployment Services (WDS) is a tool for deploying Windows operating systems. To fully automate installations, an unattended answer file is required. Answer files can be created manually using a text editor, but this can be time-consuming and error-prone. To create answer files using a graphical user interface, Will can use Windows System Image Manager (WSIM), which is part of the Windows Assessment and Deployment Kit (ADK). WSIM provides a user-friendly interface for creating and editing answer files. This simplifies the process and helps ensure accuracy, resulting in a smoother and more efficient deployment.
Learn more about Windows Deployment Services here.
https://brainly.com/question/29455341
#SPJ11
Please! I need help matching this.
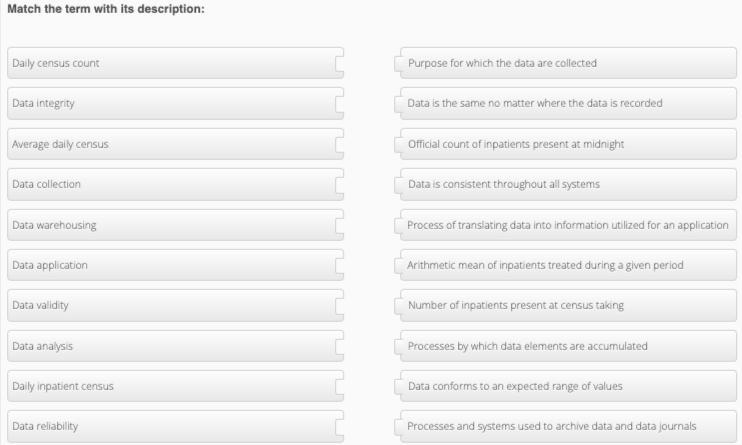
Answers
We can see here that matching the term with its description, we have:
Daily census count: Official count of inpatients present at midnightData integrity: Data conforms to an expected range of valuesAverage daily census: Arithmetic mean of inpatients treated during a given periodData collection: Processes by which data elements are accumulatedData warehousing: Processes and systems used to archive data and data journals.What is data?Data refers to a collection of facts, figures, statistics, measurements, or any other information that can be analyzed or used to gain insights and knowledge about a particular subject or topic. In today's digital age, data can exist in various forms such as text, numbers, images, audio, and video.
Continuation of the matching:
Data application: Process of translating data into information utilized for an applicationData validity: Purpose for which the data are collectedData analysis: Processes by which data elements are accumulatedDaily inpatient census: Number of inpatients present at census takingData reliability: Data is consistent throughout all systems.Learn more about data on https://brainly.com/question/28132995
#SPJ1
In what situations other than developing software might the process of analysis, design, development, test, deployment, and maintenance be a useful approach to problem solving?
Answers
In Systems development or traditional waterfall approach will the process of analysis, design, development, test, deployment, and maintenance be a useful approach.
What is software development?Software development is known to be a term that connote the composition of computer science works made for the process of developing , designing, and aiding software.
Note that In Systems development or traditional waterfall approach will the process of analysis, design, development, test, deployment, and maintenance be a useful approach. as it also uses the dteps listed above.
Learn more about software from
https://brainly.com/question/1538272
#SPJ1
An algorithm is a guiding rule used to solve problems or make decisions. Please select the best answer from the choices provided T F
Answers
True. An algorithm can be defined as a step-by-step procedure or a set of rules designed to solve a specific problem or perform a particular task.
It serves as a guiding rule for problem-solving or decision-making processes. Algorithms are used in various fields, including computer science, mathematics, and even everyday life.
In computer science, algorithms are fundamental to programming and software development. They provide a systematic approach to solving complex problems by breaking them down into smaller, manageable steps.
Algorithms can range from simple and straightforward to highly complex, depending on the nature of the problem they aim to solve.
The importance of algorithms lies in their ability to provide a structured and efficient solution to a given problem. They help in achieving consistency, accuracy, and reproducibility in decision-making processes. Additionally, algorithms enable automation and optimization, allowing for faster and more reliable problem-solving.
It is essential to acknowledge and respect the originality and intellectual property of others when using algorithms developed by someone else. Proper citation and avoiding plagiarism are crucial to ensure the integrity of one's work and uphold ethical standards.
For more such questions on algorithm,click on
https://brainly.com/question/29927475
#SPJ8
Android OS "AFTER" Beta.
A. Cupcake
B. Candy
C. Cookie
D. Carmel
Answers
Answer:
Android OS "AFTER" Beta is;
A. Cupcake
Explanation:
The Android Beta mobile operating system was released on November 2007 while on the 23rd of September, 2008, the first commercially available version of the Android, Android 1.0 was released
Android 1.0 and 1.1 were not assigned actual code names and the first Android mobile operating system release to be assigned a code name is the Android 1.5 which was code named Cupcake by the project manager
How does a modem communicate with a server in the same continent (without underwater cables)?
Answers
Answer:
A modem is typically used to send digital data over a phone line. The sending modem modulates the data into a signal that is compatible with the phone line, and the receiving modem demodulates the signal back into digital data. Wireless modems convert digital data into radio signals and back.
PLS HELP!!
In two to three paragraphs, come up with a way that you could incorporate the most technologically advanced gaming into your online education.
Make sure that your paper details clearly the type of game, how it will work, and how the student will progress through the action. Also include how the school or teacher will devise a grading system and the learning objectives of the game. Submit two to three paragraphs.
Answers
Incorporating cutting-edge gaming technology into web-based learning can foster an interactive and stimulating educational encounter. A clever method of attaining this goal is to incorporate immersive virtual reality (VR) games that are in sync with the topic being taught
What is the gaming about?Tech gaming can enhance online learning by engaging learners interactively. One way to do this is by using immersive VR games that relate to the subject being taught. In a history class, students can time-travel virtually to navigate events and interact with figures.
In this VR game, students complete quests using historical knowledge and critical thinking skills. They may solve historical artifact puzzles or make impactful decisions. Tasks reinforce learning objectives: cause/effect, primary sources, historical context.
Learn more about gaming from
https://brainly.com/question/28031867
#SPJ1
what are the 4 types of satellite?
Answers
Remote Sensing Satellite.
Drone Satellite.
Ground Satellite.
Accessibility is the degree to which a product or service is readily available and usable by _____.
A - as many people as possible
B - anyone who is disabled
C - anyone who is disabled
D - employees
Answers
Answer:
A-As many people as possible
Help me plzzzz ASAP T-T and it's Cyber Security but my last day of school is tomorrow and I'll graduate in June 24 so plzzzzz I really need correct answer ASAP
What kinds of people do you think are susceptible to being duped by "phishing" attacks?
Answers
Answer:
Find answers below.
Explanation:
Social engineering can be defined as an art of manipulating people, especially the vulnerable to divulge confidential information or performing actions that compromises their security.
Basically, it is a manipulative strategy or technique that involves the use of deceptive and malicious activities on unsuspecting victims in order to gain unauthorized access to their confidential or private information for fraud-related purposes. Some examples of social engineering attacks include quid pro quo, spear phishing, baiting, tailgating, water-holing, vishing, pretexting, phishing, etc.
Phishing is simply a form of cyber attack which typically involves making an attempt to obtain sensitive user informations such as usernames, passwords and credit card details or bank account details by disguising one's self as a trustworthy entity in an electronic communication usually over the internet.
Generally, the type of people who are susceptible to being duped by "phishing" attacks are those who post or share their email address or contact informations on public forums and don't scrutinize and examine a message before acting on it.
In conclusion, phishing is a type of fraudulent or social engineering attack used to lure unsuspecting individuals to click on a link that looks like that of a genuine website and then taken to a fraudulent web site which asks for personal information.
Answer:
what do you look like?
Which object is a storage container that contains data in rows and columns and is the primary element of Access databases? procedures queries forms tables
Answers
Answer:
tables
Explanation:
For accessing the database there are four objects namely tables, queries, forms, and reports.
As the name suggests, the table is treated as an object in which the data is stored in a row and column format plus is the main element for accessing the database
Therefore in the given case, the last option is correct
Answer:
D. tables
Explanation:
took the test, theyre right too
If you have an IPv6 address, such as: fd09:a890:0cd3:de45:0000:0000:0000:0005 What are the two correct short forms of this IP address
Answers
The two correct short forms of the given IPv6 address are
fd09:a890:cd3:de45::5 and fd09:a890:cd3:de45:0:0:0:5.
IPv6 addresses may be simplified by omitting leading zeros and compressing the address to the shortest possible representation using "::" (two colons) only once, then omitting leading zeros within the omitted section.
Two colons (": :") are placed in place of a long series of zeros. For instance:fd09:a890:0cd3:de45:0000:0000:0000:0005 => fd09:a890:cd3:de45::5Thus, the two correct short forms of the given IPv6 address are:fd09:a890:cd3:de45::5fd09:a890:cd3:de45:0:0:0:5
To know more about colons refer to:
https://brainly.com/question/30508604
#SPJ11
What is a feature of readable code?
A) The code is interesting to read.
B) The code uses meaningful names for variables, procedures, and classes.
C) The code is all aligned to the left margin.
D) The code is as compact as possible to save space.
Answers
Answer:
C) The code is all aligned to the left margin.
Explanation:
source intends to use any one of the following two strategies, to transmit independent and equiprobable BITS B
1
,B
2
∈{−1,1} over an INDEPENDENT GAUSSIAN NOISE CHANNEL; Treat the BITS as BERNOULLI 1/2 random variables and V
i
:i∈{1,2} as zero mean INDEPENDENT Gaussian r.vs with variance σ
2
. Assuming (Single BIT per channel use): Y
1
=B
1
+V
1
Y
2
=B
2
+V
2
Devise a suitable Inferencing rule For detecting bits B
1
and B
2
, when Measurements at the receiver's side are available as Y
1
=y
1
and Y
2
=y
2
Determine the Prob(ERROR). \begin{tabular}{|l|} \hline Assuming (WITH PRE-CODING): \\ Y
1
=B
1
+B
2
+V
1
\\ Y
2
=B
1
−B
2
+V
2
\end{tabular} Compare the Prob(ERROR) in both cases and comment!!
Answers
For the independent and equiprobable BITS B1 and B2, the optimal inference rule is to compare Y1 and Y2 to determine B1 and B2. The probability of error depends on the noise variance.
In the first case without pre-coding, the inference rule is to compare Y1 and Y2 individually with a threshold of zero. If Y1 > 0, then B1 = 1; otherwise, B1 = -1. Similarly, if Y2 > 0, then B2 = 1; otherwise, B2 = -1. The probability of error can be calculated based on the error probability of individual Gaussian variables.In the second case with pre-coding, the inference rule involves adding Y1 and Y2. If Y1 + Y2 > 0, then B1 = 1; otherwise, B1 = -1. The inference for B2 depends on the subtraction Y1 - Y2. If Y1 - Y2 > 0, then B2 = 1; otherwise, B2 = -1. The probability of error in this case can also be determined based on the error probability of Gaussian variables.Comparing the probabilities of error in both cases would require specific values for the noise variance (σ^2) and a comparison of the error probabilities calculated based on those values.
To know more about noise click the link below:
brainly.com/question/29991623
#SPJ11
Which Annotation tool provides the ability to convert the mouse icon when giving a presentation to better focus the audience attention?
1. Arrow
2. Ink Color
3. Eraser
4. Laser Pointer
Answers
solve the following equations and check your result 1) 3x=2x+18
Answers
Answer:
x = 18
Explanation:
3x = 2x+18
3x-2x = 18
x=18
Answer:
Explanation:
3X-2X=2X-2X+18
X=18
u.s. copyright law doesn’t apply internationally group of answer choices true false
Answers
False u.s. copyright law doesn’t apply internationally group of answer choices
While the U.S. Copyright Law is primarily enforced within the United States, it still has some international reach through treaties and agreements such as the Berne Convention and the World Intellectual Property Organization (WIPO) Copyright Treaty. These agreements provide some level of protection for U.S. copyrighted works in other countries and allow for legal action to be taken against infringement in certain situations.
The U.S. Copyright Law is a set of federal laws that provide protection to original works of authorship, including literary, dramatic, musical, and artistic works. It grants exclusive rights to the creator of the work, such as the right to reproduce, distribute, and perform the work. However, the extent to which these rights apply internationally is often a question of legal interpretation and application .While it is true that the U.S. Copyright Law is primarily enforced within the United States, it does have some international reach through treaties and agreements. One of the most important of these is the Berne Convention for the Protection of Literary and Artistic Works, which is an international agreement that establishes minimum standards for copyright protection among its member countries. The United States has been a member of the Berne Convention since 1989, and as such, U.S. copyrighted works are protected in other countries that are also members of the convention. Additionally, the World Intellectual Property Organization (WIPO) Copyright Treaty is another international agreement that the U.S. has signed. This treaty provides additional protection for copyrighted works in the digital age, specifically addressing issues related to the distribution and transmission of copyrighted materials online. However, it is important to note that the level of protection provided by these treaties and agreements can vary depending on the specific circumstances and the laws of the country where the infringement occurs. In some cases, it may be necessary to pursue legal action in the country where the infringement occurred in order to enforce U.S. copyright law.
To know more about copyright law visit:
https://brainly.com/question/22089522
#SPJ11
What is the definition of a Robot????
Answers
Answer:
Please look below for your answer
Explanation:
A robot simply refers to a machine—especially one programmable by a computer— capable of carrying out a complex series of actions automatically. Robots can be guided by an external control device or the control may be embedded within. Robots may be constructed on the lines of human form, but most robots are machines designed to perform a task with no regard to their aesthetics.
hope I really helped you
Please mark me as brainliest
Corinne would like to click on the link at the bottom of a Web page but she only sees the top portion of the page. She should _____. A.click twice on the status bar
B.use the scroll bar to scroll down to the bottom of the page
C.click on the back button
D.click on the display window and drag it up
Answers
Answer:
B
Explanation:
from 3dg3
Answer:
D.click on the display window and drag it up
What is the name of the item that supplies the exact or near exact voltage at the required wattage to all of the circuitry inside your computer?
Answers
Answer:
It's the power supply
Explanation:
The power supply is what essentially enables the computer to operate. It is able to do that by converting the incoming alternating current (AC) to direct current (DC) at the correct wattage rating that is required by the computer to function. The power supply is a metal box that is generally placed in the corner of the case.
based on current data, planetary systems appear to be
Answers
Planetary systems appear to be prevalent in the universe based on current data. The discovery of exoplanets has greatly contributed to the understanding of planetary systems.
According to NASA, as of May 2021, there were over 4,000 confirmed exoplanets. In addition, there were over 6,000 candidate planets that were awaiting confirmation. The discovery of these exoplanets has provided scientists with a deeper understanding of planetary systems.
The Kepler mission, launched by NASA in 2009, played a significant role in exoplanet discovery. It utilized the transit method to detect planets orbiting distant stars. This method measures a decrease in starlight as a planet transits, or passes in front of, the star. The duration and frequency of the transit can provide information about the planet’s size and orbital period.
As technology advances and data collection improves, more planetary systems are expected to be discovered. Planetary systems appear to be prevalent in the universe based on current data. The discovery of exoplanets has greatly contributed to the understanding of planetary systems.
Know more about the Planetary systems
https://brainly.com/question/33336009
#SPJ11
Jhon bought a new printer for his desktop computer. It does not work even though he checked all the cables and cords. What do you think he forgot to connect? *
A. The installer
B. The ports and plugs
C. The Device Driver
D. The Utility Software

Answers
Select the correct answer from each drop-down menu.
Which of the options is an empty element?
(1.a, 2. input, 3.p) is an empty element. It does not have a(n) (a. starting tag, b. ending tag, c. attribute)
Answers
Answer:
The correct answer is option 3. The p element is an empty element, which means it does not have a closing tag. It does not have an attribute, but it does have a starting tag.
Answer:
2. Input - B. Closing Tag
Explanation:
According to the HTML5 specification, there are 15 empty tags, these are also known as self-closing or void tags because they do not have a corresponding closing tag and they cannot contain other elements. <br>, <hr>, <img>, <input>, <link>, and <meta>.
Developers and customers create use-cases to help the software team understand how different classes of end-users will use the software functionality. True False
Answers
The statement "Developers and customers create use-cases to help the software team understand how different classes of end-users will use the software functionality" is TRUE.
What is a use case?A use case is a methodology used in software design and systems engineering to describe the functional requirements of a system or business process. It can also be referred to as a scenario. In other words, a use case is a document that describes the various actions that a user performs while interacting with a system to accomplish a specific objective.
Each use case is usually represented by a sequence of basic interactions between the user and the system, which can help developers, testers, and stakeholders understand how the software system is supposed to function.
The use case approach is one of the most popular methods for requirements gathering and analysis because it provides a clear and unambiguous way of describing system behavior.
Learn more about software development at:
https://brainly.com/question/12946670
#SPJ11
power supply, keyboard, monitor, mouse,ROM,CPU are belongs to Output, Input or Storage device
Answers
Answer:
Keyboard :Input
Monitor: Output
Mouse:Input
ROM:Storage
CPU: Processing device
On the following page, write a static method print Short Words that accepts two parameters:_____.
a. a String str containing a list of words (separated by spaces), and an integer maxLength .
b. This method should print out the words in str whose lengths are at most maxLength.
c. You can assume there will always be a space after the last word in the string.
Answers
Methods in Java are collections of program statements that are named, and executed when called/invoked
The printShortWords method in Java where comments are used to explain each line is as follows:
//This defines the static method
public static void printShortWords(String str, int maxLength){
//This iterates through each word in the string
for(String word: str.split(" ")){
//The compares the length of each word to maxLength
if(word.length()<=maxLength){
//If the length of the current word is atleast maxLength, the word is printed
System.out.print(word+" ");
}
}
}
Read more about static methods at:
https://brainly.com/question/19360941
2) Some graphics have usage restrictions on them. What are some copyright laws out there that affect usage of images, graphics, and photos?
(I don’t really understand what they’re asking, any help is appreciated!)
Answers
Explanation:
Ok what is Copyright The copy of something without using credit
Write any 2 differences between implicit variables and explicit variables.Plz tell :' (
Answers
Implicit is implied
Explicit leaves no room for confusion
Implicit doesn’t have to be directly stated
What is the key sequence to copy the first 4 lines and paste it at the end of the file?
Answers
Press Ctrl+C after selecting the text you want to copy. Press Ctrl+V while holding down the cursor to paste the copied text.
What comes first in the copy and paste process for a slide?Select the slide you wish to copy from the thumbnail pane, then hit Ctrl+C on your keyboard. Move to the location in the thumbnail pane where you wish to paste the slide, then hit Ctrl+P on your keyboard.
What comes first in the copying process of a segment?The secret to copying a line segment is to open your compass to that segment's length, then mark off another segment of that length using that amount of opening.
To know more about copy visit:-
https://brainly.com/question/24297734
#SPJ4
____ is a technology that exists inside another device
Answers
Answer:
Embedded technology is a technology that exists inside another device.
Answer:
Embedded
Explanation:
An embedded system is a combination of computer hardware and software designed for a specific function.