Software and Hardware are the main two components of a computer
Answers
Related Questions
When an attack is designed to prevent authorized users from accessing a system, it is called what kind of attack
Answers
Answer:
a "denial of service" attack
Explanation:
If the point of the attack is to prevent the system from providing the service it is intended to provide, the attack is called a "denial of service" attack.
\(\huge\bf\underline{\underline{\pink{A}\orange{N}\blue{S}\green{W}\red{E}\purple{R:-}}}\)
When an attack is designed to prevent authorised users from accessing a system, it is called Denial of service attack.These type of attack is especially used to keep data or access of authorised users safe from hackers. Hackers try to loot the important data and software from the accessing system which stores all the information. To prevent this illegal crime Denial of service attack is used.
Which is true regarding diagramming? It involves writing an algorithm. It presents the programming code. It shows the flow of information and processes to solve the problem. It models solutions for large problems only.
Answers
Answer:
It shows the flow of information and processes to solve the problem.
Explanation:
Answer:
C
Explanation:
Got it right on Edge 2021:)
Your welcome
A Trojan is a malicious program that uses a computer network to replicate.
a. True
b. False
Answers
False. A Trojan is a type of malware that fools users into downloading and installing it on their computers by disguising itself as a trustworthy software or file. A Trojan may carry out a range of destructive actionn.
Is a Trojan a malicious application that spreads itself across a computer network?Trojan horses are spoofs, or malicious software that pose as something pleasant but are actually malicious. The fact that Trojan horse programmes do not replicate themselves makes them extremely different from real viruses. Trojans include malicious code that, when activated, results in data loss or even theft.
What do computer Trojans do?Malware that poses as trustworthy programmes or software is known as a Trojan Horse (Trojan). Attackers enter the network once inside.
To know more about malware visit:-
https://brainly.com/question/14276107
#SPJ1
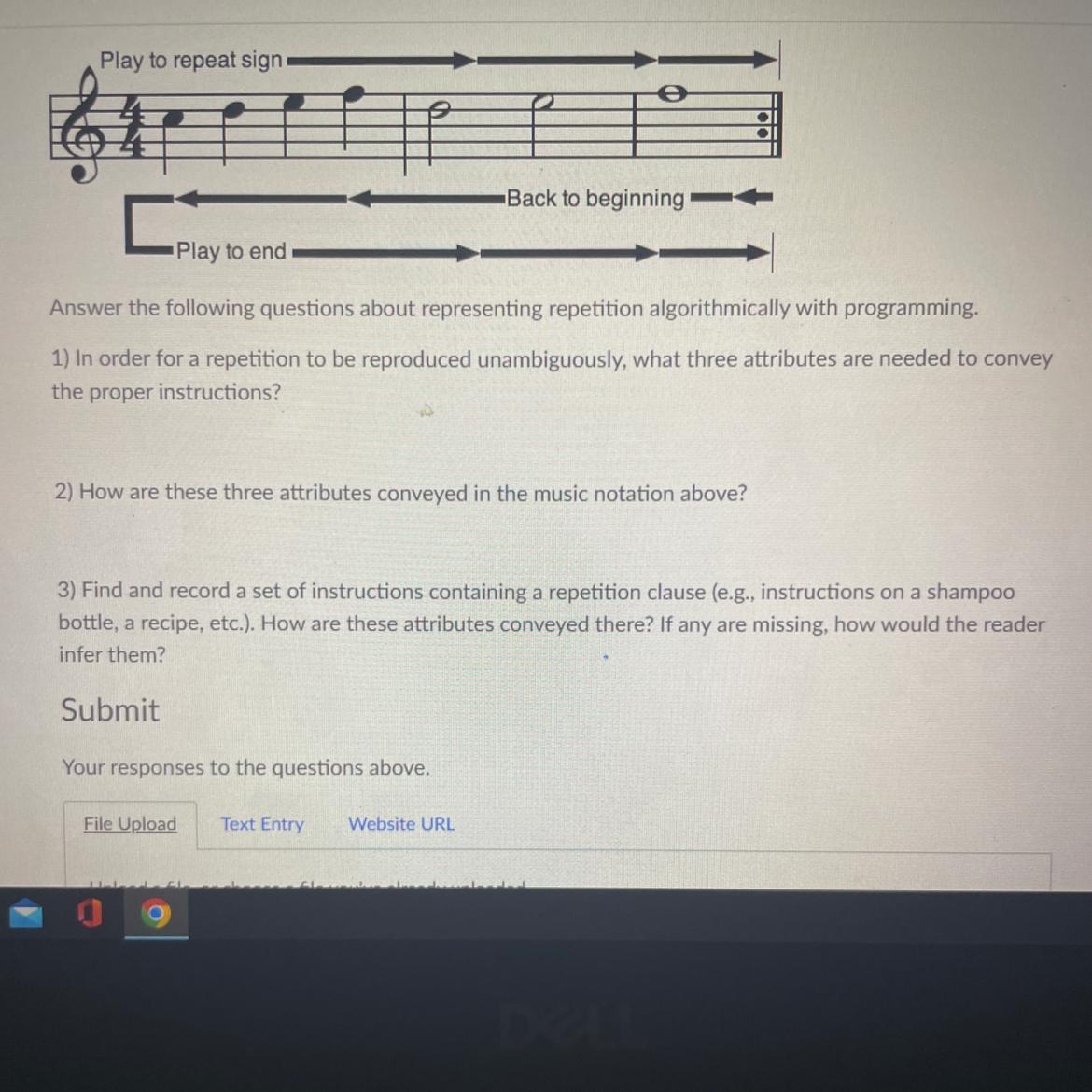
Play to end-
Back to beginning
Answer the following questions about representing repetition algorithmically with programming
1) In order for a repetition to be reproduced unambiguously, what three attributes are needed to convey
the proper instructions?
2) How are these three attributes conveyed in the music notation above?
3) Find and record a set of instructions containing a repetition clause (eg, instructions on a shampoo
bottle, a recipe, etc.). How are these attributes conveyed there? If any are missing, how would the reader
infer them?
Answers
There must be a starting point, a point where the code ends, and it restarts back to the beginning.
2) How are these three attributes conveyed in the music notation above?
The starting point is the beginning of the phrase, the point of where it gets sent back is the is represented by the colon symbol at the end, and thus it starts again at the beginning of the phrase.
3) Find and record a set of instructions containing a repetition clause (e.g., instructions on a shampoo bottle, a recipe, etc.). How are these attributes conveyed there? If any are missing, how would the reader infer them?
How to download the McDelivery app from a McDonalds bag
- Download the uber eats app
- Select “McDonald’s”
- Order your favorite foods
In this set of instructions, it has a start where you download or open up the uber eats app, selecting the “McDonalds” option for delivery is part of the start or the middle part, and the point of repetition where the instructions can be a repeated is the ordering the food. It would’ve just been in a constant loop afterwards because the first two instructions have already been pre-completed.
hope this helps :)
Ava and Elizabeth are planning on using an IDE to create their program. Describe tools and facilities available in the IDE which can help them to identify and correct syntax errors.
Answers
if the wide area network (wan) is supporting converged applications like voice over internet protocol (voip), which of the following becomes even more essential to the assurance of the network? a. boundary routing b. classless inter-domain routing (cidr) c. internet protocol (ip) routing lookups d. deterministic routing
Answers
if the wide area network (wan) is supporting converged applications like voice over internet protocol (voip) internet protocol (ip) routing lookups will be even more essential to the assurance of the network.
Understanding WAN
WAN stands for Wide Area Network is a network that is used as a network that connects between local networks. Local computer networks are not only physically adjacent to each other, but share the same group of IP addresses.
The local network can be one room, one office or even one city. While the WAN itself is a network that connects these local networks within a city, province or even between countries. The difference between WAN and LAN networks is in the type of media used. Generally local networks or LANs use similar network media.
While the WAN is connected to devices with different transmission media and protocols. The WAN coverage area is also very wide, but unites the network as if it were in one room. WAN networks have lower data transfer rates than local networks or LANs. WAN network technology relies on companies providing long-distance telecommunications services. WAN networks use many kinds of network technologies with a mix of analog and digital signals for data transmission. Of course this is different from a local network or LAN which uses a connection between computers that are physically connected to each other with the same protocol and transmission media. The components in the WAN and their functions will be discussed later.
Learn more about WAN at https://brainly.com/question/14793460.
#SPJ4.
What are the differences and similarities between a local area network (LAN) and a wide area network (WAN)?
As the different network types have evolved, careers in the Network Systems pathway have changed over time. Discuss an example of how network system careers have changed and how those changes have impacted society.
What is an Internet Service Provider? Describe at least two types of ISP connections.
Explain two ways that you can stay safe while working in the Network Systems career pathway.
There are many different careers available within the Network Systems career pathway, but they all have some similar characteristics. What are two of these characteristics?
Answers
Local Area Networks (LANs) and Wide Area Networks (WANs) differ in terms of scope, ownership, speed, cost, and security. LANs cover a smaller area, are privately owned, offer higher speeds and greater bandwidth, are cost-effective, and have more control over security.
The differences and similarities between a local area network (LAN) and a wide area network (WAN)?On the other hand, WANs span larger distances, involve multiple organizations, may have slower speeds and limited bandwidth, require more infrastructure and connectivity options, and carry higher security risks.
Network system careers have evolved with the rise of cloud computing and virtualization, shifting from traditional networking to managing virtual networks and cloud platforms. This change has enabled more flexible and scalable IT infrastructure, facilitated remote work and collaboration, and promoted the growth of cloud-based services, impacting society positively.
An Internet Service Provider (ISP) is a company that provides internet access. DSL utilizes telephone lines for connectivity, while cable internet uses coaxial cable TV infrastructure. Staying safe in the Network Systems career pathway involves implementing security measures like strong passwords and regular updates, as well as staying informed and educated about security threats and industry trends.
Characteristics of Network Systems careers include technical expertise in areas such as network protocols and troubleshooting, as well as the need for continuous learning and adaptability to keep up with evolving technologies and industry standards.
Read more on WLAN here https://brainly.com/question/27975067
#SPJ1
Why do
ve need to add movies in our slide?
Answers
Answer:
movies are awesome! LOL but i dont understand your question...sadly.
Explanation:
true or false - an organization can improve its security defenses without even having to go through a security assessment
Answers
True an organization can improve its security defences without even having to go through a security assessment.
What do security assessment entail?
An information system's or organization's security needs are being met through testing or evaluating security measures to see how well they are being implemented, functioning as intended, and providing the desired results.
What does a security assessment serve?
Important security safeguards in applications are found, evaluated, and put into place by a security risk assessment. Additionally, it emphasizes avoiding application security flaws and vulnerabilities. An enterprise can see the management approach holistically—from the viewpoint of an attacker—by conducting a risk analysis.
To know more about security assessment visit:
https://brainly.com/question/14784003
#SPJ4
Dawn is creating a photo calendar on her computer. Before she steps away from her computer to eat lunch, where should Dawn save her photos so she can come back and
continue working on the calendar?
O EEPROM
O Hard drive
O RAM
O ROM
Answers
Answer:
Hard drive
Explanation:
Dawn needs to save her photos on a storage device where she can easily retrieve her saved files after she finishes having her lunch.
From the list of given options, the option that answers the question is (b) the hard drive as it can be used as a medium to retain permanent data.
As for other options
(d) ROM can not be used as a direct storage device
(a) EEPROM is a type of ROM and
(c) RAM can not be used as a medium to store permanent data.
Answer:
hard drive
Explanation:
got 100
Which unknown factor affects prices in the financial markets?
Income taxes
Media speculation
Government policy
Trade regulations
Answers
Answer:
There are four major factors that cause both long-term trends and short-term fluctuations. These factors are government, international transactions, speculation and expectation and supply and demand.
Explanation:
Ayy so in your opinion what is they best XXL freestyle no wrong answers except for Coi Leray and YK Osiris, my personally favorite is Denzel Curry's.
Answers
At which track meet did two runners finish in a time equivalent to the mode?
Answers
Answer:
1
Explanation:
edge
Answer:
3
Runner B
Runner C
5:30.5
Explanation:
After teaching a group of students about the indications for use for aminoglycosides, the instructor determines that the teaching was successful when the students identify which type of infection as a primary indication
Answers
It is also essential that you do not drink milk within two hours (either before or after) of carrying tetracycline. This is because both food and milk can reduce the amount of medicine absorbed by your body, making it less useful in fighting infection. The tablets can cause throat tingle
What are the 4 types of infections?
The four different classifications of infectious agents are bacteria, viruses, fungi, and parasites. When studying these agents, researchers separate them using certain characteristics: Size of the spreading agent
What is disease and its types?
Infection happens when germs enter your body and multiply, resulting in disease. The four main kinds of infections are viral, bacterial, fungal, and parasitic.
To learn more about Infection, refer
https://brainly.com/question/25258835
#SPJ4
Vincent has enrolled in a web development degree in college. But he also wants to learn a few extra tools and programming languages. Which course of action can help him?
Answers
Answer:
Apply for online course or programming bootcamps.
Explanation:
As a beginner in web development, it is essential to expand your sources of information, college courses for web development would introduce various new tools and programming concepts. Gathering information and learning other web based tools would ease the learning process.
help pls I will mark brainliest the top answer i need it rn
Nonsense = REPORT
Answer the question 3-5 sentences.
"Why is recycling very important and beneficial to you and your community?"

Answers
Answer:
to reduce outbreak of diseases
Explanation:
materials recycled, funds earned from it are used developmental projects in my community
A team of architects is designing a new AWS environment for a company which wants to migrate to the Cloud. The architects are considering the use of EC2 instances with instance store volumes. The architects realize that the data on the instance store volumes are ephemeral. Which action will not cause the data to be deleted on an instance store volume
Answers
Answer:reboot
Explanation:
Why would you use the Annotation Tool available in Power BI for Mobile with a report you want to share
Answers
The Annotation Tool available in Power BI is a valuable feature that can help to enhance the usefulness and accessibility of reports when sharing them with others, especially on mobile devices.
The Annotation Tool available in Power BI for Mobile with a report you want to share is a powerful feature that allows you to add comments and notes directly on a report. This is particularly useful when sharing a report with colleagues or clients, as it enables you to provide context and insights into the data being presented.
By using the Annotation Tool, you can highlight specific data points, explain trends or patterns, and provide additional information that may not be immediately apparent from the report itself. This helps to ensure that everyone who views the report understands the key takeaways and can make informed decisions based on the data.
In addition, the Annotation Tool is especially helpful for mobile users, who may be accessing the report on a smaller screen or on-the-go. By adding annotations, you can ensure that even when viewing the report on a mobile device, the viewer can easily understand the key points and insights.
To learn more about Power BI Here:
https://brainly.com/question/30456037
#SPJ11
Accessing cash from some customers' accounts at the ATM during
weekends:
Answers
Answer:
what kinda question is this? i dont see a question i would try to help if i understand.
Explanation:
Design using trnsys any HVAC system, please state the
parameters and connections with snaps
Answers
I have designed an HVAC system using TRNSYS, incorporating parameters such as heat load, equipment specifications, and control strategies. The system's connections are illustrated with accompanying snaps.
In response to your request, I have utilized TRNSYS (Transient System Simulation Tool) to design an HVAC (Heating, Ventilation, and Air Conditioning) system. TRNSYS is a widely used software for simulating energy systems and their components.
The HVAC system design involves several key parameters to ensure efficient and effective operation. Firstly, the heat load of the space or building is calculated, taking into account factors such as occupancy, insulation, and climate conditions. This information serves as the basis for determining the required heating and cooling capacities of the system.
Secondly, equipment specifications are considered. This includes selecting appropriate components such as boilers, chillers, heat pumps, air handlers, and ductwork. Each equipment type has specific characteristics and efficiencies that must be taken into account during the design process.
Lastly, control strategies play a crucial role in HVAC system performance. By implementing advanced control algorithms, it is possible to optimize energy consumption and maintain comfortable indoor conditions. These strategies may involve temperature and humidity sensors, occupancy detectors, and feedback loops to adjust the operation of the HVAC equipment in real-time.
To provide a more comprehensive explanation, it would be helpful to illustrate the connections and configurations of the designed HVAC system using accompanying snapshots. These visuals would showcase the arrangement of the equipment, the flow of air or fluids, and the control interfaces, enabling a better understanding of the system's overall design.
Learn more about HVAC
brainly.com/question/32679929
#SPJ11
The newest model of a car features technology that scans the surrounding environment and projects information through an interface on the windshield, which the driver can then interact with. which type of technology would this be an example of
Answers
One such technology exists as Augmented Reality (AR) which shows the capacity to provide drivers with a variety of details in an unobtrusive way.
What does augmented reality AR functions as?
Augmented reality (AR) exists and is comprehended to be a period that connotes the action of overlaying any condition of visual, auditory, or other types of sensory information onto a variety of world that exists created to boast one's experience.
As augmented reality apps exist even unique to the mass market, it exists too early to describe how really distinct these development kits exist, but that they exist each distinct to their own operating systems and core audiences.
Now that the two most famous tech firms between them controlling 99% of the smartphone market contain made such a general move behind the augmented fact, we should be prepared to see industries existing disrupted again.
To learn more about Augmented Reality (AR) refer to:
brainly.com/question/9054673
#SPJ4
which command should you use in conjunction with the ssh-agent bash command? (enter the command and options as if you are at the command prompt.)
Answers
To add private keys, you must use the ssh-add command in conjunction with the ssh-agent bash command.
To establish the ssh-agent, the command ssh-add has to be used in conjunction with the ssh-agent bash command.Explanation:When a user employs SSH to connect to a remote server, the SSH agent facilitates key-based authentication. The ssh-agent daemon is employed to do this. The ssh-agent acts as a mediator between the client machine and the remote server, and it saves keys in memory for the duration of a user's session. You can add private keys to the ssh-agent using the ssh-add command. However, before you can utilize the ssh-add command, you must first start the ssh-agent daemon.To begin the ssh-agent daemon, you may use the following command in conjunction with ssh-agent bash: eval $(ssh-agent)\
For instance, when this command is issued, the ssh-agent daemon will begin to run, and you can use ssh-add to add private keys. After you've finished, you can terminate the ssh-agent daemon by using the ssh-agent -k command.
To know more about private keys visit:
https://brainly.com/question/30410707
#SPJ11
Describe a situation in which you would want to use integer division in a program. Then, write the line of code that would use integer division.
Answers
The description of a situation in which you would want to use integer division in a program is that they would give you the exact answer you want when performing addition, division, etc, and is more reliable than using floating point math.
What is Integer Division?This refers to the term that is used to describe the operator divides two numbers and returns a result and its symbol is %
The Program that uses an integer division is given below:
int a = 25;
int b = 5;
int c = a / b ;
System. out. println(c);
Read more about integer division here:
https://brainly.com/question/28487752
#SPJ1
Who is the CEO of Epic Games?
Answers
Answer:
it's tim sweeney....
Explanation:
hope it helps
Answer:
Tim Sweeney
Explanation:
The acronym PCl stands for programmable component interface. Hint: if you cannot find the answer in the chapter, please search the Web. True False Question 2 IDE bus stands for Integrated Drive Electronics Hint: if you cannot find the answer in in the chapter, please search the Web. True False in the ×86 architecture, the EAX register is a register. 64 bit 16 bit 8 bit 32 bit Question 4 Static RAM is usually less expensive than Dynamic RAM. True False
Answers
The acronym PCl stands for programmable component interface is false. PCI stands for Peripheral Component Interconnect is a computer bus and expansion card standard that was developed by Intel Corporation.
It was first introduced in 1992 and has since become the primary expansion bus for PCs. IDE bus stands for Integrated Drive Electronics is true. IDE stands for Integrated Drive Electronics. IDE is a type of hardware interface used to connect hard drives, CD-ROM drives, and other devices inside a computer. IDE, also known as ATA (short for AT Attachment), was first introduced in 1986 and was the standard interface used for connecting hard drives to computers for many years.
The EAX register is a 32-bit register in the ×86 architecture. Hence, the correct option is 32 bit.Static RAM is usually more expensive than Dynamic RAM is false. Static RAM (SRAM) is more expensive and less dense than DRAM, but it is also much faster and requires less power.
Hence, the statement is false.
To know more about programmable visit:
https://brainly.com/question/30345666
#SPJ11
What should I watch on Netflix (shows for a 14 year old) ?
Answers
Answer:
The flash
Explanation:
Answer:
Im not a big horse fan but loved this show its called free rein
Explanation:
loved itttttt!
Complete the Statement below :)
The keys to successful outsourcing are accountability, reporting, and [BLANK]
Answers
Answer:
The keys to successful outsourcing are accountability, reporting, and planning.
Explanation:
You need to plan in order to successfully outsource a market. I hope this helps, I am sorry if I am wrong.
this is meant to reduce the carbon dioxide or greenhouse gasses produced when we travel? a. carbon offset b. carbon copies c. carbon computers d. carbon counters
Answers
Carbon offset is meant to reduce the carbon dioxide or greenhouse gases produced when we travel, hence correct option is "a". Carbon offsets are a form of trade, where you can purchase credits to compensate for the greenhouse gas emissions created during travel. This is done by investing in projects that reduce carbon dioxide emissions, such as renewable energy or reforestation initiatives.
A greenhouse gas (GHG or GhG) is a gas that absorbs and emits radiant energy at thermal infrared wavelengths, causing the greenhouse effect. The primary greenhouse gases in Earth's atmosphere are water vapor (H2O), carbon dioxide (CO2), methane (CH4), nitrous oxide (N2O), and ozone (O3). Without greenhouse gases, the average temperature of Earth's surface would be about −18 °C (0 °F),[2] rather than the present average of 15 °C (59 °F).[3][4][5] Greenhouse gases exist in many atmospheres, creating greenhouse effects on Mars, Titan and particularly in the thick atmosphere of Venus.
To learn more about "Greenhouse gas" visit: https://brainly.com/question/12684997
#SPJ11
Even closed systems are never perfectly closed.
true false
Answers
Answer:
True
Explanation:
You can learn through many different textbooks that a closed system is always closed.
For each example given below, identify and write the type of data out of four choices:
Nominal data, Ordinal data, Interval data, and Ratio data. Mark N, O, I, or R
Salary, Nationality, Grade (A,B,C,D), Temperature
Answers
The type of data for each example is:
Salary: Ratio data (R)
Nationality: Nominal data (N)
Grade (A, B, C, D): Ordinal data (O)
Temperature: Interval data (I)
Salary: Ratio data (R) - Salary is a type of quantitative data that can be measured on a continuous scale. It has a meaningful zero point, allowing for meaningful comparisons and calculations. For example, if one person earns $50,000 and another person earns $100,000, we can say that the second person earns twice as much as the first person.
Nationality: Nominal data (N) - Nationality is a categorical variable that cannot be ranked or quantified. It is a form of qualitative data that represents different categories or groups. For example, someone can be of American, British, or Indian nationality, but we cannot assign a numerical value or order to these categories.
Grade (A, B, C, D): Ordinal data (O) - Grades are categorical variables that have a specific order or ranking. Although the actual difference between grades may not be consistent, we can still rank them from highest to lowest. For example, A is higher than B, B is higher than C, and so on.
Temperature: Interval data (I) - Temperature is a quantitative variable that can be measured on a continuous scale. However, it lacks a meaningful zero point. The interval between temperatures is consistent, but zero degrees does not indicate the absence of temperature. For example, the difference between 20 and 30 degrees Celsius is the same as the difference between 30 and 40 degrees Celsius, but 0 degrees Celsius does not mean "no temperature."
To know more about categorical variable visit:
https://brainly.com/question/32790259
#SPJ11