setting the suid flag is a powerful and useful feature. it can have weaknesses associated with its use. which of the following statements identifies a weakness?
Answers
The weakness of SUID flag that associated with its use is setting the SUID flag for process or application that owned by root user can make security hole.
What is SUID flag?
SUID flag is a set of owner user ID to give permission a bit flag to can be applied and executed. This will give user to execute something with same permission as the owner, or in other word the SUID flag will make the user to have owner permission rather than have the alternate user permission.
Root user is a highest user that have all permission and privileges to read and write all file in Linux or Unix base OS system. This is a special user.
So, make SUID flag for anything that associated to root user can make security hole because the user can access all file in system like root user.
You question is incomplete, but it is a general answer for SUID flag weaknesses.
Learn more about SUID flag here:
brainly.com/question/29744824
#SPJ4
Related Questions
Write a 250-word essay on the benefits and dangers of collecting and storing personal data on online databases. Things to consider:
Does the user know their data is being collected?
Is there encryption built into the system?
Is that encryption sufficient to protect the data involved?
Does collecting the data benefit the end user? Or just the site doing the collecting?
Answers
Answer:
The collection and storage of personal data on online databases has both benefits and dangers. On the one hand, collecting and storing data can be incredibly useful for a variety of purposes, such as personalized recommendations, targeted advertising, and improved user experiences. However, it's important to consider the risks and potential consequences of this practice, particularly in regards to privacy and security.
One concern is whether or not users are aware that their data is being collected. In some cases, this information may be clearly disclosed in a site's terms of service or privacy policy, but in other cases it may not be as transparent. It's important for users to be aware of what data is being collected and how it is being used, so that they can make informed decisions about whether or not to share this information.
Another important factor is the level of encryption built into the system. Encryption is a way of encoding data so that it can only be accessed by authorized parties. If a system has strong encryption, it can help to protect the data involved from being accessed by unauthorized users. However, if the encryption is weak or flawed, it may not be sufficient to protect the data. It's important to carefully consider the strength and reliability of any encryption used on a system that stores personal data.
Ultimately, the benefits and dangers of collecting and storing personal data on online databases will depend on the specific context and how the data is being used. It's important to weigh the potential benefits and risks, and to carefully consider whether the collection and storage of this data is truly in the best interests of the end user, or if it is primarily benefiting the site doing the collecting.
Explanation:
What type of input and output devices would be ideal for a college student completing his or her coursework?
Answers
Ideal input and output devices for a college student's coursework include input devices: laptop, keyboard, mouse and output devices: monitor, printer, headphones, and stylus.
We have,
Ideal input and output devices for a college student completing coursework would include:
Input Devices:
Laptop or Computer: A primary tool for typing assignments, research, and accessing online resources.
Keyboard: Allows efficient typing for creating documents, emails, and notes.
Mouse or Trackpad: Facilitates precise navigation and interaction with software and applications.
Stylus or Digital Pen: Useful for taking handwritten notes and annotating documents on touchscreen devices or tablets.
Scanner or Smartphone Camera: Helps digitize physical documents, book pages, or handwritten notes for easy storage and reference.
Microphone: Useful for recording lectures, participating in online discussions, or creating audio content.
Output Devices:
Monitor or Display: Provides a clear and comfortable visual interface for reading, writing, and viewing multimedia content.
Printer: Enables printing of assignments, readings, and reference materials for offline access.
Headphones or Speakers: Allows listening to audio lectures, videos, and online meetings without disturbing others.
External Monitor: Expands screen space for multitasking, reading, or comparing documents side by side.
Projector: Useful for presentations, group discussions, and sharing content in a classroom setting.
E-book Reader or Tablet: Portable device for reading e-books, digital textbooks, and research materials.
Thus,
Ideal input and output devices for a college student's coursework include a laptop, keyboard, mouse, monitor, printer, headphones, and stylus.
Learn more about input and output devices here:
https://brainly.com/question/1885137
#SPJ3
has anyone use romstation before

Answers
RomStation centralizes your favorite games and emulators in a single program.
What is RomStation?Old Nintendo 64, GameBoy Advance, and Super Nintendo games can be played on a computer using the RomStation programme. It is built on a database of thousands of games, the majority of which appeal to people who miss the 1980s, 1990s, and a little bit of the 2000s.The most recent fresh version of the "romstation.exe" file was found 3697 days ago. The file "romstation.exe" has 4 versions in our database that are finalised as Safe, and 0 variants that are finalised as Threat. Final evaluations are based on file assessments, the discovery date, user frequency, and the outcomes of antivirus scans.RomStation has an easy-to-use interface that makes it possible to emulate a variety of game consoles. GameCube, PS1, Saturn, Dreamcast, N64, PS2, GBA,...Learn more about Games and emulators refer to ;
https://brainly.com/question/28031867
#SPJ1
Complete the sentence.
If you wanted the best performance for a game that requires a powerful graphics processor and lots of memory, you
would run it on a
tablet
desktop
smartphone
Answers
Fill the formula in F15 down to F16:F44
Answers
If you want to fill the formula in F15 down to F16:F44, you must be required to select the cell with the formula and the adjacent cells you want to fill.
How do you Autofill the formula down?Fill the desired formula into adjacent cells by selecting the cell with the formula and the adjacent cells you want to fill. Click Home > Fill, and choose either Down, Right, Up, or Left.
Apart from this, you can use the Keyboard shortcut: by pressing Ctrl+D to fill the formula down in a column, or Ctrl+R to fill the formula to the right in a row. Put the specific function of getting the formula in F15.
To learn more about Formula fill, refer to the link:
https://brainly.com/question/28662997
#SPJ1
Problem 1 a = 4 b = 3 c = 20 while a < c a = a * 2 b = b * 3 Endwhile output a, b, c
Answers
Endwhile output is a = 4, b = 12, c = 20.
What is input and output?
Data must be added to or subtracted from code in all programmes. Inputs are the data that are entered into a programme, whether manually by the programmer or digitally. These inputs are used to run the programme and are saved as variables. A programmer may decide to include outputs to inform the user of what is happening inside the programme. Here, the user is presented with the program's data either visually (on the screen) or physically (as printouts or signals, for example). It's possible that a programme needs to talk to a user. This could be done to display the program's results or to ask for more details so that the programme can run. Output is what the user typically sees as text on their screen.
To learn more about input and output
https://brainly.com/question/27646651
#SPJ1
how do unblock a school chromebook
Answers
2. go to a website
3. to the left address click the icon you see: Lock, Info, or Dangerous.
4. click Site settings
5. change a permission setting. your changes will automatically save
Q8: Oliver invested some
2 points
money 5 years ago at 12% p.a.
interest (compounded
quarterly) and now received a
payment of N$50000. How
much was his initial
investment?
Answers
Answer:
The initial amount invested by Olivia is $ 27,683.79
Explanation:
The amount of initial investment can be computed using the present value formula given below:
PV=FV*(1+rs/t)^-n*t
FV is the future amount which is $50,000
rs is the rate of interest which is 12% per annum
t is the number of times interest is compounded yearly which is 4 times
n is the number of years the funds were invested i.e 5 years
PV=$50,000*(1+12%/4)^-4*5
PV=$50,000*(1+3%)^-20=$27,683.79
(viii) Word does not allow you to customize margins.
true/false:-
Answers
I would say false
In the space below, write the formula that needs to be added to the blank cells under the fourth column of the table. E2020 computer apps hands on assignment will mark brainliest
Answers
Answer:
=SUM(LEFT)*1.15
Explanation:
The nth Fibonacci number Fn is defined as follows: F0 = 1, F1 = 1 and Fn = Fn−1 + Fn−2 for n > 1.
In other words, each number is the sum of the two previous numbers in the sequence. Thus the first several Fibonacci numbers are 1, 1, 2, 3, 5, and 8. Interestingly, certain population growth rates are characterized by the Fibonacci numbers. If a population has no deaths, then the series gives the size of the poulation after each time period.
Assume that a population of green crud grows at a rate described by the Fibonacci numbers and has a time period of 5 days. Hence, if a green crud population starts out as 10 pounds of crud, then after 5 days, there is still 10 pounds of crud; in 10 days, there is 20 pounds of crud; in 15 days, 30 pounds of crud; in 20 days, 50 pounds of crud, and so on.
Write a program that takes both the initial size of a green crud population (in pounds) and some number of days as input from the keyboard, and computes from that information the size of the population (in pounds) after the specified number of days. Assume that the population size is the same for four days and then increases every fifth day. The program must allow the user to repeat this calculation as long as desired.
Please note that zero is a valid number of days for the crud to grow in which case it would remain at its initial value.
You should make good use of functions to make your code easy to read. Please use at least one user-defined function (besides the clearKeyboardBuffer function) to write your program.
basically I've done all the steps required except the equation in how to get the final population after a certain period of time (days). if someone would help me with this, I'll really appreciate it.
Answers
In Python, it can be expressed as follows. Using the recursive function type, we find the sum of the previous term and the sum of the two previous terms.
Python:x=int(input("Initial size: "))
y=int(input("Enter days: "))
mod=int(y/5)-1
def calc(n):
gen_term = [x,2*x]
for i in range(2, n+1):
gen_term.append(gen_term[i-1] + gen_term[i-2])
return gen_term[n]
if(mod==0):
print("After",y,"days, the population is",x)
else:
print("After",y,"days, the population is",calc(mod))

The total number of AC cycles completed in one second is the current’s A.timing B.phase
C.frequency
D. Alterations
Answers
The total number of AC cycles completed in one second is referred to as the current's frequency. Therefore, the correct answer is frequency. (option c)
Define AC current: Explain that AC (alternating current) is a type of electrical current in which the direction of the electric charge periodically changes, oscillating back and forth.
Understand cycles: Describe that a cycle represents one complete oscillation of the AC waveform, starting from zero, reaching a positive peak, returning to zero, and then reaching a negative peak.
Introduce frequency: Define frequency as the measurement of how often a cycle is completed in a given time period, specifically, the number of cycles completed in one second.
Unit of measurement: Explain that the unit of measurement for frequency is hertz (Hz), named after Heinrich Hertz, a German physicist. One hertz represents one cycle per second.
Relate frequency to AC current: Clarify that the total number of AC cycles completed in one second is directly related to the frequency of the AC current.
Importance of frequency: Discuss the significance of frequency in electrical engineering and power systems. Mention that it affects the behavior of electrical devices, the design of power transmission systems, and the synchronization of different AC sources.
Frequency measurement: Explain that specialized instruments like frequency meters or digital multimeters with frequency measurement capabilities are used to accurately measure the frequency of an AC current.
Emphasize the correct answer: Reiterate that the current's frequency represents the total number of AC cycles completed in one second and is the appropriate choice from the given options.
By understanding the relationship between AC cycles and frequency, we can recognize that the total number of AC cycles completed in one second is referred to as the current's frequency. This knowledge is crucial for various aspects of electrical engineering and power systems. Therefore, the correct answer is frequency. (option c)
For more such questions on AC cycles, click on:
https://brainly.com/question/15850980
#SPJ8
Why does the media play such an important role in our personal freedom? Select 3 options.
It holds government accountable.
It holds government accountable.
It promotes self-expression.
It promotes self-expression.
It spreads government’s views.
It spreads government’s views.
It keeps us informed.
It keeps us informed.
It keeps us entertained.
It keeps us entertained.
Answers
Answer:
It promotes self-expression
It holds the government accountable
It keeps us informed
Explanation:
I got them right Ed
The media play such an important role in our personal freedom because of the following:
A. It holds the government accountable.
B. It promotes self-expression.
D. It keeps us informed.
What is media?The media is a center of communication or transfer of information throughout the world. Its main aim is to collect information from the world and provide it to the citizens.
Because it enables the public expression of one's personal opinion about a subject, the media is crucial to freedom.
Media plays an important role in freedom because it helps in expressing a personal view about something in front of people. It gives us information about the world, and what is happening in the government, and other current situations.
Thus, the correct options are:
A. It holds the government accountable.
B. It promotes self-expression.
D. It keeps us informed.
To learn more about media, refer to the link:
https://brainly.com/question/28100033
#SPJ5
You work at the headquarters of an international restaurant chain. The launch of your mobile ordering app has been well received in your home country, increasing sales and customer satisfaction while decreasing order wait time and operating expenses. Your team is now ready to expand the mobile app into a handful of international markets. However, you first need to strategize what kinds of adjustments and adaptations will be needed to help ensure the app's success in these various cultural environments. Marketing director: Frankly, I'm a little surprised at the success we've seen with this app here at home. But it makes sense to keep buiding on that momentum You Yes, I think today's customers are indigenously comfortable with internet based technologies, an________ is a natural extension of that phenomenon. The challenge is to figure out how easily the app can be adapted to markets
a. e-business
b. global purchasing
c. language diversity
d. model networking
Answers
Answer: E-business
Explanation:
Based on the information given, a natural extension of that phenomenon is the E-business. E-business which means electronic business is when business is done through the internet.
It should be noted that e-business processes consist of the purchase and sale of goods and services, the processing of payments, servicing customers, sharing information regarding products, managing production control, etc.
Create a program that compares the unit prices for two sizes of laundry detergent sold at a grocery store.
Answers
Complete Question:
Create a program that compares the unit prices for two sizes of laundry detergent sold at a grocery store. Console Price Comparison Price of 64 oz size: 5.99 Price of 32 oz size: 3.50 Price per oz (64 oz): 0.09 Price per oz (32 oz): 0.11
Using Python
Answer:
This program does not make use of comments (See explanation section)
price64 = float(input("Price of 64 oz size: "))
price32 = float(input("Price of 32 oz size: "))
unit64 = price64/64
unit32 = price32/32
print("Unit price of 64 oz size: ", round(unit64,2))
print("Unit price of 32 oz size: ", round(unit32,2))
if unit64>unit32:
print("Unit price of 64 oz is greater" )
else:
print("Unit price of 32 oz is greater" )
Explanation:
This line prompts the user for the price of 64 oz size
price64 = float(input("Price of 64 oz size: "))
This line prompts the user for the price of 32 oz size
price32 = float(input("Price of 32 oz size: "))
This line calculates the unit price of 64 oz size
unit64 = price64/64
This line calculates the unit price of 32 oz size
unit32 = price32/32
This next two lines print the unit prices of both sizes
print("Unit price of 64 oz size: ", round(unit64,2))
print("Unit price of 32 oz size: ", round(unit32,2))
The next line compares the unit prices of both sizes
if unit64>unit32:
This line is executed if the unit price of 64 oz is greater than 32 oz
print("Unit price of 64 oz is greater" )
else:
This line is executed, if otherwise
print("Unit price of 32 oz is greater" )
You are designing a simple calculator program for young children to use. Right now, if they do something that the program didn’t expect, a message appears that reads, “User input deemed invalid.” What changes could you make so that the message would be more suitable for this audience?
Answers
In Python, you can use a try-except statement and raise an exception with a custom message.
For example:
try:
x = int(input())
except:
raise Exception("User input deemed invalid")
In JavaScript, you can try using a try-catch statement. You can use the 'throw' keyword to handle the error.
Give me quick ans pls
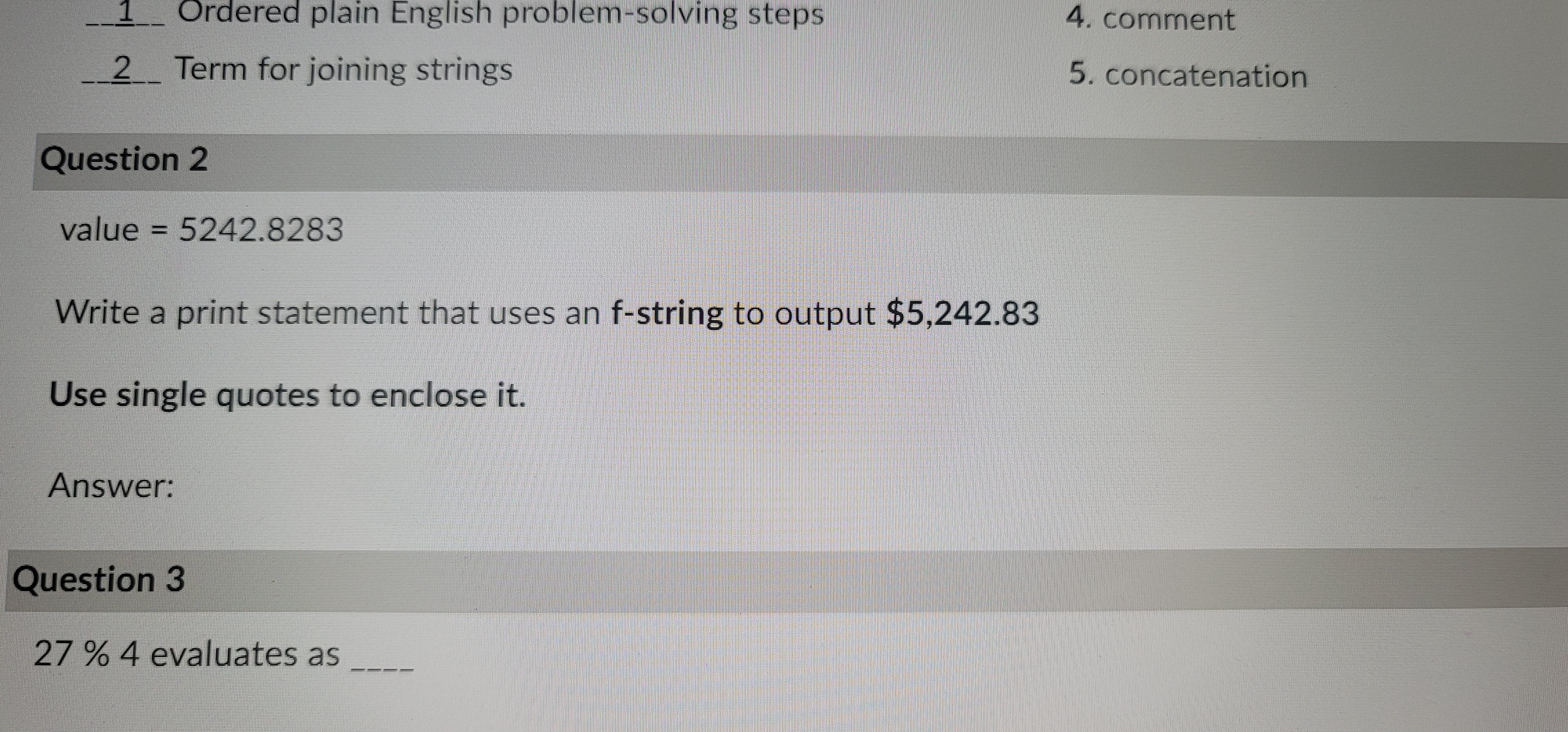
Answers
Answer: print(f'$5,242.83')
Explanation: print(f'$5,242.83')
compare and contrast the various write strategy used in cache technologies
Answers
Answer:
The abiotic factors are non-living factors in an ecosystem that affect the organisms and their lifestyle. In this case, low temperature and low humidity lead to the conditions that are unfavorable for birds. So, the birds must adapt to these factors by hiding the food in the caches.
Explanation:
What do you setup when you want to filter traffic from getting through a firewall?
Answers
Explanation:
Windows Firewall
Windows Firewall is a packet filter and stateful host-based firewall that allows or blocks network traffic according to the configuration. A packet filter protects the computer by using an access control list (ACL), which specifies which packets are allowed through the firewall based on IP address and protocol (specifically the port number). A stateful firewall monitors the state of active connections and uses the information gained to determine which network packets are allowed through the firewall. Typically, if the user starts communicating with an outside computer, it remembers the conversation and allows the appropriate packets back in. If an outside computer tries to start communicating with a computer protected by a stateful firewall, those packets are dropped automatically unless access was granted by the ACL.
When importing data using the Get External Data tools on the Data tab, what wizard is automatically
started after selecting the file you want, to help import the data?
Text Import Wizard
Excel Data Wizard
Import Wizard
Text Wrap Wizard
Answers
Answer: text import wizard
Explanation:
Write a function that accepts an int array and the array’s size as arguments.
The function should create a new array that is twice the size of the argument array.
The function should copy the contents of the argument array to the new array, and initialize the unused elements of the second array with 0.
The function should return a pointer to the new array.
Demonstrate the function by using it in a main program that reads an integer N (that is not more than 50) from standard input and then reads N integers from a file named data into an array.
The program then passes the array to your array expander function, and displays the values of the new expanded array, one value per line.
You may assume that the file data has at least N values. There are no prompts for the integer and no labels for the expanded reversed array that is printed out. If the integer read in from standard input exceeds 50 or is less than 0 the program terminates silently.
Answers
Using the knowledge in computational language in C++ it is possible to write a code that the function that accepts an int array and the array’s size as arguments.
Writting the code:#include<iostream>
#include<fstream>
// Use the standard namespace.
using namespace std;
// Define the function to expand the given array
// to twice its capacity.
int *Array_Expander(int arr[], int size)
{
// Create a new array of double size.
int *new_array = new int[2*size];
int i = 0;
// Start the loop to copy the values of the
// given array into the new array.
while(i < size)
{
// Copy the value in the new array.
new_array[i] = arr[i];
// Increment the value of the variable i.
i = i + 1;
}
// Start the loop to set the value of the second half
// of the new array to 0.
while(i < 2*size)
{
// Set the value to 0.
new_array[i] = 0;
// Increment the value of the variable i.
i = i + 1;
}
// Return the new array.
return new_array;
}
// Define the main() function.
int main()
{
// Create an integer to store the size of the array.
int N;
// Store the size of the array from the standard input.
cin >> N;
// Return if the value of N is less than 0
// or greater than 50.
if(N < 0 || N > 50)
return 0;
// Create an array of size N.
int *arr = new int[N];
// Open the file in read mode.
ifstream infile;
infile.open("data");
// Display the error message if the file is not found
// and return.
if(!infile)
{
cout << "Error: File not found!" << endl;
return 0;
}
int i = 0;
// Start the loop to read the values from the file.
while (!infile.eof() && i < N)
{
// Read the value from the file and store
// it in the array.
infile >> arr[i];
// Increment the value of the variable i.
i = i + 1;
}
// Close the input file.
infile.close();
// Call the function and store the new array.
arr = Array_Expander(arr, N);
// Start the loop to print the values of the
// array, one value per line.
for(int i = 0; i < 2*N; i++)
{
cout << arr[i] << endl;
}
// Return 0 and exit the program.
return 0;
}
See more about C++ at brainly.com/question/12975450
#SPJ1

If cell A2 contains "Today is Monday," the result of the function =LEN(A2) would be __________. Fill in the blank space.
Excel Quiz.
Answers
If cell A2 includes the phrase "Today is Monday," the result of the function =LEN(A2) would be 15, which is the number of characters in the cell.
How can I figure out how many characters there are in Excel?Type =LEN(cell) in the formula bar and hit Enter to invoke the function. In many instances, cell refers to the cell that you want to count, like B1. Enter the formula, then copy and paste it into further cells to count the characters in each cell.
What does Len have to offer?A number is returned by LEN after it counts the characters in the text, including spaces and punctuation. LEN is set to zero if text is an empty string ("") or a reference to an empty cell.
To know more about cell visit:-
https://brainly.com/question/8029562
#SPJ1
Which octet of the subnet mask 255.255.255.0 will tell the router the corresponding host ID?
Answers
Answer: The last octet
Explanation: The last octet of the subnet mask will tell the router the corresponding host ID.
The last octet is the octet of the subnet mask 255.255.255.0 will tell the router the corresponding host ID.
What is octet in IP address?An octet is a decimal value between 0 and 255, and it is referred to as x in the IPv4 component of the address. The octets are separated by periods. The IPv4 portion of the address must contain three periods and four octets.
People may have also heard people refer to the four digits that make up an IP address as "octets." An octet is the correct term to describe the four different digits that make up an IP address.
In subnetting, the third octet is used to identify particular subnets of network 150.150.0.0. Each subnet number in the example in the image has a different value in the third byte, indicating that it is a distinct subnet number.
Thus, it is last octet.
For more details about octet in IP address, click here:
https://brainly.com/question/10115477
#SPJ2
A contracting company recently completed its period of performance on a government contract and would like to destroy all information associated with contract performance. Which of the following is the best NEXT step for the company to take?
A. Consult data disposition policies in the contract
B. Use a pulper or pulverizer for data destruction
C. Retain the data for a period of no more than one year.
D. Burn hard copies containing PII or PHI
Answers
Answer:
A. Consult data disposition policies in the contract.
Explanation:
The disposition of data should be carefully handled. The data associated with government project should be handled with care as it may include sensitive information. To destroy the data the company should refer the agreement and see if there is any notes included regarding the data disposition policy. The course of action to destroy the data should be according to the agreement.
We can sell the Acrobat Reader software to the other users”. Do you agree with this statement? Justify your answer.
Answers
No, as a User, one CANOT sell Acrobat Reader software to the other users.
What is Adobe Reader?Acrobat Reader is a software developed by Adobe and is generally available as a free PDF viewer.
While individuals can use Acrobat Reader for free,selling the software itself would be in violation of Adobe's terms of use and licensing agreements.
Therefore, selling Acrobat Reader to other users would not be legally permissible or aligned with Adobe's distribution model.
Learn more about Adobe Reader at:
https://brainly.com/question/12150428
#SPJ1
If a device has obtained an IP address using Link Local, which IP configuration would be within its subnet?
Answers
Answer:
If a device has obtained an IP address using Link Local, its IP configuration will be within the 169.254.0.0/16 subnet.
Explanation:
The Internet Engineering Task Force (IETF) has reserved the IPv4 address block 169.254 if a device received an IP address. 0.0/16
A link-local address is a unicast network address that is valid only for communications within the subnetwork to which the host is linked. Link-local addresses are typically issued automatically by a method known as stateless address autoconfiguration or link-local address autoconfiguration,[1] sometimes known as automatic private IP addressing (APIPA) or auto-IP. As a result, routers do not forward packets that have link-local source or destination addresses. IPv4 link-local addresses are assigned from the address block 169.254.0.0/16.
The Address Resolution Protocol (ARP) is used to convert between Layer 2 MAC addresses and Layer 3 IP addresses.ARP resolves IP addresses to MAC addresses by requesting, "Who owns the IP address 192.168.2.140, please inform me?" They are assigned from the block that may be configured inside its subnet.ARP resolves IP addresses to MAC addresses by requesting, "Who owns the IP address 192.168.2.140, please inform me?" They are assigned from the block that may be configured inside its subnet .ARP resolves IP addresses to MAC addresses by requesting, "Who owns the IP address 192.168.2.140, please inform me?" They are assigned from the block that may be configured inside its subnet.
ARP resolves IP addresses to MAC addresses by requesting, "Who owns the IP address 192.168.2.140, please inform me?" They are assigned from the block that may be configured inside its subnet.
Write a main function that declares an array of 100 ints. Fill the array with random values between 1 and 100.Calculate the average of the values in the array. Output the average.
Answers
Answer:
#include <stdio.h>
int main()
{
int avg = 0;
int sum =0;
int x=0;
/* Array- declaration – length 4*/
int num[4];
/* We are using a for loop to traverse through the array
* while storing the entered values in the array
*/
for (x=0; x<4;x++)
{
printf("Enter number %d \n", (x+1));
scanf("%d", &num[x]);
}
for (x=0; x<4;x++)
{
sum = sum+num[x];
}
avg = sum/4;
printf("Average of entered number is: %d", avg);
return 0;
}
Which development approach was used in the article, "Protecting American Soldiers: The Development, Testing, and Fielding of the Enhanced Combat Helmet"? Predictive, adaptive or Hybrid
Answers
The sequential and predetermined plan known as the waterfall model is referred to as the predictive approach.
What is the development approachThe process entails collecting initial requirements, crafting a thorough strategy, and implementing it sequentially, with minimal flexibility for modifications after commencing development.
An approach that is adaptable, also referred to as agile or iterative, prioritizes flexibility and cooperation. This acknowledges that needs and preferences can evolve with time, and stresses the importance of being flexible and reactive to those alterations.
Learn more about development approach from
https://brainly.com/question/4326945
#SPJ1
The development approach that was used in the article "Protecting American Soldiers: The Development, Testing, and Fielding of the Enhanced Combat Helmet" is Hybrid approach. (Option C)
How is this so?The article "Protecting American Soldiers: The Development, Testing, and Fielding of the Enhanced Combat Helmet" utilizes a hybrid development approach,combining aspects of both predictive and adaptive methods.
Predictive development involves predefined planning and execution, suitable for stable projects,while adaptive methods allow for flexibility in adapting to changing requirements and environments.
Learn more about development approach at:
https://brainly.com/question/4326945
#SPJ1
Density-based spatial clustering of applications with noise is a simple and effective density-based clustering algorithm that illustrates a number of important concepts that are important for any density-based clustering approach. True False
Answers
it is correct its TRUE
Which is heavier a CRT or LED?
Answers
CRT TV is huge heavy & bulky compared to LED TV's but more reliable as far as the Tube itself is concerned. LED TV's are light and also consume less current.