________ refers to software designed to alter system files and utilities on a victim's system with the intention of changing the way a system behaves.
Answers
Malware refers to software designed to manipulate system files and utilities to alter system behavior.
How does malware aim to modify system behavior?Malware, an abbreviation for "malicious software," encompasses various types of harmful programs created with the intent to compromise computer systems and networks. It is specifically designed to alter system files and utilities, thereby influencing the behavior of the infected system. The primary objective of malware is often to gain unauthorized access, steal sensitive information, disrupt system operations, or cause harm to the targeted system and its users.
Malware can take different forms, such as viruses, worms, Trojans, ransomware, adware, and spyware. These malicious programs can be distributed through various means, including email attachments, infected websites, software downloads, or removable media. Once executed on a victim's system, malware can modify critical system files, corrupt data, exploit vulnerabilities, and establish unauthorized control.
Learn more about malicious software
brainly.com/question/14309905
#SPJ11
Related Questions
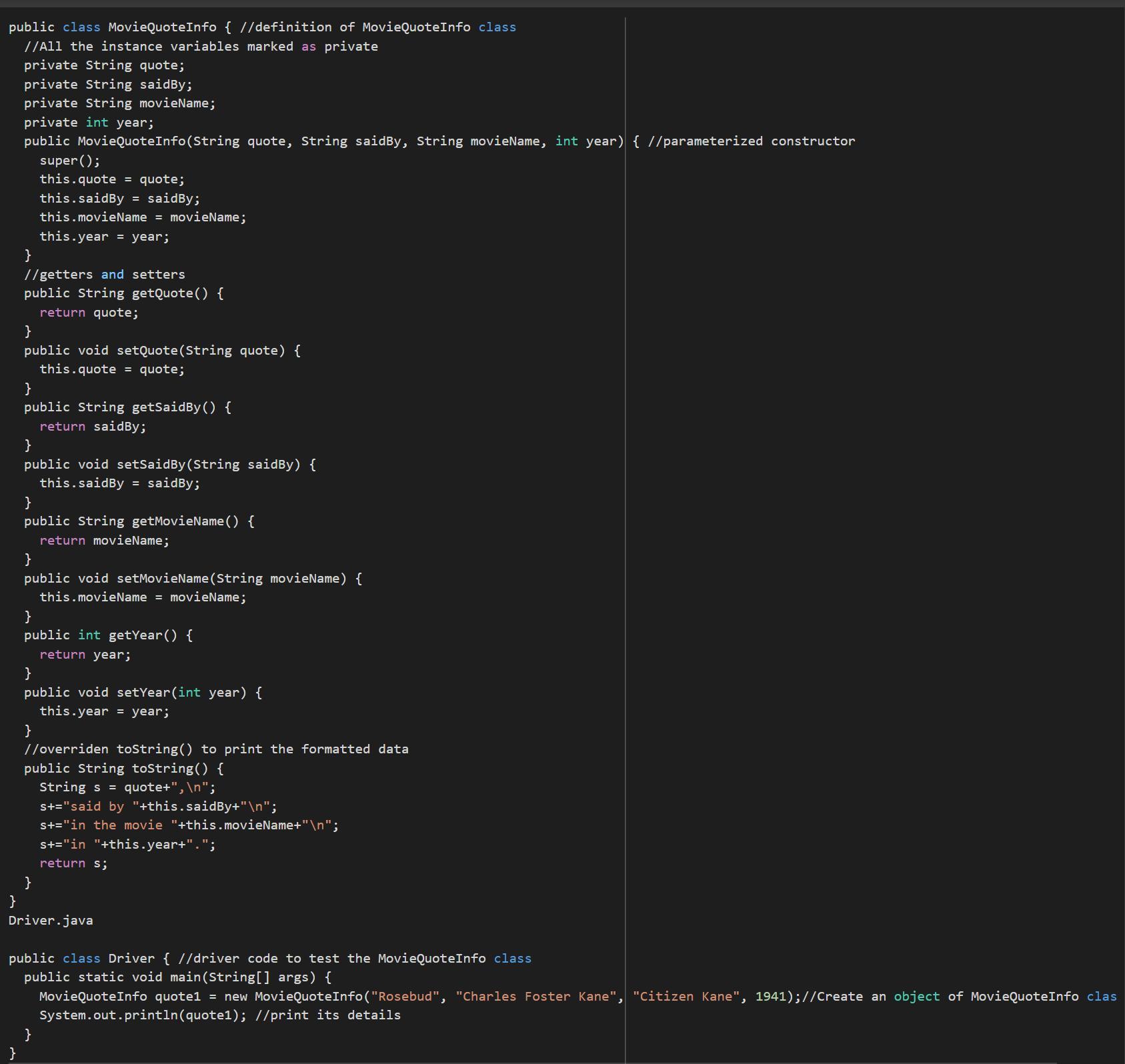
Write, compile, and test the MovieQuoteInfo class so that it displays your favorite movie quote, the movie it comes from, the character who said it, and the year of the movie: I GOT IT DONT WATCH AD.
class MovieQuoteInfo {
public static void main(String[] args) {
System.out.println("Rosebud,");
System.out.println("said by Charles Foster Kane");
System.out.println("in the movie Citizen Kane");
System.out.println("in 1941.");
}
}
Answers
Using the knowledge of computational language in JAVA it is possible to write a code that removes your favorite phrase from the movie. It consists of two classes in which one is driver code to test the MovieQuoteInfo class.
Writing code in JAVA:
public class MovieQuoteInfo { //definition of MovieQuoteInfo class
//All the instance variables marked as private
private String quote;
private String saidBy;
private String movieName;
private int year;
public MovieQuoteInfo(String quote, String saidBy, String movieName, int year) { //parameterized constructor
super();
this.quote = quote;
this.saidBy = saidBy;
this.movieName = movieName;
this.year = year;
}
//getters and setters
public String getQuote() {
return quote;
}
public void setQuote(String quote) {
this.quote = quote;
}
public String getSaidBy() {
return saidBy;
}
public void setSaidBy(String saidBy) {
this.saidBy = saidBy;
}
public String getMovieName() {
return movieName;
}
public void setMovieName(String movieName) {
this.movieName = movieName;
}
public int getYear() {
return year;
}
public void setYear(int year) {
this.year = year;
}
//overriden toString() to print the formatted data
public String toString() {
String s = quote+",\n";
s+="said by "+this.saidBy+"\n";
s+="in the movie "+this.movieName+"\n";
s+="in "+this.year+".";
return s;
}
}
Driver.java
public class Driver { //driver code to test the MovieQuoteInfo class
public static void main(String[] args) {
MovieQuoteInfo quote1 = new MovieQuoteInfo("Rosebud", "Charles Foster Kane", "Citizen Kane", 1941);//Create an object of MovieQuoteInfo class
System.out.println(quote1); //print its details
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1
Identify the problems that computer program bugs can cause. Check all that apply.
Program bugs can cause error messages.
Program bugs can cause computer viruses.
Program bugs can cause programs to halt while they are running.
Program bugs can cause software and hardware to miscommunicate.
Program bugs can provide unplanned results.
Answers
Answer:
acde not b though
Explanation:
1.) B.
2.)A.
3.)C.
Ignore this writing i coulndnt submit the answer with out it
Given the statement double "p;, the statement p++; will increment the value of p by bytes. 1 c. 4 b. 2 d. 8 a.
Answers
increment the value of p by bytes is 8.
How big are P & * P inside a 16 bit scheme?The size of the pointer depends on the system's 16/32 bit architecture.Therefore, it will need 2 bytes for 16 bit.It will occupy 4 bytes for a 32 bit system.
How big is -* P in the this program on a 64-bit system?The address bus's size is a factor.The system bus size would be 64-bit (8 bytes) for a 64-bit machine, which means the pointer would be 8 bits in length .Additionally, its size would be 32 bits on the a 32-bit system (4 bytes).Here, sizeof(*p) refers to the size of the int pointer type.
To know more about bytes visit:
https://brainly.com/question/12996601
#SPJ4
Which statement below returns 'soccer'?
sports = [2: football', 3:'soccer', 4:'volleyball', 5:'softball'}
• sports.find(soccer')
• sports[3]
• sports(3)
• sports.get(2)
Answers
Answer:
The answer is the second option.
sports = {2: 'football', 3:'soccer', 4:'volleyball', 5:'softball'};
console.log(sports[3]);
will output:
soccer
Explanation:
There were several syntax errors in the code (assuming it is javascript):
- Text strings must be enclosed in single or double quotes.
- sports is an object, not an array, so it should have { } and not [ ]
I Have a Kodak pixpro camera and I put my memory card in (sandisk) but it keeps on saying "card is not formatted" then it gives me the option of "format" "doing so will clear all data" "yes or no" but i barely bought the memory card and the camera , so What do i do ? I never used the camera or the memory card . (PLEASE HELP )
Answers
If you've never used the camera, and you're fairly certain there aren't any pictures on the memory device, then it's safe to format the disk so that you set up the table of contents properly. That way the computer can read the data in the right sectors and so on. I would choose the option "yes" and follow the instructions on the screen. It should lead you to a blank disk so you can then fill it up with future pictures down the road.
If you think there are pictures on the card and you want to retrieve them, then try putting the card into a different memory reader and see if the same message pops up. Chances are there are slightly different formats that aren't being compatible in some way if this is the case.
Devices are best suited for complex activities such as video editing
Answers
Devices such as computers or tablets are typically best suited for complex activities such as video editing. These devices offer more processing power and a larger screen, which can make editing videos more efficient and effective. Additionally, there are a variety of software options available for these devices that are specifically designed for video editing, allowing for more advanced and professional editing capabilities. While it is possible to edit videos on smartphones or other mobile devices, they may not have the same level of functionality and can be more challenging to work with for complex projects.
To know more about video editing please check the following link
https://brainly.com/question/15994070?utm_source=android&utm_medium=share&utm_campaign=question
#SPJ11
Which background-repeat value represents this div?
repeat
repeat-y
repeat-x
no-repeat

Answers
Answer:
repeat-y ................ ..
Pls help! 7th grade pythin fyi

Answers
Answer:
There should be a colon at the end of the if statement, ie:
if x > 100: print("...")
activex is used by developers to create active content. true or false
Answers
True, Developers utilize ActiveX to produce interactive content. An executable program that affixes to or infects other executable programs is referred to as a computer virus.
In order to adapt its earlier Component Object Model (COM) and Object Linking and Embedding (OLE) technologies for content downloaded from a network, particularly via the World Wide Web, Microsoft built the deprecated ActiveX software framework. In 1996, Microsoft released ActiveX. Although the majority of ActiveX controls can run on other operating systems besides Windows, in practice this is not the case. Microsoft created a suite of object-oriented programming methods and tools called ActiveX for Internet Explorer in order to simplify the playing of rich media. In essence, Internet Explorer loads other apps in the browser using the ActiveX software architecture.
Learn more about ActiveX here
https://brainly.com/question/29768109
#SPJ4
What am I doing wrong?

Answers
In your example, you're asking the user for a number and then you're setting total and nums equal to zero. This results in your first number being ignored by the program. I included the complete working code below:
num = int(input("Enter a number: "))
total = num
nums = 1
while (total <= 100):
num = int(input("Enter a number: "))
nums = nums + 1
total = total + num
print("Sum: "+str(total))
print("Numbers Entered: "+str(nums))
I hope this helps!
What is climate and how is it formed? What can cause climate change.
Answers
Answer: Climate is the weather and conditions over time (at least a year).
The things that start climate change are burning fossil fuels and tearing down forests to start construction.
Answer:
climate can be defined as weather.
Challenge: Use an if statement to trigger a sequence of
commands if your character is on a gem.
Congratulations! You've learned how to write conditional code
using if statements and else if blocks.
A condition like isOnGem is always either true or false. This is
known as a Boolean value. Coders often use Boolean values with
conditional code to tell a program when to run certain blocks of
code.
1 In the if statement below, use the Boolean condition
isOnGem and add commands to run if the condition is true.
2 Modify or keep the existing else block to run code if your
Boolean condition is false.
3 If necessary, tweak the number of times your for loop runs.
for i in 1... 16 (
if condition {
} else {
}
moveForward()

Answers
Here's an example code snippet that meets the requirements you've specified
for i in 1...16 {
if isOnGem {
collectGem()
} else {
moveForward()
}
}
How to explain the codeIn this code, the if statement checks whether the Boolean condition isOnGem is true or false. If it's true, the code runs the collectGem() function to collect the gem. If it's false, the code runs the moveForward() function to continue moving forward. The else block handles the case where isOnGem is false.
Note that I've assumed that there's a function called collectGem() that will collect the gem if the character is on it. You may need to substitute this with the appropriate function for your particular coding environment. Additionally, the for loop will run 16 times by default, but you can modify this number as needed for your program.
Learn more about program on:
https://brainly.com/question/26642771
#SPJ1
what is multimedia computer system
Answers
A Multimedia can be defined as any application that combines text with graphics, animation, audio, video, and/or virtual reality. Multimedia systems are used for security to keep intruders out of a system and for the protection of stored documents
According to recent security survey compromised passwords are responsible for.
Answers
Answer:
81 percent of hacking-related breaches
Explanation:
I found this online, if you need a more specific answer, you will need to provide the multiple-choice options.
Which statement about intellectual property is true? (CSI-7.6) Group of answer choices It is okay to use code you find on the internet, since it is searchable. Since intellectual property is about your ideas, they aren't covered by any laws. Documentation of your ideas isn't important to prove intellectual property. Laws are in place to cover your creative work, which includes code you have written.
Answers
Answer:
Laws are in place to cover your creative work, which includes code you have written.
Explanation:
Copyright law can be defined as a set of formal rules granted by a government to protect an intellectual property by giving the owner an exclusive right to use while preventing any unauthorized access, use or duplication by others.
A copyright can be defined as an exclusive legal right granted to the owner of a creative work (intellectual property) to perform, print, record, and publish his or her work. Also, the owner is granted the sole right to authorize any other person to use the creative work.
For instance, copyright law which protects the sharing and downloading rights of music is known as the Digital Millennium Copyright Act (DMCA).
An intellectual property can be defined as an intangible and innovative creation of the mind that solely depends on human intellect.
Simply stated, an intellectual property is an intangible creation of the human mind, ideas, thoughts or intelligence. They include intellectual and artistic creations such as name, symbol, literary work, songs, graphic design, computer codes, inventions, etc.
Hence, laws are in place to cover a person's creative work, and it includes code he or she have written.
2. Read the following scenarios about how three different programmera approach
programming a computer game. Identify which type of programming design
approach each represents (3 points):
a) Yolanda first breaks down the whole game she needs to program into modules.
She then breaks these modules into smaller modules until the individual parts are
manageable for programming. She writes the smallest modules, and then
recombines them into larger parts.
b) Isabella takes the game process and groups together sets of related data involved
in the process. She then identifies the messages the data should respond to. After
writing the code for each set of data, Isabella then combines, tests, and refines the
subsets until the software runs properly
Answers
a.) Structured programming
b.) Object-oriented programming
c.) Top-down programming
The programming design approach represented in this scenario is modular programming. The programming design approach represented in this scenario is object-oriented programming.
What is programming?The process of creating a set of instructions that tells a computer how to perform a task is known as programming.
Computer programming languages such as JavaScript, Python, and C++ can be used to create programs.
Modular programming is the programming design approach represented in this scenario.
Yolanda divides the entire game into modules, which are then subdivided further into smaller modules until the individual parts are manageable for programming.
Object-oriented programming is the programming design approach represented in this scenario. Isabella organizes sets of related data and determines which messages the data should respond to.
Thus, this method entails representing data and functions as objects and employing inheritance and polymorphism to generate flexible and reusable code.
For more details regarding programming, visit:
https://brainly.com/question/11023419
#SPJ2
To qualify a column name, precede the name of the column with the name of the table, followed by a(n) ____.
a. asterisk (*)
b. period (.)
c. comma (,)
d. percent sign (%)
Answers
To qualify a column name, precede the name of the column with the name of the table, followed by a(n) period (.). Correct Option: b. period (.)
When referring to a column name in SQL, it is important to include the name of the table to avoid ambiguity or confusion when multiple tables are involved in a query.
The table name is followed by a period (.) and then the name of the column. For example, if we have a table called "employees" and a column called "salary", we would refer to it as "employees.salary".
It is also important to note that if the column name contains spaces or special characters, it should be enclosed in square brackets. For example, if we have a column called "employee name" in our "employees" table, we would refer to it as "employees.[employee name]".
Using proper syntax when writing SQL queries is crucial to ensure accurate results and prevent errors. Remember to always include the table name before the column name, separated by a period.
This will help to ensure that your queries are clear and unambiguous, making it easier to understand and maintain your database.
Visit here to learn more about Column:
brainly.com/question/22085941
#SPJ11
What does the CIA do ?
Answers
To protect national security, the Central Intelligence Agency (CIA) gathers, assesses, and disseminates critical information on foreign military, political, economic, scientific, and other developments.
What is CIA?The Central Intelligence Agency (CIA) is the main foreign intelligence and counterintelligence organization of the United States government. The Office of Strategic Services (OSS) from World War II gave rise to the Central Intelligence Agency (CIA), which was officially founded in 1947.
Duplication, competition, and a lack of coordination plagued earlier U.S. intelligence and counterintelligence efforts, which were carried out by the military and the Federal Bureau of Investigation (FBI). These issues persisted, in part, into the twenty-first century.
The establishment of a civilian intelligence agency by the United States, the last of the major powers, was charged with gathering top-secret data for decision-makers.
Learn more about CIA
https://brainly.com/question/29789414
#SPJ4
What is the default view in a Word document? (5 points)
Copy View
Editing View
Paste View
Reading View
Answers
Answer:
EDITING VIEWExplanation:
Although Microsoft word has several different ways you can view or edit your documents.A single computer on a network is called a____________.
Answers
Answer: A single computer on a network is called a node. pls brainliest
pls solve the problem i will give brainliest. and i need it due today.

Answers
Answer:
1024
Explanation:
by the south of north degree angles the power of two by The wind pressure which is 24 mph equals 1024
Type the correct answer in the box. Spell all words correctly.
Which resource can you give out to your audience to ensure a better understanding of the presentation?
Provide ________
of the presentation topic to the audience at the beginning or end of the presentation to ald in better understanding.
Answers
Answer:
Eveidence
Explanation:
<3
Answer:
evidence
Explanation:
too easy lol
(ANYONE GOOD AT PYTHON!?)
Write a program that outputs some Leaderboard. Pick something that interests you.
You must have a minimum of 3 rows of data and 2 columns (name can be one).
I created 6 variables called player_1, player_2 and player_3, points_1, points_2 and points_3. Be sure to use meaningful names. I centered the names and right-justified the total points. You may format your data to your liking, but the output must be in clean rows and columns.
Answers
Answer:
# Python Recap
def main():
runTimeInMinutes = 95
movieTitle = "Daddy Day Care"
print(movieTitle)
movieTitle = "Hotel for Dogs"
print(movieTitle)
print(runTimeInMinutes)
main()
Explanation:
write a python code for a calculator
Answers
Answer :
We know that a calculater should be able to calculate ( addition , subs traction, multiplication, division …etc)
# first takng inputs
num1 = float(input("Enter first number: "))
num2 = float(input("Enter second number: "))
# operations
print("Operation: +, -, *, /")
select = input("Select operations: ")
# check operations and display result
# add(+) two numbers
if select == "+":
print(num1, "+", num2, "=", num1+num2)
# subtract(-) two numbers
elif select == "-":
print(num1, "-", num2, "=", num1-num2)
# multiplies(*) two numbers
elif select == "*":
print(num1, "*", num2, "=", num1*num2)
# divides(/) two numbers
elif select == "/":
print(num1, "/", num2, "=", num1/num2)
else:
print("Invalid input")
Answer:
numb1 = int(input('Enter a number one: '))
Operation = input('Enter operation: ')
numb2 = int(input('Enter a number two: '))
def Calculator(numb1, Operation, numb2):
if Operation == '+':
print(numb1+numb2)
elif Operation == '-':
print(numb1-numb2)
elif Operation == '×':
print(numb1*numb2)
elif Operation == '÷':
print(numb1/numb2)
elif Operation == '^':
print(numb1**numb2)
elif Operation == '//':
print(numb1//numb2)
elif Operation == '%':
print(numb1%numb2)
else:
print('Un supported operation')
Calculator(numb1, Operation, numb2)
Explan ation:
Write a Python Calculator function that takes two numbers and the operation and returns the result.
Operation Operator
Addition +
Subtraction -
Multiplication *
Division /
Power **
Remainder %
Divide as an integer //
Which term describes unjust behavior due to a person’s gender or race
Answers
Answer:
Discrimination
Explanation:
Answer:
Discrimination
Explanation:
Which of the following image file formats use lossless file compression? Choose all that apply.
BMP
GIF
JPEG
PNG
RAW
TIFF
Answers
Answer:
GIF
PNG
TIFF
Explanation:
I did this already. :)
BMP, PNG, RAW, and TIFF formats use lossless file compression. Therefore, options A, D, E, and F are correct.
What is lossless file compression?Lossless file compression is a data compression technique that reduces the size of a file without losing any of its original data. In other words, when a file is compressed using a lossless compression algorithm, it can be decompressed to its exact original form without any loss of information.
This is in contrast to lossy compression, which involves removing some data from the file in order to achieve a smaller size. Lossless compression works by identifying patterns and redundancies within the data and replacing them with more efficient representations.
Thus, BMP, PNG, RAW, and TIFF formats use lossless file compression. Therefore, options A, D, E, and F are correct.
Learn more about lossless file compression, here:
https://brainly.com/question/30225170
#SPJ2
Using try-except-else-finally, write a program that asks the user for their name and age, and handle the case where the user fails to enter a valid integer for their age. Only if the user enters a valid name and age, print “Thank you”. No matter whether the user enters valid inputs or not, print “End of program”. (40 points)
Answers
The program that asks the user for their name and age, and handle the case where the user fails to enter a valid integer for their age is in explanation part.
What is programming?The process of carrying out a specific computation through the design and construction of an executable computer program is known as computer programming.
Here's an example program that uses try-except-else-finally to ask the user for their name and age, and handles the case where the user fails to enter a valid integer for their age:
try:
name = input("Please enter your name: ")
age = int(input("Please enter your age: "))
except ValueError:
print("Please enter a valid integer for your age.")
else:
print("Thank you")
finally:
print("End of program")
Thus, in this program, we use the try statement to attempt to get the user's name and age.
For more details regarding programming, visit:
https://brainly.com/question/11023419
#SPJ1
T/F : if a graphics file is fragmented across areas on a disk, you must recover all the fragments before re-creating the file.
Answers
False. If a graphics file is fragmented across areas on a disk, you do not necessarily need to recover all the fragments before re-creating the file.
When a file is fragmented, it means that its data is scattered across non-contiguous areas on a disk. Fragmentation can occur over time as files are created, modified, and deleted. However, the process of recovering fragmented files depends on the specific file system and recovery tools being used.
In many cases, modern file systems and recovery tools can handle fragmented files without requiring the recovery of all fragments before re-creating the file. These tools can reconstruct the file by identifying and retrieving the necessary fragments, even if they are not physically adjacent on the disk.
Therefore, it is not always necessary to recover all fragments of a fragmented graphics file before re-creating the file. Advanced file systems and recovery techniques can handle fragmented files and reconstruct them efficiently.
To learn more about graphics file, refer:
brainly.com/question/9759991
#SPJ11
Which of the following is a visual thinking tool that aids students in organizing ideas through analysis, synthesis, and comprehension? outline outliner mind map drawing
Answers
Answer:
The answer is "mind map drawing".
Explanation:
In the given-question, the above given choice is correct because it includes the use of texts and images to understand the creation, explain, communicate, and resolve issues.
Its resources can help students of all ages with progress learning skills through all academic areas. The map draws visual thought resources is used to help students create ideas via analysis, synthesis, and understanding.Answer:
mind map
Explanation:
Answer these two menu engineering related questions. each answer can be just one or a couple of sentences:
1. What is the difference between food cost % menu analysis and contribution margin menu analysis?
2. Why can it be a good idea to try to sell appetizers and desserts even though they may have a lower than average contribution margin?
Answers
The difference between food cost % menu analysis and contribution margin menu analysis Food cost % menu analysis is one of the most common types of menu analysis. Selling appetizers and desserts can be a good idea even though they may have a lower than average contribution margin because they can help to increase overall sales.
The aim is to find out which menu items are more profitable than others. Contribution margin menu analysis, on the other hand, involves calculating the profit that each menu item generates after taking into account the cost of all the ingredients used to make that item and other overhead costs. The contribution margin is the difference between the revenue generated by a menu item and the variable costs associated with that item. By comparing the contribution margin of different menu items, restaurant owners can determine which items are most profitable.
By offering appetizers and desserts, restaurants can attract customers who might not have come in otherwise. Once customers are in the restaurant, they are more likely to order main courses, which generally have higher contribution margins than appetizers and desserts. Additionally, appetizers and desserts can be used to upsell customers by suggesting they order additional items. This can help to increase the overall revenue generated by a meal, even if the contribution margin for each individual item is relatively low.
Learn more about Selling appetizers: https://brainly.com/question/29805756
#SPJ11