Question # 6
Math Formula
What is the output of this program? Assume the user enters 2, 5, 1, and 6.
numA = 0
for count in range(4):
answer = input ("Enter a number: ")
fltAnswer = float(answer)
numA = numA + fltAnswer
print (numA)
Output:
Answers
Answer:
Ooooo okay, so if you can get access to a tutor I reccomend it. They can give you a well thought out explanation.
Related Questions
Assume a large shared LLC that is tiled and distributed on the chip. Assume that the OS page size is 16KB. The entire LLC has a size of 32 MB, uses 64-byte blocks, and is 32-way set-associative. What is the maximum number of tiles such that the OS has full flexibility in placing a page in a tile of its choosing?
Answers
Answer:
19 - 22 bits ( maximum number of tiles )
Explanation:
from the given data :
There is 60 k sets ( 6 blocks offset bits , 16 index bits and 18 tag bits )Address has 13-bit page offset and 27 page number bits14-22 bits are used for page number and index bitstherefore any tour of these bits can be used to designate/assign tile number
so the maximum number of tiles such that the OS has full flexibility in placing a page in a tile of its choosing can be between 19 -22 bits
PBL projects are graded using what it tells you what you are doing very well and where you may need improvements
Answers
Answer: a rubric
Explanation:
A rubric is a scoring tool that explicitly describes the instructor's performance expectations for an assignment or piece of work
Meenakshi has created a presentation of six slides. The slides have the same background, but s wants to change the background of each slide. Which option can help her in doing so?
Answers
The disadvantage from using this device results from the fact that any incoming signal on any of its ports is re-created and sent out on any connected ports which has a negative impact on network performance.
Hub
Answers
Hub has a detrimental effect on the functioning of the network Any incoming signal on any of its ports is recreated and sent out on any associated ports, which is a drawback of utilising this device.
In a local area network, a hub is a layer one (physical) device that connects different network components like switches and routers (LAN). It has several ports that are used to link different local area network segments (LAN). Because frames are replicated to every other port on the network when they are received at a hub's port, hubs are typically thought of as being.
Due to the fact that each incoming signal on any of a hub's ports is recreated and sent out on any associated ports, employing a hub has a detrimental effect on network performance.
Learn more about Network here:
https://brainly.com/question/17272513
#SPJ4
the data for this problem is provided in pokemon.txt and follows the following format. col 1: pokemon id: a unique identifier for the pokemon. col 2: is legendary: a 1 if the pokemon is legendary, and 0 otherwise. col 3: height: the height of the pokemon in meters. col 4: weight: the weight of the pokemon in kilograms. col 5: encounter prob: the probability of encountering this pokemon in the wild grass. note the sum of this entire column is 1, since when you make an encounter, exactly one of these pokemon appears. col 6: catch prob: once you have encountered a pokemon, the probability you catch it. (ignore any mechanics of the actual game if you've played a pokemon game in the past.)
def part_a(filename:str='data/pokemon.txt'):
"""
Compute the proportion of Pokemon that are legendary, the average
height, the average weight, the average encounter_prob, and average
catch_prob.
Answers
For every Pokemon specified in the pokemon.txt file, this programme calculates the percentage of legendary Pokemon as well as the height, weight, encounter chance, and capture probability.
What exactly are programme instances?A set of rules known as a programme accepts input, modifies data, and produces an output. It's also known as an application or a script. Using the word processor Microsoft Word, for example, users may create and write documents.
What distinguishes one programme from others?How to spell "programme" correctly in American English Australian English is more likely to spell the word "programme" this way than Canadian English. Despite being a common choice in computer contexts, programme is advised.
The part a function, which reads data from the pokemon.txt file and computes the required statistics, is implemented as follows:
def part_a (filename: str = 'data/pokemon.txt'):
# Initialize variables for computing the statistics
total_count = 0
legendary_count = 0
total_height = 0.0
total_weight = 0.0
total_encounter_prob = 0.0
total_catch_prob = 0.0
with open(filename) as f:
next(f) # skip the header row
for line in f:
fields = line.strip().split('\t')
pokemon_id, is_legendary, height, weight, encounter_prob, catch_prob = fields
# Update the variables with the values for this Pokemon
total_count += 1
legendary_count += int(is_legendary)
total_height += float(height)
total_weight += float(weight)
total_encounter_prob += float(encounter_prob)
total_catch_prob += float(catch_prob)
# Compute the averages and proportions
proportion_legendary = legendary_count / total_count
avg_height = total_height / total_count
avg_weight = total_weight / total_count
avg_encounter_prob = total_encounter_prob / total_count
avg_catch_prob = total_catch_prob / total_count
# Print the results
print(f"Proportion of Pokemon that are legendary: {proportion_legendary:.3f}")
print(f"Average height: {avg_height:.2f} meters")
print(f"Average weight: {avg_weight:.2f} kilograms")
print(f"Average encounter probability: {avg_encounter_prob:.3f}")
print(f"Average catch probability: {avg_catch_prob:.3f}")
To know more about Program visit:
https://brainly.com/question/27359435
#SPJ4
In the long run, why might it be less expensive to construct 100 geothermal power plants than to farm the same area for corn to make ethanol?.
Answers
In the long term, building 100 geothermal power plants might be less expensive than cultivating corn for ethanol production on the same land because: efficiency, fuel costs, sustainability, and maintenance costs.
What regions can geothermal power plants be used to produce electricity in specifically?
Geothermal heat pumps (GHPs) harness the heat from the Earth and may be installed practically anyplace. GHPs are substantially shallower than conventional oil and natural gas wells, with drilling depths ranging from 3 to 90 metres (10 to 300 ft). GHPs may access their energy source without breaking the bedrock.
Which of the following is true for geothermal energy?
It is continually created within the Earth. Hot springs or reservoirs provide hot water used in heating systems. It is created by energy from the Sun. It can be used to generate electricity.
To know more about maintenance visit:-
https://brainly.com/question/7978430
#SPJ1
Search the Internet and scan IT industry magazines or Web sites to find an example of an IT project that had problems due to organizational issues. Write a short paper summarizing the key stakeholders for the project and how they influenced the outcome.
Answers
This system aimed to replace an obsolete technology jumble with a more advanced system for earnings monitoring and paychecks for 95,000 teachers, managers, custodians, and other district staff, though and it didn't work and from the start of the project, code bugs and flaws arose.
The Los Angeles Unified School District faced a problem in Jan 2007.For a $95 million project, they developed SAP software. Some professors were unpaid, some overpaid, some unpaid.The school system needed a year and a further $37m to correct the problems. Downtown and Deloitte decided in November of 2008 to resolve a dispute over the work with the contractor agreeing to return $8.25 million in overdue invoices to forgive $7 million to $10 million.The parties involved did the right thing in this case by bringing the subject to the public. It helped create the result they wanted in this way. The proceedings were filed, even if customers did not have their money back, but at minimum people received some reimbursements.Learn more:
brainly.com/question/11489632
Use the drop-down menus to complete statements about how to use the database documenter
options for 2: Home crate external data database tools
options for 3: reports analyze relationships documentation
options for 5: end finish ok run

Answers
To use the database documenter, follow these steps -
2: Select "Database Tools" from the dropdown menu.3: Choose "Analyze" from the dropdown menu.5: Click on "OK" to run the documenter and generate the desired reports and documentation.How is this so?This is the suggested sequence of steps to use the database documenter based on the given options.
By selecting "Database Tools" (2), choosing "Analyze" (3), and clicking on "OK" (5), you can initiate the documenter and generate the desired reports and documentation. Following these steps will help you utilize the database documenter effectively and efficiently.
Learn more about database documenter at:
https://brainly.com/question/31450253
#SPJ1
Write a program that uses the conversion specifier g to output the value 9876.12345. Print the value with precisions ranging from 1 to 9.
Answers
Answer:
Written in C++
#include <stdio.h>
int main(){
double value = 9876.12345;
printf("1: %.1g\n", value);
printf("2: %.2g\n", value);
printf("3: %.3g\n", value);
printf("4: %.4g\n", value);
printf("5: %.5g\n", value);
printf("6: %.6g\n", value);
printf("7: %.7g\n", value);
printf("8: %.8g\n", value);
printf("9: %.9g\n", value);
return 0;
}
Explanation:
This declares and initializes value as double
double value = 9876.12345;
This prints the first precision
printf("1: %.1g\n", value);
This prints the second
printf("2: %.2g\n", value);
This prints the third
printf("3: %.3g\n", value);
This prints the fourth
printf("4: %.4g\n", value);
This prints the fifth
printf("5: %.5g\n", value);
This prints the sixth
printf("6: %.6g\n", value);
This prints the seventh
printf("7: %.7g\n", value);
This prints the eight
printf("8: %.8g\n", value);
This prints the ninth
printf("9: %.9g\n", value);
The precision is printed using the following syntax: printf("%.ag\n", value);
Where a represents the number of digits to print
4- In a for loop with a multistatement loop body, semicolons should appear following a. the for statement itself. b. the closing brace in a multistatement loop body. c. each statement within the loop body. d. the test expression.
Answers
Answer:
c. Each statement within the loop body.
Explanation:
In a for loop with a multistatement loop body, semicolons should appear following each statement within the loop body. This is because the semicolon is used to separate multiple statements on a single line, and in a for loop with a multistatement loop body, there will be multiple statements within the loop body.
Here is an example of a for loop with a multistatement loop body:
for (int i = 0; i < 10; i++) {
statement1;
statement2;
}
In this example, semicolons should appear following statement1 and statement2.
write a program to accept a name and roll number of 5 student using structure in C
Answers
Answer:
This C program is to store and display the information of a student using structure i.e. to store and display the roll number,name,age and fees of a student using structure.
Basically one should know how to write the syntax of a structure and the rest is just implementation of the programs done so far.
If you yet need a dry run of the program or any other query, then kindly leave a comment in the comment box or mail me, I would be more than happy to help you.
#include <stdio.h>
#include <string.h>
struct student {
char name[50];
int roll;
};
int main() {
struct student student1;
strcpy(student1.name, "Chris Hansen");
student1.roll = 38;
printf("Name: %s\nRoll number: %d\n", student1.name, student1.roll);
struct student student2;
strcpy(student2.name, "Edip Yuksel");
student2.roll = 19;
printf("Name: %s\nRoll number: %d\n", student2.name, student2.roll);
struct student student3;
strcpy(student3.name, "Skeeter Jean");
student3.roll = 57;
printf("Name: %s\nRoll number: %d\n", student3.name, student3.roll);
struct student student4;
strcpy(student4.name, "Sinbad Badr");
student4.roll = 114;
printf("Name: %s\nRoll number: %d\n", student4.name, student4.roll);
struct student student5;
strcpy(student5.name, "Titus Alexius");
student5.roll = 76;
printf("Name: %s\nRoll number: %d\n", student5.name, student5.roll);
return 0;
}
DISPLAYName: Chris Hansen
Roll number: 38
Name: Edip Yuksel
Roll number: 19
Name: Skeeter Jean
Roll number: 57
Name: Sinbad Badr
Roll number: 114
Name: Titus Alexius
Roll number: 76
EXPLANATIONUse string.h to access string functions for names.
Create a struct outside of the main on student name and roll number.
strcpy works for strings.
Create for 1 student and copy and paste for the others.
Display the name and roll number for each student.
Change the file name for index.html to index.php
Add PHP code to index.php to display an error message named $error_message just below the page heading. Be sure to check that $error_message is not an empty value. Format it to be bold, red text.
Display error messages if the Product Description, List Price and Discount Percent fields are empty after the user submits the form. (1)
Display an error message if the List Price or Discount Percent data entered is not a number after the user submits the form.
Display an error message if the List Price or Discount Percent data entered is less than zero after the user submits the form.
If an error message is displayed, take the user back to the index.php page.
Add a sales tax calculation of 8% based on the discounted price. Then, display the sales tax rate and the calculated sales tax amount after the discounted price.
Answers
The PHP code is given below:
PHP codeif(isset($_REQUEST['login_btn'])){
$email = filter_var(strtolower($_REQUEST['email']),FILTER_SANITIZE_EMAIL); //strtolower changes email to all lower case
$password = strip_tags($_REQUEST['password']);
The remaining code is in the file attached.
Read more about PHP here:
https://brainly.com/question/27750672
#SPJ1
Which statement is true about the Internet and the World Wide Web?
A•The World Wide Web is a way to access the internet
B•The internet is the World Wide Web
C•The internet is a way to access the World Wide Web
D•The World Wide Web is the only way to access the internet
Answers
Answer:
C
Explanation:
The world wide web are the pages you see when you're at a device and you're online. But the internet is the network of connected computers that the web works on, as well as what emails and files travel across.
In this question, only the "Option c" is correct which can be defined as follows:
The World Wide Web (WWW) is one way of accessing the information on the web. Even if it occupies a significant portion of the web and is the most popular, the two notions should not be viewed as synonyms because they are not the same.The WWW is indeed the pages while you're online on a computer device.This network of interconnected machines upon, that the web operates, as well as a medium through the emails and data, are being sent and received.The wrong choices can be defined as follows:
In option a and Option d, both are wrong because it's the universe of network-accessible data, a manifestation of human understanding.In option b, it is wrong because it is a global network of networks, the Internet is also known as WWW.Learn more:
Internet: brainly.com/question/20341337
What is one sign that inflation is happening?
Answers
Exercise 8-3 Encapsulate
fruit = "banana"
count = 0
for char in fruit:
if char == "a":
count += 1
print(count)
This code takes the word "banana" and counts the number of "a"s. Modify this code so that it will count any letter the user wants in a string that they input. For example, if the user entered "How now brown cow" as the string, and asked to count the w's, the program would say 4.
Put the code in a function that takes two parameters-- the text and the letter to be searched for. Your header will look like def count_letters(p, let) This function will return the number of occurrences of the letter.
Use a main() function to get the phrase and the letter from the user and pass them to the count_letters(p,let) function. Store the returned letter count in a variable. Print "there are x occurrences of y in thephrase" in this function.
Screen capture of input box to enter numbeer 1
Answers
Answer:
python
Explanation:
def count_letters(p, let):
count = 0
for char in p:
if char == let:
count += 1
print(f"There are {count} occurrences of {let} in the phrase {p}")
def main():
the_phrase = input("What phrase to analyze?\n")
the_letter = input("What letter to count?\n")
count_letters(the_phrase, the_letter)
main()
Wollongong City council is interested in the growing tourism market and opens an office to launch services for people who travel on holidays and cannot look after their properties (houses or units) while they are away. This new office currently has 200 employees whose PCs are linked by a small LAN. Each PC shares files and also services (such as printing) with the others on the LAN. What type of network model is suitable to build a small LAN for this new office? How can you protect your LAN from Malware attacks?
Answers
Answer:
list five characteristics of cpu
Part 2 Graduate Students Only Architectural simulation is widely used in computer architecture studies because it allows us to estimate the performance impact of new designs. In this part of the project, you are asked to implement a pseudo-LRU (least recently used) cache replacement policy and report its performance impact. For highly associative caches, the implementation cost of true LRU replacement policy might be too high because it needs to keep tracking the access order of all blocks within a set. A pseudoLRU replacement policy that has much lower implementation cost and performs well in practice works as follows: when a replacement is needed, it will replace a random block other than the MRU (most recently used) one. You are asked to implement this pseudo-LRU policy and compare its performance with that of the true LRU policy. For the experiments, please use the default configuration as Question 3 of Project Part 1, fastforward the first 1000 million instructions and then collect detailed statistics on the next 500 million instructions. Please also vary the associativity of L2 cache from 4 to 8 and 16 (the L2 size should be kept as 256KB). Compare the performance of the pseudo-LRU and true-LRU in terms of L2 cache miss rates and IPC values. Based on your experimental results, what is your recommendation on cache associativity and replacement policy? Please include your experimental results and source code (the part that has been modified) in your report. Hint: The major changes of your code would be in cache.c.
Answers
The outline that a person can use to implement as well as compare the pseudo-LRU and that of the true-LRU cache replacement policies is given below
What is the code about?First, one need to make changes the cache replacement policy that can be see in the cache.c file of a person's code.
Thereafter one need to Run simulations with the use of the already modified or changed code via the use of the default configuration as said in Question 3 of Project Part 1.
Therefore, one can take detailed statistics, such as L2 cache miss rates and IPC (Instructions Per Cycle) values, for all of the next 500 million instructions. etc.
Learn more about code from
https://brainly.com/question/26134656
#SPJ1
What is the name of the method used to start a thread execution? Select one:
a. Init();
b. Resume();
c. Start();
d. Run();?
Answers
The name of the method used to start a thread of execution is Start();. The correct option is c.
What is a thread of execution?
A thread of execution in computer science is the shortest series of programmed instructions that may be controlled independently by a scheduler, which is usually part of the operating system. Threads and processes are implemented differently in different operating systems.
The start() method instructs this thread to start execution; the Java Virtual Machine invokes the thread's run method.
Therefore, the correct option is c. Start();
To learn more about the thread of execution, refer to the link:
https://brainly.com/question/8817970
#SPJ1
Which of the following is NOT a computer hardware?
Question 2 options:
Monitor
Internet
Keyboard
Mouse
Answers
Answer:
Internet
Explanation:
please make my answer as brainelist
Increase the value of cell c30 by 15%
Answers
To increase the value of cell C30 by 15%, you can multiply the current value of C30 by 1.15.
To increase the value of cell C30 by 15%, you can follow these steps. First, multiply the current value of C30 by 0.15 to calculate 15% of the value. Then, add this calculated amount to the current value of C30. This can be expressed as C30 + (C30 * 0.15). For example, if the current value of C30 is 100, you would perform the calculation 100 + (100 * 0.15) to get the increased value. In this case, the result would be 115. This method ensures that the value in cell C30 is increased by 15% while retaining the existing value. Adjusting calculations accordingly based on the desired value and spreadsheet software used will allow you to increase the value of cell C30 by 15%.For more such questions on Cell C30:
https://brainly.com/question/31706410
#SPJ8
Explain how will you process identify and use texts according to the
function you wish for it to serve in the particular industry
Answers
The texts have different objectives that can be identified with the following tips:
Identify the major ideas.Identify the author's purpose.What is a text?
A text is a term to refer to the set of phrases and words contained coherently to be interpreted and to share the ideas of an author (emitter or speaker).
Texts can have a variety of topics counting on the author's intention. For example:
Scientific texts: They are the texts that have the purpose of sharing scientific knowledge with exact data and results of experiments or others.Literary texts: They are the best known texts that stand out for including a variety of topics, they are marked by telling an in-depth story.News texts: They are the texts that reveal all the details of a news story and have the goal of objectively reporting.According to the above, to identify a text it is necessary to read it and remember the main ideas and the purpose of its author when writing it. Additionally, the texts are tools for different professions to teach crafts, knowledge and techniques counting on the requirement.
To learn more about texts, refer
https://brainly.com/question/25862883
#SPJ9
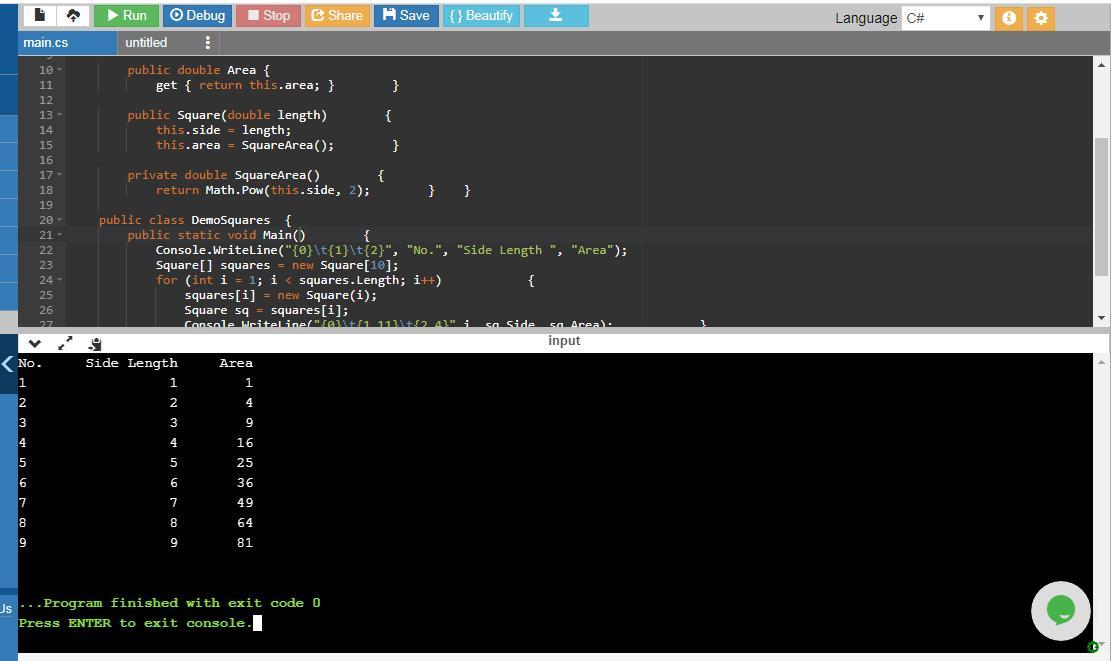
C# Create a program named DemoSquares that instantiates an array of 10 Square objects with sides that have values of 1 through 10 and that displays the values for each Square. The Square class contains fields for area and the length of a side, and a constructor that requires a parameter for the length of one side of a Square. The constructor assigns its parameter to the length of the Square’s side field and calls a private method that computes the area field. Also include read-only properties to get a Square’s side and area.
Answers
Answer:
Here is the C# program.
using System; //namespace for organizing classes
public class Square //Square class
//private fields/variables side and area of Square class
{ private double side;
private double area;
//Side has read only property to get Square side
public double Side {
get { return this.side; }
}
//Area has read only property to get Square area
public double Area {
get { return this.area; } }
/*constructor Square(double length) that requires a parameter for the length of one side of a Square. The constructor assigns its parameter to the length of the Square’s side field and calls a private method SquareArea() that computes the area field */
public Square(double length) {
this.side = length;
this.area = SquareArea(); }
//method to calcuate area of a square
private double SquareArea() {
//Pow method is used to compute square the side i.e. side^2
return Math.Pow(this.side, 2); } }
public class DemoSquares {
public static void Main() { //start of main() function body
//displays the side and area on output screen
Console.WriteLine("{0}\t{1}\t{2}", "No.", "Side Length ", "Area");
//instantiates an array to input values 1 through 10 into Side
Square[] squares = new Square[10]; //squares is the instance
for (int i = 1; i < squares.Length; i++) {
//traverses through the squares array until the i exceeds the length of the //array
squares[i] = new Square(i);
//parameter is passed in the constructor
//new object is created as arrray is populated with null members
Square sq = squares[i];
/*display the no, side of square in area after setting the alignment to display the output in aligned way and with tab spaces between no side and area */
Console.WriteLine("{0}\t{1,11}\t{2,4}", i, sq.Side, sq.Area); }
//ReadKey method is used to make the program wait for a key press from //the keyboard
Console.ReadKey(); } }
Explanation:
The program is well explained in the comments mentioned with each statement of the program. The program simply has Square class which contains area and length of side as fields and a constructor Square which has length of one side of Square as parameter and assigns its parameter to length of Square side. The a private method SquareArea() is called that computes the area field. get methods are used to include read-only properties to get a Square’s side and area. The program along with its output is attached in the screenshot.

Su now wants to highlight several inventors in her presentation, so she decides to use the underline color option.
Which tab should su use?
Which command group should she navigate to?
What does she click in the command group to open the Font dialog box?
Under which heading would the underline color menu be found?
Answers
Answer:
1) Home
2) Font
3) the arrow at the bottom right
4) All Text
Explanation:
Answer:
1. home
2. font
3. the arrow at the bottom right
4. all text
Explanation:
Which of the following is part of the process of publishing a website?
O advertising a website on a search engine
O printing a copy of all website pages
O uploading its web pages to the host directory
Ocreating web pages using templates
Answers
Which of the following activities can users do on a properly configured file storage server?
Answers
The activities that users do on a properly configured file storage server is option B: Modify shared files
What is the modifying of files?Clients can adjust shared records, get to a shared registry, and share records on a legitimately arranged record capacity server. Be that as it may, allowing a advanced certificate of believe isn't a normal action that clients would perform on a record capacity server.
Therefore, This action is more often than not performed by a certificate specialist or a trusted third-party substance that confirms the personality of a client or organization asking the certificate.
Learn more about file storage server from
https://brainly.com/question/4277691
#SPJ1
Which of the following activities can users do on a properly configured file storage server?
1 point
Grant a digital certificate of trust
Modify shared files
Access a shared directory
Share files
Which two disciplines should you study if you are considering a career in robotics 
Answers
The use of robotics is a “multi-purpose” (i.e., combining computer engineering with mechanical engineering and electrical engineering).
If one wants to work as a robotics software engineer, he needs to have a bachelor’s degree in Computer Science. If a person is interested in designing robotic parts, he needs a degree in Mechanical Engineering or Electrical Engineering.
Since its beginning, robotics has always been a multidisciplinary discipline, combining engineering, cognitive sciences, computer science, and, in recent years, social science and humanities.
To learn more about engineering, refer to the link:
https://brainly.com/question/31140236
#SPJ1
Build a 32-bit synchronous Up/Down counter. The inputs are Reset and Up. When Reset is 1, the outputs are all 0. Otherwise, when Up = 1, the circuit counts up, and when Up = 0, the circuit counts down.
Answers
A synchronous up/down binary counter with the ability to count in both directions, to or from a predetermined value as well as zero, is known as a bidirectional counter.
What is binary counter?In addition to counting "up" from zero and raising or incrementing to a preset number, it is occasionally essential to count "down" from a preset value to zero. This enables us to create an output that activates when the zero count or another preset value is reached.Normal terminology for this type of counter is "Down Counter" (CTD). With each external clock pulse from a predetermined value, the count in a binary or BCD down counter drops by one. Special dual-purpose ICs, such the 4-bit binary Up or Down counters in the TTL 74LS193 or CMOS CD4510, include an additional input pin to choose between the up count and down count modes.To Learn more About binary counter refer to:
https://brainly.com/question/29649160
#SPJ4
edhesive, 8.6 code practice question 2
Answers
Answer:
what's the question though
Answer:
What are the questions? I cannot answer you without you adding them.
ProjectSTEM CS Python Fundamentals - Lesson 3.3 Question 2 - RGB Value:
Test 6: Using 256 for all inputs, this test case checks that your program has no output. / Examine the upper condition for each color.
Test 10: This test case sets the input for blue beyond the limit, while red and green are below. It checks if your program's output contains “Blue number is not correct”, but not “Red number is not correct”, or “Green number is not correct” / Check that you output the correct phrase when the number is outside the range. Make sure that only the incorrect color phrases are output.

Answers
While CMYK is frequently used to print out colors, RGB is utilized when the colors need to be presented on a computer monitor (such as a website).Make the variable "alien color" and give it the values "green," "yellow," or "red." To determine whether the alien is green, create an if statement.
How does Python find the RGB color?Colors can only be stored in Python as 3-Tuples of (Red, Green, Blue). 255,0,0 for red, 0 for green, and 255,0 for blue (0,0,255) Numerous libraries use them. Of course, you may also create your own functions to use with them.The rgb to hex() function, which takes three RGB values, is defined in line 1.The ":X" formatter, which automatically converts decimal data to hex values, is used in line 2 to construct the hex values. The outcome is then returned.Line 4 is where we finally call the function and supply the RGB values.Verify the accuracy of the RGB color code provided. While CMYK is frequently used to print out colors, RGB is utilized when the colors need to be presented on a computer monitor (such as a website).To learn more about Python refer to:
https://brainly.com/question/26497128
#SPJ1
what would you call yourself if you were a shinobi
Answers
Answer:
someone really deleted my previous answer to this wow...
Explanation: