Question 5 (10 pts) Inverse of the mathematical constant e can be approximated as follows: - (1-7)" Write a script 'approxe' that will loop through values of n until the difference between the approximation and the actual value is less than 0.00000001. The script should then print out the built-in values of e- and the approximation to 4 decimal places and also print the value of n required for such accuracy as follows: >> approxe The built-in value of inverse of e = 0.3678794 The Approximate value of 0.3678794 was reached in XXXXXXX loops [Note: The Xs are the numbers in your answer]
Answers
The Approximate value of 0.3678794 was reached in 9 loops.
Here's the script 'approxe' that will approximate the inverse of the mathematical constant e:
python
import math
def approxe():
approx = 0
n = 1
while abs(1/math.e - approx) > 0.00000001:
approx += (-1)**n * (1-7)**n / math.factorial(n)
n += 1
print("The built-in value of inverse of e = {:.7f}".format(1/math.e))
print("The Approximate value of {:.7f} was reached in {} loops".format(approx, n-1))
This script imports the math module and defines a function called approxe. The function initializes approx to zero and sets n to 1. It then enters a while loop that continues until the absolute difference between 1/math.e and approx is less than 0.00000001.
Within this loop, the script adds the next term in the series approximation using the formula given, and updates the value of approx accordingly. It also increments n by 1 at each iteration.
Once the loop exits, the script prints out the built-in value of 1/math.e using string formatting to 7 decimal places, as well as the approximate value of approx to 7 decimal places and the value of n-1 required for such accuracy.
To run the script, simply call the function approxe():
python
approxe()
Output:
The built-in value of inverse of e = 0.3678794
The Approximate value of 0.3678794 was reached in 9 loops
Learn more about loops here:
https://brainly.com/question/14390367
#SPJ11
Related Questions
find the id, first name, and last name of each customer that currently has an invoice on file for wild bird food (25 lb)
Answers
To provide the ID, first name, and last name of each customer who currently has an invoice on file for wild bird food (25 lb), the specific data from the database or system needs to be accessed. Without access to the specific data source, it is not possible to provide the direct answer.
To find the required information, you would typically need to query a database or system that stores customer and invoice data. The query would involve joining tables related to customers and invoices, filtering for invoices with the specified product (wild bird food, 25 lb). The specific database schema and structure would determine the tables and fields involved in the query.
Here's an example SQL query that demonstrates the concept, assuming a simplified database schema:
```sql
SELECT c.id, c.first_name, c.last_name
FROM customers c
JOIN invoices i ON c.id = i.customer_id
JOIN invoice_items ii ON i.id = ii.invoice_id
JOIN products p ON ii.product_id = p.id
WHERE p.name = 'wild bird food' AND p.weight = 25;
```
In this example, the query joins the `customers`, `invoices`, `invoice_items`, and `products` tables, filtering for the specified product name ('wild bird food') and weight (25 lb). The result would include the ID, first name, and last name of each customer who has an invoice on file for that particular product.
Please note that the actual query may vary depending on the specific database schema and structure, and the query language being used.
Without access to the specific data and database structure, it is not possible to provide the direct answer to the query. However, the explanation and example query provided should give you an understanding of the process involved in retrieving the required information from a database or system.
To know more about database , visit;
https://brainly.com/question/28033296
#SPJ11
What is the name for the process that A student uses to choose only the relevant bits of information from their research
Answers
Answer:
Narrowing down
Consider the following code snippet:
public class Score
{
private String name; . . .
public boolean equals(Object otherScore)
{
Score other = (Score) otherscore;
return name.equals(other.name);
} . . .
}
What is wrong with this code?
a) The return statement should use the == operator instead of the equals method.
b) The parameter in the equals method should be declared as Score otherScore.
c) It is an error to cast otherScore as a Score object before using the equals method
d) There is nothing wrong with this code.
Answers
Answer:
Programmatically: D, the code compiles fine
Explanation:
The code compiles fine, although this is certainly a roundabout way of fulfilling this purpose.
Which statement of the visualization is incorrect? A) Virtualization works on the desktop, allowing only one operating system(Mac OS, Linux, or Windows) to run on the platform B) A server running virtualization software can create smaller compartments in memory that each behaves like a separate computer with its own operating system and resources C) Virtualization is referred to as the operating system for operating systems D) Virtualization can generate huge savings for firms by increasing the usage of their hardware capacity.
Answers
The incorrect statement is A) Virtualization works on the desktop, allowing only one operating system (Mac OS, Linux, or Windows) to run on the platform. Virtualization on the desktop enables the concurrent execution of multiple operating systems.
Explanation:
A) Virtualization works on the desktop, allowing only one operating system (Mac OS, Linux, or Windows) to run on the platform.
This statement is incorrect because virtualization on the desktop allows multiple operating systems to run concurrently on the same platform. Virtualization software, such as VMware or VirtualBox, enables users to create and run virtual machines (VMs) that can host different operating systems simultaneously, including Mac OS, Linux, and Windows.
B) A server running virtualization software can create smaller compartments in memory that each behaves like a separate computer with its own operating system and resources.
This statement is correct. Virtualization software allows the creation of virtual compartments or containers within a server's memory. Each compartment, known as a virtual machine, can operate independently with its own dedicated operating system and allocated resources.
C) Virtualization is referred to as the operating system for operating systems.
This statement is correct. Virtualization is often referred to as the "operating system for operating systems" because it provides a layer of abstraction and management for multiple operating systems running on the same physical hardware.
D) Virtualization can generate huge savings for firms by increasing the usage of their hardware capacity.
This statement is correct. Virtualization enables efficient utilization of hardware resources by consolidating multiple virtual machines onto a single physical server. This consolidation reduces the need for additional physical servers, leading to cost savings in terms of hardware procurement, maintenance, and power consumption.
To know more about operating system visit :
https://brainly.com/question/29532405
#SPJ11
true or false? while fully customizable by the customer, embedded systems are based on either the raspberry pi or the arduino design
Answers
It is true that while the embedded systems are fully customizable by the customer, they are based on either a raspberry pi or Arduino design.
An open-source electronic platform called Arduino is built on simple hardware and software. A motor can be started, an LED can be turned on, and something can be published online using an Arduino board to receive inputs such as a light on a sensor, a finger on a button, or a tweet. Sending a set of instructions to the board's microcontroller will tell your board what to do. This is achieved using the Arduino software (IDE), which is based on processing, and the Arduino programming language, which is based on wiring.
Over the years, countless projects, from simple household items to complex scientific instruments, have used Arduino as their brain. Students, enthusiasts, artists, programmers and professionals from all over the world have gathered around this open-source platform.
To know more about Arduino click here:
https://brainly.com/question/13098809
#SPJ4
A(n) _____, such as microsoft outlook, includes a private calendar, a to-do list, and powerful contact management features.
Answers
A(n) option b. personal information manager (PIM), such as Microsoft outlook, includes a private calendar, a to-do list, and powerful contact management features.
What is a personal information manager PIM software?A personal information manager (PIM) is known to be a kind of a software application that is known to function by the use of tools to help one or computer users to be able to handle and monitor contacts, calendars, tasks, appointments as well as other forms of personal data.
Therefore, A(n) option b. personal information manager (PIM), such as Microsoft outlook, includes a private calendar, a to-do list, and powerful contact management features.
Learn more about personal information manager (PIM) from
https://brainly.com/question/23664875
#SPJ1
A(n) _____, such as Microsoft Outlook, includes a private calendar, a to-do list, and powerful contact management features.
a. swim lane
b. personal information manager (PIM)
c. fact-finding application
d. enterprise architecture
Did the Z3 computer invented by Konrad Zuse have a negative effect on society?
Answers
Answer:
no
Explanation:
You are the security analyst for your organization and have discovered evidence that someone is attempting to brute-force the root password on the web server. Which classification of attack type is this?
a. External.
b. Passive.
c. Inside
d. Active.
Answers
Answer:
Active Attack
• It is an active attack 1, because someone is actively attacking your system. It is also an active attack because it is affecting the way your system works negatively, and visibly.
• 2, because they have been caught for actively committing a crime.
• lastly, because a brute-force is classified as an active attack, regardless. It is an illegal way to attempt to damage, steal or change a root password.
• Fun fact
A DDoS(distributed denial-of-service) is also classified as an active attack.
in the output of the ps -l command, what column is the most valuable to systems administrators because it indicates what the process is currently doing?
Answers
Answer:
process state
Explanation:
The process state indicates what the process is doing
In order to personalize your desktop, you may click on: Start>settings>Personalization . . .
•TRUE
•FALSE
Answers
Complete the procedure for forwarding a message by selecting the correct term from each drop-down menu.
1. ___ or open a message.
2. Click the Forward button.
3. In the To field, enter the names of intended recipients.
4. Click the ___ button.
Answers
Answer:
Preview; send.
Explanation:
Communication can be defined as a process which typically involves the transfer of information from one person (sender) to another (recipient), through the use of semiotics, symbols and signs that are mutually understood by both parties. One of the most widely used communication channel or medium is an e-mail (electronic mail).
An e-mail is an acronym for electronic mail and it is a software application or program designed to let users send texts and multimedia messages over the internet.
The procedure for forwarding a message to a recipient include;
1. Preview or open a message. This is to ensure that the appropriate or specific message is selected.
2. Click the Forward button. This button opens the dialog box to allow the sender input various details about the message and the recipient.
3. In the To field, enter the names of intended recipients.
4. Click the send button. This button automatically forwards the message to the intended recipient(s).
Beyond adding equations, what else does the Insert Equation feature allow users to do?

Answers
Answer: Write equations in your handwriting
Explanation: Edge2021
Answer:
D. Write equations in your handwriting.
Explanation:
hope this helps :)
In neighbourhood A, there is only one SPA center called JBI SPA. JBI provides a SPA service to their customers where most of whom are living in this neighbourhood and have been contacting with JBI SPA for many years. JBI's demand curve is: P = 30 - Q, and JBI's marginal cost of service is: MC = 4Q. JBI charges a single price for a unit of service.
At profit maximization level, calculate the following:
a) Price Level:_____
b) Output level:_____
c) Consumer surplus: _____
d) If JBI enforces first-degree price discrimination, the lowest priced charged is: ____ and the output level is: _____
e) Ignoring any fixed costs and under perfect price discrimination, JBI's total profit is:_____
Answers
At profit maximization level, the price level, output level and consumer surplus is given as follows:a) Price Level:The profit maximization condition of JBI Spa is given by MR = MC.Substitute the value of MR in terms of P, we have;P/2 = surplus:Consumer surplus (CS) is the difference between what the customers are willing to pay for a good or service and the actual price they pay for it.
The formula for consumer surplus is given as;CS = 0.5 * (Pmax - P) * Q, where Pmax = 30.Substitute the values of P, Pmax, and Q in the above formula, we get;CS = 0.5 * (30 - 8Q*) * Q*CS = 0.5 * (30 - 8(3.33)) * 3.33CS = $37.17d) If JBI enforces first-degree price discrimination, the lowest priced charged is and the output level is:The lowest price charged under first-degree price discrimination is the reservation price, which is equal to the maximum amount of money each customer is willing to pay for the service.
Since most of JBI's customers have been contacting with JBI Spa for many years, we can assume that their maximum willingness to pay is not too different from the price they are currently paying.So, the reservation price under first-degree price discrimination is equal to the current price level, which is P* = 8Q*.The output level under first-degree under perfect price discrimination, JBI's total profit is:Under perfect price discrimination, JBI can extract all the consumer surplus from its customers, which means P = MC = 4Q*.Substitute Q* = 3.33 in the above equation, we have;P = 4(3.33) = $13.33JBI's total profit under perfect price discrimination is equal to the total revenue which is given as;Total revenue = P * Q* = 13.33 * 3.33Total revenue = $44.45Thus, ignoring any fixed costs and under perfect price discrimination, JBI's total profit is $44.45.
To know more about maximization visit:
brainly.com/question/33009813
#SPJ11
a person has started a new technical job. in which situation would esd be an issue? when replacing a motherboard while exchanging one laptop ac adapter with one that is not from the original equipment manufacturer when installing a dual-voltage power supply when using a grounded mat and working on a computer on an ungrounded workbench
Answers
a person has started a new technical job. The situation where ESD be an issue is when installing a processor or motherboard (Option a)
What is a processor?The logic equipment that listens to and executes the basic instructions that operate a computer is known as a processor (CPU). The CPU is regarded as the primary and most important integrated circuits (IC) chip in a computer since it is responsible for understanding the majority of the computer's orders.
The CPU is regarded as the primary and most important integrated circuits (IC) chip in a computer since it is responsible for understanding the majority of the computer's orders. CPUs conduct the majority of fundamental arithmetic, logic, and I/O activities, as well as allocating commands to other processors and components in a computer.
Learn more about processor at:
https://brainly.com/question/28902482
#SPJ1
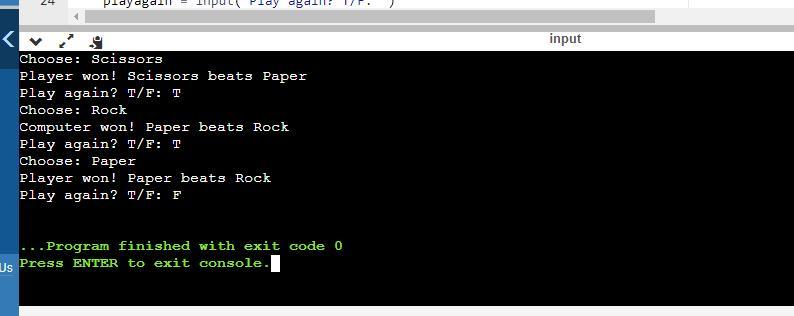
"write a program to play and score the paper-rock-scissor game. each of two users types in either p, r, or s. the program then announces the winner as well the basis for determining the winner: paper covers rock, rock breaks scissors, scissors cut paper, or nobody wins. be sure to allow the users to use lowercase as well uppercase letters. your program should include a loop that lets the user play again until the user says she or he is done."
Answers
The program is an illustration of conditional statements.
Conditional statements are used to execute instructions, if and only if certain condition or conditions are met.
Take for instance: If b = 5, print "ab"
The above print statement will only be executed, if the value of b is 5
The paper-rock-scissor program in Python where comments are used to explain each line is as follows,
#This imports the random module
import random
#This is used to control the repetition of the game
playagain ="T"
#The following is repeated until the user chooses not to play again
while(playagain == "T"):
#This generates a random choice for the computer
computer = random.choice(['Rock', 'Paper', 'Scissors'])
#This gets input for the player
player = input('Choose: ')
#If the player and computer choose the selection
if player == computer:
#Then, it's a tie
print('A tie - Both players chose '+player)
#If the player wins
elif (player.lower() == "Rock".lower() and computer.lower() == "Scissors".lower()) or (player.lower() == "Paper".lower() and computer.lower() == "Rock".lower()) or (player == "Scissors" and computer.lower() == "Paper".lower()):
#This prints "player won" and the reason
print('Player won! '+player +' beats '+computer)
#If otherwise,
else:
#This prints "computer won" and the reason
print('Computer won! '+computer+' beats '+player)
#This asks if the player wants to play again
playagain = input("Play again? T/F: ")
At the end of each round,
The program displays the winnerOr prints a tie, if there's a tieSee attachment for sample run
Read more about conditional statements at:
https://brainly.com/question/22078945
Which field in the contacts form is used to control the order in which contacts are displayed in the current view.
Answers
Answer: File as
Explanation:
A contact form is simply refered to as a web based form which is usually short and then published on the website which can be filled out by people in order to pass a message across to the person who owns the site.
The field in the contacts form that is used to control the order in which the contacts are displayed in the current view is "File As".
what should sara do when using publicly available internet such as hotel Wi-Fi?
Answers
When using publicly available internet such as hotel Wi-Fi, Sara should take the following precautions to ensure her online security and privacy that are mentioned below.
What is internet?The internet is a global network of interconnected computer networks that communicate with each other using standard protocols. It allows people around the world to access and share information, communicate with each other, and conduct online transactions in real-time.
Use a virtual private network (VPN) to encrypt her internet traffic and protect her online identity.
Use strong passwords and two-factor authentication to secure her accounts and devices.
Avoid accessing sensitive information or logging into accounts that contain personal or financial data.
Keep her devices updated with the latest security patches and anti-virus software.
Use HTTPS whenever possible, especially when accessing sensitive websites like banking or email.
Log out of accounts and clear browser history and cache after each session.
By taking these precautions, Sara can help protect herself from cyber threats and enjoy a safer online experience.
To know more about cache visit:
https://brainly.com/question/14908895
#SPJ4
When using publicly available internet such as hotel Wi-Fi, Sara should use a VPN, avoid transmitting sensitive information, and keep her device secure.
Explanation:When using publicly available internet such as hotel Wi-Fi, Sara should take certain precautions to ensure her online safety:
Use a virtual private network (VPN) to encrypt her internet connection and protect her sensitive data from potential hackers.Avoid accessing or transmitting sensitive information such as login credentials or banking details while connected to public Wi-Fi, as it can be intercepted by cybercriminals.Keep her device's software and antivirus programs up to date to minimize vulnerabilities that could be exploited by attackers.Learn more about online safety here:https://brainly.com/question/36027168
What should be entered to make the loop below print
55
60
65
x = 50
while (x < 65):
x = x + ____
print (x)
Answers
Answer:
5
Explanation:
5 is the correct answer because 50 + 5 = 55, 55 + 5 = 60, 60 + 5 = 65
One should enter 5 to make the loop below print 55, 60, and 65.
What is Loop print?A loop print is a particular kind of conditional in programming that includes expressing an outcome for a piece of code that we want the machine to run repeatedly while we are programming.
This implies that a string can be iterated over character by character.
The values listed in the reference are 55, 60, and 65, which correspond to the query. This indicates that the reference value's difference is found to be 5.
So, when we print this value as an outcome, we will require to follow some steps:
x = 50
while (x < 80):
x = x + 5
print (x).
Thus, the answer is 5.
For more details regarding loop print, visit:
https://brainly.com/question/14722722
#SPJ2
Computers convert data into information using the information processing cycle. (1 point) True False
Answers
Answer:False not true i tell you why rq i got to do something ill type why in c hat but it is False
Explanation:
Computers convert data into information using the information processing cycle is a true statement.
What is the information processing cycle?The information processing cycle is known to be the method, way or sequence of workings that are found in the way information is been processed.
Conclusively, A computer is a device that is known to change raw data into information through the four steps of the IPC namely:
InputProcessingStorage OutputLearn more about data from
https://brainly.com/question/26711803
Write 4 sentences about who advances the computer evolution

Answers
Answer: The first generation of computers took place from 1940 to 1956 and was extremely large in size.
The second generation (from 1956 to 1963) of computers managed to do away with vacuum tubes in lieu of transistors.
From 1964 to 1971 computers went through a significant change in terms of speed, courtesy of integrated circuits. Integrated circuits, or semiconductor chips, were large numbers of miniature transistors packed on silicon chips.
The changes with the greatest impact occurred in the years from 1971 to 2010. During this time technology developed to a point where manufacturers could place millions of transistors on a single circuit chip.
Explanation:
n the diagram below, why is var typed first in front of pizza?

Answers
Answer:
var is used to initialize the pizza variable
Explanation:
In order to create a variable, you first have to intiialize he variable.
This is the syntax to intiailize the variable:
var variableName
Thus, to initialize the pizza variable, you would do:
var pizza
Once you initialize the variable, you can then assign values to the variable.
pizza <- 3
Here, the value 3 is assigned to the pizza variable.
32.
To give an existing document a different name
A. retype and give it another name,
B. use the save command
C. use the same as command
D. use windows explorer to copy.
Answers
Answer:
B.
Explanation:
If you are trying to save an existing document you would use the save command and you will be prompted if you want to rename it to what ever you wish
Hope this helps :)
Robin has four copies of her midterm paper saved to a single folder on her
Windows computer. She wants to move each of these four files into a
separate folder within the existing one. How can Robin perform this task for
each file?
A. Right click on the folder containing all four files, select "Copy."
Open the same folder, select "Paste." Enter the new folder's title.
B. Open the folder containing all four files, right-click in the folder
window, select "New" enter the new folder's title, click on one file,
drag it into the new folder.
C. Open the folder containing all four files, right-click on one file,
select "New Folder," enter the new folder's title, click on the same
file, drag it into the new folder.
O
D. Open the folder containing all four files, right-click in the folder
window, select "New Folder," enter the new folder's title, click on
one file, drag it into the new folder.
Answers
Answer:
d
Explanation:
i took the test
What is a torque?
A. A linear force
B. Push or pull in a circular direction
C. A jumping force
D. A friction test
Answers
Answer:
D. A friction force
Enzo’s priority is to build more skateboards and get more customers, but his company has been losing customers due to the amount of time it takes to build a custom skateboard. He needs to focus on time-effectiveness over cost-efficiency for a month to be able to acquire more customers. What should Enzo do? Hire two more employees and spend an additional $3,000 on compensation to produce 1,200 skateboards for the month. Hire one more employee and spend $1,500 on compensation to produce 600 skateboards for the month. Get help from a friend at no cost to produce 500 skateboards for the month. Work day and night to produce 400 skateboards for the month. LIMITED TIME HELP!!
Answers
Answer:
its answer a
Explanation:
i just took the quiz
Hire two more employees and spend an additional $3,000 on compensation to produce 1,200 skateboards for the month.
What is cost-efficiency?The ability to achieve a desired outcome or output while minimizing the costs or resources required to achieve it is referred to as cost efficiency.
Given that Enzo's primary concern is to build more skateboards and get more customers, and that he needs to prioritize time-effectiveness over cost-efficiency for a month.
The best option for him is to hire two more employees and spend an extra $3,000 on compensation to produce 1,200 skateboards for the month.
This option is the most time and production capacity efficient. Hiring two more employees will increase the workforce and allow Enzo's company to produce more skateboards in a shorter period of time, improving the company's time-effectiveness.
Thus, this can be the answer for the given scenario.
For more details regarding cost-efficiency, visit:
https://brainly.com/question/28240324
#SPJ7
Help easy 50 points!!!!
How do i make someone be the brianliest? No crown thing is appering!!!!
Answers
Answer:
When someone answers your question there should be a button to crown them but it's weird there is no crown showing...
Answer:
2 ppl should answer ur question, then you'll see an option to - Mark as brainliest, then u can mark the answer as brainliest ~~~ Why not try it for me? Lolz UwU
A developer is working on a project with other developers and using GIT source control in UiPath Studio. The developer made some modifications in the workflow on the local machine and then selected the Commit and Push button.
What is the outcome of this action?
a. Current version was committed to the remote repository and pushed to the local repository
b. Local changes were committed to the local repository and then pushed to the remote repository
c. Current changes were committed and pushed to the local repository
d. Local changes were committed to the remote repository and then pushed to the remote repository
Answers
The outcome of the developer selecting the Commit and Push button in UiPath Studio while using GIT source control is: Local changes were committed to the local repository and then pushed to the remote repository.
The correct statement is B.
This means that the developer's modifications in the workflow were saved in the local repository, and then pushed to the remote repository where other developers can access and review the changes. Local changes were committed to the local repository and then pushed to the remote repository.
The outcome of a developer selecting the Commit and Push button in UiPath Studio while using GIT source control The outcome of this action is that the local changes were committed to the local repository and then pushed to the remote repository.
To know more about UiPath Studio visit:
https://brainly.com/question/24180760
#SPJ11
Which xxx completes the code to read every integer from file "data. txt"? fileinputstream inputstream = null; scanner infs = null; int total = 0; inputstream = new fileinputstream("data. txt"); infs = new scanner(filebytestream); while(xxx){ total = total + infs. nextint(); } system. out. println("total: " + total); group of answer choices inputstream. hasnextint( ) total != 0 infs. hasnextint( ) infs. eof( ) == false
Answers
Answer:
total+ infs . nex (xxx){total}
Explanation:
this is correct theres nothing wrong
What is the role of the W3C? Group of answer choices oversee research and set standards for many areas of the Internet supervise and approve corporate and commercial use of the World Wide Web control the World Wide Web; monitor and govern the use of data and information communicated over the Internet own and control the Internet
Answers
Answer:
oversee research and set standards for many areas of the Internet
Explanation:
World Wide Web Consortium was created to maintain a standard order in the cyber world. It is an international community formed by the organizations as a member. W3C sets the standards of the websites and enables them to function and appear the same in every web browser. A specific standard of guidelines, rules, and protocols are fixed so that the World Wide Web can function and grow respectively.
A jackhammer uses pressurized gas to transmit force to the hammer bit. What type of mechanical system is it?
Answers
Answer:
Constant Volume Forced Air system
Explanation:
A Constant Volume Forced Air system is a form of a mechanical system that is considered the most basic type of system. It is most common in use and high yielding in the application.
It is characterized by using any natural gas, oil, and electricity as the fuel to power the generated force.
Hence, in this case, the correct answer is "Constant Volume Forced Air system."