negative function of mass communication
Answers
Answer:
The negative effects of mass media on society can lead people towards poverty, crime, nudity, violence, bad mental and physical health disorders and others as such severe outcomes. For example, mob hitting innocents by getting carried away from the rumors spread on the internet has been common.
Explanation:
A surfeit of information and advertising messages are two of the major disadvantages of mass communication. Exposure to inappropriate content is a consideration as well. Mass communication tools provide powerful and voluminous outreach but also pose potential hazards.
Medical, social and psychological issues are a few things that Media uses against us. So it is my assertion that media has a negative impact on people's lives because it causes a dissatisfaction with body image, creates addiction, and can destroy interpersonal relationships.
Answer:
The negative effects of mass media on society can lead people towards poverty, crime, nudity, violence, bad mental and physical health disorders and others as such severe outcomes. For example, mob hitting innocents by getting carried away from the rumors spread on the internet has been common.
Related Questions
Which function is used to display a string value to the screen?
main[]
print()
run=
SHOW!
Answers
Answer:
The correct answer to this question is given below in the explanation section.
Explanation:
in most programming languages, the print() function is used to display a string value to the screen. Because, the print function prints all the string given in it as a parameter.
for example: to print hello world.
we use the function to print hello world as print("hello world").
However, it noted that other options are not correct because the main() function is an entry point of a program and it does not print string value to the screen. while run and show function do not print string value of screen also.
Answer:
in python print()
what is the entity relationship model?
Answers
7. Develop an algorithm using pseudocode to show whether a given number is even or odd
Answers
Answer:
Calculate the remainder after division by 2If remainder is 0, number is even, odd otherwise
import java.util.*;
public class PangramMissing {
public static void main (String[] argv)
{
String[] testSet1 = {"the", "lazy", "dog", "jumps", "on", "the", "fox"};
char[] missing = pangramCheck (testSet1);
System.out.println (Arrays.toString(missing));
String[] testSet2 = {"black", "quartz", "sphinx", "takes", "vow"};
missing = pangramCheck (testSet2);
System.out.println (Arrays.toString(missing));
String[] testSet3 = {"two", "driven", "jocks", "help", "fax", "my", "big", "quiz"};
missing = pangramCheck (testSet3);
System.out.println (Arrays.toString(missing));
}
public static char[] pangramCheck (String[] words)
{
// INSERT YOUR CODE HERE
}
}
finish pangramCheck() method
Answers
To implement the `pangramCheck()` method in the `PangramMissing` class, you can follow the steps below:
1. Create a `HashSet` to store the unique characters present in the words.
2. Iterate over each word in the `words` array.
3. Convert each word to lowercase using the `toLowerCase()` method to ensure case insensitivity.
4. Iterate over each character in the word.
5. Add each character to the `HashSet` using the `add()` method.
6. After iterating through all the words, create an `ArrayList` to store the missing characters.
7. Iterate over all the lowercase English alphabets (a to z).
8. Check if each alphabet is present in the `HashSet`. If not, add it to the `ArrayList`.
9. Convert the `ArrayList` to a character array using the `toArray()` method.
10. Return the character array.
The completed `pangramCheck()` method should look like this:
public static char[] pangramCheck(String[] words) {
HashSet<Character> uniqueChars = new HashSet<>();
for (String word : words) {
word = word.toLowerCase();
for (char c : word.toCharArray()) {
uniqueChars.add(c);
}
}
ArrayList<Character> missingChars = new ArrayList<>();
for (char c = 'a'; c <= 'z'; c++) {
if (!uniqueChars.contains(c)) {
missingChars.add(c);
}
}
char[] missingCharsArray = new char[missingChars.size()];
for (int i = 0; i < missingChars.size(); i++) {
missingCharsArray[i] = missingChars.get(i);
}
return missingCharsArray;
}
With this implementation, the `pangramCheck()` method will return an array of characters representing the missing characters needed to form a pangram from the given words.
For more questions on array, click on:
https://brainly.com/question/28061186
#SPJ8
Suzanne is following a fad diet. She has started to experience low energy during her workouts, and on a recent trip to the doctor, she found out she has high cholesterol. Which fad diet is Suzanne most likely following?
Answers
Answer:
Hi mate....
Explanation:
This is ur answer....
--> Suzanne just facing low carbohydrates....
hope it helps you,
mark me as the brainliest pls....
Follow me!
Answer:
A.
low-carbohydrate
Explanation:
What's the difference between cross-site scripting and cross-site request forgery? How do you protect against cross-site request forgery? Against cross-site scripting?
Answers
Answer:
Cross-site request forgery requires a secure website or network that needs user authentication while Cross-site scripting is for websites with no user authentication policies.
Explanation:
Cross-site request forgery is a process used by hackers and network administrators to forcefully grant access to users on a secure website or network. If an administration trust a user who has lost his authentication details, he uses cross-site request forgery to give access to the user.
Cross-site scripting is basically javascript program execution from a server. It is not secure and vulnerable to attacks.
If x=5 and y=3 will this condition execute? if(x > y)
A. yes
B. no
Answers
Because the x bigger than the y
because 5 > 3 is a true value, therefore if(True) will execute
what are pixels?
A: The colors In an image
B: The overall size of the image
C: The overall file size of the image
D: The smallest unit on the image that can be controlled
Answers
Answer:
D: The smallest unit on the image that can be controlled
A _____ address directs the frame to the next device along the network.
Answers
Answer:
When sending a frame to another device on a remote network, the device sending the frame will use the MAC address of the local router interface, which is the default gateway.
An unicast address directs the frame to the next device along the network.
What is network?
A computer network is a group of computers that share resources on or provided by network nodes. To communicate with one another, the computers use standard communication protocols across digital linkages. These linkages are made up of telecommunication network technologies that are based on physically wired, optical, and wireless radio-frequency means and can be configured in a number of network topologies.
The term "unicast" refers to communication in which a piece of information is transferred from one point to another. In this situation, there is only one sender and one receiver.
To learn more about network
https://brainly.com/question/28041042
#SPJ13
Three differences between Selecting and Highlighting
Answers
Answer:
highlighting is selecting a text & it turns into a color
selecting is just going over the text with a cursor
Explanation:
Answer:
Selecting an item is simply choosing something. Highlighting is to note important information. Highlighting only takes important details, selecting chooses objects.
Debug the code in the starter file so if functions as intended and does not cause any errors. This program is intended to take two integer inputs and determine whether the second is a multiple of the first or not.
the number B is a multiple of the number A if B can be divided by A with no remainder. Remember though that no number can by divided by 0- so no numbers should be considered a multiple of 0 for the purpose of this exercise.
/* Lesson 5 Coding Activity Question 2 */
import java.util.Scanner;
public class U3_L5_Activity Two{
public static void main(string[] args) {
Scanner scan = new Scanner(System.in);
system.out.println("Enter two numbers");
int a = scan.nextInt(;
intb scan.nextInt();
if(b% a = 0 || a
OD
system.out.println(b + " is not a multiple of " + a);
else
system.out.println(b + is a multiple of " + a);
10
}
}
Answers
Debugging a code involves finding and fixing the errors in a code.
The errors in the code are as follows:
Class namePrint statementsVariable declarationsInput statementsIf conditionThe class name
The class name of the program is U3_L5_Activity Two
A class name cannot contain space; instead you make use of an underscore.
So, the correct class name is: U3_L5_Activity_Two or U3_L5_ActivityTwo
The print statement
Java differentiates lower and upper case letters.
The print statements in the program begin with a small letter s. This is wrong
So, the correct statements are:
System.out.println("Enter two numbers"); System.out.println(b + " is a multiple of " + a);}System.out.println(b + " is not a multiple of " + a);The declaration and the input statements
Variables a and b were declared wrongly, and the input statements are also wrong.
The correct statements are:
int a = scan.nextInt(); int b = scan.nextInt();The condition
The if condition is not properly formatted.
The correct statement is: iif(b%a == 0)
Hence, the correct code is:
import java.util.Scanner;
public class Main{
public static void main(String[] args) {
Scanner scan = new Scanner(System.in);
System.out.println("Enter two numbers");
int a = scan.nextInt();
int b = scan.nextInt();
if(b%a == 0){
System.out.println(b + " is a multiple of " + a);}
else{
System.out.println(b + " is not a multiple of " + a);
}
}
}
Read more about debugging at:
https://brainly.com/question/23527739
which native windows application allows you to uninstall
Answers
Control panel, a native windows application, allows a user to uninstall.
What is the control panel?Microsoft Windows has a feature called the Control Panel that allows users to examine and modify system settings.
It comprises a collection of applets that enable to change user accounts, install or remove hardware and software, access networking settings, and change accessibility settings. An individual can remove using the control panel, a program that comes with Windows.
Therefore, it is control panel.
Learn more about the Native Windows, refer to:
https://brainly.com/question/24912149
#SPJ1
During an investigation, a security manager receives notification from local authorities that company proprietary data was found on a former employees home computer. The former employee's corporate workstation has since been repurposed, and the data on the hard drive has been overwritten. Which of the following would BEST provide the security manager with enough details to
determine when the data was removed from the company network?
A. Properly configured hosts with security logging
B. Properly configured endpoint security tool with darting
C. Properly configured SIEM with retention policies
D. Properly configured USB blocker with encryption
Answers
The option that would best provide the security manager with enough details to determine when the data was removed from the company network is Properly configured SIEM (Security Information and Event Management) with retention policies.The correct answer is option C.
A properly configured SIEM collects and analyzes security event logs from various sources within the network, such as firewalls, intrusion detection systems, and servers. It provides a centralized view of security events and allows for the correlation of events across multiple systems.
By having retention policies in place, the SIEM would retain security event logs for a specific period of time. This would enable the security manager to review the logs and identify any suspicious activities or indicators of data exfiltration.
In the given scenario, the security manager can examine the SIEM logs to determine if there were any unusual or unauthorized activities associated with the former employee's account.
They can identify if the employee accessed the company network or transferred data during a specific timeframe. This information can help narrow down when the data was removed from the network.
It is important to note that properly configuring the SIEM and setting appropriate retention policies is crucial for effective incident response and investigation.
Without proper configuration and retention policies, the SIEM may not have the necessary data or the ability to correlate events accurately, limiting the security manager's ability to determine when the data was removed.
Therefore,The correct answer is option C.
For more such questions data,click on
https://brainly.com/question/29621691
#SPJ8
the typing area is bordered on the right side by bars in ms word
Answers
Answer:
Explanation:
PTA NHI
Hulu suggestions? I just got it and I wanna know what's good :)
Answers
Drama show: sweet Mongolian
Adventure show: outer banks
Answer:
I love hulu almost everything is good but I recommend Zoey's Extrordinary playlist
Explanation:
Identify two stages of processing instructions
Answers
Answer:
1. Fetch instruction from memory.
2. Decode the instruction.
Write a string that contains your name and address on separate lines using embedded newline characters. Then write the same string literal without the newline characters.
Answers
Answer:
"john doe\n1234 fake st."
"john doe, 1234 fake st."
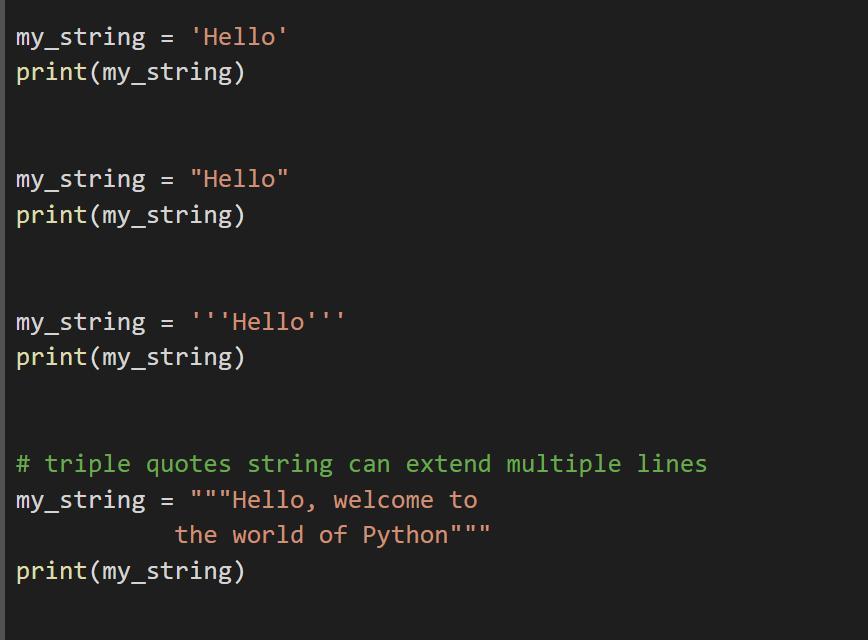
In this exercise we have to use the knowledge of the python language to write the code, so we have to:
The code is in the attached photo.
knowing what string is:
String is a collection of alphabets, words or other characters. It is one of the primitive data structures and are the building blocks for data manipulation.
So to make it easier the code can be found at:
my_string = 'Hello'
print(my_string)
my_string = "Hello"
print(my_string)
my_string = '''Hello'''
print(my_string)
# triple quotes string can extend multiple lines
my_string = """Hello, welcome to
the world of Python"""
print(my_string)
See more about python at brainly.com/question/26104476
The vast majority of the population associates Blockchain with cryptocurrency Bitcoin;
Answers
Answer:
The vast majority of the population associates Blockchain with the cryptocurrency Bitcoin; however, there are many other uses of blockchain; such as Litecoin, Ether, and other currencies. Describe at least two cryptocurrencies with applicable/appropriate examples and discuss some of the similarities and differences.
Explanation:
Discuss the important role of remote sensing application in agriculture. Do you think that the use of remote sensing is applicable in the Philippines scenario? Why? Give some of the pros and cons of remote sensing.
Answers
Answer:
Remote sensing gives the soil moisture data and helps in determining the quantity of moisture in the soil and hence the type of crop that can be grown in the soil. ... Through remote sensing, farmers can tell where water resources are available for use over a given land and whether the resources are adequate.
A data science experiment you are conducting has retrieved two historical observations for the price of Bitcoin(BTC) on December 2, 2017 of 11234 and 12475. Create a Python script that stores these two historicalobservations in a list variable namedbtcdec1.Your data science experiment requires four additional data tasks. The first task is to use the listappend()method to add the BTC price of 14560 to the listbtcdec1. The second task is to create a new empty listnamedbtcdec2and append the BTC prices of 15630, 12475, and 14972. The third task required you to usethe listextend()method to add the contents ofbtcdec2into the listbtcdec1. The fourth and final taskrequires you to use the listsort()method of the listbtcdec1to sort the items in the newly extended list,then use theprintstatement to output the content of listbtcdec1to the Python console.Starter code:_______.
Answers
Answer:
Following are the code to this question:
btcdec1=[11234, 12475] #defining a list btcdec1 that holds two integer values
btcdec1.append(14560)#using append method to add value in btcdec1 list
btcdec2=[]#defining an empty list btcdec2
btcdec2.append(15630)#using append method to add value in btcdec2 list
btcdec2.append(12475)#using append method to add value in btcdec2 list
btcdec2.append(14972)#using append method to add value in btcdec2 list
btcdec1.extend(btcdec2)#using the extend method to add value list into btcdec1
btcdec1.sort()#using sort method to arrange value in ascending order
print(btcdec1)#print list btcdec1
Output:
[11234, 12475, 12475, 14560, 14972, 15630]
Explanation:
In this code a list "btcdec1" is declared, which holds two integer variables, in the next step, it uses the append method to add another element into the list.
In the next step, another empty list "btcdec2" is declared, which uses the append method to hold the integer element, and uses the extend and sort method to add the second list into the first one and then sort the whole list and print its values.
C++ "Simon Says" is a memory game where "Simon" outputs a sequence of 10 characters (R, G, B, Y) and the user must repeat the sequence. Create a for loop that compares the two strings starting from index 0. For each match, add one point to userScore. Upon a mismatch, exit the loop using a break statement. Assume simonPattern and userPattern are always the same length.
Ex: The following patterns yield a userScore of 4:
Ex: The following patterns yield a userScore of 9:
simonPattern: RRGBRYYBGY
userPattern: RRGBBRYBGY
Result: Can't get test 2 to occur when userScore is 9
Testing: RRGBRYYBGY/RRGBBRYBGY
Your value: 4
Testing: RRRRRRRRRR/RRRRRRRRRY
Expected value: 9
Your value: 4
Tests aborted.
Answers
Answer:
In C++:
#include <iostream>
using namespace std;
int main(){
int userScore = 0;
string simonPattern, userPattern;
cout<<"Simon Pattern: "; cin>>simonPattern;
cout<<"User Pattern: "; cin>>userPattern;
for (int i =0; i < simonPattern.length();i++){
if(simonPattern[i]== userPattern[i]){
userScore++; }
else{ break; }
}
cout<<"Your value: "<<userScore;
return 0;
}
Explanation:
This initializes user score to 0
int userScore = 0;
This declares simonPattern and userPattern as string
string simonPattern, userPattern;
This gets input for simonPattern
cout<<"Simon Pattern: "; cin>>simonPattern;
This gets input for userPattern
cout<<"User Pattern: "; cin>>userPattern;
This iterates through each string
for (int i =0; i < simonPattern.length();i++){
This checks for matching characters
if(simonPattern[i]== userPattern[i]){
userScore++; }
This breaks the loop, if the characters mismatch
else{ break; }
}
This prints the number of consecutive matches
cout<<"Your value: "<<userScore;
How many NOTS points are added to your record for not completely stopping at a stop sign?
Answers
In some jurisdictions, failing to stop at a stop sign can result in a citation for running a stop sign or a similar violation. In other jurisdictions, it may be categorized as a failure to obey traffic signals or a similar violation. The number of NOTS points added to your record, if any, will depend on the specific violation charged and the point system used by the jurisdiction in question.
It's important to note that NOTS points are used to track and measure the driving record of a driver, and they may impact insurance rates and license status. It's always a good idea to familiarize yourself with the laws and regulations in your area and drive safely to reduce the risk of violations and penalties.
I need better graphic for my games on tablet
Answers
Answer:
Get a better tablet
Explanation:
No variables and only in one lines

Answers
In python 3.8, we can use a simple print statement.
print(('h0 '*3 +'Merry Christmas\n')*2)
I was opening quite a few tabs, and (i also dropped it yesterday;-; with the protective case) the screen turns to the following images( it is still being used perfectly fine after like half an hour since the drop) so uhm... Help?
It also have really low memory something because it my whole family's laptop...;(....


Answers
Based on the news you gave, it's likely that the screen issue you're experiencing had a connection with the drop, and the number of tabs you have open may be dawdling a strain on the desktop computer's thought.
What are possible solutions?I would desire to continue the desktop computer and observe if the screen issue continues. If it does, try joining an extrinsic monitor to visualize if the question is accompanying the desktop computer screen or extraordinary.
To address the reduced memory issue, you take care of try closing a few of the open tabs or programs that are not being used to permit an action room.
Alternatively, you keep feeling improving the desktop computer's memory in some way or utilizing an outside permanent computer memory to store files to allow scope
Read more about screen problems here:
https://brainly.com/question/13117463
#SPJ1
Consider the following Boolean expressions.
A && B
!A && !B
Which of the following best describes the relationship between values produced by expression I and expression II?
(A) Expression I and expression II evaluate to different values for all values of A and B.
(B) Expression and expression II evaluate to the same value for all values of A and B.
(C) Expression and expression II evaluate to the same value only when A and B are the same.
(D) Expression and expression Il evaluate to the same value only when A and B differ.
(E) Expression I and expression Il evaluate to the same value whenever A is true.
Answers
Answer:
(D) Expression I and expression Il evaluate to the same value only when A and B differ.
Explanation:
Given
\(A\ \&\&\ B\)
\(!A\ \&\&\ !B\)
Required
Select the true statement
To do this, I will create the following case scenarios.
(a): \(A = true\) and \(B = true\)
\(A\ \&\&\ B\)
\(true\ \&\&\ true \to true\) i.e. true and true is true
\(!A\ \&\&\ !B\)
\(!true\ \&\&\ !true\)
------------------------------------------------------
\(!true = false\)
------------------------------------------------------
So, we have:
\(false\ \&\&\ false \to false\)
So:
\(A =true\) and \(B = true\)
\(A\ \&\&\ B = true\)
\(!A\ \&\&\ !B = false\)
Hence, options (B) and (E) are incorrect
(b): \(A = true\) and \(B = false\)
\(A\ \&\&\ B\)
\(true\ \&\&\ false \to false\)
\(!A\ \&\&\ !B\)
\(!true\ \&\&\ !false\)
Solve each negation
\(false\ \&\&\ true \to false\)
So:
\(A =true\) and \(B = false\)
\(A\ \&\&\ B = false\)
\(!A\ \&\&\ !B = false\)
Hence, option (c) is incorrect
(c): \(A = false\) and \(B = true\)
\(A\ \&\&\ B\)
\(false\ \&\&\ true \to false\)
\(!A\ \&\&\ !B\)
\(!false\ \&\&\ !true\)
\(truee\ \&\&\ false \to false\)
So:
\(A =false\) and \(B = true\)
\(A\ \&\&\ B = false\)
\(!A\ \&\&\ !B = false\)
Case scenarios b and c implies that option (d) is correct because different values of A and B gives the same value of both expression which is false
This also implies that (a) is incorrect.
9. Which of the following is the
leading use of computer?
Answers
Complete Question:
What is the leading use of computers?
Group of answer choices.
a. web surfing.
b. email, texting, and social networking.
c. e-shopping.
d. word processing.
e. management of finances.
Answer:
b. email, texting, and social networking.
Explanation:
Communication can be defined as a process which typically involves the transfer of information from one person (sender) to another (recipient), through the use of semiotics, symbols and signs that are mutually understood by both parties. One of the most widely used communication channel or medium is an e-mail (electronic mail).
An e-mail is an acronym for electronic mail and it is a software application or program designed to let users send texts and multimedia messages over the internet.
Also, social media platforms (social network) serves as an effective communication channel for the dissemination of information in real-time from one person to another person within or in a different location. Both email and social networking involves texting and are mainly done on computer.
Hence, the leading use of computer is email, texting, and social networking.
Could anyone help :)

Answers
Answer:
2
Explanation:
This code segment iterates through the array checks to see if each element equals y if so, increments the counter variable count
Essentially, this code is taking in two parameters an array x and an integer y and counting the number of times y appears in the array x
look(numList, 1) counts the number of times the integer 1 appears in numList
1 appears two times and therefore 2 is the value returned by the function and therefore the answer
steps involved in using a class
Answers
Class
Strictness And Knowledge And Behaviorr
How many subnets and host per subnet are available from network 192.168.43.0 255.255.255.224?
Answers
It should be noted that the number of subnets and hosts available from network 192.168.43.0 255.255.255.224 is 8 and 32, respectively. Only 30 of the 32 hosts are generally functional.
What is a host in computer networking?A network host is a computer or other device that is connected to a computer network. A host can serve as a server, supplying network users and other hosts with information resources, services, and applications. Each host is given at least one network address.
A computer network is a group of computers that share resources on or provided by network nodes. To communicate with one another, computers use common communication protocols over digital links.
So, in respect to the above response, bear in mind that we may compute the total number of: by putting the information into an online IPv4 subnet calculator.
8 subnets; and30 hosts available for 192.168.43.0 (IP Address) and 255.255.255.224 (Subnet)
Learn more about hosts:
https://brainly.com/question/14258036
#SPJ1