Answers
Answer:
B.
They are the audio technicians so they do all things audio, including sound effects and different voices.
Related Questions
based on your review of physical security, you have recommended several improvements. your plan includes smart card readers, ip cameras, signs, and access logs. implement your physical security plan by dragging the correct items from the shelf into the various locations in the building. as you drag the items from the shelf, the possible drop locations are highlighted. in this lab, your task is to: install the smart card key readers in the appropriate locations to control access to key infrastructure. install the ip security cameras in the appropriate locations to record which employees access the key infrastructure. install a restricted access sign in the appropriate location to control access to the key infrastructure. add the visitor log to a location appropriate for logging visitor access.
Answers
Deploy smart card readers at all access points to critical infrastructure locations, including server rooms, data centres, and any other locations that house sensitive data or essential equipment.
What three crucial elements make up physical security?Access control, surveillance, and testing make up the three key parts of the physical security system. The degree to which each of these elements is implemented, enhanced, and maintained can frequently be used to measure the effectiveness of a physical security programme for an organisation.
What essentials fall under the category of physical security?Three crucial aspects of physical security are testing, access control, and surveillance. In order for physical security to successfully secure a structure, each element depends on the others.
To know more about access points visit:-
https://brainly.com/question/29743500
#SPJ1
How can I fix this?
I’m on school Wi-Fi and “your connection isn’t private” keeps popping up every time I try to look up something, can someone please help!

Answers
Answer:
Try these
Reload page.
Clear Browsing Data.
Restart Router.
Avoid Incognito Mode.
Check Computer Date and Time.
Disable VPN.
Explanation:
I will give brainliest!!!!! I NEED HELP ASAP!!!!!!!

Answers
Answer:
c
Explanation:
Lossy compression means that when you compress the file, you're going to lose some of the detail.
True
False
Question 2
InDesign is the industry standard for editing photos.
True
False
Question 3
Serif fonts are great for print media, while sans serif fonts are best for digital media.
True
False
Question 4
You should avoid using elements of photography such as repetition or symmetry in your photography.
True
False
Answers
Lossy compression means that when you compress the file, you're going to lose some of the detail is a true statement.
2. InDesign is the industry standard for editing photos is a true statement.
3. Serif fonts are great for print media, while sans serif fonts are best for digital media is a true statement.
4. You should avoid using elements of photography such as repetition or symmetry in your photography is a false statement.
What lossy compression means?The term lossy compression is known to be done to a data in a file and it is one where the data of the file is removed and is not saved to its original form after it has undergone decompression.
Note that data here tends to be permanently deleted, which is the reason this method is said to be known as an irreversible compression method.
Therefore, Lossy compression means that when you compress the file, you're going to lose some of the detail is a true statement.
Learn more about File compression from
https://brainly.com/question/9158961
#SPJ1
Identify two uses of 3D printing that help doctors and patients in hospitals.
Answers
Answer: Prosthetic and Diagrams
Explanation:
Prosthetics are made by 3D printing, used as a new stand in for a missing limb. Like if you were to loose a leg or an arm, 3D printing creates the outer shell most times. Diagrams are used to show examples to patients of their condition, or even sometimes for other doctors to get a better understanding of a condition. They may show them to patients to give an example of what may need to happen too. For doctors they may also be used to figure out what plan of action may be needed.
How many bits are reserved for the Transmission Control Protocol (TCP) flags?
Answers
What to do if ads keep popping up on my computer
Answers
Answer:
skip it or leave it. It is the easy answer for me
Answer: you could restart your computer or you could reset it and then go download a add blocker on your computer then it should stop
Explanation:
(Geometry: area of a regular polygon)
A regular polygon is an n-sided polygon in which all sides are of the same length and all angles have the same degree (i.e., the polygon is both equilateral and equiangular). The formula for computing the area of a regular polygon is
area = (n * s^2) / (4 * tan(PI / n)
Here, s is the length of a side. Write a program that prompts the user to enter the number of sides and their length of a regular polygon and displays its area.
Answers
Answer:
import math
n = int(input("Enter the number of sides: "))
s = float(input("Enter the length of a side: "))
area = (n * s**2) / (4 * math.tan(math.pi/n))
print("The area is: " + str(area))
Explanation:
*The code is in Python.
Import the math to be able to compute the pi and tan
Ask the user to enter the number of sides and the length of a side
Calculate the area using the given formula
Print the area
Which are benefits of using an IDE while writing a program? Select all the apply.
The IDE keeps track of and links files.
The IDE simplifies and coordinates the creation process.
The IDE allows the programmer to see errors.
Answers
Answer:
The IDE keeps track of and links files.
The IDE simplifies and coordinates the creation process.
The IDE allows the programmer to see errors.
Explanation:
The IDE stands for Integrated Development Environments. In the case when the program the following are the benefits of using an IDE
1. It tracks and link the files
2. It coordinates and simplify the proces of creation
3. Also it permits the programmer to view the errors
hence, the above represent the benefits
So all are considered to be the benefits
Answer:
Explanation:
ITs all 3. edge 2021
STM-1 contains 63 primary 2-Mbps data streams and each of them contains 30 time slots for speech.
(a) How many simultaneous calls (64 Kbps) can be transmitted over a single fiber pair used by the STM-16 optical system?
(b) What is the number of simultaneous calls if a DWDM system using a
100- GHz wavelength grid from 1,528.77 nm/196.1 THz to 1,563.86
nm/191.7 THz is implemented?
(c) The STM-16 signal is transmitted through each optical channel. What
will be the total data rate of the DWDM system from part (b)?
Answers
Which of the following is not a characteristic of a good value log entry
Answers
I'm trying to figure out how to put this together can anyone help me solve this?

Answers
The if-else statement to describe an integer is given below.
How to illustrate the informationThe if-else statement to describe an integer will be:
#include <stdio.h>
#include <stdbool.h>
int main(void) {
int userNum;
bool isPositive;
bool isEven;
scanf("%d", &userNum);
isPositive = (userNum > 0);
isEven = ((userNum % 2) == 0);
if(isPositive && isEven){
printf("Positive even number");
}
else if(isPositive && !isEven){
printf("Positive number");
}
else{
printf("Not a positive number");
}
printf("\n");
return 0;
}
Learn more about integers on:
https://brainly.com/question/17695139
#SPJ1
given 2,4,3,-1 as input, what is the output for the following program:total_product = 1 user_value = int(input()) while user_value > 0: total_product = total_product * user_value user_value = int(input()) print('Product:', total_product, end='')
Answers
The python program for any of the given values is as written below.
How to run a Program in Python?We are told to use input for the python program as;
2, 4, 3, -1
Now, the python program using 2 as user value and 1 as total product gives us the program as;
total_product = 1
user_value = (input(1)) #while user_value > 0:
total_product = total_product * user_value
user_value = (input(2))
print('Product:2', total_product, end='2')
Read more about Python Program at; https://brainly.com/question/26497128
#SPJ1
1. Human to ____Human____
2. _Human________ to machine
3. Machine to ______Machine
4. _______________ to machine
Answers
Answer:
uhmmm human machine whaT?
Explanation:
Answer:
4 is Machine to machine
When an application is being designed for a company, Windows interface standards can be superseded by ______________.
a.
the company’s interface standards
b.
usability standards
c.
the preference of the users
d.
the graphic designer
Answers
Answer:
a. the company’s interface standards
What is the output of the following code segment?
String[] cs = "Bill Gates and Paul Allen founded Microsoft on April 4, 1975.".split(" ");
System.out.println(cs[6].charAt(5));
Answers
Answer:
o
Explanation:
Should one own a smart home device
What are some security issues that one can find bothersome with these types of devices?
Answers
Yes, one can have or should one own a smart home device
Some security issues that one can find bothersome with these types of devices are:
Privacy concernsVulnerabilities to hackingLack of updatesWhat are the security issues?Smart home tools offer usefulness and can help create growth easier, but they further create freedom risks that should be deliberate.
Some freedom issues so that find bothersome accompanying smart home tools contain:
Lastly, in terms of Privacy concerns: Smart home ploys may accumulate individual dossier, such as custom patterns and choices, that could be joint accompanying after second-party parties for point or direct at a goal buildup or added purposes.
Learn more about security issues from
https://brainly.com/question/29477357
#SPJ1
Which of these is a Microsoft certification for system engineers
Answers
Answer: B. MCSE
Explanation:
Microsoft offers various courses and certifications for different careers in the IT industry. One such career is system engineering where the MCSE which stands for Microsoft Certified Solutions Expert is offered.
This certification proves that one is proficient with technologies such as server infrastructure, data platforms and business intelligence. Prospective careers apart from sound engineering include Network management and Database Analysis.
5
Jameela really likes building her own computing and gaming systems. When building the physical elements like the motherboard, what type of
technology is she MAINLY working with?
O A. software
OB. hardware
OC. social media
OD. IT services
Answers
Answer:
hardware
Explanation:
it is so because hardware are physically seen objects you can see and touch...
develop an algorithm to compute and print out the average of 3 numbers A,B,C
Answers
Answer:
Input: Take 3 numbers A, B and C
Processing: Find average of 3 numbers using formula: Average= A+B+C/3
Output: The output is Average of three numbers.
Explanation:
We need to write an algorithm to compute and print out the average of 3 numbers A,B,C
An algorithm has Input, Processing and Output
The algorithm required is:
Input: Take 3 numbers A, B and C
Processing: Find average of 3 numbers using formula: Average= A+B+C/3
Output: The output is Average of three numbers.
(01)²
what is 2 in this number
Answers
Answer and Explanation:
It's an exponent (2 is squared I believe)
When you have an exponent, multiply the big number by the exponent
Ex: \(10^2\)= 10x2=20
Ex: \(10^3\\\)= 10x3=30
FOLLOW INSTRUCTIONS BELOW , WRITTEN IN JAVA LANGUAGE PLEASE AND THANK YOU !
Project Descriptions
This project involves implementing two process scheduling algorithms. You will be
required to write a Java program to simulate FCFS and RR scheduling policies we
discussed in class. The simulator selects a task to run from a ready queue based on the
scheduling algorithm. Since the project intends to simulate a CPU scheduler, it does not
require any actual process creation or execution. The processes’ information is stored in a
text file.
When a task(process) is scheduled, the simulator will simply print out what task is
selected to run at a time. I have provided a sample run below.
The name of your Java program should be called CPUScheduler.java
The selected scheduling algorithms to implement in this project are:
Round Robin (RR)
First Come First Serve (FCSF)
The above algorithms are already described in class slides, class video recordings and
textbook Chapter 5.
Implementation
The implementation of this project should be completed in Java. Your program will read
information about processes from a text file. This supporting text file contains process
scheduling information such as the pid, arrival time and CPU burst time. Your program
should read in this information, insert the processes into a list, and invoke the scheduler.
Process information
The following example format of how your text file should look like:
P1 0 10
P2 1 8
P3 2 5
The first column represents a process ID. Process ID uniquely identifies a process.
The second column represents arrival time. This is the time when the process arrives
in the unit of milliseconds
The third column represents CPU burst. This is the CPU time requested by a time, in
the unit of milliseconds
Thus, P1 arrives at 0 and has a CPU burst of 10 milliseconds and so forth.
The program will be run from the command line where you provide the name of the file
where the processes are stored.
The simulator first reads task information from the input file and stores all data in a data
structure. Then it starts simulating one scheduling algorithm in a time-driven manner. At
each time unit (or slot), it adds any newly arrived task(s) into the ready queue and calls a
specific scheduler algorithm in order to select appropriate tasks from the ready queue.
When a task is chosen to run, the simulator prints out a message indicating what process
ID is chosen to execute for this time slot. If no task is running (i.e. empty ready queue), it
prints out an "idle" message. Before advancing to the next time unit, the simulator should
update all necessary changes in task and ready queue status.
Grading
110 Total points possible
5 follows good coding practices
5 Runs from the command line
10 Reads the processes from a text file
10 Program compiles successfully and runs
40 FCFS produces the correct output
40 RR produces the correct output
Good coding practices:
Your code must:
be commented
use meaningful variable, method, and class names
use proper indenting
use objects, as well as static and non-static variables and methods, properly
be readable
Sample Execution
Assume that you have created a file process.txt with the following data:
P0 0 3
P1 1 6
P2 5 4
P3 7 3
If you invoke your scheduler (executable CPUScheduler) using the command
java CPUScheduler process.txt 2
Note that in the above command, process.txt is the name of the file to
read from and 2 is the time slide for RR
then your program should have a behavior similar to the following:
-------------------------------------------------
CPU Scheduling Simulation
-------------------------------------------------
-------------------------------------------------
First Come First Served Scheduling
-------------------------------------------------
[0-3] P0 running
[3-9] P1 running
[9-13] P2 running
[13-16] P3 running
Turnaround times:
P0 = 3
P1 = 8
P2 = 8
P3 = 9
Wait times:
P0 = 0
P1 = 2
P2 = 4
P3 = 6
Response times:
P0 = 0
P1 = 2
P2 = 4
P3 = 6
Average turnaround time: 7.00
Average wait time: 3.00
Average response time: 3.00
-------------------------------------------------
Round Robin Scheduling
-------------------------------------------------
[0-2] P0 running
[2-4] P1 running
[4-5] P0 running
[5-7] P1 running
[7-9] P2 running
[9-11] P3 running
[11-13] P1 running
[13-15] P2 running
[15-16] P3 running
Turnaround times:
P0 = 5
P1 = 12
P2 = 10
P3 = 9
Wait times:
P0 = 2
P1 = 6
P2 = 6
P3 = 6
Response times:
P0 = 0
P1 = 1
P2 = 2
P3 = 2
Average turnaround time: 9.00
Average wait time: 5.00
Average Response time: 1.25
Answers
help!!!!!!
hhhhhhhhh

Answers
Answer:
A
Explanation:
15. What is the primary difference between how WPA2- Personal and WPA2-Enterprise are implemented on a network?
Answers
Answer:
The primary difference between WPA2-Personal and WPA2-Enterprise is in how the authentication process is handled.
WPA2-Personal uses a pre-shared key (PSK) method for authentication, where all users share the same password. This method is suitable for small home networks where there are a limited number of users.
On the other hand, WPA2-Enterprise uses a more complex method of authentication, such as the Extensible Authentication Protocol (EAP), to authenticate each individual user on the network. This method is more suitable for larger organizations with many users, as it provides greater security and control over network access. Additionally, WPA2-Enterprise requires the use of an authentication server, such as a RADIUS server, to manage user authentication.
Explanation:
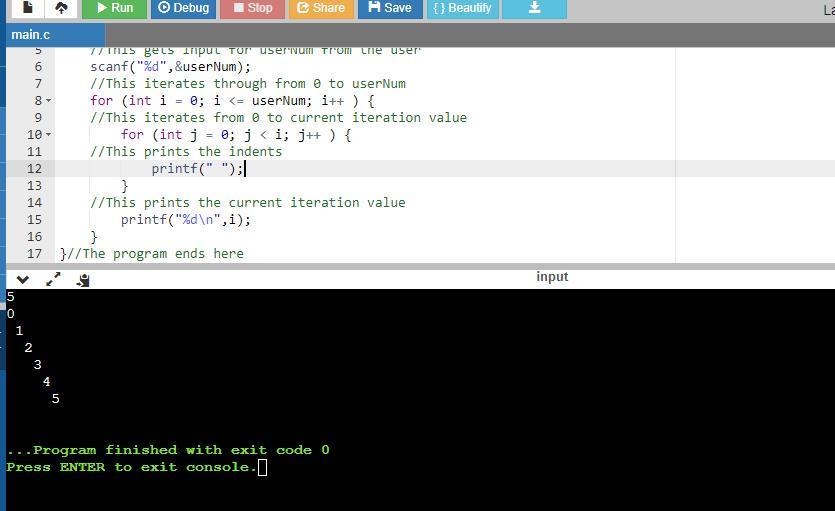
In C language. Print numbers 0, 1, 2, ..., userNum as shown, with each number indented by that number of spaces. For each printed line, print the
leading spaces, then the number, and then a newline. Hint: Use i and j as loop variables (initialize i and j explicitly). Note: Avoid any
other spaces like spaces after the printed number. Ex: userNum = 3 prints:
Answers
The program uses loops to print the numbers from 0 to the user input.
It also uses loops to print the indented space before each iteration value.
The program in C where comments are used to explain each line is as follows:
#include <stdio.h>
int main(){
//This declares userNum as integer
int userNum;
//This gets input for userNum from the user
scanf("%d",&userNum);
//This iterates through from 0 to userNum
for (int i = 0; i <= userNum; i++ ) {
//This iterates from 0 to current iteration value
for (int j = 0; j < i; j++ ) {
//This prints the indents
printf(" "); }
//This prints the current iteration value
printf("%d\n",i); }
}//The program ends here
At the end of the program, the program outputs the indent, followed by the iteration value and a new line.
See attachment for the program sample run
Read more about loops at:
https://brainly.com/question/21751160
Which computer was part of the first generation of computers?
O ENIAC
O Apple 11
O TRADIC
O UNIVAC
Answers
Answer:
ENIAC
Explanation:
It was one of the first vacuum tube computers
ENIAC computer was part of the first generation of computers. The correct option is A.
What is ENIAC?Completed in 1945, ENIAC was the first programmable, electronic, general-purpose digital computer.
These features were available on other computers, but the ENIAC offered them all in one convenient package. It could solve "a vast class of numerical problems" through reprogramming and was Turing-complete.
The ENIAC, created by John Mauchly and J. Presper Eckert, was the fastest computing system available at the time, capable of 5,000 additions per second, but it lacked internal storage, necessitating human programming for every new set of computations.
The first generation of computers included the ENIAC computer.
Thus, the correct option is A.
For more details regarding ENIAC, visit:
https://brainly.com/question/13385199
#SPJ2
QUESTION 1 Choose a term from COLUMN B that matches a description in COLUMN A. Write only the letter (A-L) next to the question number (1.1-1.10) in the ANSWER BOOK. COLUMN A 1.1. Substances that provide nourishment to the body 1.2. How you think and feel about something 1.3. Helps to cope with the challenges of being a student Exercise relating to increasing your heart rate 1.5. Having traits or qualities traditionally associated with 1.4. men 1.6. Seeing, hearing, or sensing something that is not really there 1.7. 1.8. Leaving everything till the last minute Is Chapter 2 in the Constitution of SA 1.9. Group of people who share notes and information 1.10. Ability to exercise for extended period of time COLUMN B A hallucination B nutrients C study group D procrastinate E endurance F Bill of Rights G Cardio-vascular H masculine I attitude J resilience K strength L flexibility
Answers
Answer:
1.1 B nutrients 1.2 I attitude 1.3 J resilience 1.4 H masculine 1.5 L flexibility 1.6 A hallucination 1.7 D procrastinate 1.8 F Bill of Rights 1.9 C study group 1.10 E endurance
Explanation:
If the decimal value is 45, binary value is
Answers
The binary representation of the decimal 45 is 101101.
Pls help I will give points

Answers
Answer:
Desktop
Explanation:
84 104 101 32 97 110 115 119 101 114 32 105 115 32 53 48 33 There's a way to make this meaningful; find it!
Answers
The question is about identifying the various ways of manipulating numbers. One of such is using following pair:
Input Format: Decimal ASCIITransformed Output String.Using the above process, the result given is 50.
What is ASCII?ASCII is the acronym for American Standard Code for Information Interchange.
Another way of approaching the above problem is by bucketizing.
The act of describing a problem, discovering the origin of the problem, finding, prioritizing, and selecting alternatives for a solution, and executing a solution is known as problem solving.
Similarly, bucketizing is a data organizing technique that decomposes the space from which geographic data is gathered into areas.
Some criteria for selecting area borders include the amount of things contained inside them or their physical arrangement (e.g. minimizing overlap or coverage).
A bucket data structure utilizes key values as bucket indices and stores things with the same key value in the appropriate bucket.
As a result, the job necessary to address the problem is completed.
Learn more bout Decimal ASCII:
https://brainly.com/question/26307436
#SPJ1
