Mixture Models and Digit Classification 3 points possible(graded) Assume that we have 100.000 black-and-white images of size 26 X 26 pixels that are the result of scans of hand-written digits between 0and 9. We can apply mixture models to effectively train a classifier based on clustering using the EM algorithm applied to the dataset. Identify the following parameters (according to notation developed in the lecture,assuming that we use all the data for training): K= 2 d= Submit You have used 0 of 2 attempts Save Note The Gaussian mixture model can be extended to the case where each mixture component has a general covariance matrix , The case that we have studied so far is a special case where = I, where I is the identity matrix of size d X d.The EM algorithm can also be extended to work in this general setting.
Answers
Using mixture models for classification in this scenario, we need to set the number of mixture components (K) to 10, which is equal to the number of distinct classes (0-9). Additionally, each image has 26 x 26 = 676 pixels, resulting in a feature vector dimensionality (d) of 676.
In this problem, we have hand-written digits between 0 and 9. When using mixture models for classification, the number of mixture components (K) should be equal to the number of distinct classes, in this case, 10.
Each image is of size 26 x 26 pixels, which results in a total of 26 * 26 = 676 pixels per image. Since the images are black-and-white, each pixel can be represented by a single value. Therefore, the dimensionality (d) of the feature vector for each image is 676.
When applying the EM algorithm to this dataset, the parameters K and d should be set to 10 and 676, respectively.
Learn more about EM algorithm visit:
https://brainly.com/question/31728897
#SPJ11
Related Questions
During Which model states that communication can occur simultaneously?
Answers
Answer:
i dont see any models...please include a picture
Define a function calc_pyramid_volume() with parameters base_length, base_width, and pyramid_height, that returns the volume of a pyramid with a recta
Answers
Answer:
Te ayuda
Explanation:¿Cuál es la fórmula para calcular el volumen de una pirámide rectangular?
Resultado de imagen para Defina una función calc_pyramid_volume() con los parámetros base_length, base_width y pyramid_height, que devuelve el volumen de una pirámide con una recta
El volumen de una pirámide rectangular es definido como el espacio tridimensional ocupado por esta figura. Podemos calcular la medida de este volumen al multiplicar al área de la base por la altura de la pirámide y dividir por tres.
A company is monitoring the number of cars in a parking lot each hour. each hour they save the number of cars currently in the lot into an array of integers, numcars. the company would like to query numcars such that given a starting hour hj denoting the index in numcars, they know how many times the parking lot reached peak capacity by the end of the data collection. the peak capacity is defined as the maximum number of cars that parked in the lot from hj to the end of data collection, inclusively
Answers
For this question i used JAVA.
import java.time.Duration;
import java.util.Arrays;;
class chegg1{
public static int getRandom (int min, int max){
return (int)(Math.random()*((max-min)+1))+min;
}
public static void display(int[] array){
for(int j=0; j< array.length; j++){
System.out.print(" " + array[j]);}
System.out.println("----TIME SLOT----");
}
public static void main(String[] args){
int[] parkingSlots= new int[]{ -1, -1, -1, -1, -1 };
display(parkingSlots);
for (int i = 1; i <= 5; i++) {
for(int ij=0; ij< parkingSlots.length; ij++){
if(parkingSlots[ij] >= 0){
parkingSlots[ij] -= 1;
}
else if(parkingSlots[ij]< 0){
parkingSlots[ij] = getRandom(2, 8);
}
}
display(parkingSlots);
// System.out.println('\n');
try {
Thread.sleep(2000);
} catch (InterruptedException e) {
e.printStackTrace();
}
}
}
}
output:
-1 -1 -1 -1 -1----TIME SLOT----
8 6 4 6 2----TIME SLOT----
7 5 3 5 1----TIME SLOT----
6 4 2 4 0----TIME SLOT----
5 3 1 3 -1----TIME SLOT----
4 2 0 2 4----TIME SLOT----
You can learn more through link below:
https://brainly.com/question/26803644#SPJ4
Use what you know about the properties of metal to explain why you think it is incredibly dangerous and potentially deadly to stick something metal in an electrical outlet.
Answers
It is incredibly dangerous and potentially deadly to stick something metal in an electrical outlet because metals are conductors of electricity.
Metals are known to be the best conductors of electricity. An electrical outlet will have electrons in abundance present.
When a metal is stuck to an electrical outlet, it will begin to conduct electricity. As metals are good conductors, the flow of electrons for electrical conduction would be heavy.
A person who touches the metal will experience an electrical shock that would be life-threatening and dangerous. Hence, due to the high conductivity of metals, when they are stuck to an electrical outlet, they can be potentially deadly.
To learn more about metal, click here:
https://brainly.com/question/4701542
#SPJ4
nowadays, which is more effective and efficient to use, the manual database or manual database? explain
Answers
Answer:
Advantages of Electronic Databases over Manual databases
Electronic databases make it easier to query, search, filter and retrieve required data. Electronic databases allow centralised use of information amongst many users over a network and therefore reduce duplication, e.g in banks.
2.17.5 coders answers
Answers
Answer:
start();
if(colorIs(Color.blue)){
paint(Color.red);
if(frontIsClear());
move();
}else{
if(colorIs(Color.red)){
paint(Color.blue);
if(frontIsClear());
move();
}
}
if(colorIs(Color.blue)){
paint(Color.red);
if(frontIsClear());
move();
}else{
if(colorIs(Color.red)){
paint(Color.blue);
if(frontIsClear());
move();
}
}
if(colorIs(Color.blue)){
paint(Color.red);
if(frontIsClear());
move();
}else{
if(colorIs(Color.red)){
paint(Color.blue);
if(frontIsClear());
move();
}
}
if(colorIs(Color.blue)){
paint(Color.red);
if(frontIsClear());
move();
}else{
if(colorIs(Color.red)){
paint(Color.blue);
if(frontIsClear());
move();
}
}
if(colorIs(Color.blue)){
paint(Color.red);
if(frontIsClear());
move();
}else{
if(colorIs(Color.red)){
paint(Color.blue);
if(frontIsClear());
move();
}
}
if(colorIs(Color.blue)){
paint(Color.red);
if(frontIsClear());
move();
}else{
if(colorIs(Color.red)){
paint(Color.blue);
if(frontIsClear());
move();
}
}
if(colorIs(Color.blue)){
paint(Color.red);
if(frontIsClear());
move();
}else{
if(colorIs(Color.red)){
paint(Color.blue);
if(frontIsClear());
move();
}
}
if(colorIs(Color.blue)){
paint(Color.red);
if(frontIsClear());
move();
}else{
if(colorIs(Color.red)){
paint(Color.blue);
if(frontIsClear());
move();
}
}
if(colorIs(Color.blue)){
paint(Color.red);
if(frontIsClear());
move();
}else{
if(colorIs(Color.red)){
paint(Color.blue);
if(frontIsClear());
move();
}
}
if(colorIs(Color.blue)){
paint(Color.red);
if(frontIsClear());
}else{
if(colorIs(Color.red)){
paint(Color.blue);
if(frontIsClear());
}
}
function start(){
}
Q. 5.1.3: Move to Wall
Ans:
function start(){
while(frontIsClear()){
move();
}
}
I apologize if its incorrect
Computer and Network Security
Total word count must be 250 to 300 words in your posting
Who ultimately has ultimate responsibility for the computer security policies and organization implements and why? Consider the data owner, system owner, executive management, CIO, CEO, and the company’s Board members? Which of the social engineering scams do you find the most interesting? Have any you ever been the victim
Answers
Computer and network security is essential to any organization, and the person who has ultimate responsibility for security policies and organization implementation is the Chief Information Officer (CIO) in a company.
The CIO is responsible for ensuring that the company's computer systems are secure and free from attacks.The CIO collaborates with the data owner, system owner, executive management, CEO, and the company's board members to ensure that all security policies are in place and implemented correctly.
They also establish a security culture that promotes security awareness throughout the organization. The CIO sets policies for access control, data protection, network security, and other security measures. They have a team of security professionals who report to them, and they are ultimately responsible for ensuring the security of the company's systems and data. In today's digital world, where social engineering attacks have increased, everyone is vulnerable to these scams.
To know more about security visit:
https://brainly.com/question/33632906
#SPJ11
num_boxes = 0 num_apples = 9 if num_apples < 10: if num_apples < 5: num_boxes = 1 else: num_boxes = 2 elif num_apples < 20: num_boxes = num_boxes 1
Answers
In the first snippet, `num_boxes` will be 2.
In the second snippet, `num_boxes` will be 2.
Based on the given code snippets:
1. Initially, `num_boxes` is assigned a value of 0.
The condition `num_apples < 10` is true (since `num_apples` is 9), so the code inside the if statement is executed. It sets `num_boxes` to 2.
2. Initially, `num_boxes` is assigned a value of 0.
The condition `num_apples < 10` is true (since `num_apples` is 9), so it enters the if statement.
The nested condition `num_apples < 5` is false, so it goes to the else part. `num_boxes` is then assigned a value of 2. Since `num_apples` is less than 20, the code block inside the elif statement is not executed. Therefore, the final value of `num_boxes` remains as 2.
Learn more about If statement here:
https://brainly.com/question/33442046
#SPJ4
The Complete question is:
Determine the final value of num_boxes.
1. num_boxes = 0
num_apples = 9
if num_apples < 10:
num boxes 2
if num_apples < 20:
num_boxes = num boxes +
2. num_boxes = 0
num_apples = 9
if num_apples < 10:
if num_apples < 5:
2
num boxes 1
else:
num boxes = 2
elif num_apples< 20:
num boxes
= num_boxes + 1
solve plz
Jenae helps maintain her school web site and needs to create a web site poll for students. Which tool will she use?
JavaScript
HTML
CSS
Text editor
Answers
Answer:
HTML
Explanation:
HTML is used is making web pages.
Answer:
what
Explanation:
i’m failing this class and i’m stuck on this one, this is the code from the last lesson:
def GPAcalc(grade, weighted):
grade = grade.lower()
dictionary = {"a":4, "b":3, "c":2, "d":1, "f":0}
if weighted == 1 and grade in dictionary:
return "Your GPA score is: " + str(dictionary[grade] + 1)
elif weighted == 0 and grade in dictionary:
return "Your GPA score is: " + str(dictionary[grade])
else:
return"Invalid"
print(GPAcalc(input("Enter your Letter Grade: "), int(input("Is it weighted? (1 = yes, 0 = no) "))))
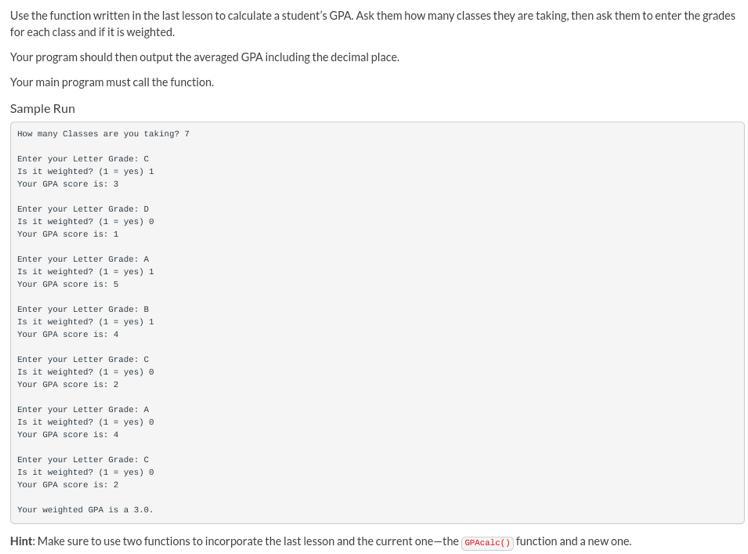
Answers
lst=([])
def avgGPA(lst1):
total = 0
count = 0
for x in lst:
if type(x) == int:
total += x
count += 1
return total/count
def GPAcalc(grade, weighted):
grade = grade.lower()
dictionary = {"a": 4, "b": 3, "c": 2, "d": 1, "f": 0}
if weighted == 1 and grade in dictionary:
lst.append(dictionary[grade]+1)
return "Your GPA score is: " + str(dictionary[grade] + 1)
elif weighted == 0 and grade in dictionary:
lst.append(dictionary[grade])
return "Your GPA score is: " + str(dictionary[grade])
else:
lst.append("Invalid")
return "Invalid"
classes = int(input("How many Classes are you taking? "))
i = 0
while i < classes:
print(GPAcalc(input("Enter your Letter Grade: "), int(input("Is it weighted? (1 = yes) "))))
i += 1
print("Your weighted GPA is a "+str(avgGPA(lst)))
If you need me to change any code, I'll do my best. I hope this helps!
Which technological innovation had the most impact on settlement processes in both the united states and canada?.
Answers
The most likely reason for the emergence of a megalopolis is its proximity to key transportation corridors and economic growth.
A new or enhanced product or procedure with considerably better technological features is referred to as a technological innovation. New products (product innovations) or processes (process innovations) that have been commercialized constitute technologically implemented product innovations. Innovation in technology benefits society. By bringing new, better products and services to the populace, it raises productivity and raises the level of living for everyone. Innovation's advantages sometimes take time to manifest. As industries expanded as a result of the Industrial Revolution, there was an urban labor shortage.
Learn more about technological here-
https://brainly.com/question/15059972
#SPJ4
you are the administrator of a network with a single active directory domain. the domain includes two domain controllers. your company's security policy requires that locked out accounts are unlocked by administrators only. upon reviewing the account lockout policy, you notice the account lockout duration of 99999. you need to configure your domain's account lockout policy to comply with your company's security policy. what should you do next?
Answers
Then, I would guarantee that only administrators have the authority to unlock accounts, and I would shorten the account lockout length to something more manageable, like 30 minutes or an hour.
Then, I would guarantee that only administrators have the authority to unlock accounts, and I would shorten the account lockout length to something more manageable, like 30 minutes or an hour.
Users may recover access to their accounts without getting in touch with an administrator if the account lockout length was decreased to a more acceptable amount, like 30 minutes or an hour. This would still deter brute force attempts. To further restrict unwanted access to user accounts, make sure that only administrators have the authority to unlock accounts. The domain would comply with the company's security policy by making these adjustments.
learn more about account here:
https://brainly.com/question/29970290
#SPJ4
The library is purchasing Argus TL2530P All-In-One Thin clients. What does it mean that the thin clients are 802.3at compliant?
Answers
In this set up, the servers are workstations which perform computations or provide services such as print service, data storage, data computing service, etc. The servers are specialized workstations which have the hardware and software resources particular to the type of service they provide.
1. Server providing data storage will possess database applications.
2. Print server will have applications to provide print capability.
The clients, in this set up, are workstations or other technological devices which rely on the servers and their applications to perform the computations and provide the services and needed by the client.
The client has the user interface needed to access the applications on the server. The client itself does not performs any computations while the server is responsible and equipped to perform all the application-level functions.
Each server handles a smaller number of thin clients since all the processing is done at the server end. Each server handles more thick clients since less processing is done at the server end.
Learn more about server on:
https://brainly.com/question/29888289
#SPJ1
A speed limit sign that says "NIGHT" indicates the _____ legal speed between sunset and sunrise.
Answers
Answer:
Maximum
Explanation:
Speed limits indicate the maximum speed you are legally allowed to drive.
What is the scope of the variable capacity?
class raft:
def __init__(self,capacity):
self.capacity = capacity
self.location = 'Gauley'
self.repairs = []
def __str__(self):
result = "Capacity: " + str(self.capacity)
result = result + "\n Location:" + self.location
result = result + "\nRepairs:"
if len(self.repairs) < 1:
result = result +"No repairs were needed."
else:
for item in self.repairs:
result = result + item + '\n'
return result
myRaft = raft(30)
print(myRaft)
Responses
#1 limit to the method __init__
#2 limited to the method __str__
#3 accessible to the entire program
#4 limited to the raft class
Answers
The scope of the variable "capacity" in the given code is (#4) limited to the "raft" class. This means that the variable can be accessed and used within the class, but not outside of it.
In the code, the variable "capacity" is defined as a parameter in the constructor method (__init__) of the "raft" class. This means that whenever a new object of the "raft" class is created, the "capacity" value needs to be provided.
The variable "capacity" is then stored as an instance variable, using the "self" keyword, which makes it accessible to all methods within the class. This includes the "__str__" method, where it is used to generate the string representation of the object.
However, since the variable is not defined as a global variable or passed as an argument to other functions or methods, it cannot be accessed outside of the class. It is specific to the "raft" class and can only be used within its methods.
So, in summary, the scope of the variable "capacity" is limited to the "raft" class and it is accessible within all methods of the class.
For more Questions on variable
https://brainly.com/question/29360094
#SPJ8
You make me the happiest person on earth
i feel joy when i see your face
when i am depressed all i have to do is to think about you and it puts me in a good mood.
do i need to add more to thut
Answers
Answer:
Fixed
Explanation:
I feel joy when I see your face
When I'm depressed all I have to do is to think about you, and it puts me in a good mood.
The first generation of computers used microprocessors. false true
Answers
Answer:
False.
Explanation:
The first generation of computers used something called vacuum tubes. Microprocessors weren't used for many years later until the fourth generation.
objects in object oriented programming are designed to do things and to know things. what terminology do we use in object oriented programming to describe the functionality that does things for an object like scanner? scanner in
Answers
In Object Oriented Programming, the functionality that does things for an object like a scanner is known as its "methods". These methods define the actions that can be performed on the object and provide a way for the object to interact with the outside world.
In object-oriented programming, the term "method" is used to describe the functionality that performs actions or "does things" for an object like a scanner. A method is essentially a piece of code that is associated with an object and provides the object with the ability to perform a specific task. For example, a scanner object may have a method called "scan" that, when invoked, takes a physical document and converts it into a digital representation. Another method may be called "save" that saves the digital representation of the scanned document to a file on disk. The methods associated with an object are part of the object's interface and allow users of the object to interact with it and make use of its functionality.
To know more about Object Oriented Programming Please click on the given link
https://brainly.com/question/30122096
#SP4
Most information on social media has been reviewed by experts.
True
False
Answers
False
Explanation:Information on social media cannot be trusted to be accurate.
Social Media
Social media is widely accessible to almost anyone. This means that anyone can post any information on social media. Additionally, this information is rarely reviewed by anyone, especially not experts. Information on social media is commonly inaccurate because anyone, even those without expertise, can post information freely.
Trustworthy Sources
Social media is not a trustworthy source, but there are many other sources you can use for research. For example, websites with .edu or .gov are often reviewed by experts and can be trusted. Furthermore, academic journals and databases have peer-reviewed sources. This means that all of the information has been reviewed by experts. Both of these sources are more trustworthy and accurate than social media.
Answer:
B. False Most information on social media has'nt been reviewed by experts.
Explanation:
How do I convert BCD to denary and denary to BCD? (For Both positive and Negative integer of denary)
Answers
Answer:
BCD is very similar to regular binary code. Decimal digits are represented as binary like so:
0 = 0000
1 = 0001
2 = 0010
3 = 0011
etc...
9 = 1001
However, in BCD the structure of decimal code is maintained, so e.g., the number 123 would be encoded digit-by-digit as:
0001 0010 0011
whereas in pure binary it would be encoded as
01111011
So you immediately see that BCD is not so efficient. That's why it is not used very often. Encoding and decoding is very easy as you take the same approach as with pure binary, but perform it per digit (ie., per group of 4 bits).
Please help urgently i will give 61 points

Answers
Web browsers can be used to access the internet.
What is a short history of web browsers?When we talk of the web browsers we are talking about the kind of applications that we can use to access pages on the web. Today there are so many of such applications that we can be able to use search for pages on the web.
The initial attempts at web browsers were the hyperlinked applications that were produced by Tim Berners-Lee during the mid and late 1980s and 1990.
Today, we have a lot of the web browsers in use like the Chrome, Safari, Internet Explorer (IE), Firefox, and Opera.
Learn more about web browsers:https://brainly.com/question/9776568
#SPJ1
A site has been issued the ip address of 192. 168. 10. 0/24. The largest network contained 100 hosts and was given the lowest numbered network number possible. The second largest network has 60 hosts. If it is given the next network number, what network number and mask will be assigned to the second largest network?
Answers
The network number and mask assigned to the second largest network would be 192.168.10.128/26.
The site has been assigned the IP address of 192.168.10.0/24, which means that it has been allocated 256 IP addresses, ranging from 192.168.10.0 to 192.168.10.255.
The largest network contained 100 hosts, so it requires 7 bits for the host part of the address (2^7 - 2 = 126 usable hosts). This leaves 24 - 7 = 17 bits for the network part of the address, which gives us 2^17 = 131,072 possible network addresses. The lowest numbered network number possible for this network size is 192.168.10.0/25 (subnet mask of 255.255.255.128).
The second largest network has 60 hosts, so it requires 6 bits for the host part of the address (2^6 - 2 = 62 usable hosts). This leaves 24 - 6 = 18 bits for the network part of the address, which gives us 2^18 = 262,144 possible network addresses. The next network number would be 192.168.10.128/26 (subnet mask of 255.255.255.192).
Therefore, the network number and mask assigned to the second largest network would be 192.168.10.128/26.
To learn more about network number
https://brainly.com/question/29506804
#SPJ11
In which phase of the ethical hacking methodology would a hacker be expected to discover available targets on a network
Answers
Answer:
Scanning and enumeration.
Explanation:
In the scanning and enumeration phase of the ethical hacking methodology, a hacker would be expected to discover available targets on a network.
The scanning and enumeration phase of the ethical hacking follows the reconnaissance phase and it typically involves discovering available targets on a network for informations such as username, password, IP address etc.
what channel does the news come on?
i dont have cable i have roku :\
Answers
Answer:
I have roku to
Explanation:
I think there's is a channel for it just search up news it probs come up
To find the item with the lowest cost in column C, what Excel formula should be used in C11? SUM (C3:C10) =MAX (C4:C10) MIN (C3:C10) =MIN (C4:C10)
Answers
Answer:
The correct excel formula to use can't be sum cause that's addition of everything in the column. It can't be Max cause that's for the highest. Depending on where the values start, it could be either MIN(C3:C10) or MIN(C4:C10)
The correct Excel formula to find the item with the lowest cost in column C would be =MIN(C3:C10).
The MIN function in Excel is used to find the minimum value in a range of cells. In this case, we want to find the lowest cost in column C, so we use the MIN function with the range C3:C10. This will compare the values in cells C3 to C10 and return the smallest value.
When you enter the formula =MIN(C3:C10) in cell C11, Excel will evaluate the range C3:C10 and return the smallest value in that range. It will display the item with the lowest cost from column C.
By using the MIN function in Excel, you can easily identify the item with the lowest cost in a given range of cells. This is useful for analyzing data and making decisions based on the minimum value in a set of values. Excel provides a range of functions to perform calculations and analyze data, making it a powerful tool for managing and manipulating numerical information.
To know more about Excel Formula, visit
https://brainly.com/question/20497277
#SPJ11
You want to create a new system account for a server program you’re installing. What option can you pass to useradd when creating the account to ensure that it’s created as a system account?
Answers
When creating the account, you can use the --system option to tell useradd to create it as a system account.
A program or utility that runs from the command line is known as a Linux command. An interface that accepts lines of text and converts them into instructions for your computer is known as a command line.
A graphical user interface (GUI) is simply a command-line program abstraction. For instance, a command is carried out every time you click the "X" to close a window. We can give the command you run options by using a flag.
Learn more about linux https://brainly.com/question/15122141
#SPJ4
The option that ensure that it’s created as a system account is system. The correct option is A.
What is system account?A local system account is a user account created by an operating system during installation and used for purposes defined by the operating system.
User IDs for system accounts are frequently pre-defined (e.g. the root account in Linux.) The line between system and service accounts is sometimes blurred.
As the person is trying to create a new system account for a server program, System can help to pass to user end when creating the account to ensure that it’s created as a system account.
Thus, the correct option is A.
For more details regarding system account, visit:
https://brainly.com/question/14989055
#SPJ1
Your question seems incomplete, the missing options are:
A. --system
B. --nonuser
C. --sysaccount
D. --shared
E. --nohome
What term is used to describe how mobile computing allows individuals to initiate real-time contact with other systems anywhere, any time since they carry their mobile device everywhere?.
Answers
The term "broad reach" refers to mobile computing enables consumers to initiate real-time contact to other systems at any time and from any location because they bring their mobile device with them at all times.
What is meant by the term mobile computing?Mobile computing is the set of IT technologies, goods, services, operational strategies, and procedures that allow end users to utilize computation, information, and related capabilities and resources while on the move. Mobile access is most commonly used to describe access while on the move, where the consumer is not constrained to a specific geographic location.Mobile access can also refer to availability in a single position via equipment which users can move as needed but remains stationary while in use. This type of operation is commonly referred to as nomadic computing.Mobile technology is now ubiquitous. It has applications in the consumer and commercial markets, as well as the industrial as well as entertainment industries and a variety of specialized vertical markets.Thus, "broad reach" is known as the mobile computing which enables consumers to initiate real-time contact to other some other systems at any time and from any location because they bring their mobile device with them at all times.
To know more about mobile technology, here
https://brainly.com/question/29106845
#SPJ4
A file extension of .mp4 means that the file contains what?
Answers
Answer:
It's a highly versatile and compressed video format that also can store audio, subtitles, and still images.
Explanation:
It contains video, audio and text.
Answer:
Imma let you know that it is NOT D i got it wrong on my test
Explanation:
i got it wrong on my test
To make a profit the price of the items sold in the furniture store are marked up by 80 %after marking up the prices each item is put on the sale of 10%design algorithm to convert find the selling price of the items sold in the furniture store.
Answers
Answer:
The algorithm is as follows:
1. Start
2. Display "Input Item Price: "
3. Input Price
4. Markup = Price + 80% * Price
5. Selling_Price = 10% * Markup
6. Display "The Selling Price is "+Selling_Price
7. Stop
Explanation:
This signals the beginning of the algorithm
1. Start
This is a prompt that asks for the price of the item
2. Display "Input Item Price: "
This gets the price of the item
3. Input Price
This calculates the Markup (80% of the inputted price)
4. Markup = Price + 80% * Price
This calculates the selling price (10% of the markup)
5. Selling_Price = 10% * Markup
This prints the selling price
6. Display "The Selling Price is "+Selling_Price
This signals the end of the algorithm
7. Stop
how many bits are contained in 1 terabyte of storage
Answers
In 1 terabyte of storage, there are 8,796,093,022,208 bits.
To reach this calculation, we can start with the knowledge that there are 8 bits in 1 byte. Since there are 1,099,511,627,776 bytes in 1 terabyte (as 1 terabyte is equal to 1024 gigabytes and 1 gigabyte is equal to 1024 megabytes and so on), we can multiply this number by 8 to determine the total number of bits in 1 terabyte. Therefore, 1 terabyte of storage contains 8,796,093,022,208 bits.The unit "terabyte" is commonly used to measure digital storage capacity. It is equal to 1,099,511,627,776 bytes, as 1 terabyte is equal to 1024 gigabytes, 1 gigabyte is equal to 1024 megabytes, and so on. Each byte consists of 8 bits. Therefore, to calculate the number of bits in 1 terabyte of storage, we can multiply the number of bytes by 8. By doing so, we find that there are 8,796,093,022,208 bits in 1 terabyte.
In summary, 1 terabyte of storage contains 8,796,093,022,208 bits. This can be calculated by multiplying the number of bytes in 1 terabyte by 8, as each byte consists of 8 bits.
To know more about terabyte, Visit:
https://brainly.com/question/30390418
#SPJ11