Lower-level subtypes inherit all attributes and relationships from its upper-level supertypes. Group of answer choices foreign keys date types relationships from its lower-level supertypes. relationships from its upper-level supertypes
Answers
In this talk, we'll take a closer look at a specific and crucial kind of decision in data modelling.
Thus, In order to enable our E-R diagrams to display multiple alternatives simultaneously, we offer a specific convention subtyping.
Subtyping will be helpful for controlling complexity as well as for succinctly expressing rules and limitations. We focus on conceptual modelling in this discussion, with logical modelling difficulties receiving only passing attention.
It is crucial to understand that the generalization level we choose will have a significant impact not just on the database but also on the overall system's design.
Thus, In this talk, we'll take a closer look at a specific and crucial kind of decision in data modelling.
Learn more about Data modelling, refer to the link:
https://brainly.com/question/31086794
#SPJ4
Related Questions
1) A ______ is a block of code that when run produces an output.
2) A _________ represents a process in a flowchart.
Answers
1) A function is a block of code that when executed produces an output.
2) A rectangle represents a process in a flowchart, signifying a specific task or operation within the overall process.
1) A function is a block of code that when run produces an output.
A function is a reusable block of code that performs a specific task. It takes input, performs operations, and produces an output. Functions help in modularizing code, improving code reusability, and enhancing readability. By encapsulating a specific task within a function, we can easily call and execute that code whenever needed, producing the desired output.
2) A rectangle represents a process in a flowchart.
In flowchart diagrams, different shapes are used to represent different elements of a process. A rectangle is commonly used to represent a process or an action within the flowchart. It signifies a specific task or operation that is performed as part of the overall process. The rectangle typically contains a description or label that indicates what action or process is being performed. By using rectangles in flowcharts, we can visually represent the sequence of steps and actions involved in a process, making it easier to understand and analyze.
learn more about code here:
https://brainly.com/question/20712703
#SPJ11
Which of the following does not properly nest control structures?
Pilihan jawaban
for i in range(3):
for j in range(6):
print(j)
for i in range(3):
if i > 2:
break
else:
print(i)
count = 0
if count < 10:
for i in range(3):
print(count)
count = count + 1
count = 10
for i in range(3):
if count > 0:
print(i)
else:
print(count)
Answers
Using the knowledge in computational language in python it is possible to write a code that following the properly nest control structures.
Writting the code:# Prints out the numbers 0,1,2,3,4
for x in range(5):
print(x)
# Prints out 3,4,5
for x in range(3, 6):
print(x)
# Prints out 3,5,7
for x in range(3, 8, 2):
print(x)
while count < 5:
print(count)
count += 1 # This is the same as count = count + 1
How to iterate over range Python?
To loop through a set of code a specified number of times, we can use the range() function, The range() function returns a sequence of numbers, starting from 0 by default, and increments by 1 (by default), and ends at a specified number.
See more about python at brainly.com/question/18502436
#SPJ1

According to the video, what tasks do Carpenters commonly perform? Select four options. supervising Plumbers, Electricians, and Roofers forming walls and flooring out of concrete cutting, shaping, and fastening wood installing rafters, joists, windows, and subflooring operating heavy equipment setting hardwood floors building kitchen cabinets painting interior walls and cabinets
Answers
Answer:
Cutting, shaping, and fastening wood.
Installing rafters, joists, windows, and subflooring.
Setting hardwood floors.
Building kitchen cabinets.
Answer:
- Cutting, shaping, and fastening wood.
- Installing rafters, joists, windows, and sub-flooring
- Setting hardwood floors
- Building kitchen cabinets
___________________________________________________________
With _____, human thinking and problem-solving is performed by a machine, including learning, reasoning, and self-correction. wearable technologies quantum computers artificial intelligence Moore's Law
Answers
Answer:
THE ANSWER IS B
Explanation:
Nathaniel is creating a concept map for his upcoming history test. His class has been studying the American Revolution, and he wants to better understand the connection between the important dates, people, and events that are discussed in his textbook.
What is the best way for Nathaniel to organize his concept map?
“American Revolution” should be central, and important events should connect to that.
“1776” should be central, and famous people should connect to that.
“United States” should be central, and “American Revolution” should connect to that.
“Freedom” should be central, and the names of the Founding Fathers should connect to that.
Answers
Answer:
The best possible answer is:
American Revolution” should be central, and important events should connect to that
The explanation to the answer is given below.
Explanation:
American Revolution” should be central, and important events should connect to that because
we are studying American Revolution, this should be the central topic.
There is no point in centering 1776 or United state because the are not the main focused topic they are only general topics.
Answer:
A
Explanation:
Right on edge 2021
Which of the following does not contribute to the increasing vulnerability of organizational information resources?
a. International organized crime taking over cybercrime b. Smaller, faster, cheaper computers and storage devices c. Additional management support d. Today's interconnected, interdependent, wirelessly networked business environment
e. Decreasing skills necessary to be a computer hacker
Answers
A statement which does not contribute to the increasing vulnerability of organizational information resources is: c. Additional management support.
What is information security?Information security can be defined as a preventive practice which is typically used for the protection of an information system (IS) that make use, store, and transmit information, from potential attack, damage, theft by thieves, or unauthorized access, especially through the use of a body of technologies, encryption, frameworks, processes and network engineers.
What is vulnerability?Vulnerability is any form of weakness, flaw, or defect that is found in a computer system, website, network, or software application, which can be exploited by an attacker or a hacker, in order to gain an unauthorized access and privileges to sensitive user data and information that are stored in a computer system.
In Computer technology, increasing the skills that are necessary to be a computer hacker would most likely increase the vulnerability of all organizational information resources.
Read more on vulnerability here: brainly.com/question/17094626
#SPJ1
List some of the icons present in Microsoft Windows 7 desktops.
Answers
Answer:
Common desktop icons include Computer, your personal folder, Network, the Recycle Bin, Internet Explorer, and Control Panel.
Explanation:
Assume a connection with RTT=100ms, MSS=1460 bytes. Ignoringoverhead spent on headers, calculate the transfer time and theeffective throughput for transferring a 500 KB file. Assume thereare no losses and that both the connection bandwidth and thereceiver window are infinite (and in particular,not limited to64K).
(a) Calculate the transfer time for TCP using slow start
(b) Calculate the transfer time supposing TCP used additiveincrease, starting with a window size of 1 MSS and increasing it by1 MSS every RTT.
Answers
(a) The transfer time for TCP using slow start is approximately 6.8 seconds.
(b) The transfer time for TCP using additive increase, starting with a window size of 1 MSS and increasing it by 1 MSS every RTT, is approximately 2.3 seconds.
Explanation:
To calculate the transfer time and effective throughput for transferring a 500 KB file, we first need to calculate the number of packets required to transmit the file. This can be done as follows:
Number of packets = 500 KB / 1460 bytes per packet ≈ 342 packets
(a) To calculate the transfer time for TCP using slow start, we assume that the initial congestion window size is 1 MSS, and doubles for every RTT until the maximum receiver window size is reached. In this case, the maximum receiver window size is not limited to 64K, so we can assume that the congestion window size will eventually reach the maximum receiver window size. The total transfer time can be calculated as:
Transfer time = RTT * (log2 342 + 1) ≈ 6.8 seconds
(b) To calculate the transfer time for TCP using additive increase, we assume that the congestion window size starts at 1 MSS and is increased by 1 MSS every RTT until the maximum receiver window size is reached. The total transfer time can be calculated as:
Transfer time = RTT * (ceil(342 / w) * w) / w, where w is the window size in MSS
Assuming a starting window size of 1 MSS and increasing by 1 MSS every RTT, the transfer time can be calculated as:
Transfer time = RTT * (ceil(342 / 1) * 1) / 1 ≈ 2.3 seconds
Note that the effective throughput for both slow start and additive increase can be calculated as the total amount of data transferred divided by the transfer time. In this case, since there are no losses and the connection bandwidth and receiver window are both infinite, the effective throughput is equal to the sending rate of the sender, which is simply the MSS divided by the round-trip time:
Effective throughput = MSS / RTT = 1460 bytes / 0.1 seconds ≈ 14.6 Mbps
To know more about TCP click here:
https://brainly.com/question/27975075
#SPJ11
URGENT! REALLY URGENT! I NEED HELP CREATING A JAVASCRIPT GRAPHICS CODE THAT FULFILLS ALL THESE REQUIREMENTS!

Answers
In the program for the game, we have a garden scene represented by a green background and a black rectangular border. The cartoon character is a yellow circle with two black eyes, a smiling face, and arcs for the body. The character is drawn in the center of the screen.
How to explain the informationThe game uses Pygame library to handle the graphics and game loop. The garden is drawn using the draw_garden function, and the cartoon character is drawn using the draw_cartoon_character function.
The game loop continuously updates the scene by redrawing the garden and the cartoon character. It also handles user input events and ensures a smooth frame rate. The game exits when the user closes the window.
This example includes appropriate use of variables, a function definition (draw_garden and draw_cartoon_character), and a loop (the main game loop). Additionally, it meets the requirement of using the entire width and height of the canvas, uses a background based on the screen size, and includes shapes (circles, rectangles, arcs) that are used appropriately in the context of the game.
Learn more about program on
https://brainly.com/question/23275071
#SPJ1
Any description of the goods which is made part of the basis of the bargain creates an express warranty that the goods shall conform to the description.
True
False
Answers
Any description of the goods which is made part of the basis of the bargain creates an express warranty that the goods shall conform to the description is true
What is express warranty?This sort of warranty is commonly seen on product packaging or warranty cards. An express warranty can be created by any statement, promise, description of goods, or sample which must conform to the guarantee claimed by a seller while selling any product
Elements in an express warranty case may include: The plaintiff purchased a product. The defendant gave an express warranty by way of a description of the product, a promise, or a fact. The product failed to perform according to the seller's description
An express warranty can take several different forms, whether spoken or written, and is basically a guarantee that the product will meet a certain level of quality and reliability. If the product fails in this regard, the manufacturer will fix or replace the product for no additional charge
To learn more about express warranty refers to:
brainly.com/question/15564074
#SPJ4
Which of the following behaviors is considered ethical?
A. copying another user’s password without permission
B. hacking software to test and improve its efficiency
C. using a limited access public computer to watch movies
D. deleting other user’s files from a public computer
Answers
Answer:
answer is c. using a limited access public computer to watch movies
Answer:
using a limited access public computer to watch movies
Explanation:
It is the only one that will not get you in big trouble
Give 2 example of application software and three advantages and disadvantages
Answers
The concurrent model in the software engineering has been defines the series of the events that will trigger the transition from the state to state for each of the software engineering activities.
What is the use of concurrent model?The concurrent model has been used for the development of the client server applications. The advantages of this model are the following has that it has easy to the implement, the server TCP/IP logic has the simple and one listener has shared by many TPs.
The drawbacks of the model is that it increased the network overhead and delays due to the requirement of the TRM exchange and more CPU and resource intensive than is the Iterative model.
Therefore,The concurrent model in the software engineering has been defines the series of the events that will trigger the transition from the state to state for each of the software engineering activities.
Learn more about concurrent model on:
https://brainly.com/question/4237375
#SPJ1
List any two features of this computer
h. Who invented Electronic Discrete Variable Automatic Computer?
Answers
Answer:
John Mauchy 1. designed to be a stored-program computer 2. it was binary rather than decimal
which og the figures ilustration kinetic potential energy? where only the water of your energy
Answers
Which is the best description of a computer virus?
a program that can damage a computer
a hacker who adds programs to a computer
a scam that steals information from a computer
a biological disease that destroys a computer
Answers
Answer:
A- a program that can damage a computer
Explanation:
The best description of a computer virus is a program that can damage a computer. The correct option is A.
What is a computer virus?Any software that has been designed to be dangerous is frequently referred to as "virus" as a catch-all word. The definition of a virus is a computer program that has the ability to replicate itself, infect other programs, and propagate to other systems, although a virus is merely one sort of malware.
The analogy of the "computer virus" was chosen because it resembles biological viruses that affect the human body in terms of structure, behavior, and effects. Computer viruses have the ability to infiltrate other programs and take over control or negatively impact the program's functionality.
Therefore, the correct option is A, a program that can damage a computer.
To learn more about a computer viruse, refer to the link:
https://brainly.com/question/29446269
#SPJ2
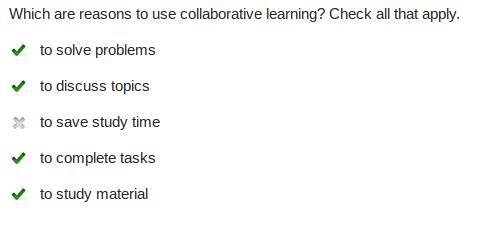
Which are reasons to use collaborative learning? Check all that apply.
to solve problems
to discuss topics
to save study time
to complete tasks
to study material
Plz help
Answers
Answer:
i say the answers are
A. to solve problems
B. to discuss topics)
D. to complete tasks
E. to study material
Explanation:
I say it's NOT (C. to save study time) because you are still taking times to study
Answer:
A, B, D, E
Explanation:
Algunos de los navegadores que existen son:
Answers
Answer:
Un navegador que no existe es firechicken. ja ja
A browser that does not exist is firechicken. lol
Explanation:
Un navegador que no existe es firechicken.
¡Espero que esto ayude! :)
¡Marque el más inteligente!
A browser that does not exist is firechicken.
Hope this helps! :)
Please mark brainliest!
Can someone explain this question & answer to me?
var list = [11, 35, 6, 0];
var sum = 0;
for (var i = 0; i < list.length; i++) {
sum = sum + list[i];
}
sum = sum/list.length;
console.log(sum);
Answers
The sum is then divided by the length of the list to get a percentage.
The code will iterate through the list of numbers and add them up.
The sum variable is then divided by the number of items in the list to determine the average value.
NEED THIS ASAP!!) What makes open source software different from closed source software? A It is made specifically for the Linux operating system. B It allows users to view the underlying code. C It is always developed by teams of professional programmers. D It is programmed directly in 1s and 0s instead of using a programming language.
Answers
Answer: B
Explanation: Open Source software is "open" by nature, meaning collaborative. Developers share code, knowledge, and related insight in order to for others to use it and innovate together over time. It is differentiated from commercial software, which is not "open" or generally free to use.
Here is a complete binary tree using array representation; [5, 7, 9, 4, 2, 3, 1]. How many internal nodes (enter the value in the first blank below) and what are values of them (enter the values in the second blank below. sperate values by a comma)? Blank # 1 Blank # 2
Answers
The given complete binary tree represented by the array [5, 7, 9, 4, 2, 3, 1] contains 3 internal nodes. The values of these internal nodes are 5, 7, and 9.
In a binary tree, an internal node is a node that has at least one child. To determine the number of internal nodes in the given complete binary tree, we need to identify the nodes that have at least one child. In this case, the values 5, 7, and 9 are the internal nodes as they have children.
The complete binary tree can be visualized as follows:
5
/ \
7 9
/ \ /
4 2 3
/
1
From the above representation, we can see that nodes 5, 7, and 9 have at least one child, making them internal nodes. Therefore, the number of internal nodes in the given tree is 3. The values of these internal nodes are 5, 7, and 9.
To learn more about binary trees visit:
brainly.com/question/28388846
#SPJ11
Manny copied a table from an ms excel file, closed the file, and then pasted the table in an ms word document. Where was the table stored after he copied it?.
Answers
The table was stored after he copied it into the RAM memory. It is a fundamental part of a computer.
What is the RMA memory?Random Access Memory (RAM) is a fundamental part of the hardware of a computer device.
The RAM stores information of the operating system and applications in current use in order to be recovered rapidly during work.
This short-term memory (RAM) enables the management of different active tasks and applications.
Learn more about RAM memory here:
https://brainly.com/question/13196228
The ____ view displays the worksheet the way it will look when it prints.
A) Normal
B) Page layout
C) Break
D) Page settings
Answers
4. Are instructions designed to ensure that your manufacturing processes are consistent, timely and repeatable.
A. Management
B. Quality
C. SOP
D. SWI
Answers
Answer:
SWI
Explanation:
SWI (Standardized Work Instructions) are instructions designed to ensure that your manufacturing processes are consistent, timely and repeatable
Which tab would help you toggle between views?
Answers
The View tab enables you to toggle between different views
View tab
The View tab enables you to toggle between different views, selecting either Normal or master Page, single or Two-Page Spread views.
The view tab also provides several options such as rulers, boundaries, layout.
By default, the view used while working is the normal view, but this view can be toggled to the one you want.
Find out more on or view tab at: https://brainly.com/question/25629383
TLE(ICT)-10
Research on other forms of Operating systems used in smartphones and give a description for each.
Answers
Answer:
Android
iOS
Explanation:
Operating systems refers to the embedded software program upon which a machine ( computer or smartphone) is programmed to work. Applications or programs which machines would run must be compatible with that which is designed for the operating system. Operating systems handles and controls process and file management, input and output among others.
The Android and iOS operating system are the two most popular operating systems used on smartphones. In terms of ownership, iOS is developed by Apple and it is not open source (closed source). It has a simple and very less customizable interface. Smart products such as iPhones, iPads run on iOS operating system.
Android on the other hand is runned by googl and is more open source, with a much more customizable interface, android garners more
popularity in the smartphone ecosystem. Most major smartphone devices run on Android such as Samsung, Sony and so on.
Other operating systems may include windows which are very less popular.
The other forms of operating systems include Android and iOS.
It should be noted that operating systems simply mean the embedded software program through which a computer or smartphone is programmed to work.
Operating systems are important as they handle and controls processes and file management. The Android and iOS operating systems are used on smartphones. iOS is owned by Apple.
Learn more about operating systems on:
https://brainly.com/question/1326000
If C2=20 and D2=10 what is the result of the function = mathcal I F(C2=D2,^ prime prime Ful "Open")?
Open
Unknown
Full
10
Answers
Excel IF functions are used to test conditions.
The result of the IF function is (a) Open
The function is given as: = IF(C2 = D2, "Full","Open")
Where: C2 = 20 and D2= 10
The syntax of an Excel IF conditional statement is: = IF (Condition, value_if_true, value_if_false)
The condition is: IF C2 = D2
The values of C2 and D2 are: 20 and 10, respectively.
This means that, 20 does not equal 10.
So, the value_if_false will be the result of the condition.
In other words, the result of the IF function is (a) Open
Read more about Excel functions at:
https://brainly.com/question/10307135
Damage to data or equipment that in which the data or equipment can not be recovered is which concern
Answers
Damage to data or equipment in which the data or equipment can not be recovered in the concern associated with data loss.
What happens when data is lost or damaged?The notoriety of a business may definitely suffer due to data loss or damage. It involves a complete process of communicating a data loss incident to customers, but it can unintentionally outcome in a lack of trust and discontent.
According to the context of this question, the mechanism of data loss takes place when data is completely or partially destroyed, corrupted, or made unreadable by software applications and users. It is thought that the process of data loss accidentally or unintentionally happens.
Therefore, damage to data or equipment in which the data or equipment can not be recovered is the concern associated with data loss.
To learn more about Data loss, refer to the link:
https://brainly.com/question/15027705
#SPJ9
Your question seems incomplete. The most probable complete question is as follows:
Damage to data or equipment that in which the data or equipment can not be recovered is which concern?
a concern associated with data loss. a concern associated with data recovery.a concern associated with data indentation.Whats the overall mood of the song Rags2Riches by rod wave
Answers
Answer:
9.5/10
Explanation: Because you can vibe with the muisc but i just dont like the name so with out the name 10/10
Answer:
it would be a sad/get turnt
Based on the characteristics common to successful entrepreneurs, do you think you would make a good one? Discuss at least one of these traits and explain why it is the trait most developed in you now, and discuss another that would require work to develop?
Answers
Answer:
the answer is 24
Explanation:
Data type can only be true or false
Answer: Bool