look at the activity network below for the production of a new system that is going to help your organization. the numbers represent how many days it will take to complete each activity. what are the values that should be entered into the boxes labeled x, y, and z?
Answers
The network of actions listed below will help your business by developing a new system. The numbers display how many days are needed to complete each task.
What is network in computer explain?A computer network is a collection of interconnected computing devices that may share resources and exchange data. These networked devices use a set of rules called communications protocols to send data across wired or wireless technologies. Let's react to a few computer networking-related commonly asked questions (FAQs).
Computers, servers, mainframes, network devices, peripherals, and other devices are interconnected to create a network in order to share data. A network is an example of. At their core, local area networks (LANs) and wide-area networks are two different types of networks (WANs). LANs connect computers and auxiliary equipment inside a constrained physical location, such as a business office, lab, or college campus, using quick-transmitting links (wires, Ethernet cables, fiber optics, and Wi-Fi). the world's largest network of connections, the Internet.
To learn more about network, visit:
brainly.com/question/1326000
#SPJ4
Related Questions
Chief Financial Officer (CFO) has been receiving email messages that have suspicious links embedded from unrecognized senders.
The emails ask the recipient for identity verification. The IT department has not received reports of this happening to anyone else.
Which of the following is the MOST likely explanation for this behavior?
a) The CFO is the target of a whaling attack.
b) The CFO is the target of identity fraud.
c) The CFO is receiving spam that got past the mail filters.
d) The CFO is experiencing an impersonation attack.
Answers
The Chief Financial Officer (CFO) has been receiving email messages that have suspicious links embedded from unrecognized senders. The emails ask the recipient for identity verification. The IT department has not received reports of this happening to anyone else. Which of the following is the MOST likely explanation for this behavior?Answer: The CFO is the target of a whaling attack.What is whaling?Whaling is a social engineering attack on high-profile executives and senior management in organizations, as well as celebrities and other public figures.
The victim is an individual of particular importance or power within a company or organization, who has access to sensitive data. Whaling is also referred to as business email compromise (BEC).Attackers employ many of the same methods as spear-phishing but specifically target senior executives and other high-profile targets. The attack is aimed at acquiring valuable information, such as the CEO's or CFO's login credentials, employee details, and customer data, through targeted phishing. They can then use the information to gain access to the victim's systems and data.In the above scenario, since the CFO is the only person receiving such emails, it is likely that the CFO is the target of a whaling attack. The emails have suspicious links that require the recipient to provide identity verification. Attackers frequently use whaling attacks to obtain sensitive information such as account login credentials, personal information, and confidential corporate data that can be sold on the black market or used in future attacks.
To know more about whaling attack visit :
https://brainly.com/question/29971956
#SPJ11
explain digital divide
Answers
Answer:
A digital divide is any uneven distribution in the access to, use of, or impact of Information and Communication Technologies (ICT) between any number of distinct groups.
The digital divide is the gap that exists between individuals who have access to modern information and communication technology and those who lack access.
Jill is interested in a career as a paramedic. She is trained to use medical equipment, she remains calm under pressure, and she has good bedside manner. Which career pathway would best fit Jill’s interests and skills?
Answers
This question is incomplete because it lacks the appropriate options
Complete Question:
Jill is interested in a career as a paramedic. She is trained to use medical equipment, she remains calm under pressure, and she has good bedside manner. Which career pathway would best fit Jill’s interests and skills?
A. Security and Protective Services
B. Law Enforcement Services
C. Emergency and Fire Management Services
D. Correction Services
Answer:
c) Emergency and Fire Management Services
Explanation:
Emergency and Fire Management Services is a career path or occupation where personnels work to ensure that there is a prompt emergency response to incidents or accidents whereby the safety of human lives and properties are threatened.
Emergency and Fire Management services deal with the following incidents listed below:
a) Fire incidents
b) Car accidents
c) Medical emergencies
Staffs or Personnels that work in Emergency and Fire Management services:
a) Fire Fighters
b) Paramedics
Personnels who work with Emergency and Fire Management services should have the following traits or characteristics.
a) They must be calm regardless of any situations they are in
b) They must have the ability and training to use essential medical equipments.
c) They must have excellent people skills as well as good bedside manners.
d) They must possess the ability to work under intense pressure
e) They must possess the ability to calm victims of fire or car accidents
In the question above, the career pathway that is best for Jill based on the skills and interests that she possesses is a career pathway in Emergency and Fire Management Services.
Answer:
the person above me is right
Explanation:
describe the various uses of the EFTPS and then
discuss how it provides benefit to the users .only 7 to 8 lines
brief essay. payroll subject.
Answers
Electronic Federal Tax Payment System (EFTPS) is an electronic tax payment system that enables taxpayers to pay their federal taxes electronically.
It was introduced in 1996, and it has since made it easy for individuals and businesses to pay their taxes electronically. Below are some of the various uses of the EFTPS:EFTPS can be used to pay a wide range of federal taxes, including income tax, excise tax, and employment tax.EFTPS can be used by individuals, businesses, and organizations that are required to pay federal taxes.
EFTPS can be used to schedule federal tax payments for up to 365 days in advance.EFTPS can be used to view payment history and federal tax payment status.The benefits of EFTPS are significant, especially for individuals and businesses that use it. For example:EFTPS is convenient, and it saves users time. Users can make their tax payments from anywhere, anytime.EFTPS is secure, and it reduces the risk of tax fraud. Users receive immediate confirmation of their payments.
EFTPS is reliable, and it eliminates the possibility of payment delays. Users can schedule payments in advance and receive reminders before payments are due.EFTPS is cost-effective. Users do not incur any transaction fees when making payments through EFTPS.
In conclusion, EFTPS is an excellent tool for individuals and businesses that want to pay their federal taxes electronically. It offers convenience, security, reliability, and cost savings, making it a preferred tax payment method.
To learn more about EFTRS:
https://brainly.com/question/13960816
#SPJ11
Conceptual note-taking is the act of writing down information in the order it is given. drawing attention to details with a marker or pen. adding main ideas and details to a graphic organizer. creating lists to organize homework and study time.
Answers
Answer:A
Explanation:Conceptual notetaking is the act of writing down information in the order it is given.
Conceptual note-taking is class of note-taking characterized with writing down in order, drawing of attention to details with a pen and adding of main ideas.
Conceptual note-taking is most useful when we need to show how the main ideas and details relate to each other.
Therefore, in short, the Conceptual note-taking basically focus on the concepts of the lecture, classwork etc
Learn more about this here
brainly.com/question/7321210
What are the features of MS Excel
Answers
Learn to use shortcuts. Once you are able to live without the mouse, you get the speed that counts. There are two types of shortcuts - one where you press a set of keys sequentially - like Alt>H>O>I to adjust column width. And the second where you simultaneously press a combination of keys - like Ctrl+Shift+L for applying filters or Ctrl+1 for the format numbers dialog box. It takes repetition to get the speed but once you are there, you get an edge.
Learn excel functions and apply them to build formulas. Start with easy ones like SUM, COUNT, SUMIF, COUNTIF, IF etc, then move to VLOOKUP, SUMIFS, COUNTIFS, HLOOKUP, INDEX, MATCH, then move to building nested complex formulas like IF inside an IF, VLOOKUP with HLOOKUP, INDEX+MATCH and so on.
Learn about data analysis and data aggregation. This includes tools like Pivot table, solver, goal seek, data tables, descriptive statistics, regression.
Learn about conditional formatting. Style and colour your spreadsheets.
what is the number of mbr partitions contained in a hard drive?
Answers
An MBR drive can have up to four standard partitions. Typically, these standard partitions are designated as primary partitions.
What is meant by mbr partitions?
Simply put, the MBR is a boot sector category that provides information about the hard disk partitions. It also provides information about the OS so it can be loaded for the system boot. The MBR contains programs that determine which partition on the hard disk is used for the system boot.An MBR has a partition table describing the partitions of a storage device. The maximum size of an MBR partition cannot exceed 2 TB (2.19 TB). MBRs are constrained by supporting only four main partitions and a volume size of less than 2 TB.MBR disks are primarily BIOS booted, as a result BIOS firmware and MBR disks are linked and much like BIOS, MBR also has several limitations. MBR is limited to 4 primary partitions that can span no more than 2TB.To learn more about mbr partitions refers to:
https://brainly.com/question/10762771
#SPJ4
An MBR drive can have up to four standard partitions. Typically, these standard partitions are designated as primary partitions.
What is meant by mbr partitions?Simply put, the MBR is a boot sector category that provides information about the hard disk partitions. It also provides information about the OS so it can be loaded for the system boot. The MBR contains programs that determine which partition on the hard disk is used for the system boot.
An MBR has a partition table describing the partitions of a storage device. The maximum size of an MBR partition cannot exceed 2 TB (2.19 TB). MBRs are constrained by supporting only four main partitions and a volume size of less than 2 TB.
MBR disks are primarily BIOS booted, as a result BIOS firmware and MBR disks are linked and much like BIOS, MBR also has several limitations. MBR is limited to 4 primary partitions that can span no more than 2TB.
To learn more about mbr partitions refers to:
https://brainly.com/question/29415709
#SPJ4
Give at lesat 3 examples of how is NLG (Natural Language Generation) beneficial and unbeneficial (pls support your points)
Answers
NLG (Natural Language Generation) is beneficial isuch as automating content creation, personalizing user experiences, and generating insights from data but have limitations including potential biases in generated content and difficulties in capturing nuanced human language.
How is NLG beneficial and unbeneficial?NLG offers numerous benefits including the ability to automate the generation of content across different domains, such as news articles, product descriptions, and weather reports. This helps save time and resources by eliminating the need for manual content creation.
NLG systems may have limitations. One concern is the potential for biased content generation as the models are trained on existing data that may contain biases. This can lead to the generation of discriminatory or misleading content.
Read more about Natural Language
brainly.com/question/14222695
#SPJ1
NLG is beneficial in generating content quickly and accurately, maintaining consistency, and providing a personalized user experience
NLG, or Natural Language Generation, is the method of generating natural language text using computer algorithms. It is a subfield of artificial intelligence that focuses on creating human-like texts, thereby making it easier for humans to interact with machines. Natural Language Generation is beneficial in many ways, but it also has its limitations. In this response, we will discuss the benefits and drawbacks of NLG in detail. Benefits of Natural Language Generation (NLG):
1. Efficient content creation: NLG algorithms can generate content faster than human writers, making it easier for businesses and publishers to create large amounts of content in less time. This is particularly beneficial for news and sports articles, where quick updates are required.
2. Consistent quality and tone: NLG can ensure that the content is written in a consistent tone and style, maintaining the brand's voice and values. In contrast, human writers can experience mood changes, which may influence the quality of their writing.
3. Personalization: NLG algorithms can create personalized messages and content, providing a better user experience for customers and clients. It can also be used for chatbots to provide human-like interactions with customers, improving customer satisfaction.
Unbeneficial of Natural Language Generation (NLG):1. Limited creativity: NLG algorithms can generate text based on the data it is fed. However, it lacks creativity and may fail to produce the same level of creativity as human writers. NLG cannot replace human writers' creativity, which is required in fields such as literature and poetry.
2. Dependence on data quality: NLG requires high-quality data to generate effective texts. Low-quality data may result in incorrect information and errors in the generated text.
3. Lack of empathy: NLG algorithms lack human empathy and understanding of social and emotional contexts. This may cause problems in situations that require a high level of emotional intelligence, such as counseling, medical diagnosis, and human resources. Therefore, NLG is beneficial in generating content quickly and accurately, maintaining consistency, and providing a personalized user experience. However, it has its limitations and cannot replace human creativity, empathy, and emotional intelligence.
For more questions on articles
https://brainly.com/question/25276233
#SPJ8
Asia pacific and Japanese sales team from cloud kicks have requested separate report folders for each region.The VP of sales needs one place to find the reports and still wants to retain visibility of the reports in each folder. What should a consultant recommended to meet this requirement.
Answers
Answer:
B) Create all new regional folders and move the reports to the respective region folder with viewer access.
Explanation:
Below are the options
A) Create grouped folders, keeping the top region folder sharing settings and limiting the sharing settings for the grouped folders for each region.
B) Create all new regional folders and move the reports to the respective region folder with viewer access.
C) Create all new regional folders and move the reports to the respective region folder with subscribe access.
D) Create subfolders, keeping the top region folder sharing settings and limiting the sharing settings for the subfolders for each region
In order to required reports at one place and also wants to retain the visibility for each folder the consultant should suggest that all new regional folders should be created and afterwards it would be moved to their relevant region folders by involving the viewer access feature so that the VP should access it anytime
Hence, the correct option is B.
Based on the information given, the correct option will be B. Create all new regional folders and move the reports to the respective region folder with viewer access.
From the information given, it was stated that the VP of sales needs one place to find the reports and still wants to retain visibility of the reports in each folder.
Therefore, it's important to create all new regional folders and move the reports to the respective region folder with viewer access.
Learn more about folders on:
https://brainly.com/question/20262915
The ____ and ____ times are determined by calculating forward through the network.
Answers
The "forward" and "prediction" times in a neural network are critical factors that determine the efficiency and speed of the model. The forward time refers to the duration it takes for the input data to propagate through the layers of the network, resulting in an output.
This process involves performing matrix multiplications, applying activation functions, and passing information from one layer to the next. The complexity of the network architecture, including the number of layers and the size of each layer, can influence the forward time. On the other hand, the prediction time corresponds to the period required to make predictions on new, unseen data once the network has been trained. This involves feeding the input data through the trained network, performing forward propagation, and obtaining the output predictions. The prediction time is influenced by the complexity of the network, the size of the input data, and the computational resources available for inference. Efforts are continuously made to optimize neural network architectures and algorithms to minimize both forward and prediction times, ensuring efficient and real-time performance in various applications such as computer vision, natural language processing, and speech recognition.
Learn more about network here
https://brainly.com/question/28342757
#SPJ11
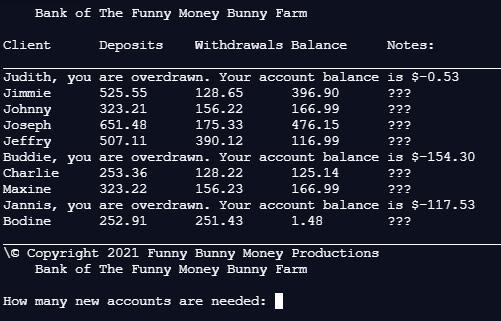
Can someone help me figure out why my else statment is not working?
----------------------------------------------------------------------------------------------------------------------------
print("\tBank of The Funny Money Bunny Farm\n")
print("Client\t\tDeposits\tWithdrawals\tBalance\t\tNotes:")
print("__________________________________________________________________________________________________________________________")
names = ['Judith', 'Jimmie', 'Johnny', 'Joseph', 'Jeffry', 'Buddie', 'Charlie', 'Maxine', 'Jannis', 'Bodine']
deposists = [255.23, 525.55, 323.21, 651.48, 507.11, 101.11, 253.36, 323.22, 611.45, 252.91]
withdrawals = [255.76, 128.65, 156.22, 175.33, 390.12, 255.41, 128.22, 156.23, 728.98, 251.43]
balance = []
notes = []
for i in range(len(names)):
balance.appened(deposits[i] - withdrawals[i])
if(balance < 0):
print((names[i] + ", you are overdrawn. Your account balance is " + "$%.2f"%(balance[i]))
else:
print("" + names[i] + "\t\t" + "%.2f"%(deposits[i]) + "\t\t" + "%.2f"%(withdrawals[i]) + "\t\t" + "%.2f"%(balance[i]) + "\t\t" + notes[i])
print("__________________________________________________________________________________________________________________________")
print("\© Copyright 2021 Funny Bunny Money Productions")
#Main
print("\tBank of The Funny Money Bunny Farm\n")
account = int(input("How many new accounts are needed: "))
for i in range(account):
input("Enter the name of the client: ")
input("Enter the deposist of the client: ")
input("Enter the withdraral of the client: ")
Answers
Answer:
below is a version of your code that runs.
I'm not sure if it does what you expect it to do.

true or false: change context allows you to change your login department without requiring you to log out first
Answers
Changing context typically refers to switching between different contexts or environments within a software application or system. It does not specifically relate to changing login departments.The statement is false.
A software application, commonly referred to as an "app," is a program or set of programs designed to perform specific tasks or functions on a computer or mobile device. These applications can range from simple programs that perform basic functions to complex applications that offer advanced features and capabilities.
Desktop Applications: These applications are designed to run on personal computers or laptops. They provide a wide range of functionalities, such as word processing, spreadsheet management, graphic design, video editing, and more. Examples include Microsoft Office Suite (Word, Excel, PowerPoint), Adobe Photoshop, and VLC Media Player.
Therefore, The statement is false.
Learn more about Desktop Applications on:
https://brainly.com/question/31783966
#SPJ1
There is a file that is written using Java. Ben wants to convert this file into a machine-understandable code. Which of these can help Ben with his work?
A.
interpreter
B.
operating system
C.
compiler
D.
output device
Answers
True or false. The PIC is an inter grated circuit in which the microprocessor architecture, along with read only memory (ROM) and random access memory (RAM), are all placed into one integrated circuit that may be reprogrammed; the microprocessor cannot.
Answers
Answer:
your partner in crime can not ROM around without a RAM.
Explanation:
so it would be false.
Positive numbers
Print all positive divisors of X from 1 to itself in ascending order
Input: natural number X.
Output: all positive divisors.
Answers
To print all positive divisors of a given natural number X in ascending order, you can follow the code written in Python language.
Code implementation:
1. Start by initializing a variable 'divisor' to 1.
2. Then, using a loop, check if 'divisor' divides 'X' completely (i.e., the remainder is 0). If it does, print 'divisor'.
3. Increment 'divisor' by 1 and repeat step 2 until 'divisor' becomes greater than 'X'.
4. By the end of the loop, you would have printed all the positive divisors of 'X' in ascending order.
Here is the code that you can use:
```
X = int(input("Enter a natural number: "))
divisor = 1
while divisor <= X:
if X % divisor == 0:
print(divisor)
divisor += 1
```
For example, if the input is X = 10, the output would be:
```
1
2
5
10
```
To know more about Python visit:
https://brainly.com/question/31055701
#SPJ11
for (int j- 4; j > 0; j--)
for (int k 1; k < j; k+)
System.out.print (j +);
System.out . println() ;
What is output when the program runs?
a.
4444
b
4321
321
21
4444
333
22
1234
123
12
4321
432
43
Answers
Answer:
C is your awnser
Explanation:
Which conditional formatting option is not found in the Quick Analysis Gallery? A) Duplicate Values B) Unique Values C) Text Contains D) Undo Format.
Answers
D) Undo Format is not found in the Quick Analysis Gallery in Microsoft Excel.
The Quick Analysis Gallery is a feature that allows users to quickly apply formatting, charts, and formulas to their data without having to navigate through menus. The options available in the gallery include conditional formatting, which allows users to highlight cells based on specific criteria. However, the "Undo Format" option is not available in the Quick Analysis Gallery. To undo formatting in Excel, users can use the "Undo" button or keyboard shortcut, or they can go to the "Home" tab and click on the "Clear" button to remove formatting from selected cells.
Learn more about Quick Analysis Gallery here;
https://brainly.com/question/14895673
#SPJ11
True or false
an exception is generally a runtime error caused by an illegal operation that Is just not possible, like trying to open a file that does not exist
Answers
Answer:
True
Explanation:
True.
An exception can be a runtime error caused by an illegal operation that is not possible, such as trying to open a file that does not exist.
the memwrite control bit for memory is set to 1, when the memory is in the write mode and it is set to 0 when the memory is in the read mode.
Answers
The memwrite control bit is a vital component in memory systems that governs access modes, specifically distinguishing between write and read operations. When the CPU needs to write data to memory, the memwrite control bit is set to 1, indicating the write mode. Conversely, when the CPU intends to read data from memory, the memwrite control bit is set to 0, signaling the read mode.
In most computer memory devices, such as dual-ported memories, there are separate read and write ports. The memwrite control bit acts as a selector, determining which port will be utilized based on its value. When the memwrite control bit is set to 1, data is written to memory using the designated write port. Conversely, when the memwrite control bit is set to 0, data is read from memory using the assigned read port.
In summary, the memwrite control bit is a crucial signal that governs memory access and specifies whether the CPU intends to read from or write to memory. It serves as a determinant for selecting the appropriate port and enables efficient data transfer between the CPU and memory subsystem.
Learn more about CPU
https://brainly.com/question/31034557
#SPJ11
What is the purpose of an End User License Agreement?
Answers
Answer: An End User License Agreement, or EULA for short, is a set of conditions under which a licensor gives a licensee permission to use a piece of intellectual property in the form of proprietary software. The licensor is the person or business that designed or developed the software.
Explanation:
A program is written to categorize images. One of its functions is to find a image of a bird. There are four images in the data set that are of the same size. The computer processing this information has four cores that can be used to perform this operation. How much faster can the data set be processed if the computer uses all its performing power?
A) There is no change to the processing speed
B) The processing time will decrease by 25%
C) The processing time will decrease by 50%
D) The processing time will decrease by 75%
Answers
Assuming the program is parallelizable and can distribute the work among the four cores evenly, the processing time will be reduced by a factor of 4. Therefore, the correct answer is option D) The processing time will decrease by 75%.
How much faster can the data set be processed if the computer uses all its performing power?If the program can be parallelized and distributed equally among the four cores, then the processing time can be reduced by a factor of 4. This is because each core can work on a separate image simultaneously. Therefore, the correct answer is option D) The processing time will decrease by 75%.
Learn more about processing in:https://brainly.com/question/29487063
#SPJ1
There are two general approaches to attacking a symmetric encryption scheme: cryptanalytic attacks and __________ attacks.
Answers
There are two general approaches to attacking a symmetric encryption scheme: cryptanalytic attacks and brute-force attacks.
What are the general approaches to attacking a Cypher?An assault attempts every key on a piece of cypher text until a plaintext translation that can be understood is produced.Half of all potential keys must be tested in order to be successful.A brute force attack is a method of hacking that uses trial and error to break encryption keys, passwords, and login credentials.It is an easy-to-use but reliable technique for breaking into systems and networks of businesses as well as individual accounts.Typical brute force attacks produce a lot of guesses every second—hundreds of them.Simple passwords that don't include a mix of capital and lowercase letters or widely used phrases like "123456" or "password" can be broken in a matter of minutes.To learn more about symmetric encryption scheme, refer
https://brainly.com/question/8455171
#SPJ4
Difference between software developer and software engineer.
Answers
Answer:
The core difference between the two jobs is that software developers are the creative force that deals with design and program implementation, while software engineers use the principles of engineering to build computer programs and applications.
Explanation:
Answer: The terms "software developer" and "software engineer" are often used interchangeably, but there are some subtle differences between the two roles.
Explanation: Here are some key differences:
Focus: A software developer typically focuses on the implementation of software code and applications based on design specifications, while a software engineer is involved in the entire software development lifecycle, including design, development, testing, deployment, and maintenance.Education and training: Software engineers usually have a broader education and training than software developers, with a strong foundation in computer science and software engineering principles. Software developers may have more specialized training in specific programming languages, frameworks, or technologies.Job responsibilities: Software engineers often take on more managerial or leadership responsibilities, such as project management, requirements analysis, and team leadership, while software developers typically focus more on writing and testing code.Professional standards: Software engineering is typically governed by professional standards and codes of ethics, which may not apply to software development. This reflects the more rigorous and disciplined approach to software engineering compared to software development.To learn more about software developer; https://brainly.com/question/3188992
What is self management
Answers
Answer:
when you manage or construct something by yourself, taking full reponsiblity, etc
Explanation:
Drag each label to the correct location on the image. Match the movie qualities with the right period of movies.
Answers
Assume that you were to build a new 7Tesla MRI system. You currently had a 3Tesla MRI system.
A) Which parts from the 3T could you use in the 7Tesla system? Explain
B) Could the same computer and analysis methods be used for the 7 Tesla system. Explain.
Q4.Trace the steps involved in the reception of the MR signal beginning with the insertion of the patient into the magnet.
Q9. Explain the behavior of relaxation times as the strength of the static magnetic field is increased.
Answers
The basic structure such as the patient bed and the gradient coils can be used, but critical components such as the radiofrequency coils, power supplies, and cooling systems would need to be replaced or upgraded.
What components from a 3T MRI system can be used in building a new 7T MRI system?A) Some parts from the 3T MRI system that could be used in the 7T MRI system include the scanner's basic structure, such as the patient bed and the gradient coils.
However, most of the critical components, such as the radiofrequency coils, the power supplies, and the cooling systems, would need to be replaced or upgraded to accommodate the higher field strength of the 7T MRI system.
B) While the same computer and analysis methods could potentially be used for the 7T MRI system, modifications and upgrades may be necessary to ensure compatibility with the higher field strength.
The software and algorithms used to acquire, process, and analyze data would need to be adjusted to account for the changes in signal-to-noise ratio, tissue contrast, and other factors that arise with a stronger magnetic field.
Q4. The reception of the MR signal begins with the insertion of the patient into the magnet, where a strong static magnetic field aligns the hydrogen atoms in their body.
A short radiofrequency pulse is then applied to the tissue, causing the hydrogen atoms to emit a signal as they return to their original state.
The signal is then detected by the scanner's receiver coil, which converts it into an electrical signal that can be processed and reconstructed into an image.
Q9. The behavior of relaxation times as the strength of the static magnetic field is increased can vary depending on various factors such as tissue type, temperature, and other variables.
Generally, the T1 relaxation time, which is the time it takes for the hydrogen atoms to return to their equilibrium state after being excited, increases with higher field strength. This can result in brighter and more contrasted images.
On the other hand, the T2 relaxation time, which is the time it takes for the hydrogen atoms to lose their phase coherence after excitation, tends to decrease with higher field strength, resulting in decreased contrast.
The exact behavior of relaxation times as the field strength is increased can vary and may require specific adjustments to optimize imaging parameters and protocols.
Learn more about components
brainly.com/question/30324922
#SPJ11
coding word scramble
ICOAIPAPLTSN- a software program for end users
AADT- processed information
RAAEHWRD- physical parts of computer system
MRNPAGOGIMR- instruction given to the computer
plz answer as soon as possible
Answers
The decoded words for the coding word are:
ICOAIPAPLTSN - ApplicationAADT - DataRAAEHWRD - HardwareMRNPAGOGIMR - ProgrammingWhat is coding words?In the above decoded words, "ICOAIPAPLTSN" unscrambles to "Application." An application, often referred to as software or a program, is a set of instructions designed to perform specific tasks or functions for end users. Applications can be anything from productivity tools, games, communication software, and more.
Also, "AADT" unscrambles to "Data." Data refers to any piece of information or raw facts that are collected, stored, and processed by a computer system. Data can be in various forms, such as text, numbers, images, videos, and more.
Read more about coding here:
https://brainly.com/question/26134656
#SPJ3
1. Which of the following is true about social media content? D. Once the content is published, it is very difficult to edit or correct it. O C. The tools to create social media content are not easily accessible. B. It can be user-generated and shared by many people. D A It is only created and distributed by the publisher
Answers
Answer:
B. It can be used-generated and shared by many people.It can be user-generated and shared by many people, is true about social media content. Thus, option (b) is correct.
What is social media?
Social media is a term used to describe online communication. Social media systems enable users to have discussions, exchange information, and create content for the internet. Social media mostly used in the youth. The social media are to share the information quickly.
Social media re to share the content are the user generated and the share by the many people. The social media are the share the news and the information to the quickly, but sometimes share the information is fake, the audience are the trust. The social media are the opinion to share with everyone. It's the medium of the communication.
Therefore, option (b) is correct.
Learn more about on social media, here:
https://brainly.com/question/24687421
#SPJ2
in the following uniform resource locator, what is product.html? http://www.microsoft/bin/services/product.html. group of answer choices folder/path name. host name. web page name. none of the listed can be used as the name or descriptor of product.html. server domain name.
Answers
In the given URL http://www.microsoft/bin/services/product.html, the term product.html refers to the web page name. A web page name is a specific file that contains the HTML code and other multimedia elements that are used to display content on the internet.
In this case, product.html is the name of the web page that is being accessed within the Microsoft website.The URL structure consists of different components that help in identifying the location of the web page on the internet. The host name in this case is www.microsoft.com, which represents the server domain name where the website is hosted. The folder/path name is bin/services, which represents the location of the web page within the website's directory structure.To summarize, product.html is the web page name in the given URL, and it is located within the bin/services folder on the Microsoft server domain. Understanding the different components of a URL is important for web developers, marketers, and anyone who wants to navigate the internet efficiently.For more such question on Microsoft
https://brainly.com/question/30236893
#SPJ11
place the steps in order for customizing the outlook ribbon
Answers
Answer: click the file tab, then options, click the customize ribbon, click the add new tab button, rename the tab and command group, add a command to the group
Explanation:in that order, just did it.