Local Area Networks (LANs)
1)only cover a short block
2)increase networking speed
3)take too long
4)are not used anymore

Answers
Answer:
increase networking speed
Explanation:
2020 edge
Answer:
increasing network speed
Explanation:
took the assignment on edge 2020 mark me as brainiest
Related Questions
Our solution to the IMDB problem thus far has not actually told us who is the busiest individual in the Internet Movie Database. Your job in this part is to complete this task. Starting from the code produced in class, which will be immediately posted on the Course Website (in the Code written in class area), write a program that finds and prints the name of the individual who appears the most times in the IMDB file you are given. Also, count and output the number of individuals who appear only 1 time in the IMDB. For example. if the answer was Thumb, Toni and this person had appeared 100 times, and if 2,000 people had only appeared once, then your output would be: Enter the name of the IMDB file imdb_data.txt Thumb, Toni appears most often: 100 times 2000 people appear once We strongly suggest that you test your solution on the hanks.txt dataset first! We will test on multiple files. You do not need to worry about the possibility of a tie for the most commonly occurring name. Please initialize your dictionary using dict() rather than []
Answers
To find the busiest individual in the IMDB file and count the number of individuals who appear only once, we need to read the data from the IMDB file and store it in a dictionary.
We can use the name of the individual as the key in the dictionary and the count of their appearances as the value. To find the busiest individual, we can iterate through the dictionary and find the key with the highest value. To count the number of individuals who appear only once, we can iterate through the dictionary and count the number of keys with a value of 1. It's important to initialize the dictionary using dict() rather than [] to avoid errors.The code will be posted on the Course Website (in the Code written in class area), and it can be modified to include the above functionalities.
To know more about IMDB file click here:
brainly.com/question/16518625
#SPJ4
What is design reference threat
Answers
public static int countPeaks (int[] data){int numPeaks = 0; for ( missing loop header */ ){if (data[p 1] < data[p] && data[p]> data[p+ 1]){numPeaks++;}}return numPeaks;}Consider the following method, which is intended to return the number of local maximum values in an array. Local maximum values are array elements that are greater than both adjacent array elements. The first and last elements of an array have only a single adjacent element, so neither the first nor the last array element is counted by this method. For example, an array containing the values {3, 9, 7, 4, 10, 12, 3, 8} has two local maximum values: 9 and 12. Which of the following can replace /* missing loop header */ so the method countPeaks works as intended?a. int p = data.length - 1; p > 0; p--b. int p = 0; p < data.length - 1; p++c. int p = 1; p < data.lenght - 1; p++d. int p = 0; p < data.length; p++e. int p = 1; p < data.lenght; p++
Answers
c) (int p = 1; p < data.length - 1; p++) can replace /* missing loop header */ so the method count Peaks works as intended,
What is loop ?
A loop is a set of instructions that are repeatedly carried out until a specific condition is met in computer programming. In most cases, a given procedure, such as collecting data and modifying it, is followed by a condition check, such as determining whether a counter has reached a predetermined number.
(int p = 1; p < data.length - 1; p++) can replace /* missing loop header */ so the method countPeaks works as intended.
This loop header will start the loop at the second element of the array (index 1) and end the loop at the second-to-last element of the array (index data.length - 2). This is because we don't want to check the first or last element of the array for local maximum values, as they have only a single adjacent element.
The other options are not suitable because they either start the loop at the wrong position (options a and e), end the loop at the wrong position (options a and d), or use the incorrect spelling of "length" (options c). Option c is the only one that starts the loop at the second element of the array and ends the loop at the second-to-last element of the array, making it the correct choice.
To know more about loop checkout https://brainly.com/question/14390367
#SPJ4
FOLLOW INSTRUCTIONS BELOW , WRITTEN IN JAVA LANGUAGE PLEASE AND THANK YOU !
Project Descriptions
This project involves implementing two process scheduling algorithms. You will be
required to write a Java program to simulate FCFS and RR scheduling policies we
discussed in class. The simulator selects a task to run from a ready queue based on the
scheduling algorithm. Since the project intends to simulate a CPU scheduler, it does not
require any actual process creation or execution. The processes’ information is stored in a
text file.
When a task(process) is scheduled, the simulator will simply print out what task is
selected to run at a time. I have provided a sample run below.
The name of your Java program should be called CPUScheduler.java
The selected scheduling algorithms to implement in this project are:
Round Robin (RR)
First Come First Serve (FCSF)
The above algorithms are already described in class slides, class video recordings and
textbook Chapter 5.
Implementation
The implementation of this project should be completed in Java. Your program will read
information about processes from a text file. This supporting text file contains process
scheduling information such as the pid, arrival time and CPU burst time. Your program
should read in this information, insert the processes into a list, and invoke the scheduler.
Process information
The following example format of how your text file should look like:
P1 0 10
P2 1 8
P3 2 5
The first column represents a process ID. Process ID uniquely identifies a process.
The second column represents arrival time. This is the time when the process arrives
in the unit of milliseconds
The third column represents CPU burst. This is the CPU time requested by a time, in
the unit of milliseconds
Thus, P1 arrives at 0 and has a CPU burst of 10 milliseconds and so forth.
The program will be run from the command line where you provide the name of the file
where the processes are stored.
The simulator first reads task information from the input file and stores all data in a data
structure. Then it starts simulating one scheduling algorithm in a time-driven manner. At
each time unit (or slot), it adds any newly arrived task(s) into the ready queue and calls a
specific scheduler algorithm in order to select appropriate tasks from the ready queue.
When a task is chosen to run, the simulator prints out a message indicating what process
ID is chosen to execute for this time slot. If no task is running (i.e. empty ready queue), it
prints out an "idle" message. Before advancing to the next time unit, the simulator should
update all necessary changes in task and ready queue status.
Grading
110 Total points possible
5 follows good coding practices
5 Runs from the command line
10 Reads the processes from a text file
10 Program compiles successfully and runs
40 FCFS produces the correct output
40 RR produces the correct output
Good coding practices:
Your code must:
be commented
use meaningful variable, method, and class names
use proper indenting
use objects, as well as static and non-static variables and methods, properly
be readable
Sample Execution
Assume that you have created a file process.txt with the following data:
P0 0 3
P1 1 6
P2 5 4
P3 7 3
If you invoke your scheduler (executable CPUScheduler) using the command
java CPUScheduler process.txt 2
Note that in the above command, process.txt is the name of the file to
read from and 2 is the time slide for RR
then your program should have a behavior similar to the following:
-------------------------------------------------
CPU Scheduling Simulation
-------------------------------------------------
-------------------------------------------------
First Come First Served Scheduling
-------------------------------------------------
[0-3] P0 running
[3-9] P1 running
[9-13] P2 running
[13-16] P3 running
Turnaround times:
P0 = 3
P1 = 8
P2 = 8
P3 = 9
Wait times:
P0 = 0
P1 = 2
P2 = 4
P3 = 6
Response times:
P0 = 0
P1 = 2
P2 = 4
P3 = 6
Average turnaround time: 7.00
Average wait time: 3.00
Average response time: 3.00
-------------------------------------------------
Round Robin Scheduling
-------------------------------------------------
[0-2] P0 running
[2-4] P1 running
[4-5] P0 running
[5-7] P1 running
[7-9] P2 running
[9-11] P3 running
[11-13] P1 running
[13-15] P2 running
[15-16] P3 running
Turnaround times:
P0 = 5
P1 = 12
P2 = 10
P3 = 9
Wait times:
P0 = 2
P1 = 6
P2 = 6
P3 = 6
Response times:
P0 = 0
P1 = 1
P2 = 2
P3 = 2
Average turnaround time: 9.00
Average wait time: 5.00
Average Response time: 1.25
Answers
Keisha needs to connect to the Internet, but no wireless networks or Wi-Fi hotspots are available. What can she use instead to make the connection
Answers
There are several ways of connecting to the internet aside the use of WiFi Hotspot. Hence, Keisha could make use of Bluetooth or a modem.
Bluetooth tethering allows users to establish internet connection between smart devices such as a smartphone and a computer by using the Bluetooth functionality of the devices. Similarly, modems can be used to establish a connection by inserting a data Sim into the USB modem and Inputting it into the port of the computer.Learn more : https://brainly.com/question/25698028
A manufacturing company produces products. The following product information is stored: product name, product ID and quantity on hand. These products are made up of many components. Each component can be supplied by one or more suppliers. The following component information is kept: component ID, name, description, suppliers who supply them, and products in which they are used. Create an ERD to show how you would track this information.Show entity names, primary keys, attributes for each entity, relationships between the entities and cardinality.
Assumptions:
A supplier can exist without providing components.
A component does not have to be associated with a supplier.
A component does not have to be associated with a product.
Not all components are used in products.
A product cannot exist without components
Required:
Analyze the above scenario and assumptions and create an ERD to show how you would track ali the above information.
Answers
I couldn't read all, it was too long.
Explanation:
Nah, I gave up
A database of manufacturing companies contains: Relational Database Schema ER Diagram
What is database?
Database is defined as an ordered grouping of data that has been arranged and is usually stored electronically in a computer system. They make it possible to manipulate and store data digitally. Databases make data administration easy. Computer databases are frequently used to collect and store data records or files comprising information such as sales transactions, customer information, financial data, and product information.
Choose the Entities for Your ERD. Each Entity Should Have Attributes. Explain the connections between the entities. Completion and saving of your ERD Initially, just one instance of each entity is needed. Usually used in pairs from each associated entity's point of view, define the relationship.
Thus, a database of manufacturing companies contains: Relational Database Schema ER Diagram.
To learn more about database, refer to the link below:
https://brainly.com/question/29412324
#SPJ2
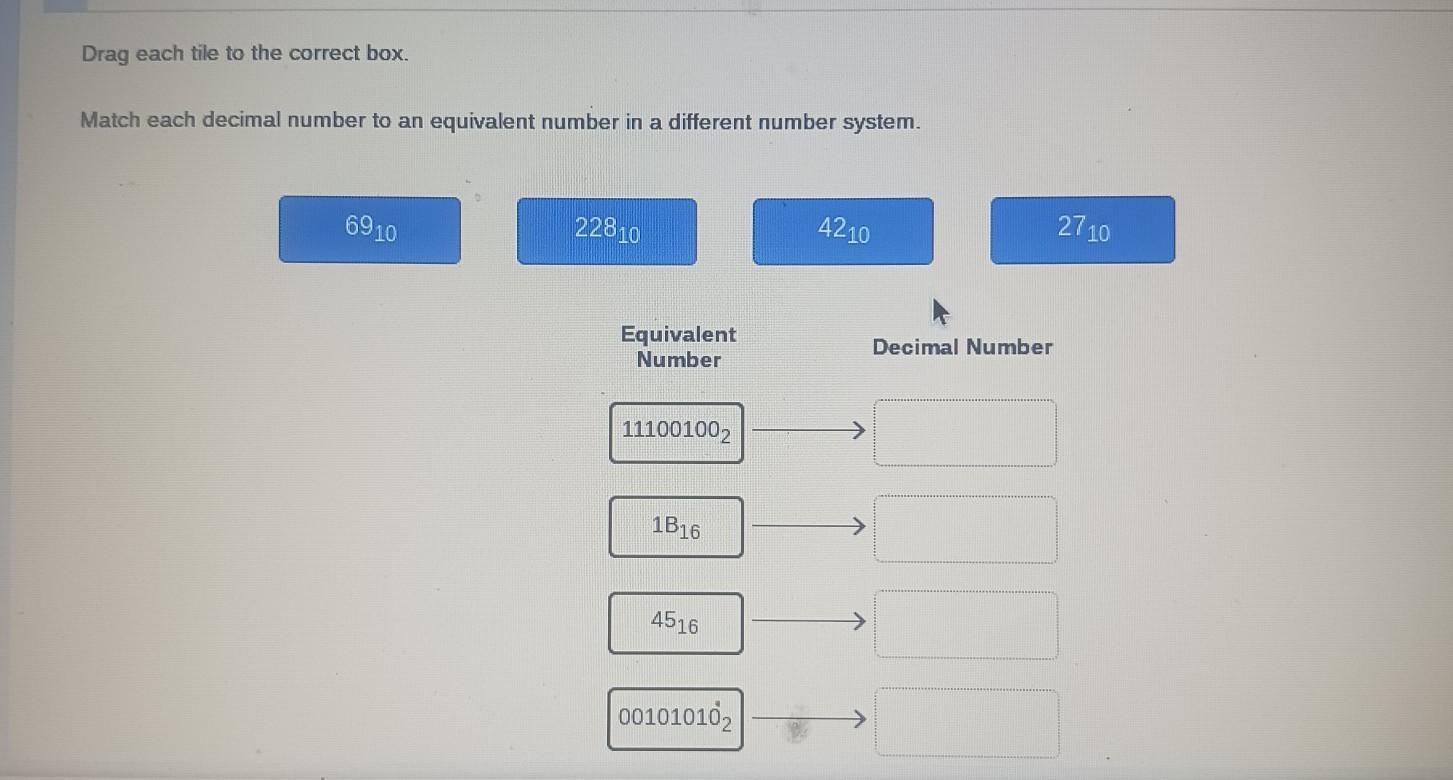
Drag each tile to the correct box. Match each decimal number to an equivalent number in a different number system. 6910 22810 4210 2710
Answers
Explanation:
you can do that with calculator only

What is the running time to perform the following operations: (a) minimum (b) maximum (c) median (d) average (e) search/look-up (f) predecessor (g) successor, for a dynamic set with n keys implemented using the following data structures: (a) binary search tree (b) hash table based dictionary (c) direct address based dictionary (d) red-back tree (e) van-emde boas tree.
Answers
The running time that is used for a lot of operations in a lot of data structures for any given dynamic set with n keys are known to be given below.
What is the running time about?In terms of (a) Minimum time they are:
Binary search tree: This is seen as O(h), and it is one where h is seen as the height of the said tree.
In terms of Hash table based dictionary: It is one that is not applicable, as it is one where the hash tables do not aid or support any form of finding of any kind in terms of the minimum element.
Lastly in terms of Direct address based dictionary: O(1) is one that is seen as as the minimum element that is it is one that can be directly accessed via the use of its key. Red-black tree: is one where the O(1), is one that act as red-black trees that tends to keep a subtree via the use of the minimum element found at its root.
Learn more about running time from
https://brainly.com/question/26046491
#SPJ1

Q1:most common cybercrimes?
Q2: Difference between Hacker and crackers
Answers
Q1: phishing and similar fraud
Q2: Hackers are good people who hack devices and systems with good intentions. They might hack a system for a specified purpose or for obtaining more knowledge out of it. Crackers are people who hack a system by breaking into it and violating it with some bad intentions.
Complete each statement by choosing the correct answer from the drop-down menu.
A portable technological device is a
✔ tablet computer.
. A technological device used by IT professionals to check e-mail, make phone calls, and surf the Internet while away from the office is a/an
✔ smartphone.
. A
✔ thumb drive
is essentially a smaller version of an external hard drive. A
✔ smartphone
is a cell phone that has added functionality. The debit card replaced the need to use
✔ checks.
. In a classroom, an interactive whiteboard replaced the
✔ chalkboard.
. Many people use
✔ a global positioning system (GPS)
instead of maps.
Answers
Answer:
A portable technological device is a: tablet computer.
A technological device used by IT professionals to check e-mail, make phone calls, and surf the Internet while away from the office is a/an: smartphone.
A thumb drive is essentially a smaller version of an external hard drive.
A smartphone is a cell phone that has added functionality.
The debit card replaced the need to use: checks.
In a classroom, an interactive whiteboard replaced the: chalkboard.
Many people use a global positioning system (GPS) instead of maps.
Im being timed please help!!
Where might you find help if material becomes truly difficult?
a.
A teacher
c.
A study group
b.
A tutor
d.
All of these
Please select the best answer from the choices provided
A
B
C
D
Answers
Answer:
ALL
Explanation:
Because if it was a test you can ask a teacher, if it was group projects you can ask the study group, if it was homework or 1 on 1 you can ask a tutor
Answer:
b
Explanation:
because a tutor deals with materials
Advika needs to send files from one computer to another computer. Which of the following methods is the simplest ways to accomplish this task?
Answers
Make sure the two PCs are joined with the same Wi-Fi networks. Locate the file you want to send using File Explorer.
What is a computer?
A laptop is an electronic tool for handling data or information. It has the power to store, retrieve, and process data. You may already be aware of the fact that a computer may be used to make a report, send emails, play games, and surf the Internet.
What component of a computer is most vital?
Your computer's "brain" is the central developed the ability (CPU), often known as the processor. The complex calculations and programming that your computer performs while running apps or programs are all handled by the CPU.
To know more about computer visit:
https://brainly.com/question/21474169
#SPJ1
Who is the best RL player?
A. Firstkiller
B. Aztral
C. Squishy
D. Sunlesskhan lol definitely not :)
Answers
Answer:
Killa and gon
Explanation:
Answer:
C. SquishyMuffinz (Mariano)
Explanation:
Itsjustmyopinionbackoffman.
The game Batman Begins was intentionally released to coincide with the release of the Batman Begins movie. Based on this information, which option best describes the game?
A.
It is a game that promotes artistic expression.
B.
It is an advergame.
C.
It is an exergame
D.
It is a game that promotes social causes.
Answers
The correct option is B. "It is an advergame."
What is game?
A game is an activity that involves one or more players, who engage in a structured form of play with a set of rules or objectives. Games can be played for entertainment, educational purposes, or competition, and they can take many different forms, including board games, video games, sports, puzzles, and more. Games often require skill, strategy, and critical thinking, and can be played individually or in teams. They can also provide social and psychological benefits, such as promoting teamwork, communication, and problem-solving skills, and can be enjoyed by people of all ages and backgrounds.
An advergame is a video game that is created to promote a specific product or brand. In this case, the game "Batman Begins" was created to coincide with the release of the Batman Begins movie, serving as a promotional tool to increase public awareness and interest in the movie. The game includes elements and characters from the movie, and the gameplay is designed to be similar to the movie's storyline, making it a part of the overall marketing campaign for the movie. Therefore, it can be considered an advergame.
To know more about marketing visit:
https://brainly.com/question/30699183
#SPJ1
who was Widely regarded as the world's first computer programmer
Answers
Answer:
Ada Lovelace
The world’s first computer programmer was a woman named Ada Lovelace. Born in Britain on December 10, 1815, she was introduced to the concept of the calculating machines developed by Charles Babbage when she was 17. It was in 1842 that she became thoroughly involved in what we call today computer programming.
Explanation:
pls pls pls pls pls pls pls pls plks
Answers
Answer:
Want to begin introduction?.......
write the html to place an image called prime logo.gif on a web page. The image is 100 pixel high by 65- pixel wide
Answers
Answer:
Um, HOW??????????????¿??
Suppose we have 999 records of employees Emp1, Emp2, Emp5, Emp6 and so on up to Emp998 and Emp999 stored in a sequence. Hence, records are nothing but a row in the table. In the employee table, we want to insert new records Emp3 and Emp4 in the sequence, and once we have done insertion we need to update and retrieve the record efficiently to optimize the performance of a database by minimizing the access time when query is being executed.
You are required to solve the problem with the index sequential access method with pros and cons in the given scenario
Answers
The records in the table represents the employee ID of each employee. Assume the table name is EMPLOYEES and the field name of employee IDs is ID, the following SQL query inserts Emp3 and Emp4 into the employees table.
INSERT INTO EMPLOYEES (ID) values (Emp3), (Emp4)
The advantage of using ISAM is that priorities are given to the indices of the records being inserted. So, Emp3 and Emp4 will be inserted immediately after Emp2.
However, a major disadvantage of using ISAM is that it is very expensive to keep the indices in a sequential order;
See attachment for the illustration of Index sequential access method (ISAM).
Read more about Index sequential access method (ISAM) at:
https://brainly.com/question/4692093

What is unsolicited junk mail?
Answers
Answer: spam mail
Explanation:
Answer: GoodMorning: ) ✨Unsolicited means that the Recipient has not granted verifiable permission for the message to be sent. So another word that people use for unsolicited junk is = Spam email is unsolicited and unwanted junk email sent out in bulk to an indiscriminate recipient list. Typically, spam is sent for commercial purposes.
HAVE AN AMAZING REST OF YOUR DAY: )
Purchase a PC
This exercise can be done in class and allows the Instructor to walk through the process of deciding on which equipment to purchase from an online vendor for personal use or professional use.
You can visit the site here: Configurator
Create a Word Document and Answer the following:
1. Why choose the accessories?
2. What is RAM and explain in general terms what the different types are (DDR3, DDR4)?
3. Why does some RAM have DDR4-3200? What does the 3200 mean?
4. What is the difference between Storage devices like SSD and HDD?
5. Why choose an expensive Video card (GPU)?
6. What are the general differences between i3, i5, i7, i9 processors?
7. What is the difference in Audio formats like 2.1, 5.1, 7.1, Atmos, and so on? What is the .1?
Answers
1. Choosing accessories depends on the specific needs and requirements of the individual or the purpose of use. Accessories enhance functionality, improve performance, and provide additional features that complement the main equipment.
They can optimize user experience, improve productivity, or cater to specific tasks or preferences.
2. RAM stands for Random Access Memory, a type of computer memory used for temporary data storage and quick access by the processor. DDR3 and DDR4 are different generations or versions of RAM. DDR (Double Data Rate) indicates the type of synchronous dynamic random-access memory (SDRAM). DDR4 is a newer and faster version compared to DDR3, offering improved performance and efficiency.
3. DDR4-3200 refers to the speed or frequency of the RAM. In this case, 3200 represents the data transfer rate of the RAM module in mega transfers per second (MT/s). Higher numbers, such as DDR4-3200, indicate faster RAM with higher bandwidth and improved performance than lower-frequency RAM modules.
4. SSD (Solid-State Drive) and HDD (Hard Disk Drive) are both storage devices but differ in technology and performance. HDDs use spinning magnetic disks to store data, while SSDs use flash memory chips. SSDs are generally faster, more durable, and consume less power than HDDs. However, SSDs are typically more expensive per unit of storage compared to HDDs.
5. Expensive video cards, also known as graphics processing units (GPUs), offer higher performance, better graphics rendering capabilities, and improved gaming experiences. They can handle demanding tasks such as high-resolution gaming, video editing, 3D modeling, and other graphically intensive applications. Expensive GPUs often have more advanced features, higher memory capacities, and faster processing speeds, allowing for smoother gameplay and better visual quality.
6. i3, i5, i7, and i9 are processor models from Intel. Generally, i3 processors are entry-level and offer basic performance for everyday tasks. i5 processors provide a good balance between performance and affordability and are suitable for most users. i7 processors offer higher performance and are better suited for demanding tasks such as gaming and multimedia editing. i9 processors are the most powerful and feature-rich, designed for professional users and enthusiasts who require top-tier performance for resource-intensive applications.
7. Audio formats like 2.1, 5.1, 7.1, and Atmos refer to the configuration of speakers and audio channels in a surround sound system. The number before the dot represents the number of prominent speakers (left, right, center, surround) in the system, while the number after the dot represents the number of subwoofers for low-frequency sounds. For example, 2.1 indicates two main speakers and one subwoofer, 5.1 refers to five main speakers and one subwoofer, and so on. Atmos is an immersive audio format that adds height or overhead channels to create a more
To know more about RAM:
https://brainly.com/question/31089400
#SPJ1
How does a hash help secure blockchain technology?
Hashes do not allow any new blocks to be formed on a chain or new data to be
added, Hashes block all changes.
Hashes are like fingerprints that make each block of data unique, Blocks form a
chain that can only have new blocks added.
Hashtags allow others to see if someone is trying to change something and it
alerts the government to prevent the changes.
Blocks of data require passwords that are called hashes, Hashes are impossible
to guess.
Answers
Blocks of data require passwords that are called hashes, Hashes are impossible to guess.
Blockchain security and Hash functionA hash is a function that meets the encryption requirements required to secure data. Because hashes have a set length, it is nearly impossible to estimate the hash if attempting to crack a blockchain.
The same data always yields the same hashed value. Hashes are one of the blockchain network's backbones.
Learn more about Blockchain security here:
https://brainly.com/question/31442198
#SPJ1
A backup operator wants to perform a backup to enhance the RTO and RPO in a highly time- and storage-efficient way that has no impact on production systems. Which of the following backup types should the operator use?
A. Tape
B. Full
C. Image
D. Snapshot
Answers
In this scenario, the backup operator should consider using the option D-"Snapshot" backup type.
A snapshot backup captures the state and data of a system or storage device at a specific point in time, without interrupting or impacting the production systems.
Snapshots are highly time- and storage-efficient because they only store the changes made since the last snapshot, rather than creating a complete copy of all data.
This significantly reduces the amount of storage space required and minimizes the backup window.
Moreover, snapshots provide an enhanced Recovery Time Objective (RTO) and Recovery Point Objective (RPO) as they can be quickly restored to the exact point in time when the snapshot was taken.
This allows for efficient recovery in case of data loss or system failure, ensuring minimal downtime and data loss.
Therefore, to achieve a highly time- and storage-efficient backup solution with no impact on production systems, the backup operator should utilize the "Snapshot" backup type.
For more questions on Recovery Time Objective, click on:
https://brainly.com/question/31844116
#SPJ8
Use the drop-down menus to complete the steps for creating a conditional formatting rule.
1. Select the object.
2. On the Form Tools
tab, click the Control Formatting group, and then click Conditional Formatting.
V.
3. In the dialog box, click
4. Select a rule type, edit the rule description, and set the formatting to apply to values that meet the criteria.
5. Click OK, and then click OK again.
Answers
Note that the complete steps for creating a conditional formatting rule are:
Use the drop-down menus to complete the conditional formatting rule steps.
1. Select the object.
2. On the Form Tools tab, click the Control Formatting group, and then click Conditional Formatting.
3. In the dialog box, click ADD
4. Select a rule type, edit the rule description, and set the formatting to apply to values that meet the criteria.
5. Click OK, and then click OK again.
What is Conditional Formatting?Conditional formatting makes it simple to highlight certain values or identify specific cells. Based on a condition, this alters the look of a cell range (or criteria). Conditional formatting can be used to highlight cells that contain values that fulfill a specific requirement.
Conditional formatting is used to alter the look of cells in a range based on the conditions you specify. The criteria are rules that are based on numerical numbers or matching language.
Learn more about Conditional Formatting:
https://brainly.com/question/16014701
#SPJ1
Convert totalseconds to hours, minutes, and seconds, finding the maximum number of hours, then minutes, then seconds. Ex: If the input is 25274 , the output is: Hours: 7 Minutes: 1 Seconds: 14 Nole: An hour has 3600 seconds. A minule has 60 seconds.
Answers
totalSeconds have been converted to hours, minutes and seconds=7hr 1min 14sec
Code of the problem
int main()
{
int totalSeconds;
int numHours;
int numMinutes;
int numSeconds;
cin >> totalSeconds;
// total number of hours.
numHours = totalSeconds / 3600;
totalSeconds %= 3600;
// total number of minutes
numMinutes = totalSeconds / 60;
totalSeconds %= 60;
// total number of seconds
numSeconds = totalSeconds;
cout << "Hours: " << numHours << endl;
cout << "Minutes: " << numMinutes << endl;
cout << "Seconds: " << numSeconds << endl;
return 0;
}
To know more about Hour,click on the link :
https://brainly.com/question/13533620
#SPJ1
Answer:
numHours = totalSeconds/ 3600;
numMinutes = totalSeconds % 3600 / 60;
numSeconds = totalSeconds % 60;
Explanation:
18. Which hardware component interprets and carries out the instructions contained in the software?
Answers
The hardware component that significantly interprets and carries out the instructions contained in the software is known as the central processing unit or the processor.
Which part of the computer carries out program instruction?The processor that is also called a CPU (central processing unit), is the electronic component that interprets and carries out the basic instructions that operate the computer. Memory consists of electronic components that store instructions waiting to be executed and data needed by those instructions.
Therefore, the central processing unit or the processor is the component of hardware that interprets and carries out the basic instructions that operate a computer.
To learn more about the Central processing unit, refer to the link:
https://brainly.com/question/474553
#SPJ1
Arrange the given binary numbers in increasing order of their decimal equivalent. 110111 101101 110010 111110

Answers
Answer:
101101 < 110010<110111 <111110
Explanation:
We will convert binary number to their decimal equivalent
110111 - (1 × 2⁵) + (1 × 2⁴) + (0 × 2³) + (1 × 2²) + (1 × 2¹) + (1 × 2⁰) = (55)₁₀
101101 - (1 × 2⁵) + (0 × 2⁴) + (1 × 2³) + (1 × 2²) + (0 × 2¹) + (1 × 2⁰) = (45)₁₀
110010 - (1 × 2⁵) + (1 × 2⁴) + (0 × 2³) + (0 × 2²) + (1 × 2¹) + (0 × 2⁰) = (50)₁₀
111110 - (1 × 2⁵) + (1 × 2⁴) + (1 × 2³) + (1 × 2²) + (1 × 2¹) + (0 × 2⁰) = (62)₁₀
Now, arranging the given binary numbers in increasing order of their decimal equivalent , we get -
101101 < 110010<110111 <111110
Answer: 101101<110010<110111<111011<111110
used a binary translator.
Explanation:
Major stress in your life can cause:
O a. headaches and Insomnia
O b. Fatigue and dry mouth
O c. Muscular and abdominal pain
O d. All of the above
Answers
explanation- Chronic stress can disrupt every system in your body. For example, your immune system, reproductive system, and can increase the risk of a heart attack.
who here has a crush on jk from bts but feels more mature than him
Answers
Answer:
Nope not K-pop fan
Explanation:
Will mark brainliest :) _____ is a way to protect a system from hackers.
A. Installing a botnet
B. Making "Deny" the default
C. Using packet sniffers
D. Installing a troll on the server
Answers
Answer: B
Explanation:
A way to protect a system from hackers is : ( B ) Making "Deny" the default
Protecting a system from hackersThe best way to protect a system from hackers is the use of firewalls such as making "Deny" the default whenever a user tries to enter the system. Firewalls are software programs which help protect system from hackers penetration.
Hence we can conclude that A way to protect a system from hackers is : ( B ) Making "Deny" the default.
Learn more about firewalls : https://brainly.com/question/13693641.
#SPJ2
The marketing company era marks the time when companies realized they needed to switch from just trying to sell
products to actually trying to satisfy the needs of customers.
True
False
Answers
Answer:
False
Explanation:
I hope this is right