legal regulation of assisted reproductive technology is well-defined and serves as a basis to adjudicate ethical disputes.
Answers
The majority of current public laws are collected in the 50 titles of the United States Code, which is divided into 50 subject-specific sections.
Why are legal regulations important?The Code of Federal Regulations lists regulations by subject and organizes them by the executive departments and agencies that make them. Looking up Federal Laws, Acts, and Bills. The majority of current public laws are collected in the 50 titles of the United States Code, which is divided into 50 subject-specific sections.
An official rule is defined as a regulation. Within their purviews, the government's administrative agencies are only given limited authority to regulate behavior. Legislative authority to develop and implement the "regulations" has been delegated to these agencies.
Both social and economic regulation are recognized by economists.
Our rights as citizens are protected by laws, which guard against violations on the part of other people, groups, or even the government. Laws also guarantee our general safety.
To learn more about legal regulation refer to:
https://brainly.com/question/25368237
#SPJ4
Related Questions
how to make windiws 10 to wundows 21?
Answers
Answer:
You multiply it.
All of the following would be useful information to capture and evaluate as end-of-project lessons learned EXCEPT:
a. Areas for which a different method might yield better results
b. What went well that team members think should be copied and/or adapted for use on future work
c. Information about mistakes and what went wrong
d. Names of team members who made the mistakes and should be blamed
Answers
All of the following would be useful information to capture and evaluate as end-of-project lessons learned EXCEPT: d. Names of team members who made the mistakes and should be blamed
What is the lesson?When capturing and assessing lessons learned at the conclusion of a venture, it is vital to center on valuable criticism and recognize ranges for advancement instead of doling out fault to particular group individuals.
In all, the center of lessons learned ought to be on recognizing zones for enhancement, capturing effective hones, and advancing a culture of continuous learning and change, instead of accusing people for botches.
Learn more about lessons from
https://brainly.com/question/25547036
#SPJ1
Professor Gekko has always dreamed of inline skating across North Dakota. He plans to cross the state on highway U.S. 2, which runs from Grand Forks, on the eastern border with Minnesota, to Williston, near the western border with Montana. The professor can carry two liters of water, and he can skate m miles before running out of water. (Because North Dakota is relatively flat, the professor does not have to worry about drinking water at a greater rate on uphill sections than on flat or downhill sections.) The professor will start in Grand Forks with two full liters of water. His official North Dakota state map shows all the places along U.S. 2 at which he can refill his water and the distances between these locations. The professor’s goal is to minimize the number of water stops along his route across the state.
a. Give an efficient algorithm by which he can determine which water stops he should make.
b. Prove that your strategy yields an optimal solution, and give its
Answers
The efficient algorithm by which he can determine which water stops he should make; has been determined below and the strategy which is the greedy strategy has been proven to yield an optimal solution.
To solve this question optimally, we will make use of the greedy solution.
In this method, we will maximize the distance that can be covered from a particular point in such a way that there must be a place where water can be gotten before a run out is experienced.
Now, the first point at which there will be a stop should be located at a point that is farthest from the starting position and is also made to be ≤ m miles from the starting position.
Now, this this situation is one that shows optimal substructure and since our first stopping point will be made to be at p, it means that we are solving the sub-question with the assumption that our starting point is at p.
When we combine the two stated plans above, we will arrive at an optimal solution for the normal reasons via cut and paste.
B) Now we need to show that the greedy approach earlier used produce a first stopping point which is contained in the optimal solution.
Let O represent any optimal solution whereby the professor stops at positions o₁, o₂, o₃....oₙ.
Let h₁ represent the farthest stopping point that is reachable from the starting point. Then we can replace o₁ by h₂ to generate a modified solution H since o₁ - o₂ < o₂ - h₁.
Finally, we can really make it to the positions in H without having to run out of water and since H has the same number of stops, we can conclude that h₁ is contained in one of optimal solution.
Therefore our strategy which is the greedy strategy has been proven to work.
Read more about algorithms at; https://brainly.com/question/24793921
We have stated that key size of the ideal block cipher is n x 2 n bits. However, if there are 2 n! possible mappings, the key length should be log2 2 n! bits - the key is able to discriminate among the different mappings. Explain the discrepancy, noting that log2 2 n !
Answers
The statement that the key size of an ideal block cipher is n x 2^n bits assumes that each possible key uniquely maps to a single permutation of the plaintext.
What is cipher?A cypher is an algorithm used in cryptography that consists of a set of stages that can be followed as a process to conduct encryption or decryption. Encipherment is a different, less frequently used term.
The same permutation of the plaintext may correspond to more than one key. For instance, there are n! potential permutations of the plaintext if the block size is n bits.
Instead of just assuming that each key uniquely maps to a single permutation, the key length must be big enough to be able to distinguish between all potential acceptable permutations in order to account for this.
The number of bits required to express 2n! different permutations can be estimated as log2(2n!).
Thus, the discrepancy between n x \(2^n\) and log2(2n!) is due to the assumption of unique mappings in the former, and the need to account for all possible valid permutations in the latter.
For more details regarding cipher, visit:
https://brainly.com/question/13155546
#SPJ9
List questions you would be asking to software developers about the form.
List potential risks if there are any with the form.

Answers
difference between liner land nonlinear presentation
Answers
Answer: The linear multimedia will go from the start all the way through to the finish without variation. Non-linear media is the opposite; it doesn't follow that one-way structure and instead allows free movement around all aspects of the multimedia in any order.
What additional uses of technology can u see in the workplace
Answers
Answer:
Here are some additional uses of technology in the workplace:
Virtual reality (VR) and augmented reality (AR) can be used for training, simulation, and collaboration. For example, VR can be used to train employees on how to operate machinery or to simulate a customer service interaction. AR can be used to provide employees with real-time information or to collaborate with colleagues on a project.Artificial intelligence (AI) can be used for a variety of tasks, such as customer service, data analysis, and fraud detection. For example, AI can be used to answer customer questions, identify trends in data, or detect fraudulent activity.Machine learning can be used to improve the accuracy of predictions and decisions. For example, machine learning can be used to predict customer churn, optimize marketing campaigns, or improve product recommendations.Blockchain can be used to create secure and transparent records of transactions. For example, blockchain can be used to track the provenance of goods, to manage supply chains, or to record financial transactions.The Internet of Things (IoT) can be used to connect devices and collect data. For example, IoT can be used to monitor equipment, track assets, or collect data about customer behavior.These are just a few of the many ways that technology can be used in the workplace. As technology continues to evolve, we can expect to see even more innovative and creative uses of technology in the workplace.
Question 4: What will be the output of the code? Show a complete analysis.
#include
int main(void)
{
int A[3][3]={{1,4,3},{6,2,4},{-3,8,2}};
int s;
for(int i = 0; i<=2; i++)
{
S = ALOIi]+A[111]+A[21i];
printf("%d",s);
}
return 0;
}
Answers
Answer:
The output of the code is 8
A brand of shame .. from infancy " is a brand on Jocasta
Answers
Answer: DIDN'T UNDERSTAND
How many binary digits does a single hexadecimal digit represent?
Answers
Four binary digits
A single hexadecimal digit can represent four binary digits.
1. A network administrator was to implement a solution that will allow authorized traffic, deny unauthorized traffic and ensure that appropriate ports are being used for a number of TCP and UDP protocols.
Which of the following network controls would meet these requirements?
a) Stateful Firewall
b) Web Security Gateway
c) URL Filter
d) Proxy Server
e) Web Application Firewall
Answer:
Why:
2. The security administrator has noticed cars parking just outside of the building fence line.
Which of the following security measures can the administrator use to help protect the company's WiFi network against war driving? (Select TWO)
a) Create a honeynet
b) Reduce beacon rate
c) Add false SSIDs
d) Change antenna placement
e) Adjust power level controls
f) Implement a warning banner
Answer:
Why:
3. A wireless network consists of an _____ or router that receives, forwards and transmits data, and one or more devices, called_____, such as computers or printers, that communicate with the access point.
a) Stations, Access Point
b) Access Point, Stations
c) Stations, SSID
d) Access Point, SSID
Answer:
Why:
4. A technician suspects that a system has been compromised. The technician reviews the following log entry:
WARNING- hash mismatch: C:\Window\SysWOW64\user32.dll
WARNING- hash mismatch: C:\Window\SysWOW64\kernel32.dll
Based solely ono the above information, which of the following types of malware is MOST likely installed on the system?
a) Rootkit
b) Ransomware
c) Trojan
d) Backdoor
Answer:
Why:
5. An instructor is teaching a hands-on wireless security class and needs to configure a test access point to show students an attack on a weak protocol.
Which of the following configurations should the instructor implement?
a) WPA2
b) WPA
c) EAP
d) WEP
Answer:
Why:
Answers
Network controls that would meet the requirements is option a) Stateful Firewall
Security measures to protect against war driving: b) Reduce beacon rate and e) Adjust power level controlsComponents of a wireless network option b) Access Point, StationsType of malware most likely installed based on log entry option a) RootkitConfiguration to demonstrate an attack on a weak protocol optio d) WEPWhat is the statement about?A stateful firewall authorizes established connections and blocks suspicious traffic, while enforcing appropriate TCP and UDP ports.
A log entry with hash mismatch for system files suggest a rootkit is installed. To show a weak protocol attack, use WEP on the access point as it is an outdated and weak wireless network security protocol.
Learn more about network administrator from
https://brainly.com/question/28729189
#SPJ1
you have a 10vdg source available design a voltage divider ciruit that has 2 vdc , 5vdc , and 8 vdc available the total circuit current is to be 2mA
Answers
If you try to divide 10V in three voltages, the sum of the three voltages must be equal to the total voltage source, in this case 10V. Having said this, 2 + 5 + 8 = 15V, and your source is only 10V. So you can see is not feasible. You can, for example, have 2V, 5V and 3V, and the sum is equal to 10V. Before designing the circuit, i.e, choosing the resistors, you need to understand this. Otherwise, I suggest you to review the voltage divider theory.
For instance, see IMG2 in my previous post. If we were to design a single voltage divider for the 5VDC, i.e, 50% of the 10V source, you generally choose R1 = R2., and that would be the design equation.
In order to estimate the cost of painting a house, a painter needs to know the surface area of the exterior. Develop an algorithm for computing that value. Your inputs are the width, length, and height of the house, the number of windows and doors, and their dimensions. (Assume the windows and doors have a uniform size.)
Answers
Algorithms are used as prototypes for a complete program.
The algorithm to print the surface area of the exterior is as follows:
1. Start
2. Input the number of windows (n1)
3. Input the number of doors (n2)
4. Input the Length and Width of the windows (L1, W1)
5. Input the Length and Width of the doors (L2, W2)
6. Input Length, Width and Height of the Building
7. Calculate the area of the all windows: Area1 = n1 * L1 * W1
8. Calculate the area of the all doors: Area2 = n2 * L2 * W2
9. Calculate the surface area of the building: Area = 2 * (Length * Width + Length * Height + Width * Height)
10. Calculate the surface area of the exterior. Exterior = Area - Area1 - Area2
11. Display the surface area that can be painted; Exterior
12. Stop
The algorithm is self-explanatory, as all 12 lines of the algorithm are in plain English language.
The surface area of the exterior is calculated by subtracting the areas of all doors and windows from the surface area of the building.
Read more about algorithms at:
https://brainly.com/question/24568182
a student received a poor grade on her last two language art tests. what are the steps she should take for solving this problem
PLEASE HURRYYYY!
Answers
Answer:
Study and do practice tests
Which printing process is represented in this scenario? A newsroom is preparing a copy of a daily paper. Typed articles are hung throughout the room. Editors are reading through each article, cutting out pieces and taping new text over old text.
- phototypesetting
- linotype
- movable type
- relief printing
Answers
To move an object to the bottom of the stack, click the Send Backwards arrow and then click Send to Back in the Arrange group on the DRAWING TOOLS _____ tab.
Answers
Answer:
thank you good sir!!!!!!!!
Consider function search(elm, low, high, myArray) that searches for the value elm in the array myArray between the indexes low and high and returns the index where elm is found in the array or returns -1 if not found.
For example, if myArray is [4, 7, 8, 9, 12, 56], then you have the following:
search(12, 0, 5, myArray) returns 4
search(10, 0, 5, myArray) returns -1
Now consider the linear and binary algorithms below for the function search:
Linear Search
Function search(elm,low,high, myArray)
index = low
While(index <= high)
If myArray[index] == elm then
Return index // found
Else index = index + 1
End While
Return -1 // not found
End Function
Binary Search
Function search(elm,low,high, myArray)
While(high >= low) then
mid = (low + high) / 2
If (myArray[mid] == elm
Return mid; // found
Else
If (myArray[mid] > elm) then // search in the left half
high = mid-1
Else // search in right half
Low = mid +1
End While
Return -1 // not found
End Function
Complete the following:
How many iterations are performed in each algorithm for the function call search(12, 0, 6, myArray) if myArray = [2, 3, 6, 9, 12, 15, 19]?
Which of these two algorithms runs faster?
Why do you believe that one runs faster than the other?
Answers
The iterations that are performed in each algorithm for the function is 5.
Binary search algorithms run faster because of their searching way is based on divide and conquer technique
What is an algorithm?An algorithm is a limited set of precise instructions that are usually applied to carry out a computation or solve a group of related problems. Calculations and data processing are done according to specifications called algorithms.
Case 1: Linear Search
The number of Iterations is 5, and the returned index value will be 4, that is the after 4th Iteration(that is at 5th) the array element will be matched with the searching element
Case 2: Binary Search
The number of Iterations is 3, and the returned index value will be 4, that is the after 2nd Iteration (that is at 3rd )the array element will be matched with the searching element.
Because there are fewer iterations in the Binary Search algorithm than there are in the Linear Search algorithm, it operates more quickly.
Learn more about algorithm on;
https://brainly.com/question/24953880
#SPJ1
How did early computing device such as Charles Babbage's analytical engine and Ada Lovelace's contributions set the foundation for modern computing
Answers
Early computing devices, such as Charles Babbage's Analytical Engine and Ada Lovelace's contributions, played a crucial role in setting the foundation for modern computing. Here's how their work contributed to computing development:
1. Charles Babbage's Analytical Engine: Babbage designed the Analytical Engine, a mechanical general-purpose computer concept, in the 19th century. Although the Analytical Engine was never fully built, its design and principles laid the groundwork for modern computers. Key features of the analytical engine include:
a. Stored Program: Babbage's Analytical Engine introduced the concept of storing instructions and data in memory, allowing complex calculations and tasks.
b. Control Flow: The Analytical Engine could make decisions and perform conditional operations based on previous computations, resembling the modern concept of control flow in programming.
c. Loops: Babbage's design incorporated looping mechanisms, enabling repetitive instruction execution, similar to modern programming languages.
2. Ada Lovelace's Contributions: Ada Lovelace, an English mathematician, collaborated with Charles Babbage and made significant contributions to computing. Her work on Babbage's Analytical Engine included writing the first algorithm intended for machine implementation. Lovelace realized the potential of the analytical engine beyond numerical calculations and recognized its capability for processing symbols and creating complex algorithms. Her insights laid the foundation for computer programming and algorithms.
Lovelace's ideas about the analytical engine extended beyond what was initially envisioned. He stressed the importance of machines handling more than just numbers. Her contributions demonstrated computers' potential to perform tasks beyond basic calculations and numerical processing.
Collectively, Babbage's analytical engine and Lovelace's contributions provided early conceptual frameworks for modern computing. Their ideas influenced subsequent pioneers in the field, and the concepts they introduced paved the way for the development of the digital computers we use today.
To prepare his book report on The Adventures of Tom Sawyer, Anand must research life on the Mississippi River in the 1800s. Which strategy should Anand use in examining both the book and his research?
Answers
While setting up annetwork segment you want to check the functionality cable before putting connectors on them. You also want to meaure the termination point or damange in cable which tool used
Answers
A network is divided into several parts (subnets) using network segmentation, which creates smaller, independent networks for each segment.
What is network Segementation?Segmentation works by regulating the network's traffic flow. The term "network segmentation" should not be confused with "microsegmentation," which limits east-west communication at the workload level in order to lower an organization's network attack surface.
Despite having some uses, microsegmentation should not be confused with standard network segmentation.
A network is divided into several zones via network segmentation, and each zone or segment is independently managed. To regulate what traffic is allowed to pass through the segment and what is not, traffic protocols must be used.
Dedicated hardware is used to create network segments that are walled off from one another and only permit users with the proper credentials to access the system.
Therefore, A network is divided into several parts (subnets) using network segmentation, which creates smaller, independent networks for each segment.
To learn more about network, refer to the link:
https://brainly.com/question/15088389
#SPJ1
Given two integers low and high representing a range, return the sum of the integers in that range. For example, if low is 12 and high is 18, the returned values should be the sum of 12, 13, 14, 15, 16, 17, and 18, which is 105. If low is greater than high, return 0.
Examples:
sumRange(12, 18) -> 105
sumRange(1, 5) -> 15
sumRange(1, 100) -> 5050
Answers
System.out.println(sumRange(12, 18)); // prints 105
System.out.println(sumRange(18, 12)); // prints 0
System.out.println(sumRange(18, 18)); // prints 18
}
public static int sumRange(int low, int high)
{
int sum = 0;
for (int val = low; val <= high; val++){
sum += val;
}
return sum;
}
}
TEST 2
DESCRIPTION
This test case checks your HTML contains a red color style.
PASS?
x
MESSAGE
Ensure you are using red, #f00, #ff0000, or rgb(255, 0, 0) to style your element
red.
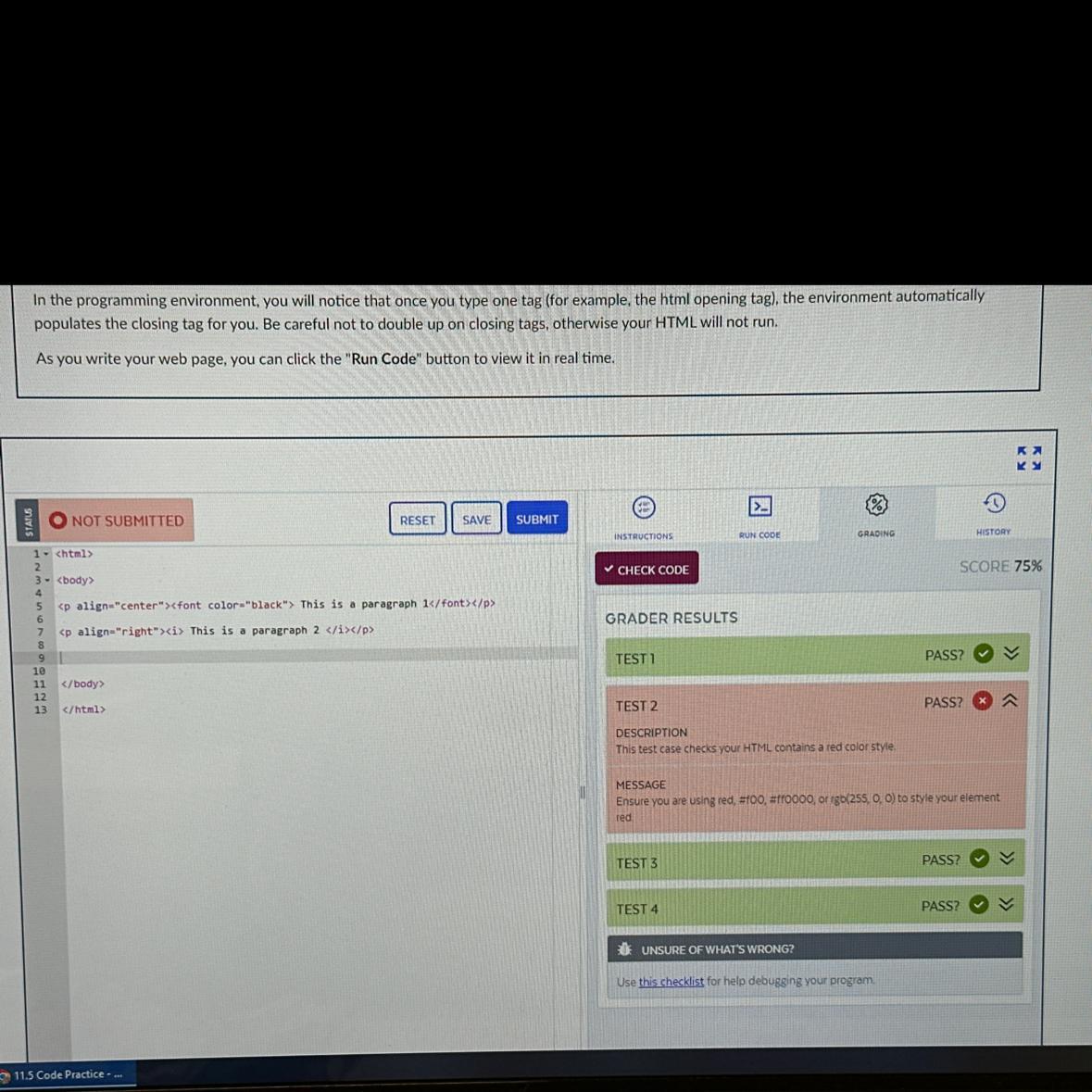
Answers
The test case has failed, as indicated by the 'x' in the 'PASS?' field. The message suggests that the HTML element should be styled using the color red, either through the color keyword 'red', or using one of the specified color codes (#f00, #ff0000) or the RGB value (rgb(255, 0, 0)).
What is the solution to the above problem?To fix the issue, the HTML element needs to be styled with one of the specified color codes or keywords. For example, to style a text element in red using the color keyword, the following CSS rule can be used:
color: red;
Alternatively, to use the hex color code #f00, the following rule can be used:
color: #f00;
Once the element has been styled correctly, the test case should be rerun to confirm that it passes.
Learn more about HTML on:
https://brainly.com/question/17959015
#SPJ1
What are five types of applications you can create in Visual Basic 2017?
Answers
Answer:
1) Windows Desktop applications
2) Windows Store apps
3) Web/Cloud applications
4) Office/SharePoint applications
5) Database applications.
Windows console mode applications.
Standard Windows applications.
Windows services.
Windows controls and Windows control libraries.
Web (ASP.NET) applications.
Web services.
Web controls and web control libraries.
Drag each tile to the correct box.
Match the certifications to the job they best fit.
CompTIA A+
Cisco Certified Internetwork Expert (CCIE)
Microsoft Certified Solutions Developer (MCSD)
help desk technician
network design architect
software developer
Answers
Answer:
software developer- microsoft certified solutions developer
help desk technician- CompTIAA+
network design architect- Cisco certified internetwork expert
Explanation
edmentum
Work out and List the Big-Oh notation that corresponds to each of the following examples. Afterwards, list them by the order of complexity from LEAST to MOST.
(1.1) A bacteria that doubles itself every generation N.
(1.2) Following a single path along a branching story with N choices that change the story until you reach an ending.
(1.3) Pulling a single ball out of a pit filled with N balls.
(1.4) Searching the N rooms in a house for your keys.
(1.5) Trying to route a band’s world tour through N cities with the shortest mileage possible.
(1.6) Breaking an equation with N pieces down into smaller, simpler pieces, then solving those pieces to solve the entire equation.
Answers
An example of an O(2n) function is the recursive calculation of Fibonacci numbers. O(2n) denotes an algorithm whose growth doubles with each addition to the input data set. The growth curve of an O(2n) function is exponential - starting off very shallow, then rising meteorically.This function runs in O(n) time (or "linear time"), where n is the number of items in the array.
If the array has 10 items, we have to print 10 times. If it has 1000 items, we have to print 1000 timesHere we're nesting two loops. If our array has n items, our outer loop runs n times and our inner loop runs n times for each iteration of the outer loop, giving us n2 total prints.
Thus this function runs in O(n2) time (or "quadratic time"). If the array has 10 items, we have to print 100 times. If it has 1000 items, we have to print 1000000 times.An example of an O(2n) function is the recursive calculation of Fibonacci numbers. O(2n) denotes an algorithm whose growth doubles with each addition to the input data set.
The growth curve of an O(2n) function is exponential - starting off very shallow, then rising meteorically.When you're calculating the big O complexity of something, you just throw out the constantsThis is O(1 + n/2 + 100), which we just call O(n).
Why can we get away with this? Remember, for big O notation we're looking at what happens as n gets arbitrarily large. As n gets really big, adding 100 or dividing by 2 has a decreasingly significant effect.
O(n3 + 50n2 + 10000) is O(n3)O((n + 30) * (n + 5)) is O(n2)
Again, we can get away with this because the less significant terms quickly become, well, less significant as n gets big.
hope it helps you.....*_*
In a balanced budget, the amount is the amount
Answers
In a balanced budget, the Income amount is same as the expense amount.
What is a balanced budget?A balanced budget is one in which the revenues match the expenditures. As a result, neither a fiscal deficit nor a fiscal surplus exist. In general, it is a budget that does not have a budget deficit but may have a budget surplus.
Planning a balanced budget assists governments in avoiding excessive spending and focuses cash on regions and services that are most in need.
Hence the above statement is correct.
Learn more about Budget:
https://brainly.com/question/15683430
#SPJ1
Assume the variable s is a String and index is an int. Write an if-else statement that assigns 100 to index if the value of s would come between "mortgage" and "mortuary" in the dictionary. Otherwise, assign 0 to index.
Answers
Using the knowledge in computational language in python it is possible to write a code that Assume the variable s is a String and index is an int.
Writting the code:Assume the variable s is a String
and index is an int
an if-else statement that assigns 100 to index
if the value of s would come between "mortgage" and "mortuary" in the dictionary
Otherwise, assign 0 to index
is
if(s.compareTo("mortgage")>0 && s.compareTo("mortuary")<0)
{
index = 100;
}
else
{
index = 0;
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

In this network, devices are connected directly to each other without any additional
networking devices between them. Individual users are responsible for their own
resources and can decide which data and devices to share.
Explain this type of network with its advantages and disadvantages
Answers
The network described in the prompt is a Peer-to-Peer (P2P) network, also known as a "workgroup."
Advantages of a P2P networkCost-effective: P2P networks are relatively inexpensive to set up and maintain since they don't require any additional networking equipment or servers.
Flexibility: In a P2P network, devices can be added or removed easily without affecting the rest of the network.
Decentralized: Since there is no central server or device controlling the network, it is more resistant to failure and can continue to function even if some devices are offline.
Security: P2P networks can be more secure since there is no central point of attack or failure, and individual users have more control over their own resources and security settings.
Disadvantages:Limited scalability: P2P networks are not designed to handle large numbers of devices or users, and as the network grows, it can become difficult to manage and maintain.
Reliability: Since each device is responsible for its own resources, the network can be less reliable if individual devices fail or are offline.
Security: While P2P networks can be more secure in some ways, they can also be vulnerable to malware and other security threats if individual devices are not properly secured and maintained.
Learn more about Peer-to-Peer at:
https://brainly.com/question/10571780
#SPJ1
which statement best describes application developers

Answers
The statement that best describes a website builder is option C. a tool that enables developers to create websites without programming knowledge
A website builder is a software tool that allows individuals or organizations to create websites without the need for advanced technical skills or knowledge of programming languages.
Website builders are designed to simplify the website creation process by providing an intuitive drag-and-drop interface and pre-designed templates that users can customize with their own content.
Therefore, With a website builder, users can create and edit web pages, add images and videos, and customize the design and layout of their website without needing to write code.
Read more about programming here:
brainly.com/question/23275071
#SPJ1
what does the GPU do?
Answers
Answer:
With graphics processing units (GPU), many pieces of data can be processed simultaneously, which makes them useful for applications such as machine learning, editing, and gaming. It is an electronics circuit capable of accelerating the processing of images, animations, and videos.
Explanation: