Leading to the creation of the World Wide Web, the __ allowed users to send documents and images across networks
Answers
Leading to the creation of the World Wide Web, the World Wide Web (WWW) allowed users to send documents and images across networks.
What was the technology enabling document and image transmission across networks?The World Wide Web, commonly referred to as the WWW or simply the web, revolutionized the way information is shared and accessed. Created by British computer scientist Sir Tim Berners-Lee in the late 1980s, the World Wide Web is an interconnected system of documents and resources linked by hyperlinks.
It is built on the foundation of the internet, which provides the infrastructure for transmitting data across networks. The World Wide Web introduced a standardized format for documents called HTML (Hypertext Markup Language) and a protocol for transferring these documents called HTTP (Hypertext Transfer Protocol).
Learn more about World Wide Web
brainly.com/question/14477788
#SPJ11
Related Questions
ideally, the backrest is tilted back slightly, so when you turn the wheel your shoulders are __ the seat
Answers
**Parallel** to the seat
Which of the following statements does not explain the difference between safety stock
Inventory and the cross docking method?
Answers
The statements does not explain the difference is that Cross-docking reduces inventory and storage space requirements, but handling costs and lead times tend to increase.
What is the difference between safety stock inventory and the cross-docking method?safety stock inventory is known to be a kind of traditional warehousing systems that needs a distributor to have stocks of product already at hand to ship to their customers.
But a cross-docking system is one that is based on using the new and best input such as technology and business systems to produce a JIT (just-in-time) shipping method.
Learn more about safety stock Inventory from
https://brainly.com/question/18914985
How can we solve mental stress?
Hello can anyone answer
Answers
Answer:
Please don't delete it. Because other people did!
Explanation:
Use guided meditation, Practice deep breathing, Maintain physical exercise and good nutrition!
By making yourself comfortable around your environment.I know it can be hard but try making yourself feel distracted from stress.Have a break from what you are doing and take your time to heal.
Explanation:
what is the full form of GUI
Answers
Graphical User Interface
HELP ME!!! I WILL GIVE BRAINLY THINGY!!!
What does the code if (num2==50){ do?
Answers
Answer:
What subject is this?
Explanation:
Can someone help me on how to start this essay?

Answers
Answer:
Start off with an interesting introduction (add questions) make it interesting.
Software developers_____their programs, while buyers only own the right to____use the software.
Answers
The majority of software works are copyright protected, which means that in order to use the software in any way, you must first obtain a license from the developer or other copyright holder.
How is using a piece of software sanctioned legally?The majority of software works are copyright protected, which means that in order to use the software in any way, you must first obtain a license from the developer or other copyright holder. Public domain products, on the other hand, are not protected by copyright; anybody is free to alter and utilize such software.The software application may be made available to users for a one-time price in exchange for ownership rights. It is generally accepted that this strategy—purchasing the license up front and acquiring the right to use the software perpetually—is the conventional method of owning software. Perpetual licenses are a particular kind of buying agreement.To learn more about software refer to:
https://brainly.com/question/28224061
#SPJ1
You have a network ID of 192.168.55.0 and you need to divide it into multiple subnets. You need at least 30 host ID's in each subnet. What is the maximum number of subnets you could have?
Answers
8 subnets could be present in this format that was taken.
Use the following equation: 2n, where n is the quantity of borrowed host bits, to get the number of potential subnets.
And must utilize 5 bits for our hosts because this is a Class C address (25 - 2 = 30 hosts). 3 bits are still available for use in subnets. 8 subnets out of 23.
The last three bits of the last octet are able to be employed in host ID addressing, which can be seen using the binary format above. The router in question is shown to have connections with four of the 256 potential subnets. Either the subnet address associated with the Host ID set for it or the Internet subnet ID itself serves as identifier for each subnet. 0. The host ID is sent to the router interfaces.
Learn more about subnets, here:
https://brainly.com/question/15055849
#SPJ4
the processing is done in the
Answers
Answer:
CPU Central Processing Unit
Answer:
CPU.... I'm not sure but it might be right or can u put the full question because it sorta don't make any sense
what channel does the news come on?
i dont have cable i have roku :\
Answers
Answer:
I have roku to
Explanation:
I think there's is a channel for it just search up news it probs come up
PLEASE HURRY I WILL GIVE BRANLIEST
Which of the following statements is true concerning cloud computing?
- provides storage and processing capabilities at the user’s location
- provides storage and processing capabilities using computers that are owned and maintained by the user
-reduces the cost of storage and processing, allowing smaller businesses to be more competitive
-can only be accessed during business hours
Answers
Answer:
provides storage and processing capabilities using computers that are owned and maintained by user
The statement which is true regarding cloud computing is Provides storage and processing capabilities using computers that are owned and maintained by user .
What is cloud computing?The on-demand availability of computer system resources, in particular data storage (cloud storage) and processing power, without direct active supervision by the user, is known as cloud computing. Functions in large clouds are frequently dispersed over several sites, each of which is a data center.
Cloud computing often uses a "pay as you go" model, which can help reduce capital expenses but may also result in unanticipated running expenses for users.
Cloud computing depends on resource sharing to accomplish coherence. The on-demand, pay-as-you-go delivery of IT resources over the Internet is known as cloud computing.
Therefore, The statement which is true regarding cloud computing is Provides storage and processing capabilities using computers that are owned and maintained by user .
To learn more about cloud computing, refer to the link:
https://brainly.com/question/11973901
#SPJ2
What symbol indicates that material has been copyrighted?
Answers
Answer:
Ermmmmmm...
I Think if a thing doesn't hhave a trademark or something like that.
Explanation:
Up there
Answer: I believe it’s the circle one with the c, sorry if I’m rong ༼つ ◕◡◕ ༽つ
Explanation:
In the bremmer article, the author states that _________ translates into greater risks.
Answers
Answer:
instability
Explanation:
need help on question 5! no links pls

Answers
Answer: less than 50%, it’s about 49%
Explanation:
Answer:
59.5
so I would say the 3 third option
Which of the following is not a method used in the preseason to promote an All-America candidate?A. A websiteB. MailersC. Media guideD. Preseason MagazinesE. None of the Abov
Answers
The method that is not used in the preseason to promote an All-America candidate is none of the Above. The correct option is E.
What is promotion?Promotion is a marketing tactic employed by my marketers to publicize their products to their consumers and future buyers in the business world.
When there is an ongoing paid or unpaid effort to promote/publicize the concepts, products, or services of a certain company, that promotion is said to be active. The term "promotion" covers a wide range of activities designed to increase public awareness or advance a product.
Therefore, the correct option is E. None of the Above.
To learn more about promotion, refer to the link:
https://brainly.com/question/26239758
#SPJ1
_______ is a tool for developing a virtual representation of any three-dimensional object.
Answers
A 3D modeling software is a tool for developing a virtual representation of any three-dimensional object.
3D modeling software allows users to create digital 3D models of objects, characters, and environments. These models can be used for a variety of applications, such as video game development, animation, and product design. They provide a way to visualize and manipulate objects in three-dimensional space, allowing designers and artists to create complex and detailed designs with precision.
You can learn more about 3D modeling software at
https://brainly.com/question/30590141
#SPJ11
Stacy is in the process of creating a storyboard for her personal website, but she is unable to decide which storyboarding technique to use. Which technique would work best for her?
Answers
Answer:
Webbed storyboard technique
Explanation:
There are several storyboard techniques; however, the best for a website is the webbed storyboard technique.
Coined from the word "web", this technique does not only help in linking pages within the website where a page can be access from other pages, it also links pages of the website to external pages.
An illustration is as follows:
From the homepage of a website, one can access the contact page, the about page, etc.
Each of the listed pages also have link back to the homepage and to every other pages.
Within a word processing program, predesigned files that have layout and some page elements already completed are called
text boxes
templates.
frames
typography
Answers
Answer:
I think it's B) templates
Sorry if it's wrong I'm not sure!!
Explanation:
Within a word processing program, predesigned files that have layout and some page elements already completed are called: B. templates.
In Computers and Technology, word processor can be defined as a processing software program that is typically designed for typing and formatting text-based documents. Thus, it is an application software that avail end users the ability to type, format and save text-based documents such as .docx, .txt, and .doc files.
A template refers to a predesigned file or sample in which some of its page elements and layout have already completed by the software developer.
In this context, predesigned files in a word processing program, that have layout and some page elements already completed by the software developer is referred to as a template.
Read more on template here: https://brainly.com/question/13859569
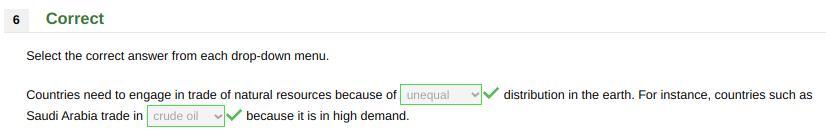
Countries need to engage in trade of natural resources because of distribution in the earth. For instance, countries such as Saudi Arabia trade in because it is in high demand.
Answers
Answer:
unequal, crude oil
Explanation:
Countries need to engage in trade of natural resources because of unequal distribution in the earth. For instance, countries such as Saudi Arabia trade in crude oil because it is in high demand.
Answer: unequal; crude oil
Explanation: Correct on Edmentum
Csc. Please help me
My app costs Imagine you are creating an app that will take 1 month to make. Use the costs below to find out the total cost.
Two developers cost 80,000 AED each per month. Research costs 60,000 AED.
Testing costs 40,000 AED.
One server costs 1000 AED per month.
Customer service costs 30,000 AED per month. a. What is the total cost of your app for one month?

Answers
Answer:
291 000 AED for one month
____, as a technique, is quite similar to e-mail bombing. However, it is accomplished differently and involves enrolling potentially hundreds of target users through e-mail lists and distributed e-mail message systems.
Answers
The term mentioned in the question is "list bombing." It is a technique that is quite similar to e-mail bombing. However, it is accomplished differently and involves enrolling potentially hundreds of target users through e-mail lists and distributed e-mail message systems.
In list bombing, attackers will obtain email addresses and create email addresses in bulk that are often fake, and then add them to a large number of email lists. Through this method, they gain access to the user's email account, and as a result, they receive several emails that they did not opt for. This technique is used to overload email accounts, resulting in lost or delayed legitimate emails. List bombing is a problem because users frequently abandon email accounts as a result of being overwhelmed by unwanted emails, and attackers can later use these accounts to gather information or commit fraud.In conclusion, list bombing is a malicious technique that attackers use to flood target users' email accounts with unwanted emails.
Attackers use this technique to gain access to user's email accounts and later use them to gather sensitive information or commit fraud. It is, therefore, important for email providers to take proactive steps to detect and mitigate this threat to protect their users' email accounts.
To know more about list bombing visit:-
https://brainly.com/question/15087590
#SPJ11
which of the following is an open-source intrusion detection system that provides search and analysis tools to help index collected data?
Answers
The answer is OSSEC, which stands for Open Source Security. OSSEC is an open-source Intrusion Detection System (IDS) that provides search and analysis tools to help index collected data. It is designed to detect and prevent cyber attacks on both local and remote systems and networks, while also providing security log analysis and file integrity checking.
What Is An Intrusion Detection System:The Intrusion detection system is the one that works on detection and prevention systems and determines whether the activity is present that is contrary to organization policy.A monitoring system called an intrusion detection system (IDS) looks for abnormal activity and sends out alarms when it does.a(n) reprsents the intrusion.
More About Intrusion Detection System: https://brainly.com/question/28962475
#SPJ11
Patricia wants to write a program that will determine how many ice cream
cones are left over when the scoops of ice cream are divided by the
cones. Which operation will Patricia need to use?
Answers
Answer:
she will need to use math what else?
iterations ?selection?
Explanation:
what sort of question si this
Answer:
modulus
Explanation:
you can run the windows error-checking tool by using the ________ command from an elevated command prompt.
Answers
You can run the Windows error-checking tool by using the "chkdsk" command from an elevated command prompt.
The HDD is checked for faulty sectors, file system faults to determine whether specific files or folders are misplaced, and mistakes are fixed using Microsoft's error-checking tool. This error-checking tool is also known as "Check Disk." Use this tool to identify and fix HDD issues. Close any active files.
examining the computer system's internal workings or a communications network for proper data delivery.
SFC searches the cache for any vital Windows operating system files that are missing and restores them. Your drive is scanned by CHKDSK to look for faulty sectors and to attempt to correct file system faults.
To know more about chkdsk, click here:
https://brainly.com/question/29350383
#SPJ11
To run the Windows error-checking tool, you can use the chkdsk command from an elevated command prompt.
The chkdsk command stands for "check disk" and is a useful tool for detecting and repairing errors in the file system.To open an elevated command prompt, you can right-click on the Windows Start button and select "Command Prompt (Admin)." Alternatively, you can press the Windows key + X and select "Command Prompt (Admin)" from the menu.Once you have opened the elevated command prompt, you can use the chkdsk command followed by the drive letter that you want to check. For example, to check the C drive, you would use the command "chkdsk C: /f /r /x". The /f switch tells chkdsk to fix any errors it finds, the /r switch tells it to locate bad sectors and recover readable information, and the /x switch tells it to force the drive to dismount before it runs.It's important to note that running the chkdsk command can take some time, depending on the size of the drive and the amount of data stored on it. It's also a good idea to close any open programs and save your work before running the command, as it may cause your computer to restart.For such more questions on chkdsk command
https://brainly.com/question/14666638
#SPJ11
You want to create a pivottable that uses fields from two excel tables. What is the first step?.
Answers
The first step to create a pivot table that uses fields from two Excel tables is to ensure that the tables are properly arranged in Excel. Pivot tables, as the name suggests, summarizes and presents large volumes of data in a more manageable and understandable format.
They are one of the most powerful and versatile tools for data analysis and business intelligence in Excel. Here are the steps to follow when creating a pivot table using fields from two Excel tables:Step 1: Ensure that the tables are properly arranged in ExcelEnsure that the tables are structured and arranged appropriately in Excel. The tables should have a common field that can be used to link them. Make sure that the column headers of the tables are distinct and unique to avoid confusion.Step 2: Select the tablesThe next step is to select the tables that you want to include in the pivot table.
Highlight the entire table, including the headers and column labels. Be sure to include all columns that you want to summarize in the pivot table.Step 3: Click on "Insert" tabClick on the "Insert" tab on the Excel ribbon to display the "Tables" group. Then click on "PivotTable" to start the PivotTable Wizard.
To know more about Excel visit:
https://brainly.com/question/3441128
#SPJ11
Check all that apply to Raster Graphics
in photoshop
only use certain colors
infinitely scalable
made from pixels
based on math
limited scalability
Answers
Answer: made from pixels, limited scalability
Explanation:
everything in PS is made up of pixels and you can see this if you zoom in too much or scale up too much, it will look like Mario 64. It is not like a vector based program, wich uses math to calulate lines so you can scale it indefinetly and it will remain crisp.
If you have an on-premise system and you use AWS Cloud to mirror data or replicate data from your on-premise system, which architectural pattern are you using?
Select one:
a.
Fully Working Low-Capacity Standby
b.
Pilot Light
c.
Multi-Site Active-Active
d.
Backup and Restore
Answers
The architectural pattern that corresponds to using AWS Cloud to mirror or replicate data from an on-premise system is the Multi-Site Active-Active pattern. By using the Multi-Site Active-Active pattern, organizations can achieve increased scalability, resilience, and disaster recovery capabilities.
In the Multi-Site Active-Active pattern, both the on-premise system and the AWS Cloud infrastructure are active and operational simultaneously. The on-premise system serves as one site, while the AWS Cloud serves as another site. Data is replicated or mirrored between these two sites, ensuring that both systems are synchronized and up-to-date.
This pattern allows for high availability and fault tolerance. In case of a failure or disruption in one site, the other site can seamlessly take over and continue serving the workload. The data replication ensures that the systems stay synchronized, minimizing any potential data loss.
It allows them to leverage the flexibility and scalability of the AWS Cloud while maintaining the on-premise system for certain specific requirements or to distribute the workload across multiple locations.
Learn more about data here:
https://brainly.com/question/21927058
#SPJ11
How are computer clasified into different types?
Answers
Answer:
Computers differ based on their data processing abilities. They are classified according to purpose, data handling and functionality. ... According to data handling, computers are analog, digital or hybrid. Analog computers work on the principle of measuring, in which the measurements obtained are translated into data.
A friend wants to build a database of her music collection. What suggestions can you make to help her as she gets started? Select all that apply.
A. She should use a logical, organized naming structure for her music.
B. She must learn SQL to query the database.
C. She should save her most common queries to save time later.
D. She should create separate database files to hold information about her CDs and MP3 files.
Answers
Answer:
A & C
Explanation:
Write a for loop to print the numbers from 20 to 30, inclusive (this means it should include both the 20 and 30). The output should all be written out on the same line. Expected Output 20 21 22 23 24 25 26 27 28 29 30
Answers
Answer:
for b in range(20,31):
print(b, end=" ")
Explanation:
Hint: Variable does not matter. Meaning the b that I put in does not matter. You can put in any other letter you want. Hope it helps!
A loop to print the numbers from 20 to 30, inclusive for b in range(20,31) : print(b, end=" ").
What is loop?Loop is defined as a computer program or script that continuously executes the same commands or processing the same data until told to stop. A loop is used in computer programming to perform a set of instructions or a block of code repeatedly without having to start from scratch each time. The code block is executed in accordance with a particular situation. Loops are the control structures in a program.
Variables are data values that can change depending on the user's response to a query, such as their age. During the running of a program, variables could change. A variable is a piece of memory. It has a name that's connected to that place. The memory location is where data is stored. Variable is irrelevant. In other words, it doesn't matter what b I enter. Any additional letter can be entered.
Thus, a loop to print the numbers from 20 to 30, inclusive for b in range(20,31) : print(b, end=" ").
To learn more about loop, refer to the link below:
https://brainly.com/question/14390367
#SPJ3