Item 27 Printers connected to the Internet that provide printing services to others on the Internet are called
Answers
Item 27 Printers connected to the Internet that provide printing services to others on the Internet are called Internet Printers.
What is the name of a printer connected to the Internet to provide printing services?Internet printers, also known as network printers or cloud printers, are printers that are connected to the Internet and offer printing services to users over the Internet. These printers have the capability to receive print jobs from remote locations and can be accessed by users who are not physically connected to the local network.
By connecting these printers to the Internet, users can send print requests from their devices to the printer's IP address or through cloud-based printing services. Internet printers enable convenient and flexible printing options, allowing users to remotely print documents and files without the need for direct physical closeness to the printer.
Learn more about printers
brainly.com/question/28110846
#SPJ11
Related Questions
1
TIME REMAINING
01:51:06
Zubair needs to change some of the data in a table that he has created. How should he go about selecting a row in
the table?
Moun the mourn nointor in a noint hefore the text in a cell
Answers
Write an LMC program as follows instructions:
A) User to input a number (n)
B) Already store a number 113
C) Output number 113 in n times such as n=2, show 113
113.
D) add a comment with a details exp
Answers
The LMC program takes an input number (n) from the user, stores the number 113 in memory, and then outputs the number 113 n times.
The LMC program can be written as follows:
sql
Copy code
INP
STA 113
INP
LDA 113
OUT
SUB ONE
BRP LOOP
HLT
ONE DAT 1
Explanation:
A) The "INP" instruction is used to take input from the user and store it in the accumulator.
B) The "STA" instruction is used to store the number 113 in memory location 113.
C) The "INP" instruction is used to take input from the user again.
D) The "LDA" instruction loads the value from memory location 113 into the accumulator.
E) The "OUT" instruction outputs the value in the accumulator.
F) The "SUB" instruction subtracts 1 from the value in the accumulator.
G) The "BRP" instruction branches back to the "LOOP" label if the result of the subtraction is positive or zero.
H) The "HLT" instruction halts the program.
I) The "ONE" instruction defines a data value of 1.
The LMC program takes an input number (n) from the user, stores the number 113 in memory, and then outputs the number 113 n times.
To know more about LMC program visit :
https://brainly.com/question/14532071
#SPJ11
How did tribes profit most from cattle drives that passed through their land?
A.
by successfully collecting taxes from every drover who used their lands
B.
by buying cattle from ranchers to keep for themselves
C.
by selling cattle that would be taken to Texas ranches
D.
by leasing grazing land to ranchers and drovers from Texas
Answers
The way that the tribes profit most from cattle drives that passed through their land is option D. By leasing grazing land to ranchers and drovers from Texas.
How did Native Americans gain from the long cattle drives?When Oklahoma became a state in 1907, the reservation system there was essentially abolished. In Indian Territory, cattle were and are the dominant economic driver.
Tolls on moving livestock, exporting their own animals, and leasing their territory for grazing were all sources of income for the tribes.
There were several cattle drives between 1867 and 1893. Cattle drives were conducted to supply the demand for beef in the east and to provide the cattlemen with a means of livelihood after the Civil War when the great cities in the northeast lacked livestock.
Lastly, Abolishing Cattle Drives: Soon after the Civil War, it began, and after the railroads reached Texas, it came to an end.
Learn more about cattle drives from
https://brainly.com/question/16118067
#SPJ1
The length of time that a slide appears before automatically advancing to the next slide can be set in the
A. Timing group under the Transitions tab.
B. Transition to This Slide group under the Transitions tab.
C. Timing group in the Master Slide view.
D. Transition to This Slide group in the Master Slide view.
Answers
Answer:
A.
Explanation:
The transition time between slides can be specified in a presentation. The duration of transition can be set by going to the 'Transitions Tab' then in 'Timing Group/Section'. In the timing group, duration can be increased or decreased, as per the desire. The time is set in seconds in duration section.
So, the length of time between two slides can be changed by going to the 'Timing group' under the 'Transitions Tab'.
Therefore, option A is correct.
Answer:
A
Explanation:
The first thing to do upon notification of a new software patch is to____.a. run automatic updatingb. test the patchc. deploy the patchd. identify the criticality of the patch
Answers
The first thing to do upon notification of a new software patch is to identify the criticality of the patch. Therefore, the correct option is (d) identify the criticality of the patch.
The first thing to do upon notification of a new software patch is to identify the criticality of the patch.
This involves evaluating the severity of the vulnerability or issue that the patch is intended to address and determining the potential impact it could have on the system or network.
Once the criticality of the patch is determined, the next step is to test the patch in a controlled environment to ensure that it does not introduce new issues or conflicts with existing software.
This testing process helps to mitigate the risk of unintended consequences that could arise from deploying an untested patch.
After testing, the patch can be deployed, either through an automatic updating system or through manual installation.
Regularly applying patches is a critical component of maintaining system security and minimizing the risk of cyber attacks and data breaches.
Therefore, the correct option is (d) identify the criticality of the patch.
For more such questions on Software patch:
https://brainly.com/question/20376876
#SPJ11
Find solutions for your homework
Find solutions for your homework
engineeringcomputer sciencecomputer science questions and answersread an integer (>=3 digits) from user input. extract and print the last two digits as an integer. #example 1 user input: 123 desired output: 23 #example 2 user input: 1990 desired output: 90 # read an integer (>=3 digits): a = input() a = int(a) # extract the last two digits: b = (a // 10 %
Question: Read An Integer (>=3 Digits) From User Input. Extract And Print The Last Two Digits As An Integer. #Example 1 User Input: 123 Desired Output: 23 #Example 2 User Input: 1990 Desired Output: 90 # Read An Integer (≫=3 Digits): A = Input() A = Int(A) # Extract The Last Two Digits: B = (A // 10 %
Read an integer (>=3 digits) from user input. Extract and print the last two digits as an integer.
#Example 1
User input:
123
Desired output:
23
#Example 2
User input:
1990
Desired output:
90
# read an integer (>=3 digits):
a = input()
a = int(a)
# extract the last two digits:
b = (a // 10 % 10)
c = (a % 10)
# final output
print(b,c)
this is the code I have so far please show me the correct code using Python and the code I have so far
Answers
The code you have provided is mostly correct. However, you don't need the variable c to extract and print the last two digits. Here's the corrected code:
# read an integer (>=3 digits):
a = input()
a = int(a)
# extract the last two digits:
b = a % 100
# final output
print(b)
In this code, we directly extract the last two digits using the modulo operator % with 100. This will give us the remainder when a is divided by 100, which corresponds to the last two digits. Then we simply print the value of b.
You can replace the code you have so far with this corrected code to achieve the desired output.
To know more about extract click the link below:
brainly.com/question/33223493
#SPJ11
What is the bandwidth available to the memory controller, in MBps (megabytes per second), if the SDRAM (Synchronous Dynamic Random Access Memory) bus is running at 100 MHz (megahertz)
Answers
The bandwidth available to the memory controller, in MBps (megabytes per second), if the SDRAM (Synchronous Dynamic Random Access Memory) bus is running at 100 MHz (megahertz) is 800 MBps.
Therefore, if the SDRAM bus is running at 100 MHz, the memory controller's bandwidth will be 800 MBps. Furthermore, the SDRAM is a type of RAM that operates synchronously with the system bus. SDRAM is a type of dynamic random-access memory (DRAM) that runs on a system clock in computers.
The data bandwidth of a memory device is a measure of how much data it can transmit per second. In other words, it refers to the amount of data that can be transferred between the memory and the processor per second. It's calculated using the following formula:Bandwidth = Bus width x Clock rate x (number of bits transferred per clock cycle/8)For SDRAM, the bus width is 64 bits, and the number of bits transferred per clock cycle is two.
As a result, the bandwidth formula for SDRAM is:Bandwidth = 64 x 100 MHz x 2/8= 800 MBpsTherefore, the bandwidth available to the memory controller, in MBps (megabytes per second), if the SDRAM (Synchronous Dynamic Random Access Memory) bus is running at 100 MHz (megahertz) is 800 MBps.
To learn more about SDRAM :
https://brainly.com/question/31568054
#SPJ11
Which cloud storage architecture enchances the opportunity for data policy enforcement such as data loss prevention?
Answers
Answer:
DRM or DLP.
Explanation:
Cloud computing is an old phenomenon in computing infrastructure dating back to the early days of the Internet that involves moving computing resources out to the Internet.
a. True
b. False
Answers
Answer:
b. False
Explanation:
Cloud computing may be defined as an on-demand availability of any computer system resources. These are especially the data storage as well as the computing power, without the direct active management by a user.
It is the delivery of the computing services which including storage, software databases, analytics, servers, networking and intelligence.
Hence the answer is false.
The configuration and basic components of digital optical encoders for precise control of angular or linear position of robot actuators and arms. Rotating Code disc configuration with optical tracks. Photoemitter-optical detectors pair. Give detailed and pictorial brief on their destination and functions.
Answers
Digital optical encoders consist of a rotating code disc configuration with optical tracks and a photoemitter-optical detectors pair. They are used to precisely control the angular or linear position of robot actuators and arms.
Digital optical encoders play a crucial role in robotics by providing accurate feedback on the position of robot actuators and arms. These encoders typically consist of two main components: a rotating code disc configuration with optical tracks and a photoemitter-optical detectors pair.
The rotating code disc configuration is a disc-shaped component with optical tracks engraved on its surface. These tracks contain alternating transparent and opaque sections. As the code disc rotates, the optical tracks pass through the photoemitter-optical detectors pair, which consists of a light source (photoemitter) and a light sensor (optical detector).
When the light from the photoemitter falls on the rotating code disc, it passes through the transparent sections of the tracks and is detected by the optical detector. Conversely, when the light encounters the opaque sections, it is blocked, resulting in no detection. By analyzing the patterns of light and dark intervals, the encoder can determine the precise position and movement of the code disc.
This position information is then used to control the angular or linear position of robot actuators and arms. The encoder provides real-time feedback, allowing the robot's control system to make adjustments and ensure precise positioning and movement.
In summary, digital optical encoders with rotating code disc configurations and photoemitter-optical detectors pairs are essential components for achieving precise control of the angular or linear position of robot actuators and arms. They provide accurate feedback on position and movement, enabling robots to perform tasks with precision and efficiency.
Learn more about Digital optical encoders:
brainly.com/question/33281468
#SPJ11

Multiple choice:
Select the terms relating to comparisons for equality.
A) ==
B) ^=
C) <>
D) =
E) <
F) !=
G) <=
H) >=
Answers
Answer:
Well there is only 1
"==" is checking for equality and "=" is assigning a value to a variable. Although "==" should be the only answer, since the question is asking you to select multiple, I'd select both of those
YOOO CAN ANYONE SOLVE THIS IN JAVA??
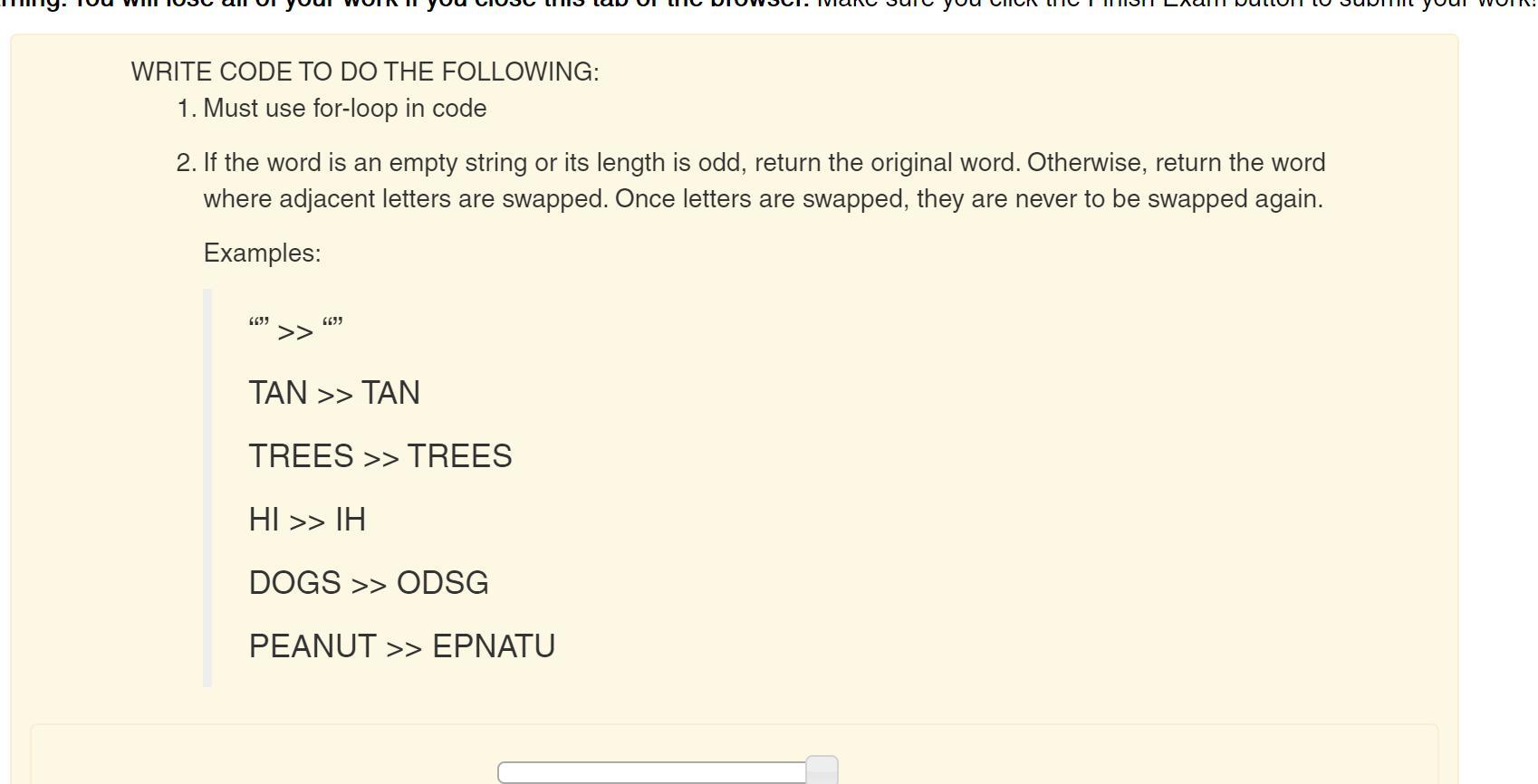
Answers
public class JavaApplication80 {
public static String swapLetters(String word){
char prevC = '_';
String newWord = "";
int count = 0;
if (word.length() % 2 == 1 || word.isBlank()){
return word;
}
else{
for (int i = 0; i<word.length(); i++){
char c = word.charAt(i);
if(count % 2 == 1){
newWord += (c +""+ prevC);
}
prevC = c;
count+=1;
}
}
return newWord;
}
public static void main(String[] args) {
System.out.println(swapLetters("peanut"));
}
}
This works for me. Best of luck.
Answer:
I do not know
Explanation:
Have you been a victim of identity theft or had a data breech occur and been impacted because of it? Share why it is important to secure data. Think about all the new apps that exist today and the data that they contain. What would happen if that data became public knowledge?
Answers
Securing data is of utmost importance due to the potential risks and consequences associated with unauthorized access or exposure of personal information. Data breaches and identity theft can have severe financial, emotional, and reputational impacts on individuals and organizations.
In today's digital landscape, numerous apps collect and store vast amounts of user data, including personal details, financial information, and behavioral patterns. If this data were to become public knowledge, it could lead to various negative outcomes. Firstly, individuals may become victims of identity theft, where their personal information is used to commit fraudulent activities, access financial accounts, or obtain credit in their name. This can result in financial loss, damage to credit scores, and significant stress.
Additionally, the exposure of sensitive data can compromise personal privacy and expose individuals to various forms of exploitation, such as targeted advertising, phishing attempts, or even harassment. Furthermore, confidential business data held by apps could be used by competitors or malicious actors for corporate espionage, leading to substantial financial and reputational damage for companies.
Overall, securing data is vital to protect individuals' privacy, financial well-being, and personal safety. It also safeguards businesses from potential legal liabilities, financial losses, and reputational harm. Robust data security measures, including encryption, access controls, and regular security audits, are crucial to prevent data breaches and ensure the confidentiality, integrity, and availability of sensitive information.
Learn more about unauthorized access here
https://brainly.com/question/30871386
#SPJ11
The web lab consists of which elements. Select all that apply. Group of answer choices Files Inspector Tool Preview Hints Work Space Instructions
Answers
Answer:
Inspector Tool
Preview
Work Space
Instructions
Explanation:
Web Lab is a function that incorporates HTML in web development. It has functions such as Workspace where the developer writes the body of the website. Preview helps the developer take a look at the final product of what he is creating. Instructions panel provides a list of the different types of html packages that the developer can chose from.
All of these options help the developer produce a website that is up to standard.
Shelley works in a dental office as an administrative assistant and uses a desktop computer for scheduling appointments. What type of keyboard is she most likely to use?.
Answers
according to the question A mechanical keyboard is the one that Shelley is most likely to utilize.
What is mechanical keyboard?In addition to a wide range of customization possibilities for look and feel, mechanical keyboards provide a noticeably more pleasant typing experience. They are also more robust and simple to fix.
With mechanical keyboards, signal transmission to your computer frequently just requires a half-press of a key, making typing quicker and simpler.
She is an assistant and makes use of a desktop computer to make reservations, hence a mechanical keyboard will be employed in this instance. She refused to utilize virtual keyboards, computers, or tablets. A mechanical keyboard is the one that Shelley is most likely to utilize.
To learn more about mechanical keyboard refer :
brainly.com/question/28866303
#SPJ4
question a technician that is new to 3d printers needs to call service for a malfunctioning printer. the technician explains that the problem is with what looks to be a print-head. which component does the tech report as a problem? a.extruder b.motion control c.build plate d.bed
Answers
The correct option is (A) i.e. Extruder, the technician explains that the problem is with what looks to be a print - head i.e. Extruder.
The technician reports the print head as the problematic component. In 3D printers, the print head, also known as the extruder, is responsible for melting the filament and depositing it layer by layer to create the 3D printed object. If there is an issue with the extruder, it can result in problems such as clogged nozzles, inconsistent filament flow, or improper filament melting.
These issues can lead to poor print quality, failed prints, or even damage to the printer. Identifying the extruder as the problem component helps the service team understand the specific area that needs troubleshooting or potential replacement to resolve the malfunctioning printer.
To know more about Extruder please refer:
https://brainly.com/question/30631842
#SPJ11
Under which accounting method are most income statement accounts translated at the average exchange rate for the period ?
A) current/concurrent method
B) monetary/nonmonetary methode
C)temporal method
D)All of the options
Answers
Under the accounting method where most income statement accounts are translated at the average exchange rate for the period, the correct option is D) All of the options.
The current/concurrent method considers both monetary and nonmonetary balance sheet items and translates income statement accounts at the average exchange rate for the period. This method takes into account the fluctuations in exchange rates throughout the period and provides a more accurate representation of the financial results in the reporting currency.
By using the average exchange rate, the impact of exchange rate fluctuations on income statement accounts is spread out over the period, reducing the impact of currency volatility on reported earnings.
Learn more about accounting method here: brainly.com/question/30512760
#SPJ11
This question has two parts : 1. List two conditions required for price discrimination to take place. No need to explain, just list two conditions separtely. 2. How do income effect influence work hours when wage increases? Be specific and write your answer in one line or maximum two lines.
Answers
Keep in mind that rapid prototyping is a process that uses the original design to create a model of a part or a product. 3D printing is the common name for rapid prototyping.
Accounting's Business Entity Assumption is a business entity assumption. It is a term used to allude to proclaiming the detachment of each and every monetary record of the business from any of the monetary records of its proprietors or that of different organizations.
At the end of the day, we accept that the business has its own character which is unique in relation to that of the proprietor or different organizations.
Learn more about Accounting Principle on:
brainly.com/question/17095465
#SPJ4
Choose the answer. Janice's IT department found that her computer had a program on it that was collecting her personal information as she browsed the Web. What is this an example of?
spyware
pharming
spam
spoofing
Answers
Answer:
Spyware
Spam is just unwanted soliciation, spoofing is making links appear as something else, pharming is creating a fake website for victims to use.
What will the output be from the following program?
print("hi")
print(3 + 4)
print("bye")
Answers
Answer:
I'm going to assume this is Python syntax. In that case, it will print
hi
7
bye
Explanation:
You are using the print function to print what is in the parenthesis, so thats why itll print what is stated above.
Please Help with C# Binary Search Tree
Hello, I am having trouble with a method for searching A binary tree of of collection of objects.
I have a Student Collection of objects of class Student. I am correctly able to add Students to the binary tree in a sorted fashion but need to search for Student by an ID string.
This is my current code:
public IStudent Search(string id)
{
BTreeNode r = root;
if (r != null)
{
if (r.Student.ID.CompareTo(id) == 0)
{
return r.Student;
}
else
if (id.CompareTo(r.Student.ID) < 0)
Search(r.Student);
else
Search(r.Student);
}
else
Console.WriteLine("Student is not in student collection");
return null;
}
The 'nested' search method should use another method that simply returns true if the student is in the collection or returns false if not.
it should be iniitalised as below:
public bool Search(IStudent student)
{
}
The IStudent interface does not allow for adding a BTreeNode parameter to be added in the constructor.
The main method should similar to:
StudentCollection students = new StudentCollection();
**the adding some students to the collection, then adding them to the binary tree**
students.Search(examplestudent) should return true if in the collection or false if not, and also the root as I also then need to use the Search method in a seperate RemoveStudent function
Answers
In this code, the `BTreeNode` class represents a node in the binary search tree. Each node contains a reference to a `Student` object and references to its left and right child nodes.
The `StudentCollection` class is responsible for managing the binary search tree. The `Add` method inserts a student into the tree by comparing the student's ID with the IDs of existing nodes to determine the correct position.
The `Search` method takes an ID string and recursively searches the binary search tree to find a matching student. If the student is found, it returns `true`; otherwise, it returns `false`.
To use this code, you can create a new instance of `StudentCollection`, add students to it, and then call the `Search` method to check if a specific student exists in the collection.
```csharp
StudentCollection students = new StudentCollection();
students.Add(exampleStudent);
bool found = students.Search(exampleStudent.ID);
```
If the `Search` method returns `true`, it means the student is in the collection, and if it returns `false`, the student is not present.
This implementation ensures that the binary search tree remains sorted, allowing for efficient search and retrieval of students by their ID.
To know more about class, visit
https://brainly.com/question/30001841
#SPJ11
Describe an association or rhyming phrase you have used to remember information. Was this a useful technique for you? Why or why not?
Answers
Answer:
I used the names George Clooney and Tim Allen to remember the pairs of nitrogenous bases in DNA.
Explanation:
DNA is composed of nucleotides, however the nucleotides are formed by nitrogenous bases called Adenine, Guanine, Cytosine and Thymine. Each nucleotide has a nitrogenous base, but these bases form pairs, allowing the nucleotides to come together. The pairs are formed solely by Timine and Adenine or Guanine and Cytosine.
As I needed to remember the formation of the pairs to do my biology test, I associated the first letter of each base, with the initials of two famous names.
As Guanina is paired with Cytosine (G-C), I associated this pair with the initial letters of the name George Clooney. As Timina is paired with Adenina (T-A), I associated this pair with the initials of the name Tim Allen.
give their answer according to the given in
Give short answer of the following questions.
1. What is the primary function of computer?
2. What does computer affect due to radiation?
3. What are electronic devices? Name any two electronic computers.
4. Write main two characteristics of Fourth Generation Computer.
5. Where are super computers mainly used?
Give long answer of the following questions:
1. Write any four disadvantages of using computer.
2. How are software classified into different types?
3. Define computer software. What are the types of application
Differentiate between the following:
1. Data and information
2. Second and third generation computer
3. General purpose and special purpose computers
internreter
Answers
Answer:SHORT ANSWER
3.) Electronic devices are components for controlling the flow of electrical currents for the purpose of information processing and system control. Any two electronic computers are - Digital computer and Electronic computers.
Describa la clasificación de los recursos educativos digitales abiertos. vea este video, para hacer eso
Answers
hola una pregunta dónde está el vídeo ?
hola una pregunta dónde está el vídeo ?
A ____ FTP website allows anyone to log on using "anonymous" as their username.
A) private
B) secret
C) public
D) protected
Answers
A public FTP website allows anyone to log on using "anonymous" as their username.
So, the correct answer is C.
This means that the website is open to the public and does not require any special permissions or credentials to access.
Public FTP sites are commonly used for sharing large files such as software programs, media files, and other types of data. It is important to note that while public FTP sites are accessible to anyone, they may not be secure or safe to use.
It is recommended to exercise caution when downloading files from unknown sources and to use antivirus software to protect your computer from potential threats.
Hence the answer of the question is C.
Learn more about FTP at https://brainly.com/question/31721198
#SPJ11
Darla is going to start writing the HTML code for a web page. What would she start with?
Answers
Answer:
opening
Explanation:
Your answer would be opening
when using a multiple-baseline design, how would one decide when to implement the independent variable?
Answers
The independent variable is introduced at various times across several baselines in a multiple-baseline design to evaluate its impact on the dependent variable.
The particular research topic and study design will determine when to use the independent variable. The independent variable should typically be applied to the baselines in a staggered fashion, with each baseline acting as a control for the others. This makes it possible to evaluate the impacts of the independent variable methodically while accounting for any possible confounding factors that can have an impact on the dependent variable. Several criteria, such as time, behavior, or other occurrences that can be pertinent to the study topic, might be used to create the independent variable.
learn more about design here:
https://brainly.com/question/14035075
#SPJ4
\(3x - 5 = 3x - 7\)
Answers
Answer:
x = -1/2
Explanation:
Hey there!
To solve for x we need to simplify the following,
3x - 5 = 7x - 3
-3x to both sides
-5 = 4x - 3
+3 to both sides
-2 = 4x
Divide both sides by 4
-1/2 = x
Hope this helps :)
Is MOOC's potentially harmful to copyright? Why or why not ?
Answers
Answer:
Fair-use exceptions to traditional copyright protection face challenges as well, given a MOOC's potential for global reach. Nonetheless, fair use and MOOCs are not mutually exclusive ideas. MOOCs remain an experiment...
Where can the slide layout be changed?
from the Edit menu
from the Task pane
from the Slide pane
from the Tools menu
Answers
Anwser
3. From the Slide Pane
Answer:
The Task Pane
Explanation:
This is where the slide layout can be changed.