In the AutoCAD Civil 3D workflow, what are the two main methods of project collaboration (or the sharing of intelligent AutoCAD Civil 3D design data)
Answers
The two main methods of project collaboration, or sharing of intelligent AutoCAD Civil 3D design data, are "Data Shortcuts" and "Reference Templates."
How does AutoCAD Civil 3D facilitate project collaboration?In the AutoCAD Civil 3D workflow, project collaboration and the sharing of intelligent design data are facilitated through two main methods: Data Shortcuts and Reference Templates.
Data Shortcuts allow multiple users to work on a project simultaneously while maintaining a centralized source of design data. With Data Shortcuts, design elements such as surfaces, alignments, profiles, and corridors are created and managed in a central project location.
Each user can then create references to these data shortcuts in their local drawings, enabling them to work on their specific tasks while maintaining the integrity of the shared data.
Reference Templates, on the other hand, provide a way to establish standardization and consistency across multiple projects. A Reference Template is a preconfigured drawing that contains predefined settings, styles, and data references specific to a particular project type or company standards.
By referencing a template, users can leverage the predefined elements, reducing errors and ensuring compliance with project requirements. These methods of collaboration in AutoCAD Civil 3D enhance efficiency, promote collaboration among team members, and maintain data consistency throughout the project lifecycle.
Learn more about AutoCAD
brainly.com/question/32391284
#SPJ11
Related Questions
can you imagine what life might have been like before the internet laptops and smartphones were part of everyday life what are some ways thst life was better, worse, or just different
Answers
Answer:
no
Explanation:
it does not matches me
The article asserts that all resources need to be realigned and focused on primary services and products that will keep the business afloat through the economic crisis. Explain FOUR (4) executive challenges associated with information technology economics.
Answers
Executive challenges associated with IT economics include cost management, ROI evaluation, risk management, and alignment with business strategy.
Executive challenges associated with information technology economics include:
Cost Management: Executives need to effectively manage and control the costs associated with information technology (IT) investments. This involves optimizing resource allocation, reducing unnecessary expenses, and aligning IT spending with business objectives. It requires making strategic decisions on IT budgeting, vendor selection, and cost-saving measures to ensure that IT investments deliver maximum value to the organization.
Return on Investment (ROI): Executives face the challenge of evaluating and measuring the ROI of IT investments. They need to determine the financial benefits and outcomes derived from IT initiatives and justify the allocation of resources. This requires defining clear metrics and performance indicators to assess the effectiveness and efficiency of IT projects and ensure that they contribute to the organization's bottom line.
Risk Management: Executives must address the risks associated with IT investments and mitigate potential negative impacts. This includes identifying and managing risks such as technological obsolescence, cybersecurity threats, data breaches, and regulatory compliance. They need to implement risk mitigation strategies, establish robust IT governance frameworks, and ensure business continuity in the face of IT-related disruptions.
Alignment with Business Strategy: Executives need to ensure that IT investments align with the organization's overall business strategy. This involves understanding the business goals, identifying how IT can support and enhance those goals, and aligning IT initiatives with the strategic priorities of the organization. It requires effective communication and collaboration between business and IT leaders to ensure that technology investments are in line with the organization's long-term vision and contribute to its competitive advantage.
Learn more about information technology economics here: brainly.com/question/28811002
#SPJ11
Check the devices that are external peripheral devices:

Answers
Answer:
Mouse, and keyboard
Explanation:
Common Sense
You have been assigned the task to store a number in a variable. The number is 51,147,483,647,321. You have different data types like Integer, Float, Char, and Double. Which data type will you use from the given data types to store the given number and why? Justify your answer with logical reasoning.
Answers
To store the number 51,147,483,647,321, the data type that can be used is long int. The reason why long int is the best choice is because it can store large values of data like 51,147,483,647,321 and it does not need any floating-point calculations.
A data type is a fundamental concept in programming. A data type specifies a particular type of data and defines a set of operations that can be performed on the data. In programming, data types are used to define variables. The data type of a variable determines the type of data that can be stored in the variable.
The best data type to use to store the number 51,147,483,647,321 is long int because it is a 64-bit integer that can store large values like 51,147,483,647,321. It is a perfect fit for the given number and it does not need any floating-point calculations. Thus, the long int data type is the best choice to store the number 51,147,483,647,321.
To know more about store visit:
https://brainly.com/question/29122918
#SPJ11
Which of the following labor surplus tactics is likely to be the fastest in terms of helping companies meet their labor surplus needs? Select one: A. Hiring Freezes B. Employee Movement C. Layoffs D. Attrition
Answers
Out of the given options, layoffs are likely to be the fastest labor surplus tactic for companies.
Layoffs involve terminating employment contracts with employees, which can be implemented relatively quickly and effectively. It allows companies to reduce their labor force quickly to align with their current needs and economy situation.
Hiring freezes and employee movement may take more time to implement. Hiring freezes involve not filling vacant positions, which can take some time to become effective. Employee movement involves moving employees from one department to another to fill gaps, which may require training or re-skilling before they can effectively perform the new role. Therefore, it may not be the quickest solution for labor surplus issues.
Attrition is a slow and passive labor surplus tactic. It involves waiting for employees to leave the company naturally, such as through retirement, resignation or termination due to poor performance. This method may take years to achieve the desired level of reduction in the workforce.
In conclusion, layoffs are likely to be the fastest tactic to implement when a company needs to meet their labor surplus needs. However, companies should always consider the ethical implications of such actions and explore alternative strategies that prioritize retaining their workforce.
Learn more about economy :
https://brainly.com/question/30131108
#SPJ11
why do scientist use mathamatical equations
Answers
Main function of Ubuntu
Answers
Answer:
Ubuntu includes thousands of pieces of software, starting with the Linux kernel version 5.4 and GNOME 3.28, and covering every standard desktop application from word processing and spreadsheet applications to internet access applications, web server software, email software, programming languages and tools
Explanation:
Answer:
Explanation:
It is a free OS
Which should you consider when selecting a highlighting color?
size
equality
alignment
contrast
Answers
Answer:
contrast
Explanation:
Answer:
I'm pretty sure it's contrast
Explanation:
It would be contrast because when you're looking for a highlighting color, you'd want to use colors that stand out from the rest. This helps you find what you want to see again very easily.
I'm sorry if this is wrong, but if it's right pls vote me brainliest
Which of the following types of mobile Internet access methods offers the least amount of security?
O Mobile broadband
Wi-Fi hotspot
Tethering
a
O Gateway
Answers
Answer:
Hot Spot since it provides viruses and security disable
Explanation:
if the computer applies huffman coding to the wizard spell, which letter is the most likely to be represented with a shorter bit code?
Answers
The letter "e" is the most likely to be represented with a shorter bit code when the computer applies Huffman coding to a wizard spell.
What is the bit code?Bit code is a type of computer code that consists of bits, or binary digits (0s and 1s). Bits are used to store and transmit data, and are the most basic form of information a computer can understand. Bit code is used in computer programming, and is the language that computers use to communicate with each other. Bit code is also used to create applications, software, and hardware that can be used by humans. Bit code is the basis of the digital world and is one of the most important coding languages used today.
To learn more about bit code
https://brainly.com/question/29579837
#SPJ1
you are reviewing new ram to purchase for a gaming computer and find three different ram modules that are the same except for their cl rating. the memory with which rating will work best? group of answer choices cl15 cl18 cl20 they will all perform at the same speed.
Answers
shows many RAM modules that are identical besides CAS Latency as having a 15 ns CL.
What kind of memory feature will be necessary if data accuracy is crucial for a new computer?Computer data storage that is capable of spotting and fixing the most prevalent forms of internal data damage is known as error-correcting code memory (ECC memory).
Which RAM includes an additional layer of security?A memory chip that serves as both error detection and correction for the other eight RAM chips distinguishes ECC memory, also known as ECC RAM. Though slightly more expensive than non-ECC RAM, the additional security it offers is crucial as applications become more reliant on huge volumes of data.
To know more about RAM modules visit :-
https://brainly.com/question/28776521
#SPJ4
A database is an organized collection of systems files.
Answers
(More info is needed)
It might be hard for some people to see the options so I’ma just;
A. What will happen if a certain condition is not met.
B. What color the ball is.
C. Whether the ball’s value is y-value is greater than 110.
D. The overall size of the ball used in the game.

Answers
I put the document in photos!
The question is - “According to the first paragraph of this document, did Hawaii agree to the annexation by the United States of America? Cite evidence for your claim?
URGENT What information is available in the Document Inspector Dialog Box? Check all that apply.
comments
document properties
privacy settings
presentation notes
embedded documents
digital IDs
Answers
These are all aspects of the document that can be inspected by the document inspector. The document inspector is a tool that allows us to examine documents in order to remove or alter information.
This is a useful tool to employ before finishing and distributing a document. Other aspects that the inspector can check in Powerpoint are embedded documents, data models, content apps and off-slide content.
Therefore, comments and annotations
document properties and personal informationinvisible on-slide contentLearn more about document on:
https://brainly.com/question/17673965
#SPJ1
Answer:
A, B, D, E
Explanation:
right on edge22
why is a computer called diligent machine ?
Answers
Computer is called diligent machine because it can perform the task repeatedly without loosing its speed and accuracy for a long time.
when a hacker steals personal information with the intent of impersonating another individual to commit fraud, it is known as .
Answers
Answer: Identity theft
Explanation: occurs when someone uses another person's personal identifying information, like their name, identifying number, or credit card number, without their permission, to commit fraud or other crimes. The term identity theft was coined in 1964.
When a hacker steals personal information with the intent of impersonating another individual to commit fraud it is called identity theft
What is fraud?False statements about the facts are a component of fraud, whether they are made to another party with the intent to deceive or purposefully withheld for the goal of obtaining something that might not have been given otherwise.
A fraud takes place when an individual commits fraud or another crime using another person's personal information, such as their name, identification number, or credit card number without that person's consent.
Identity theft is a term in which the dishonest act of applying for credit, loans, etc. using someone else's name and personal information.
Identity theft refers to the act of a hacker taking personal information with the intention of using it to defraud someone else.
Hence, identity theft is correct answer.
To know more about Fraud on:
https://brainly.com/question/11523638
#SPJ12
What will print to the console after running this code segment?
A. 15.
B. 16.
C. 18.
D. 21.
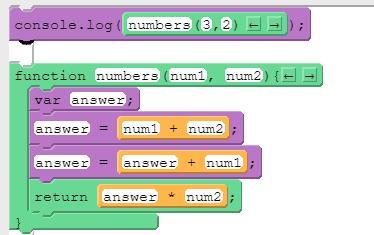
Answers
Answer:
16
Explanation:
answer =3+2
answer =5+3
return 8 × 2
16 will print to the console after running this code segment. Therefore, option B is correct.
What do you mean by code segment ?A code segment, also known as a text segment or simply text, is a section of an object file or the program's virtual address space that contains executable instructions.
A character array segment that represents a text fragment. Even though the array is directly accessible, it should be treated as immutable. This allows for quick access to text fragments without the overhead of copying around characters.
In memory, the code segment functions normally as read-only memory and has a fixed size; thus, without the need for loading, it can generally be found in read-only memory (ROM) on embedded systems.
answer = 3+2, answer = 5+3
return 8 × 2
= 16
Thus, option B is correct.
To learn more about the code segment, follow the link;
https://brainly.com/question/20063766
#SPJ2
What is meant by saving a sheet document
Answers
Answer:
While you'll use Save or press Ctrl+S to save an existing workbook in its current location, you need to use Save As to save your workbook for the first time, in a different location, or to create a copy of your workbook in the same or another location.
Which one of the following is a type of network security?
a) Login Security
b) Rights Security
c) Both (a) and (b)
d) Neither (a), nor (b)
Answers
Answer:
I think it's (login security)
What are characteristics of fluent readers? Check all that apply. reading known words automatically pronouncing words correctly reading words as quickly as possible understanding the meanings of the words being read O looking up all unknown words in the text being read
it's A,B,D
Answers
Answer:
D,A,B hope this is it!!!!!
Answer:
The person above me is correct
Explanation: credit to him
what command displays the ip address, subnet mask, and default gateway of the system you are currently on? ipconfig ping tracert nslookup
Answers
The correct option is "ipconfig". This command displays the IP address, subnet mask, and default gateway of the system you are currently on.
When you run ipconfig in the command prompt, it will provide you with the necessary network information about your system.
The other commands you mentioned serve different purposes:
1. Ping: This command is used to check the connectivity between your computer and another device on the network, such as a router, by sending small data packets. It helps in identifying if there are any issues with the connection.
2. Tracert: Short for "trace route," this command is used to track the path that data packets take from your system to a destination address. It can be helpful in diagnosing network issues and identifying potential bottlenecks.
3. Nslookup: This command is used to obtain domain name or IP address mapping by querying the Domain Name System (DNS) server. It can help you find out the IP address associated with a specific domain name, or vice versa.
Remember to use ipconfig for retrieving IP address, subnet mask, and default gateway information of your system.
Know more about the IP address
https://brainly.com/question/14219853
#SPJ11
What is wrong with the following code?
numl = int (input("Enter a number: "))
numz = int (input("Enter a number: "D)
num3 = int (input("Enter a number: "))
print ("The average is: + (numl + num2 + num3/3)
The last line should be print ("The average is: (numl + num2 + num/3)
The variables should be lnum, 2num, Bnum
It needs a into command
It needs a stro command
Answers
Code:
numl = int (input("Enter a number: "))
num2 = int (input("Enter a number: "))
num3 = int (input("Enter a number: "))
print ("The average is:" + ((numl + num2 + num3)/3))
Answer:
It needs a str command
Explanation:
Given
The above code
Required
Determine and correct the error
At the last line of the code, there is an attempt to print the average of the three numbers.
However, this will return an error because:
In order to print the literal "The average is:" and the numeric value of (numl + num2 + num3)/3, a str command is needed.
This converts (numl + num2 + num3)/3 to a literal and then print without error.
So, the correct instruction is:
print ("The average is:" + str((numl + num2 + num3)/3))
will is the network manager for a large company. he has been tasked with creating a deployment plan to automate installations for 100 computers that need to have windows server 2016 installed. will wants to use wds for the installations. to fully automate the installations, he needs to create an answer file. will does not want to create the answer files with a text editor. what other program can he use to create unattended answer files via a gui interface?
Answers
Will can use Windows System Image Manager (WSIM) to create unattended answer files via a GUI interface instead of a text editor for fully automating installations using WDS.
Windows Deployment Services (WDS) is a tool for deploying Windows operating systems. To fully automate installations, an unattended answer file is required. Answer files can be created manually using a text editor, but this can be time-consuming and error-prone. To create answer files using a graphical user interface, Will can use Windows System Image Manager (WSIM), which is part of the Windows Assessment and Deployment Kit (ADK). WSIM provides a user-friendly interface for creating and editing answer files. This simplifies the process and helps ensure accuracy, resulting in a smoother and more efficient deployment.
Learn more about Windows Deployment Services here.
https://brainly.com/question/29455341
#SPJ11
How do you use the value of a cell in a formula in Excel?
Answers
In a formula, reference the cells. To enter the formula, click the cell where you want to do so. Type = in the formula bar (equal sign). Choose the cell that has the desired value or type the cell's reference to do one of the following. Enter the key in Excel.
In Excel, you often enter =A1 to refer to cell A1. There is also another approach, though: applying the INDIRECT formula. The formula outputs the text's reference. Therefore, you may use =INDIRECT("A1") in instead of explicitly connecting to =A1. how to paste and copy a formula .Choose the cell containing the formula you wish to duplicate. Press "+C." Wherever you wish to paste the formula, click the cell. Press + V to swiftly paste the formula with its formatting. A menu appears when you click the arrow. You can use the formula =TEXT to refer to the top cell that contains the values, where the amount of 0s in the formula stands for the total number of characters you desire, and then copy and paste to another cell.
Learn more about Excel from
brainly.com/question/24749457
#SPJ4
how did you ensure that your code was efficient? cite specific lines of code from your tests to illustrate.
Answers
one way to ensure that code is efficient is to use the Python profiling tool. This tool allows developers to identify which parts of their code take the most time to execute and optimize them. For example, the following code snippet uses the cProfile module to profile a function:
```
import cProfile
def my_function():
for i in range(1000000):
pass
cProfile.run('my_function()')
```
The output of this code will show how long the function took to run and which lines took the most time. Developers can then use this information to optimize the code for better efficiency. Additionally, using built-in functions and libraries such as NumPy and Pandas can also improve code efficiency.
Hi! To ensure that your code is efficient in Python, you can follow several best practices and optimization techniques. I can't provide specific lines from your tests since I don't have access to your code, but I can give you general guidelines.
1. Use built-in functions and libraries: Python has many built-in functions and libraries that are optimized for performance. Utilize these whenever possible.
2. Avoid using global variables: Global variables can make your code harder to understand and maintain. Try to use local variables and pass them as arguments to functions.
3. Use list comprehensions: List comprehensions are more efficient than using loops to create lists.
4. Optimize loops: Use the 'enumerate' function instead of 'range' and 'len' when iterating over a list. Avoid using nested loops if possible.
5. Use appropriate data structures: Choosing the right data structure can greatly impact the performance of your code. For example, using sets or dictionaries for membership checks is faster than using lists.
6. Profile your code: Use Python's built-in 'cProfile' module to profile your code and identify performance bottlenecks. This will help you understand which parts of your code need optimization.
Remember, efficient code in Python relies on using best practices, optimizing loops, and selecting the appropriate data structures. Keep these guidelines in mind when reviewing and optimizing your code.
Learn more about phyton language brainly.com/question/16757242
#SPJ11
HELP!!!!!!!!!! I'M SOO STUCK ON EXCEL OFFICE FUNDAMENTALS!!!!!! I'LL GIVE BRAINLIEST TO THE FIRST RIGHT ANSWER!!!! PLEASE, I'M BEGGING YOU!!!!!
Provide two examples of a situation or task in which a business would want a workbook that contains multiple spreadsheets.
Answers
Answer:
Time Sheet And Accounting
Answer:
Time Sheet and Accounting
Explanation:
8 9. McWhorter argues that being able to understand in textspeak has many of the same benefits as being able to speak two languages. Can this same argument be applied to emojis? Why or why not?
NEED HELP ASAP WILL GIVE BRAINIST TO BEST AWNSER
Answers
Answer:
yes because i could use ️ to say im eating a chicken leg and or talking with my mouth full and got slapped so yes i believe so
Explanation:
Answer: Yes because if you speak in "emoji" you technically can talk in any language you want because whoever you are sending it to could knows what you're implying by them
Explanation:
Which situations make use of interactive multimedia and which do not? Amelia is exploring a shopping website looking for clothes or accessories she could give to her sister. Roy is going through a tutorial on his laptop that explains a do-it-yourself project. Jaden is listening to a presentation on early music in his class. Fred is answering an online quiz that requires him to select correct answers. Linear Multimedia Kristen is watching an educational film on her tablet. Non-linear Multimedia
Answers
The situation that make use of interactive multimedia is Roy is going through a tutorial on his laptop that explains a do-it-yourself project, and that do not is Amelia is exploring a shopping website looking for clothes or accessories she could give to her sister.
What is an interactive multimedia?Interactive multimedia is a type of interaction in which the user can operate, control, and change the text, image, and picture, and function in a phone or computer.
Thus, the correct options are A and B.
Learn more about interactive multimedia
https://brainly.com/question/26090715
#SPJ1
What is an example of new technology having a positive impact on sustainability?
Answers
Answer:
The main technology that brings positive news on sustainability in any company would be the use of renewable technology more because we can use energy. For example, by using equipment such as solar panels, windmills or water turbines, we can generate electricity and use it many times.
Define spyware and virus
Answers
Answer:
Brainliest pls
Explanation:
Spyware is a kind of malware that gathers your own data and accumulates information about you without your assent. Viruses are a kind of pernicious programming intended to spread from your gadget to different gadgets.