In recursion, if a base case is missed or does not exist then there is: In recursion, if a base case is missed or does not exist then there is: indirect recursion time inefficiency recursive calling infinite recursion tail recursion
Answers
In recursion, if a base case is missed or does not exist, it can lead to infinite recursion.
Infinite recursion occurs when a recursive function does not have a terminating condition, causing it to call itself indefinitely. This can result in the program running out of stack space and eventually crashing or causing a stack overflow error.
Without a base case, the recursive function does not have a stopping condition, and the recursion continues indefinitely, leading to a recursive loop. Each recursive call consumes additional memory on the stack, eventually causing the stack to overflow.
To avoid infinite recursion, it is crucial to define and include a proper base case in recursive functions. The base case serves as the termination condition that stops the recursion and allows the function to start returning values back up the call stack. The absence of a base case or a missed base case can lead to various issues, including program crashes, excessive memory usage, and incorrect results.
To know more about Recursion related question visit:
https://brainly.com/question/32344376
#SPJ11
Related Questions
Select the correct answer.
Ben wants to keep similar items close to each other in the image he is working on. Which is the most effective technique for applying the gestalt
concept of proximity?
The BLANK technique is the most effective technique for applying the gestalt concept of proximity.
Answers
Gestalt Principles are principles/laws of human perception that describe how humans group similar elements, recognize patterns and simplify complex images when we perceive objects.
What are the Gestalt Principles?The tendency to view items as belonging to the same grouping when they are close to one another is known as the gestalt principle of
proximity
. It claims that regardless of how different the forms and sizes are from one another, if shapes are close to one another, you will perceive them as groups. One of Gestalt's principles, the concept of closeness focuses on how each stimulus would be seen in its most basic form. The
Law of Simplicity
or the Law of Pragnanz are other names for it. It is founded on the idea that the sum of a thing is worth more than the sum of its components.
To learn more about Gestalt Principles refers to;
https://brainly.com/question/4734596
#SPJ1
what is the primary function of the ike protocol used with ipsec?
Answers
The primary function of the ike protocol used with ipsec is to Establish a secure channel, Authentication, Key exchange, Establish IPSec SAs, and Manage and refresh keys.
IKE achieves this by facilitating the exchange of keys through a series of steps, including:
1. Establishing a secure channel: IKE initiates a secure communication channel between two parties by creating an IKE Security Association (SA), which is a set of shared security parameters used to facilitate secure communication.
2. Authentication: IKE authenticates the parties involved in the communication, ensuring that they are who they claim to be. This process typically involves the use of digital certificates, pre-shared keys, or other authentication methods.
3. Key exchange: Once authenticated, the parties exchange cryptographic keys through the Diffie-Hellman key exchange algorithm, ensuring that the keys remain private and secure throughout the process.
4. Establishing IPSec SAs: IKE creates the necessary IPSec SAs for secure communication, specifying the encryption and authentication algorithms to be used for data transmission.
5. Managing and refreshing keys: IKE dynamically manages and refreshes the cryptographic keys to maintaining a high level of security throughout the communication.
In summary, IKE is an essential component of the IPSec framework, ensuring secure communication over IP networks by managing the authentication, key exchange, and establishment of security associations.
know more about primary function here:
https://brainly.com/question/22340031
#SPJ11
Natalie is writing an

Answers
Answer:
A
The answer is A according to me because there are no match making 0 match.
What is the operating system written to, and what does nonvolatile mean?
Answers
Answer:
Non-volatile memory (NVM) is a type of memory that retains stored data after the power is turned off. Unlike volatile memory, it does not require an electric charge to maintain the storage state. Only reading and writing data to non-volatile memory requires power.
what is a core hardware and distribution hardware
Answers
Answer:
The term “core hardware “ is merely a reference to the minimum physical hardware requirements for a given application to run to benchmarks established by the programmers.. DISTRIBUTION HARDWARE.. Electrical Distribution Hardware for the Energy Industry
Does each box at the fruit stand contain a different fruit?
In [164]:
# Set all_different to "Yes" if each box contains a different fruit or to "No" if multiple boxes contain the same
fruit all_different = "No" all_different
Out[164]: 'No' In [165]: _
= ok.grade('q6_3')
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ Running tests
Answers
Answer:
yes
Explanation:
The value of the variable all_different is: all_different = No
Complete questionDoes each box at the fruit stand contain a different fruit? Set all_different to True if each box contains a different fruit or to False if multiple boxes contain the same fruit.
Hint: You don't have to write code to calculate the True/False value for all_different. Just look at the inventory table and assign all_different to either True or False according to what you can see from the table in answering the question.
box ID fruit name count
53686 kiwi 45
57181 strawberry 123
25274 apple 20
48800 orange 35
26187 strawberry 255
57930 grape 517
52357 strawberry 102
43566 peach 40
all_different = ...
How to determine the true statement?From the hint given, we can see that writing a code is not necessary.
All we need to do is to scan through the table.
From the given table, we can see that there are several fruits on the table.
These include peach, kiwi, grape, strawberry, etc.
Since the fruits are different, then the value of the variable all_different is:
all_different = No
Read more about boolean variables at:
https://brainly.com/question/18089222
#SPJ2
Write a program in C++ to calculate product of digits of any number.
I NEED HELP FINISHING THIS!

Answers
The example of a program in C++ that calculates the product of the digits of any number is given below
What is the C++ programThe variable for the product is set to a value of 1 at the start. Within the while loop, the digit variable is assigned the value of the number's final digit, which is achieved by utilizing the modulus operator %. To update the product, the digit is multiplied with it.
Upon calling the calculateProductOfDigits function with the inputted number, the resultant product is saved into the product variable. Ultimately, the output appears on the console.
Learn more about C++ program from
https://brainly.com/question/13441075
#SPJ1

what refers to the ability of a company to identify, search, gather, seize, or export digital information in responding to a litigation, audit, investigation, or information inquiry?
Answers
The ability of a company to identify, search for, gather, seize, or export digital information in responding to a litigation, audit, investigation, or information inquiry is referred to as "electronic discovery" or "e-discovery."
The ability of a company to identify, search, gather, seize, or export digital information in response to a litigation, audit, investigation, or information inquiry is known as electronic discovery or eDiscovery. With the increasing amount of digital data generated by companies, the process of eDiscovery has become essential in legal and regulatory matters. The eDiscovery process involves the preservation, collection, processing, review, and production of electronic documents and data in a legally defensible manner. This includes not only traditional documents such as emails and spreadsheets but also social media posts, instant messages, and other forms of electronic communication. The process of eDiscovery requires a combination of technical expertise, legal knowledge, and project management skills to ensure that all relevant information is collected and produced in a timely and cost-effective manner.
Learn more about Spreadsheets here:
https://brainly.com/question/8284022
#SPJ11
How do people decide their ethical behavior
Answers
Explanation:
Ethical behavior is based on written and unwritten codes of principles and values held in society. Ethics reflect beliefs about what is right, what is wrong, what is just, what is unjust, what is good, and what is bad in terms of human behavior.
Answer:
most people go by the crowd to the way they act. theres are also people who have to make very hard decisions and not everyone makes the right choice.
Explanation:
creating a small author-article-publication database in this assignment, we’ll follow the database design process with a step-by-step example. your client, wellness week is a small, specialized publisher that publishes articles on health and wellness issues. the owner would like to have a small database that would track authors and articles.
Answers
After you've finished writing your paper, follow these steps to publish it in a journal: After taking into account the article's nature, references, the journal's goals and scope, availability, and performance metrics, choose the best publication. To reach your target audience, this is crucial.
What is the process of article publication?The acquisition and editing phases of publishing are the first steps. Although acquisition can happen in a variety of ways, authors typically send a proposal or a draft of their manuscript to many publishers.
Knowing the Publication Process
Internal examinations of fresh submissions.Peer evaluation.Decision on revisionReceived a revised submission.Following Peer Review.preliminary approvalOfficial approval and publication.Making information, books, music, software, and other items available to the public, whether for a fee or for free, is known as publishing. The phrase has historically been used to describe the production and distribution of printed materials like books, newspapers, and magazines. The act of releasing unique content on the Internet is known as web publishing.
To learn more about article publication, refer to:
https://brainly.com/question/14189081
#SPJ4
A program is
O the language computers use to communicate.
O writing a program in a specific language.
a set of instructions given to a computer.
a specific coding language.
A program is ?
Answers
Answer:
The correct answer is option 3: a set of instructions given to a computer.
Explanation:
A computer works on the instructions that are given by the user. The user has to provide both, the data and the instructions. There are several methods to give input to a computer. One of them is a program which is written in a programming language.
Hence,
A program is a set of instruction given to a computer
The correct answer is option 3: a set of instructions given to a computer.
Using a trick or fraud to steal personal information is called (5 points)
A. hacking
B. identity theft
C. netiquette
D. scamming
Answers
Answer:
its D
Explanation:
ive done this before i remeber i got d
Select the correct answer.
Susan is writing a program that organizes weather data into a table using conditional phrases. If she wants to operate on the results of these conditional phrases, what must she do?
A use Boolean values for the results
B. use the results in more conditional phrases
C. use logical operators on the results
D use either >,<, or =
Answers
Answer:
B.use the results in more conditional phrases
You must be connected to the Internet in order to work on a document on a shared document workspace.
a. True
b. False
Answers
hackers often set up their own wireless access points in popular areas with the hope that users connect to them. these are known as:
Answers
A computer worm is a sort of virus that replicates itself and spreads to other computers while still functioning on infected ones. A computer worm multiplies in order to infect other systems.
Transaction processing systems (TPS) handle business transactions for the corporation, supporting overall enterprise operations. The most prevalent topology is by far stars. This system has a star-like form because each node is autonomously connected to a central hub by a physical wire. All information must pass through the central node in order to go to its final location. After the link was established, the malicious access point might have viewed every Internet request that his laptop issued. A worm is a self-replicating, self-propagating, self-contained software that spreads to other computers over networking protocols. Worms can propagate through software flaws, show up in phishing email attachments, or be accessed through malicious URLs.
To learn more about computer worm click the link below:
brainly.com/question/16893265
#SPJ4
Which of these is a compound morphology?
A.
bookkeeper = book + keeper
B.
happiness = happy + ness
C.
books = book + s
D.
banker = bank + er
Answers
Answer:
D.
Explanation:
yarn po answer ko po eh
because bank +er =banker
Write a program in QBasic to accept any three numbers and then find out the smallest number between
them.
Answers
Answer:
CLS
INPUT "Enter the first number"; a
INPUT "Enter the second number"; b
INPUT "Enter the third number"; c
IF a < b AND a < c THEN
PRINT "The smallest number is "; a
ELSEIF b < a AND b < c THEN
PRINT "The smallest number is "; b
ELSE
PRINT "The smallest number is "; c
END IF
END
hope this clears your queries
mark my answer as the brainliest if you found it useful
thank you, have a fantabulous day !!
Which of the following statements is true about scalability? Choose 3 options.
Horizontal scaling has fewer limits than vertical scaling.
Scalability refers to the ability of hardware components to increase their capacity.
Scalability should be considered very early in the project.
The cloud offers services to automatically scale your system and balance the workload between components.
An example of vertical scaling is adding a new server to the network.
Answers
Answer:
Horizontal scaling has fewer limits than vertical scaling.
The cloud offers services to automatically scale your system and balance the workload between components.
Scalability should be considered very early in the project.
Explanation:
Hope this helps :) If not, please let me know what answers are wrong
The statements that is true about scalability are:
The clouds provide resources to scale the system and balance the workload between components Scalability should be considered at the beginning of the project.Horizontal scaling has fewer limits than vertical scaling.Horizontal scaling is a type of scaling by adding more machines to your po of resources.
It is also called adding more power.
The difference between scaling up and scaling out is that horizontal scaling simply adds more machine resources to your existing machine infrastructure.
Vertical scaling is simply known to adds power to your existing machine infrastructure by increasing power from CPU or RAM to existing machines.
Conclusively, Scalability part of a system that handle a growing amount of work by adding resources to the system.
Learn more from
https://brainly.com/question/17661222
Miguel is using the New Virtual Machine Wizard to create a new virtual machine for the first time. Which of the following statements is true if Miguel creates a virtual machine with default settings?
a) The virtual machine will be a Generation 1 virtual machine.
b) The virtual machine will be named VM1.
c) The virtual machine will have 4 GB of memory, which is expandable up to 36 GB.
d) The virtual machine will have a 127 GB dynamically expanding hard disk.
Answers
Among all the given statements, the one that is true if Miguel creates a virtual machine with default settings is: “The virtual machine will be a Generation 1 virtual machine.” Hence, Option A is correct.
What are the default settings?When a user-configurable setting is assigned to a piece of software, a computer programme, or a hardware, it is known as the default value in computer science. Presets or factory presets are other names for these settings, particularly when applied to electronic devices.
A default in computer technology is a predesigned value or setting that a computer programme will use if the programme user does not specify a value or configuration.
Therefore, Option A is correct.
Learn more about default settings from here:
https://brainly.com/question/28493813
#SPJ1
Advances in technology have enabled HR to ______ activities and, where possible _____ the data entry at the source.
a. automate; download b. improve; import c. improve; upload d. expedite; secure e. expedite; import the day-to-day
Answers
Advances in technology have enabled HR (Human Resources) to automate activities and, where possible, improve the data entry at the source.
Technology has revolutionized HR practices by automating various activities and improving data management processes. HR departments can leverage software applications and systems to automate routine tasks, such as employee onboarding, leave management, and performance evaluations. This automation reduces the time and effort required for these activities, allowing HR professionals to focus on more strategic initiatives.
Furthermore, technology enables HR to improve data entry at the source. By providing self-service portals and online platforms, employees can directly enter and update their personal information, such as contact details, benefits enrollment, and time and attendance records. This eliminates the need for manual data entry by HR staff, reducing errors and ensuring that the data is accurate and up to date. For example, employees can log into a self-service portal to update their address or submit their timesheets, which automatically updates the HR database.
Automating HR activities and improving data entry at the source offer several advantages. Firstly, it saves time and increases efficiency by eliminating manual and repetitive tasks. HR professionals can focus on more strategic initiatives, such as talent management, employee development, and organizational culture. Secondly, automation and improved data entry enhance data accuracy and integrity. By reducing human errors in data entry, HR processes can rely on reliable and up-to-date information, leading to more informed decision-making.
Moreover, technology enables HR departments to secure and protect sensitive employee data. Robust security measures, such as encryption, access controls, and regular data backups, can be implemented to safeguard employee information. This ensures compliance with data protection regulations and builds trust among employees regarding the confidentiality and security of their personal data.
Learn more about technology here : brainly.com/question/9171028
#SPJ11
Could someone please tell me what is the error in my code?
I'm trying to write a code for finding the cube of a number using C programming.

Answers
I think you have to remove the semicolon at the end of line 15. From what I see, this is not a logic error, rather than a syntax error.
Looking at the error on the bottom, it's expecting a '(' before the '{'.
which of the following views displays the text of your slides instead of slide thumbnails?
Answers
The view that displays the text of your slides instead of slide thumbnails is the Outline view.
In this view, you can see all the text on each slide in a simple list format, making it easier to review and edit the content of your presentation. The Outline view is especially helpful when creating longer presentations with many slides, as it allows you to quickly navigate between sections and make changes to the content without having to constantly switch back and forth between the Slide view and Thumbnail view. To access the Outline view in PowerPoint, click on the View tab in the ribbon and select the Outline View option from the Presentation Views group.
learn more about slide thumbnails here:
https://brainly.com/question/31179359
#SPJ11
when configuring a windows server with a class c private internet protocol (ip) address of , which of the following is the appropriate subnet mask?
Answers
When configuring a Windows Server with a Class C private IP address, the appropriate subnet mask is 255.255.255.0.
In Class C IP addressing, the first three octets (or 24 bits) are reserved for the network portion of the IP address, while the last octet (or 8 bits) is used for host addressing. With a subnet mask of 255.255.255.0, all the bits in the first three octets are set to 1, indicating the network portion, while the bits in the last octet are set to 0, allowing for host addressing within that network.This subnet mask allows for up to 254 host addresses within the network (since the first and last addresses are reserved for network and broadcast addresses, respectively) and is commonly used in small to medium-sized networks that require a limited number of hosts.
To learn more about appropriate click on the link below:
brainly.com/question/31516886
#SPJ11
Understanding others so I can effectively work with them is ___________. meekness discretion cooperation diligence
Answers
Answer:
cooperation
Explanation:
Cooperation is defined as the teamwork or the process in which few people work together to achieve a single goal.
In the given statement also, the person wants to understand other members in the team so that they can work together or cooperate with each other towards the same goal. Cooperation or teamwork will be successful only when team members will each other and will help each other to done the work effectively.
Hence, the correct answer is "cooperation".
Help me, I'll mark brainiest

Answers
Answer:
i believe the answers that you are looking for are c and c
Explanation:
again im not 100% sure that is right but i hope they are!
In the query design grid in access query design view, you place and criteria on _____, and you place or criteria on _____.
Answers
The query design grid in Access allows you to specify "AND" criteria on the same row and "OR" criteria on separate rows, enabling you to refine your query results based on multiple conditions.
In the query design grid in Access query design view, you place "AND" criteria on the same row, and you place "OR" criteria on separate rows. When you want to apply multiple conditions that must all be true, you use the "AND" operator. For example, if you want to retrieve records where the employee's age is greater than 30 and their salary is more than $50,000, you would place these criteria on the same row.On the other hand, when you want to apply multiple conditions where at least one condition must be true, you use the "OR" operator. For instance, if you want to retrieve records where the employee's job title is "Manager" or their department is "Sales," you would place these criteria on separate rows.
To know more about criteria, visit:
https://brainly.com/question/21602801
#SPJ11
the word item referred to as a: A.value B.label C.Formula
Answers
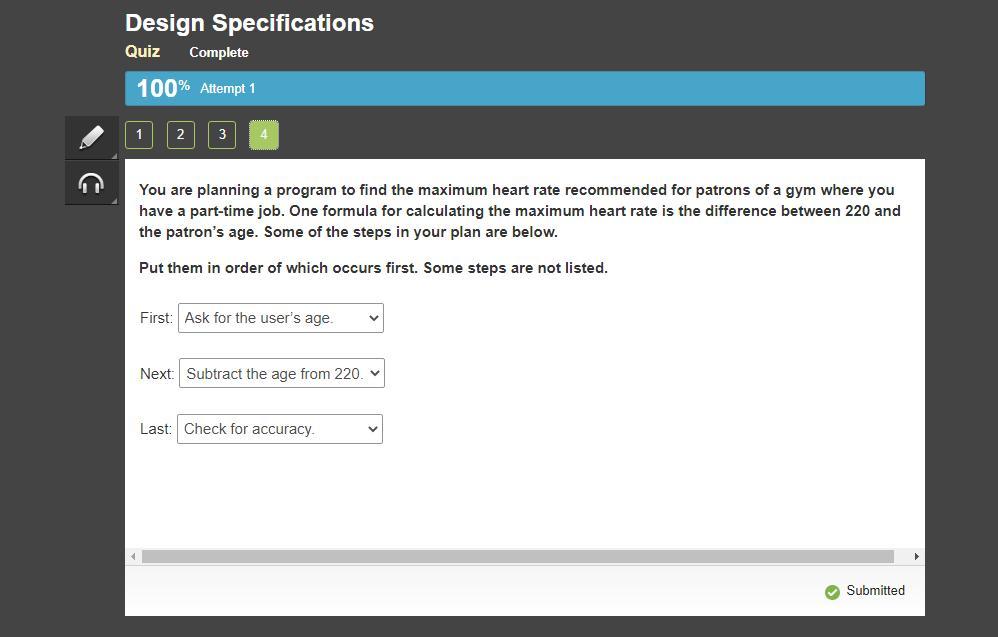
You are planning a program to find the maximum heart rate recommended for patrons of a gym where you have a part-time job. One formula for calculating the maximum heart rate is the difference between 220 and the patron’s age. Some of the steps in your plan are below.
Put them in order of which occurs first. Some steps are not listed.
Answers
Answer:
Age = int(input(Enter your age? "))
print(f"Your maximum heart rate is {220 - age}.")
Explanation:
The programs will be as follows
Age = int(input(Enter your age? "))
print(f"Your maximum heart rate is {220 - age}.")
Answer:
got 100 on the quiz
Explanation:
write an assembly program that has a macro maximumthat finds the larger of two numbers inputted by the user
Answers
By converting combinations of mnemonics and syntax for operations and addressing modes into their numerical representations, an assembler program generates object code.
What is assembler program?The majority of the statements or instructions in assembly language are mnemonic processor instructions or data. It is created by compiling the source code of high-level languages like C and C++. Assembly Language aids in program optimization.
.586
.MODEL FLAT
INCLUDE io.h
.STACK 4096
.DATA
value1 DWORD ?
value2 DWORD ?
"Enter the initial number," prompt1 BYTE, 0
"Enter the second number," prompt2 BYTE, 0
string BYTE 40 DUP (?)
resultLbl BYTE "The maximum value you entered was:", 0
.CODE
_MainProc PROC
input prompt1, string, 40 ;get user input value1
atod string ;convert input (ASCII) to integer
mov ebx, eax
input prompt2, string, 40 ; repeat for value2
atod string
mov value2, eax
cmp eax, ebx ;compare user inputs
jg greater_than ;jump conditional if value 1 is greater then value 2
greater_than: ;condition if greater than ouput
dtoa value1, eax ;decimal to ASC for output of
integer value stored at ebx
output resultLbl, value1 ;output value 1
jmp exit
less_than: ;condition if less than ouput
dtoa value1, eax
output resultLbl, value2 ;else output value 2
jmp exit
exit: ;quit jump ;end if/else conditional
mov eax, 0 ;clear memory
mov ebx, 0
ret
_MainProc ENDP
END
assemblyx86
The complete question is
Simple assembly program to spit out the greater of two user input numbers. I am having trouble getting the output correct. Example if I entered 45 and 55, the maximum value would be 55, however when I try the reverse 55 and 45 (the answer should still be 55) I get 45. It would appear that this program only ever outputs the second value entered and stored at EAX. Any help is greatly appreciated.
To learn more about assembler program refer to:
https://brainly.com/question/13171889
#SPJ4
; Set up input/output
movlw 0x00
movwf TRISA
movlw 0x00
movwf TRISB
; Define MAXIMUM macro
MAXIMUM MACRO num1, num2
movf num1, W
subwf num2, W
btfsc STATUS, C
movf num2, W
movwf num1
ENDM
; Main program
main:
; Prompt user to enter first number
movlw 0x31
call putch
call getch
movwf num1
; Prompt user to enter second number
movlw 0x32
call putch
call getch
movwf num2
; Find and display larger number
MAXIMUM num1, num2
call putch
; Repeat
goto main
Are the following scenarios a breach of confidentiality, integrity or availability? Explain your reasoning.
In September of 2017, Equifax announced a data breach that exposed the personal information of 147 million people. How did this exposure breach the CIA Triad?
Downloading what appears to be a legitimate app, a user installs malware which contains keylogging software. What type of breach is the downloading of malware?
An email phishing attack results in ransomware, in which the files and folders on a computer are encrypted. What type of breach is ransomware?
How do fake social media accounts breach the CIA Triad?
Answers
The Equifax data breach violated confidentiality by exposing the personal information of 147 million people. Social Security numbers and other private information were accessible to the attackers.
What are the data's confidentiality, accessibility, and integrity?You must be assured that your data is secure against unauthorised access. Integrity – Your data must be trustworthy. Accessibility – You must have access to your data.
What constitutes a violation of integrity?Failure to act with integrity is BREACH. For instance, if you promise to be on time for a meeting then arrive late, your tardiness is seen as a BREACH of INTEGRITY. BREAKS destroy TRUST; they render you unreliable and make you appear less important to the group.
To know more about data visit:-
https://brainly.com/question/11941925
#SPJ1