In order to generate a public and private key for use with SSH, what command line utility should you use?
ssh-keygen
NAT mode
Network layer
SDN controller
Answers
In order to generate a public and private key for use with SSH, you should use the command line utility `ssh-keygen`. Your answer: ssh-keygen. Hence, the correct option is A.
A command-line interface is used by a command-line interpreter or processor to receive instructions from a user in the shape of lines of text. By doing so, it is possible to specify environment-specific parameters, call executables, and tell them of the tasks they are to complete.
The command line functions as our operational hub from which we can run and communicate with other programmes. It has a unique syntax that you must learn, but since you'll be typing the same commands repeatedly, you'll rapidly learn the ones you use the most.
To learn more about command-line interface, click here:
https://brainly.com/question/29590552
#SPJ11
Related Questions
Write a method that takes a RegularPolygon as a parameter, sets its number of sides to a random integer between 10 and 20 inclusive, and sets its side length to a random decimal number greater than or equal to 5 and less than 12. Use Math.random() to generate random numbers.
This method must be called randomize() and it must take an RegularPolygon parameter.
Could someone help me out here thanks! C:
Answers
Answer:
public static void randomize(RegularPolygon r){
int side = (int)((20-10) * Math.random()) + 10;
int length = (int)((12-5) * Math.random()) + 5;
// assuming the regularpolygon class has setSide and setLength methods.
r.set.Side(side);
r.setLength(length);
}
Explanation:
The randomize method is used to access and change the state of the RegularPolygon class attributes sides and length. The method accepts the class as an argument and assigns a random number of sides and length to the polygon object.
According to Dr. Marianne Cooper from Stanford University, to transform a toxic culture, instead of celebrating the ________, senior leadership should be celebrating the ________. a
Answers
According to Dr. Marianne Cooper from Stanford University, to transform a toxic culture, senior leadership should be celebrating the behaviors and values that align with the company's desired culture, rather than celebrating individual accomplishments or achievements.
Instead of celebrating the "rockstars" or top performers who may engage in toxic behaviors, senior leadership should be celebrating the team players, those who exhibit empathy, collaboration, and a willingness to learn and grow. By celebrating these behaviors and values, senior leadership can set the tone for the type of culture they want to foster within the organization, and help to shift the focus away from toxic behaviors that may have been previously rewarded. Ultimately, this can lead to a healthier and more productive work environment for all employees.
learn more about toxic culture, here:
https://brainly.com/question/31448721
#SPJ11
A set of data with a correlation coefficient of -0.855 has a a. moderate negative linear correlation b. strong negative linear correlation c. weak negative linear correlation d. little or no linear correlation
Answers
A set of data with a correlation coefficient of -0.855 has a weak negative linear correlation.
Thus, A correlation coefficient gauges how closely two variables are related to one another. The Pearson coefficient, which has a range of -1.0 to +1.0, is the correlation coefficient that is most frequently employed.
Two variables that have a positive correlation tend to move in the same direction. Two variables with a negative correlation tend to move in the opposing directions.
While a correlation value of -0.3 or lower shows a very weak association, one of -0.8 or lower suggests a strong negative relationship.
Thus, A set of data with a correlation coefficient of -0.855 has a weak negative linear correlation.
Learn more about Corelation, refer to the link:
https://brainly.com/question/30116167
#SPJ4
Imagine that you are going to recommend a pet to someone. What are three questions you would ask them to help make that recommendation?
Answers
Answer: what kind of pet do u like? Would u like a big animal? Would u want a reptile or a dog and that stuff?
Explanation:
The three questions to ask to help make a suitable recommendation:
What is your daily routine like, and how much time can you dedicate to caring for a pet?Do you have any allergies or sensitivities to pet dander or fur?What type of living situation do you have (apartment, house, etc.), and are there any pet-related restrictions?What is the recommendationIf we know what a person does every day, it will help us figure out if they have enough time to take care of a pet.
This includes giving them food, keeping them clean, making sure they get enough exercise, and spending time with them. Some pets need more time and care than others, so it's important to choose a pet that matches the person's lifestyle.
Read more about recommendation here:
https://brainly.com/question/25288497
#SPJ3
Using more than one array to store related data is called _____________ arrays.
Answers
Answer:
Using more than one array to store related data is called parallel arrays.
Explanation:
I just did it and got 100% on the quiz
Using more than one array to store related data is called parallel arrays.
What is array?An array is a type of data structure used in computer science that holds a set of elements that are all uniquely recognised by at least one array index or key.
An array is stored in a way that allows a mathematical formula to determine each element's position given its index tuple.
In parallel arrays, a collection of data is represented by two or more arrays, where each corresponding array index represents a field that matches a particular record.
For instance, the array items at names and ages would explain the name and age of the third person if there were two arrays, one for names and one for ages.
Thus, the answer is parallel array.
For more details regarding parallel array, visit:
https://brainly.com/question/27041014
#SPJ6
it is defined as the interloping of yarn with the use of a hook to make a design . A smocking B knitting C crocheting D embroidery
Answers
Answer:
letter C
Explanation:
because the crocheting is defined as the interloping yarn and use to make and made a design to excellent.
6. relate how windows server active directory and the configuration of access controls achieve cia for departmental lans, departmental folders, and data.
Answers
To relate how Windows Server Active Directory and the configuration of access controls achieve CIA (Confidentiality, Integrity, and Availability) for departmental LANs, departmental folders, and data, follow these steps:
1. Implement Active Directory (AD): AD is a directory service provided by Windows Server for organizing, managing, and securing resources within a network. It centralizes the management of users, computers, and other resources, ensuring consistent security settings and access controls across the entire environment.
2. Organize resources into Organizational Units (OUs): Within AD, create OUs to represent different departments or functional areas. This allows for the efficient application of security policies and access controls based on departmental requirements.
3. Create user accounts and groups: In AD, create user accounts for each employee and assign them to appropriate departmental groups. This allows for the management of access rights and permissions based on group membership, ensuring that users only have access to the resources required for their roles.
4. Configure access controls: Apply access control lists (ACLs) to departmental LANs, folders, and data. ACLs define the permissions that users or groups have on specific resources, ensuring confidentiality by restricting unauthorized access.
5. Implement Group Policy Objects (GPOs): Use GPOs to enforce security policies and settings across the entire network. This ensures consistent security configurations, such as password policies and software restrictions, contributing to the integrity of the environment.
6. Monitor and audit: Regularly review security logs and reports to identify potential security breaches or unauthorized access attempts. This allows for prompt remediation and ensures the ongoing availability of resources to authorized users.
In summary, Windows Server Active Directory and the configuration of access controls achieve CIA for departmental LANs, departmental folders, and data by centralizing the management of resources, implementing access controls based on user roles, and enforcing consistent security policies across the environment.
Learn more about Windows Server: https://brainly.com/question/30985170
#SPJ11
Which of the following statements is FALSE?
A. The Internet allows people to spread news across borders and time zones quickly.
B. Late breaking news typically goes to television coverage before the Internet because of
accessibility.
C. Via the Internet, anyone can share their reactions to events instantly.
D. On the Internet, anyone can report news events.
Answers
Need answer ASAP. Thanks
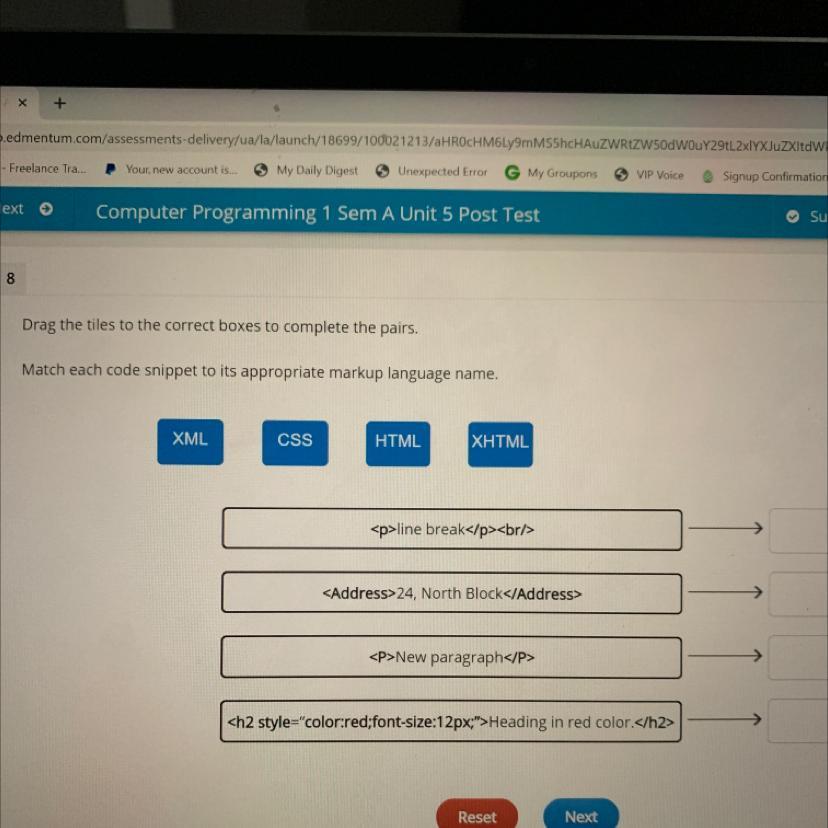
Answers
Answer:
1. XHTML
2. XML
3. HTML
4. CSS
Explanation:
Which of these is considered a server? Check all that apply.Software that's only available to the computer it's installed onA computer that provides a service to other computersSoftware that provides a service to other machinesA software that provides a service to other software
Answers
A computer that provides a service to other computers and software that provides a service to other machines are both considered servers.
A server is a computer or software that provides services or resources to other devices or software, such as hosting websites, sharing files, managing networks, or running applications. A server typically has more processing power, storage, and memory than a typical desktop computer, and is designed to handle multiple requests and clients simultaneously.In the context of software, a server can be a program that runs in the background and provides services to other software applications, such as a database server or a web server. This type of server can be accessed by other software applications over a network or the internet, allowing them to share data or access specific resources.To know more about servers visit:
https://brainly.com/question/28445434
#SPJ1
a packet analyzer is a program that can enable a hacker to do all of the following except ________.
Answers
A packet analyzer is a computer network that has the ability to intercept and log traffic that flows through the network of a computer. A packet analyzer is a program that can enable a hacker to do all of the following except;
D) Launch a denial of service (DoS) attack on your computerSince it is able to read and capture the raw data moving through a network, hackers can use a packet analyzer to decode the details in a user's debit card.
Identity theft can be executed and passwords can be captured using this program.
However, the computer's network cannot be shut down with this program. Therefore, option D is right.
Options:
A) Use your debit card information to purchase items illegally
B) Assume your identity
C) Steal your logons and passwords for various accounts
D) Launch a denial of service (DoS) attack on your computer
Learn more here:
https://brainly.com/question/14390016
you are given a dataframe consisting of three columns and four rows. a ufunc is then applied to that dataframe and another dataframe is outputted. how many columns are present in that final dataframe
Answers
If a person is given a dataframe consisting of three columns and four rows. the columns that are present in that final dataframe is 7.
What is a DataFrame?A DataFrame is known to be a term that connote a kind of a data structure that put together data into a kind of a 2-dimensional table that is said to be made up of rows and columns, such like a spreadsheet.
Note that DataFrames are said to be one of the most popular data structures that is said to be used in modern data analytics due to the fact that they are a flexible and good way of saving and working with data.
Hence, If a person is given a dataframe consisting of three columns and four rows. the columns that are present in that final dataframe is 7.
Learn more about data frame from
https://brainly.com/question/24024733
#SPJ1
Large-scale, long term storage is typically implemented with what kind of memory technology? a. Disk b. DRAM c. SRAM d. Does not matter. e. Flash
Answers
Large-scale, long term storage is typically implemented with disk technology. Disk technology, also known as hard disk drives (HDDs), is widely used for large-scale storage because it provides high capacity and relatively low cost per gigabyte compared to other memory technologies like DRAM and SRAM. While flash memory is also becoming increasingly popular for storage, it is still not commonly used for large-scale, long term storage due to its high cost and limited write endurance. Therefore, for large-scale storage needs, disk technology remains the most practical and cost-effective solution. Overall, disk technology has proven to be a reliable and efficient method for storing data over long
Disk storage, such as hard disk drives (HDD) or solid-state drives (SSD), provides high capacity, cost-effective solutions for storing data over an extended period. In contrast, DRAM and SRAM are volatile memory types that do not retain data when power is lost, making them unsuitable for long-term storage. Flash memory, such as USB drives, can be used for some storage purposes, but disk storage remains the preferred choice for large-scale, long-term data storage due to its higher capacity and reliability.
To know more about disk technology visit:
https://brainly.com/question/31116227
#SPJ11
How do clinical information systems with decision support incorporate evidence-based information?.
Answers
Clinical Information systems helps in decision making by analyzing the data within the EHRs which reminders to assist the healthcare.
What is Clinical Information system?Clinical information system is the data which gives immediate information of the patients about their medical history, X-rays, laboratory reports etc.
CIS helps to support the evidence based information by analyzing the data within the EHRs which reminders to assist the healthcare.
It is also applicable cardiovascular disease (CVD) prevention also gives information on treatment, medication for changes in the health.
Learn more about Clinical information system here:
https://brainly.com/question/14700439
#SPJ1
Hello!
Can you help me to write a program for tranpose and determinant of matrix in C++ with functions?
Please I must be done tonight :(((
Answers
Answer:
std::cout << "Hello World!\ n";
What is string literal in Java?
variable type that allows more than one character
group of printable characters enclosed within double quotation marks
group of printable characters enclosed within curly brackets
variable type that only allows for one character
Answers
Answer:
A string literal in Java is basically a sequence of characters from the source character set used by Java programmers to populate string objects or to display text to a user. These characters could be anything like letters, numbers or symbols which are enclosed within two quotation marks.
Explanation:
Independence Day celebration in school paragraph
Answers
Answer:
We celebrated the Independence day in our school compound, with great pump and show. The school building and the ground were cleaned and decorated for the occasion. A flag pole was put up at the top of the school building. The seating arrangement was made on the platform
Explanation:
please Mark my answer in brainlist
when is it appropriate for head office to decide transfer price in highly decantralised organisation
Answers
In a highly decentralized organization, it is generally appropriate for the head office to decide on the transfer price in certain situations. Here are a few scenarios when this may be necessary:
Ensuring consistency: The head office may set transfer prices to ensure uniformity across different units or divisions of the organization. This helps in maintaining consistent pricing strategies and avoids any discrepancies that may arise due to decentralized decision-making.
Overall, the appropriateness of the head office deciding on transfer prices in a highly decentralized organization depends on the specific circumstances and goals of the organization. It is essential to consider factors such as consistency, cost control, conflict resolution, profitability, and specialized knowledge when making such decisions.
To know more about decentralized visit:
https://brainly.com/question/32568277
#SPJ11
What parameter can be used in the windows cli to force a user to change their password on the next logon?
Answers
To change the password, Enter the password command together with the user's login name to change another user's password (the User parameter).
What is command?By changing the user's password in a way that can be recovered, the command "passwd" effectively locks the user out of the system.In Unix, the "passwd" command is used to create and modify user passwords. Change your own password or another user's password with this command. The 'passwd' command can also be used to modify your shell, which serves as your interface to the operating system, and the complete name (gecos) linked to your login name.The password of the user may be stored locally or remotely, depending on how the user is recognised. Users' local passwords are stored in the database /etc/security/passwd. Users' remote passwords, however, are kept in a database made available by the remote domain.To learn more about command refer to:
https://brainly.com/question/26075927
#SPJ4
James entered into a public cloud computing arrangement without reviewing the standard contract carefully. What problem is he most likely to face as a result?
a) Unexpected cloud downtime
b) Insufficient storage capacity
c) Inadequate data security
d) Inflexible pricing structure
Answers
Unexpected cloud downtime is the most likely to face as a result.
Thus, A disruption in cloud-based services is known as cloud downtime. The migration of more businesses to the cloud means that any disruption in cloud services might be expensive.
According to Gartner, the average cost of cloud downtime is $300,000 per hour. Major cloud service companies appear to routinely report disruptions. These interruptions can endure for a few hours or several days. Three outages affected AWS in a single month in 2021.
An outage of any length can have a negative impact on the bottom line for businesses that are still working to incorporate cloud technology into their business strategy.
Thus, Unexpected cloud downtime is the most likely to face as a result.
Learn more about Downtime, refer to the link:
https://brainly.com/question/28334501
#SPJ4
Some people worry that there won’t be enough jobs in the future because computers will be able to do everything better than people can. Do you think that will happen? Why or why not? pls explain
Answers
Answer: I think it will because there are cars that Drive by there self
Explanation:
CRT displays are used in laptops because they a flat.
True
False
Answers
Answer:
true
is answer
Explanation:
he ha hagbxbffjyet
Answer:
They used to, but they dont anymore. So the answer is false!
Have a great day!
Is an object something that contains both state and behavior?
Answers
Yes, an object is something that contains both state and behavior. Objects in programming are typically made up of two parts: data (or state) and methods (or behavior).
What is programming ?Programming is the process of creating instructions that tell a computer how to perform a task. It involves writing code using a programming language, such as Java, C++, or Python, to create an algorithm that can be executed by a computer. Programming is an essential part of software development, and it requires an understanding of the logic and structure of the underlying language to write effective code. Programming can be used to create applications, games, websites, and other software systems. It can also be used to automate repetitive tasks and create data visualizations. Programming is an essential skill for many jobs in the tech industry.
To learn more about programming
https://brainly.com/question/23275071
#SPJ4
Topic: Video Games.
What game is the song "Lost in Thoughts all Alone" from? I will give you a hint: It's a JRPG.
Please...No links or gibberish.
Answers
Answer:
Fire Emblem
Explanation:
When searching for your word processing file to finish writing your report, you should look for a file with which extension? (6 points)
Answers
Answer:
doc
Explanation:
the join column must be included in the select statement when you use the natural join clause. true or false
Answers
The statement is false. When using the NATURAL JOIN clause in a SQL query, the join column(s) are not required to be explicitly included in the SELECT statement.
The NATURAL JOIN clause is used to join two or more tables based on columns with the same name in each table. It automatically matches the columns with the same name and performs the join operation. In this case, the join column(s) are implied and automatically included in the join operation.
When using NATURAL JOIN, the resulting join column(s) are not explicitly listed in the SELECT statement. The columns with the same names from the joined tables are combined into a single column in the result set.
It's important to note that the NATURAL JOIN clause can introduce ambiguity or unexpected results if the tables being joined have additional columns with the same name but different meanings. Therefore, it is recommended to use caution when using the NATURAL JOIN clause and consider explicitly specifying the join conditions or using other types of joins to ensure clarity and accuracy in the query results.
learn more about join column here; brainly.com/question/31313425
#SPJ11
Keith needs to import data into an Access database from a text file. Which option is the most common delimiter and easiest to work with?
Answers
Answer:tab
Explanation:
Cause I got it right
Answer:
The answer is a comma.
Explanation:
This is the correct answer because space and tab are not delimiters. Therefore it has to be either comma or semicolon and a semicolon is bigger and harder to navigate around. So this gives you the answer of a comma.
The quick access toolbar can be customized, but the ribbon can not be customized. True or false?.
Answers
Answer:
False
Explanation:
Given the code above, which item identifies the method's return type?
A.public
B.println
C.static
D.
Answers
The method's return type in the given code is identified by the term "void".
The return type of a Java method is specified just before the name of the method. In this case, we have a method called main, and its return type is indicated by the keyword void, which means that the method does not return any value.
So, the correct answer to your question is option d: void. Options a, b, and c do not specify the return type of the method.
Additionally, there is a syntax error in the given code. The correct syntax for defining a class and its main method in Java is as follows:
public class First {
public static void main(String[] args) {
System.out.println("First Java application");
}
}
Note the use of curly braces to define the body of the class and the method, and the use of uppercase S and System for the out object's reference.
Learn more about void here:https://brainly.com/question/25644365
#SPJ11
Your question is incomplete but probably the full question was:
public class First
(
public static void main(String[] args)
(
system.out.println("First Java application");
)
)
given the above code, which item identifies the method's return type?
a. public
b. println
c. static
d. void

Write code that reads in a value for variable numcarrots and then outputs as follows. end with a newline. if the input is 3, the output is:
Answers
In both cases, a newline will be printed at the end.
An example code in Python that reads the value for the variable numcarrots and generates the desired output:
numcarrots = int(input("Enter the number of carrots: "))
output = ""
for i in range(numcarrots):
output += "carrot"
if i != numcarrots - 1:
output += ", "
print(output)
This code prompts the user to enter the number of carrots and stores it in the numcarrots variable. It then iterates from 0 to numcarrots - 1 and appends the string "carrot" to the output variable. Commas are added between the carrots except for the last one. Finally, the output is printed, resulting in the desired output.
If the input is 3, the output will be:
carrot, carrot, carrot
Note that this code assumes that the input will be a valid integer. If you want to handle potential errors or validate the input further, you can add appropriate error handling or input validation code.
Learn more about Python click;
https://brainly.com/question/30391554
#SPJ4