In order to complete each sentence, click and drag each word or phrase into the appropriate blank. Then, place the given events of fertilization in a logical order.
Answers
Sperms for two, noun, plural, sperms. spermatozoon, a cell of male reproduction.
What root word means seed or sperm?The fallopian tube, which connects the egg with the uterus, guides it. In the event of fertilization, it clings to the uterine wall, signaling the start of pregnancy. The uterus is where an unfertilized egg begins to degrade. Through the cervix, which is the uterine base, it exits the uterus.
Zygote, cleavage, morula, blastocyst, embryo, and fetus are the proper list of those that was given. To put it succinctly, the act of fertilization begins when a sperm cell penetrates the egg. The oocyte has now transformed into a zygote as a result of the union of the egg and sperm cells.
The prefix spermato-, which means "seed" and "sperm," is a combining form. The reproductive cells in semen are known as sperm.
To learn more about logical order refer to :
https://brainly.com/question/1294562
#SPJ1
Related Questions
Which model is used to guide IT security practices?
FBI triad
OSI triad
CIA triad
CSI triad
Answers
Answer:
OSI triad
Explanation:
This OSI is pratice to guide IT security.
The model used to guide IT security practices is the CIA triad.
Option C is the correct answer.
We have,
CIA stands for Confidentiality, Integrity, and Availability, and it is a fundamental concept in information security.
The CIA triad is used as a guideline to design, implement, and assess the security of information systems and data.
It helps organizations ensure that their information and resources are protected against unauthorized access, data tampering, and service disruptions.
Each component of the triad:
- Confidentiality:
Confidentiality refers to the principle of ensuring that sensitive information is only accessible to authorized individuals or entities.
It aims to prevent unauthorized access to sensitive data, such as personal information, financial records, or proprietary business data. Measures like access controls, encryption, and user authentication are used to maintain confidentiality.
- Integrity:
Integrity involves maintaining the accuracy, consistency, and trustworthiness of data throughout its lifecycle.
It ensures that information remains unaltered and protected against unauthorized modification, deletion, or corruption. Techniques like checksums, digital signatures, and data validation mechanisms help ensure data integrity.
- Availability:
Availability focuses on ensuring that information and services are accessible and usable when needed.
This means preventing service disruptions, downtime, or denial of service attacks, which could prevent legitimate users from accessing resources. Redundancy, backup systems, load balancing, and disaster recovery plans are some strategies to maintain availability.
Thus,
The model used to guide IT security practices is the CIA triad which is option C.
Learn more about IT security here:=
https://brainly.com/question/28902889
#SPJ3
What is the Law of Magnetic Force?
Answers
Answer:
The force between two magnetic poles is directly proportional to the product of their poles strength and inversely proportional to the square of the distance between them.
Have a great day! Brainliest?
Using Phyton
Write a program with the following functions.
function 1: Accepts 2 strings as arguments. returns true if the second string is a part of the first string.
Answers
def something(string1, string2):
return True if string2 in string1 else False
This would be the most concise way of writing this function.
An algorithm is:
A set of steps used to complete a specific task
The first step in the problem-solving process
The study of people's efficiency in their working environment
A block-coding program used in computer science
Answers
what is the role of product management in agile safe
Answers
Product management plays a crucial role in Agile SAFe (Scaled Agile Framework) by defining desirable, viable, feasible, and sustainable solutions that meet customer needs and supporting development across the product life cycle.
In an Agile SAFe environment, product management acts as the bridge between the customer and the development teams. They are responsible for understanding customer needs, gathering feedback, and translating those needs into actionable requirements.
By collaborating with stakeholders, product management ensures that the product vision aligns with customer expectations.
To define desirable solutions, product management conducts market research, user interviews, and analyzes customer feedback. They identify market trends, user pain points, and prioritize features accordingly.
They work closely with customers to gather insights and validate product ideas through iterative feedback loops.
Viable solutions are determined by evaluating market demand, competitive landscape, and business objectives. Product management considers factors like revenue potential, market share, and return on investment to ensure the product is financially sustainable.
Feasible solutions require close collaboration with development teams. Product management works with engineering, design, and other teams to assess technical feasibility, define scope, and establish delivery timelines.
They engage in Agile ceremonies such as sprint planning, backlog refinement, and daily stand-ups to facilitate efficient development.
Sustainable solutions are designed with long-term success in mind. Product management focuses on creating scalable, adaptable products that can evolve with changing customer needs and market dynamics. They continuously monitor and analyze product performance, customer feedback, and market trends to make informed decisions and drive iterative improvements.
In summary, product management in Agile SAFe is responsible for understanding customer needs, defining desirable and viable solutions, ensuring technical feasibility, and supporting development teams throughout the product life cycle to deliver sustainable products that meet customer expectations.
For more such questions Product,click on
https://brainly.com/question/28776010
#SPJ8
5 operating systems from the best to the worst and why.
I'll give brainliest fr
Answers
Answer:
Microsoft windows.Mac Operating system.iOSLinux Operating system.Ubuntu Operating system.\(.\)
My best memory was the first time I ever saw a movie like Despicable Me with my father, which was at a movie theater.
Answers
Answer: That sounds really nice. I used to go see movies with my dad all the time too. One of my favorites was Monsters vs. Aliens
Explanation:
19 POINTS! What does the icon for changing the color of a cell or range look like? (Excel)
a pencil
the letter A
a paint bucket
a paintbrush
Answers
Answer:
Paintbucket
Explanation:
I got it right
Answer:
A Paint Bucket
Explanation:
Luke is setting up a wireless network at home and is adding several devices to the network. During the setup of his printer, which uses 802. 11g standard, he finds that he can't connect to the network. While troubleshooting the problem, he discovers that his printer is not compatible with the current wireless security protocol because it is an older version of hardware.
What wireless network security protocol will allow Luke to use the printer on his wireless network?
a. WPA
b. WEP
c. WPA2
d. WPA-PSK+WPA2-PSK
Answers
The wireless network security protocol that will allow Luke to use the printer on his wireless network is WEP. The correct answer is option b.
WEP (Wired Equivalent Privacy) is a security protocol that is used to secure wireless networks. It was introduced in 1999 and was widely used in the early days of wireless networking. However, it is an older version of hardware and is considered less secure than newer protocols such as WPA (Wi-Fi Protected Access) and WPA2 (Wi-Fi Protected Access 2).
Since Luke's printer is an older version of hardware, it is not compatible with the current wireless security protocol. Therefore, using WEP will allow Luke to use the printer on his wireless network.
Learn more about wireless network security:
brainly.com/question/30087160
#SPJ11
A ________ monitors network traffic for particular network segments or devices and analyzes network, transport, and application protocols to identify suspicious activity
Answers
A network intrusion detection system (NIDS) monitors network traffic for particular network segments or devices and analyzes network, transport, and application protocols to identify suspicious activity. NIDS are designed to detect and alert on potential security threats or anomalies that may indicate a breach or attack on a network.
A network intrusion detection system (NIDS) is a type of security software designed to monitor a network for malicious activity or policy violations. NIDSs operate by analyzing network traffic and comparing it against a set of rules or criteria to identify potentially malicious activity.
NIDSs can be configured to monitor specific protocols, ports, or traffic patterns and to alert administrators when suspicious activity is detected. They can also be configured to take automatic action in response to certain types of activity, such as blocking traffic from a particular IP address or triggering a system lockdown.
Learn more about NIDS, here https://brainly.com/question/20556615
#SPJ4
write an sql statement to display the warehouseid and the sum of quantityon-hand grouped by warehouseid. name the sum totalitemsonhand and display the results in descending order of totalitemsonhand. (provide the select script statement and screenshot) g
Answers
The command used in SQL statement is SELECT, SUM(), and DESC to display the warehouseid and the sum of quantityon-hand grouped by warehouseid and display the result in descending order.
What is command in SQL?Command in SQL is used as instructions to communicate the data in database.
The code is below,
SELECT warehouseid,
SUM(quantityon-hand) AS totalItemsonhand
FROM INVENTORY
GROUP BY warehouseid
ORDER BY totalItemsonhand DESC
First, we select the data that want to be displayed with SELECT command. Then SUM() command will sum all quantityon-hand from inventory in group warehouseid. Displayed result in descending order can be instructed by command DESC.
Since, we want to name it totalitemsonhand, then use AS command to rename the result of SUM() to totalitemsonhand.
Learn more about SQL here:
brainly.com/question/25694408
#SPJ4
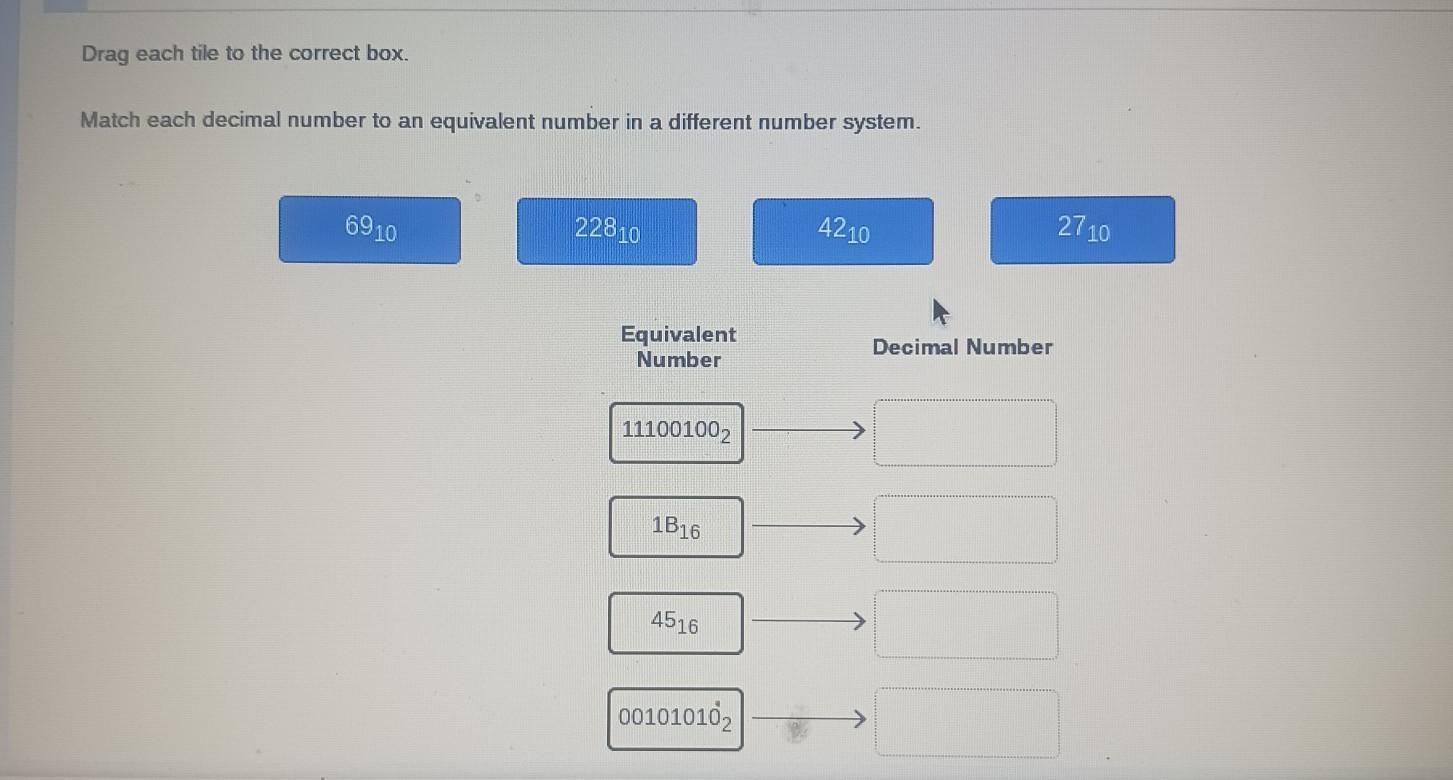
Drag each tile to the correct box. Match each decimal number to an equivalent number in a different number system. 6910 22810 4210 2710
Answers
Explanation:
you can do that with calculator only

What is a disadvantage of shopping online? A. Less choice of products B. Harder to compare prices than in stores C. A higher risk of financial data theft D. More time is spent traveling
Answers
Answer:
C. A higher risk of financial data theft
Explanation:
In Business, e-commerce can be defined as a business model which involves the buying and selling of goods or products over the internet.
Generally, e-commerce comprises of four (4) business models and these are;
1. Business to Business (B2B).
2. Business to Consumer (B2C).
3. Business to Government (B2G).
4. Consumer to Consumer (C2C).
Generally, in e-commerce the producer creates an online store where various customers can access to choose and purchase the products they like. Thus, the payment for this type of transaction is primarily or mainly done over the internet through the use of internet banking using credit or debit card details.
Hence, a disadvantage of shopping online is a higher risk of financial data theft because the customers are required to provide their credit or debit card details which if not done securely or kept safe by the merchant, it may be compromised and as such giving unauthorized access to online hackers.
Line formatting can be accomplished by using
Answers
Answer:
How can line formatting be accomplished?
To format line spacing:
Select the text you want to format. Selecting text to format.
On the Home tab, click the Line and Paragraph Spacing command. A drop-down menu will appear.
Move the mouse over the various options. A live preview of the line spacing will appear in the document. Select the line spacing you want to use.
The line spacing will change in the document.
ti-84 plus ce 5.3.0 notes program error invalid attempted to use a variable or function where it is not valid
Answers
If you attempt to graph a function that does not use the stat plot features, you may receive the ERR:INVALID DIMENSION error notice. Turning off the stat plots will fix the mistake. To disable the data plots, click y and then 4:PlotsOff.
Why is my TI-84 displaying an incorrect dimension?DIM IS INVALID If you try to graph a function and receive this notification, it indicates that the calculator is attempting to graph points from a set of lists but is unable to do so due to their varying sizes (or empty). This usually indicates that the list visualization was inadvertently enabled.
all from the same box If the calculator display does not appear after changing the batteries, consider adjusting the contrast (step 2). Take one of the AAA batteries out. Hold down the [CLEAR] button. Replace the AAA cell and hit [ON] while holding [CLEAR].
Learn more about calculator from here;
https://brainly.com/question/28358915
#SPJ4
Lossy compression means that when you compress the file, you're going to lose some of the detail.
True
False
Question 2
InDesign is the industry standard for editing photos.
True
False
Question 3
Serif fonts are great for print media, while sans serif fonts are best for digital media.
True
False
Question 4
You should avoid using elements of photography such as repetition or symmetry in your photography.
True
False
Answers
Lossy compression means that when you compress the file, you're going to lose some of the detail is a true statement.
2. InDesign is the industry standard for editing photos is a true statement.
3. Serif fonts are great for print media, while sans serif fonts are best for digital media is a true statement.
4. You should avoid using elements of photography such as repetition or symmetry in your photography is a false statement.
What lossy compression means?The term lossy compression is known to be done to a data in a file and it is one where the data of the file is removed and is not saved to its original form after it has undergone decompression.
Note that data here tends to be permanently deleted, which is the reason this method is said to be known as an irreversible compression method.
Therefore, Lossy compression means that when you compress the file, you're going to lose some of the detail is a true statement.
Learn more about File compression from
https://brainly.com/question/9158961
#SPJ1
What happens after the POST?
Answers
After the POST, the computer is ready for user interaction. Users can launch applications, access files, browse the internet, and perform various tasks depending on the capabilities of the operating system and the installed software.
After the POST (Power-On Self-Test) is completed during a computer's startup process, several important events take place to initialize the system and prepare it for operation. Here are some key steps that occur after the POST:
1. Bootloader Execution: The computer's BIOS (Basic Input/Output System) hands over control to the bootloader. The bootloader's primary task is to locate the operating system's kernel and initiate its loading.
2. Operating System Initialization: Once the bootloader locates the kernel, it loads it into memory. The kernel is the core component of the operating system and is responsible for managing hardware resources and providing essential services.
The kernel initializes drivers, sets up memory management, and starts essential system processes.
3. Device Detection and Configuration: The operating system identifies connected hardware devices, such as hard drives, graphics cards, and peripherals.
It loads the necessary device drivers to enable communication and proper functioning of these devices.
4. User Login: If the system is set up for user authentication, the operating system prompts the user to log in. This step ensures that only authorized individuals can access the system.
5. Graphical User Interface (GUI) Initialization: The operating system launches the GUI environment if one is available. This includes loading the necessary components for desktop icons, taskbars, and other graphical elements.
6. Background Processes and Services: The operating system starts various background processes and services that are essential for system stability and functionality.
These processes handle tasks such as network connectivity, system updates, and security.
For more such questions on POST,click on
https://brainly.com/question/30505572
#SPJ8
Assume the variable s is a String and index is an int. Write an if-else statement that assigns 100 to index if the value of s would come between "mortgage" and "mortuary" in the dictionary. Otherwise, assign 0 to index.
Answers
Using the knowledge in computational language in python it is possible to write a code that Assume the variable s is a String and index is an int.
Writting the code:Assume the variable s is a String
and index is an int
an if-else statement that assigns 100 to index
if the value of s would come between "mortgage" and "mortuary" in the dictionary
Otherwise, assign 0 to index
is
if(s.compareTo("mortgage")>0 && s.compareTo("mortuary")<0)
{
index = 100;
}
else
{
index = 0;
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

How many combinations of 1s and Os can we make with 6 place values?
Answers
Explanation:
which question is this
Write a program named palindromefinder.py which takes two files as arguments. The first file is the input file which contains one word per line and the second file is the output file. The output file is created by finding and outputting all the palindromes in the input file. A palindrome is a sequence of characters which reads the same backwards and forwards. For example, the word 'racecar' is a palindrome because if you read it from left to right or right to left the word is the same. Let us further limit our definition of a palindrome to a sequence of characters greater than length 1. A sample input file is provided named words_shuffled. The file contains 235,885 words. You may want to create smaller sample input files before attempting to tackle the 235,885 word sample file. Your program should not take longer than 5 seconds to calculate the output
In Python 3,
MY CODE: palindromefinder.py
import sys
def is_Palindrome(s):
if len(s) > 1 and s == s[::-1]:
return true
else:
return false
def main():
if len(sys.argv) < 2:
print('Not enough arguments. Please provide a file')
exit(1)
file_name = sys.argv[1]
list_of_palindrome = []
with open(file_name, 'r') as file_handle:
for line in file_handle:
lowercase_string = string.lower()
if is_Palindrome(lowercase_string):
list_of_palindrome.append(string)
else:
print(list_of_palindrome)
If you can adjust my code to get program running that would be ideal, but if you need to start from scratch that is fine.
Answers
Open your python-3 console and import the following .py file
#necessary to import file
import sys
#define function
def palindrome(s):
return len(s) > 1 and s == s[::-1]
def main():
if len(sys.argv) < 3:
print('Problem reading the file')
exit(1)
file_input = sys.argv[1]
file_output = sys.argv[2]
try:
with open(file_input, 'r') as file open(file_output, 'w') as w:
for raw in file:
raw = raw.strip()
#call function
if palindrome(raw.lower()):
w.write(raw + "\n")
except IOError:
print("error with ", file_input)
if __name__ == '__main__':
main()
Where do charts get the data series names?
O data entries
O row labels
O column labels
O worksheet title
Answers
Answer:
B) Row labels
Explanation:

Write a complete Python program that opens a file called 'myfile', reads the entire contents of the file into a string s, determines the number of words in myfile and prints that number on a line, then prints out all words in myfile in alphabetical order, each word on a separate line.
Answers
Answer:
myfile = open("myfile","r").readlines();
myfile_altered = "".join(myfile.split("\n"))
length = len(myfile_altered)
myfile_sort = " ".join(myfile).split(" ")
myfile.sort()
print(length)
print(myfile)
Explanation:
I read the file and split the text by a space, and just sorted the list using `.sort()`
Should work (didnt test it). If it doesn't, just comment on this answer and I will debug it.
what is super computer ? List out application area of super computer.
Answers
Explanation:
Common applications for supercomputers include testing mathematical models for complex physical phenomena or designs, such as climate and weather, the evolution of the cosmos, nuclear weapons and reactors, new chemical compounds (especially for pharmaceutical purposes), and cryptology.
OR
A supercomputer is a computer that performs at or near the highest operational rate for computers. Traditionally, supercomputers have been used for scientific and engineering applications that must handle massive databases, do a great amount of computation, or both.
NEED HELP AS SOON AS POSSIBLE
A guideline for visual composition is to make use of lines. What do the following types of lines represent?
Vertical lines
Horizontal lines
Curved lines
Diagonal lines
Answers
True or False: To just display 1 letter on your
screen after you've typed it on your keyboard,
your-computer has to follow thousands of
instrucitons
Answers
Answer:
true
Explanation:
Choosing ideas and developing them is done during which step of the writing process
Answers
Answer:
prewriting.
Explanation:
Decide on a topic to write about and Brainstorm ideas about the subject and how those ideas can be organized.
does anyone play r0bIox
Answers
Answer:
Ah, okay okay, I know that game seems like a MEME, but it's actually good. I know a lot of kids play it and this community is filled with people...
Declare a constant named YEAR, and initialize YEAR with the value 2050. Edit the statement myNewAge = myCurrentAge + (2050 − currentYear) so it uses the constant named YEAR. Edit the statement cout << "I will be " << myNewAge << " in 2050." << endl; so it uses the constant named YEAR.#include
using namespace std;
int main()
{
int myCurrentAge = 29;
int myNewAge;
int currentYear = 2014;
myNewAge = myCurrentAge + (2050 - currentYear);
cout << "My Current Age is " << myCurrentAge << endl;
cout << "I will be " << myNewAge << " in 2050." << endl;
return 0;
}
looking for code pattern
Answers
Answer:
The following edits will be made to the source code
const int YEAR = 2050;
cout << "I will be " << myNewAge << " in "<<YEAR<<"." << endl;
Explanation:
First, YEAR has to be declared as an integer constant. This is shown as follows;
const int YEAR = 2050;
This will enable us make reference to YEAR in the program
Next,
Replace the following:
cout << "I will be " << myNewAge << " in 2050." << endl;
with
cout << "I will be " << myNewAge << " in "<<YEAR<<"." << endl;
I've added the edited source file as an attachment;
Create a Python program that prints all the numbers from 0 to 4 except two distinct numbers entered by the user.
Note : Use 'continue' statement.
Answers
Here is a Python program that prints all numbers from 0 to 4, excluding two distinct numbers entered by the user, using the 'continue' statement:
```python
numbers_to_exclude = []
# Get two distinct numbers from the user
for i in range(2):
num = int(input("Enter a number to exclude: "))
numbers_to_exclude.append(num)
# Print numbers from 0 to 4, excluding the user-entered numbers
for i in range(5):
if i in numbers_to_exclude:
continue
print(i)
```
The program first initializes an empty list called `numbers_to_exclude` to store the two distinct numbers entered by the user.
Next, a loop is used to prompt the user to enter two distinct numbers. These numbers are appended to the `numbers_to_exclude` list.
Then, another loop is used to iterate through the numbers from 0 to 4. Inside the loop, an 'if' condition is used to check if the current number is in the `numbers_to_exclude` list. If it is, the 'continue' statement is executed, which skips the current iteration and proceeds to the next iteration of the loop.
If the current number is not in the `numbers_to_exclude` list, the 'print' statement is executed, and the number is printed.
This program ensures that the two distinct numbers entered by the user are excluded from the output, while all other numbers from 0 to 4 are printed.
For more such answers on Python
https://brainly.com/question/26497128
#SPJ8
Problem 1 a = 4 b = 3 c = 20 while a < c a = a * 2 b = b * 3 Endwhile output a, b, c
Answers
Endwhile output is a = 4, b = 12, c = 20.
What is input and output?
Data must be added to or subtracted from code in all programmes. Inputs are the data that are entered into a programme, whether manually by the programmer or digitally. These inputs are used to run the programme and are saved as variables. A programmer may decide to include outputs to inform the user of what is happening inside the programme. Here, the user is presented with the program's data either visually (on the screen) or physically (as printouts or signals, for example). It's possible that a programme needs to talk to a user. This could be done to display the program's results or to ask for more details so that the programme can run. Output is what the user typically sees as text on their screen.
To learn more about input and output
https://brainly.com/question/27646651
#SPJ1