in healthcare, regulations often dictate that important systems remain unpatched to maintain compliance. which kind of vulnerability does this introduce? answer inherent vulnerabilities weak passwords misconfigurations application flaws
Answers
Application defects are problems with user authentication and authorization. The biggest risk to security in full development comes from these issues.
What does the term "vulnerability" mean?the attribute of being weak or an object that is weak: the capacity to be easily harmed, swayed, or attacked: A doctor who recognizes the patient's vulnerability is what you want. Attack planners took advantage of weak spots in the country's defenses.
Why is it so frightening to be exposed?Why do we worry about being exposed? We worry that if someone learns the truth about who we actually are, they won't accept us. In actuality, pretense frequently has the inverse result from what we intend, even if we may strive to appear flawless, powerful, or clever in order to communicate with others.
To know more about vulnerability visit:
https://brainly.com/question/15593733
#SPJ4
Related Questions
Which three functions could be used with the HIRE_DATE, LAST_NAME, or SALARY columns? (Choose three.)
MAX (*)
SUM
MIN (*)
COUNT (*)
AVG
Answers
The SQL value functions are MAX, MIN, COUNT.
The three functions that could be used with the HIRE_DATE, LAST_NAME, or SALARY columns are:
MAX
MIN
COUNT
These functions can be used to perform various calculations on the values in the HIRE_DATE, LAST_NAME, or SALARY columns of a database table. Specifically:
MAX: Returns the maximum (or highest) value from the column.
MIN: Returns the minimum (or lowest) value from the column.
COUNT: Returns the count of non-null values in the column.
Note that the "(*)" in the options is not relevant to the functions that can be used with the given columns. It indicates that the COUNT and MIN options are incorrect, as they are not the only functions that can be used with the given columns.
Hence , the SQL functions are solved
To learn more about functions in SQL click :
https://brainly.com/question/14744689
#SPJ4
Any ideas its python code projectstem.com is what we use, code shown by teacher is the same but cant find the issue to this,

Answers
Answer: Bro first read the error and fix it.
Explanation:
If it does not work, then it might be bugged, it usually happens when you are doing a large program with any programming language. So maybe save the work, and restart the PC or laptop.
If it still doesn't work, then you should try installing extension or pip for the code you are using, because you might be coding it right but have not installed an extension in the terminal.
What I mean by pip is that a pip is like an extension, and if for example you want to use turtle to draw in a program, you should go to the terminal and write:
pip install extension_name
And if you want to see if the pip is installed then do:
pip -V
or
pip --version
Also, if you want to upgrade the pip, do:
python -m pip install -U pip
It may happen sometimes that your pip current pip version is not supporting your current version of python or machine for that you can downgrade your pip version with the following command.
Note: You can mention the version you want to install
do:
python -m pip install pip==17.0
Note: remember that to install pips, you need to install them in a terminal, please don't do it in your code... It does not work.
fr, last note: always check if you have the last python version installed, and if not, go to the offical python website and install the latest python version possible, or intall python is you don't have it already.
Correct me if i'm wrong,
Happy to help :)
why do people make posts about talking or sharing social media. this is for SCHOOL and NOT social media.
Answers
Answer:
yeah j dont know why why they do that
you are the network administrator for a large organization. you are in charge of developing a plan to install 200 windows 10 computers in your company
Answers
As the network administrator for a large organization, developing a plan to install 200 Windows 10 computers requires careful consideration and organization. Here is a step-by-step plan to help you: Assess hardware requirements: Determine the specifications needed for each computer, such as processor speed, RAM, and storage capacity.
Decide on licensing: Choose the appropriate licensing option for Windows 10, considering factors like volume licensing or individual licenses for each computer.
Create an installation strategy: Decide whether to use an image deployment or install Windows 10 from scratch on each computer. An image deployment can save time and ensure consistency across computers.
To know more about organization visit:
https://brainly.com/question/12825206
#SPJ11
In order to terminate multiple network cables that converge in one location such as an electrical closet or server room, what should you use?a. patch panelb. loopback portc. terminal adapterd. RJ-45 jack
Answers
Patch panels should be used to terminate multiple network cables that converge in one location, such as an electrical closet or server room. Correct answer: letter A.
This is due to improved cable management, connectivity and security.
What are the reasons for using patch panels to terminate several network cables converging at the same location?Patch panels should be used to terminate multiple network cables that converge in one location for several reasons:
Firstly, patch panels provide easy and organized access to the network cables by allowing them to be managed and labeled. This makes troubleshooting and management of the cables much easier. Secondly, patch panels also help protect the cables from damage and wear and tear, as the cables are routed through the panel and then connected, rather than being exposed to other equipment or furniture in the room. Finally, patch panels also provide cable grounding and shielding, which helps protect the network from electromagnetic interference and ensures that the network performance remains good.Learn more about Network connection panels:
https://brainly.com/question/17243681
#SPJ4
Hello can someone help me with this, please
1) What kinds of siding does the house from “Up” have?
2) What type of roof does our house have?
3) How many gables/hips does the roof have? :
4) Look at the following styles of houses. What style home do you think the house from up is?
5) How do you know?




Answers
The house from "Up" has clapboard siding, which is a type of wooden siding that consists of long, narrow boards that overlap each other horizontally.
How to explain information regarding the houseThe house from "Up" appears to be a Victorian-style house with elements of Queen Anne style.
There are several characteristics of the house from "Up" that suggest it is a Victorian-style home. First, the house has a steeply pitched roof with multiple gables and dormer windows, which is a common feature of Victorian architecture.
The house also has a wrap-around porch with decorative railing, another hallmark of Victorian design. Additionally, the use of ornate detailing and vibrant colors, such as the elaborate trim work and bold purple paint, is typical of the Queen Anne style of Victorian architecture.
Learn more about house on:
brainly.com/question/23241042
#SPJ1
In this module you learned about making decisions. You learned about the syntax and rules used to develop programs containing decisions and how the logic can make your programs more robust.
Draw a flowchart for a program that shows the logic for a program that generates a random number and the player tries to guess it.
There are NO LOOPS, NO Functions(other than the random number generator) and NO MODULES at this point. Everything at this point is in sequence(Line-By-Line). You can add comments at the beginning of each block to explain what the code is doing..
Declare the variables and data types used
import random (Generate random integers using Python randint() - AskPython )
You want to add the code so the player can enter their name, then display a welcome message using their name.
You also want to display a message that describes what the program will do.
The program should allow the player to guess the number that was randomly generated.
Display a message indicating whether the player’s guess was too high, or too low.
When your program ends, thank the person for playing and display "Game Over"
Complete the Python code using IDLE Editor.
Complete the flowchart. Upload the exported PDF to the Blackboard assignment area by clicking on the Browse My Computer button below the text editor.
Answers
A flowchart for a program that shows the logic for a program that generates a random number and the player tries to guess it, and declares the variables and data types used, imports random (Generate random integers using Python randint() - AskPython), and displays a message that describes what the program will do.
Let's see the solution step-by-step:
Step 1: Importing the random module and declaring variables import randomplayer = input("Enter your name:")# Declare variables and data types usedrandom_number = random.randint(1,100)guess = 0print(f"\nWelcome {player}, let's play a game!")print("I am thinking of a number between 1 and 100. Can you guess it?")
Step 2: Starting the game with while loop. The game will continue until the player guesses the number. The player has to guess the number, and the program should give feedback if the guess is too high or too low, using if statements.while guess != random_number: guess = int(input("\nTake a guess: ")) if guess > random_number: print("Too high, try again!") elif guess < random_number: print("Too low, try again!")
Step 3: Printing the output If the player guesses the number, the program will end with a message thanking the person for playing and displaying "Game Over".print("\nCongratulations, you guessed the number!")print(f"Thank you for playing, {player}!")print("Game Over")
Step 4: FlowchartPlease see the attached file for the flowchart.
To learn more about flowchart:
https://brainly.com/question/31697061
#SPJ11
5. Apart from the above sounds, colours and symbols,( high pitched sound- low pitched sound, red , green, amber, cross, ticks) describe three other ways that a user
interface could signal to a user that an action was successful or unsuccessful.
Successful
a.
b.
C.
Unsuccessful
a.
b.
C.
Answers
The three ways that a user interface could signal to a user that an action was successful or unsuccessful are as follows:
Text color.Image construction. Graphical representation. What do you mean by User interface?The user interface may be defined as the point of interaction between the human-computer and communication in a device. It can typically include display screens, keyboards, a mouse, and the appearance of a desktop.
According to the question, the user interface generally governs the way through which a user can typically interact with an application or a website. It is a type of space that effectively involves the connection or interaction between humans and other machines.
A user interface could signal to a user that an action was successful or unsuccessful. This must be dependent on several factors like text color, graphical representation, and image construction.
To learn more about the User interface, refer to the link:
https://brainly.com/question/17372400
#SPJ9
a national truck transportation services company, truckco, approached you to develop web app for their trucks. g
Answers
Developing a web app for TruckCo's trucks involves understanding requirements, designing UI, backend and frontend development, testing, deployment, and regular maintenance for a seamless and user-friendly experience.
Understanding the requirements: The first step in developing a web app for TruckCo's trucks is to clearly understand their requirements. This involves gathering information about the specific features and functionalities they need in the app, such as tracking and monitoring capabilities, inventory management, driver communication, and scheduling.
Designing the user interface: Once the requirements are clear, the next step is to design the user interface (UI) of the web app. The UI should be intuitive and user-friendly, allowing truck drivers and administrators to easily navigate and perform tasks. It should also be responsive and accessible, ensuring compatibility across different devices and screen sizes.
Backend development: After designing the UI, the focus shifts to backend development. This involves building the server-side components of the web app that handle data storage, retrieval, and processing. It may also involve integrating with external APIs or systems, such as GPS tracking or inventory management systems, to enhance the functionality of the app.
Frontend development: With the backend in place, the next step is to develop the frontend of the web app. This involves implementing the visual elements, user interactions, and client-side functionality using web technologies like HTML, CSS, and JavaScript. The frontend should communicate with the backend to retrieve and display relevant data to the users.
Testing and quality assurance: Throughout the development process, it is crucial to conduct thorough testing and quality assurance to ensure the web app functions as intended. This involves testing the app's usability, performance, security, and compatibility across different browsers and devices. Any issues or bugs identified should be fixed promptly.
Deployment and maintenance: Once the web app has been thoroughly tested and approved, it can be deployed to the production environment where it will be accessible to TruckCo's truck drivers and administrators. Regular maintenance and updates should be performed to address any issues, add new features, and ensure the app remains secure and up to date.
In summary, developing a web app for TruckCo's trucks involves understanding their requirements, designing the user interface, developing the backend and frontend components, testing the app, and finally deploying it to the production environment. Regular maintenance and updates are also necessary to keep the app running smoothly.
Learn more about Developing a web: brainly.com/question/22775095
#SPJ11
Cross peoples father chops just disappear with the advent of manufacturing today some manufacturing jobs are disappearing in favor of digital solutions what parallel can you draw between these two phenomena guns
Answers
Both the disappearance of manual labor jobs in manufacturing and the decline in the use of hand-chopped firewood can be seen as consequences of technological advancements and increased automation.
What is Automation?
Automation refers to the use of technology to perform tasks that would otherwise require human intervention. This can be achieved through the use of machines, software, or algorithms that are designed to perform specific tasks without the need for direct human involvement.
Automation has been widely adopted in industries such as manufacturing, transportation, and finance, as it allows for greater efficiency, speed, and cost savings. However, it can also result in job loss and the need for workers to acquire new skills to adapt to changing job markets.
To learn more about Automation, visit: https://brainly.com/question/28530316
#SPJ1
marcus white has just been promoted to a manager. to give him access to the files that he needs, you make his user account a member of the managers group, which has access to a special shared folder. later that afternoon, marcus tells you that he is still unable to access the files reserved for the managers group. what should you do? answer manually refresh group policy settings on his computer. have marcus log off and log back in. manually refresh group policy settings on the file server. add his user account to the acl for the shared folder.
Answers
manually update his computer's group policy settings. Refresh group policy settings manually on Marcus' PC to fix the issue. By doing this, he will make sure that his computer recognises the new group membership.
Marcus' PC needs to manually update group policy settings to resolve the problem. He will ensure that his computer recognises the new group membership by performing this. It's also a good idea to log out and back in again because doing so will update the group policy settings. It wouldn't be necessary to include his user account in the ACL for the shared folder if the managers group already has access to it. It would be fruitless to manually alter the file server's group policy settings either, as the problem seems to be with Marcus' PC's accurate recognition of his new group membership.
learn more about computer here:
https://brainly.com/question/30146762
#SPJ4
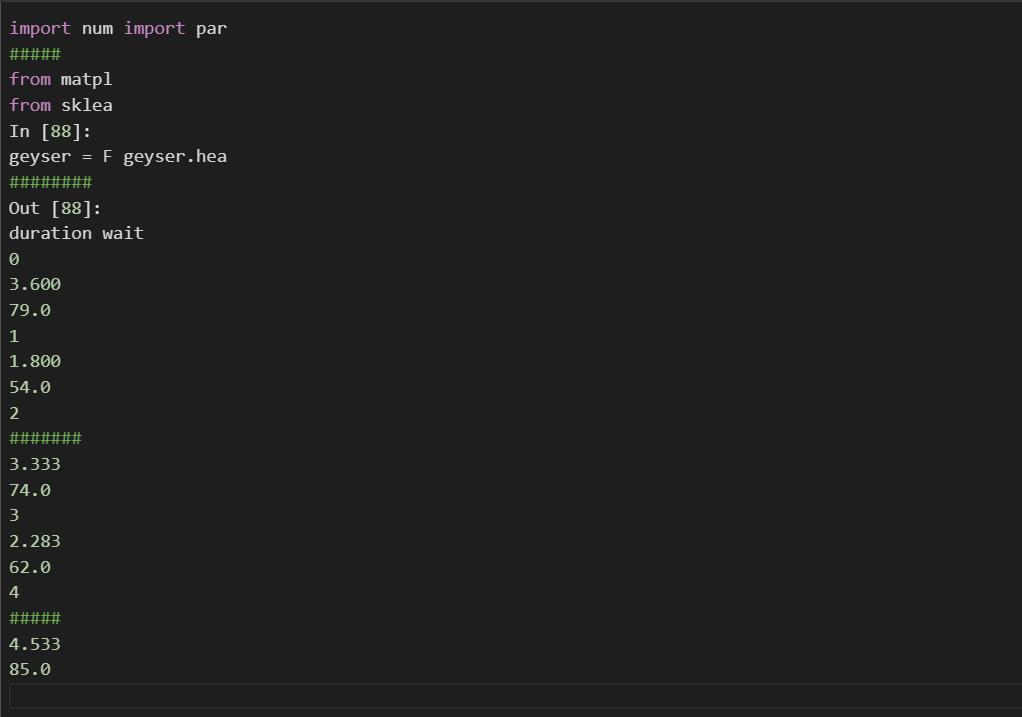
task-4: compute the eruption duration in standard units and append it as a new column named duration (standard units) to the dataframe geyser. also, compute the waiting times in standard units and append it as a new column named wait (standard units) to the dataframe geyser. after appending the 2 new columns successfully, print the first 5 rows of the dataframe geyser to the output.
Answers
Using the knowledge in computational language in C++ it is possible to write a code that compute the eruption duration in standard units and append it as a new column named duration.
Writting the code:import num import par
#####aa
from matpl
from sklea
In [88]:
geyser = F geyser.hea
########
Out [88]:
duration wait
0
3.600
79.0
1
1.800
54.0
2
#######
3.333
74.0
3
2.283
62.0
4
#####
4.533
85.0
What is matplotlib and example?Matplotlib is a cross-platform, data visualization and graphical plotting library for Python and its numerical extension NumPy. As such, it offers a viable open source alternative to MATLAB. Developers can also use matplotlib's APIs (Application Programming Interfaces) to embed plots in GUI applications.
See more about C++ at https://brainly.com/question/29632676
#SPJ1
Datawriter
Create a File object using "data.txt" as the argument to its constructor. Store the reference to the new File object in a variable of type File.
Will mark brainliest
Answers
Answer:
Explanation:
briefly describe how you would detect a sql injection in a network capture file (pcap).
Answers
Detecting SQL injection in a network capture file (pcap) involves analyzing the captured traffic for abnormal patterns that may indicate SQL injection attacks.
This can be done by examining the contents of the packets in the capture file to identify SQL statements that contain malicious code. To identify SQL injection attacks in a pcap file, one can use specialized tools like Wireshark or tcpdump to extract and filter SQL-related packets from the network traffic. The extracted packets can then be analyzed for any suspicious SQL syntax or commands that deviate from normal usage. Other techniques for detecting SQL injection attacks in a pcap file include comparing the SQL statements in the captured traffic to known attack patterns, monitoring the query response times, and identifying any unusual traffic patterns, such as multiple SQL queries being sent in rapid succession. Additionally, signature-based intrusion detection systems (IDS) can be used to automatically detect and alert network administrators of SQL injection attacks in real-time.
Learn more about SQL :
https://brainly.com/question/20264930
#SPJ4
Explain how Steve Jobs created and introduced the iPhone and iPad.
Answers
Answer:Today, we're introducing three revolutionary products. The first one is a widescreen iPod with touch controls. The second is a revolutionary mobile phone. And the third is a breakthrough Internet communications device. So, three things: a widescreen iPod with touch controls, a revolutionary mobile phone, and a breakthrough Internet communications device. An iPod, a phone, and an Internet communicator. An iPod, a phone...are you getting it? These are not three separate devices. This is one device. And we are calling it iPhone. Today, Apple is going to reinvent the phone.
Late last year, former Apple engineer Andy Grignon, who was in charge of the radios on the original iPhone, gave behind-the-scenes look at how Apple patched together demos for the introduction, with Steve Jobs showing off developmental devices full of buggy software and hardware issues. The iPhone team knew that everything had to go just right for the live iPhone demos to succeed, and they did, turning the smartphone industry on its head even as Apple continue to scramble to finish work on the iPhone.
Apple had actually been interested first in developing a tablet known as "Safari Pad", but as noted by a number of sources including Steve Jobs himself, the company shifted gears once it became clear how revolutionary the multi-touch interface developed for the tablet could be for a smartphone. Apple's tablet wouldn't surface until the launch of the iPad in 2010, three years after the introduction of the iPhone.
Seven years after the famous Macworld 2007 keynote, the iPhone has seen significant enhancements in every area, but the original iPhone remains recognizable as Apple has maintained the overall look of a sleek design with a larger touchscreen and a single round home button on the face of the device.
Explanation:
Sophia wants to purchase and use a mat board that will be the safest option for long-term use. What would likely be the BEST option for her?
A. Installation board
B. velveteen mat board
OC. acid-soaked board
OD. archival rag board
Answers
The most likely best option for Sophia is installation board is Installation board.
What can I use in place of a mat board?An alternative forms of matboard is Scrapbooking papers as it is made up of a wide range of options that one can be able to see at any craft store.
Therefore, the most likely best option for Sophia is installation board is Installation board. as it is the best option.
Learn more about board from
https://brainly.com/question/5016185
#SPJ1
Answer:
archival rag board
Explanation:
I just took it and this is the correct answer
Which of these criteria would be important to consider when choosing aprogramming language?1.The gameplay of the game.2.The color scheme of the game.3.Whether the game is aimed at themobile or web market.4.Whether the game is played on WiFior cellular data.
Answers
When choosing a programming language, some important criteria to consider are 3. whether the game is aimed at the mobile or web market and 4. whether the game is played on WiFi or cellular data.
Programming is a language that a computer can understand. Writing code, developing algorithms, and integrating software are all parts of programming. It's crucial to choose the best programming language for any specific project. There are numerous programming languages available, each with its own set of advantages and disadvantages. Some popular programming languages are Java, Python, and C++.Importance to consider when choosing a programming language.
There are several criteria to consider when selecting a programming language, some of which are listed below:
Project needs: It is critical to choose a language that suits the project's specific needs. Some languages are better suited for certain types of projects than others, such as data processing, web applications, or gaming. Support and community: when selecting a programming language, it's critical to consider the language's support and community. Developers should be able to get help from the language's documentation and forums. They may also seek help from fellow developers.Language popularity: Choosing a popular language may provide several advantages, such as community support, documentation, and tutorials. It's also worth noting that some languages have a more significant talent pool than others.
To sum up, the criteria that would be important to consider when choosing a programming language are 3. whether the game is aimed at the mobile or web market and 4. whether the game is played on WiFi or cellular data.
Know more about Programming language here:
https://brainly.com/question/28021308
#SPJ11
Jeremy has been asked by his manager to begin drafting a report on last year sales figures when he’s midway through the report a co-worker stops by and asks if Jeremy will help him with a problem she has on her project Jeremy also needs to respond to number of emails before the end of the day he is able to accomplish all these tasks which positive workplace behavior has he demonstrated
Answers
Answer:
Time management.
Explanation:
Answer:
Adaptability.
Explanation:
because he was being ASKED to do it if he wasn't asked and did it, it's initiative.
in order to create a namespace called student, you use a. namespace student { //code goes here } b. { namespace student //code goes here } c. student namespace { //code goes here } d. { student namespace //code goes here } (write the letter that corresponds to the correct code in the box)
Answers
The correct code to create a namespace called "student" is option A: namespace student { //code goes here }.
To create a namespace called "student" in C++, the correct syntax is to use the keyword namespace followed by the desired namespace name and a block of code enclosed in curly braces. Option A demonstrates the correct syntax:
namespace student {
// code goes here
}
This code snippet creates a namespace called "student" and allows you to define classes, functions, variables, or other entities within that namespace.
Options B, C, and D do not follow the correct syntax for creating a namespace. In option B, the placement of the opening and closing curly braces is incorrect. Option C places the keyword namespace after the namespace name, which is not valid. Option D also has the incorrect order of keywords and does not use the correct syntax for creating a namespace.
Learn more about namespace here;
https://brainly.com/question/32104357
#SPJ11
im going to find where u live and bring a doctor to give u a tetnus shot
Answers
Please dont find me
complete the fillcolor function which sets the image pointed to by data to the color represented by its color parameter. the image will have 4-bytes-per pixel in the form rgba.
Answers
The following code completes the fillcolor function:
void fillcolor(unsigned char* data, int width, int height, unsigned char color[4]) {
int i, j;
for (i = 0; i < height; i++) {
for (j = 0; j < width; j++) {
// Calculate the index of the current pixel
int index = (i * width + j) * 4;
// Set the RGBA values of the current pixel
data[index + 0] = color[0]; // Red
data[index + 1] = color[1]; // Green
data[index + 2] = color[2]; // Blue
data[index + 3] = color[3]; // Alpha
}
}
}
What is a fillcolor function?fillcolor(): This function assists in determining the color to use to fill the shape.
The fillcolor function in this code takes data as a pointer to the picture data, width and height as image dimensions, and color as an array encoding the RGBA color values.
Using nested loops, the method iterates over each pixel of the picture.
Learn more about codes at:
https://brainly.com/question/29330362
#SPJ4
I’ll give Brainly if u answer all please
ASAP

Answers
Answer:
Answers are: 38, 135, 23, 209, 53 & 181 respectively
Explanation:
Explain the expression below
volume = 3.14 * (radius ** 2) * height
Answers
Answer:
Explanation:
Cylinder base area:
A = π·R²
Cylinder volume:
V = π·R²·h
π = 3.14
R - Cylinder base radius
h - Cylinder height
Please help me as soon as you can

Answers
Answer:
(x > = 17)
Explanation:
Answer:
>
Explanation:
what is the first nmap command you ran in this lab? explain the switches used.
Answers
Answer:
The first Nmap command ran was nmap -O -v 10.20. 100.50.
Explanation:
The first Nmap command I ran was nmap -O -v 10.20. 100.50. The switches used are represented with -O AND –v this allows to detect the operating system used on 10.20. 100.50 and also shows the detail of open ports.
The initial nmap command in the lab was nmap -sP 192.168.1.0/24, using the -sP switch for a ping scan to check online hosts within the specified IP range.
We have,
The first nmap command used in this lab was: nmap -sP 192.168.1.0/24.
Explanation of switches:
-sP: This switch instructs nmap to perform a ping scan, sending ICMP echo requests to check which hosts are online without performing a full port scan.
192.168.1.0/24: This specifies the target IP range to scan, covering all IP addresses from 192.168.1.0 to 192.168.1.255 within the specified subnet.
Thus,
The initial nmap command in the lab was nmap -sP 192.168.1.0/24, using the -sP switch for a ping scan to check online hosts within the specified IP range.
Learn more about the use of the nmap tool here:
https://brainly.com/question/32144349
#SPJ3
A photograph is created by what
A) Silver
B) Shutters
C) Light
4) Mirror
Answers
A photograph is created by Light.
What are photographs made of?Any photograph created is one that is made up of Support and binders.
The steps that are needed in the creation of a photograph are:
First one need to expose or bring the film to light.Then develop or work on the imageLastly print the photograph.Hence, for a person to create a photograph, light is needed and as such, A photograph is created by Light.
Learn more about photograph from
https://brainly.com/question/25821700
#SPJ1
what are the three elements of protecting information
Answers
1. Confidentiality- preventing unauthorized access.
2. Integrity- maintaining accuracy and completeness.
3. Availability- ensuring access to authorized users.
Authorized users are individuals who have been granted permission to access a system, network, or application. This usually involves the assignment of a user ID and password, or another type of authentication. Authorized users are typically employees, contractors, partners, or customers of an organization, who have a legitimate need to access the system or application. Access is typically granted on a need-to-know basis, and users are typically monitored to ensure they are using the system or application appropriately.
To know more about Authorized users
https://brainly.com/question/13615355
#SPJ4
Next
Emerging Network Technology - Cloud Computing: Mastery Test
Type the correct answer in the box spell all words correctly
Which type of virtualization de storage area networks (ANS) typically use?
SANs typically use
virtualization
Reset
Next
Answers
Answer:
SANs typically use block-level virtualization. Block-level virtualization involves creating virtual copies of physical storage devices, such as hard drives or solid-state drives, and presenting them to the host computer as if they were physical devices. This allows for the creation of multiple virtual storage devices on a single physical storage device, enabling the host computer to access and manage the virtual devices as if they were separate physical devices. Block-level virtualization is commonly used in SANs because it allows for the creation of multiple virtual storage devices with different performance characteristics, such as different capacity or performance levels, that can be tailored to the specific needs of different applications or workloads.
Explanation:
how should a security analyst review system generated events for signs of intrusion or other problems on the network?
Answers
A software program called an intrusion detection system (IDS) automates the intrusion detection procedure. Software that combines all the features of an intrusion detection system with the ability to try to thwart potential events is known as an intrusion prevention system (IPS).
What security analyst review system generated events?Through the client-side injection of malicious scripts, XSS vulnerabilities give attackers the ability to manipulate user interactions with web applications, plan impersonations, and/or launch phishing campaigns.
Therefore, A network intrusion detection system (NIDS) is installed at one or more strategic locations so that it can keep track of all incoming and outgoing traffic between all networked devices.
Learn more about security here:
https://brainly.com/question/16354463
#SPJ1
open accomplishing your task I was able to
Answers
Answer:
WTH KINDA QUESTION IS THIS !
I DON'T UNDERSTAND DUDE