In a five-choice multiple-choice test, which letter is most often the correct
answer?
A. A
B. B
C. C
D. D
Answers
I believe the answer is C.
I think there was a study done on this a while back!
Related Questions
proper location/storage of device/system and materials give me rhe key information please
Answers
Answer:
Organize and label storage areas so parts and materials can be quickly located without searching. Store materials and supplies in an organized manner to ensure easy access for retrieval and transportation. Place heavier loads on lower or middle shelves. Store long, tall or top-heavy items on their side or secure them to
Explanation:
Write an algorithm to compute the mean value of all odd numbers between 1 to 500 inclusive
Answers
An algorithm to compute the mean value of all odd numbers between 1 to 500 inclusive is: sum = sum + i count = count + 1 mean = sum / count return mean
Here is an algorithm to compute the mean value of all odd numbers between 1 to 500 inclusive:
1. Initialize a variable called 'sum' to 0
2. Initialize a variable called 'count' to 0.
3. Loop through all the odd numbers from 1 to 500 inclusive.
4. For each odd number, add it to the 'sum' variable and increment the 'count' variable by 1.
5. After the loop, divide the 'sum' variable by the 'count' variable to get the mean value.
6. Return the mean value as the output.
Here's what the algorithm would look like in pseudocode:
sum = 0 count = 0 for i from 1 to 500 inclusive:
if i is odd:
sum = sum + i count = count + 1 mean = sum / count return mean
Learn more about algorithm at:
https://brainly.com/question/24216401
#SPJ11
Explain why it is wise to memorize your social security number.
Answers
It is memorize your social security number as one can be able to recur it for any given purpose if one did not carry it along with them.
Why memorize your social security number?The reason why it is important to memorize your social security number is that by doing so, one do not need to carry or use their card again.
Conclusively, Note that It is not the card but the number that is very important and as such it is vital that one knows their Social Security number that is the nine digits number off heart and in cases of emergencies when one forgot to carry their cards.
Learn more about social security number from
https://brainly.com/question/5213237
#SPJ4
write Motherboard Components?
Answers
Answer:
These are the parts of a mother board or at least mine for my pc
Hope this helped.
A brainliest is always appreciated.
Explanation:

1) What did you leam from reading The Life we Buyy? Be specific and give at least two examples. 2) What overall theme(s) or idea(s) sticks with you as a reader? Highlight or underline your answers CHO
Answers
Allen Eskens' novel, The Life We Bury, reveals numerous character secrets and demonstrates how honesty and truth always triumph.
The story centers on the characters Joe and Carl and how their shared secrets cause them to become close. Examples that illustrate the book's concept and lessons include those Carl's conviction will be overturned after his innocence has been established.
Joe receives the money since there was a financial incentive for solving the crimes, which he can use to take care of Jeremy and pay for Jeremy's education.
Learn more about the novel "The Life We Buy here:
https://brainly.com/question/28726002
#SPJ4
You have two Windows Server 2016 computers with the Hyper-V role installed. Both computers have two hard drives, one for the system volume and the other for data. One server, HyperVTest, is going to be used mainly for testing and what-if scenarios, and its data drive is 250 GB. You estimate that you might have 8 or 10 VMs configured on HyperVTest with two or three running at the same time. Each test VM has disk requirements ranging from about 30 GB to 50 GB. The other server, HyperVApp, runs in the data center with production VMs installed. Its data drive is 500 GB. You expect two VMs to run on HyperVApp, each needing about 150 GB to 200 GB of disk space. Both are expected to run fairly disk-intensive applications. Given this environment, describe how you would configure the virtual disks for the VMs on both servers.
Answers
The virtual disk configuration for the VMs on both servers in this environment is shown below.
In the Hyper V Test,
Since there will be two or three virtual machines running at once, each of which needs between 30 and 50 GB of the total 250 GB of disk space available,
What is virtual disks?Setting up 5 virtual disks, each 50 GB in size.
2 VMs each have a 50 GB virtual drive assigned to them.
The above setup was chosen because running three VMs with various virtual disks assigned to them will not pose an issue when two or three VMs are running concurrently and sharing the same virtual disk. This is because the applications are disk-intensive.
To learn more about virtual disks refer to:
https://brainly.com/question/28851994
#SPJ1
Given this environment, the virtual disk configuration for the VMs on both servers is shown below. Because two or three VMs will be running at the same time, and each VM has disk requirements ranging from 30 to 50 GB of total disk space of 250 GB.
What is Hyper V Test?While there are several methods for testing new virtual machine updates, Hyper-V allows desktop administrators to add multiple virtual machines to a single desktop and run tests. The Hyper-V virtualization technology is included in many versions of Windows 10. Hyper-V allows virtualized computer systems to run on top of a physical host. These virtualized systems can be used and managed in the same way that physical computer systems can, despite the fact that they exist in a virtualized and isolated environment. To monitor the utilization of a processor, memory, interface, physical disk, and other hardware, use Performance Monitor (perfmon) on a Hyper-V host and the appropriate counters. On Windows systems, the perfmon utility is widely used for performance troubleshooting.Therefore,
Configuration:
Creating 5 Virtual disks of 50 GB each.
1 virtual disk of 50 GB is assigned to 2 VM.
The above configuration is because since two or three VM will be running at the same time and using the same virtual disk will cause a problem since the applications are disk intensive, running three VMs with different virtual disks assigned to them, will not cause a problem.
For Hyper V App,
Two VM will run at the same time, and the disk requirement is 150 - 200 GB of 500 GB total disk space.
Configuration:
Creating 2 virtual disks of 200 GB each with dynamic Extension and assigning each one to a single VM will do the trick.
Since only two VMs are run here, the disk space can be separated.
To learn more about Hyper V Test, refer to:
https://brainly.com/question/14005847
#SPJ1
Which of the following represents the correct order in which you should install components into the case after disassembling a computer?a. power supply, drives, motherboard, cards
b. drives, motherboard, cards, power supply
c. cards, motherboard, power supply, drives
d. motherboard, drives, cards, power supply
Answers
The correct order to install components into the case after disassembling a computer is: "power supply, drives, motherboard, cards". Thus, Option A is correct.
This is because this order allows for proper cable management and avoids interference with other components during installation.
Starting with the power supply ensures proper cable management and allows for easy access to connect the power cables to the motherboard and other components, followed by the installation of drives to avoid any possible damage to the motherboard during installation.
The motherboard should be installed next, followed by any expansion cards, which should be installed last to avoid interference with other components. This order ensures that all components are properly installed and connected, reducing the risk of damage and ensuring proper functionality of the computer.
Learn more about disassembling a computer https://brainly.com/question/30561810
#SPJ11
what is grid computing? group of answer choices it is parallel computing where autonomous computers act together to perform very large tasks. it is distributed computing where autonomous computers perform independent tasks.
Answers
Parallel computing is when multiple autonomous computers work together to complete highly challenging tasks.
In order to complete exceedingly big jobs, a group of autonomous computers known as a "grid" work in simultaneously. Grid computing is a type of computing infrastructure that pools computer resources dispersed over numerous sites to accomplish a single objective. Multiple computers' unused resources are combined and made available for a single task. Grid computing is the use of interconnected computer systems to pool resources for collective use. Grid computing involves a single main computer that distributes data and tasks to a network of connected computers in order to achieve a common objective.
Learn more about interconnected here-
https://brainly.com/question/984908
#SPJ4
How are comments in a Java program treated by the compiler?
A) They are converted.
B) They are interpreted.
C) They are ignored.
D) They are coded.
Answers
Answer:
D) They are coded.
Explanation:
Java comments are notes in a Java code file that are ignored by the compiler and runtime engine. They are used to annotate the code in order to clarify its design and purpose. You can add an unlimited number of comments to a Java file, but there are some "best practices" to follow when using comments.
The answer is they are codee
A user receives an email containing a co-workers birth date and social security number. The email was not requested and it had not been encrypted when sent. What policy does the information in the email violate
Answers
Answer:
PII
Explanation:
The information in the email violates the PII. That is Personally identifiable information. PII, are nothing but any data that could potentially be used to identify a person. Examples of which can be a full name, Social Security number, driver's license number, bank account number, passport number, and email address, etc.
You receive a worksheet in which the rows are numbered 1, 2, 3, 5,6. This means that row 4 is _____.
Answers
People often hide cells of worksheet due to different reasons. This means that row 4 is hidden.
A worksheet is commonly know as a sheet of paper/computer sheet with which work is done or performed.
An individual can hide any worksheet so that it can be removed from their view. The data in hidden worksheets is not visible to the person, but it can still be referenced from other worksheets and workbooks. One can unhide hidden worksheets if need be.
Learn more from
https://brainly.com/question/17106092
Tell me everything that happened in the fortnight galactics event. WHO EVER HAS THE BEST EXPLANATION WILL GET BONUS POINTS AND WILL BE MARK BRAINLYNESS
Answers
Answer:
people still play fortnight?!?!
Explanation:
psn: Smallboy_life
1} What are ways in which computer programs can be improved for efficiency?
A) Avoiding recognizing patterns
B) Breaking a problem down into smaller steps and recognizing relevant patterns
C) Writing functions in programs in large chunks, rather than as independent parts
D) Writing functions that can only be used to solve one problem
2} Which of the following would be an optimal data structure for storing a text information?
A) Dictionary
B) Integer
C) List
D) String
3} What data type is best suited to store the length of a string?
A) Boolean
B) Integer
C) List
D) String
4} Which of the following are best commenting practices?
A) Identify all of the output statements.
B) State the obvious.
C) Use block comments for long comments.
D) Use triple quotes to comment.
Answers
Answer: 1. B) Breaking a problem down into smaller steps and recognizing relevant patterns
2. D) String
3. B) Integer
4. D) Use triple quotes to comment.
Explanation:
What is the keyboard shortcut for the Undo command?
Choose the answer.
CTRL+X
CTRL+Z
CTRL+U
CTRL+V
Answers
Answer:
CTRL+Z is Undo
Explanation:
CTRL+X: Cut
CTRL+Z: Undo
CTRL+U: Underline
CTRL+V: Paste
Implement maketree, setleft, and setright for right in-threaded binary trees using the sequential array representation.
Answers
Maketree, setleft, and setright functions can be implemented for right in-threaded binary trees using the sequential array representation. These functions allow the creation of the tree structure and setting the left and right pointers of the nodes efficiently.
In a right in-threaded binary tree, each node maintains a right-threaded pointer, which points to the next node in the inorder traversal if the right child is null. To implement maketree, we allocate a new node in the array and set its left and right pointers to null. For setleft and setright, we update the left and right pointers of a given node by assigning the indices of the desired child nodes in the array.
To set the left pointer, we simply assign the index of the left child node to the left pointer of the given node. To set the right pointer, we first check if the given node has a right child. If it does, we assign the index of the right child to the right pointer. If it doesn't, we update the right pointer to the index of the next node in the inorder traversal. By utilizing these functions, we can construct and manipulate right in-threaded binary trees efficiently using a sequential array representation.
Learn more about sequential array here: brainly.com/question/32296744
#SPJ11
What are some constraints you will run
into when designing your client's game?
Answers
When designing a client's game, several constraints can arise, including technical limitations, budget constraints, time restrictions, target platform limitations, and design considerations.
One of the primary constraints in game design is technical limitations. The game's performance may be affected by hardware specifications, such as processing power, memory, and graphics capabilities of the target platform. Designers must optimize the game's assets, features, and mechanics to ensure smooth gameplay within these limitations.
Budget constraints also play a crucial role. The client may have a limited budget allocated for game development, which can impact the scope and complexity of the project. Designers must find creative solutions and prioritize essential features to deliver a high-quality game within the allocated resources.
Time restrictions can be another significant constraint. Clients often have deadlines or specific release dates in mind. Designers need to manage their time effectively, ensuring that development milestones are met while maintaining the game's quality and addressing any unforeseen challenges that may arise during the process.
Target platform limitations must be considered as well. Different platforms, such as PC, consoles, or mobile devices, have their own technical specifications and user expectations. Designers need to adapt the game's design and mechanics to fit the capabilities and limitations of the chosen platform.
Lastly, design considerations also impose constraints. Clients may have specific design preferences, target demographics, or thematic requirements that need to be incorporated into the game. Designers must strike a balance between meeting the client's vision and creating an enjoyable and engaging experience for the players.
learn more about designing a client's game here:
https://brainly.com/question/32197598
#SPJ11
How do I send the face to the back? Seriously, I can't find out how...

Answers
Answer:
i think you can layer it :)
Explanation:
nice drawing btw!
Decimal numbers are based on __________.
letters (a and b)
16 digits
10 digits
two digits (1s and 0s)
Answers
I’m not sure.
Answer:
They are based on 10 digits.
Explanation:
I just did the test and got the answer right.
What is the value of the variable named result after this code is executed?
numA = 3
numB = 2
result = numA ** numB
An error occurred.
An error occurred.
ANSWER IS 9
Answers
Answer: result = 9
Explanation:
numA has an integer value of 3
numB has an integer value of 2
result is the value of numA ** numB (or 3 ** 2)
In python, "**" operator means "to the power of" and it is used to create exponents. So writing result mathematically would be the same as:
\(3^{2} \)
The value of 3 to the power of 2 is 9 because 3 x 3 is equal to 9.
advantages and disadvantages of technology and what is technology
Answers
Explanation:
technology is the application of scientific knowledge to make work easier and faster the disadvantage of technology is the making of atomic bombs . unemployment because there have been introduction of robots . the advantages of technology is improving health and transportation .
what happens in the winding house of a mine
Answers
Explanation:
A winding house is where the wind for the mine elevator is located, typically a steel rope operated by a steam engine
1
The tire pressure is 20% underinflated.
The service life is reduced by...
%
check
Answers
Answer
A constant 20 percent underinflated condition will reduce the life of a tire by 30 percent, and 40 percent underinflation will reduce tire life by 50 percent. Underinflation will increase flexing and heat buildup within the tire components which deteriorate tires and reduces casing life and retreadability.
guys tell the answer correctly
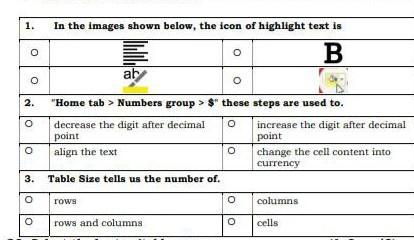
Answers
Answer:
1st ans: where u can see yellow colored line
2nd ans: currency one
3rd ans: cells
Explanation:
This action allows workflow items to automatically reroute to a selected Member based on the process ID and transaction type.
Answers
The action you're referring to is called "Automatic Routing." It enables workflow items to be efficiently rerouted to a designated member based on the process ID and transaction type, streamlining the workflow process and increasing overall productivity.
The action you are referring to is called "Dynamic Routing." This feature enables the system to automatically reroute workflow items to a specific member based on the process ID and transaction type. With Dynamic Routing, organizations can streamline their workflow processes and ensure that the right people are handling the appropriate tasks at the right time. This can help to improve efficiency and reduce errors in the workflow process.
The action you're referring to is called "Automatic Routing." It enables workflow items to be efficiently rerouted to a designated member based on the process ID and transaction type, streamlining the workflow process and increasing overall productivity.
To learn more about Automatic Routing, click here:
brainly.com/question/30846998
#SPJ11
How do I find where I have used Premium Feature in CANVA
I am a free user
Answers
Answer: Ok go to the website (Canva) and you will see they have plan like there is one that is free, and there is one that is name pro but you have to pay $12.95 and the last one is Enterprise which cost $30.00
Hope this help :)
Explanation:
look plz help :))))))))))))))))))))

Answers
Answer:
false
Explanation:the answer is false
What is the goal of destroying CUI?A. Make it unreadableB. Make it indecipherableC. Make it unrecoverableD. All of the above - Correct AnswerE. None of the above
Answers
The goal of destroying CUI is typically to make it unrecoverable, meaning that the information is permanently deleted or destroyed in a way that it cannot be reconstructed or retrieved.
What is CUI?
CUI stands for Controlled Unclassified Information, which refers to unclassified information that is sensitive and requires protection.
The goal of destroying CUI is typically to make it unrecoverable, meaning that the information is permanently deleted, destroyed in a way that it cannot be reconstructed or retrieved once deleted or destroyed.
This is usually done to prevent unauthorized access or disclosure of sensitive information. Therefore, the correct answer is C) Make it unrecoverable.
Controlled Unclassified Information (CUI) is unclassified information that requires safeguarding or dissemination controls and is governed by specific laws, regulations, and policies to protect it from unauthorized access or disclosure.
To know more about CUI, visit: https://brainly.com/question/29626718
#SPJ4
Bruce has set up his Git environment and finished working on his new GreenMass.sh script. What should he do next?
A. Add the script to the staging area.
B. Issue the git init command.
C. Commit the script to the local repository.
D. Issue the git log command.
E. Commit the script to the remote repository.
Answers
Bruce should add the script to the staging area using the "git add" command, and then commit the script to the local repository using the "git commit" command. If he wants to share his changes with others, he can also push the changes to a remote repository using the "git push" command. Therefore, the correct answer is A and C.
Assuming that Bruce has already initialized a Git repository in the directory where he has been working on his GreenMass.sh script, the next step for him would be to add the script to the staging area using the git add command. This command will prepare the changes made to the GreenMass.sh script for the next commit.
After adding the script to the staging area, Bruce can then commit the changes to the local repository using the git commit command. This will create a new commit object that contains the changes made to the GreenMass.sh script along with a commit message that describes the changes.
Once the changes have been committed to the local repository, Bruce can optionally view the commit history using the git log command. This command will display a list of commits along with their commit messages, author information, timestamps, and other metadata.
Finally, if Bruce wants to share his changes with others, he can push the commits to a remote repository using the git push command. This will upload the commits to a remote Git server, making them available for others to pull and merge into their own local repositories.
Learn more about GreenMass.sh script here:
https://brainly.com/question/15047823
#SPJ11
Bruce has already initialized a Git repository for his project, the next step would be to add the GreenMass.sh script to the staging area using the "git add" command. A
The script to the staging area, Bruce should commit the changes to the local repository using the "git commit" command with a meaningful commit message.
If he wants to see the commit history, he can use the "git log" command.
However, issuing the "git init" command (option B) is not necessary as Bruce has already set up his Git environment and initialized a repository. Similarly, committing to the remote repository (option E) would come after committing to the local repository and setting up the remote repository with the "git remote" command.
The "git add" command to add the GreenMass.sh script to the staging area, supposing Bruce has previously set up a Git repository for his project.
Bruce needs to use the "git commit" command to add the script to the staging area and then commit the modifications to the local repository with a clear commit note.
He may use the "git log" command to view the commit history.
Bruce has already built up his Git environment and initialised a repository, thus using the "git init" command (option B) is not required.
For similar questions on Script
https://brainly.com/question/26165623
#SPJ11
describe a recursive algorithm for finding the maximum element in an array a of n elements. what is your running time and space usage?
Answers
A recursive approach to finding the maximum element in the array is given below:
Approach: Get the array for which the maximum is to be foundRecursively find the maximum according to the following: Recursively traverse the array from the endBase case: If the remaining array is of length 1, return the only present element i.e.
arr[0]
if(n == 1)
return arr[0];
The Program Implementation// Recursive C++ program to find maximum
#include <iostream>
using namespace std;
// function to return maximum element using recursion
int findMaxRec(int A[], int n)
{
// if n = 0 means whole array has been traversed
if (n == 1)
return A[0];
return max(A[n-1], findMaxRec(A, n-1));
}
// driver code to test above function
int main()
{
int A[] = {1, 4, 45, 6, -50, 10, 2};
int n = sizeof(A)/sizeof(A[0]);
cout << findMaxRec(A, n);
return 0;
}
Read more about recursive algorithms here:
https://brainly.com/question/489759
#SPJ1
What is the result of the following program? print(“10 + 2”) print(3 + 5) 12 8 10 + 2 3 + 5 12 3 + 5 10 + 2 8
Answers
Answer:
print(“10 + 2”) Will output "10 + 2" without the quotation marks. This is because the text to print is encapsulated in quotation marks, indicating a "string literal." This means, to put it simply, it will always print what you put there even if it's a math equation.