If you need speeds of 16 Mbps between two corporate sites in the United States, you would need a ________ leased line. T1 T3 OC3 None of these
Answers
Answer:
T3.
Explanation:
A T3 is an acronym for Transmission system 3 and it is also known as Digital Signal Level 3 (DS3). T3 is a point-to-point physical circuit connection which is capable of transmitting up to 44.736Mbps.
This simply means that, when using a Transmission system 3 (T3), it is very much possible or easier to transmit data such as video and audio at the rate of 44.736Mbps.
Please note, Mbps represents megabit per seconds and it is a unit for the measurement of data transmission rate. The Transmission system 3 is an internet connection that has up to 672 circuit channels having 64Kbs.
Also, worthy of note is the fact that a T3 line is made up of twenty-eight (28) Transmission system 1 lines (T1) each having a data transfer rate of 1.544Mbps.
Additionally, Transmission 3 lines are symmetrical and duplex and thus, has equal upload and download speeds. Therefore, transmissions can be done on T3 lines simultaneously without the data lines being clogged or jammed.
If you need speeds of 16 Mbps between two corporate sites in the United States, you would need a T3 leased line.
Generally, the T3 lines are mostly used for multichannel applications and uninterrupted high bandwidth consumptions such as Telemedicine, internet telephony, video conferencing, e-commerce etc.
Related Questions
which type of ethernet framing is used for TCP IP and DEC net
Answers
Trust me u will get it right
Define a constructor as indicated. Sample output for below program:Year: 0, VIN: -1Year: 2009, VIN: 444555666// ===== Code from file CarRecord.java =====public class CarRecord {private int yearMade;private int vehicleIdNum;public void setYearMade(int originalYear) {yearMade = originalYear;return;}public void setVehicleIdNum(int vehIdNum) {vehicleIdNum = vehIdNum;return;}public void print() {System.out.println("Year: " + yearMade + ", VIN: " + vehicleIdNum);return;}// FIXME: Write constructor, initialize year to 0, vehicle ID num to -1./* Your solution goes here */}// ===== end ===== //===== Code from file CallCarRecord.java =====public class CallCarRecord {public static void main (String args) {CarRecord familyCar = new CarRecord();familyCar.print();familyCar.setYearMade(2009);familyCar.setVehicleIdNum(444555666);familyCar.print();return;}}// ===== end =====
Answers
Answer:
public CarRecord(){
yearMade = 0;
vehicleIdNum = -1;
}
Explanation:
A constructor is used to initialize an object instantly. It does not have a return type and has the same name as class.
Create a constructor and set the year as 0 and vehicleIdNum as -1.
This constructor is the default constructor, initializes the default values for the variables, for this class.
A constructor is a block of code that is called and executed each time an object is created.
The constructor in Java is as follows:
public CarRecord(){
yearMade = 0;
vehicleIdNum = -1;
}
A constructor would have the same name as the class.
The class of the program is CarRecord; so the constructor name is CarRecord()
From the question, variables year and vehicles ID are to be initialized to 0 and -1 respectively.
So, the variable initialization is:
yearMade = 0;
vehicleIdNum = -1;
Hence, the complete code segment is:
public CarRecord(){
yearMade = 0; vehicleIdNum = -1;
}
Read more about constructors at:
https://brainly.com/question/14608885
You have been asked to write a loop that outputs values in a database column ranging between 10 and 100. Any number that is not divisible by 5, and any value that is not an integer, should be ignored. When the value in the loop hits 95, break the loop prematurely. One of your team members has advised the use of break, continue, and pass statements.
Answers
Explanation:
This is going to depend on the language you're working in heavily.
First you will want to verify your number is an integer rather than a floating point which will completely depend on the language and whether you care if the floating point is 1.0 for example, which could still be converted a valid integer value.
After you've determined if it is an integer you can use modulo to check if the integer is evenly divisible by 5. In C-like languages you would write this as `x % 5`. Any result other than zero would mean it is not evenly divisible.
You also need to check if the integer is >= 10 and <= 100.
Read up on for/while loops and break/continue in those loops to understand that concept, it is pretty universal to all languages.
Good luck!
With ____, applications are delivered to users via web browsers; with ___, subscribers get tools and services that enable them to quickly deploy custom applications; with ___, subscribers gain access to software and hardware for deploying applications.
Answers
We have that the complete statement is
With __SaaA__, applications are delivered to users via web browsers; with _PaaS__, subscribers get tools and services that enable them to quickly deploy custom applications; with _IaaS__, subscribers gain access to software and hardware for deploying applications.
Option C
Computer Applications & The InternetGenerally For handing over services by internet browser, we use Software as a Service, usually, provider issuer offers utility through browser. This choice itself will remove different options.
Hence, Infrastructural service is therefore required
SaaS;PaaS;IaaS
Option C
For more information on Computer visit
https://brainly.com/question/950632
Complete Question
Complete Question is attached below

When writing technical information to a non-technical audience, you discover that the information appears to be geared more toward an expert audience. Which of the following strategies can help to adapt the writing to meet the needs of your audience?
Answers
When adapting technical information for a non-technical audience, several strategies can be employed to ensure clarity and understanding:
The StrategiesSimplify language: Replace technical jargon and acronyms with plain language that is easily understood by the general audience.
Define terms: If technical terms are necessary, provide clear definitions or explanations to help readers comprehend their meaning.
Use analogies: Relate complex concepts to familiar everyday situations or objects, making it easier for non-experts to grasp the ideas.
Break down complex ideas: Divide complex information into smaller, more manageable sections, and provide step-by-step explanations or examples.
Visual aids: Utilize visuals such as diagrams, charts, or infographics to supplement the text and enhance understanding.
Provide context: Frame technical information within a broader context to help readers understand its relevance and importance.
Test for comprehension: Seek feedback from non-technical individuals to gauge their understanding and make necessary revisions.
By implementing these strategies, you can effectively bridge the gap between technical content and a non-technical audience, facilitating comprehension and engagement.
Read more about technical information here:
https://brainly.com/question/7788080
#SPJ1
What is used for risk response control?
Answers
Answer:
Risk response control uses methods such as mitigate, avoidance, shift, actively accept, and passively accept.
Explanation:
Risk Response Control refers to the procedure of evaluating residual risks, detecting new risks, guaranteeing the execution of risk plans, and assessing the success of the plans in decreasing risk is known as risk response control. Whereby the risk response control techniques include acceptance, avoidance, transfer, and mitigation
1. What is a sprite?
O A sprite is a graphical representation of an object
A sprite is a function
A sprite is a game
A sprite is a string
Answers
Answer:
A
Explanation:
A sprite is a character or object that moves in a video game. For example, in Mario, Mario is the sprite because he is a character and can move.
TRUE/FALSE. spy cells, or spying base stations, are also called international mobile subscriber identity (imsi) catchers because they capture the unique imsi number from a mobile device.
Answers
An IMSI-catcher, also known as an international mobile subscriber identity-catcher, is a telephone listening device used to eavesdrop on phone conversations and track the whereabouts of mobile phone users.
What spy cells, or spying base stations?Launching Man in the Middle Attacks using IMSI Catchers is one of the most common ways attackers break into cellular devices.
These tools, also known as Stingrays, are capable of carrying out a variety of nefarious tasks like data collection, identity theft, and real-time position tracking.
Therefore, it is false that spy cells, or spying base stations, are also called international mobile subscriber identity.
Learn more about spying stations here:
https://brainly.com/question/25212136?
#SPJ1
put the pieces of a function into the correct order as if you were writing a formula.
ANSWER: = function arguments
Answers
The correct order for the pieces of a function is:
=function argumentsWhat is a function?In Computer programming, a function can be defined as a named portion of a block of executable code that performs a specific task, which is usually a single, related action.
This ultimately implies that, a function comprises a group of related statements (block of code) that only runs and returns a data when it is called.
In conclusion, =NOW() is an example of the correct order for the pieces of a function.
Read more on a function here: https://brainly.com/question/19181382
- A blacksmith is shoeing a miser's horse. The blacksmith charges ten dollars for his work. The miser refuses to pay. "Very well", says the blacksmith, "there are eight nails in each horseshoe. The horse has four shoes. There are 32 nails in all. I will ask you to pay one penny for the first nail, two pennies for the next nail, four pennies for the next nail, eight pennies for the next nail, sixteen pennies for the next, etc. until the 32nd nail". How much does the miser have to pay?
Answers
Answer:
1+ 2^31= 2,146,483,649 pennies.
in Dollars- $21,464,836.49
edit for total=
42, 929,672. 97
Explanation:
,
Write a complete Java program that prompts the user to input two integer values and outputs the largest and smallest numbers. The program includes JOptionPane for both the input and output statements.
Answers
Using the knowledge in computational language in JAVA it is possible to write a code that complete Java program that prompts the user to input two integer values and outputs the largest and smallest numbers.
Writting the code:import javax.swing.JOptionPane;
public class Main
{
public static void main(String[] args) {
String firstNumber = JOptionPane.showInputDialog("Enter first integer");
String secondNumber = JOptionPane.showInputDialog("Enter second integer");
int number1 = Integer.parseInt(firstNumber);
int number2 = Integer.parseInt(secondNumber);
int largestNumber = Math.max(number1, number2);
int smallestNumber = Math.min(number1, number2);
JOptionPane.showMessageDialog(null, "Largest Number is: " + largestNumber + "\nSmallest Number is :" + smallestNumber);
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

Using a K-Map, simplify the sum of the minterms.

Answers
Karnaugh Map or K-Map is a pictorial method used to simplify Boolean algebra expressions and produce a minimized version of a given truth table and the simplified expression is D(B+AC)+D(AC+C) + BD.
Karnaugh Map or K-Map is a grid-like representation of truth tables that enables the user to identify patterns that correspond to logical operations of the Boolean variables.
K-Maps are useful tools for simplifying Boolean expressions.
They provide a graphical method of representing a Boolean function's truth table that simplifies the process of reducing the function using Boolean algebra.
The following steps are used to simplify the sum of the minterms using K-Map:
Construct the K-Map. In this case, since the function is a sum of minterms, we are given that the output is high whenever A=0, B=1, C=0, D=0, A=1, B=1, C=0, D=0, A=0, B=1, C=1, D=0, A=1, B=1, C=1, D=0, A=1, B=0,C=1, D=1, and A=0, B=1, C=1, D=1.
These are the cells with 1 in the map.
Group the adjacent cells containing 1s in groups of 2, 4, or 8.
Convert the groupings into Boolean expressions.
Simplify the expressions by using Boolean algebra.
The K-Map for the given sum of minterms, the two groups can be converted into Boolean expressions as follows:
Group 1: BD+ACD+ABCD
Group 2: AC+BD+BCD
Simplify the Boolean expressions by using Boolean algebra.
Group 1: BD + ACD + ABCD = D (B+AC+ABC)
= D(B+AC)
Group 2: AC + BD + BCD = D(AC+B+C) + BD = D(AC+B+C+B)
= D(AC+C)
The simplified expression is D(B+AC)+D(AC+C) + BD.
For more questions on Karnaugh Map:
https://brainly.com/question/27873494
#SPJ8
Which topic would be included within the discipline of information systems
Answers
, , , , , are only a few of the subjects covered within the study area of information systems. Business functional areas like business productivity tools, application programming and implementation, e-commerce, digital media production, data mining, and decision support are just a few examples of how information management addresses practical and theoretical issues related to gathering and analyzing information.
Telecommunications technology is the subject of communication and networking. Information systems is a branch of computer science that integrates the fields of economics and computer science to investigate various business models and the accompanying algorithmic methods for developing IT systems.
Refer this link to know more- https://brainly.com/question/11768396
problem description IT
Answers
In IT, a problem description refers to a clear and concise explanation of an issue or challenge that needs to be resolved within a technology system or application.
How is this so?It involves providing relevant details about the symptoms, impact, and context of the problem.
A well-written problem description outlines the specific errors, failures, or undesired behavior observed and provides enough information for IT professionals to analyze and identify potential solutions.
A comprehensive problem description is crucial for effective troubleshooting and problem-solving in the IT field.
Learn more about Problem Description at:
https://brainly.com/question/25923602
#SPJ1
Do you trust machine learning application?
Answers
Answer:
Trusting a machine learning model, in general, can be interpreted as creating a robust model which gives largely accurate results and has a high generalization ability. Classification models learn from past experience, so the robustness of a model primarily depends on the given training set
Explanation:
Hope it helps
Please mark as brainliest
A broadband connection is defined as one that has speeds less than 256,000 bps.
Question 25 options:
True
False
Answers
Answer:
A typical broadband connection offers an Internet speed of 50 megabits per second (Mbps), or 50 million bps.
Explanation:
I think I got it right, plz tell me if im wrong
How can we work together to fix problems with our websites?
Answers
i think this is or what hihi
Explanation:
The value proposition, or mission statement, tells the visitor what you do and why you do it.
Put your value proposition on your home page, in your headline if possible. Add it to your blog or about page. Let the visitors know exactly what they will be getting if they hire you, buy your product, subscribe to your newsletter or read your blog.
Assume that a signal is encoded using 12 bits. Assume that many of the encodings turn out to be either 000000000000, 000000000001, or 111111111111. We thus decide to create compressed encodings by representing 000000000000 as 00, 000000000001 as 01, and 111111111111 as 10. 11 means that an uncompressed encoding follows. Using this encoding scheme, if we decompress the following encoded stream:
00 00 01 10 11 010101010101
Required:
What will the decompressed stream look like?
Answers
Answer:
The following is the answer to this question:
Explanation:
In the binary digit
\(000000000000\) is equal to 0 bit
\(000000000001\) is equal to 1 bit
\(1 1 1 1 1 1 1 1 1 1 1 1\) is equal to 10
Similarly,
\(000000000010\)=11
Thus,
\(00 \ 00 \ 01 \ 10\ 010101010101\) is equal to
\(000000000000\), \(000000000000\), \(000000000001\) ,
\(000000000010\), \(1 1 1 1 1 1 1 1 1 1 1 1\) , \(000000000001\) , \(000000000001\) , \(000000000001\) ,
\(000000000001\) , \(000000000001\) , \(000000000001\)
Fundamental of nanotechnology and nanoscience
Answers
Nanoscience, which deals with the manipulation of materials at the atomic and molecular scales, is a synthesis of physics, materials science, and biology.
What is nanotechnology?Nanotechnology is the process of modifying matter at a size close to the atomic level to create novel structures, materials, and gadgets.
The technique offers advances in science across a wide range of industries, including manufacturing, consumer goods, energy, and medical.
Nanoscience is a combination of physics, materials science, and biology that deals with the manipulation of materials at the atomic and molecular scales.
Nanotechnology is the study and application of how to observe, measure, control, assemble, and manufacture materials at the nanoscale.
Thus, this is fundamental of nanotechnology and nanoscience.
For more details regarding nanotechnology, visit:
https://brainly.com/question/23463634
#SPJ9
When creating a user generated function, what procedure is followed?
a) create a function prototype before main()
b) create a function definition after main()
c) create a function definition before main()
d) all of the above
Answers
When creating a user-generated function, what procedure is followed d) all of the above.
What are the three factors of user-described characteristic?
A user-described characteristic has 3 essential additives which might be characteristic declarations, characteristic definition and characteristic called.
The characteristic prototypes are used to inform the compiler approximately the variety of arguments and approximately the specified datatypes of a characteristic parameter, it additionally tells approximately the go-back kind of the characteristic. By this information, the compiler cross-assessments the characteristic signatures earlier than calling.
Read more about the prototype :
https://brainly.com/question/7509258
#SPJ1
The keyboard shortcut to enter the current date in a field is
Ctrl+semicolon (;)
Ctrl+ampersand (&)
Ctrl+asterisk (*)
Spacebar
Answers
Answer:
oh cool I'm gonna try that
What is the most important quality of lossless compression?
Answers
Answer:
Text
Explanation:
When a file is being compressed from it original form to a compressed form, it's important that the text retains its unique form or at the very least, it should be similar to its original form
This is so because a little drop in quality can cause distortion to the text and thereby changing its meaning or making it unreadable.
The most important quality of lossless compression is that there is no data loss.
Lossless compression is the use of data compression algorithms or techniques to compress an original data to a compressed data with no data loss in the compression process.
Hence, the contents of the compressed data is identical to the original data, therefore the original data to can be reconstructed from the compressed data.
We can conclude that there should be no loss of data during lossless compression.
You can find more on data compression at: https://brainly.com/question/19878993
What is the arithmetic mean of the following numbers?
10.6.4.4.6.4.1
Answers
Answer:
5
Explanation:
Sum= 10+6+4+4+6+4+1=35
Total nos=7
Mean= sum/total nos.
=35/7= 5
10 + 6 + 4 + 4+ 6 + 4+ 1 /7 = 28.2
During the projects for this course, you have demonstrated to the Tetra Shillings accounting firm how to use Microsoft Intune to deploy and manage Windows 10 devices. Like most other organizations Tetra Shillings is forced to make remote working accommodations for employees working remotely due to the COVID 19 pandemic. This has forced the company to adopt a bring your own device policy (BYOD) that allows employees to use their own personal phones and devices to access privileged company information and applications. The CIO is now concerned about the security risks that this policy may pose to the company.
The CIO of Tetra Shillings has provided the following information about the current BYOD environment:
Devices include phones, laptops, tablets, and PCs.
Operating systems: iOS, Windows, Android
Based what you have learned about Microsoft Intune discuss how you would use Intune to manage and secure these devices. Your answer should include the following items:
Device enrollment options
Compliance Policy
Endpoint Security
Application Management
Answers
I would utilise Intune to enrol devices, enforce compliance regulations, secure endpoints, and manage applications to manage and secure BYOD.
Which version of Windows 10 is more user-friendly and intended primarily for users at home and in small offices?The foundation package created for the average user who primarily uses Windows at home is called Windows 10 Home. It is the standard edition of the operating system. This edition includes all the essential tools geared towards the general consumer market, including Cortana, Outlook, OneNote, and Microsoft Edge.
Is there employee monitoring in Microsoft Teams?Microsoft Teams helps firms keep track of their employees. You can keep tabs on nearly anything your staff members do with Teams, including text conversations, recorded calls, zoom meetings, and other capabilities.
To know more about BYOD visit:
https://brainly.com/question/20343970
#SPJ1
Help please!, explain what is missing and what needs to be changed if anything.
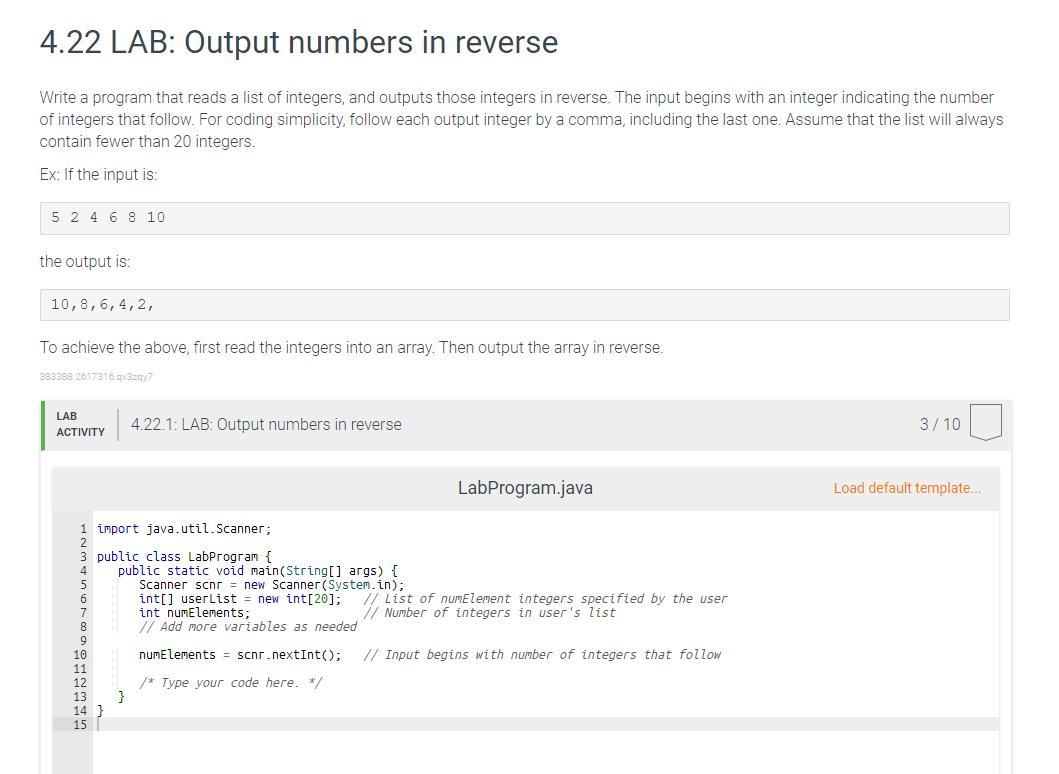
Answers
Using the computer language in JAVA to write a function code that output numbers in reverse
Writting the code in JAVA:import java.util.Scanner;
public class LabProgram {
public static void main(String[] args) {
Scanner scnr = new Scanner(System.in);
int[] userList = new int[20];
int numElements;
numElements = scnr.nextInt();
for (int i = 0; i < numElements; ++i) {
userList[i] = scnr.nextInt();
}
for (int i = numElements - 1; i >= 0; --i) {
System.out.print(userList[i] + " ");
}
System.out.println();
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1


3
Type the correct answer in the box. Spell all words correctly.
Graphic designers can compress files in different formats. One of the formats ensures that the quality and details of the image are not lost when the
graphic designer saves the file. Which file format is this?
file format ensures that images don't lose their quality and details when graphic designers save them.
The
te rocarvad.
Reset
Next
ents-delivery/ua/la/launch/48569421/ /aHR0cHM6Ly9mMi5hcHAUZWRIZW50aWQuY2911 2xlYXlZXdhch
Answers
The PNG file format ensures that images don’t lose their quality and details when graphic designers save them.
Why is the PNG format preserve image quality?PNG files employ a compression technique that preserves all image data, and as a result, can reduce file size without compromising image quality. This is called lossless compression.
Therefore, based on the above, PNG has gained widespread popularity because it enables one to save graphics with transparent backgrounds, precise contours, and other intricate elements that require preservation.
Read more about graphic design here:
https://brainly.com/question/28807685
#SPJ1
see full text below
Type the correct answer in the box. Spell all words correctly.
Graphic designers can compress files in different formats. One of the formats ensures that the quality and details of the image are not lost when the graphic designer saves the file. Which file format is this?
The PNG (Portable Network Graphics) format is the ideal file type for graphic designers to save their images, as it guarantees optimal retention of both quality and detail.
What is the PNG format?The Portable Network Graphics (PNG) file format is extensively utilized in the field of digital imaging and graphic design. The notable feature of this technique is its ability to compress images without sacrificing their accuracy and intricacy. It achieves this through lossless compression, ensuring that all information is preserved in its original format.
By using the PNG file format, graphic designers can compress images in a manner that shrinks file size while maintaining top-notch image quality. Lossless compression is the term used for this compression technique, as it preserves all of the image's original data.
In contrast to JPEG, which utilizes a lossy compression method and can lead to a decrease in the quality of an image, PNG maintains the original form of the image and allows for its replication with no decline in visual accuracy. PNG format is ideal for preserving images that demand intricate details and precision, such as designs, artworks, and visuals characterized by sharp lines or see-through backgrounds.
Read more about PNG format here:
https://brainly.com/question/18435390
#SPJ1
..............is a piece of hardware used to provide data and instructions to a computer used for interaction and control. *
Output device.
Processing.
input device.
All of above.
Answers
Answer:
output
Explanation:
it can be seen and touched
Can someone help me with the following logical circuit, perform two actions. FIRST, convert the circuit into a logical
statement. SECOND, create a truth table based on the circuit/statement. (20 pts. each for statement and
truth table.

Answers
Creation of Truth Table Based on the logical statement, we can create a truth table as shown below:
A B (not A) (not A) and B (not A) and B or A A or (not A) and B 0 0 1 0 1 0 0 1 0 0 1 0 1 1 0 1 1 0 1 1 1 0 1 1 0 1 1 0 1 1 1
The first two columns show the input values, the next column shows the output of the NOT gate, then the output of the AND gate, then the output of the OR gate and finally the output of the logical statement.
We can observe that the output of the logical statement is the same as the output of the OR gate.
Given the logical circuit, we are required to perform two actions on it. Firstly, convert the circuit into a logical statement. Secondly, create a truth table based on the circuit/statement. Let's understand how to do these actions one by one:Conversion of Circuit into Logical Statement.
The given circuit contains three components: NOT gate, AND gate and OR gate. Let's analyze the working of this circuit. The two input variables A and B are first passed through the NOT gate, which gives the opposite of the input signal.
Then the NOT gate output is passed through the AND gate along with the input variable B. The output of the AND gate is then passed through the OR gate along with the input variable A.We can create a logical statement based on this working as: (not A) and B or A. This can also be represented as A or (not A) and B. Either of these statements is correct and can be used to construct the truth table.
Creation of Truth Table Based on the logical statement, we can create a truth table as shown below:
A B (not A) (not A) and B (not A) and B or A A or (not A) and B 0 0 1 0 1 0 0 1 0 0 1 0 1 1 0 1 1 0 1 1 1 0 1 1 0 1 1 0 1 1 1
In the truth table, we have all possible combinations of input variables A and B and their corresponding outputs for each component of the circuit.
The first two columns show the input values, the next column shows the output of the NOT gate, then the output of the AND gate, then the output of the OR gate and finally the output of the logical statement.
We can observe that the output of the logical statement is the same as the output of the OR gate.
For more such questions on Truth Table, click on:
https://brainly.com/question/13425324
#SPJ8
Reynold is writing a news story about the government handling a health epidemic. He reads a report from a different news organization to use as a reference. His deadline for the story is coming up soon, so Reynold heavily paraphrases parts from the other organization's report to help him write. While Reynold's story also includes some of the same quotes as the other report, he forgets to attribute the sources at the end. Reynold says that since no one can copyright the facts of world news, he is not plagiarizing.
a) What unethical or illegal actions has Reynold taken in writing his news article? (3 points)
b) What kind of consequences might result from Reynold's actions? (2 points)
Answers
Answer:
1. He was plagiarizing
2. He might get sued, bad reputation, and he might get fired.
Explanation:
If he Paraphrasing from something online and doesn't cite the website he is plagiarizing.
what product and service type should I choose in quickbooks online if I do not want to track inventory
Answers
Answer:
is that what you're looking for
In QuickBooks Online, it’s easy to track how much you make and spend on each product or service. You can also enter these products and services you sell as items so you can quickly add them to sales forms. This gives you more detailed financial reports and helps you complete transactions faster.
Here's how to add services and products you don't plan to track inventory for (also known as non-inventory items).
Note: If you want to track product quantities, add them as inventory items instead.
Answer:
Non-inventory: Products or items you buy or sell, but don't need to track quantities. For example, nuts and bolts you use for installation jobs but don't sell directly.