hich of the following could be a constructor for the public class MyClass? public int MyClass() public MyClass() public MyClass(int a, int b)
Answers
The constructor for the public class MyClass could be "public MyClass(int a, int b)". This constructor takes two integer parameters and is commonly used to initialize the object of the MyClass class with specific values for the variables 'a' and 'b'.
In object-oriented programming, a constructor is a special method that is called when an object of a class is created. It is responsible for initializing the object's state and preparing it for use. Constructors typically have the same name as the class they belong to and can have different parameter lists.
The constructor "public MyClass(int a, int b)" allows the creation of MyClass objects with custom values for 'a' and 'b'. It enables the caller to pass specific integers to initialize the object's internal state. This constructor can be useful when different instances of MyClass need to have different initial values or when the object requires specific parameters for proper initialization.
On the other hand, the constructors "public int MyClass()" and "public MyClass()" do not follow the standard constructor syntax. Constructors do not have a return type, including void or int. Therefore, these two options would not be valid constructors for the public class MyClass.
To learn more about object-oriented programming, click here:
brainly.com/question/31741790
#SPJ11
Related Questions
Identify and label the parts fo the audio mixer (use the provided list as a guide).
____________. Audio Input Knob Potentiometers
____________. Audio Input Slider Potentiometers
____________. Audio Mixer
____________. Main Output Control
____________. Sub-master Controls
____________. VU Meter

Answers
Input jacks. Audio Input Knob Potentiometers. Microphone preamplifiers. Audio Input Slider Potentiometers.
What is audio mixer?Audio mixer is defined as a device that accepts, combines, processes, and monitors audio as its primary function. Mixers are used for live sound reinforcement, streaming, and broadcast. They allow you to "mix" many sound sources together.
Equalization. Audio Mixer. Dynamics processing. Main Output Control. Routing, Sub-master Controls. Level-control faders. VU Meter are the parts of audio mixer.
Thus, the parts of audio mixer are as given.
To learn more about audio mixer, refer to the link below:
https://brainly.com/question/14299038
#SPJ1
You have just finished installing an updated kernel on your email server that has been patched to solve a security vulnerability and wish to reboot as soon as possible. This is a busy time of day, and you do not want the server down any longer than necessary. Which option prevents fsck from running after the reboot and allows the system to boot faster?
Answers
In order to prevent fsck from running after the reboot and allow the system to boot faster, the `tune2fs` command can be used.
The `fsck` command is a file system checking tool that can be used to check the integrity of a file system, as well as to repair inconsistencies that are discovered.What is tune2fs?The `tune2fs` command is a Linux command that can be used to change the file system parameters of the `ext2`, `ext3`, or `ext4` file system.
This can include changing parameters such as the size of the file system journal, the maximum number of mounts before the file system is checked, and so on.
Now, to prevent `fsck` from running after the reboot and allow the system to boot faster, execute the following command:`tune2fs -c 0 -i 0 /dev/sda1`Where:`-c` stands for "maximum mount count."
Set to 0 to disable check on a specified number of mounts `-i` stands for "time interval."
Set to 0 to disable time-based checking. `/dev/sda1` stands for the block device that corresponds to the root partition.
To know more about `fsck` command, visit https://brainly.com/question/32137810
#SPJ11
Explain how the Fourier transform can be used to remove image noise.
Answers
The Fourier transform can be used to remove image noise by isolating the noise in the frequency domain and filtering it out. The Fourier transform allows us to analyze an image in the frequency domain by decomposing it into its component frequencies. Image noise appears as high-frequency components in the image.
By applying a low-pass filter in the frequency domain, we can remove the high-frequency noise components and preserve the low-frequency components that make up the image. Once the filtering is complete, the inverse Fourier transform is applied to convert the image back to the spatial domain. This results in an image that has been effectively denoised. The Fourier transform can be used to remove image noise by transforming the image from the spatial domain to the frequency domain, filtering out high-frequency noise, and then transforming the filtered image back to the spatial domain.
Step 1: Convert the image to the frequency domain using the Fourier transform. This process decomposes the image into its frequency components, representing various spatial frequencies present in the image. Step 2: Apply a low-pass filter to the transformed image. This filter removes high-frequency components, which are typically associated with noise, while retaining low-frequency components that represent the essential features of the image. Step 3: Convert the filtered image back to the spatial domain using the inverse Fourier transform. This step restores the image to its original form, but with the high-frequency noise components removed. By following these steps, the Fourier transform can effectively be used to remove image noise and improve image quality.
To know more about domain visit :
https://brainly.com/question/30133157
#SPJ11
You have been managing a $5 million portfolio that has a beta of 1.45 and a required rate of return of 10.975%. The current risk-free rate is 3%. Assume that you receive another $500,000. If you invest the money in a stock with a beta of 1.75, what will be the required return on your $5.5 million portfolio? Do not round intermediate calculations.
Round your answer to two decimal places.
%
Answers
The required return on the $5.5 million portfolio would be 12.18%.
1. To calculate the required return on the $5.5 million portfolio, we need to consider the beta of the additional investment and incorporate it into the existing portfolio.
2. The beta of a stock measures its sensitivity to market movements. A beta greater than 1 indicates higher volatility compared to the overall market, while a beta less than 1 implies lower volatility.
Given that the initial portfolio has a beta of 1.45 and a required rate of return of 10.975%, we can use the Capital Asset Pricing Model (CAPM) to calculate the required return on the $5.5 million portfolio. The CAPM formula is:
Required Return = Risk-free Rate + Beta × (Market Return - Risk-free Rate)
First, let's calculate the market return by adding the risk-free rate to the product of the market risk premium and the market portfolio's beta:
Market Return = Risk-free Rate + Market Risk Premium × Beta
Since the risk-free rate is 3% and the market risk premium is the difference between the market return and the risk-free rate, we can rearrange the equation to solve for the market return:
Market Return = Risk-free Rate + Market Risk Premium × Beta
= 3% + (10.975% - 3%) × 1.45
= 3% + 7.975% × 1.45
= 3% + 11.56175%
= 14.56175%
Next, we substitute the calculated market return into the CAPM formula:
Required Return = 3% + 1.75 × (14.56175% - 3%)
= 3% + 1.75 × 11.56175%
= 3% + 20.229%
= 23.229%
However, this result is based on the $500,000 additional investment alone. To find the required return on the $5.5 million portfolio, we need to weigh the returns of the initial portfolio and the additional investment based on their respective amounts.
3. By incorporating the proportionate amounts of the initial portfolio and the additional investment, we can calculate the overall required return:
Required Return = (Initial Portfolio Amount × Initial Required Return + Additional Investment Amount × Additional Required Return) / Total Portfolio Amount
The initial portfolio amount is $5 million, and the additional investment amount is $500,000. The initial required return is 10.975%, and the additional required return is 23.229%. Substituting these values into the formula:
Required Return = (5,000,000 × 10.975% + 500,000 × 23.229%) / 5,500,000
= (548,750 + 116,145.45) / 5,500,000
= 664,895.45 / 5,500,000
≈ 0.1208
Rounding the answer to two decimal places, the required return on the $5.5 million portfolio is approximately 12.18%.
Learn more about portfolio
brainly.com/question/17165367
#SPJ11
A ______ device makes it possible for multiple computers to exchange instructions, data, and information.
Answers
A communications device makes it possible for multiple computers to exchange instructions, data, and information.
We can define a communication device as a kind of hardware device that makes it possible to transmit information between multiple computers.
Data, information, and instructions are passed from a sending system to a receiving system through communication devices. A communication device can exchange information with other kinds of electronic devices.
An example of a communication device is a modem. A modem is a hardware device that can change digital information from a computer to a signal that can be transmitted over the telephone. The modem also has the capability to transfer an analog system into a digital system so that it can be viewed on a computer.
To learn more about communication devices, click here:
https://brainly.com/question/14891213
#SPJ4
In 1843 Ada Lovelace wrote an algorithm for a machine she is considered to be the worlds first programmer.
True
False
Answers
Ada Lovelace is widely considered to be the world's first computer programmer. In 1843, she wrote an algorithm for Charles Babbage's Analytical Engine, a proposed mechanical general-purpose computer. Lovelace's algorithm is considered to be the first computer program, as it was intended to be processed by a machine and could perform a series of complex mathematical calculations. Lovelace also recognized the potential for computers to go beyond number-crunching and be used for creative endeavors, such as generating music or graphics. Her contributions to computer science and her foresight into the potential of computing have earned her a place in history as a pioneer in the field.
The correct answer is True
Which of the following is the main challenge in acquiring an image of a Mac system? (Choose all that apply.) a. Most commercial software doesn’t support Mac. b. Vendor training is needed. c. Macs are incompatible with most write-blockers. d. You need special tools to remove drives from a Mac system or open its case.
Answers
options are: b and d. is the main challenge in acquiring an image of a Mac system. b. Vendor training is needed, d. You need special tools to remove drives from a Mac system or open its case.
The main challenge in acquiring an image of a Mac system is the need for special tools to remove drives from a Mac system or open its case, which makes it difficult for non-experts to acquire data from these systems. Additionally, vendor training may be necessary to understand the nuances of acquiring data from Mac systems.
While there may be some commercial software that does not support Mac, there are also many specialized tools available for Mac forensics. Macs are not necessarily incompatible with most write-blockers, although some write-blockers may not be compatible with certain Mac models.
To know more about Mac , click here:
https://brainly.com/question/31083179
#SPJ11
Write a function create_password() expects two parameters: pet_name (a string) and fav_number (an integer). The function returns a new password generated using the following pattern:
Answers
Answer:
Explanation:a
Which of the following are true statements about the Java wrapper classes (Select all that apply.): Select one or more: a. Objects of these type are immutable b. Objects of these types are mutable c. The wrapper classes do not have no-arg constructors d. The wrapper classes do have no-arg constructors
Answers
Answer:
a. Objects of these type are immutable.
Explanation:
Java wrapper classes are used to convert data into objects. The primitive data is not object and it does not belong to any class. Therefore Java wrapper classes help the user to convert primitive data into object. These objects are immutable and they have no arg constructor.
Computers were originally developed to accomplish various tasks in relative isolation, very different from the collaboration and communication we see today.
A.
True
B.
False
Answers
given a 12-bit adc with vfs=3.3v, what is the equivalent analog voltage given an digital code of 583?
Answers
Equivalent analog voltage refers to a voltage that represents a continuous analog signal in a digital system. The analog voltage is sampled at discrete intervals, and the resulting values are quantized and converted to digital form for processing. The equivalent analog voltage represents the original analog signal and is used for further processing or output.
To find the equivalent analog voltage for a 12-bit ADC with Vfs=3.3V and a digital code of 583, we need to first determine the resolution of the ADC. The resolution is calculated as Vfs/2^12, which gives us 0.000805664V per step.
Next, we multiply the resolution by the digital code to get the analog voltage. So, the equivalent analog voltage for a digital code of 583 is 0.000805664V x 583 = 0.469V.
follow these steps:
1. Identify the ADC resolution: For a 12-bit ADC, there are 2^12 (4096) distinct codes.
2. Determine the voltage step size: Divide the full-scale voltage (VFS) by the number of codes. In this case, it's 3.3V / 4096 = 0.000805V (or 0.805mV) per code.
3. Calculate the equivalent analog voltage: Multiply the digital code (583) by the voltage step size (0.000805V). This gives 583 x 0.000805V = 0.469415V.
So, the equivalent analog voltage for a digital code of 583 in a 12-bit ADC with VFS = 3.3V is approximately 0.469V.
To know more about Equivalent analog voltage visit:
https://brainly.com/question/29358436
#SPJ11
A file with the extension .doc usually indicates that the file contains a note written by a doctor.
a. True
b. False
Answers
The statement "A file with the extension .doc usually indicates that the file contains a note written by a doctor" is false.
The file extension .doc typically indicates that the file is in the Microsoft Word document format. It is commonly used for various types of documents, including text documents, reports, letters, and other written content. The .doc extension does not specifically imply that the file contains a note written by a doctor.
File extensions are used to indicate the format or type of a file, allowing computer systems and software to recognize and handle the file appropriately. In the case of .doc, it is associated with Microsoft Word and is used for general-purpose document files, not limited to any specific content or authorship.
Therefore, it is important to note that the extension of a file, such as .doc, does not provide any specific information about the content or author of the file. The content of a file can vary widely, and the extension is merely a designation of the file format rather than its actual content or source.
Learn more about extension here :
https://brainly.com/question/32421418
#SPJ11
Give a recursive solution to the following problem. State the requirements for a recursive solution, and justify that your solution satisfies each requirement. Input: int[] nums Output: The sum of the values, i.e., nuns [0] + nums [1] + nums [2] + ...
Answers
The recursive solution to the following problem. State the requirements for a recursive solution, and justify that your solution satisfies each requirement.
Recursion is a procedure that can be repeated over and over. When a process refers to itself, it is known as recursion. Recursion is typically used to resolve issues that may be broken down into simpler or similar subproblems.
For a recursive solution, there are a few criteria that must be met: Stopping criterion – There must be some point at which the recursion ends. The criteria for stopping determine when to halt the recursion. Development towards the end – The procedure must move toward the stopping criterion.
In order to obtain a recursive solution for the problem of adding up values, you may start with the following code:```int sum(int[] nums, int index, int n){if(index == n) return 0; else return nums[index] + sum(nums, index + 1, n);} ```In this code, the sum() function accepts an array, a starting index, and the number of elements in the array. If the starting index is equal to the array's length, 0 is returned; otherwise, the value at the current index is added to the recursive call sum(nums, index + 1, n) of the sum function.
The result is the sum of all of the values in the array. If there is no issue, this recursive solution satisfies the criteria for recursive solutions, which are a stopping criterion and development towards the end.
To know more about recursive solutions here:
brainly.com/question/32069961
#SPJ11
How to include quotation marks in a string javascript.
Answers
Explanation:
Try ' " and the beginning and " ' at the end.
What are some real-life situations where multi-dimensional arrays might be useful?
Answers
If you think, there are many game application where you can use a Multi-dimensional array. If we talk about a game then chess is the first game where rows and columns are used. The Second is the tic-tac-toe game and other board games are there too.
Which of the following is not one of the most common operating systems for personal computers
Answers
Answer:
Linux.
Explanation:
Linux isn't very common at all compared to Windows or even MacOS.
The profile picture that you plan to use to market your professional brand on social media networks should feature you only.
True
False
Answers
Answer:
false
Explanation:
T/F. the components in an array object may refer to other array objects. the number of bracket pairs used in the declaration of the reference variable indicates the depth of array nesting (in the sense that array elements can refer to other array objects).
Answers
TRUE statement that An array object's components may make references to other array nesting.
How can an array be nested in JavaScript?Utilizing the technique A new array is created by concatenating all sub arrays recursively up to the depth you choose using the Array. Array. flat() method. Simply explained, flat() will assist you in joining all entries together into a single array if you have an array of arrays (perhaps more arrays within them).
I need to retrieve a nested array.A nested array's elements can be accessed in what way You must first access an element of the outer array that yields an inner array in order to access an element of the multidimensional array, and then use another square bracket to access the element of the inner array.
To know more about array nesting visit:-
https://brainly.com/question/8151971
#SPJ4
Anyone help me on this ?

Answers
Answer:
The first one is Mobile Marketing Second Box is social media and the last is Search engine
Explanation:
a. Why are the data known as raw facts? Explain.
Answers
Answer:
The word raw means that the facts have not yet been processed to get their exact meaning. Data is collected from different sources. ... The result of data processing is Information.
Answer:
The Raw Facts and Figures are Called Data.
The word raw means that the facts have not yet been processed to get their exact meaning. Data is collected from different sources. It is collected for different purposes. ... The process of sorting or calculating data is called Data Processing
Hope you got it
If you have any question just ask me
If you think this is the best answer please mark me as branliest
How does a parity check work?
A.checking whether the number of 1s in a byte is odd or even and whether it is like the original
B/.checking the exact number of 1s in a byte against the original
C.checking whether the total number of digits in the byte is odd or even and whether it is like the original
D.checking the exact number of digits in the byte
In which of the following situations will an ARQ be returned?
A.a frame is not received
B.a frame is received
C.an error in the link causes the frame to not be received
D.a frame is received with errors and thus rejected
Answers
The simple explanation of how a parity check works is:
A. Checking whether the number of 1s in a byte is odd or even and whether it is like the originalThe situation which will return an ARQ is:
D. A frame is received with errors and thus rejectedWhat is a Parity Check?This refers to the authentication process whereby there is a check to see if the data being transmitted is accurate and is the same with the original for security purposes.
This process has to do with the number of 1s in a byte whether odd or even and if they are the same after transmission from the nodes.
With this in mind, we can see that when a packet is missing, then it is a ARQ system and this is an acronym that means Automatic Repeat Request and occurs when a frame is received with errors and thus rejected.
Read more about parity check here:
https://brainly.com/question/185730
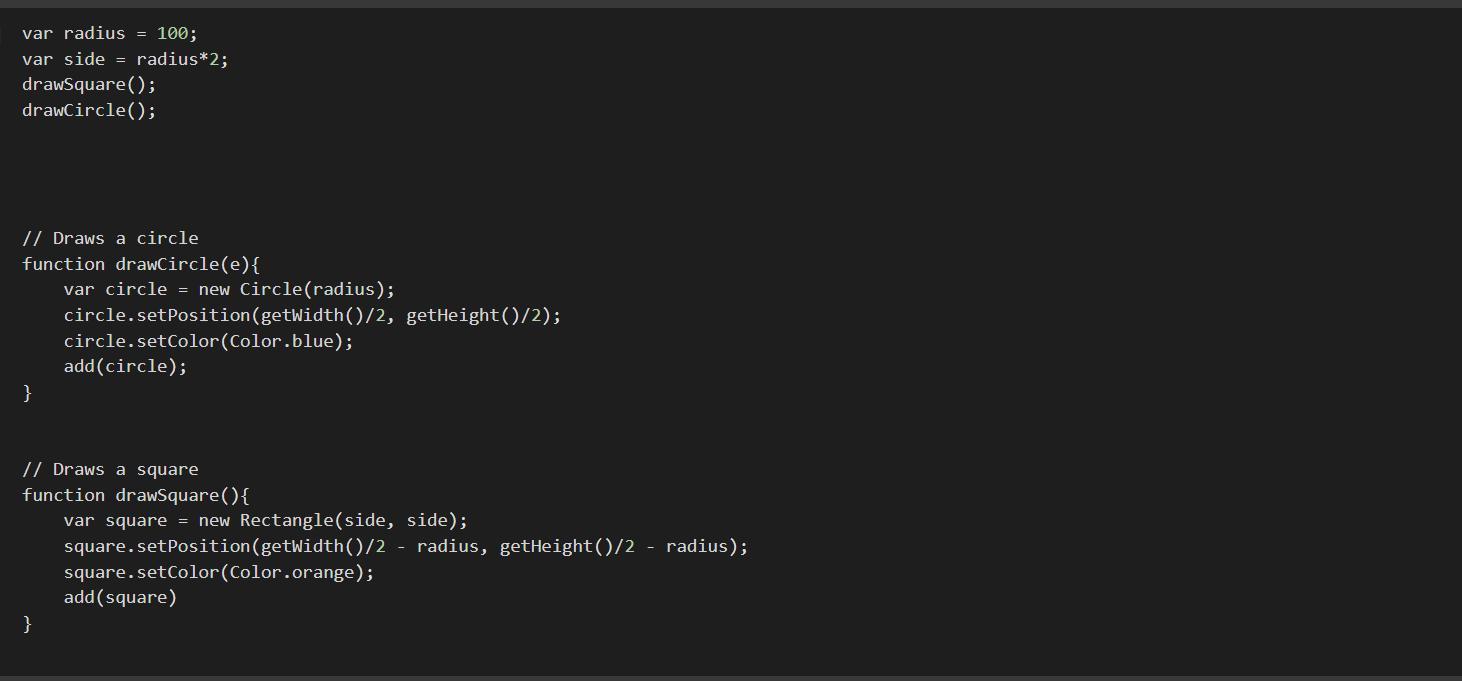
6.1.3 Circles in Squares Code HS JavaScript
Repeatedly draw a circle inside of a square and then a square inside that circle and so on. You should repeat this while the size is greater than MIN_SIZE. Each time you draw a shape, it should be centered on the screen and a new random color. You’ll need to update the size based on the size of the previous one.
Hint: The radius of a circle inside a square is half the side length of the square. The side length of a square inside a circle is 2 * radius divided by the square root of 2. You can use Math.sqrt(2) to take the square root.
Be careful not to get into an infinite loop in this program. It may be helpful to solve it with a for loop first to make sure you’re doing it right before attempting using a while loop.
Answers
Using the knowledge in computational language in JAVA it is possible to write a code that repeatedly draw a circle inside of a square and then a square inside that circle and so on.
Writting the code:var radius = 100;
var side = radius*2;
drawSquare();
drawCircle();
// Draws a circle
function drawCircle(e){
var circle = new Circle(radius);
circle.setPosition(getWidth()/2, getHeight()/2);
circle.setColor(Color.blue);
add(circle);
}
// Draws a square
function drawSquare(){
var square = new Rectangle(side, side);
square.setPosition(getWidth()/2 - radius, getHeight()/2 - radius);
square.setColor(Color.orange);
add(square)
}
Can arrays copyOf () be used to make a true copy of an array?There are multiple ways to copy elements from one array in Java, like you can manually copy elements by using a loop, create a clone of the array, use Arrays. copyOf() method or System. arrayCopy() to start copying elements from one array to another in Java.
See more about JAVA at brainly.com/question/18502436
#SPJ1
what are the three most important ideas of marine ecosystems
Answers
The three that is most important ideas of marine ecosystems are
BiodiversityFood websHuman impactsWhat is the marine ecosystems about?Biodiversity: Marine ecosystems are home to a wide range of species, from tiny plankton to massive whales, and the diversity of life in these ecosystems plays a critical role in maintaining their overall health and stability.
Food webs: Marine ecosystems are interconnected through a complex web of relationships, with different species serving as predators, prey, or decomposers. Understanding these food webs is essential for understanding how marine ecosystems function and how they are affected by human activities.
Lastly, Human impacts: Human activities such as overfishing, pollution, and climate change have significant impacts on marine ecosystems, and it is essential to understand and address these impacts in order to protect and preserve these vital systems for future generations.
Learn more about marine ecosystems from
https://brainly.com/question/1788473
#SPJ1
design a program for hunterville college. the current tuition is $20,000 per year, and tuition is expected to increase by 3 percent each year. display the tuition each year for the next 10 years. b. modify the hunterville college program so that the user enters the rate of tuition increase instead of having it fixed at 3 percent. c. modify the hunterville college program so that the user enters the rate of tuition increase for the first year. the rate then increases by 0.5 percent each subsequent year.
Answers
Here's the design of the program for Hunterville College, considering all the requested modifications:
Option a: Fixed 3% increase each year
tuition = 20000
for year in range(1, 11):
tuition = tuition + (tuition * 0.03)
print(f"Year {year}: ${tuition:.2f}")
Option b: User-entered rate of tuition increase
tuition = 20000
rate = float(input("Enter the rate of tuition increase (%): "))
for year in range(1, 11):
tuition = tuition + (tuition * (rate / 100))
print(f"Year {year}: ${tuition:.2f}")
Option c: Rate of tuition increase increases by 0.5% each subsequent year
tuition = 20000
rate = float(input("Enter the rate of tuition increase for the first year (%): "))
for year in range(1, 11):
tuition = tuition + (tuition * (rate / 100))
rate += 0.5
print(f"Year {year}: ${tuition:.2f}")
In all three options, the program initializes the tuition to $20,000. It then calculates the tuition for each subsequent year based on the provided rate of increase. The tuition for each year is displayed using formatted output to show the year and the corresponding tuition amount.
Option b allows the user to input the rate of tuition increase, while option c introduces an increasing rate by 0.5% each year after the initial rate entered by the user.
Learn more about program here
https://brainly.com/question/23275071
#SPJ11
state two features of a word processor
Answers
Answer:
Some of the functions of word processing software include:
Creating, editing, saving and printing documents.
Copying, pasting, moving and deleting text within a document.
Formatting text, such as font type, bolding, underlining or italicizing.
Creating and editing tables.
Hope it will help you! !!!!!!!
How do you identify quality resources on the Internet? There are 4 correct answers. Select each answer.
Question 3 options:
Check the information for accuracy by looking for references or searching for the same information with another source.
Determine if the information seems to balance pros and cons. If it's difficult to tell the difference between facts and opinions, the website may not be research based.
Determine who wrote the information. Anyone can post to the internet.
Find out when the information was published or edited last. The facts could be out of date.
When you conduct an Internet search, observe where the website is in the list of search results. The websites listed first are the most reliable resources.
Answers
Answer:
Every option except option E.) is true. I hope this helps! :)
For windows xp, 2000, and nt servers and workstations, raid 0 or ____ is available.
Answers
For windows XP, 2000, and NT servers and workstations, raid 0 or 1 is available.
What is NT in network?NT's technology is known to be a type of tech that is said to be the base for any form of Microsoft successor operating system, that is Windows 2000.
Note that Windows NT which is "New Technology," is known to be made up of two products: Microsoft NT Workstation as well as Microsoft NT Server.
Therefore, For windows XP, 2000, and NT servers and workstations, raid 0 or 1 is available.
Learn more about servers from
https://brainly.com/question/15498455
#SPJ1
a data model is the diagrammatic representation of a database that clearly defines a database’s
Answers
A data model is the diagrammatic representation of a database that clearly defines a database’s Entities, Attributes,& relationships
What is a data model ?A data model is an all-encompassing framework that presents a graphical portrayal of a database system. It assumes the form of a diagrammatic representation meticulously outlining the core elements of the database, namely entities, attributes, and relationships, with unparalleled clarity and precision.
Entities, the vital constituents of the data model, embody distinct real-world objects or concepts of significance, such as customers, products, or orders. Rendered as rectangles or boxes in the diagram, each entity possesses its own unique collection of attributes, which capture the intrinsic qualities and descriptors associated with the respective entity.
Find out more on data models at https://brainly.com/question/28964142
#SPJ4
Which of the following steps must be performed first to round the decimal 0.135 to the hundredths place?
Answers
First, keep in mind that 0.135 is divided into two pieces. The fractional component to the right of the decimal point and the integer part to the left of the decimal point:
Part of an integer: 0
135th fractional part
To round 0.135 to the closest hundredth is to round the numbers such that the fractional element has just two digits. Recall that you can only round a number if it is up to 5. Hence, the hundredth place of the above decimal will be 1.4.
What is a decimal?The decimal numeral system is the most widely used system for representing both integer and non-integer values. It is the Hindu-Arabic numeral system's expansion to non-integer numbers. Decimal notation is the method of representing numbers in the decimal system.
To convert a number from integer to percent, multiply it by 100 and then add a percent sign%. To convert a decimal to a percentage, multiply the decimal number by 100 and add %. To convert from decimal to percent, shift the decimal point two positions to the right and then add a percent sign.
Learn more about decimals:
https://brainly.com/question/1827193
#SPJ1
what is remote assistance?
Answers
Answer:
Quick Assist, Windows 10 feature, allows a user to view or control a remote Windows computer over a network or the Internet to resolve issues without directly touching the unit. It is based on the Remote Desktop Protocol.
Explanation:
.....