Heroku Industries has a SQL Servr database thaat provides data to clients throughout its network. It has now asked George, a network engineer, to sort an issue with the administration branch where the Windows firewall does not allow access to the users to such databases. Analyze what port should George open up in the firewall so that the issue is resolved.
Answers
George should open up port 1433 in the Windows firewall to allow access to the SQL Server database.
Port 1433 is the default port for SQL Server communication. By opening up this port in the Windows firewall, George will enable network traffic to pass through and reach the SQL Server database.
This port is specifically reserved for the default instance of SQL Server. If the database is using a named instance, a different port may be assigned, and George would need to open that specific port instead.
Opening port 1433 in the Windows firewall will allow clients throughout the network to establish connections and retrieve data from the SQL Server database.
However, it's important to note that opening a port in the firewall can introduce security risks, so proper access control measures should be in place to ensure that only authorized users can access the database. Additionally, it's recommended to consult with the organization's security policies and guidelines before making any changes to the firewall configuration.
To learn more about database click here
brainly.com/question/3520803
#SPJ11
Related Questions
Any Suggestions on what to do here? I already restarted my PC twice, cleared my browsing data, and rebooted the wifi network....

Answers
Answer:
if u r at school, then it might be blocked.
if not, get a vpn proxy.
Which of the following types of traffic is not exchange by Remote Desktop clients and servers using the Remote Desktop Protocol (RDP)?a. Keystrokesb. Mouse movementsc. Display informationd. Application data
Answers
The types of traffic that are not exchange by using Remote Desktop Protocol (RDP) is d. Application data.
Remote Desktop Protocol (RDP) is a proprietary protocol developed by Microsoft to provide a graphical interface for remote access to another computer over a network connection. When a user connects to a remote desktop using RDP, they can interact with the remote computer as if they were physically present at that computer.
RDP exchanges various types of traffic between the client and server, including keystrokes, mouse movements, and display information. Keystrokes and mouse movements allow the user to interact with the remote desktop environment, while display information is used to send visual data from the remote desktop to the client computer.
Learn more about Remote Desktop Protocol here:
brainly.com/question/28903876
#SPJ11
Some one help pls will mark brainless !!!!!
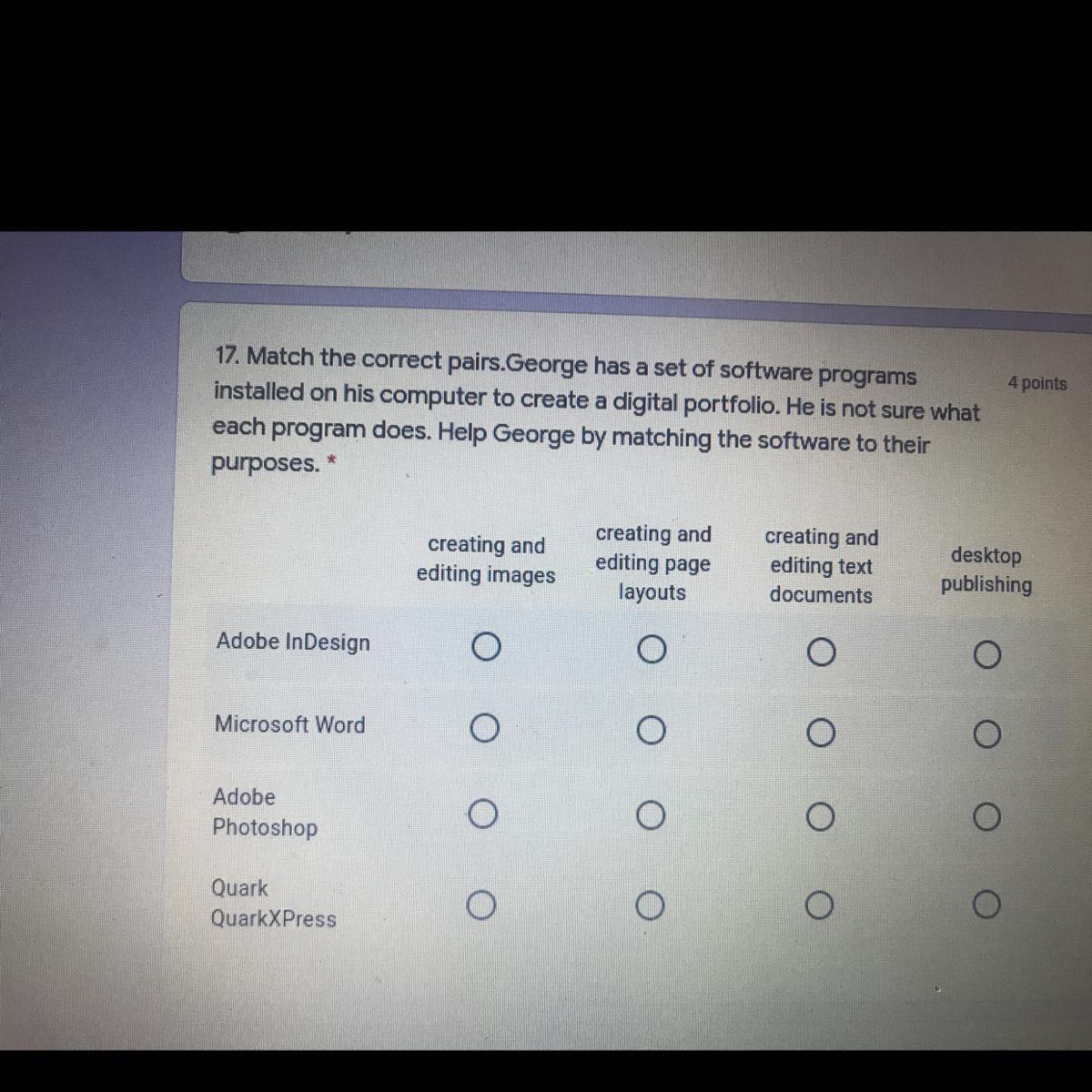
Answers
microsoft word- creating and editing word documents
adobe indesign- layouts
qaurk- publishing
Why is it so important to have a checking account?
Answers
Answer: Having a checking account sets you up for financial success. Get access to your money quicker, complete financial transactions on your phone or tablet, rest assured that your money is protected, and easily track your spending so you can make better money choices.
Explanation: Hopefully this helps you. (pls don't report if wrong)
A LAN is usually confined in a single building.
True
False
Answers
Answer:
true
Hope it helps.you
Drag the tiles to the correct boxes to complete the pairs.
Match the testing tools to their use.
Selenium
JMeter
load testing tool
functional testing tool
test management tool
defect-tracking tool
QTP
web browser automation tool
Quality Center
Bugzilla
Answers
Answer:
JMeter is a functional testing tool
Can someone please tell me the answer

Answers
We can see here that in converting sound from analogue to digital, we have:
A. The x- axis is the horizontal line while the y-axis is the vertical.
B. A is Quantization
B is Encoding process.
C is Decoding process.
What is sound energy?Sound energy is a form of energy that is produced by vibrations or disturbances in matter that create waves of pressure that travel through a medium such as air, water, or solids. The energy of sound is related to the amplitude or intensity of the sound wave, which is the measure of the magnitude of the pressure fluctuations caused by the sound.
Sound energy is typically measured in units of decibels (dB), which represents the relative intensity of the sound compared to a standard reference level. Higher decibel levels correspond to higher sound energy and louder sounds.
Learn more about sound energy on https://brainly.com/question/30763236
#SPJ1
insert a function in cell h18 to calculate the total number of orders based on entries in column a.
Answers
=COUNTA(A5:A13). Get the number of entries in a number field that is part of a range or array of numbers by using the COUNT function.
How can the text from cell A8 be displayed using a formula in cell B8?To display the text from cell A8 in all uppercase letters, enter a formula in cell B8. Click the Text button under the Function Library group on the Formulas tab. From the list, choose UPPER. In the Text box, enter "A8," then press OK.
What is the cell count formula?The number of cells in your suspension can be determined using the formula below: Total number of cells equals (total cells counted)/(4 squares counted)*10-4*initial volume*dilution factor; Observe.
To know more about array visit:-
https://brainly.com/question/19570024
#SPJ1
Choose the missing words in the code below.
quotient = numA/ numB
ZeroDivisionError:
print("You attempted to divide by zero")
print ("Quotient", quotient)
Answers
Answer:
try
except
else
Explanation:
just got it right
Answer:
try
except
else
Explanation:
What are two problems that can be caused by a large number of arp request and reply messages? (choose two. ).
Answers
Due to the traffic concentration from the linked subnets, switches get overloaded. The ARP request will overwhelm the entire subnet because it is transmitted as a broadcast.
What are the ARP difficulties and what caused them?Two computers sharing the same IP address frequently result in ARP table issues. Because the IP of the host that answered to the last ARP request the fastest is listed as the item in the table, the issues seem to come and go.
As to why Afailed?The arp cache's FAILED output means your server was unable to connect to the gateway. You may test this in your LAN by pinging any PC there, checking the arp status, disconnecting the PC, and then checking the arp status again.
To know more about ARP visit :-
https://brainly.com/question/12975431
#SPJ4RP
Activating the ______ will make the trigger stay in the operating mode even when it is released.
Answers
Answer:
Trigger lock
Explanation:
Elias is writing poems and is formatting several to fit on a page that has been divided into columns. Which column break would allow him to end one poem and start the next poem on the same page?
Question 6 options:
next page
sequential
text wrap
continuous
Answers
Answer:
Explanation:
Column break continous
in a hypertext markup language (html) file, the markers are the codes that tell the browser how to format the text or graphics that will be displayed.
Answers
In an HTML file, the codes or tags are used to indicate how the content should be displayed in a web browser. These tags can be used to format text, insert images and graphics, create links, and more. By using HTML codes, web developers can create dynamic and interactive websites that can be viewed on any device with an internet connection. Graphics can be added to an HTML file using the tag, which allows images to be displayed on a webpage.
In an HTML file, tags or codes are utilized to specify the presentation of content in a web browser. These tags serve various purposes, including formatting text, inserting images and graphics, creating hyperlinks, and more. With HTML codes, web developers can design dynamic and interactive websites that are accessible across different devices connected to the internet. To incorporate graphics into an HTML file, the `<img>` tag is employed, enabling the display of images on web pages. By utilizing these tags effectively, developers can enhance the visual appeal and functionality of web content, resulting in engaging and visually appealing websites.
Learn more about HTML: https://brainly.com/question/4056554
#SPJ11
Many project documents were introduced this week.
Respond to the following prompt in a minimum of 175 words and at least two paragraphs:
Determine which 2 documents you would consult to identify the stakeholder who might present the biggest potential problem for the project. Explain your choices.
Offer 2 other related project documents you will reference or update to help manage that stakeholder. Explain your choices.
Answers
When identifying the stakeholder who might present the biggest potential problem for a project, two documents that can provide valuable insights are the Stakeholder Register and the Risk Register.
The Stakeholder Register is a document that identifies and provides information about all stakeholders involved in the project. It typically includes their roles, responsibilities, interests, and level of influence. By consulting this document, project managers can identify stakeholders who may have conflicting interests, high levels of influence, or a history of challenging projects. Such stakeholders may present potential problems for the project due to their ability to impede progress, introduce delays, or create conflicts.
The Risk Register is another critical document that identifies and assesses potential risks that could impact the project. Within the Risk Register, there may be specific risks associated with stakeholder management. By reviewing this document, project managers can identify risks related to difficult stakeholders or those who may introduce obstacles that could affect project success. These risks could include resistance to change, lack of cooperation, or conflicting priorities.
To manage the stakeholder who presents the biggest potential problem, two other related project documents that can be referenced or updated are the Communication Plan and the Issue Log.
The Communication Plan outlines the communication strategies, channels, and frequency for engaging with stakeholders throughout the project. By updating the Communication Plan, project managers can tailor their communication approach to address the concerns and challenges associated with the problematic stakeholder. This may involve identifying specific messages, selecting appropriate communication channels, and determining the best timing for engaging with the stakeholder.
The Issue Log is a document that tracks and manages project issues as they arise. By referencing or updating the Issue Log, project managers can ensure that any concerns, conflicts, or obstacles associated with the problematic stakeholder are recorded and addressed in a systematic manner. This helps in tracking the progress of issue resolution, assigning responsibilities, and escalating issues to higher levels of management if needed.
In summary, by consulting the Stakeholder Register and the Risk Register, project managers can identify the stakeholder who might present the biggest potential problem for the project. To manage that stakeholder effectively, referencing or updating the Communication Plan and the Issue Log can provide valuable guidance in addressing their concerns, mitigating risks, and resolving issues that may arise throughout the project lifecycle.
To know more about Risk Register click the link below:
brainly.com/question/32533417
#SPJ11
give an example that shows that coordinate descent may not end the optimum of a convex function.
Answers
Coordinate descent is an iterative optimization method that iteratively minimizes the objective function along one coordinate at a time while holding all other coordinates fixed.
While this method is widely used for optimizing convex functions, there are situations where it may not converge to the global optimum. In other words, coordinate descent may end up at a suboptimal solution when optimizing a convex function.Let us take an example to understand this.
Suppose we want to minimize the following convex function f(x, y) = x^2 + 100y^2. Using coordinate descent, we start with an initial guess (x0, y0) and iteratively update the values of x and y as follows:x_{i+1} = argmin_{x} f(x, y_i)y_{i+1} = argmin_{y} f(x_{i+1}, y)At each iteration, we choose the coordinate that minimizes the objective function while holding all other coordinates fixed.
Therefore, we have the following update rules:x_{i+1} = 0y_{i+1} = 0However, it is easy to see that (x=0, y=0) is not the global optimum of f(x, y) = x^2 + 100y^2. The global optimum is at (x=0, y=0), which is not reached by coordinate descent in this case. Therefore, we can conclude that coordinate descent may not always converge to the global optimum of a convex function.
To know more about fixed visit:
https://brainly.com/question/29818792
#SPJ11
6C: Given the following AVL tree with a newly inserted node in double outline), choose the correct sequence of rotations to restore the height balance property + Inserts Single right rotation: move 2 up/right; 4 down/right B: Single left ratation move 7 up/left: 4 dawn/left Double rotation: first 6 up/right: 7 down/right then 6 up/left: 4 down/left D: Double rotation: first 7 up/left; 4 down/left then 6 upleft:4 down/left B D
Answers
Based on the given AVL tree, the correct sequence of rotations to restore the height balance property after a newly inserted node would be:
Single right rotation: Move 2 up/right; 4 down/right
Double rotation: First 7 up/left; 4 down/left then 6 up/left: 4 down/left
So the correct answer would be B and D.
For more questions like node visit the link below:
https://brainly.com/question/14448757
#SPJ11
The online underground is used___.
Select 3 options.

Answers
Answer:
I think its the 4th one but im not that sure tho sorry!
Explanation:
Answer:
1,3,4
Explanation:
By cybercriminals to sell ransom services,by cybercriminals to purchase malicious software,for networking by criminal organizations
Write a program that reads two integers, checks if a digit repeats 3 times in a row in the first integer and that same digit repeats two times in a row in the second integer.
Answers
Answer:
first_num = input("Enter integer digits (should be four or more digits): ")
sec_num = input("Enter integer digits (should be four or more digits): ")
num = '3'
if
def count_check( digit):
if (digit * 3) in first_num and (digit * 2) in sec_num:
print(True)
else:
print(False)
count_check(num)
Explanation:
The python source code above receives two values assigned to variables "first_num" and "sec_num" and defines a function called count_check to check if a digit occurs three consecutive times in the first input and two in the second to print a value of true or false otherwise.
True/False. In the cloud computing stack, a service provider hosts the application at its data center and customers access it via a standard Web browser.
Answers
In the cloud computing stack, a service provider hosts the application at its data center and customers access it via a standard Web browser is a False statement.
What is cloud computing?In order to provide quicker innovation, adaptable resources, and scale economies, cloud computing is the distribution of computer services over the Internet ("the cloud"), including servers, storage, databases, networking, software, analytics, and intelligence.
Hence, Service providers are people or businesses that offer services to businesses and other parties. They offer network, processing, and storage services. The service providers provide real estate, communication, educational, legal, and consulting services to organizations.
Learn more about cloud computing from
https://brainly.com/question/19057393
#SPJ1
how do we Rewrite the following Python code to avoid error. mark=inpt("enter your mark ")
Answers
Answer:
mark=input("enter your mark ")
Explanation:
the input method is used to get the input from the user.
T/F VLANs provide faster performance compared to switched, collapsed or routed backbone architectures
Answers
The statement is false because VLANs do not inherently provide faster performance compared to switched, collapsed, or routed backbone architectures.
The performance of a network depends on several factors such as the quality of network equipment, network design, bandwidth availability, and network congestion.
VLANs are primarily used for logical segmentation and improved network management, rather than directly impacting network performance. They allow for better control, security, and flexibility by dividing a physical network into multiple virtual networks.
Switched, collapsed, or routed backbone architectures can also provide efficient network performance, depending on their design, scalability, and configuration. The choice of network architecture and technologies should be based on the specific requirements, scalability needs, and performance goals of the network.
Learn more about VLANs https://brainly.com/question/31136256
#SPJ11
Write the definition of a function printDottedLine, which has no parameters and doesn't return anything. The function prints a single line consisting of 5 periods (terminated by a new line character) .
Answers
Answer:
See the short code Below
Explanation:
Let us implement the code with Python programming language
def printDottedLine ():
print("..... "\n) # this line will print 5 dots
there are 2 fields coming in on a file and we need to verify that the values populated are valid, without explicit direction from business. the two fields are dob (yyyymmdd) and ssn (000000000). true or false
Answers
In order to verify that the values populated in two fields, dob (yyyymmdd) and ssn (000000000) are valid, we need to check their formats and ensure that they meet the specified criteria.
To verify that the values populated in two fields, dob (yyyymmdd) and ssn (000000000), are valid without explicit direction from busines, follow the given steps :
1. For the dob field, check that it has exactly 8 characters and follows the format yyyymmdd. Ensure that the year, month, and day are within valid ranges (e.g., month between 01-12, day between 01-31 depending on the month and year).
2. For the ssn field, check that it has exactly 9 characters and is composed of numerical digits.
By following these steps, you can verify the values in both fields without needing explicit direction from the business.
To learn more about files visit : https://brainly.com/question/29511206
#SPJ11
question 2 what are the benefits of using a programming language for data analysis? select all that apply.
Answers
Analysis and Data Visualization: You can use data analysis platforms and tools to make sense of data by learning a programming language. Here, the major 3 are SQL, R, and Python. You may utilize data analysis and visualization libraries like Matplotlib and Plotly with Python.
What is meant by programming language?A programming language is a notational scheme used to create computer programs. While they occasionally include graphics, formal programming languages tend to be text-based. They are an instance of a computer language. The most widely used programming language today in the entire globe is JavaScript. It's used by the majority of web browsers and is one of the simplest languages to learn, so there's a strong reason for this. When you start studying JavaScript, you may practice and play with it right away; it practically doesn't require any prior coding experience. Common language styles include object-oriented, logical, functional, and imperative. To best suit their needs for a given project, programmers might select from among three coding language paradigms.To learn more about programming language, refer to:
https://brainly.com/question/16936315
Read the integer numbers in the text file "1000 Random Number from 0 to 100.txt" into a list
PLEASE HELP THANK U!!
Answers
Answer:
random_number_file = open("1000 Random Number from 0 to 100.txt", 'r')
random_number_list = random_number_file.readlines()
print('random_number_list)
Explanation:
The name of the file containing the random integer text is ; "1000 Random Number from 0 to 100.txt"
The random_number_file variable stores the opened file ("1000 Random Number from 0 to 100.txt") using the open keyword and reads it ('r')
This file stored in the random_number_file variable is the read into a list by using the readlines() method on the random_number_file
provide(s) many scalability benefits by offering additional network and storage resources on demand and services like autoscaling and load balancing.
Answers
Answer:
The answer is cloud services.
Explanation:
The other answer choices just don't make sense. Python is a coding language and has nothing to do with scalability. Benchmarking has to do with finding out how powerful your system is. Denial of Service is when a website doesn't allow you to access it due to their servers being down.
Which line of code will print I can code on the screen? print("I can code") print(I can code) print("I CAN CODE") print = I can code
Answers
The line of code that will print "I can code" on the screen is: print("I can code").
print("I can code"): This line of code uses the print() function in Python to display the text "I can code" on the screen. The text is enclosed within double quotation marks, indicating that it is a string.print(I can code): This line of code will result in a syntax error because "I can code" is not enclosed within quotation marks. Python interprets it as a variable or function call, which will throw an error if not defined.print("I CAN CODE"): This line of code will print "I CAN CODE" on the screen. However, it does not match the required output "I can code" exactly as specified in the question.print = I can code: This line of code will result in a syntax error because the assignment operator (=) is used incorrectly. It should be print("I can code") istead of assigning the string "I can code" to the print variable.Therefore, the correct line of code to print "I can code" on the screen is: print("I can code").
For more such question on line of code
https://brainly.com/question/13902805
#SPJ8
b. Differentiate between static and dynamic WebPages?in computer
Answers
1 Think about the five steps to writing an algorithm. Why is each step necessary?
2 Why is it important to be precise when writing computer code?
3 Some problems are better solved by a computer and some are better solved by humans. How do you know when a problem should be solved by a computer or by a person?
Answers
Answer and Explanation:
1. The steps in writing an algorithm include:
Step 1: obtain description of problem
Step 2: Analyze the problem. ...
Step 3: Develop a high-level algorithm.
Step 4: Refine the algorithm by adding more detail. ...
Step 5: Review the algorithm
In describing our problem we aim to define our problem and know exactly what problem we are looking to solve. We analyze and breakdown this problem to know where it begins and ends and therefore be able to understand it and develop algorithm to solve it. A high level algorithm is developed to fInd the main part of the problem and leave the details for later . We refine our algorithm and give more detail to further algorithm. We go ahead to review our algorithm to be sure it would solve the problem and ask questions like does it solve the problem and how much? Can the algorithm be simplified?
2. Computers are machines and therefore only understand instructions in the form of code languages. Coding must be precise because there is particular syntax and semantics in computer coding languages which if not followed cannot be understood by the computer
3. When a problem is repetitive and tedious at same time, it should be coded into computer programs and therefore automated
Digital and analog audio recordings have pros and cons. Do you think the pros of digital recordings outweigh the cons and therefore prefer digital audio recordings? Or, do you think the cons outweigh the pros and therefore you prefer analog audio recordings? Explain.
Answers
Digital vs Analog Audio is completely personal preference and there is no clear winner on which is better.
But there are some pros and cons about both, Analog sometimes distorts when playing and can be easily scratched and ruins the grooves. Analog is believed to be the true representation of the sound when it was recorded. Digital is not the actual recording of the sound, it's actually a combination of binary code. It is also sometimes mixed or remastered in Digital and sounds a bit different to make it sound better. It also depends on the system you are listening it from. You could have a horrible Digital system its playing through and an amazing Analog system playing, of course the Analog system will sound better in that case. Some believe that Digital is on par to overtake Analog in the "true picture of sound" category but some also say Analog will forever be the best at playing sound and Digital will always be the alternative.
But, in the end it's all personal preference and the pros and cons don't overweigh to make one better than the other.