Hardware Name:
Description:
Picture:
1. Motherboard
2. Power Supply
3. CPU (Central Processing Unit)
4. Random Access Memory (RAM)
5. Hard Disk Drive/Solid State Drive
6. Video Card
7. Optical Drives
8. Input and Output Devices
Answers
Answer:
I think 2.power supply yaar
Related Questions
Regarding a VDU, Which statement is more correct?
Answers
A VDU displays images generated by a computer or other electronic device.
What is regarding a VDU?The statement that a VDU is a peripheral device is more accurate in this case. Although "monitor" and "VDU" are frequently used interchangeably, the phrase can also refer to other displays, like digital projectors.
Visual display units may be incorporated with the other components or they may be peripheral devices. A VDU is a screen-equipped device that displays data from a computer. VDU stands for visual display unit in abbreviated.
In general, a peripheral device is any auxiliary item that interacts in some way with a computer, such as a computer mouse or keyboard. Expansion cards, graphics cards, and image sensors are other examples of peripherals.
To learn more about regarding a VDU refer to:
https://brainly.com/question/13704196
#SPJ1
Which measurement symbol is this?
PLS HELP ME
Answers
Answer:
hi! can you please leave the symbol so I can help you??
Explanation:
What does it mean, when a patch is displayed with a “key-shaped” symbol?
Answers
The patch needs to be purchased from the vendor, according to an icon in the shape of a key. Most of the fixes that are listed on the Patches tab can be patched using Qualys.
A security patch is what?If you use an Android device, security updates tailored to that platform are frequently released. These upgrades, which resemble standard patches, are intended to increase security and correct any flaws. An Android security update often doesn't include any new features, at least not ones you'd notice.
What's the process for Qualys patch management?Your remediation response time can be improved by automatically correlating vulnerabilities and patch data using Qualys Patch Management. due to the Qualys Cloud Agent's use in Qualys Patch Management.
To know more about Patches visit:-
https://brainly.com/question/30458260
#SPJ1
Should one own a smart home device
What are some security issues that one can find bothersome with these types of devices?
Answers
Yes, one can have or should one own a smart home device
Some security issues that one can find bothersome with these types of devices are:
Privacy concernsVulnerabilities to hackingLack of updatesWhat are the security issues?Smart home tools offer usefulness and can help create growth easier, but they further create freedom risks that should be deliberate.
Some freedom issues so that find bothersome accompanying smart home tools contain:
Lastly, in terms of Privacy concerns: Smart home ploys may accumulate individual dossier, such as custom patterns and choices, that could be joint accompanying after second-party parties for point or direct at a goal buildup or added purposes.
Learn more about security issues from
https://brainly.com/question/29477357
#SPJ1
How is blockchain different from traditional database models?
Blockchain can lead to increased transparency and trust in data, ultimately driving more innovation, improved productivity, and quality.
Blockchain prohibits transparency by redefining the fundamental nature of business ecosystems and business flows.
Blockchain provides multiple versions of the data that can be kept by individual entities.
Blockchain increases innovation; however, it decreases productivity and quality.
I don't know this yet.
Answers
The difference between blockchain and traditional database models is that: C. Blockchain provides multiple versions of the data that can be kept by individual entities.
What is a database?A database simply refers to an organized and structured collection of data that're stored on a computer system as a backup and they're usually accessed electronically.
What is a blockchain?A blockchain can be defined as a digital and dynamic financial system that is designed and developed to be used in recording and maintaining transactions that are associated with or made through the use of a bitcoin, usually as a database.
In this context, we can infer and logically deduce that unlike the traditional database models, blockchain is designed and developed to provide multiple versions of financial transactions (data), and they can also be kept by individual business entities.
Read more on blockchain here: brainly.com/question/25700270
#SPJ1
I. Direction: Write TRUE if the statement shows Principles of Facility Planning, and FALSE if
the statement is not.
1. An ideal facility building should serve in achieving the long-term goals of the
organization.
2. An ideal facility building should be unsustainable in long run.
3. A hotel lobby is difficult and cheap to maintain.
4. An ideal facility building should fulfill the needs of the intended user.
5. An ideal facility building should be in harmony with local community & law of the
land.
Answers
The following are either true or false in respect of Principles of Facility Planning/Management.
No. 1 is True. No. 2 is False. No. 3 is False. No. 4 is True. No. 5 is True.
What are the Principles of Facility Planning?The main principles of facility planning are given below:
The planner must coordinate the plans with other government agencies that provide facilities look at other options before selecting the final location for the facilitygive adequate justification for the proposed facilitydevelop a management plan that includes design priorities and operational strategiesuse the Life-Cycle Cost principles while designing ensure that it is in line with the organisations plans/goals etcPlease see the link below for more about Facility Management:
https://brainly.com/question/5047968
Twisted pair cables characteristics
Answers
Twisted pair cables are a type of copper cable consisting of two insulated wires twisted together to reduce electromagnetic interference.
What varieties do they come in?They come in two varieties, shielded and unshielded, and can support data transmission rates up to 10 Gbps over short distances. They are commonly used for Ethernet networking, telephone systems, and other communication applications.
Twisted pair cables have a maximum length of around 100 meters, and their performance can be affected by factors such as cable quality, interference from other devices, and environmental conditions.
Read more about twisted pair cables here:
https://brainly.com/question/13187188
#SPJ1
Starting a corporation is ________.
DIFFICULT
FAIRLY SIMPLE
ALWAYS NON-PROFIT
Answers
Starting a corporation is FAIRLY SIMPLE. (Option B). This is because there is such a vast amount of information and paid guidance that is available to those who want to start a corporation.
What is a corporation?A corporation is an organization—usually a collection of individuals or a business—that has been permitted by the state to function as a single entity and is legally recognized as such for certain purposes.
Charters were used to form early incorporated companies. The majority of governments currently permit the formation of new companies through registration.
It should be emphasized that examples of well-known corporations include Apple Inc., Walmart Inc., and Microsoft Corporation.
Learn more about Corporation:
https://brainly.com/question/13551671
#SPJ1
explain the major innavotions made from the establishment of abacus
Answers
Answer:
The abacus is one of many counting devices invented to help count large numbers.
Explanation:
write a java program to accept the Age of 23 student and print
Answers
PLEASE HELP ASAP!!!
Type the correct answer in the box.
What is the correct way to complete each sentence written by the author?
Broadcasting a film requires licensing and a copyright. Filmmakers need the blank license to bind non-actors from retracting their statements. They may also need a blank release to gain full permission to use copyright material. They may need a blank release that grants full permission to shoot at a particular location. Then, they need the blank license. This written agreement allows the filmmaker to visually reproduce copyright music. Finally, they also need a blank license to use a recording of a song in a film.
Answers
The right form is:
Broadcasting a film requires licensing and a copyright. Filmmakers need a release form to bind non-actors from retracting their statements. They may also need a release form to gain full permission to use copyrighted material. They may need a location release form that grants full permission to shoot at a particular location. Then, they need a synchronization license. This written agreement allows the filmmaker to visually reproduce copyrighted music. Finally, they also need a master use license to use a recording of a song in a film.What is the Sentence structure about?When a film is produced, it includes a variety of elements such as actors, locations, music, and copyrighted material that may be subject to legal rights and permissions. In order to legally broadcast a film, filmmakers need to obtain licenses and clearances for these elements.
Therefore, A release form is a legal document that binds non-actors from retracting their statements or appearances in the film. This is important for filmmakers as it protects them from any legal issues that may arise from individuals claiming they did not give permission to be in the film.
Learn more about Sentence structure from
https://brainly.com/question/364311
#SPJ1
e requirements of Phase 3 are as follows:
In this third phase, you will be obtaining the case, power supply, and monitor for your computer. You will also include a printer.
Case:
Analyze the specifications for the case. Discuss what stood out to you about your choice. For example, "Why did you choose this specific component?" What stood out to you (price, specifications, etc.)?
What are the specifications, source, and price of the case? How did each of these components influence your decision to select it?
Power Supply:
Analyze the specifications for the power supply. Discuss what stood out to you about your choice. For example, "Why did you choose this specific component?" What stood out to you (price, specifications, etc.)?
What are the specifications, source, and price of the power supply? How did each of these components influence your decision to select it?
Monitor:
Analyze the specifications for the monitor. Discuss what stood out to you about your choice. For example, "Why did you choose this specific component?" What stood out to you (price, specifications, etc.)?
What are the specifications, source, and price of the monitor? How did each of these components influence your decision to select it?
Printer:
Analyze the specifications for the printer. Discuss what stood out to you about your choice. For example, "Why did you choose this specific component?" What stood out to you (price, specifications, etc.)?
What are the specifications, source, and price of the printer? How did each of these components influence your decision to select it?
References:
List references used.
References should relate to decision-making articles in addition to a website where one could purchase the product.
All references must be in APA format.
Any images used must be cited properly.
Format:
APA formatted cover page as well as the entirety of the document.
Paragraphs are coherently organized, including the use of proper grammar and correct spelling.
Clearly organized using graphics and tables (where appropriate).
Acronyms are spelled out on first use.
Answers
Because this is a research that should b carried out, I will guide you on how to do same. Pay attention to the requirement on APA Formatting.
How can the above research be executed?In order to make an informed decision on each component, it is imperative that you conduct thorough research on their specifications, source and price.
Reliable sources of information such as reputable tech review websites should be utilized in the comparison of features and prices for each option available.
Proper citation using APA format will need to be observed together with inclusion of any images used. Organizing your document with clear and coherent structure will further enhance readability- utilizing tables and graphics where applicable.
Learn more about APA Formatting:
https://brainly.com/question/12548905
#SPJ1
this uses software to try thousands of common words sequentially in an attempt to guess a user's password.
Answers
Dictionary attack uses software to try thousands of common words sequentially in an attempt to guess a user's password. Hence option C is correct.
What is software?Software is defined as a set of guidelines, information, or software that you can use to run a computer and carry out the specific duties you need. It is the antithesis of hardware, which refers to a computer's external components.
A malicious attack use software to test thousands of popular terms in an effort to log into a user's account without authorization. Devices that use biometric authentication rely on physical traits to confirm user identity, such as fingerprints, facial patterns, iris or retinal patterns, or facial or iris patterns.
Thus, dictionary attack uses software to try thousands of common words sequentially in an attempt to guess a user's password. Hence option C is correct.
To learn more about software, refer to the link below:
https://brainly.com/question/985406
#SPJ1
Your question is incomplete, but probably your complete question was
This uses software to try thousands of common words sequentially in an attempt to guess a user's password.
A. Password
B. Firewall
C. Dictionary attack
D. Encryption
Consider the following statements:struct rectangleData { double length; double width; double area; double perimeter; }; rectangleData bigRect;Which of the following statements correctly initializes the component length of bigRect?a. bigRect[0]= 10 b. bigRect.length = 10; c. length[0]= 10; d. bigRect = {10};
Answers
The following statement is correct among the following: bigRect.length = 10 where the length of the rectangle can be initialized by its component length.
How to determine the correct statement for a rectangle's length?
To capture the length of the rectangle treating the rectangle variable as
bigRect to initialize the component length of bigRect
Two sides of the rectangle are length and breadth
So, to calculate the length of the rectangle, since it is the component we can get the length by using bigRect.length which gives the length, in the same way to calculate the breadth we can use
bigRectbreadth.length which gives the breadth of the rectangle
In the same way we can get the area of the rectangle as bigRect.length x bigRectbreadth.length which gives the area
To know more on programming in C following this link:
https://brainly.com/question/16936315
#SPJ4
In computer science what major jobs is appropriate for someone who majors in information systems
Answers
Answer:
manager
Explanation:
Write an acronym for the following set of information. The pieces of information can be remembered in any order. Your
acronym can be a real word or a nonsense word you are able to pronounce.
Native American Tribes: Apache, Comanche, Pequot, Sioux
Save and Exit
Next
Submit
Answers
ACOPS stands for "Apache, Comanche, Pequot, Sioux," representing four Native American tribes. Each tribe has a rich cultural heritage and historical significance.
What is the Apache tribe known for?The Apache tribe is known for their resilience and warrior tradition, while the Comanche tribe is recognized for their horsemanship and dominance in the Great Plains.
The Pequot tribe has a notable history in the northeastern region, particularly their interactions with European settlers.
The Sioux tribe encompasses various subgroups, such as the Lakota, Dakota, and Nakota, and played a significant role in the history of the American West. ACOPS provides a concise acronym to remember these diverse Native American tribes.
Read more about Native American tribes here:
https://brainly.com/question/3271247
#SPJ1
1.ShoppingBay is an online auction service that requires several reports. Data for each auctioned
item includes an ID number, item description, length of auction in days, and minimum required bid.
Design a flowchart or pseudocode for the following:
-a. A program that accepts data for one auctioned item. Display data for an auction only if the
minimum required bid is more than $250.00
Answers
The pseudocode for the program: Announce factors for the unloaded thing information, counting:
auction_id (numbers)
item_description (string)
auction_length (numbers)
minimum_bid (drift)
Incite the client to enter the auction_id, item_description, auction_length, and minimum_bid.
What is the pseudocode?The program acknowledges information for one sold thing, counting the auction_id, item_description, auction_length, and minimum_bid. It at that point checks in case the minimum_bid for the unloaded thing is more prominent than or rise to to $250.00.
The pseudocode for the program pronounces factors for the sold thing information and prompts the client to enter the information. At that point it employments an in the event that articulation to check in case the minimum_bid is more noteworthy than or break even with to 250.00.
Learn more about pseudocode from
https://brainly.com/question/24953880
#SPJ1

What is the first thing we should set up in SolidWorks when creating a new model?
Answers
Answer:
The first thing we should do is choose the units we would like to use.
Explanation:
When starting a new CAD file, the first thing we should do is choose the units we would like to use. The Unit system for the active document can be changed or customized using the System Units option on the Status Bar at the bottom of the SolidWorks window.
In what year was napier bone invented
Answers
The Napier's Bones is a manually-operated calculating device, invented by the Scottish mathematician John Napier in the early 17th century, around the year 1617.
What is Napier bone used for?Napier's Bones, also known as Napier's rods, are used for multiplication, division, and square root calculations. The device consists of a set of rectangular rods or bones with each bone representing a single digit in the multiplication table.
By manipulating the rods, users can quickly perform calculations that would otherwise be time-consuming to complete by hand. The Napier bone is an early example of a calculating device and is considered a predecessor to modern mechanical calculators.
Learn more about Napier bone at:
https://brainly.com/question/24242764
#SPJ1
PLEASE HELP!!!
I have no clue how to find my recently viewed images on the web on my windows 10. Please help, if you could also give a step-by-step image example or if that's too much I will and might give you brainly.
Answers
Answer:
To find your recently viewed images on the web on a Windows 10 computer, you can try the following steps:
Open the Start menu and type "history" into the search bar.
Click on "History" in the search results. This will open the history menu in your web browser.
In the history menu, click on the "Images" tab. This will show a list of all the images you have recently viewed on the web.
If you want to see more details about a specific image, you can click on it in the list to view its URL and the date it was viewed.
If you want to delete any images from your history, you can click on the checkbox next to the image and then click on the "Remove selected items" button.
Alternatively, you can use the search feature in your web browser to search for specific images that you have recently viewed. To do this, you can type the name or description of the image into the search bar and press Enter. This will show a list of search results, including any images that match your search criteria.
I hope this helps! Let me know if you have any questions or need further assistance.
Explanation:
For each of the descriptions below, perform the following tasks:
i) Identify the degree and cardinalities of the relationship.
ii) Express the entities and the relationships with attributes in each description graphically with an E-R diagram
A piano manufacturer wants to keep track of all the pianos it makes individually. Each piano has an identifying serial number and a manufacturing completion date. Each instrument represents exactly one piano model, all of which have an identification number and a name. In addition, the company wants to maintain information about the designer of the model. Over time, the company often manufactures thousands of pianos of a certain model, and the model design is specified before any single piano exists. (20p)
A piano manufacturer (see (e) above) employs piano technicians who are responsible for inspecting the instruments before they are shipped to the customers. Each piano is inspected by at least two technicians (identified by their employee number). For each separate inspection, the company needs to record its date and a quality evaluation grade. (14p)
The piano technicians (see (f) above) have a hierarchy of reporting relationships: some of them have supervisory responsibilities in addition to their inspection role and have multiple other technicians report to them. The supervisors themselves report to the chief technician of the company. (10p)
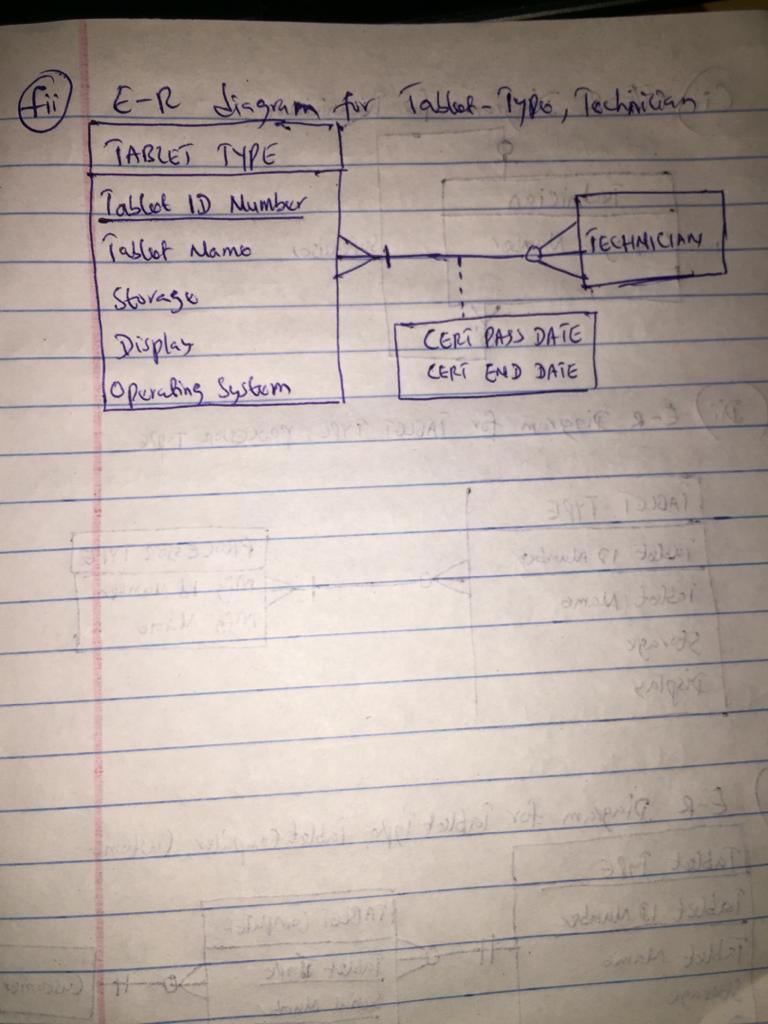
A vendor builds multiple types of tablet computers. Each type has a type identification number and a name. The key specifications for each type include amount of storage space and display type. The company uses multiple processor types, exactly one of which is used for a specific tablet computer type; obviously, the same processor can be used in multiple types of tablets. Each processor has a manufacturer and a manufacturerâs unique code that identifies it. (13p)
Each individual tablet computer manufactured by the vendor (see h above) is identified by the type identification number and a serial number that is unique within the type identification. The vendor wants to maintain information about when each tablet is shipped to a customer. (17p)
Each of the tablet computer types (see (h) above) has a specific operating system. Each technician the company employs is certified to assemble a specific tablet type â operating system combination. The validity of a certification starts on the day the employee passes a certification examination for the combination, and the certification is valid for a specific period of time that varies depending on tablet type â operating system combination. (11p)
Grading Schema:
1)Correct answer for degree in i) â 1p
2)Correct answer for cardinalities in i) â 1p
3)Entity with complete set of attributes including key attributes +4p
4)Incomplete set of attributes â (minus)-1p
5)Absence of key attributes if they defined â (minus)-1p
6)No or wrong attributes â (minus)-1p
7)Relationship with attributes +4p
8)Wrong left arrowhead â (minus)-1p
9)Wrong right arrowhead â (minus)-1p
10)Absence of relationship attributes â (minus)-1p
11)Relationship without attributes +3p
12)Wrong left arrowhead â (minus)-1p
13)Wrong right arrowhead â (minus)-1p
Answers
Answer:
attached below in the explanation and the diagrams attached
Explanation:
question
i) identify the degree and cardinality of the relationship
ii) Express the entities and the relationships with attributes in each description graphically with an E-R diagram
A)
i) The degree and cardinality of the relationship
The entities PIANO, MODEL and DESIGNER have a degree of two i.e. Binary relationship The cardinality of the entities PIANO, MODEL and DESIGNER have a relationship of ONE-to-manyii) description graphically with an E-R diagram
The E-R diagrams show that The degree of the relationship for the entities PIANO, MODEL, and DESIGNER is two(2). and also shows that there is a One-to-Many cardinality available in the entities PIANO, MODEL, and DESIGNER
E-R diagram Attached below
B)
i) The degree and cardinality of the relationship
entities PIANO and Technician have a degree of two ( 2 ) ; i.e. a Binary relationship The cardinality of the entities PIANO, and TECHNICIAN have a relationship of Many-to-Many.ii) Graphical description with an E-R diagram
The diagram describes/ shows that, entities PIANO and Technician have a degree of two ( 2 ) ; i.e. a Binary relationship and also The cardinality of the entities PIANO, and TECHNICIAN have a relationship of Many-to-Many.
E-R diagram attached below
C)
i) Degree and cardinality of the entity Technician
The entity TECHNICIAN has a degree one, i.e. a unary relationship. The cardinality of the entity TECHNICIAN have the relationship of One-to-Many.ii) E-R diagram attached below
D)
i) Degree and cardinality of the relationship
The entities TABLET TYPE and PROCESSOR TYPE have a degree of two(2) , i.e. a binary relationship The cardinality these entities TABLET TYPE, and PROCESSOR TYPE have is a Many-to-Many relationshipii) E-R diagram attached for TABLET TYPE, PROCESSOR TYPE is attached below
E)
i) Degree and cardinality of the relationship
The entities TABLET TYPE, TABLET COMPUTER, and CUSTOMER have a degree of two(2) ; i.e. a binary relationship. The cardinality these entities TABLET TYPE, TABLET COMPUTER, and CUSTOMER have is a One-to-Many relationshipalso the shipment to the customer is multiple hence the relationship can be said to be Many-to-Many relationship
also The attribute Shipping Date will become an attribute of that M: M relationship.
ii) The E-R diagram for TABLET TYPE, TABLET COMPUTER, CUSTOMER is attached below
F)
i) Degree and cardinality of the relationship between TABLET TYPE, TECHNICIAN
The entities TABLET TYPE, and TECHNICIAN have a degree of two(2); i.e. a binary relationship. The cardinality these entities TABLET TYPE, and TECHNICIAN have is a Many-to-Many relationshipii) E-R diagram attached below


Write a program that reads in an integer, and breaks it into a sequence of individual digits. Display each digit on a separate line. For example, the input 16384 is displayed as 1 6 3 8 4 You may assume that the input has no more than five digits and is not negative.
Answers
Answer:
The program in Python is as follows:
num = int(input())
for i in str(num):
print(int(i))
Explanation:
This gets input for the number
num = int(input())
This converts the number to string and iterates through each element of the string
for i in str(num):
This prints individual digits
print(int(i))
If I am working in a document and wish to follow a hyperlink, what should I do?
Copy the link and paste it in your web browser.
Hold the Control key and click on the link.
Click on the link.
Select Ctrl+K.
Answers
Answer:
Click on the link or copy and paste it to your browser
Explanation:
What computing paradigm can solve a problem by describing the requirements, without writing code in a step-wise fashion to solve the problem.
Answers
The computing paradigm that can solve a problem by describing the requirements, without writing code in a step-wise fashion to solve the problem is called; Imperative
Programming ParadigmThe correct answer here is Imperative Paradigm because imperative programming is a programming paradigm that utilizes statements which change the state of a program.
Now, further to the definition, an imperative program usually consists of commands that the computer should perform and this imperative programming focuses on describing the way that a program operates.
Read more about Programming paradigm at; https://brainly.com/question/14260799
wite a short essay recalling two instance, personal and academic, of when you used a word processing software specifically MS Word for personal use and academic work
Answers
I often use MS Word for personal and academic work. Its features improved productivity. One use of MS Word was to create a professional resume. MS Word offered formatting choices for my resume, like font styles, sizes, and colors, that I could personalize.
What is MS WordThe software's tools ensured error-free and polished work. Using MS Word, I made a standout resume. In school, I often used MS Word for assignments and research papers.
Software formatting aided adherence to academic guidelines. Inserting tables, images, and citations improved my academic work's presentation and clarity. MS Word's track changes feature was invaluable for collaborative work and feedback from professors.
Learn more about MS Word from
https://brainly.com/question/20659068
#SPJ1
What is installing?
the process of putting new software on a computer
the process of replacing an older version of software with a newer version
O the process of limiting who is allowed to access your information
O the process of programming a language to use on a web page
Answers
Answer:
The process of putting a new software on a computer.
Explanation:
Installing is the process of putting a new software on a computer.
Updating is process of replacing an older version of software with a newer version.
Select each procedure that could harm the computer and cause it to work improperly.
Answers
There are numerous actions that could potentially harm a computer and cause it to function improperly. Some of the most common ones are given below.
What is the actions that can harm a computer?Installing untrustworthy software or malware that can damage system files and slow down the computer's performance or steal personal information.Physically damaging the computer by dropping it, spilling liquids on it, or exposing it to extreme temperatures, which can cause hardware components to malfunction or fail entirely.Modifying or deleting system files, which can lead to system crashes and data loss.Overclocking or overheating the computer's CPU or GPU, which can cause hardware damage and potentially void any warranties.Failing to update software regularly, which can leave vulnerabilities in the system that hackers can exploit.Using unlicensed or pirated software, which can introduce viruses and other malware into the system.Opening suspicious emails or clicking on links from unverified sources, which can result in malware infections and data breaches.Learn more about computer at:
https://brainly.com/question/21080395?
#SPJ1
What is the importance of the Define stage when designing a game?
A.
It helps programmers choose what color scheme to use when making sprites.
B.
It helps programmer decide what features and elements to include in their flowchart and pseudocode.
C.
It helps programmers understand their audience so they can market their game to them.
D.
It helps programmers find errors in the game so they will know what to do when restarting the cycle.
Answers
The importance of the Define stage when designing a game is option B. It helps programmer decide what features and elements to include in their flowchart and pseudocode.
What is the game about?The Define stage of game design is a crucial step in the development process. During this stage, the designers and programmers plan and outline the general concept, objectives, and requirements of the game. This stage is important because it helps establish a clear understanding of what features and elements need to be included in the game.
Therefore, the Define stage plays a crucial role in the design process by helping to determine what features and elements need to be included in the game, and provides a foundation for the rest of the development process.
Learn more about game form
https://brainly.com/question/24855677
#SPJ1
Answer:
B
2.4.2 just did it
Explanation:
What is unit testing? a. Checking that the integer values of a function use proper units (yards, meters, etc.) b. Ensuring a program is not one large function but rather consists of numerous smaller functions (units) c. Dividing larger function parameters into several smaller parameters known as units d. Individually testing a small part (or unit) of a program, typically a function, using a separate program called a test harness
Answers
Answer:
d. Individually testing a small part (or unit) of a program, typically a function, using a separate program called a test harness.
Explanation:
A software development life cycle (SDLC) can be defined as a strategic process or methodology that defines the key steps or stages for creating and implementing high quality software applications. There are seven (7) main stages in the creation of a software and these are;
1. Planning.
2. Analysis.
3. Design.
4. Development (coding).
5. Testing.
6. Implementation and execution.
7. Maintenance.
Unit testing can be defined as a software development procedure that involves the process of individually testing a small part (or unit) of a program, typically a function, using a separate program called a test harness.
This ultimately implies that, if the observed behavior of the small part of a software program is consistent with the expectations, then the unit test is considered a pass. Otherwise, the unit test failed.
From the philosophical standpoint, especially in the discussion of moral philosophy or ethics, why do we consider “murder” or “killing” wrong or bad?
Answers
Explanation:
Morality is a set of values and habits that a society acquires over time and can be categorized as good and bad values, right and wrong, justice and crime. Ethics is defined as the study of morals, the practical application of moral behaviors defined by society.
Therefore, the concept of "murder" or "killing" is seen as an immoral act by the vast majority of society around the world, strengthened by the set of moral conduct common to all human beings, which are the Articles on the Universal Declaration of Human Rights. Human Rights, which is an official document of the UN, which contains several universair and analytical rules on the rights of every individual, such as the right to life, security, freedom, etc.