full form of SMPT???
Answers
Answer:
Simple Mail Transfer Protocol (SMTP) is the standard protocol for sending emails across the Internet.
Related Questions
What is self-confidence ? Is it necessary to have self-confidence ? Give an example to justify your answer .
Answers
Self-confidence is the belief in one's own abilities, qualities, and judgment. It is an important aspect of one's personality and plays a crucial role in achieving success in life.
What is personality?The term "personality" refers to the persistent traits, interests, motivations, values, self-concept, abilities, and emotional patterns that make up a person's particular way of adjusting to life.
The belief in one's own skills, talents, and judgment is known as self-confidence. It is an essential component of a person's personality and is essential to obtaining success in life.
People with self-confidence are able to take calculated risks, overcome difficulties, and persevere in the face of failures and disappointments.
Self-confidence is crucial because it enables people to adopt a positive perspective on their capabilities and selves, which can enhance their mental health and general wellbeing.
Thus, it is important to have self-confidence.
For more details regarding self-confidence, visit:
https://brainly.com/question/2222347
#SPJ9
(a) Discuss Strategy, Architecture and Infrastructure implementation for an Internet café environment in Malaysia.
(b) Explain the TWO (2) advantages and TWO (2) disadvantages of Infrastructure long term planning as compared to short term planning for an Internet café environment in Malaysia. Suggest TWO (2) solutions to minimize the disadvantages.
Answers
Internet café in Malaysia, it is crucial to develop a strategy aligned with business goals, identify the target market, and determine pricing models and marketing strategies.
(a) Strategy, Architecture, and Infrastructure Implementation for an Internet Café Environment in Malaysia: To establish an Internet café in Malaysia, it is crucial to develop a strategy aligned with business goals, identify the target market, and determine pricing models and marketing strategies. Design a user-friendly layout for the café, ensuring easy access to workstations. Provide reliable internet connectivity, invest in quality hardware, and implement data security measures. (b) Advantages and Disadvantages of Infrastructure Long-Term Planning in an Internet Café Environment in Malaysia:
Advantages: Long-term planning allows for scalability and cost efficiency, anticipating future growth and reducing frequent infrastructure changes. Disadvantages: Technological obsolescence and limited flexibility may occur with long-term planning. Solutions to minimize disadvantages: Regular technology assessments and adopting a modular infrastructure design can help minimize the risks of obsolescence and provide flexibility for future upgrades or replacements.
Learn more about infrastructure planning for an Internet café environment in Malaysia here:
https://brainly.com/question/33489272
#SPJ11.
Explain why the receptionist responded as indicated in the following scenario.
Situation: Jim and Roger are meeting with the executives of the company. They are both wearing blue jeans, polo shirts, and ties. As they walk past the receptionist, he stops them and reminds them the dress code is white collar.
Answers
Hope this helps!
What does the Flippy Do Pro show about representing very small numbers?
Answers
Answer:
it shows number that is near the target figure, but not the actual figure
Explanation:
What Flippy Do Pro reveal about representing a very small number is a number that is near the expected number in value. This is because Flippy Do Pro would not reveal some particular lesser numbers in their precise value.
However, this often results in roundoff blunder, which is mostly caused by the inability of bit compositions to depict the outcome of numbers as it should precisely be.
The advantage of a digital camera in taking nighttime photographs is that you can see
the results right away.
• True
© False
Answers
Answer:
Ima say true
Explanation:
The Internet is a(n) ______
made up of wires, cables, satellites, and rules for exchanging information between computers connected to the network.
A. Physical network
B. Virtual network
C. Multimedia interface
D. Domain name
Answers
Answer:
The Internet is a(n) B. Virtual network made up of wires, cables, satellites, and rules for exchanging information between computers connected to the network.
Explanation:
Recall when you built your information sending device. Why did we decide to send a message as a sequence of two options rather than modifying our devices to represent more options
Answers
Learn more:
brainly.com/question/13187838
software-based virtual private networks (vpns) are typically more scalable than hardware vpns.T or F
Answers
True.
Software-based virtual private networks (VPNs) are typically more scalable than hardware VPNs. This is because software VPNs can be easily installed and configured on a larger number of devices, and can be easily scaled up or down as needed. Additionally, software VPNs can be used on a wider range of operating systems and devices, making them more versatile and flexible than hardware VPNs.
Software VPNs are simple to set up and install on a variety of devices: Software VPNs can be set up on any device that can run the required software, as opposed to hardware VPNs, which need to be installed on physical devices.
As a result, software VPNs are more scalable because they can be set up on more devices.
Software VPNs provide for simple scaling up and down based on demand: Software VPNs may be readily scaled up or down to meet demand as the number of devices requesting VPN connection rises or falls.
A wider variety of devices and operating systems support software VPNs: Because they may be used with a larger variety of operating systems and devices, software VPNs are often more adaptable and flexible than hardware VPNs.
Hardware VPNs may need more substantial configuration adjustments or extra actual hardware to handle rising demand: Scaling up a hardware VPN might be more expensive and time-consuming than scaling up a software VPN since it may be necessary to add more physical devices or make more significant configuration adjustments to handle rising demand.
Learn more about virtual private networks (VPNs) :
https://brainly.com/question/29671312
#SPJ11
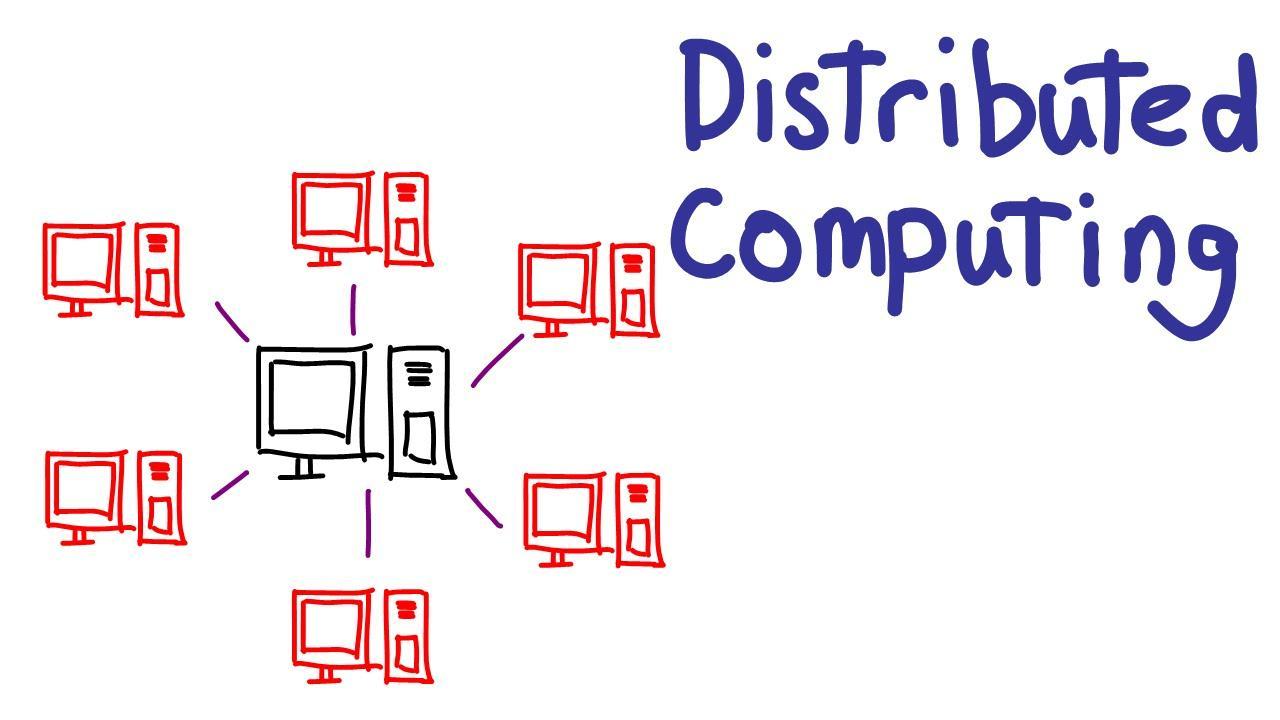
Which of these applications is NOT an example of distributed computing?a. Excel is a spreadsheets application developed by Microsoft. An Excel spreadsheet can contain many formulas that require computation, so loading a spreadsheet or changing its data can take a lot of time. To speed up the process, Excel is configured to utilize all of a computer's processors at once for concurrent computation.b. The Great Internet Mersenne Prime Search is a project to find Mersenne prime numbers, a special kind of prime number which is one less than a power of 2. Volunteers run the GIMPS application onto their home computer. The application checks numbers for primality and notifies the main server if it finds a Mersenne prime. As of 2019, GIMPS had found 17 Mersenne primes.c. A Beowulf cluster is a collection of computers that are networked with each other and run software that makes it easy for them to send messages to each other. Beowulf clusters are used for tasks that need increased computing power such as speech recognition and astrophysics simulations.d. SiteWhere is an open source platform for creating sensor networks. Anyone can install the SiteWhere platform on a server and then configure sensors to communicate with the server. SiteWhere can be used for use cases such as home automation or vehicle tracking.
Answers
Option A is not distributed computing because this Excel application is not using: Internet, many computers connected to achieve better levels of processing, nor hundreds of volunteer users, which are essential features of distributed computing.
What is distributed computing?It is a system approach, software development, implementation work, where hundreds of computers connected locally and globally are used in order to achieve a development goal.
In this sense, when you implement distributed computing each computer in the network adds more data processing and storage capacity, human resources, and other components in order to raise the work potential to levels much higher than those of any local computer.
To learn more about distributed computing see: https://brainly.com/question/20769806
#SPJ4
9. Which of the following statements about polymorphism is correct? a) Polymorphism is only possible through inheritance. b) Polymorphism is only possible through interfaces. c) Polymorphism is only possible through abstract classes. d) Polymorphism is possible through both inheritance and interfaces. e) Polymorphism is always possible.
Answers
Form the given statements, Polymorphism is possible through both inheritance and interfaces is True. Polymorphism refers to the ability of objects to take on different forms or to exhibit different behavior in different situations. So, option D is the correct answer.
Polymorphism in object-oriented programming refers to the ability of an object to take on multiple forms. Polymorphism enables treating objects from different classes as if they belong to a shared superclass or interface.
Inheritance is one way to achieve polymorphism by creating a hierarchy of classes where a subclass can override methods of its superclass.
Interfaces also enable polymorphism by defining a contract that classes can implement, allowing them to be treated uniformly through the interface type. Therefore, polymorphism can be achieved through both inheritance and interfaces. So, the correct option is d.
To learn more about polymorphism: https://brainly.com/question/29887432
#SPJ11
To prevent and remove malware infections you should manually install and run anti-malware software, keep software and OSes up to date with current patches, and be careful when downloading files, programs, attachments, and such.
True
False
Answers
To find the location’s name of the cell, look to the . To add an action to the cell for that data, add commands in the . To move from one cell to the next, use .
Answers
Answer:
Name Box
Formula Bar
Either Tab or Enter
Explanation:
Answer:
To find the location’s name of the cell, look to the
✔ name box
.
To add an action to the cell for that data, add commands in the
✔ formula bar
.
To move from one cell to the next, use
✔ either tab or enter
.
Explanation:
Which loop prints the numbers 1, 3, 5, 7, …, 99?\
c = 1
while (c <= 99):
c = c + 2
print(c)
c = 1
while (c < 99):
c = c + 1
print(c)
c = 1
while (c <= 99):
print(c)
c = c + 2
c = 1
while (c < 99):
print(c)
c = c + 1
Answers
The loop that prints the numbers 1, 3, 5, 7, …, 99 is:
The Loopc = 1
while (c <= 99):
print(c)
c = c + 2
This loop initializes the variable c to 1, then enters a while loop that continues as long as c is less than or equal to 99.
During each iteration of the loop, the value of c is printed using the print function, and then c is incremented by 2 using the c = c + 2 statement.
This means that the loop prints out every other odd number between 1 and 99, inclusive.
Read more about loops here:
https://brainly.com/question/19344465
#SPJ1
Cryptocurrency is a form of payment that:
• A. can be used for digital or face-to-face transactions.
•
B. can only be exchanged for specific things.
®
C. exists online and in local banks.
•
D. can be exchanged online for goods and services.
Answers
Cryptocurrency is a form of payment that can be used for digital or face-to-face transactions. Option A is the correct answer.
Cryptocurrencies is a decentralized digital currency that is secured through cryptography, and it exists solely online. Cryptocurrencies are not backed by any government or financial institution and can be used to purchase goods and services, as well as exchanged for other currencies. Transactions made using cryptocurrency are recorded in a decentralized public ledger called a blockchain.
Cryptocurrency can be stored in digital wallets and can be bought and sold on various online exchanges. As it is not bound by traditional banking regulations, cryptocurrency has the potential to offer a more secure and efficient way to make payments.
Option A is the correct answer.
You can learn more about Cryptocurrency at
https://brainly.com/question/26103103
#SPJ11
Assume you need to create a presentation on the effects of global warming. Keeping the topic in mind, you need to
focus on certain key guidelines while creating the presentation. In a table, list those appropriate guidelines that you
would follow to create an effective presentation. Your table should have guidelines related to image choices, font
size for the heading and body text, background and text color for the slide, number of bullet points you will use,
and number of words per line. Also, provide your rationale about the choices for these elements.
Answers
Answer:
................................................................................................
Explanation:

Which of the following numbers might this code generate: random.randint(1,9)?
0
10
11
1
Answers
Answer:
1
Explanation:
In Python programming language, the random.randint function is an abbreviation for random integers.
Basically, the random.randint is used for generating or creating a random integer numbers.
The syntax for this code can be written as;
A = random.randint(1,9)
Print ("Random number between 1 and 9 is % s" % (A))
Note, the numbers between 1 and 9 are 1, 2, 3, 4, 5, 6, 7, 8 and 9.
From the answer choices given (0, 1, 10 and 11), the only number that matches the requirement is 1.
Therefore, the number this code random.randint (1,9) might generate is 1.
With the knowledge of computer studies or ICT mention two methods of keeping material
Answers
Answer:
ICT teaching tools include simulation, modelling, CD-ROMs, teacher web publishing, word processing, spreadsheets, data logging, databases, e-mail, smart boards, interactive whiteboards and Internet browsing.
Explanation:
Discuss how you communicate with your project team/co-workers.
o What are some of the advantages/disadvantages of different technologies used? (i.e. virtual meetings, social media, instant messaging, texting, etc.)
o What have you done/seen done to overcome any verbal/nonverbal communication barriers?
o Discuss how you communicate with important project stakeholders.
Answers
As a project team member or co-worker, communication is key to ensure smooth collaboration. Different technologies offer advantages and disadvantages in this regard. Virtual meetings, for example, allow for face-to-face interactions regardless of geographical location.
This fosters better engagement and understanding among team members. Social media platforms provide a convenient way to share updates and gather feedback. However, it is important to be mindful of distractions and potential misuse of these platforms.Instant messaging and texting offer quick and efficient communication, enabling immediate responses and clarifications. However, they can be prone to misinterpretation due to the lack of nonverbal cues and tone of voice. To overcome this, it is crucial to be clear and concise in your messages and use emojis or emoticons when appropriate to convey emotions.
To address verbal/nonverbal communication barriers, active listening is essential. Paraphrasing and asking clarifying questions can help ensure everyone is on the same page. Additionally, utilizing video calls or meeting in person can enhance nonverbal communication and build stronger relationships.When communicating with project stakeholders, it is vital to provide regular updates and involve them in decision-making processes. Clear and concise reports, presentations, and meetings tailored to their needs can effectively convey information and address any concerns they may have.
To know more about collaboration visit:
https://brainly.com/question/31675403
#SPJ11
Create an infographics using the Word Processing Software, informing the audiences about internet safety practices.
Answers
Here is a suggested infographic on internet safety practices using Microsoft Word:
[A Word document shows the following infographic:]
Staying Safe Online
Protect your personal information. Never share your name, address, phone number, passwords, or Social Security Number on social media or public websites.
Be wary of phishing emails and malicious links. Never click links or download attachments from unknown or untrusted sources. Legitimate companies will not ask for sensitive data via email.
Use strong and unique passwords. A strong password contains a minimum of 8 characters, a mix of letters, numbers and symbols, and is not based on personal information. Use different passwords for different online accounts.
Be cautious of what you post. Anything you post online can potentially last forever. Do not post anything that you would not want seen by anyone.
Turn on two-factor authentication whenever possible. This adds an extra layer of security for your accounts like email, social media, and cloud storage services.
Ensure all devices and software are up to date. Install the latest updates to keep security patches current to protect against threats.
Be wary of public Wi-Fi networks. Public networks are not secure and all your online activity and information can be visible to others. Avoid conducting sensitive activities on public Wi-Fi.
Signal for help if anything suspicious happens. If you notice any suspicious activity on your accounts or devices, changing passwords or unauthorized logins, report it immediately to the concerned companies and consider filing a police report.
Online privacy and security is a shared responsibility. Be proactive and spread awareness about internet best practices to help keep everyone safe online. Together, we can make the internet a safer place!
Does this infographic look okay? I tried to highlight some key best practices around protecting personal information, using strong passwords, being cautious of what is posted online, enabling two-factor authentication, keeping software up to date, avoiding public Wi-Fi and knowing how to get help if needed. Please let me know if you would like me to modify anything in the infographic. I can also suggest some other topics or formatting styles if required.
A brief overview of some important internet safety practices that you can include in your infographic using the Word Processing Software is given.
How to explain the informationUse strong passwords: Use a combination of uppercase and lowercase letters, numbers, and symbols in your passwords, and avoid using personal information.
Enable two-factor authentication: Two-factor authentication provides an extra layer of security by requiring a second form of authentication in addition to your password.
Be careful with personal information: Don't share personal information like your full name, address, phone number, or social security number online.
Learn more about Word Processing on
https://brainly.com/question/985406
#SPJ1
what is cicada 3301? i will give brainliest if you give me a correct answer (not copy and pasted) and somewhat well detailed, i guess
Answers
Answer:
From what I know it's a seris of web puzzles dating a few years back. The creators were looking for really smart people to work in their organizations as coders
You have a Mobile Legends account???
Can I play with You???
Answers
Answer:
yes oo you want to play with me
A virus does not harm the ________ of a computer
Answers
Answer:
Hardware part
Explanation:
The hardware part of computer is not harmed by virus.
I hope this will be helpful for you
Answer: Hardware part
Simple Arithmetic Program
Using the instructions from Week 1 Lab, create a new folder named Project01. In this folder create a new class named Project01. This class must be in the default package. Make sure that in the comments at the top of the Java program you put your name and today's date using the format for Java comments given in the Week 1 Lab.
For this lab, you will write a Java program to prompt the user to enter two integers. Your program will display a series of arithmetic operations using those two integers. Create a new Java program named Project01.java for this problem.
Sample Output: This is a sample transcript of what your program should do. Items in bold are user input and should not be put on the screen by your program. Make sure your output looks EXACTLY like the output below, including spacing. Items in bold are elements input by the user, not hard-coded into the program.
Enter the first number: 12
Enter the second number: 3
12 + 3 = 15
12 - 3 = 9
12 * 3 = 36
12 / 3 = 4
12 % 3 = 0
The average of your two numbers is: 7
A second run of your program with different inputs might look like this:
Enter the first number: -4
Enter the second number: 3
-4 + 3 = -1
-4 - 3 = -7
-4 * 3 = -12
-4 / 3 = -1
-4 % 3 = -1
The average of your two numbers is: 0
HINT: You can start by retyping the code that was given to you in Exercise 3 of ClosedLab01. That code takes in a single number and performs a few arithmetic operations on it. How can you modify that code to take in two numbers? How can you modify it to display "number * number =" instead of "Your number squared is: "? Take it step by step and change one thing at a time.
You can use the following as a template to get you started. Note that you must create your class in the default package and your project must be named Project01.java for the autograder to be able to test it when you submit it.
Answers
Answer:
Written in Java
import java.util.*;
public class Project01{
public static void main(String[] args) {
Scanner input = new Scanner(System.in);
int num1,num2;
System.out.print("Enter first number: ");
num1 = input.nextInt();
System.out.print("Enter second number: ");
num2 = input.nextInt();
System.out.println(num1+" + "+num2+" = "+(num1 + num2));
System.out.println(num1+" - "+num2+" = "+(num1 - num2));
System.out.println(num1+" * "+num2+" = "+(num1 * num2));
System.out.println(num1+" / "+num2+" = "+(num1 / num2));
System.out.print("The average of your two numbers is: "+(num1 + num2)/2);
}
}
Explanation:
import java.util.*;
public class Project01 {
public static void main(String[] args) {
Scanner input = new Scanner(System.in);
This line declares myfirstnum and mysecnum as integer
int myfirstnum,mysecnum;
This line prompts user for first number
System.out.print("Enter first number: ");
This line gets user input
myfirstnum= input.nextInt();
This line prompts user for second number
System.out.print("Enter second number: ");
This line gets user input
mysecnum = input.nextInt();
This line calculates and prints addition operation
System.out.println(myfirstnum+" + "+mysecnum+" = "+(myfirstnum + mysecnum));
This line calculates and prints subtraction operation
System.out.println(myfirstnum+" - "+mysecnum+" = "+(myfirstnum - mysecnum));
This line calculates and prints multiplication operation
System.out.println(myfirstnum+" * "+mysecnum+" = "+(myfirstnum * mysecnum));
This line calculates and prints division operation
System.out.println(myfirstnum+" / "+mysecnum+" = "+(myfirstnum / mysecnum));
This line calculates and prints the average of the two numbers
System.out.print("The average of your two numbers is: "+(myfirstnum + mysecnum)/2);
}
}
Omar wants to research additional information about asteroids. Complete the sentences to describe how he should use the Smart Lookup feature in PowerPoint. Step 1: He should ____________ the word asteroid. Step 2: He should navigate to the _________ tab. Step 3. He should go to the __________ command group. Step 4: He should turn on the Intelligent Services of PowerPoint in the pane. Step 5: He should click the ________ option to open links that contain information about asteroids. Please answer quickly! It is quite urgent
Answers
Answer:
Step 1: He should
✔ select
the word asteroid.
Step 2: He should navigate to the
✔ Review
tab.
Step 3. He should go to the
✔ Insights
command group.
Step 4: He should turn on the Intelligent Services of PowerPoint in the pane.
Step 5: He should click the
✔ Explore
option to open links that contain information about asteroids.
Explanation:
Edg2020
Omar should use the Smart Lookup feature in PowerPoint in several steps 1. Select, 2. Review, 3. Insights, 4. Explore.
What is the Smart Lookup feature in PowerPoint?The new Smart Lookup feature in PowerPoint 2016 for Windows is an option that shows up definitions, images, and other results from various online platforms about a word or phrase, right within PowerPoint.
There are four steps to use the Smart Lookup feature in PowerPoint:
Step 1: He should select the word asteroid.
Step 2: He should navigate to the Review tab.
Step 3. He should go to the Insights command group.
Step 4: He should turn on the Intelligent Services of PowerPoint in the pane.
Step 5: He should click the Explore option to open links that contain information about asteroids.
Therefore, he should use 1. Select, 2. Review, 3. Insights, 4. Explore.
Learn more about PowerPoint, here:
https://brainly.com/question/19238885
#SPJ2
Write a program to:
• It will collect and output some basic data about the user such as name, and gender which will be
displayed with an accompanying welcome message [3]
• Use appropriate data structures to store the item code, description and price information for
the mobile devices, SIM cards and accessories [2]
• Allow the customer to choose a specific phone or tablet [3]
• Allow phone customers to choose whether the phone will be SIM Free or Pay As You Go [2]
• Calculate the total price of this transaction [4]
• Output a list of the items purchased and the total price. [3]
• Any other choice outside of these three categories would give out appropriate message to the
user and requesting the user to make a new choice. [2]
Answers
According to the question, a program using appropriate data structures are given below:
#include <iostream>
#include <string>
#include <vector>
#include <map>
using namespace std;
int main() {
string name;
string gender;
cout << "Please enter your name: ";
cin >> name;
cout << "Please enter your gender (male/female): ";
cin >> gender;
cout << "Welcome " << name << ", you are a " << gender << ".\n\n";
map<string, vector<string>> items;
items["mobile"] = {"iphone11", "1000", "samsungs20", "800"};
items["sim"] = {"sim1", "30", "sim2", "40"};
items["accessories"] = {"charger", "20", "headphone", "30"};
string choice;
cout << "Please choose a device (mobile/sim/accessories): ";
cin >> choice;
string phone;
if (choice == "mobile") {
cout << "Which phone do you want to buy (iphone11/samsungs20) ? ";
cin >> phone;
cout << "Do you want to buy a SIM Free or Pay As You Go ? ";
cin >> choice;
}
int totalPrice = 0;
for (auto item : items[choice]) {
totalPrice += stoi(item);
}
cout << "You have chosen " << phone << " (SIM Free/Pay As You Go) and your total price is: " << totalPrice << endl;
if (choice != "mobile" && choice != "sim" && choice != "accessories") {
cout << "Please choose a valid item from the list (mobile/sim/accessories)." << endl;
}
return 0;
}
What is data structures?Data structures are the way in which data is organized and stored in a computer system. Data structures provide a means to manage large amounts of data efficiently, such as large databases and internet indexing services. Data structures are used in almost every program or software system. They are essential in providing an efficient way to store and retrieve data. Data structures are divided into two categories: linear and non-linear. Linear structures include arrays, linked lists, stacks, and queues.
To learn more about data structures
https://brainly.com/question/24268720
#SPJ9
Murphy communications has been running a vlan-managed network to connect different devices. you as a network analyst want to assign a name to the vlan network, but you are unable to do so. what kind of vlan is most likely being used in the organization?
Answers
The kind of VLAN likely to be used in this organization is Default VLAN
VLAN stands for Virtual Local Area Network. Default VLAN
Following the switch's initial bootup, all switch ports join the default VLAN. The broadcast domain is shared by all of these ports because they participate in the default VLAN. As a result, any device on any port can communicate with devices on other switch ports.
Any untagged data packets will be tagged with the default VLAN tag on ports with a configured default VLAN. Also, before leaving these ports, incoming data packets with the default VLAN tag will be untagged.
Configuring all switches' ports to be associated with VLANs other than VLAN 1 is a security best practice. Usually, to do this, all open ports are given to a black hole VLAN that is not used for any network activities.
learn more about Default VLAN here: https://brainly.com/question/5789383
#SPJ4
answer luca knows a little bit about computers and is asked to help set up a small office with seven computers and an older high-quality printer that does not have an ethernet port. luca connects the printer to a computer and configures sharing. however, none of the computers seem able to connect or send jobs to the printer. what should luca do?
Answers
Since Luca connects the printer to a computer and configures sharing and, none of the computers seem able to connect or send jobs to the printer. The thing that Luca can do is to Install the driver for the said printer on all of the computers.
Does printing require a driver?Without using a printer driver, the direct print function sends a file from the host terminal to the printer, enabling the printer to recognize the file and print.
Consequently, you can print without opening a file. A printer driver is a piece of software that converts your computer's data into a format that can be understood by your printer.
Therefore, your computer must learn how to communicate with each specific printer because they are each built with unique hardware and software. For this purpose, a printer driver is used.
Learn more about Printer drivers from
https://brainly.com/question/29312634
#SPJ1
An insurance organization has data on a large number of claims made by policyholders. The management has a process in place to regularly check the data warehouse for fake claims. Which application of data mining does the organization use? A. market segmentation B. customer retention C. fraud detection D. direct marketing
Answers
The application of data mining the organization uses is known as : Fraud detection.
What is data mining?Data mining refers to the process of retrieving data that can be worked on from a large set of data, to solve business problems and reduce risk.
In a data mining process, the aim is to find anomalies and correlation so that outcomes can be predicted using different types of techniques.
Hence, the application of data mining the organization uses is known as fraud detection.
Learn more about data mining here : https://brainly.in/question/2000228
Answer:
C. Fraud Detection
Explanation:
2.4 Code Practice: Question 1
Write the code to input a number and print the square root. Use the absolute value function to make sure that if the user enters a negative number, the program does not crash.
Answers
Answer:
num = float(input("Enter a number : "))
ab = abs(num)
sqrt = float(ab ** 0.5)
print(sqrt)
Explanation:
If you had an idea for a new software company, what would be the best approach to help make it a successful business?
-develop a business plan to describe how to maintain and grow revenues
-go back to school to get a degree in IT business administration
- hire employees who understand the software development industry
-seek out financial support for venture capital, angel investors and grants
Answers
Answer:
a
Explanation: